Mastering Windows Updates & Microsoft Updates – Part 3 – Controlling Automatic Updates in On-Prem and Cloud Environments
Keeping Windows servers properly patched can feel deceptively simple, until you realize that automatic updates don’t behave the same everywhere.
Whether it’s an on-prem VM, an Azure instance managed by Update Manager, or a GCP VM under OS Patch Management, each environment has its own logic that decides if and when updates install automatically.
In this post, we’ll look at how to determine a system’s default update behavior, how Windows decides to apply patches without explicit Group Policy settings, and how you can take back control across both on-prem and hyperscaler environments.
Controlling Automatic Updates on Windows Server 2016 and later
The following GPO specifies whether this computer will receive security updates and other important downloads through the Windows automatic updating service.
Computer Configuration -> Administrative Templates -> Windows Components -> Windows Update -> Configure Automatic Updates
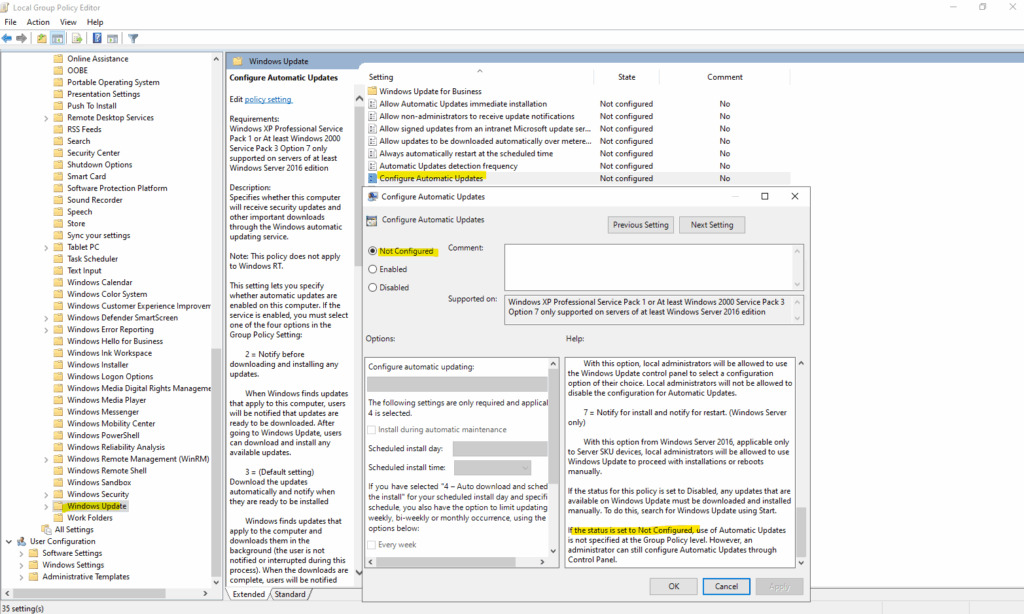
When the “Configure Automatic Updates” policy isn’t configured (by default), Windows Server 2016 and newer revert to their built-in behavior, automatically downloading and installing updates during the default Automatic Maintenance window at 2:00 AM (local time).
This behavior is driven by Windows’ Automatic Maintenance feature (shown next), which handles updates, scans, and optimizations in the background during the default scheduled maintenance windows unless you override its schedule.
On Windows Server, the Configure Automatic Updates policy setting option is configured to 3 in the registry by default.
This value isn’t reflected in the GPO editor. If an admin configures the option to a different setting, the new setting takes effect.
Setting the Configure Automatic Updates policy setting to Not Configured results in the behavior of automatically downloading and installing updates.
Right after setup, without touching any update settings, these are the only registry entries Windows creates by default.
Default registry key value (value not set) and the AUOptions registry value set to 3 ==> Automatically download and notify of installation. Finally they will also installed during the Automatic Maintenance window at 2:00 AM (local time) as mentioned.
If the server misses its nightly maintenance window, Windows may install pending updates and reboot as soon as it’s back online, even during active business hours.
The system restarts a suspended maintenance task during the next idle period; however, the system won’t suspend any task marked as critical. Instead, the system allows a critical task to complete, regardless of user action.
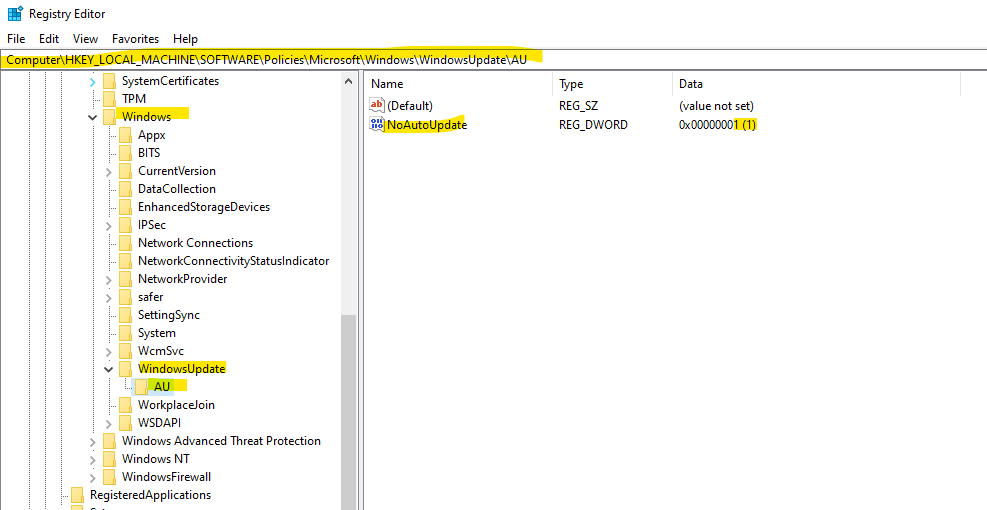
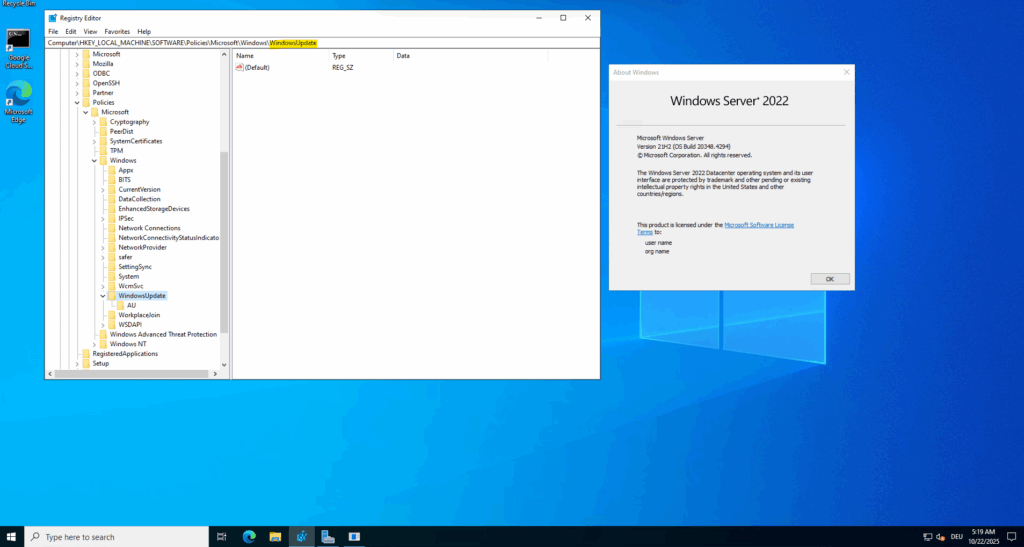
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate
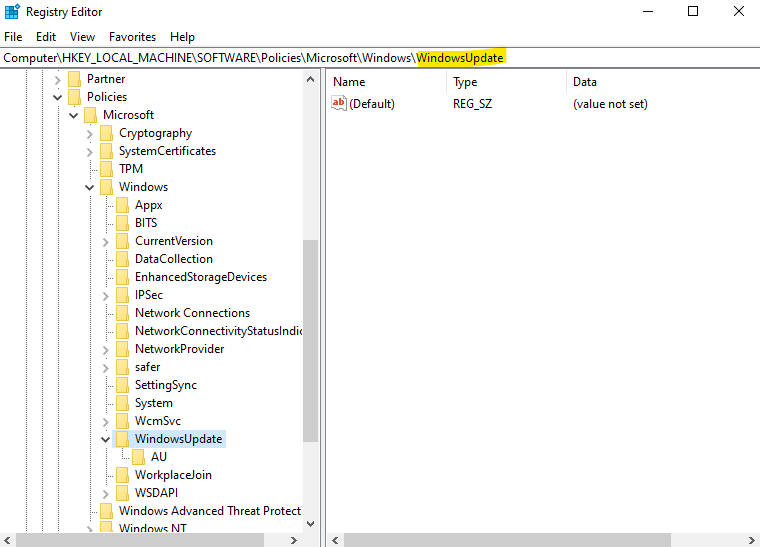
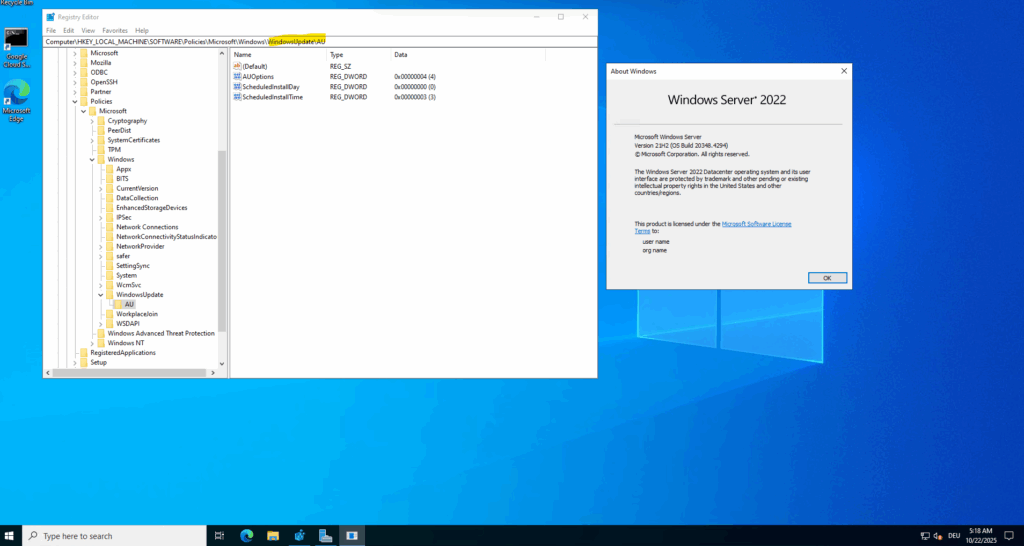
The following AU registry keys are just two of a bunch available options but both are crucial and therefore listed with its different values they can have.
- NoAutoUpdate (REG_DWORD):
- 0: Automatic Updates is enabled (default).
- 1: Automatic Updates is disabled.
- AUOptions (REG_DWORD):
- 1: Keep my computer up to date is disabled in Automatic Updates.
- 2: Notify of download and installation.
- 3: Automatically download and notify of installation.
- 4: Automatically download and scheduled installation.
- 5: Allow local admin to select the configuration mode. This option isn’t available for Windows 10 or later versions.
- 7: Notify for install and notify for restart. (Windows Server 2016 and later only)
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU
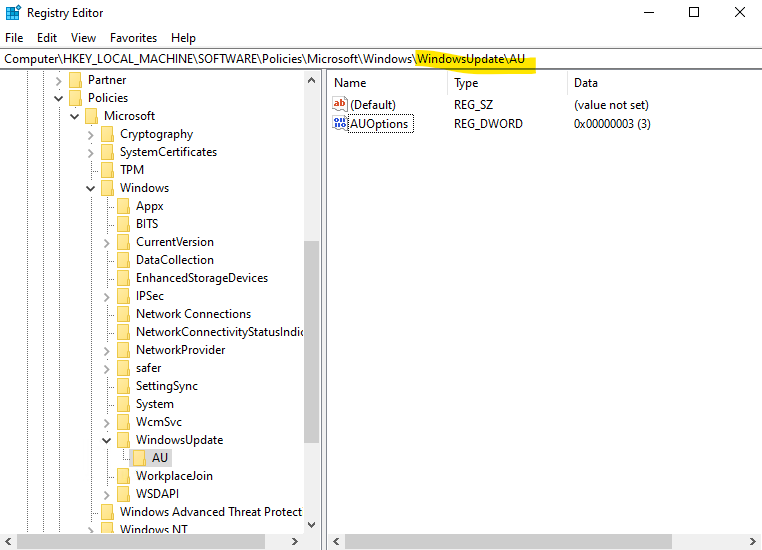
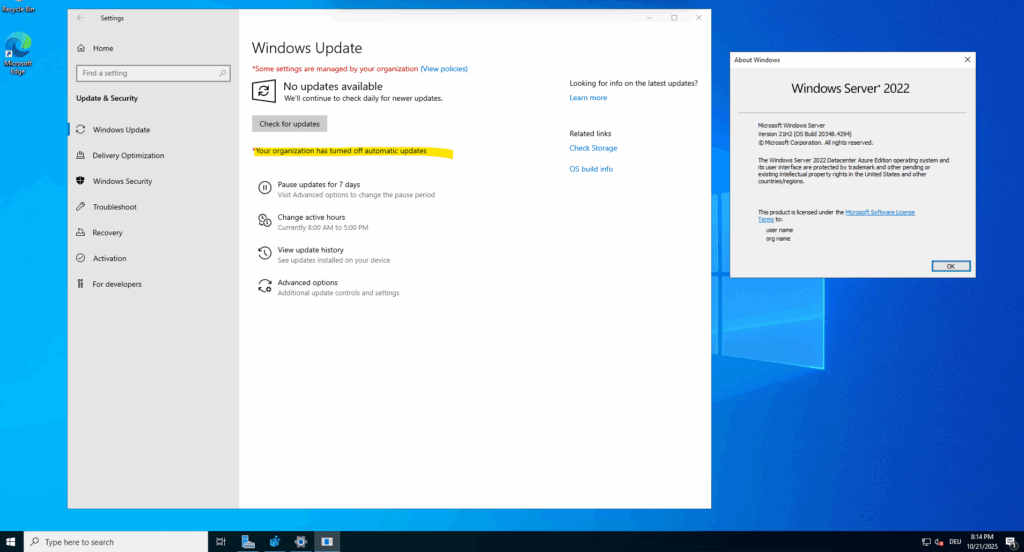
On Windows Server 2022 and later, you’ll notice the following output on the Update & Security page right after a clean installation.
Finally that’s just because of the by default set AUOptions registry value with 3.
Even though this is the default configuration applied during setup, Windows treats it as a policy-driven setting, so the Update page immediately shows the red banner “Some settings are managed by your organization.”
The message typically appears when one or more update-policy registry keys (such as under HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU) are set, whether by Group Policy, imaging, or by default.
Even on systems not joined to a domain, this message can show up because the OS interprets those registry values as organization-managed settings.
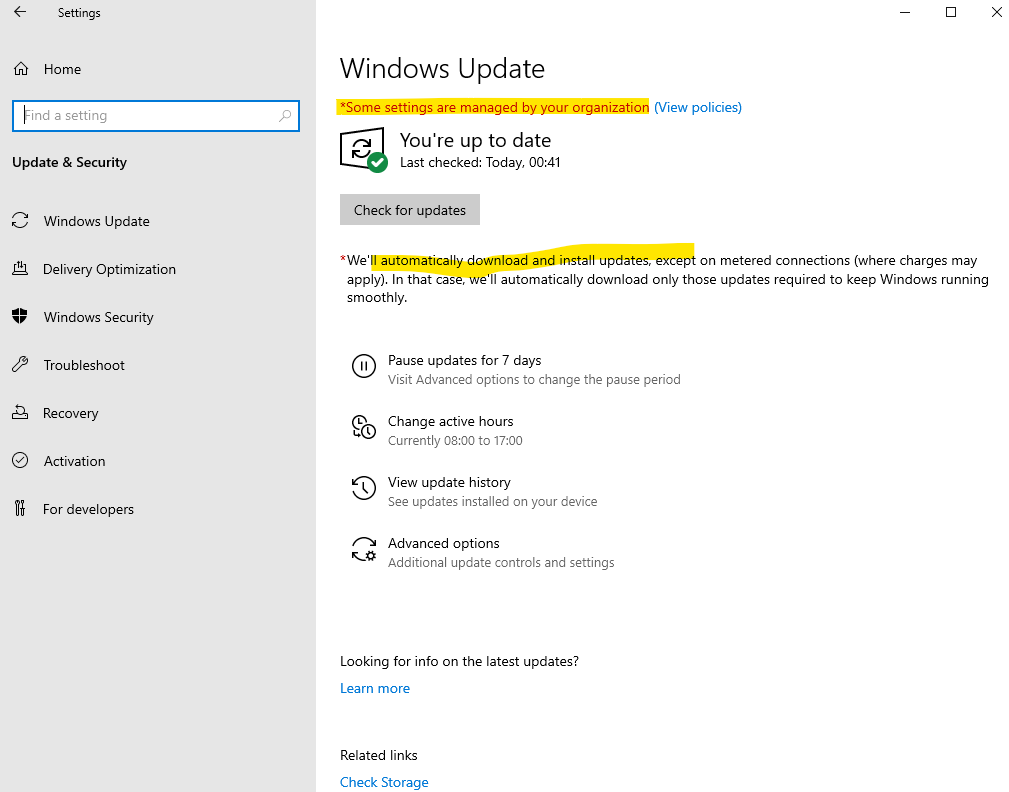
In contrast, on Windows Server 2016 or 2019, a clean installation initially shows the following output in the Update & Security settings. The AU registry key is identical to that on Windows Server 2022, but the red notification only appears after you manually check for updates.
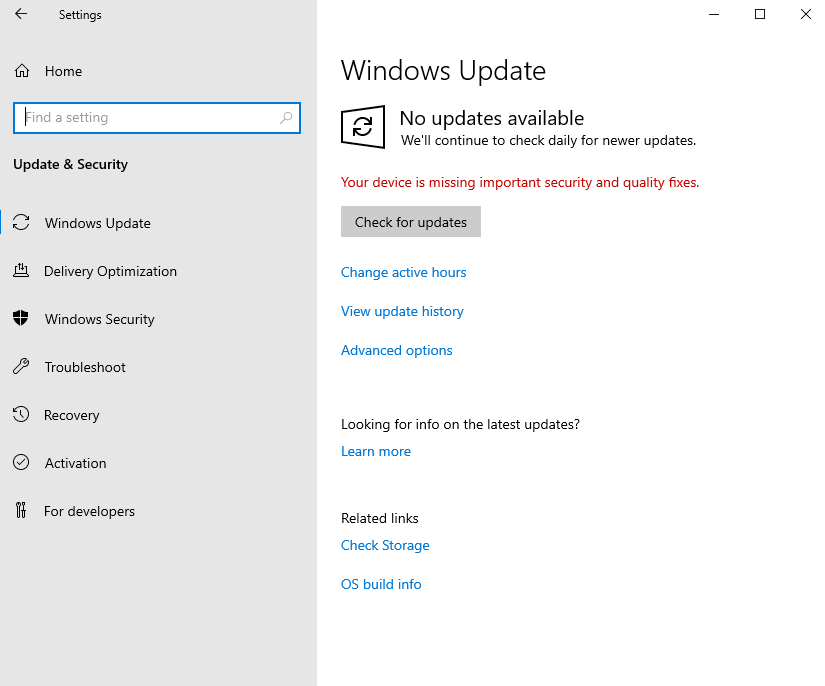
To fully control update behavior, it’s recommended to explicitly configure the GPO.
In case we configure Automatic Updates and set to enabled, a new registry key will be created as shown below.
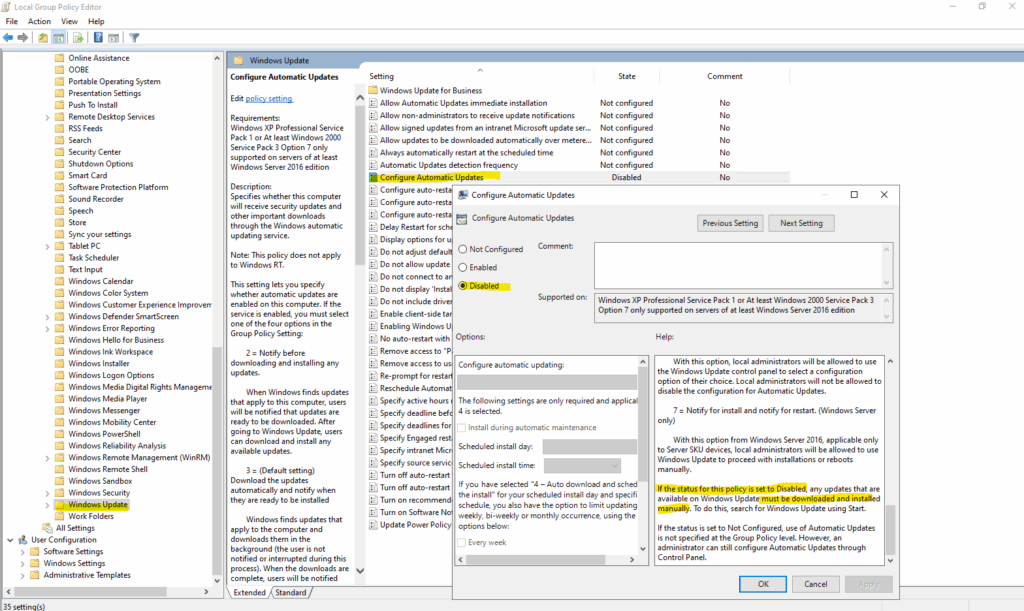
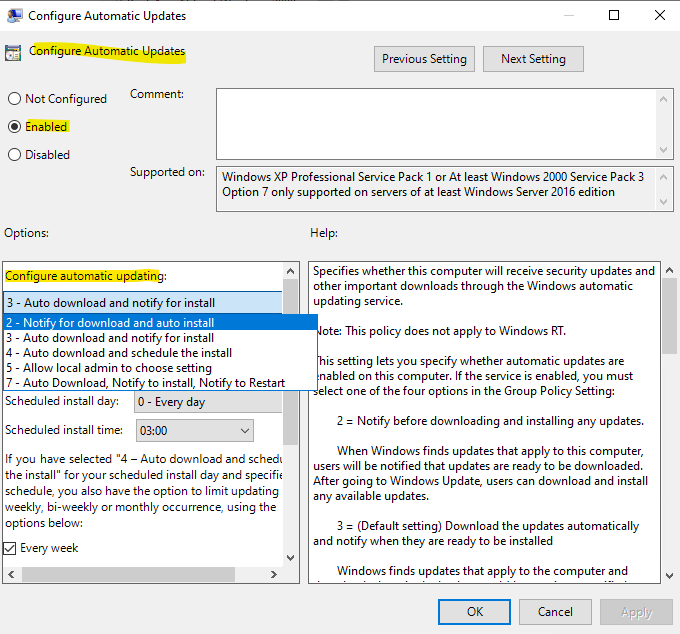
The GPO will finally create the following new registry key.
NoAutoUpdate = 1
When the “Configure Automatic Updates” policy is set to Enabled, Windows first creates the registry value NoAutoUpdate = 1, which simply signals that automatic updates are now managed by policy, not disabled entirely.
To actually define how updates behave, we must still choose one of the options in the policy’s dropdown menu shown above (e.g., Auto download and notify for install or Auto download and schedule the install).
Only after selecting one of these options, and optionally checking “Install during automatic maintenance”, does Windows apply the intended automatic update behavior.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate
Tracking Windows Update Reboots with Event Viewer (Event ID 1074)
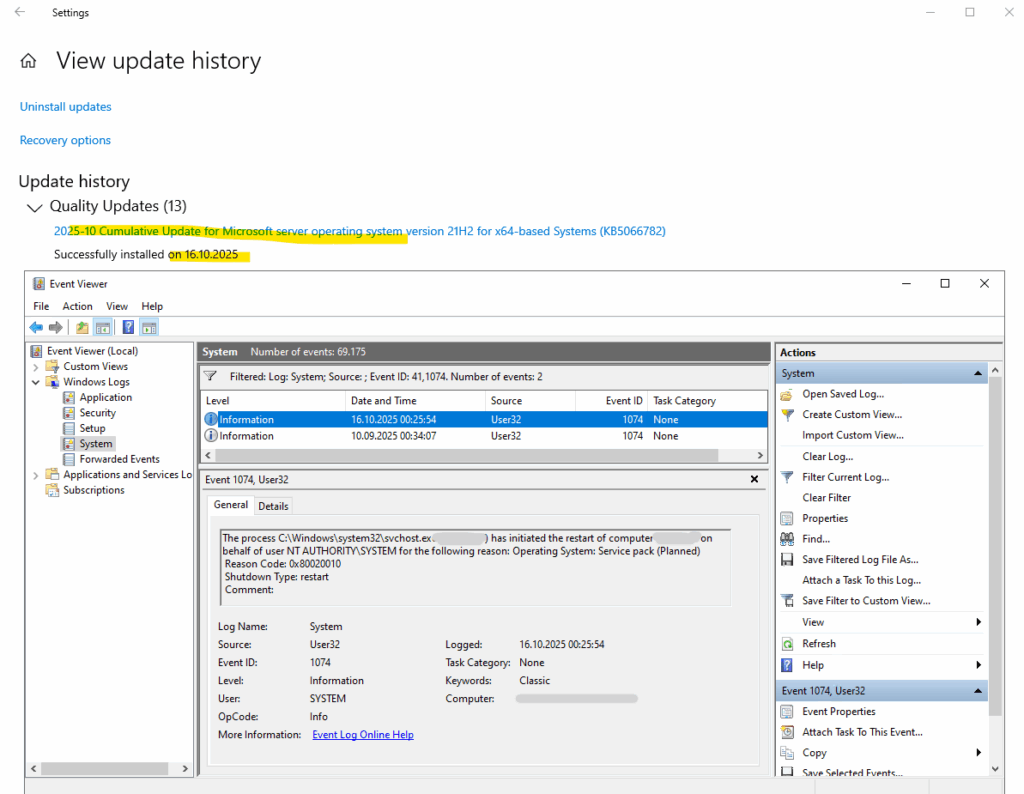
As already shown in Part 1, we can determine when I reboot was triggered by automatic cumulative updates for example by using the event viewer.
The exact date and time when a system reboot occurred during a cumulative update installation, we will see by checking Event ID 1074 in the Windows Event Viewer under System logs.
This event records the user or process (such as WindowsUpdateAgent or TrustedInstaller) that initiated the restart, along with the reason and timestamp of the reboot.
This Event ID 1074 entry indicates that the Windows Update service (svchost.exe), running under the SYSTEM account, automatically initiated a planned restart to complete the installation of the cumulative update KB5066782.
The reason code 0x80020010 and the “Operating System: Service pack (Planned)” message confirm it was a scheduled reboot triggered by Windows Update after successfully applying the update.
Windows Automatic Management (WAM)
Windows Automatic Management (WAM) in Windows is a system feature designed to perform routine maintenance tasks during idle periods, helping keep your system healthy and optimized without interrupting your work.
Automatic Maintenance includes tasks like:
- Windows Updates (download and install)
- Security scans (e.g., Windows Defender)
- Disk optimization (defragmentation or trimming)
- System diagnostics
- Software updates for certain apps
Windows depends on execution of inbox and third party maintenance activity for much of its value-add, including Windows Update, and automatic disk defragmentation, as well as antivirus updates and scans.
Additionally, enterprises frequently use maintenance activity such as Network Access Protection (NAP) scanning to help enforce security standards on all enterprise workstations.
Source: https://learn.microsoft.com/en-us/windows/win32/w8cookbook/automatic-maintenance
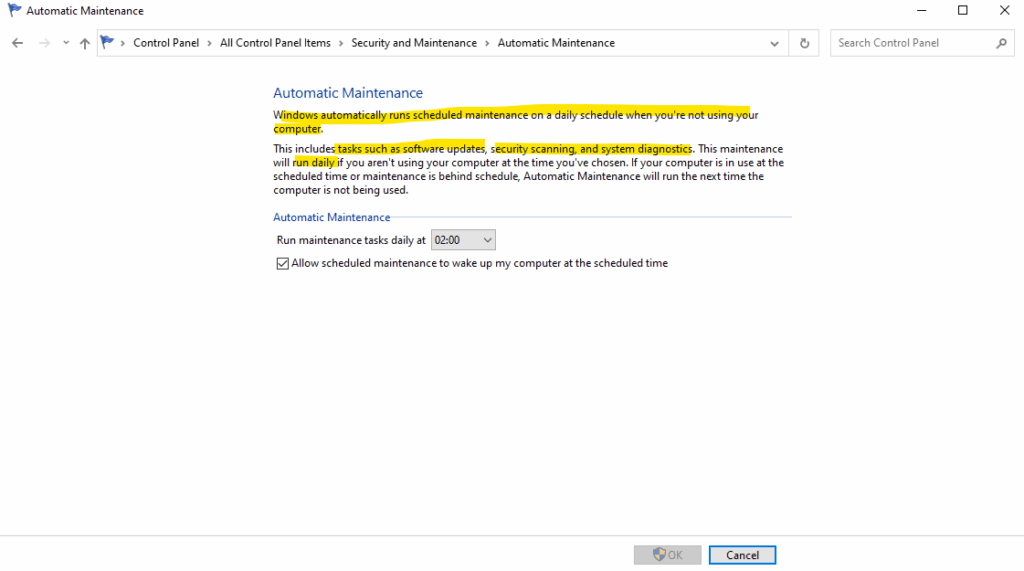
By default, it runs daily at 2:00 AM, but only if the computer is idle and plugged in (for laptops). If the system isn’t idle at the scheduled time, it will retry later.
When AUOptions = 3 is set (“Automatically download updates and notify for install”), Windows doesn’t strictly limit installation or restarts to off-hours, it only prefers to perform them during Automatic Maintenance, typically around 2 AM.
If the server is offline or asleep during that time, Windows reschedules the maintenance task and may install pending updates as soon as possible after startup, even if that falls within your defined active hours.
This means cumulative updates (which often require a reboot) can still trigger an unexpected restart during business hours, unless you explicitly configure update installation and restart behavior through Group Policy, Windows Update for Business, or orchestration tools like Azure Update Manager or GCP VM Manager.
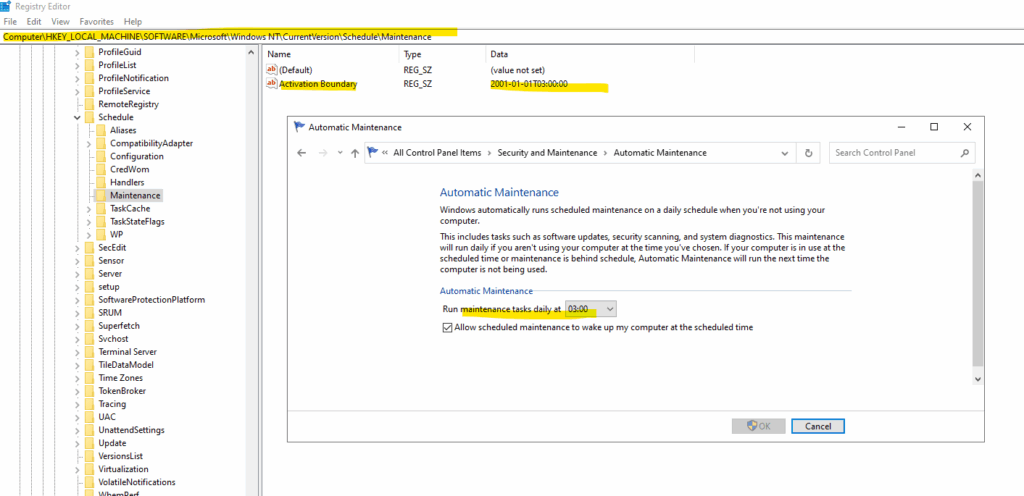
We can change the time via Control Panel > Security and Maintenance > Automatic Maintenance.
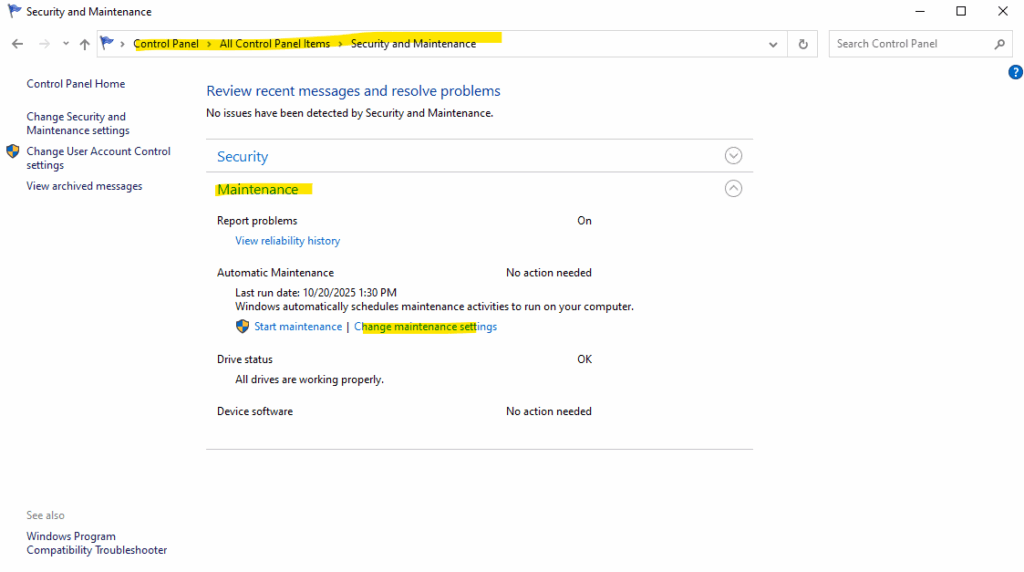
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\Maintenance
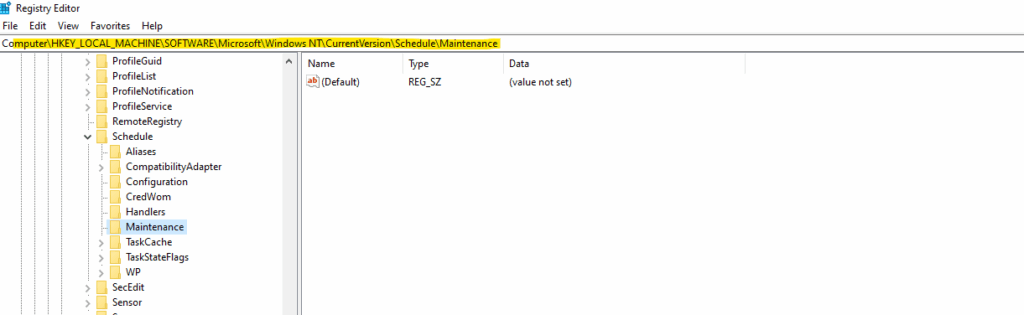
When the keys are missing, Windows falls back to its internal defaults, which are:
| Registry Value | Default (implicit) | Description |
|---|---|---|
| MaintenanceDisabled | 0 | Automatic Maintenance is enabled |
| MaintenanceStartTime | 02:00 (local time) | Runs daily at 2:00 AM |
| ExclusiveMaintenancePeriod | 1 hour | Maximum duration for exclusive maintenance |
| WakeUp | 1 | Can wake the system if allowed in power plan |
Below I was changing the default maintenance start time from 02:00 (local time) to 03:00, afterwards we can see that the custom setting is added to the registry.
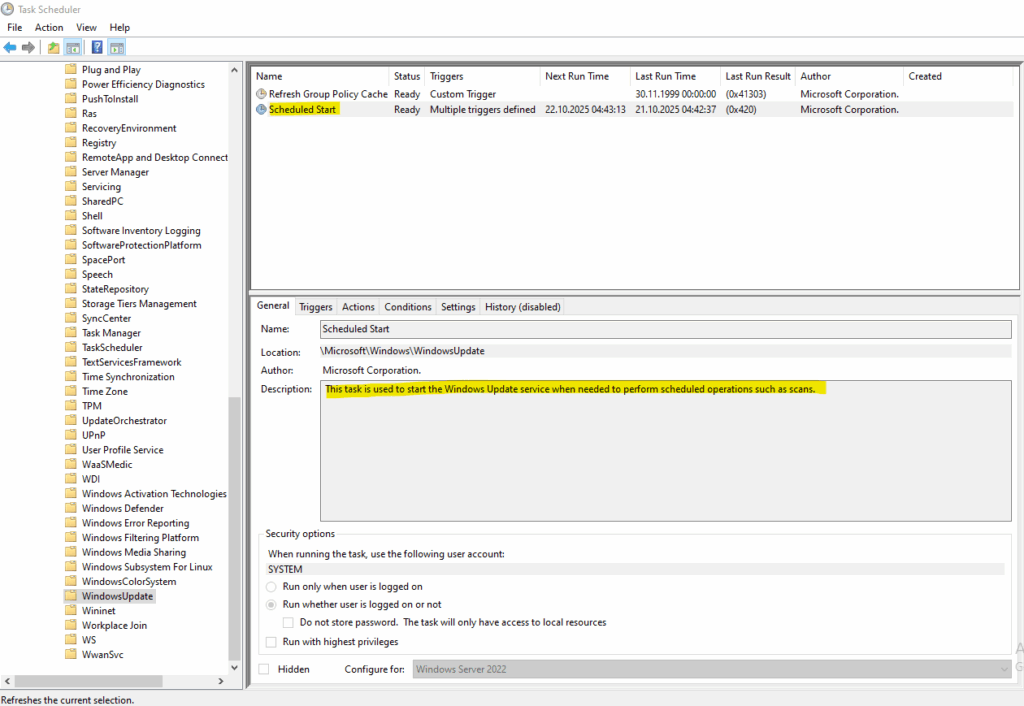
Task Scheduler -> Microsoft -> Windows -> Windows Update
This task is used to start the Windows Update service when needed to perform scheduled operations such as scans.
It is one of the core background triggers used by the Windows Update Agent (WUA) to initiate update scans and maintenance cycles.
The Scheduled Start task is created and managed by the Windows Update service (wuauserv).
Its job is to periodically start an update detection cycle, and (depending on configuration) trigger automatic download or installation during the system’s Automatic Maintenance window.
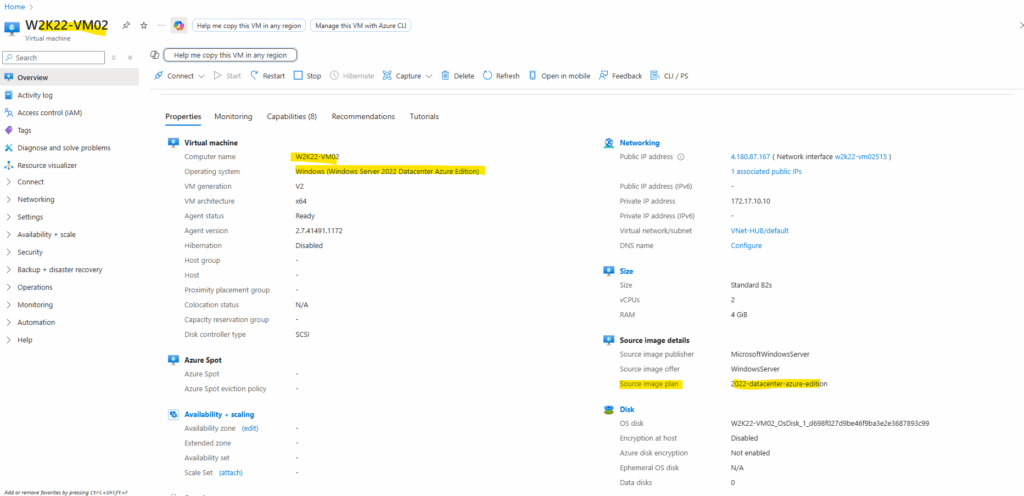
Azure Virtual Machines
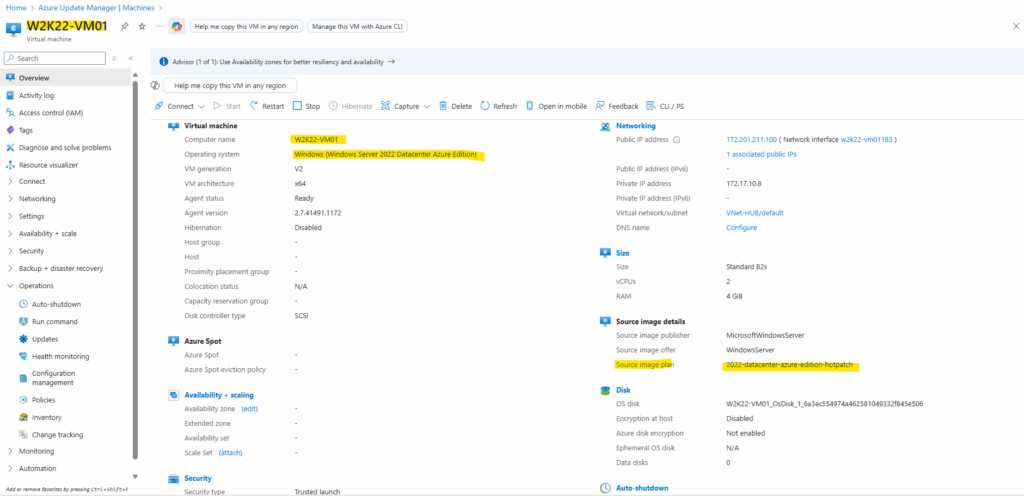
The default patch orchestration mode in Azure Update Manager isn’t the same for every image, it depends on the Windows edition you choose during VM creation.
For example, when selecting the Windows Server 2022 Datacenter: Azure Edition – Hotpatch image, Azure automatically sets the orchestration mode to Azure Managed – Safe Deployment, enabling Azure to control the update rollout and apply hotpatches without reboots.
For a standard Windows Server 2022 Datacenter: Azure Edition, the default mode is Automatic by OS (Windows Automatic Updates), letting Windows manage its own patch schedule.
Windows Server 2022 (Default Datacenter Image)
Below we will see the behavior for the default 2022-datacenter-azure-edition version.
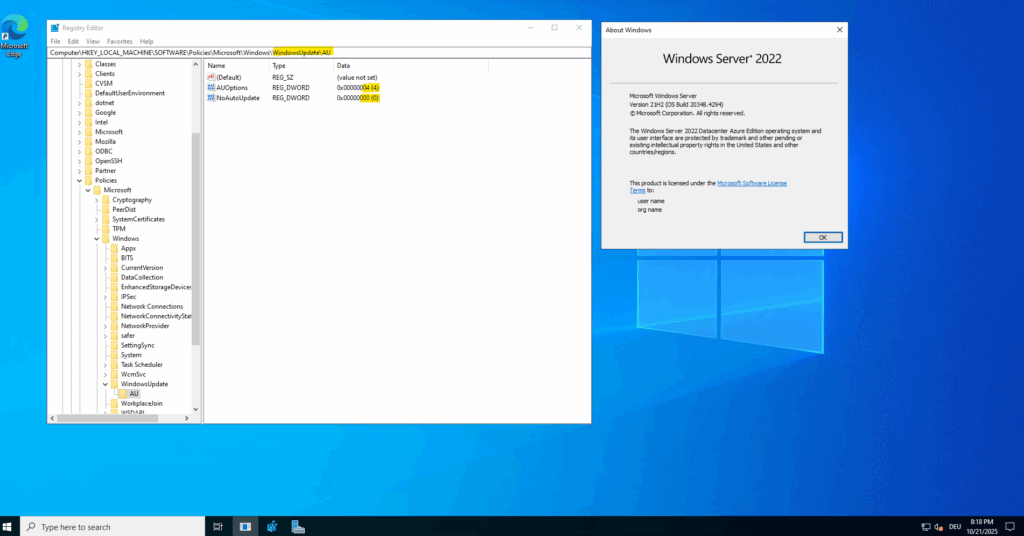
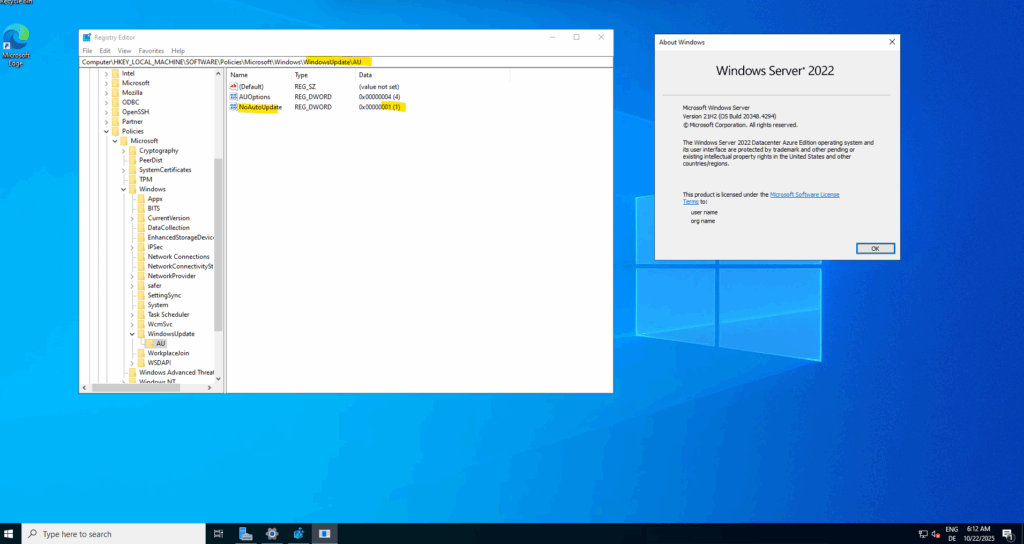
Immediately after spinning up the virtual machine in Azure the AU key named NoAutoUpdate is set to 0 which means automatic updates are enabled.
- NoAutoUpdate (REG_DWORD):
- 0: Automatic Updates is enabled (default).
- 1: Automatic Updates is disabled.
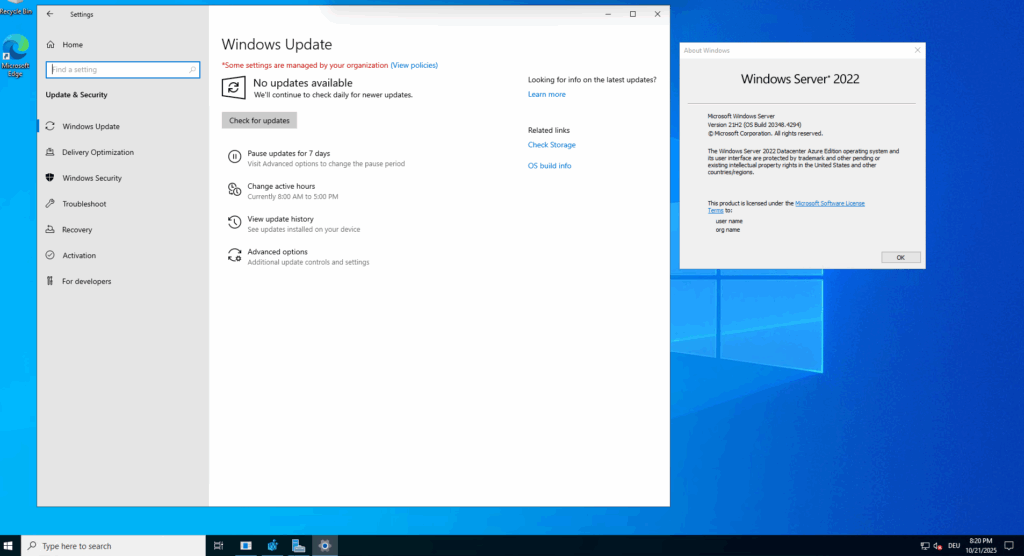
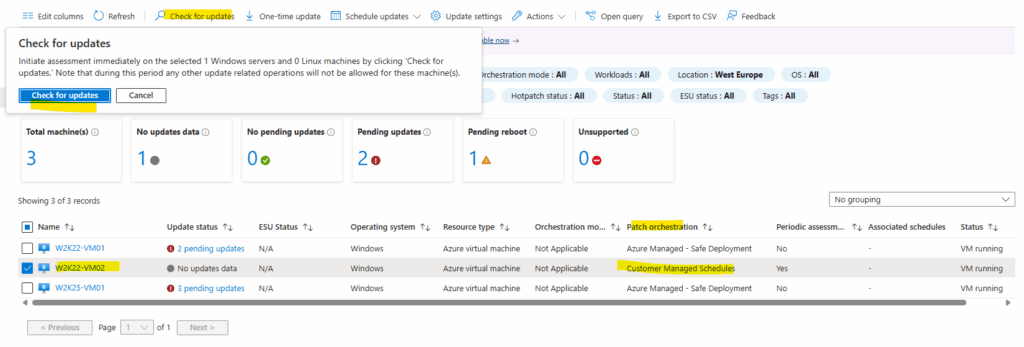
By default new virtual machines are set during creation to Windows automatic update in Azure Update Manager as shown below. The above screenshots are from the virtual machine named W2K22-VM02.
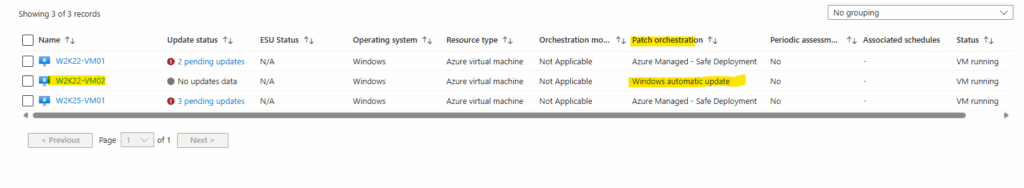
When you create a new virtual machine, you can set the patch orchestration mode already within the Management tab as shown below, by default Automatic by OS (Windows Automatic Updates) is preselected.
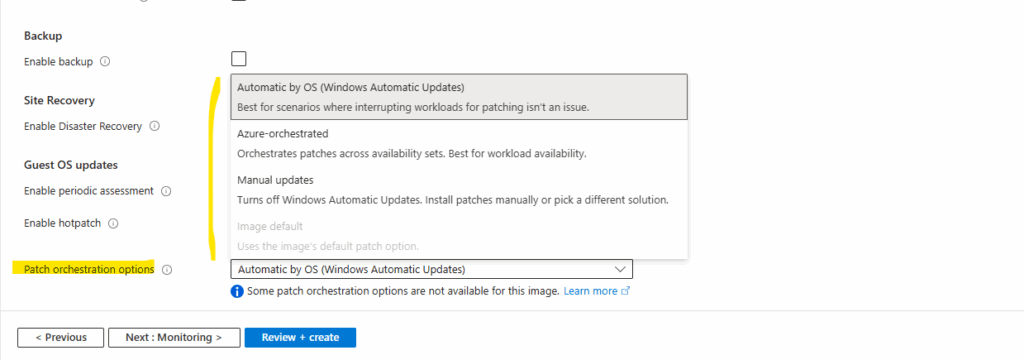
When we now change the patch orchestration mode to Customer Managed Schedules and trigger either an assessment (check for updates) or one-time update, the AU key named NoAutoUpdate will be changed to 1 for Automatic Updates is disabled.
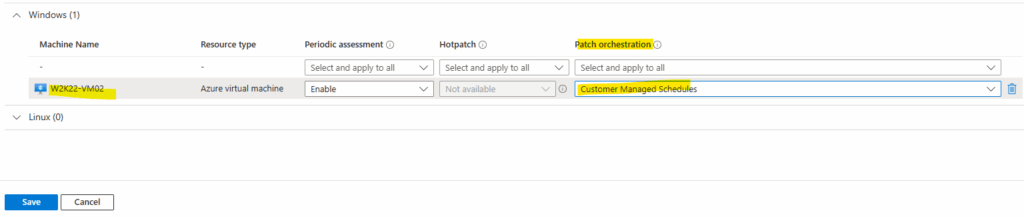
As mentioned, a few minutes later the AU key named NoAutoUpdate is set to 1 which finally disables Windows’ own automatic update logic so Azure Update Manager can fully control the patch cadence from now on and set on the associated schedules.
More about the Azure Update Manager you will find in my following post https://blog.matrixpost.net/mastering-azure-update-manager-part-1/.
Windows Server 2022 (Datacenter Hotpatch Image)
The Hotpatch edition is delivered as a separate Azure image from the standard Windows Server Azure Edition.
They share the same base OS but differ in how updates are applied and how they integrate with Azure’s patch orchestration:
- The Hotpatch image includes the additional hotpatching components and Azure integration needed to install security patches without requiring reboots (except for periodic baseline updates).
- The non-Hotpatch Azure Edition behaves like a regular Windows Server image that uses traditional reboot-based cumulative updates.
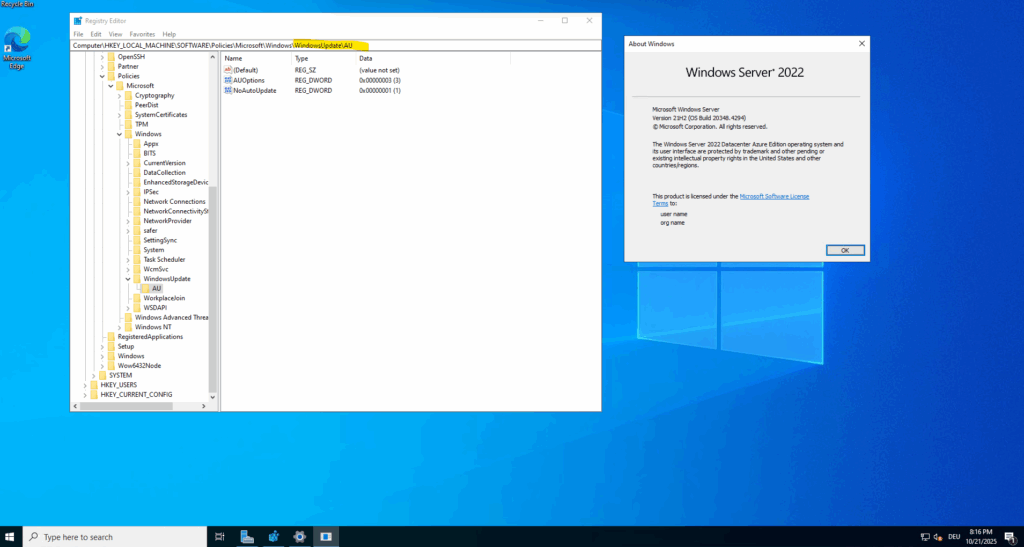
By default NoAutoUpdate is set to 1 which finally disables Windows’ own automatic update logic so Azure Update Manager can fully control the patch cadence.
For the hotpatch version by default the the patch orchestration mode to Azure Managed – Safe Deployment.
This mode enables automatic VM guest patching for the Azure virtual machine. Subsequent patch installation is orchestrated by Azure in a safe, controlled, and reliable manner. E.g. when patching VMs in an availability set, Azure coordinates reboots so that not all VMs in the availability set reboot at the same time.
Azure Update Manager
Below we can see both W2K22 virtual machines and their configured patch orchestration mode in Azure Update Manager.
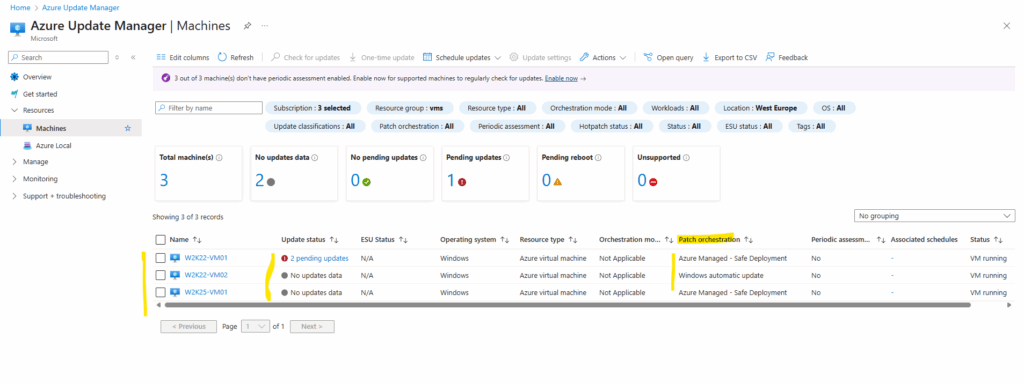
More about the Azure Update Manager you will find in my following post.
Google Cloud (GCP) Virtual Machines
When we create a Patch Job or configure a Patch Deployment in GCP, the mechanism works differently from Azure.
GCP’s OS Config agent (service: GoogleOSConfigAgent) does not modify or depend on Windows’ built-in Windows Update Agent (WUA) policy keys like AUOptions or NoAutoUpdate.
Instead, it calls the Windows Update API directly via its own execution context, temporarily overriding the system’s policy during the patch job.
After completion, it leaves the local Windows Update configuration unchanged, meaning no registry keys are added or modified.
Instead, when you deploy a Windows Server 2022 VM from the Google Cloud image catalog, Google preconfigures several Windows Update policy keys during image build.
These are not set by Group Policy at runtime, but are baked into the image to standardize update behavior across VMs.
Typical defaults you’ll find:
HKLM\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU AUOptions = 4 ScheduledInstallDay = 0 ScheduledInstallTime = 3
That corresponds to “Auto download and schedule the install”, with installation scheduled every day at 3:00 AM.
This ensures updates happen automatically, even for unmanaged standalone instances, aligning with Google’s “secure-by-default” image policy.
Links
Windows unexpectedly installs updates when automatic updates are disabled by Group Policy
https://learn.microsoft.com/en-us/troubleshoot/windows-server/installing-updates-features-roles/unexpected-automatic-update-when-disabled-by-group-policyWindows Update showing “Some settings are managed by your organization” on Azure Windows Server 2019 VM
https://serverfault.com/questions/1041307/windows-update-showing-some-settings-are-managed-by-your-organization-on-azureAutomatic maintenance
https://learn.microsoft.com/en-us/windows/win32/taskschd/task-maintenence
https://learn.microsoft.com/en-us/windows/win32/w8cookbook/automatic-maintenance
Tags In
Related Posts
Latest posts
Mastering Nested Junction Paths: Qtrees and Export Policies in NetApp Cloud Volumes ONTAP (CVO)
Follow me on LinkedIn


