How to request a Certificate from an internal PKI (AD CS) by using the Certreq Command without relying on the Web Enrollment service
The Certification Authority (CA) Web Enrollment role service provides a set of web pages that allow users to perform certificate tasks.
For example, requesting and renewing certificates, retrieving certificate revocations lists (CRLs) and enrolling for smart card certificates.
These web pages are located at https://<servername>/certsrv, where <servername> is the name of the server that hosts the CA Web Enrollment pages.
In case the Web Enrollment role service is not installed or for whatever reason not available, we can also request new certificates by using the certreq command as shown in this post.
The certreq command can be used to request certificates from a certification authority (CA), to retrieve a response to a previous request from a CA, to create a new request from an .inf file, to accept and install a response to a request, to construct a cross-certification or qualified subordination request from an existing CA certificate or request, and to sign a cross-certification or qualified subordination request.
Source: https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/certreq_1
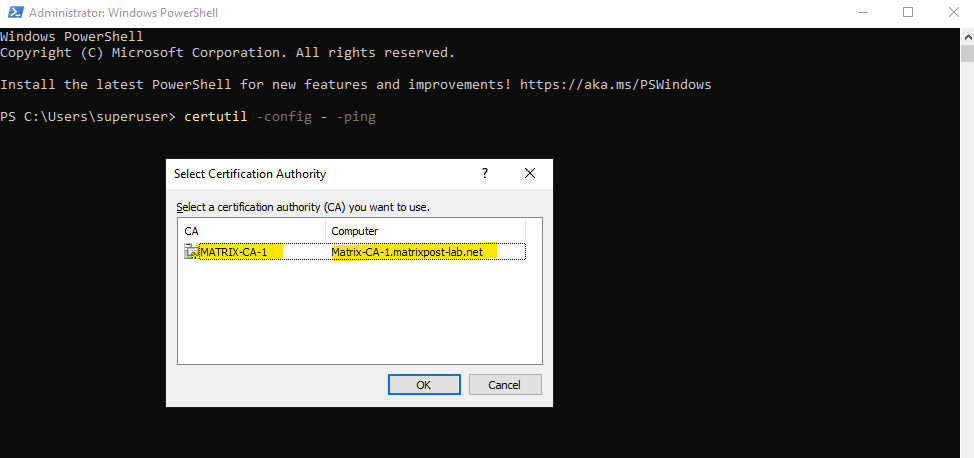
In order to use the certreq command and to request new certificates, we first need to determine the CA name and computer name on which our internal PKI resp. the Active Directory Certificate Services (AD CS) which are issuing certificates are installed on.
Therefore we can just enter the following command on a domain joined computer in Windows PowerShell or CMD .
This queries Active Directory for available CAs.
PS> certutil -config - -ping
- Create a Certificate Signing Request (CSR or Certification Request) directly on the System we want to create a Certificate for
- Create a Certificate Signing Request (CSR or Certification Request) on Windows by using the certreq command
- Submit the CSR to the internal CA (AD CS) on Windows by using the certreq command
- Create a Private Key and Certificate Signing Request (CSR or Certification Request) on Linux by using OpenSSL
- Troubleshooting
- Links
Create a Certificate Signing Request (CSR or Certification Request) directly on the System we want to create a Certificate for
To create a certificate signing request (CSR or certification request) we can either use the system (here e.g. the IIS Web Server) for which we want to request a new certificate if supported or by using the certreq command shown further down.
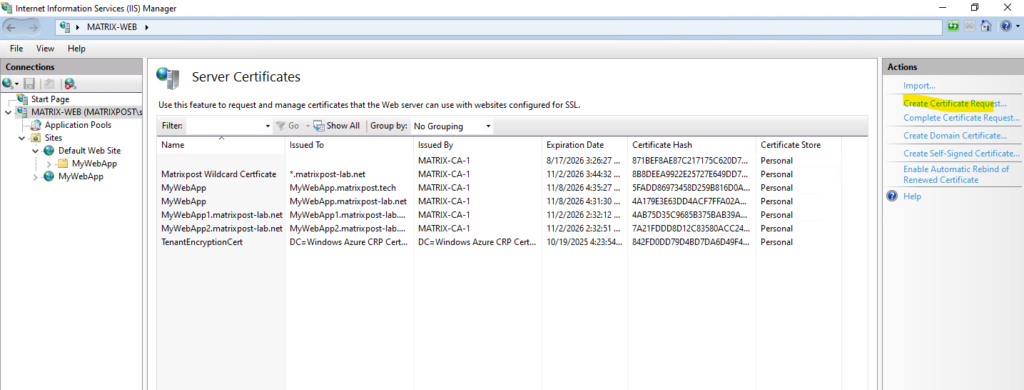
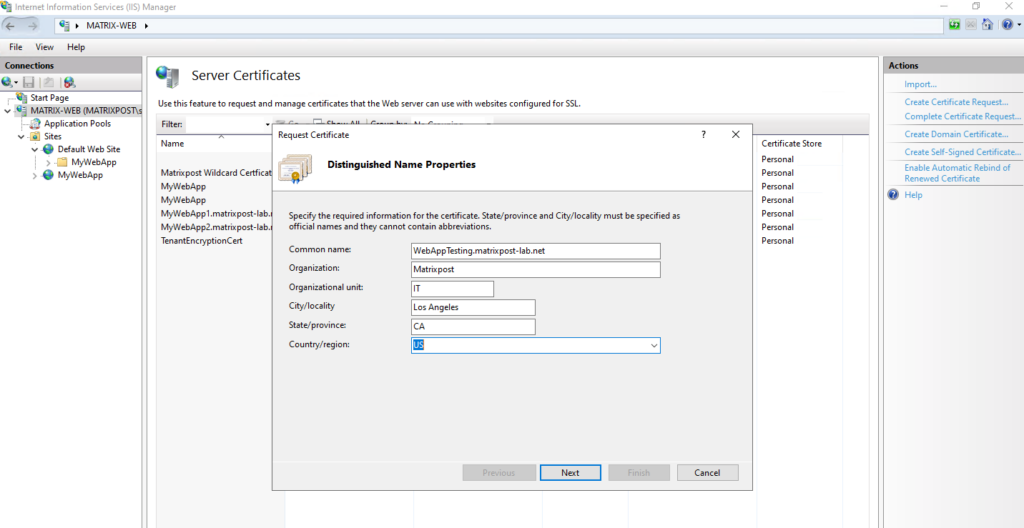
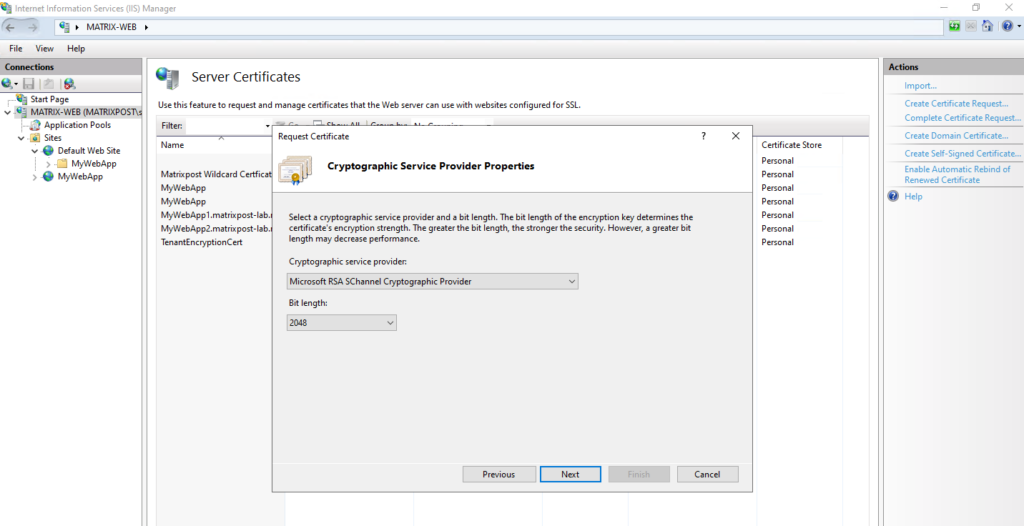
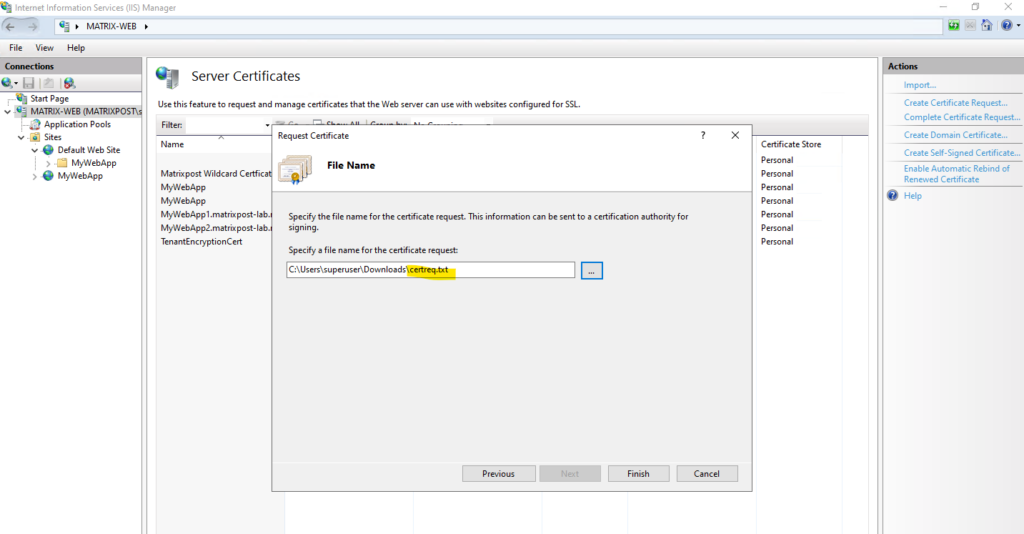
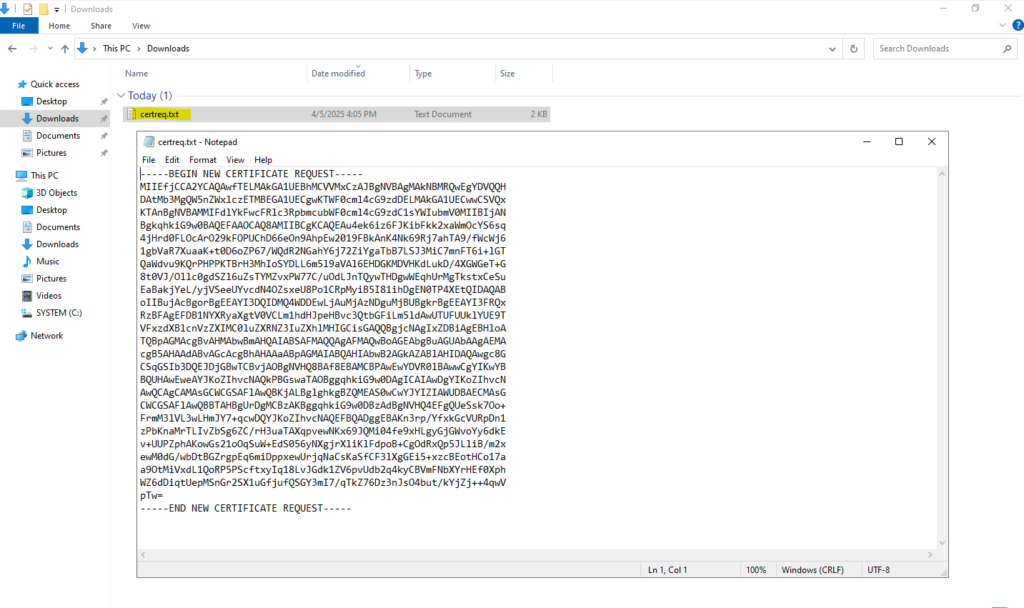
Create a Certificate Signing Request (CSR or Certification Request) on Windows by using the certreq command
As mentioned we can also create a CSR by using the certreq command and a file (e.g. request.ini) where we define the properties of the certificate request by hand.
[Version]
Signature="$Windows NT$"
[NewRequest]
Subject = "CN=server.domain.com, O=Your Organization, L=Your City, S=Your State, C=US"
KeySpec = 1 ; AT_KEYEXCHANGE (for SSL/TLS)
KeyLength = 2048 ; RSA key size
Exportable = TRUE ; Allows private key export
MachineKeySet = TRUE ; Stores key in machine store (for server certs)
ProviderName = "Microsoft RSA SChannel Cryptographic Provider"
RequestType = PKCS10
HashAlgorithm = SHA256 ; Recommended for security
[Extensions]
2.5.29.17 = "{text}" ; SAN (Subject Alternative Names)
_continue_ = "dns=server.domain.com&"
_continue_ = "dns=altname.domain.com"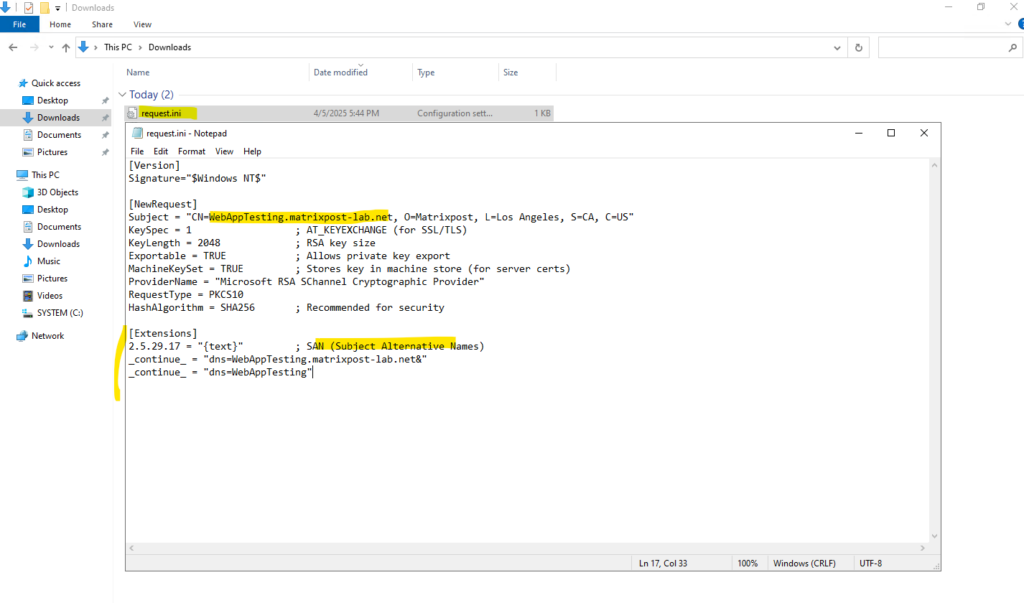
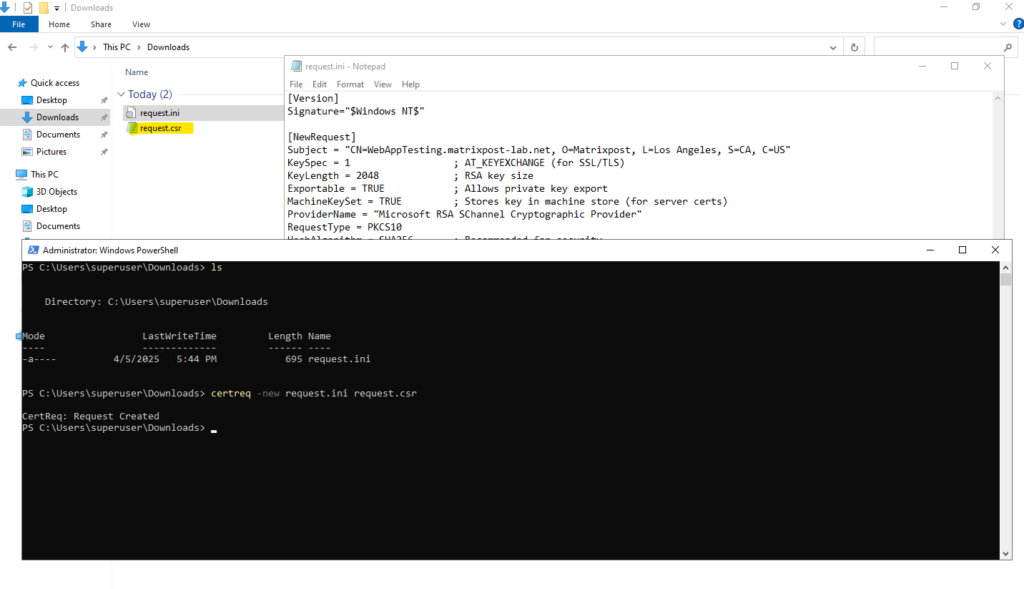
Below we will generate the CSR by using the certreq command.
PS> certreq -new request.ini request.csr
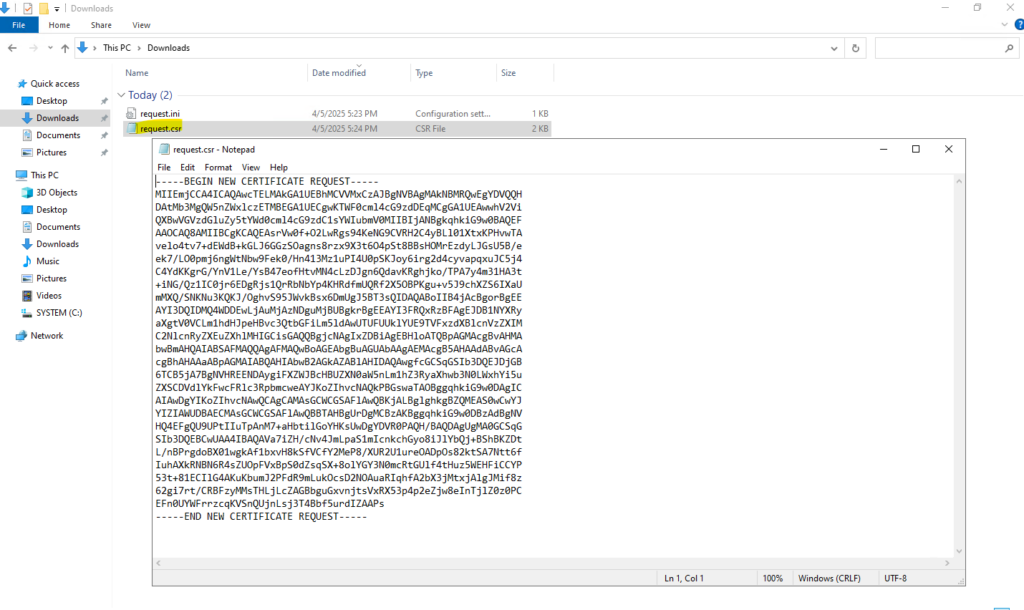
Submit the CSR to the internal CA (AD CS) on Windows by using the certreq command
Finally to retrieve a new certificate from our internal CA, we will now submit the CSR to it.
!! Note !!
In case your certificate template name will actually have spaces between like in my case, you need to leave them for this command, otherwise you will run into an error as shown in the troubleshooting section further down.Replace CA-Server\CA-Name with your CA server (e.g., dc01\MyDomain-CA).
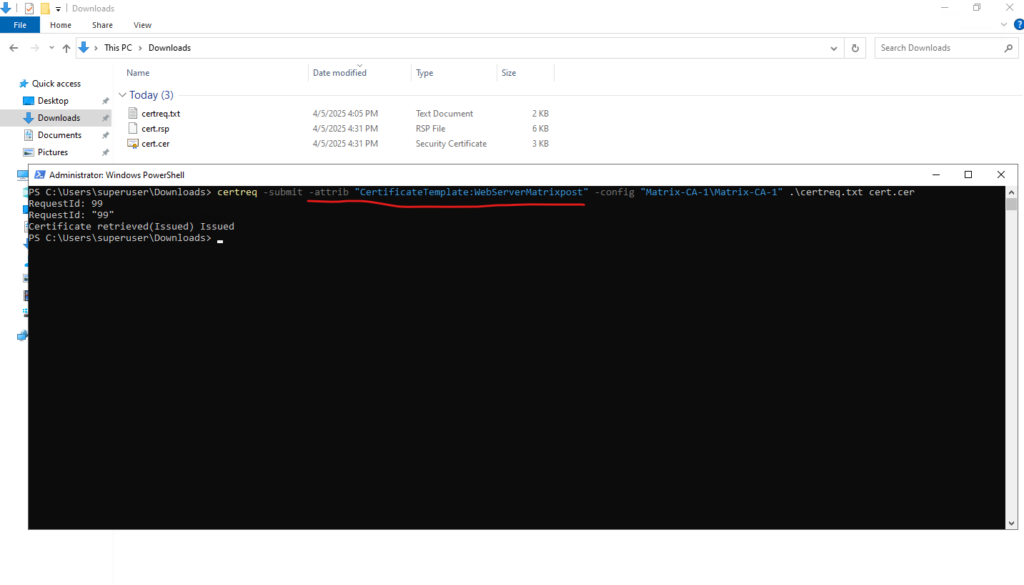
> certreq -submit -attrib "CertificateTemplate:<TemplateNameWithoutSpaces>" -config "CA-Server\CA-Name" request.csr request.cer > certreq -submit -attrib "CertificateTemplate:WebServerMatrixpost" -config "Matrix-CA-1\Matrix-CA-1" request.csr cert.cer
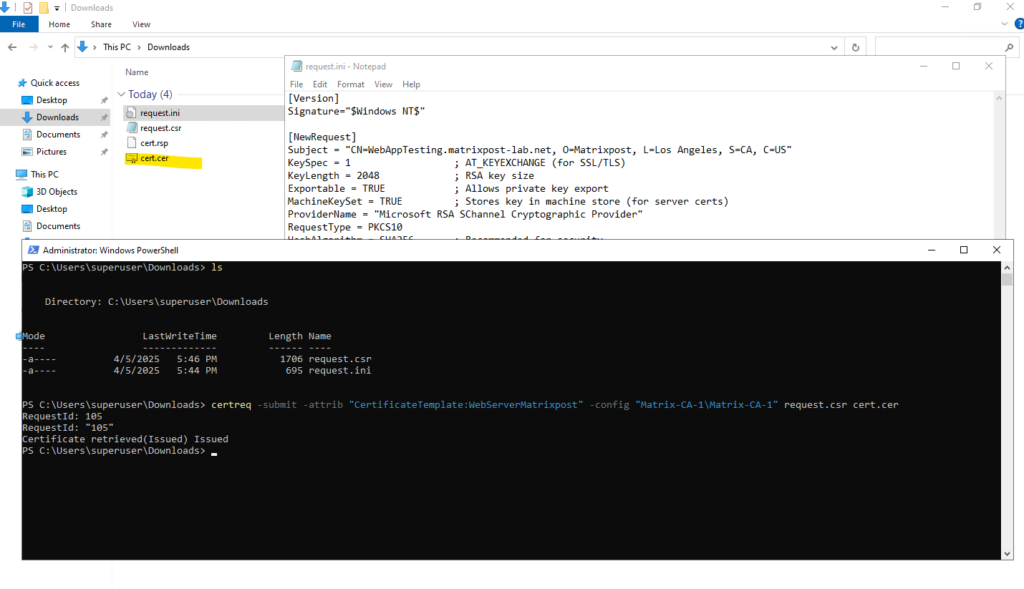
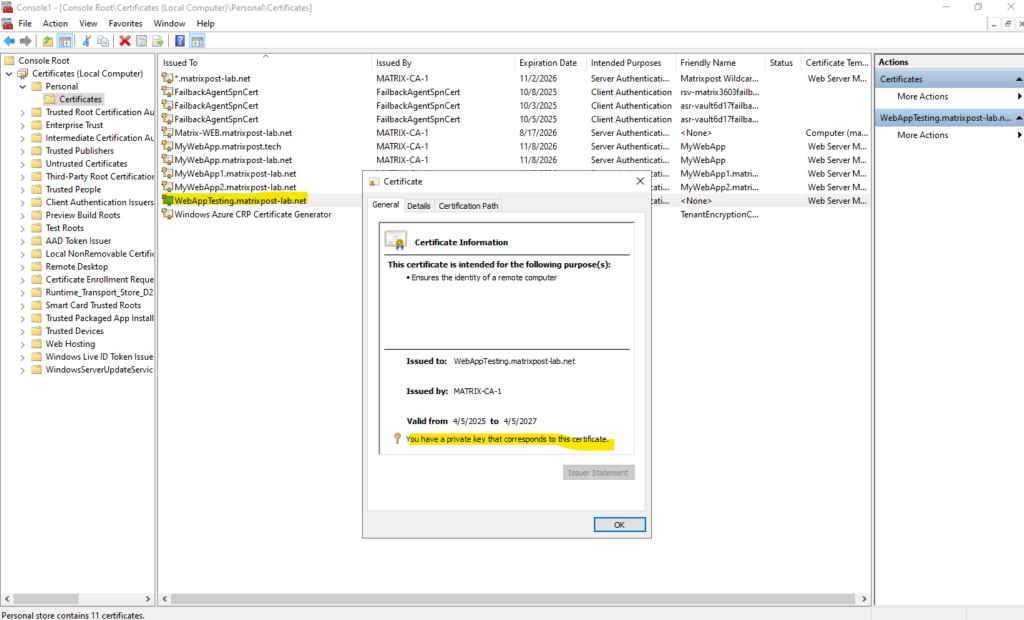
The certificate was issued and created successful.
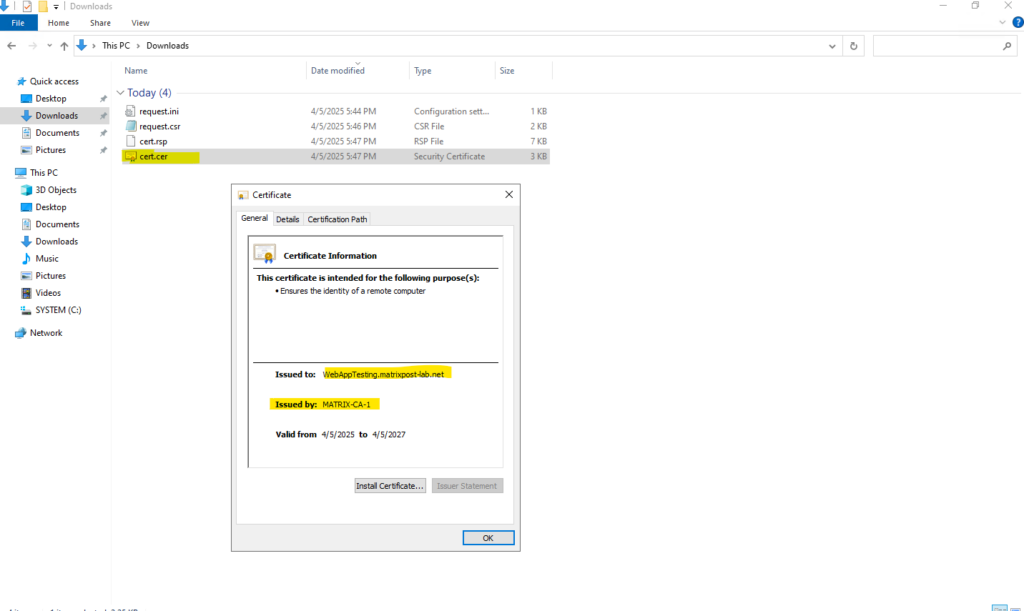
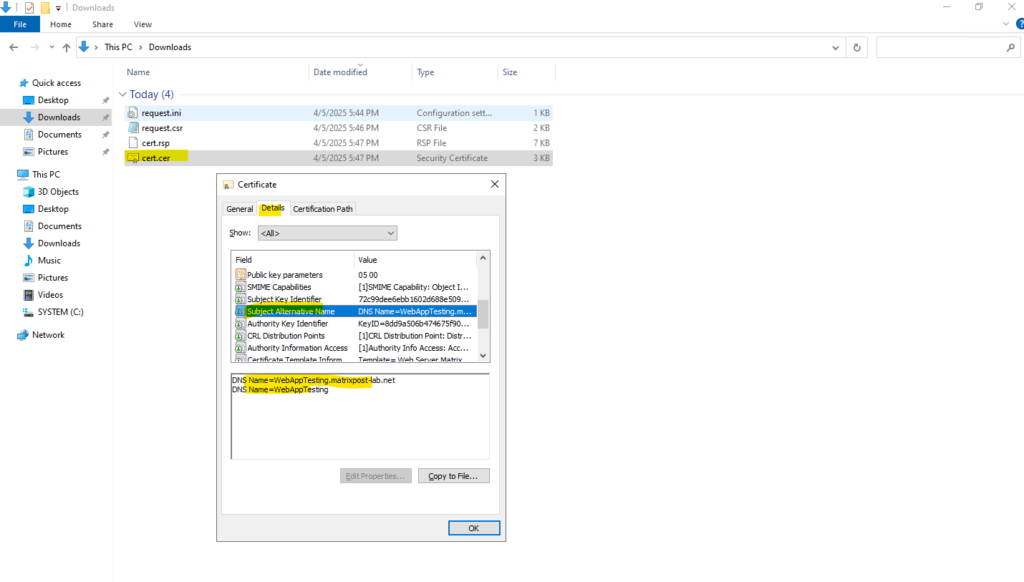
We can now install the certificate on the computer on which we created the CSR, on this computer also the corresponding private key was created and finally is stored.
Further we can also export the certificate from this computer as we included the following parameter in our request.ini file previously.
Exportable = TRUE ; Allows private key export
Create a Private Key and Certificate Signing Request (CSR or Certification Request) on Linux by using OpenSSL
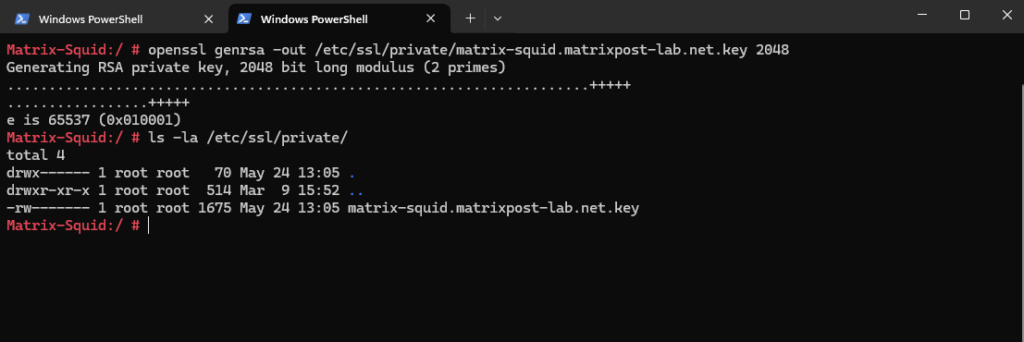
On Linux to generate a new private key we can use the following openssl command.
# openssl genrsa -out /etc/ssl/private/matrix-squid.matrixpost-lab.net.key 2048
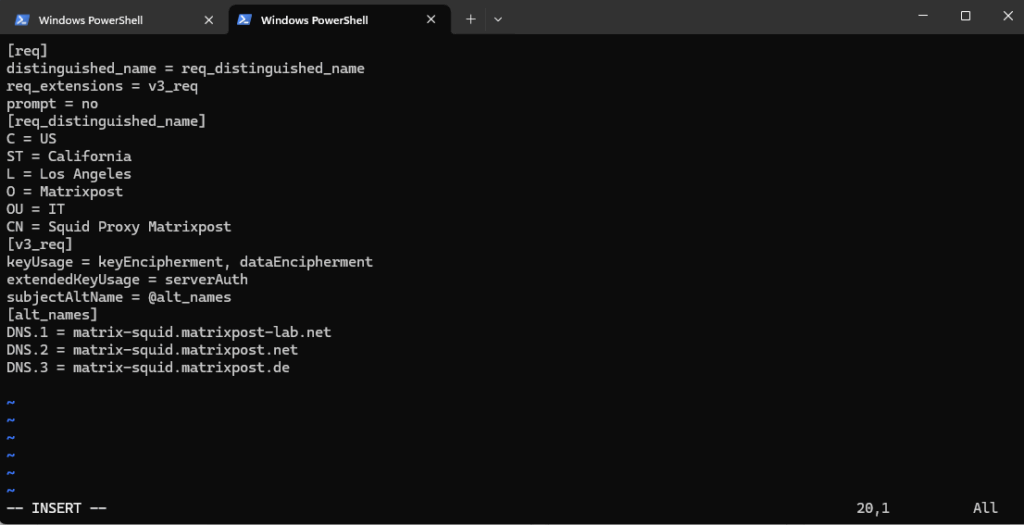
In the next step, we create the Certificate Signing Request (CSR) — a digital request for the creation of an identity certificate (here: a public key certificate).
I will first create an extension file named req.conf to also include a subject alternative name which is these days mandatory for most browsers.
[req] distinguished_name = req_distinguished_name req_extensions = v3_req prompt = no [req_distinguished_name] C = US ST = California L = Los Angeles O = Matrixpost OU = IT CN = Squid Proxy Matrixpost [v3_req] keyUsage = keyEncipherment, dataEncipherment extendedKeyUsage = serverAuth subjectAltName = @alt_names [alt_names] DNS.1 = matrix-squid.matrixpost-lab.net DNS.2 = matrix-squid.matrixpost.net DNS.3 = matrix-squid.matrixpost.de
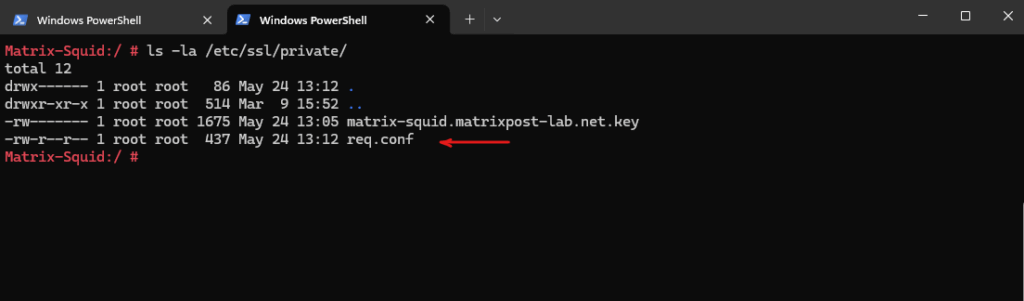
Now we can create the Certificate Signing Request (CSR) by using our extension file named req.conf.
# openssl req -new -key /etc/ssl/private/matrix-squid.matrixpost-lab.net.key -out /etc/ssl/private/matrix-squid.matrixpost-lab.net.csr -config /etc/ssl/private/req.conf
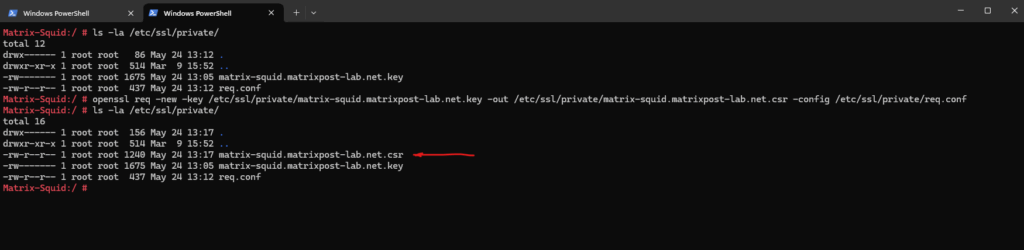
To finally submit the CSR to the internal CA (AD CS) and to issue the signed certificate, the best way is to copy the CSR to a domain joined Windows machine and using there the certreq tool or CA Web Enrollment role service as previously shown further above.
Troubleshooting
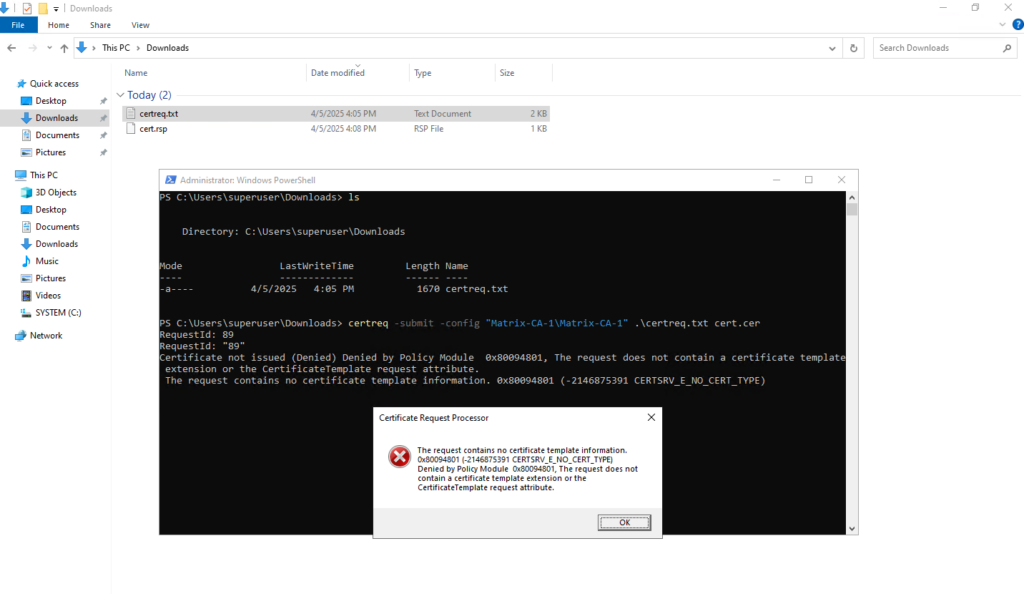
The request contains no certificate template information
We need to include the -attrib flag with the desired certificate template when submitting the CSR to our internal CA.
> certreq -submit -attrib "CertificateTemplate:<TemplateNameWithoutSpaces>" -config "CA-Server\CA-Name" request.csr request.cer
The request certificate template is not supported by this CA
For this error message there could be several reasons. In my case below its just because of the certificate template name which includes spaces and isn’t supported.
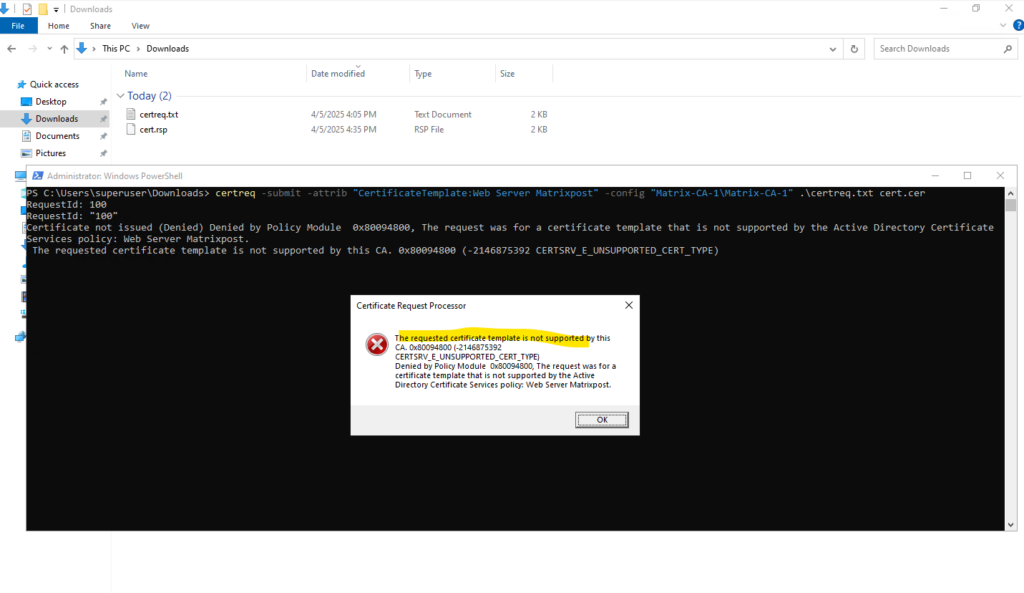
We can just leave the spaces here and it works.
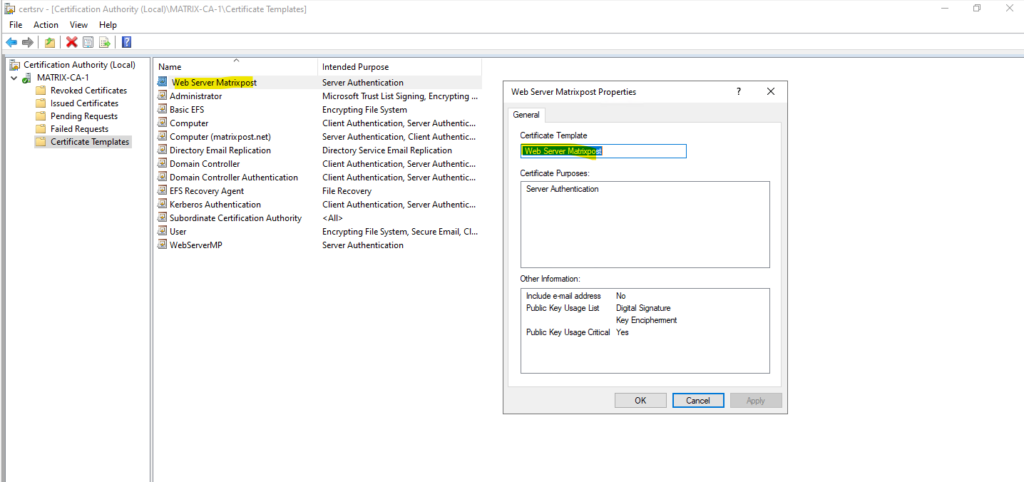
!! Note !!
The certificate template name shouldn’t include any spaces when using the command above. So in case the certificate template name is for example “Web Server Matrixpost”, we need to use here simply “WebServerMatrixpost” like shown below.
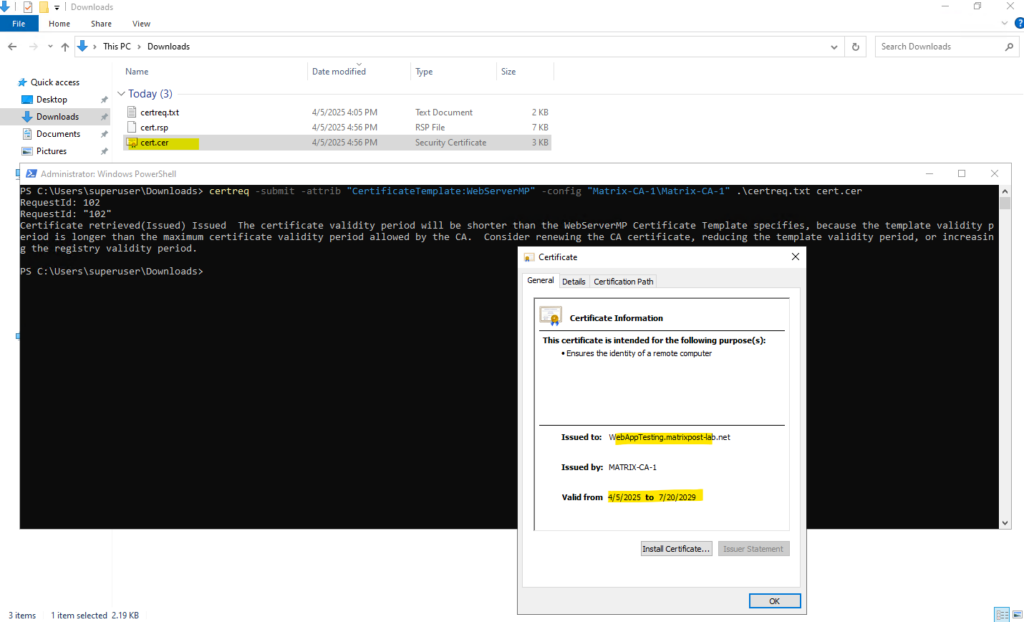
The certificate validity period will be shorter than the Certificate Template specifies
By default, the lifetime of a certificate that is issued by a Stand-alone Certificate Authority CA is one year.
After one year, the certificate expires and is not trusted for use. There may be situations when you have to override the default expiration date for certificates that are issued by an intermediate or an issuing CA.
The validity period that is defined in the registry affects all certificates that are issued by Stand-alone and Enterprise CAs. For Enterprise CAs, the default registry setting is two years. For Stand-alone CAs, the default registry setting is one year. For certificates that are issued by Stand-alone CAs, the validity period is determined by the registry entry.
For certificates that are issued by Enterprise CAs, the validity period is defined in the template that is used to create the certificate. The validity period defined in the template applies to all certificates issued by any Enterprise CA in the Active Directory forest.
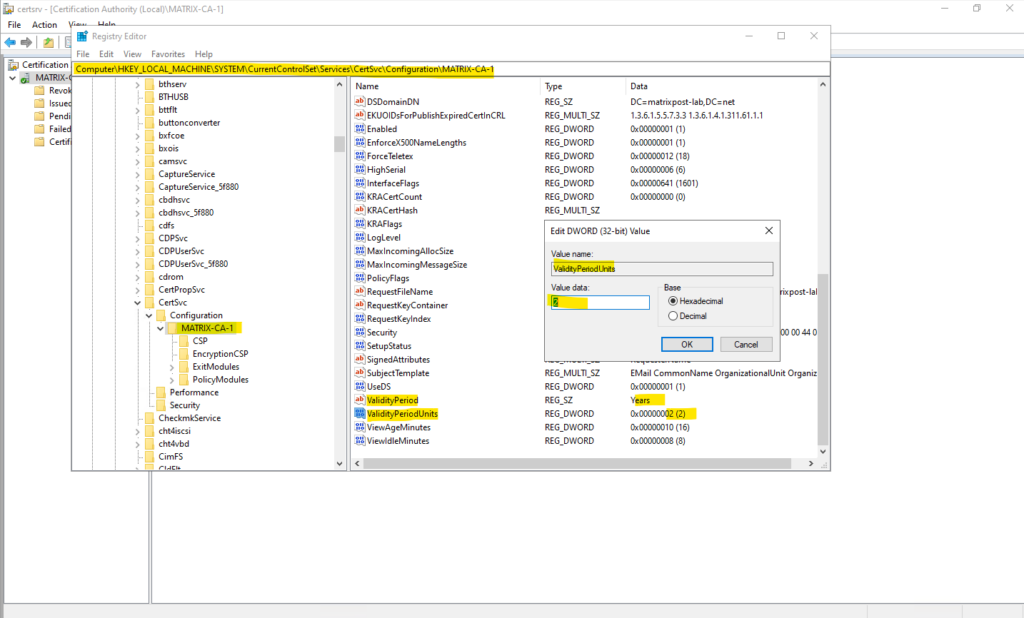
As mentioned, for a Stand-alone Certificate Authority CA you can change the lifetime of a certificate in the registry as shown below.
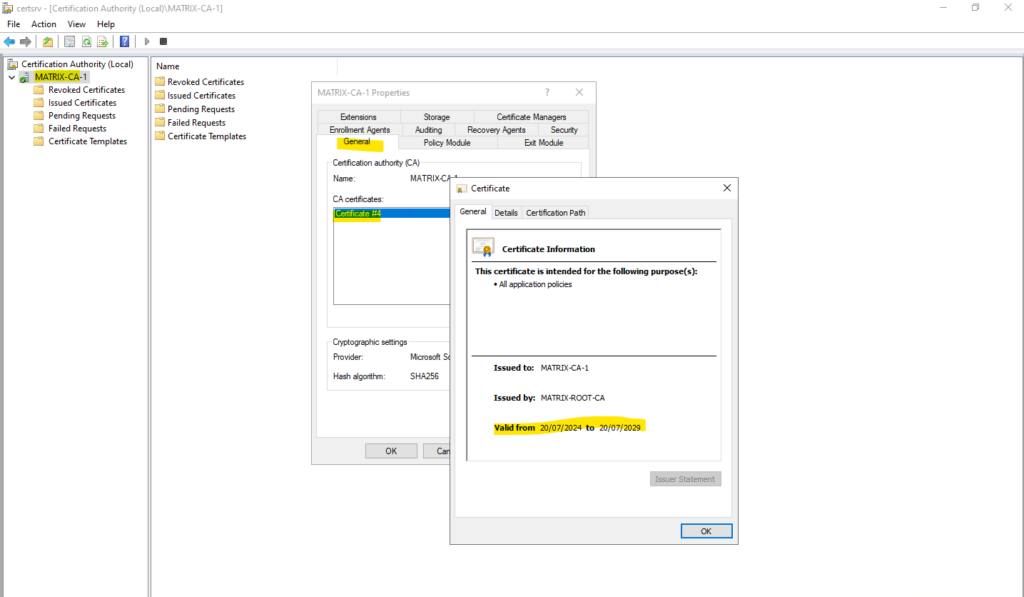
In my case the MATRIX-CA-1 is a Enterprise CA and intermediate CA of a standalone offline Root CA, so to change the validity period here we would need to renewing the CA certificate and adjust its lifetime.
So far its valid till 20/07/2029, therefore the certificate validity period of our previously issued certificate will not be valid beyond this date and therefore we get this message.
About how to set up a 2-tier PKI in Active Directory Certificate Services (AD CS), you can also read my following post.
Links
certreq
https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/certreq_1Change the expiration date of certificates that are issued by Certificate Authority
https://learn.microsoft.com/en-us/troubleshoot/windows-server/certificates-and-public-key-infrastructure-pki/change-certificates-expiration-dateChange expiration date of certificates issued by CA
https://learn.microsoft.com/en-us/troubleshoot/windows-server/certificates-and-public-key-infrastructure-pki/change-certificates-expiration-date#change-expiration-date-of-certificates-issued-by-ca
Follow me on LinkedIn


