How to elevate access to an Azure Subscription when you have assigned the Global Administrator Role in Microsoft Entra ID
As a Global Administrator in Microsoft Entra ID, you might not have access to all subscriptions and management groups in your tenant.
Below I will show how we can elevate access to all subscriptions and management groups in our tenants where we are Global Administrator.
Microsoft Entra ID and Azure resources are secured independently from one another. That is, Microsoft Entra role assignments do not grant access to Azure resources, and Azure role assignments do not grant access to Microsoft Entra ID.
However, if you are a Global Administrator in Microsoft Entra ID, you can assign yourself access to all Azure subscriptions and management groups in your tenant.
Use this capability if you don’t have access to Azure subscription resources, such as virtual machines or storage accounts, and you want to use your Global Administrator privilege to gain access to those resources.
Sign in to the Azure portal as a Global Administrator.
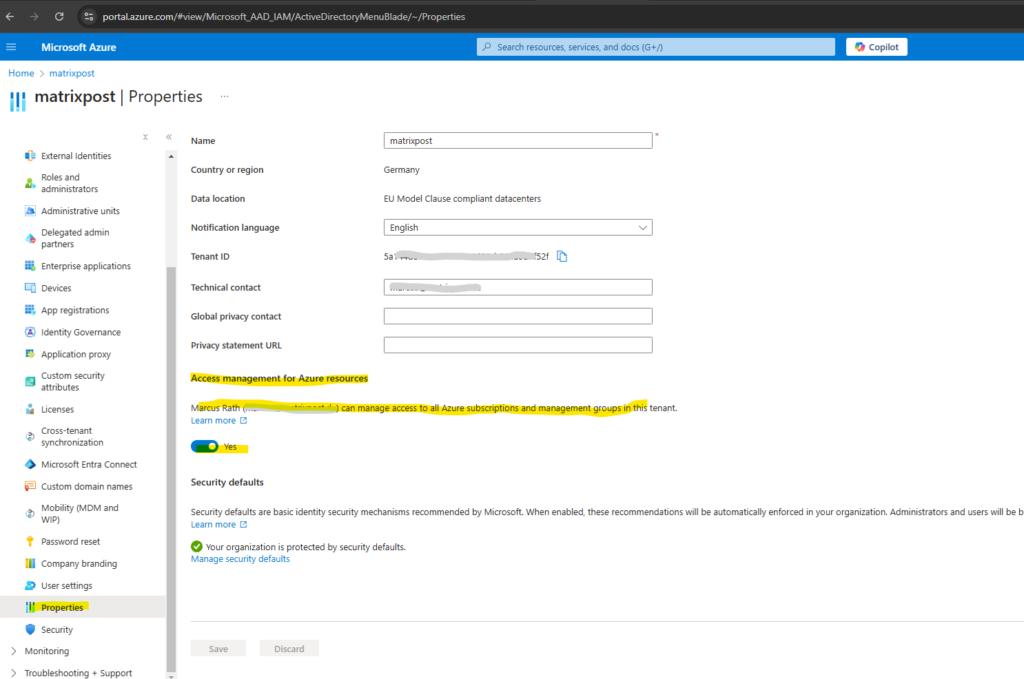
Browse to Microsoft Entra ID > Manage > Properties.
Under Access management for Azure resources, set the toggle to Yes.
When you set the toggle to Yes, you are assigned the User Access Administrator role in Azure RBAC at root scope (/).
This grants you permission to assign roles in all Azure subscriptions and management groups associated with this Microsoft Entra tenant.
This toggle is only available to users who are assigned the Global Administrator role in Microsoft Entra ID.
More about in my following post.
Links
Elevate access to manage all Azure subscriptions and management groups
https://learn.microsoft.com/en-us/azure/role-based-access-control/elevate-access-global-admin?tabs=azure-portal


