How to Migrate to Microsoft Entra’s New Unified MFA and SSPR Policies
Starting September 30, 2025, Microsoft will retire the legacy per-user MFA and SSPR settings in Entra ID. From then on, all authentication methods are managed centrally through the new Unified Authentication Methods policy.
The Authentication methods policy is the recommended way to manage authentication methods, including modern methods like passwordless authentication. Authentication Policy Administrators can edit this policy to enable authentication methods for all users or specific groups.
Methods enabled in the Authentication methods policy can typically be used anywhere in Microsoft Entra ID, for both authentication and password reset scenarios.
In this post, we will see how to migrate our existing configurations by using the built-in migration wizard or by doing the migration manual before the legacy policies are deprecated.
Further at the end of this post we will see several ways we can use to enable MFA for the users.
After moving to the unified authentication methods policies, Multifactor Authentication (MFA) itself is not going away, only the legacy policy pages used to configure it.
All MFA enforcement now happens within the Authentication methods framework, where each method (like the Authenticator app, FIDO2 key, or SMS) can be centrally managed, targeted to groups, and audited.
So while the old “MFA” label disappears from the portal, the feature remains an integral part of Microsoft Entra’s sign-in process, just with a more modern and unified configuration model.
The shift to the new unified policies is mainly about how MFA and SSPR settings are managed and controlled, not about changing how authentication itself works.
Centrally managed means that all authentication methods are now configured in one unified location, where admins can define which methods are available, to whom, and under what conditions, instead of maintaining separate, overlapping MFA and SSPR settings.
This makes policy management more consistent, auditable, and easier to apply across specific groups or user types compared to the legacy approach.
Manage the legacy MFA policy
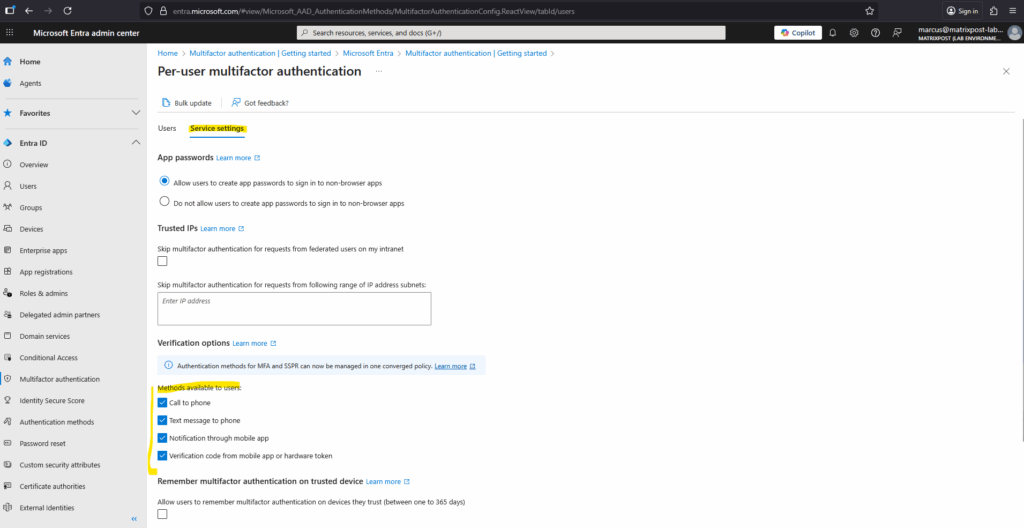
Two other policies, located in Multifactor authentication settings and Password reset settings, provide a legacy way to manage some authentication methods for all users in the tenant. You can’t control who uses an enabled authentication method, or how the method can be used.
To manage the legacy MFA policy, browse to Entra ID > Multifactor authentication > Getting started > Configure > Additional cloud-based multifactor authentication settings.
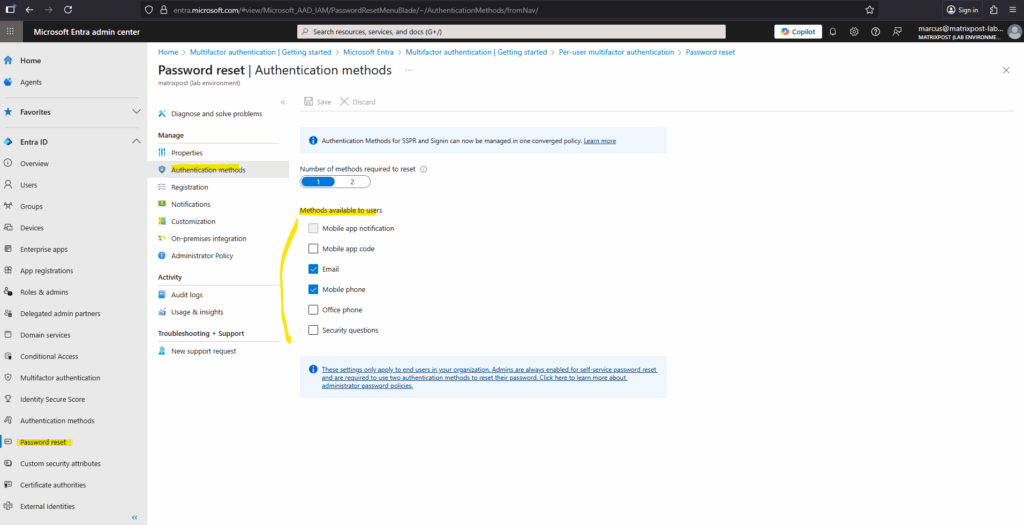
To manage authentication methods for self-service password reset (SSPR), browse to Entra ID > Password reset > Authentication methods. The Mobile phone option in this policy allows either voice calls or text message to be sent to a mobile phone. The Office phone option allows only voice calls.
Migrate to the Authentication Methods Policy for Microsoft Entra ID
You can use the authentication methods migration guide in the Microsoft Entra admin center to automate the migration. The guide provides a wizard to help audit your current policy settings for MFA and SSPR. Then it consolidates those settings in the Authentication methods policy, where they can be managed together more easily.
You can also migrate policy settings manually on your own schedule. The migration process is fully reversible. You can continue to use tenant-wide MFA and SSPR policies while you configure authentication methods more precisely for users and groups in the Authentication methods policy.
Source: https://learn.microsoft.com/en-us/entra/identity/authentication/how-to-authentication-methods-manage
Automated migration guide
The automated migration guide lets you migrate where you manage authentication methods in just a few clicks. It can be accessed from the Microsoft Entra admin center by browsing to Entra ID > Authentication methods > Policies.
Click on Begin automated guide highlighted below.
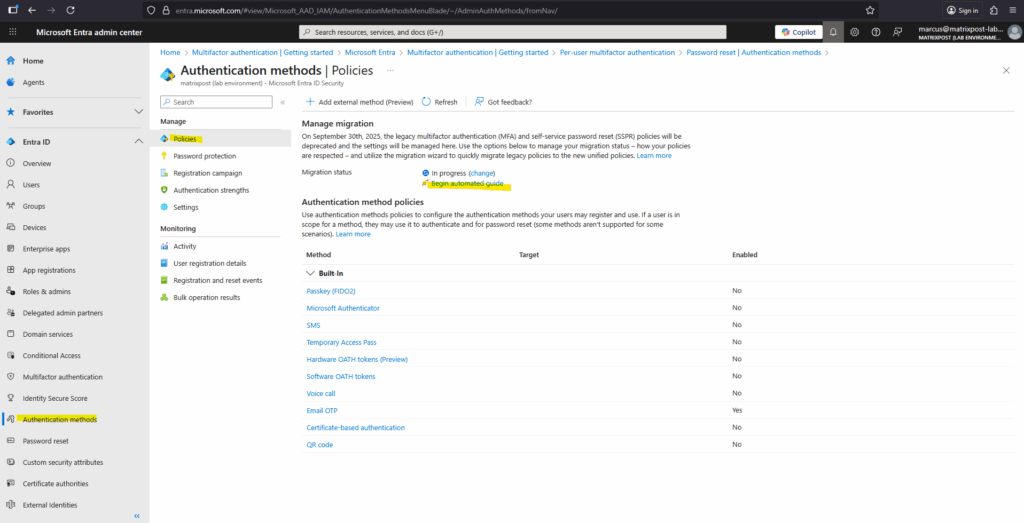
The first page of the wizard explains what it is and how it works. It also provides links to each of the legacy policies for your reference. Click on Next.
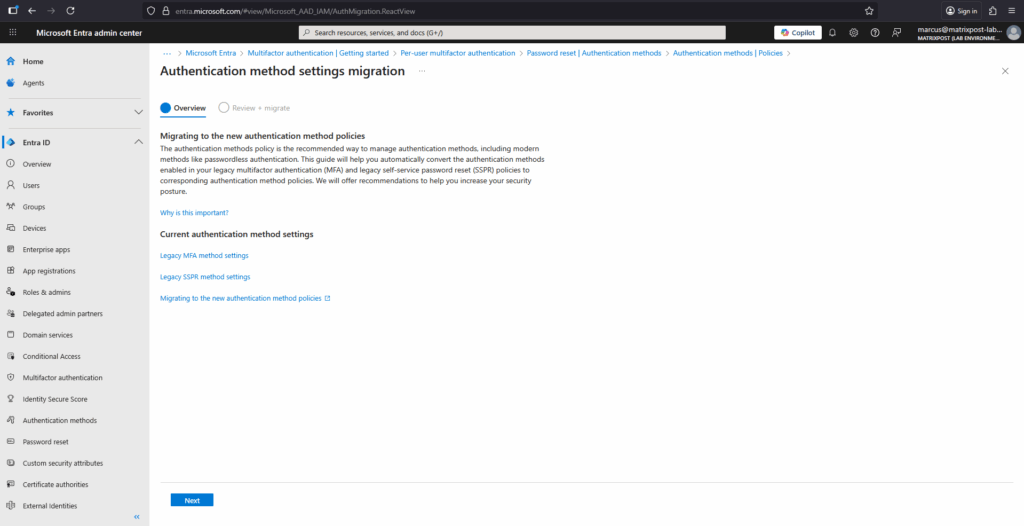
The wizard then configures the Authentication method policy based on what your organization currently has enabled in the legacy MFA and SSPR policies.
If a method is enabled in either legacy policy, the recommendation is to also enable it in the Authentication method policy. With that configuration, users can continue to sign in and reset their password by using the same method they used previously.
In addition, we recommend you enable the latest modern, secure methods like passkeys, Temporary Access Pass, and Microsoft Authenticator to help improve your organizations security posture. To edit the recommended configuration, select the pencil icon next to each method.
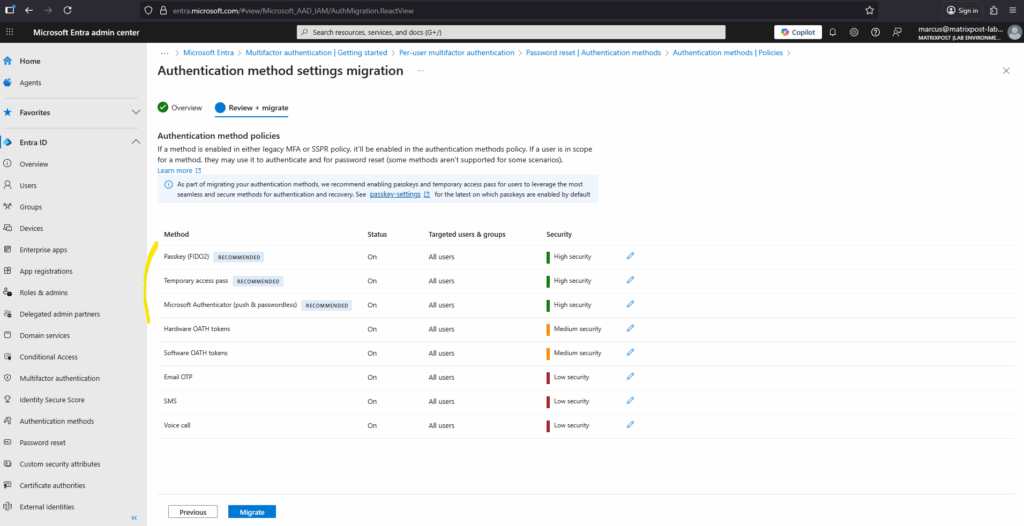
We can edit each method to either turn off the migration or to just migrate some groups and not all users.
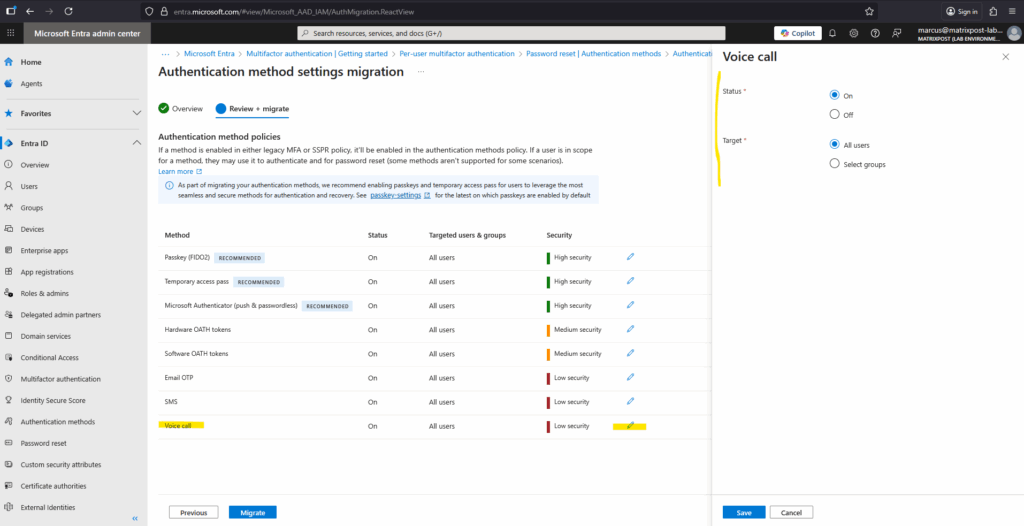
Finally select Migrate, and then confirm the migration. The Authentication methods policy gets updated to match the configuration specified in the wizard.
Authentication methods in the legacy MFA and SSPR policies become grayed out and no longer apply.
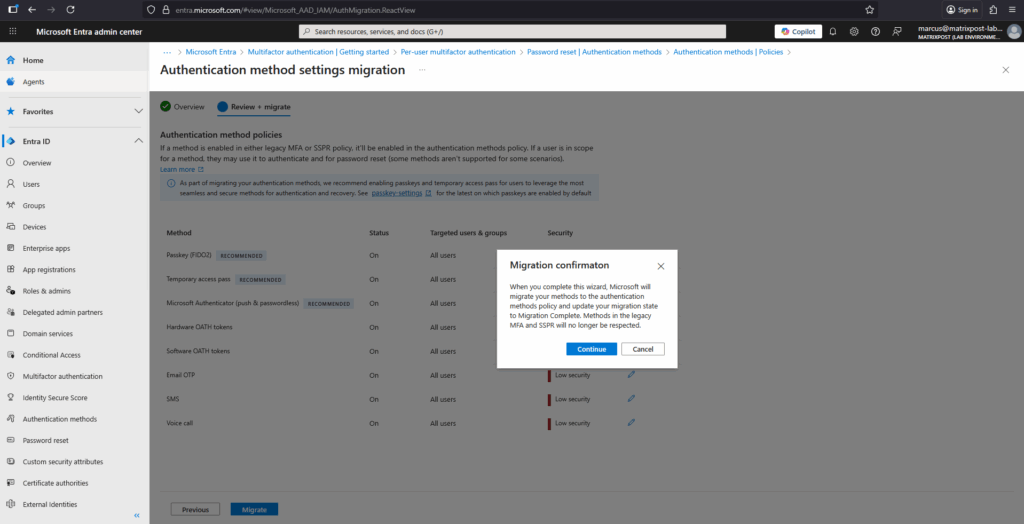
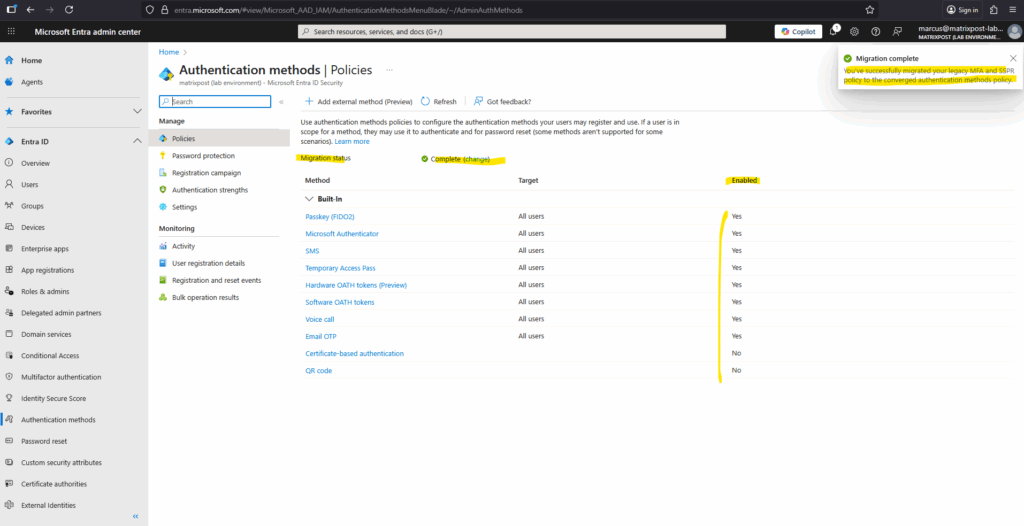
Your migration status is updated to Migration Complete. You can change this status back to In Progress anytime to re-enable methods in the legacy policies if needed.
Click on the change link below in case you want to switch back.
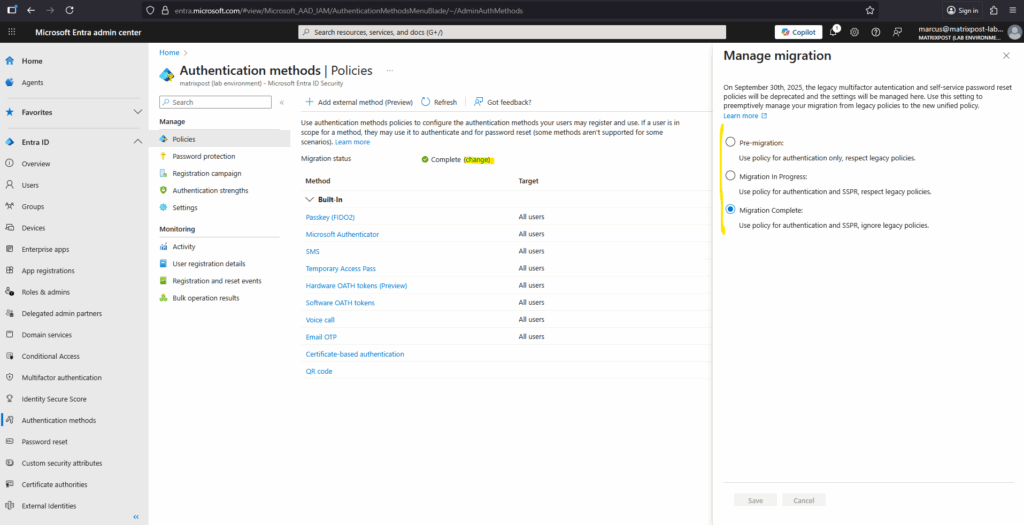
As mentioned the Authentication methods in the legacy MFA and SSPR policies no longer apply.
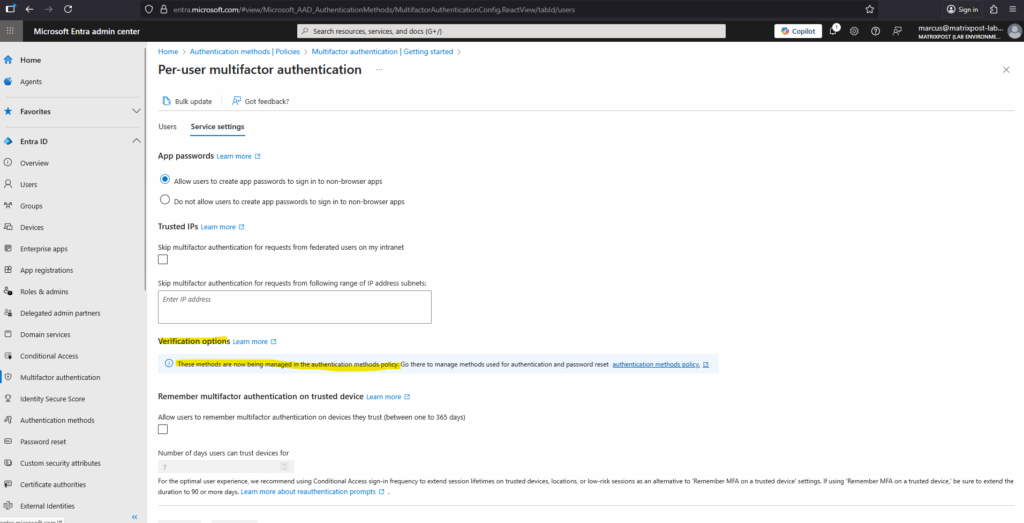
The same for the password reset authentication methods, which now also be managed by the authentication methods policy.
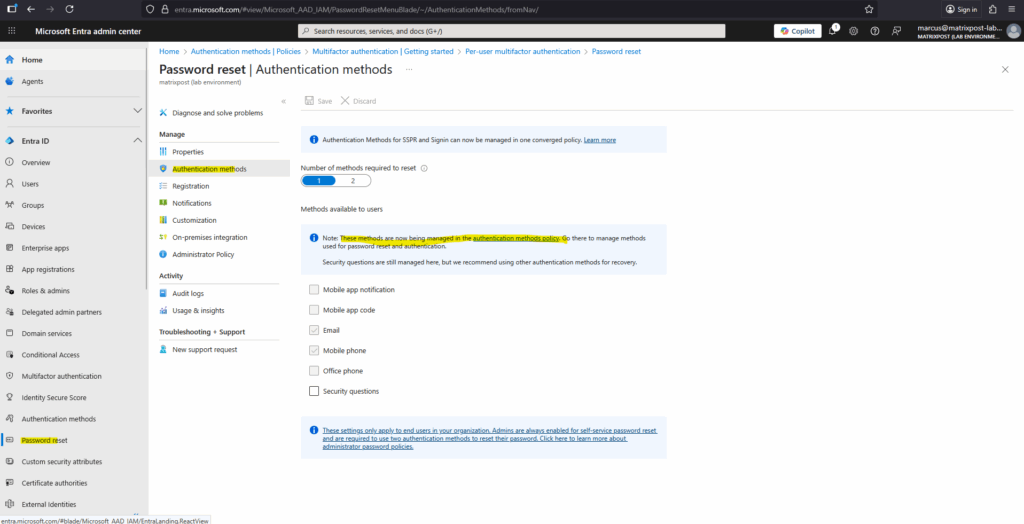
Manual Migration
Begin by doing an audit of your existing policy settings (legacy as shown above) for each authentication method that’s available for users. If you roll back during migration, you might want a record of the authentication method settings from each of these policies:
- MFA policy
- SSPR policy (if used)
- Authentication methods policy (if used)
If you aren’t using SSPR and aren’t yet using the Authentication methods policy, you only need to get settings from the MFA policy.
To check settings in the Authentication methods policy, sign in to the Microsoft Entra admin center as at least an Authentication Policy Administrator and browse to Entra ID > Authentication methods > Policies.
A new tenant has all methods Off by default, which makes migration easier because legacy policy settings don’t need to be merged with existing settings.
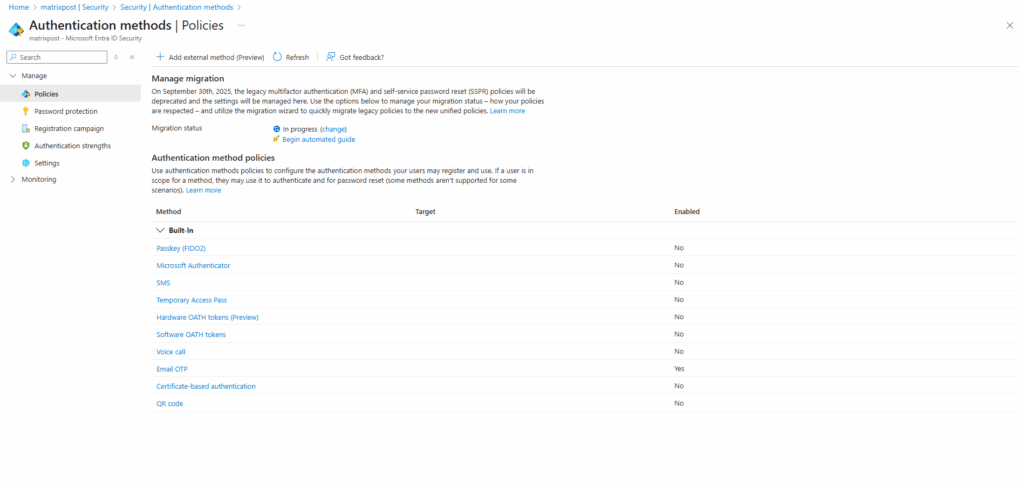
The Authentication methods policy has other methods that aren’t available in the legacy policies, such as FIDO2 security key, Temporary Access Pass, and Microsoft Entra certificate-based authentication. These methods aren’t in scope for migration and you won’t need to make any changes to them if you’ve configured them already.
Click on Manage migration if here is not already shown In progress below.
Select Migration In Progress below.
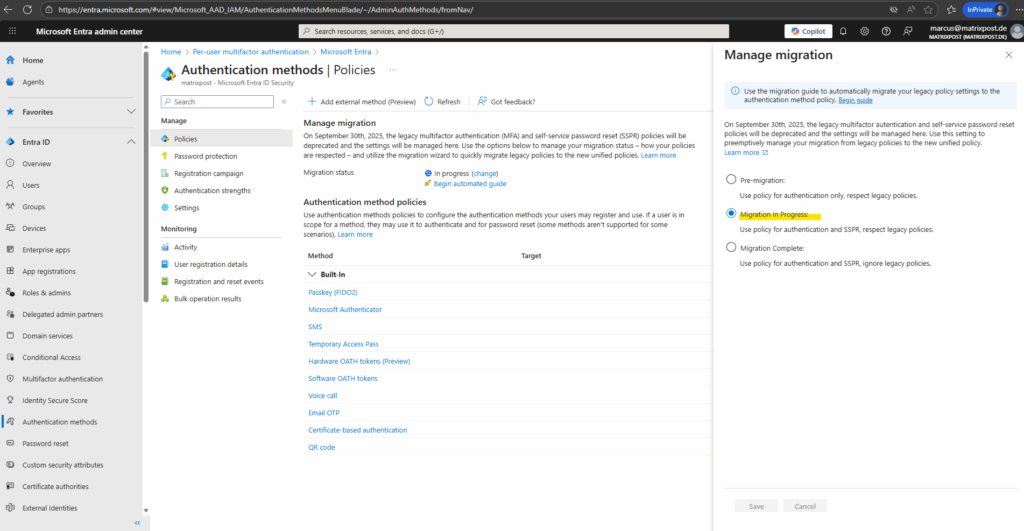
The next step is to update the Authentication methods policy to match your audit. You’ll want to review each method one-by-one. If your tenant is only using the legacy MFA policy, and isn’t using SSPR, the update is straightforward – you can enable each method for all users and precisely match your existing policy.
If your tenant is using both MFA and SSPR, you’ll need to consider each method:
- If the method is enabled in both legacy policies, enable it for all users in the Authentication methods policy.
- If the method is off in both legacy policies, leave it off for all users in the Authentication methods policy.
- If the method is enabled only in one policy, you need to decide whether, or not it should be available in all situations.
Below e.g. configure manual the Microsoft Authenticator (authentication method). Click on it.
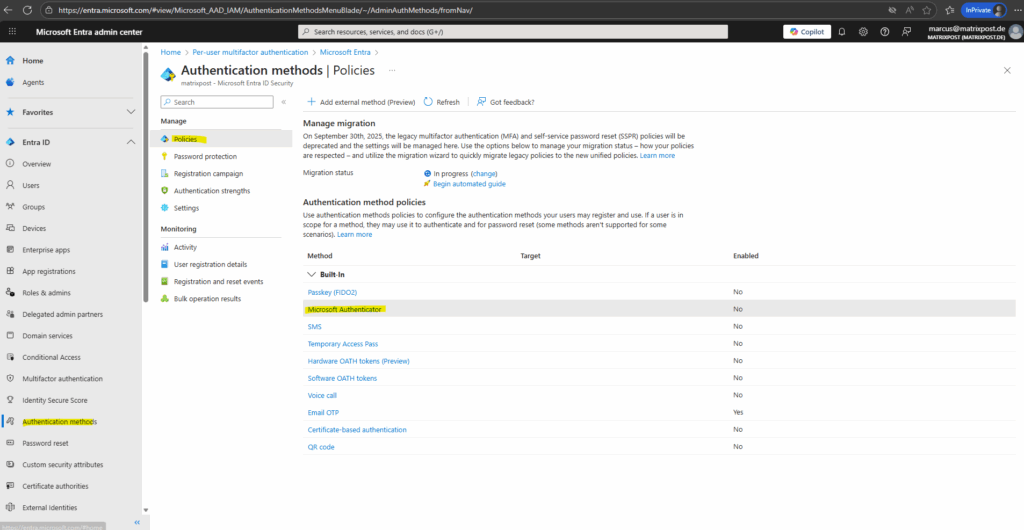
Enable the authentication method for either all users or just selected groups.
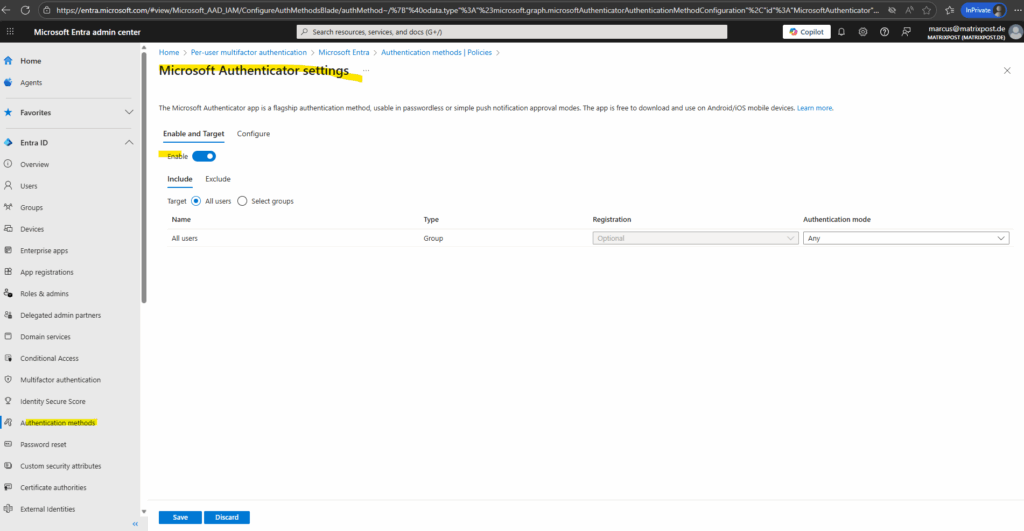
Within the Configure tab we can adjust specific settings for the selected authentication method.
After you update the Authentication methods policy, go through the legacy MFA, and SSPR policies and remove each authentication method one-by-one. Test and validate the changes for each method.
When you determine that MFA and SSPR work as expected and you no longer need the legacy MFA and SSPR policies, you can change the migration process to Migration Complete.
In this mode, Microsoft Entra-only follows the Authentication methods policy. No changes can be made to the legacy policies if Migration Complete is set, except for security questions in the SSPR policy. If you need to go back to the legacy policies for some reason, you can move the migration state back to Migration in Progress at any time.
More about here https://learn.microsoft.com/en-us/entra/identity/authentication/how-to-authentication-methods-manage.
Enable MFA (Configuration Options)
To protect user sign-ins with multifactor authentication, Microsoft Entra offers several ways to enable it, from simple, tenant-wide defaults to fine-grained Conditional Access policies.
Depending on your environment’s complexity, you can choose the approach that best balances security, flexibility, and control.
Security Defaults
Security Defaults provide a built-in baseline of protection in Microsoft Entra ID by automatically requiring MFA for all users and key administrator roles.
They’re ideal for smaller organizations without complex security needs but offer no customization or granular control compared to Conditional Access.
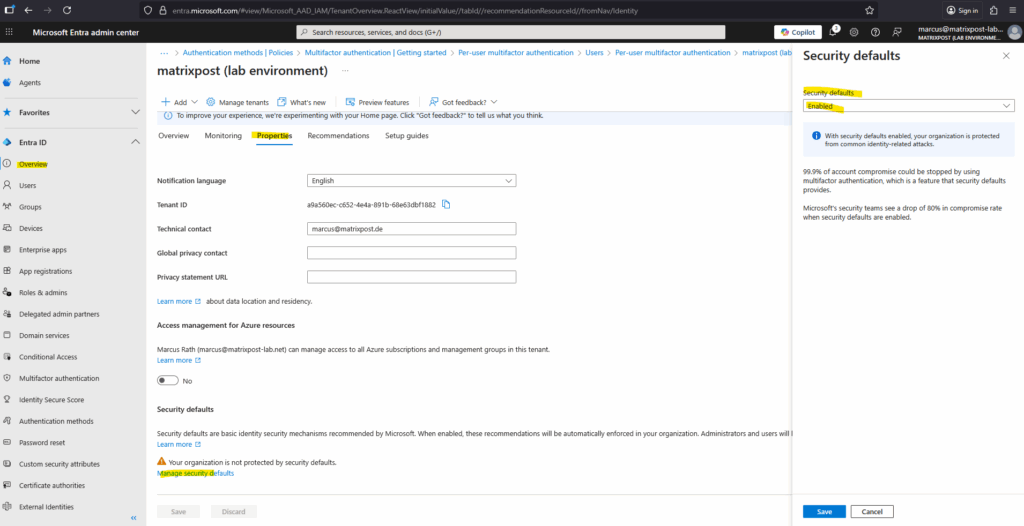
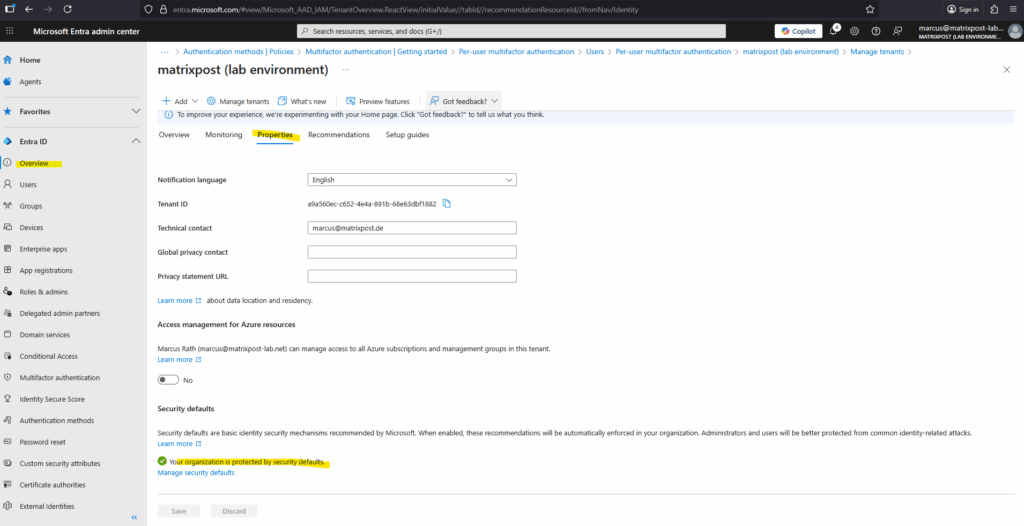
Go to Microsoft Entra Admin Center Entra ID > Properties > Manage Security Defaults.
Click on the Manage security defaults link.
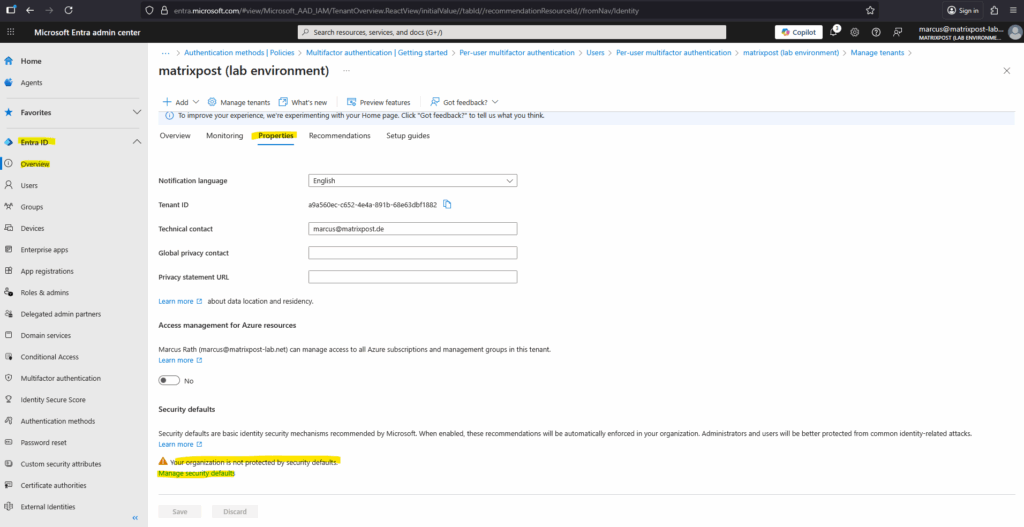
Select Enabled and click on Save.
Per-User MFA (Legacy)
Per-user MFA is the legacy method of enabling multifactor authentication directly on individual user accounts.
It offers only basic on/off enforcement without the flexibility or contextual controls provided by Conditional Access policies.
Go to Microsoft Entra Admin Center Entra ID > Overview > All users -> Per-user MFA.
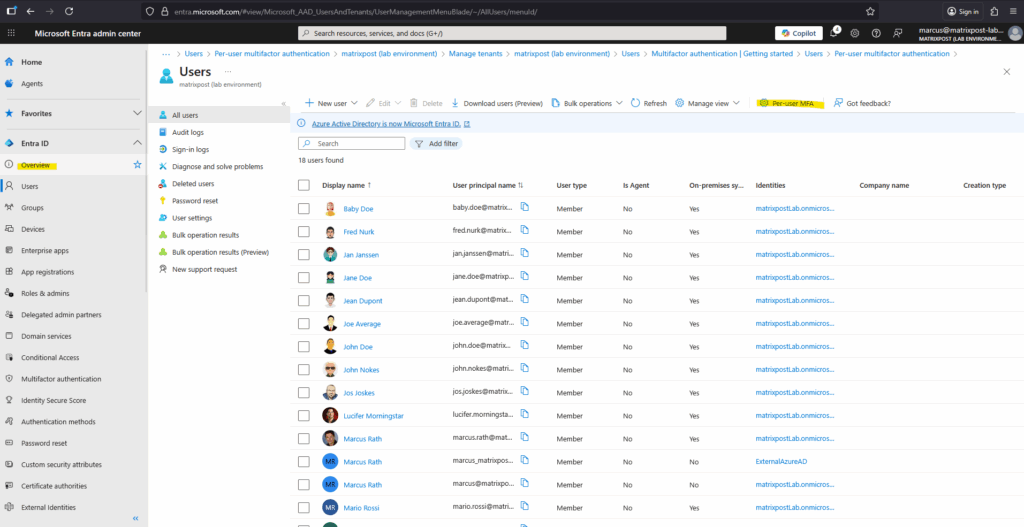
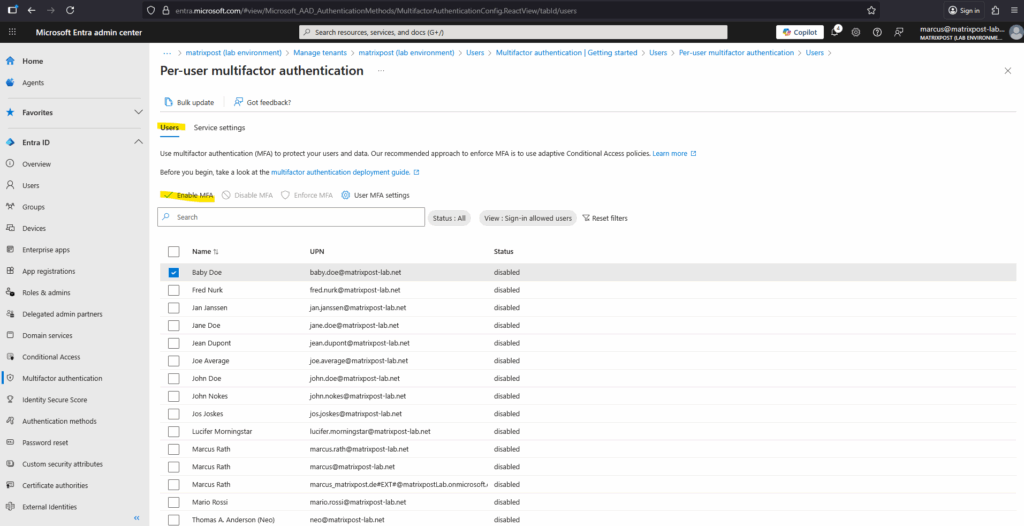
Select the users you want to enable or disable MFA and click on the corresponding option below.
Conditional Access Policies
We can enable and enforce MFA in Microsoft Entra ID also through Conditional Access policies, which provide flexible, context-based control over when users must authenticate with multiple factors.
This approach replaces the legacy per-user MFA enforcement with a more granular and adaptive security model.
Go to Microsoft Entra Admin Center Entra ID > Conditional Access > Overview -> Create new policy.
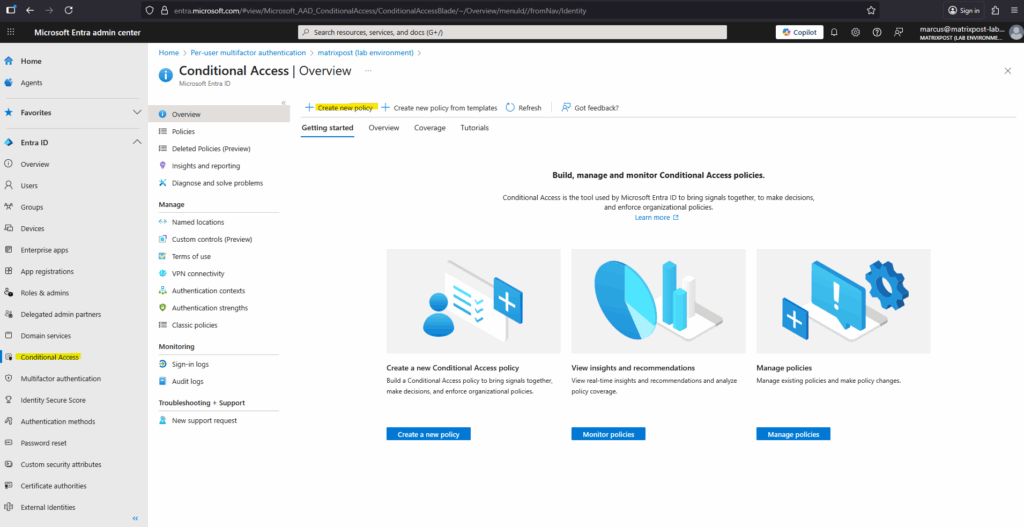
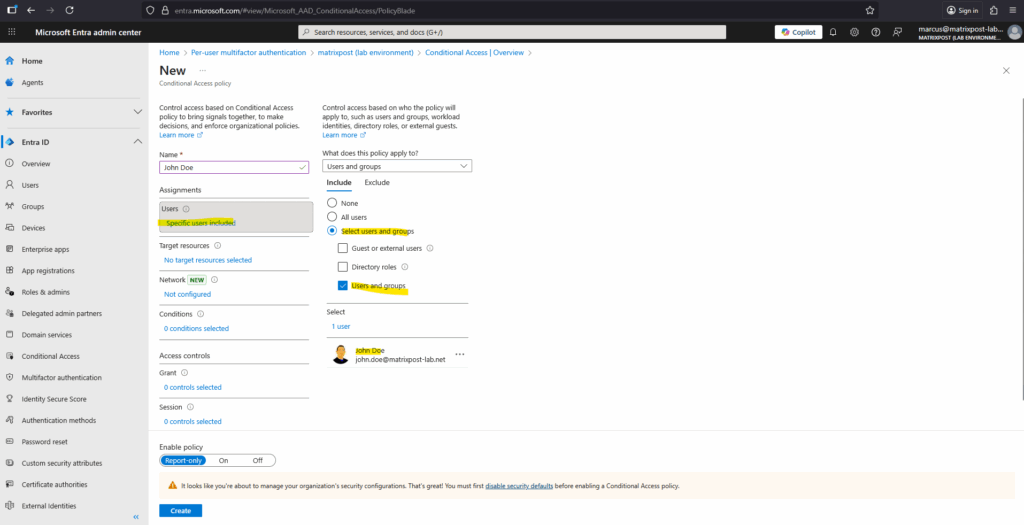
We can define target resources such as specific cloud apps, user actions, or authentication contexts to which the policy applies.
This lets you enforce MFA or other access controls only when users access certain applications or perform sensitive operations.
I will enable MFA below for all resources.
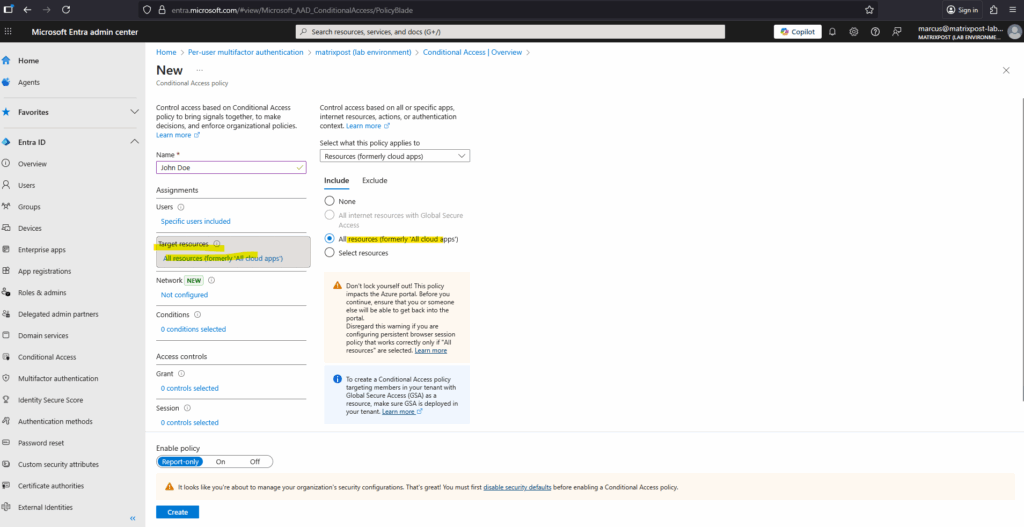
We can also specify the network conditions under which the policy applies. This allows you to control access based on trusted or untrusted locations, named networks, or IP ranges, for example, requiring MFA only when users sign in from outside your corporate network.
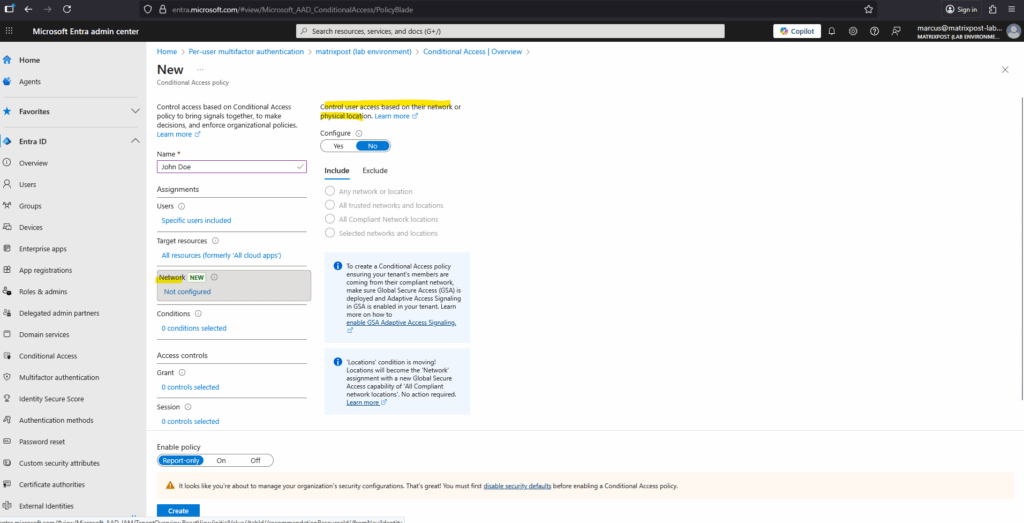
The Conditions section lets you define the circumstances that trigger the Conditional Access policy.
You can tailor access requirements based on factors like user risk level, device state, platform, client app type, or location, ensuring MFA or other controls are enforced only when specific conditions are met.
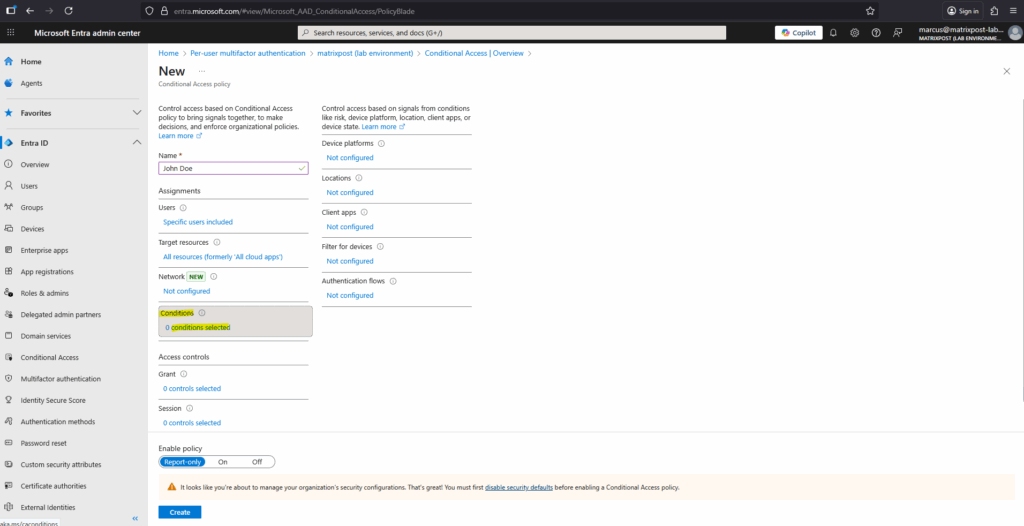
The Grant section defines what access controls are applied when the policy conditions are met.
Here you can choose to block access entirely or grant access only if additional requirements, such as requiring multifactor authentication, compliant devices, or approved client apps, are satisfied.
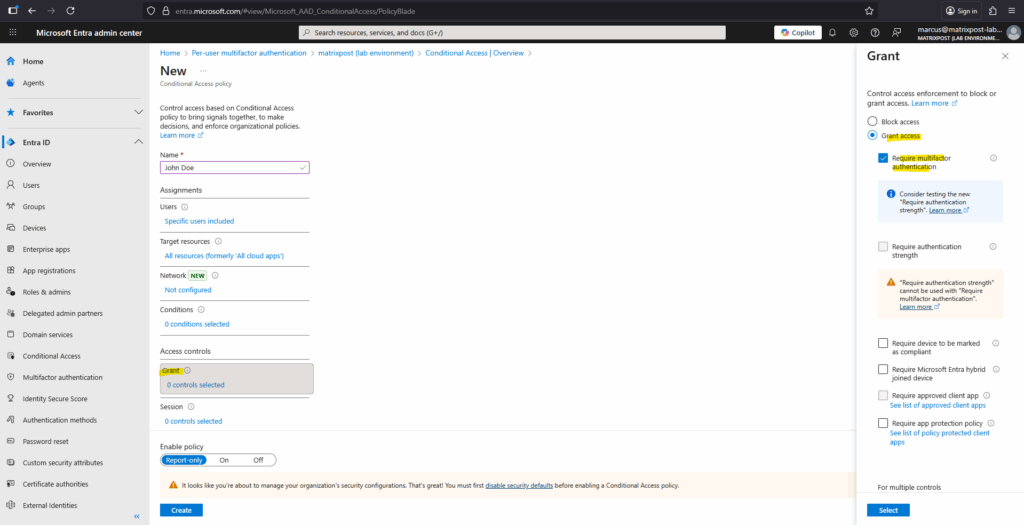
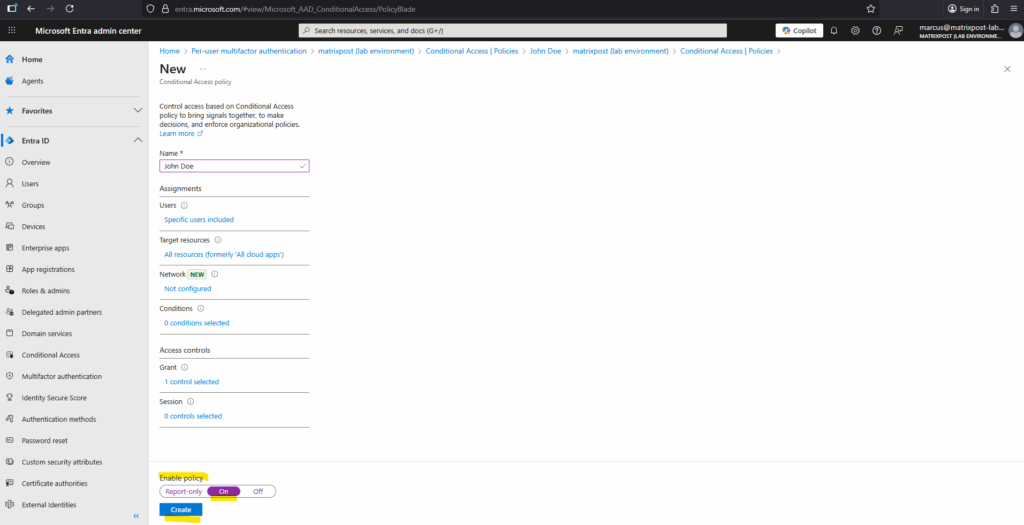
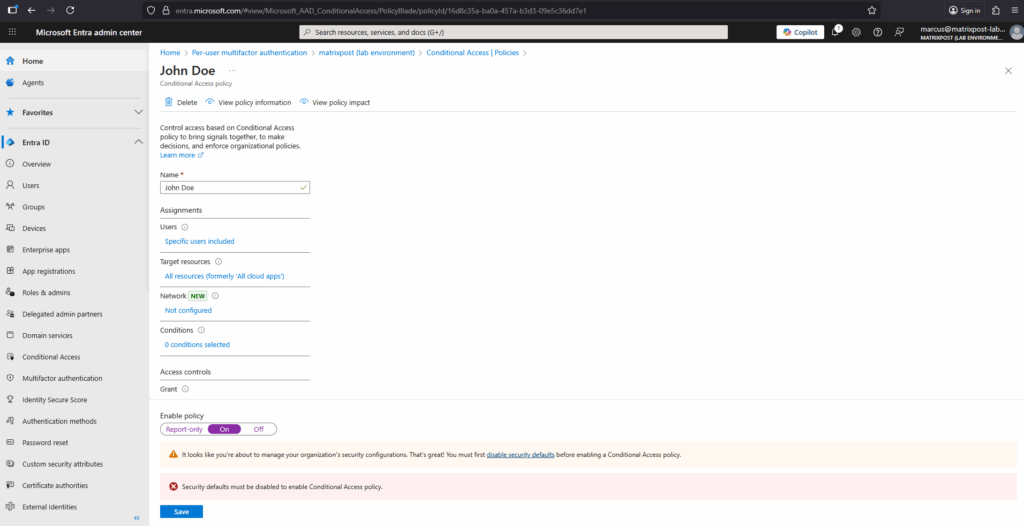
Finally enable the policy and click on Create.
Troubleshooting
Security defaults must be disabled to enable Conditional Access policy
Security Defaults and Conditional Access can’t be active at the same time, you must disable Security Defaults before enabling Conditional Access.
Security Defaults apply Microsoft’s global baseline MFA enforcement to all users, while Conditional Access provides granular control over when and for whom MFA is required.
Disabling Security Defaults lets you replace the blanket enforcement with tailored Conditional Access policies that match your organization’s security model.
Links
How to migrate MFA and SSPR policy settings to the Authentication methods policy for Microsoft Entra ID
https://learn.microsoft.com/en-us/entra/identity/authentication/how-to-authentication-methods-manageManage authentication methods for Microsoft Entra ID
https://learn.microsoft.com/en-us/entra/identity/authentication/concept-authentication-methods-manage
Tags In
Latest posts
Mastering Nested Junction Paths: Qtrees and Export Policies in NetApp Cloud Volumes ONTAP (CVO)
Follow me on LinkedIn


