pfSense and APIPA (169.254/16): Enabling Link-Local Transit Networks for IPsec VTI and BGP
Using APIPA (169.254.x.x) addresses as a transit network for IPsec IKEv2 VTI tunnels is a common best practice in major cloud environments such as AWS, Azure, and Google Cloud Platform, where these link-local ranges are reserved for internal VPN and BGP peer connections.
On pfSense, however, this setup doesn’t work out of the box, the system blocks APIPA traffic by default for security reasons.
Even if the tunnel and BGP configuration appear correct, no traffic will pass until this restriction is explicitly lifted.
To use APIPA-based transit networks successfully on pfSense, we must first enable APIPA traffic in the advanced system settings or by applying a short PHP command to disable the default block rule.
Enabling by using the Web GUI Option
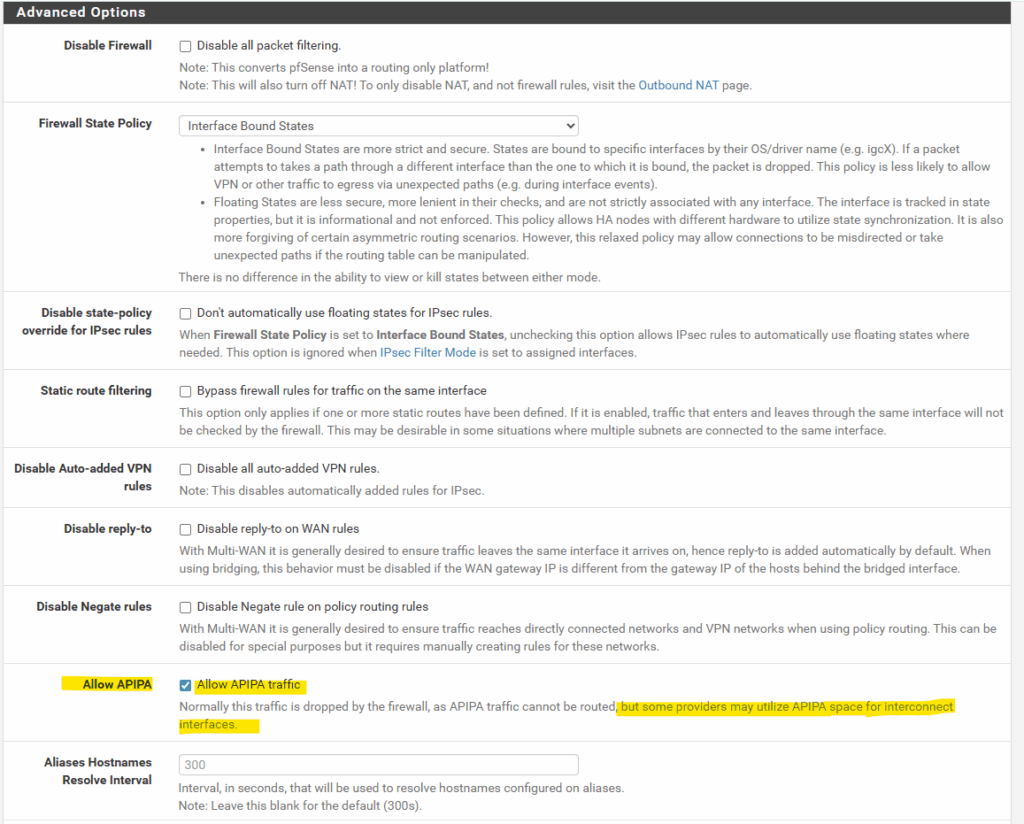
Or in pfSense version 2.5 and later we can just go to System -> Advanced ->Firewall & NAT and here within the Advanced Option section we can check Allow APIPA as shown below.
Firewall & NAT -> Allow APIPA
When Allow APIPA traffic is checked, the default block rules are removed, and user firewall rules can control the traffic.
There are some use cases which utilize these addresses for private communication on an interface, such as AWS VPC BGP, and in those cases, the option can be enabled along with carefully crafted manual firewall rules.
Enabling by using the Web GUI Diagnostics Command Prompt and PHP Script
Or by running the following PHP command under Diagnostics -> Command Prompt.
$config['system']['no_apipa_block'] = true;
write_config("Do not block APIPA");
send_event("filter reload");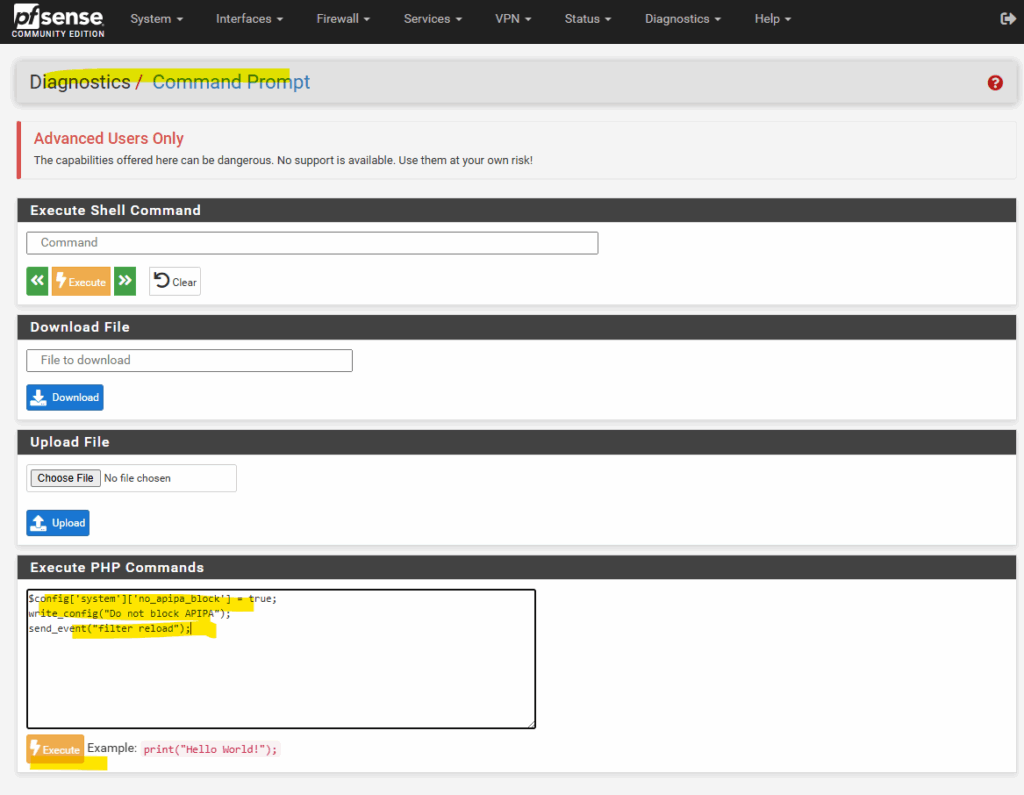
Links
Firewall & NAT -> Allow APIPA
https://docs.netgate.com/pfsense/en/latest/config/advanced-firewall-nat.html?utm_source=chatgpt.com#allow-apipa
Tags In
Related Posts
Follow me on LinkedIn


