Set up an Azure Storage Account and Blob Storage for SFTP Access by using a Private Endpoint
In one of my previous posts we already saw how to setup up an Azure storage account and blob storage for SFTP Access.
The storage account we configured then with public access through the internet as shown on the screenshot below.
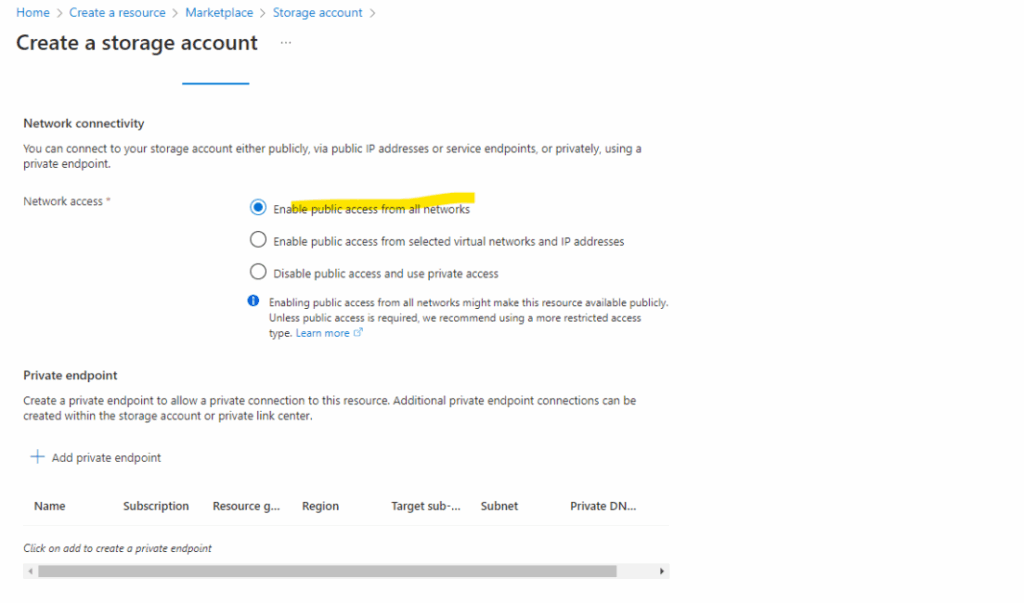
Now this time we will see how we can restrict access by using private access through a private endpoint in Azure assigned to our storage account.
You can use private endpoints for your Azure Storage accounts to allow clients on a virtual network (VNet) or your on-premise network (by using a Site-to-site VPN tunnel) to securely access data over a Private Link.
The private endpoint uses a separate IP address from the VNet address space for each storage account service.
Network traffic between the clients on the VNet or routed (through VPN tunnel) on-premise network and the storage account traverses over the VNet or VPN tunnel and a private link on the Microsoft backbone network, eliminating exposure from the public internet.
More about using Azure Private Endpoints you will also find here https://learn.microsoft.com/en-us/azure/storage/common/storage-private-endpoints.
More details about Private Endpoints, Azure Integrated Private DNS Zones and Azure DNS Private Resolver you will also find in my following post.
Set up the Storage Account and Blob Storage by using Private Access
In this post I just want to show the different configuration when using a private endpoint to access the storage account and blob storage.
About set up a new storage account in general, please refer to one of my last posts and section https://blog.matrixpost.net/set-up-an-azure-storage-account-and-blob-storage-for-sftp-access/#create_storage_account.
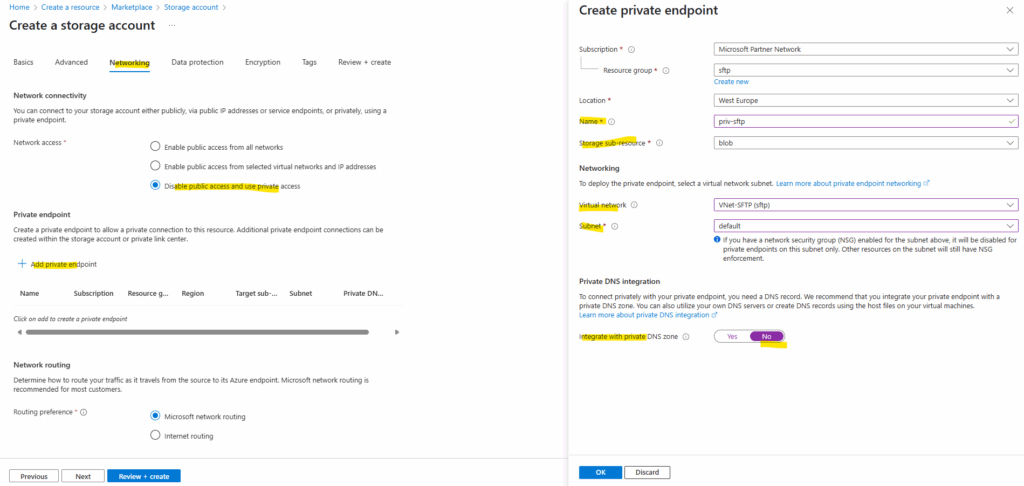
The different configuration starts on the Networking tab below. Select Disable public access and use private access and click on Add private endpoint.
Under Create private endpoint here Microsoft recommends to use a private DNS zone, just for testing purpose in my lab environment I want to save the costs and choose here No. I will configure this on my on-premise DNS server later.
Also select here the virtual network and subnet in which the private endpoint (IP address VNet) will be created and assigned to our storage account.
Finally its not about the price of the Azure private DNS zones itself in Azure, but about the Azure DNS Private resolver costs for endpoints and rulesets, which are really expensive. When using here Azure private DNS zones, we also need the Azure DNS Private resolver to forward on-premise DNS queries to Azure as shown in my following post and section https://blog.matrixpost.net/how-to-onboard-on-premise-server-to-azure-arc-by-using-a-site-to-site-ipsec-vpn-and-azure-arc-private-link-scope/#dns_integrated_private_zones.
Azure DNS pricing
https://azure.microsoft.com/en-us/pricing/details/dns/
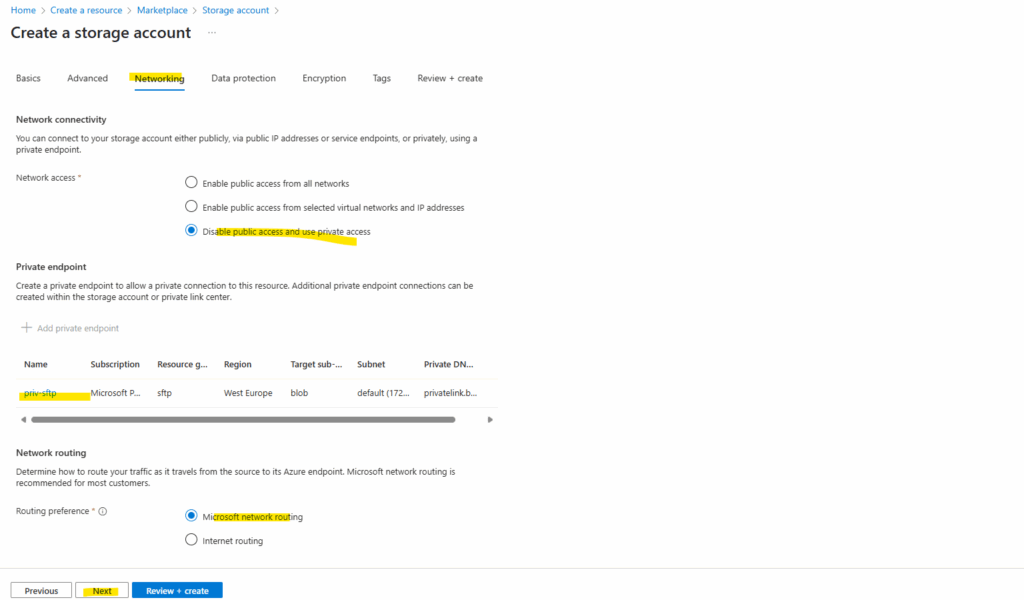
Private endpoint IPs assigned dynamically (by using the Azure portal by default) are generally stable but can change in rare cases. If you want to assign static IP address to your storage account and blob storage you can read my following post and section.
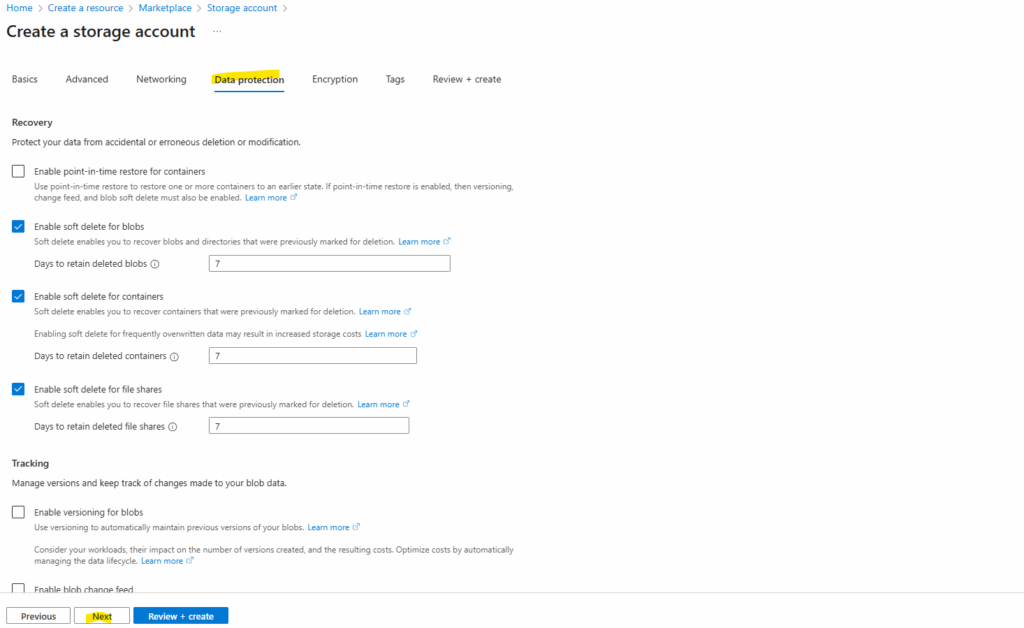
For data protection I will use the default settings.
Also for the encryption I will use the default settings.
Finally click on Create.
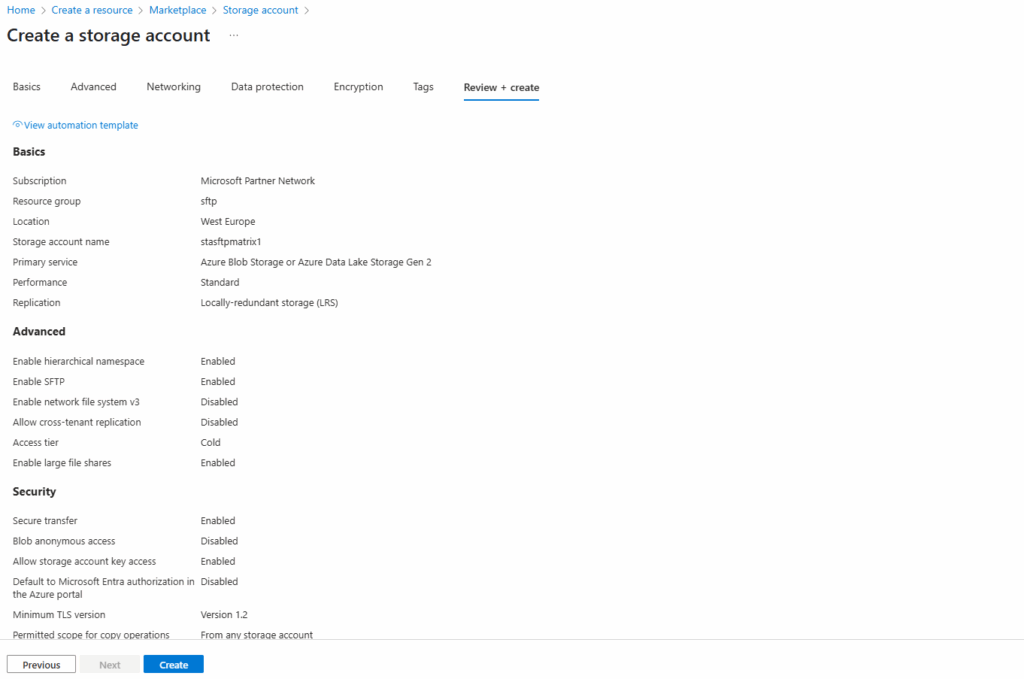
When the storage account is successfully created, we will see the network access under Storage account -> Security + networking -> Networking as shown below.
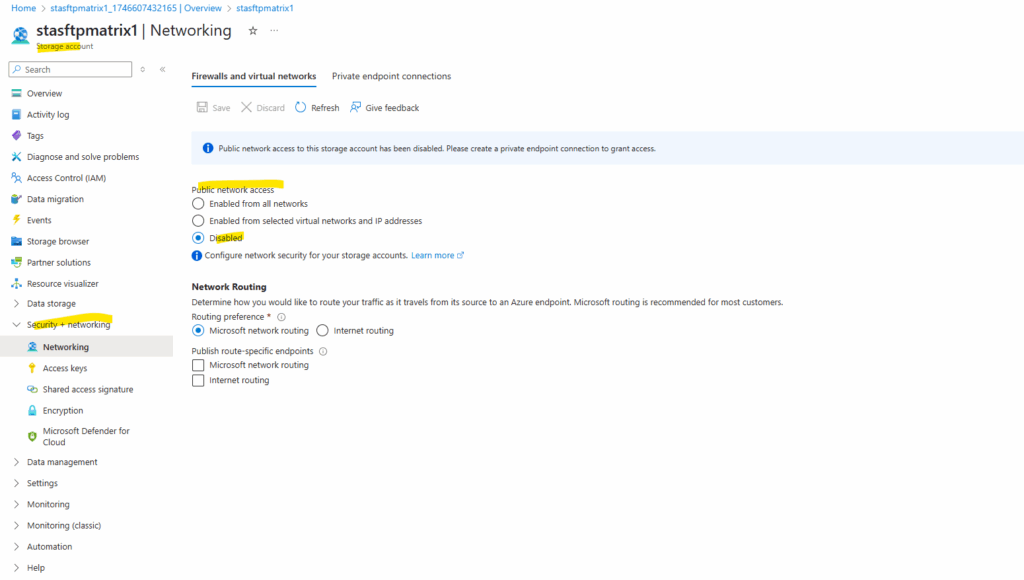
On the Private endpoint connections tab we will also see that our created private endpoint is successfully assigned to the storage account.
DNS Configuration
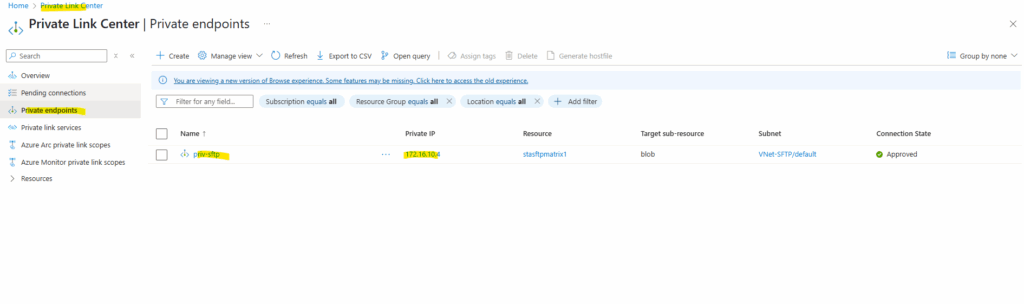
The private endpoint we configured when creating our storage account above, we will later find in the Private Link Center shown below. Just search for private endpoints.
We can also see below the assigned private IP address from the virtual network we choose to use for.
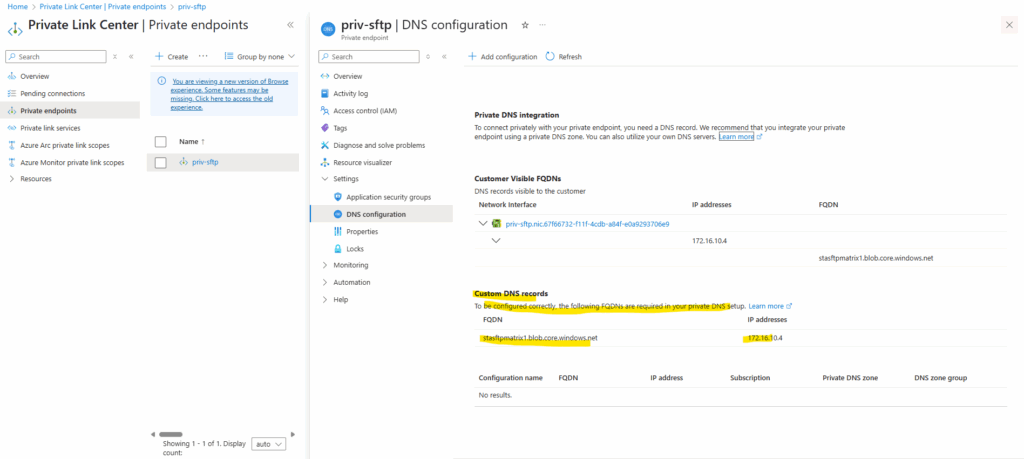
We first need to note the DNS records within the newly created private endpoint. We need to configure them later on our on-premise DNS server.
In case just a bunch of machines needs to access the storage account and blob storage, we can of course also just add the DNS records to the local hosts file for name resolution.
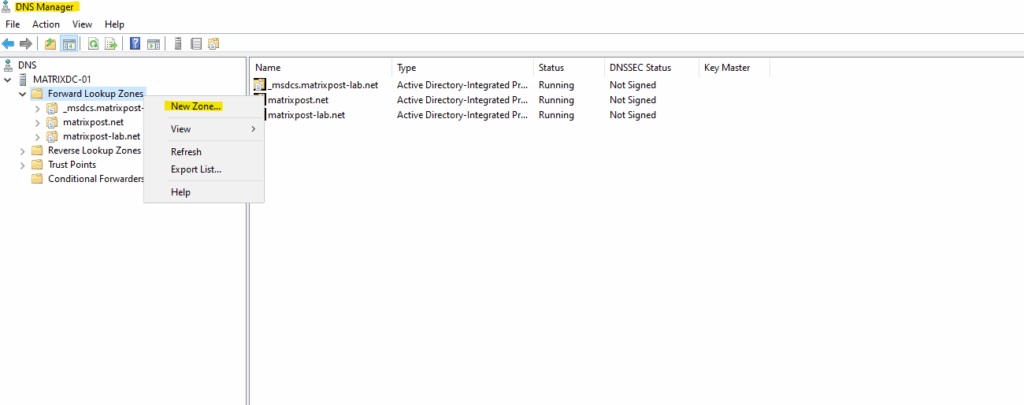
Configured on my on-premise DNS server. Create a new forward lookup zone.
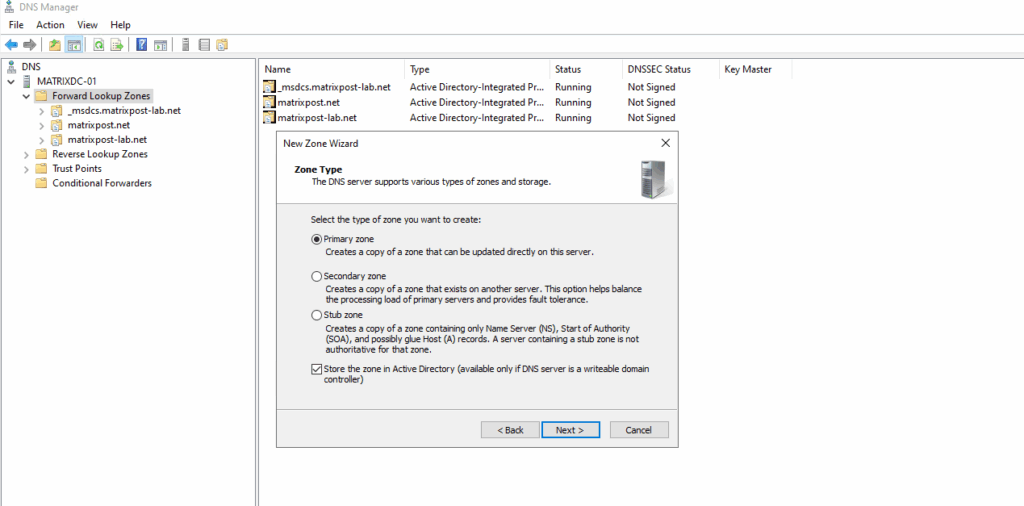
We will configure here a primary zone.
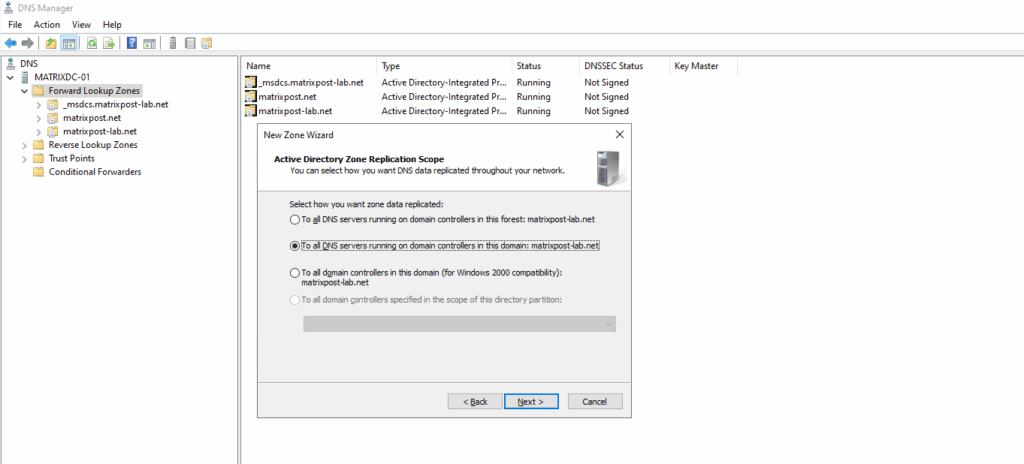
For the zone name enter the domain part of the private endpoint.
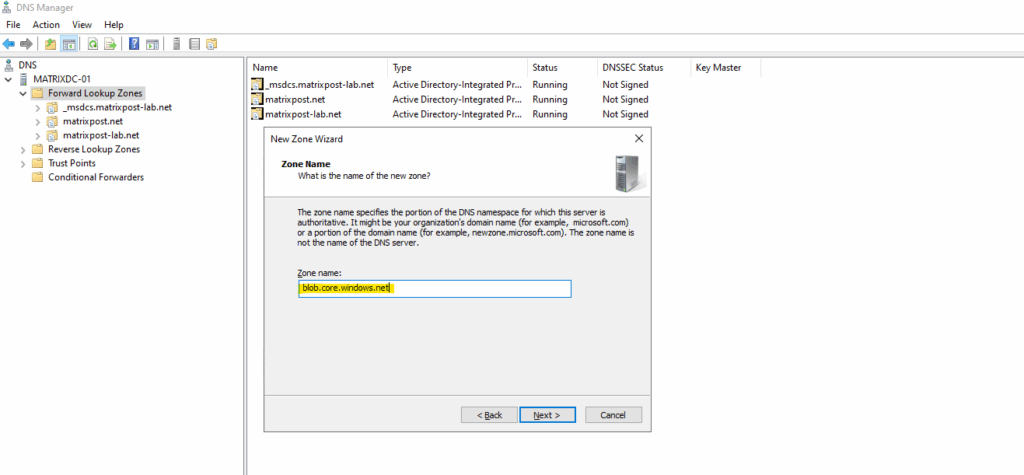
The domain we will find as shown further above under Private Endpoint -> Settings -> DNS configuration.
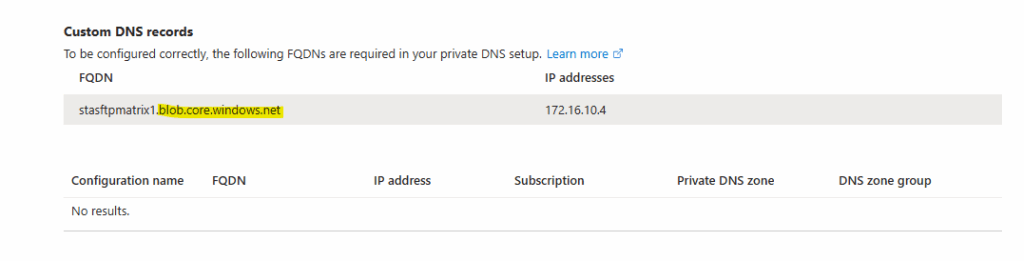
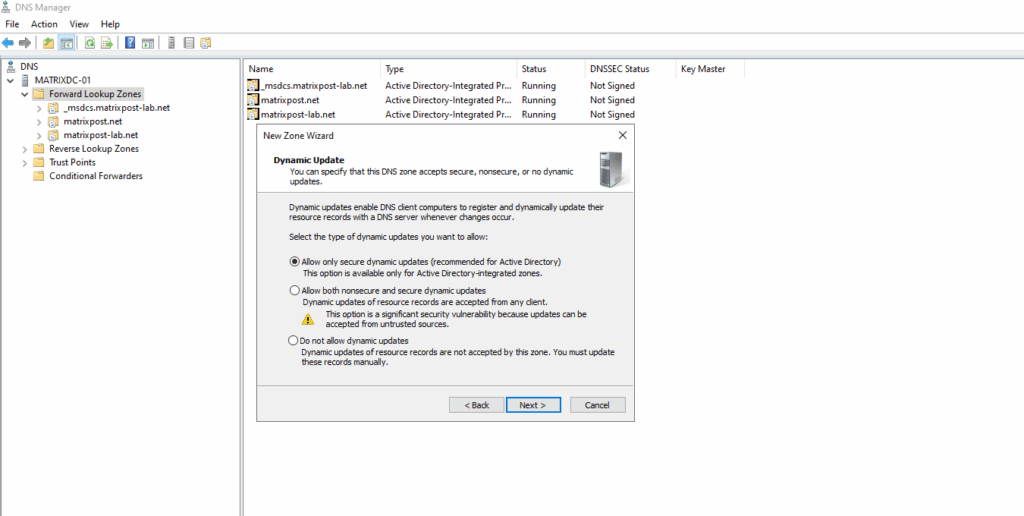
Create the A-Record for the private endpoint.
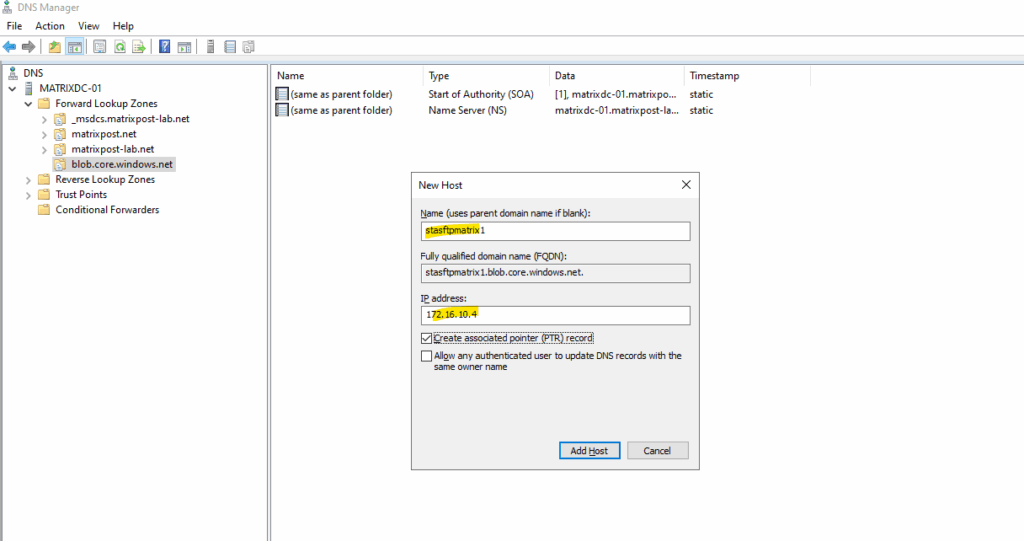
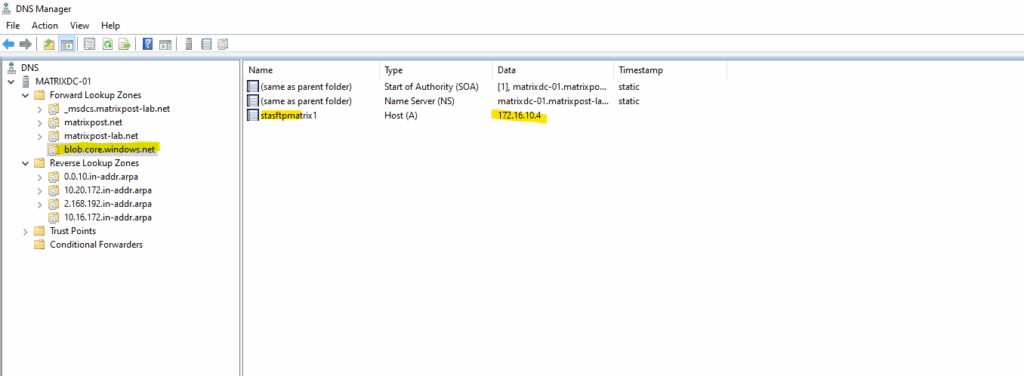
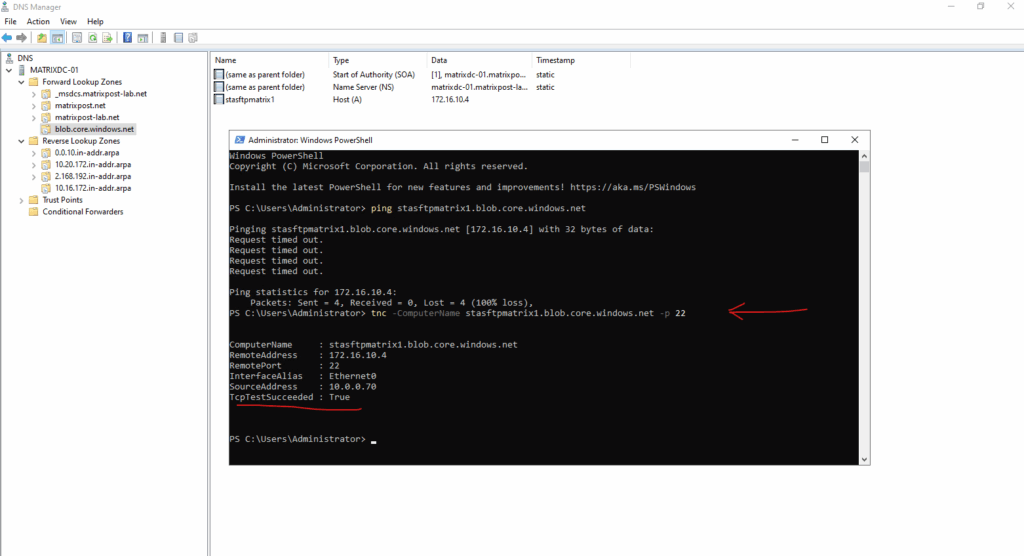
As my Site-to-Site IPSec VPN tunnel between my on-premise lab environment and Azure is already established, I can now first check if I can connect to my Azure storage account and blob storage on its assigned private endpoint (IP address) and SSH/SFTP Port 22.
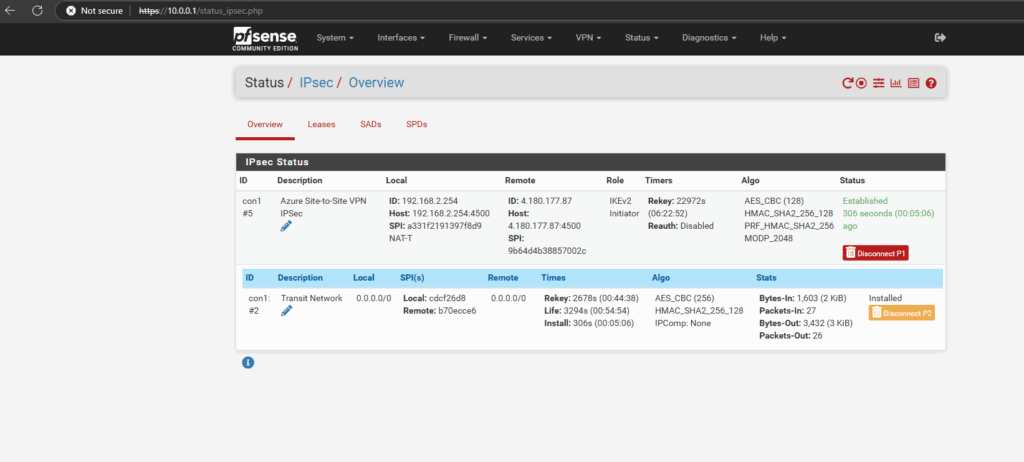
About how to set up an IPSec route-based Site-to-Site VPN Tunnel between Azure and your on-premise network, you can also read my following posts.
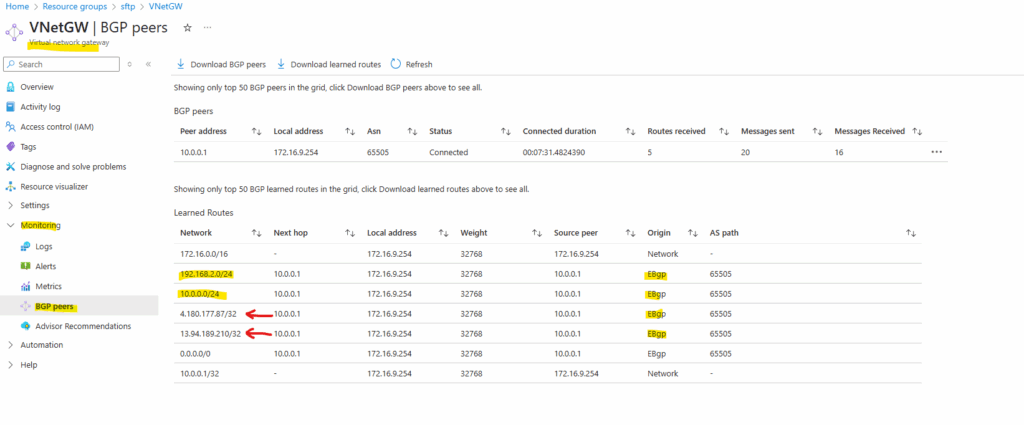
BGP is also working and advertised both of my internal LAN subnets (10.0.0.0/24 & 192.168.2.0/24).
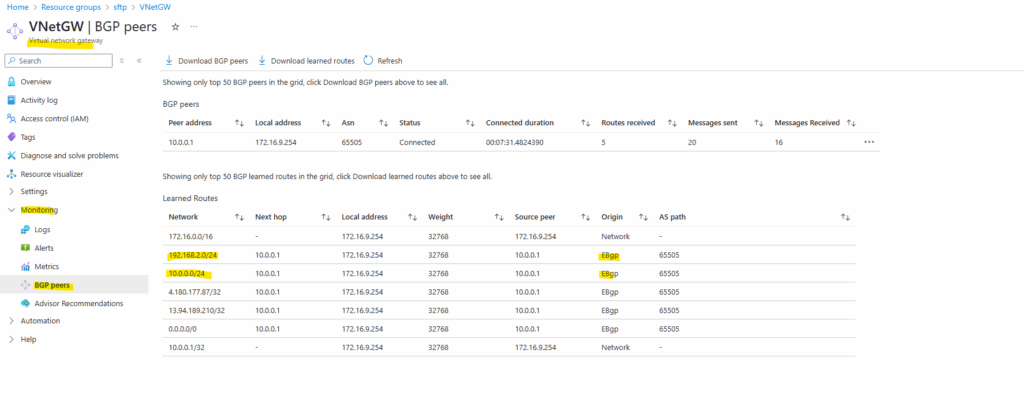
By the way we can also see that here both public IP addresses of the VPN Gateways (on-premise and Azure) will be advertised by my on-premise VPN applicance (pfSense) to Azure which will lead to some issues and we should avoid here.
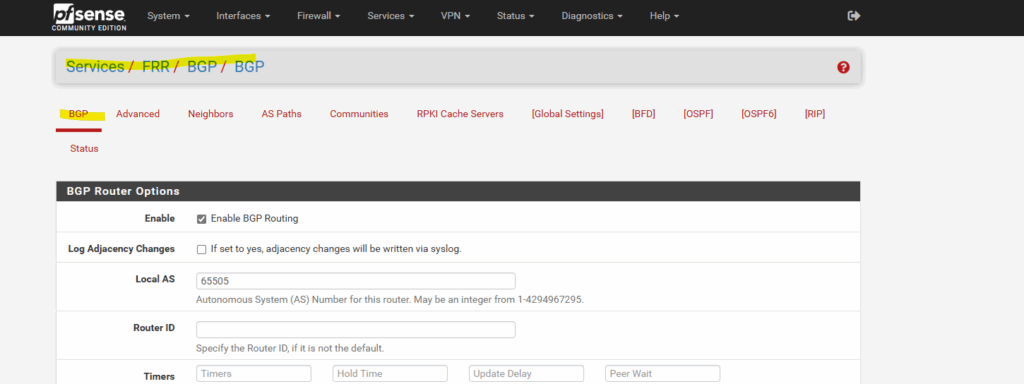
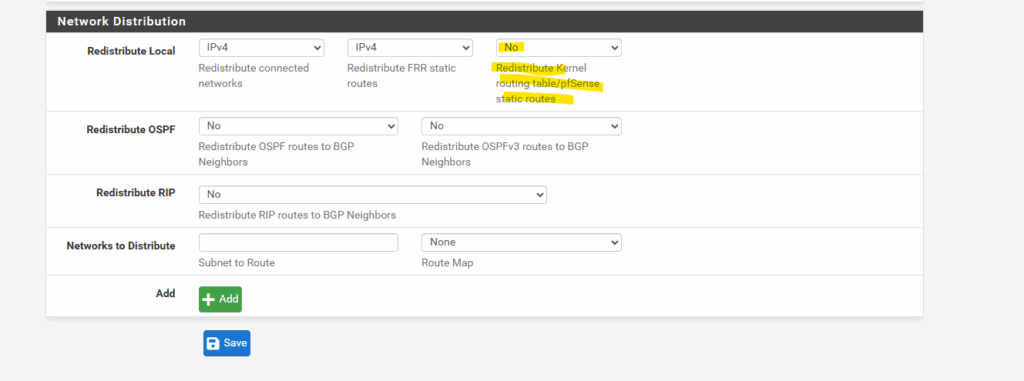
In pfSense we need to set the following to No under Services -> FRR -> BGP -> BGP -> Network Distribution section in order to avoid that also the public IP addresses of the VPN Gateways will be advertised through BGP.
More about this issue you will also find in my following post about how to set up dynamic routing with FRR (Free Range Routing) in pfSense which is the successor of OpenBGPD.
Also on the on-premise VPN appliance (pfSense).
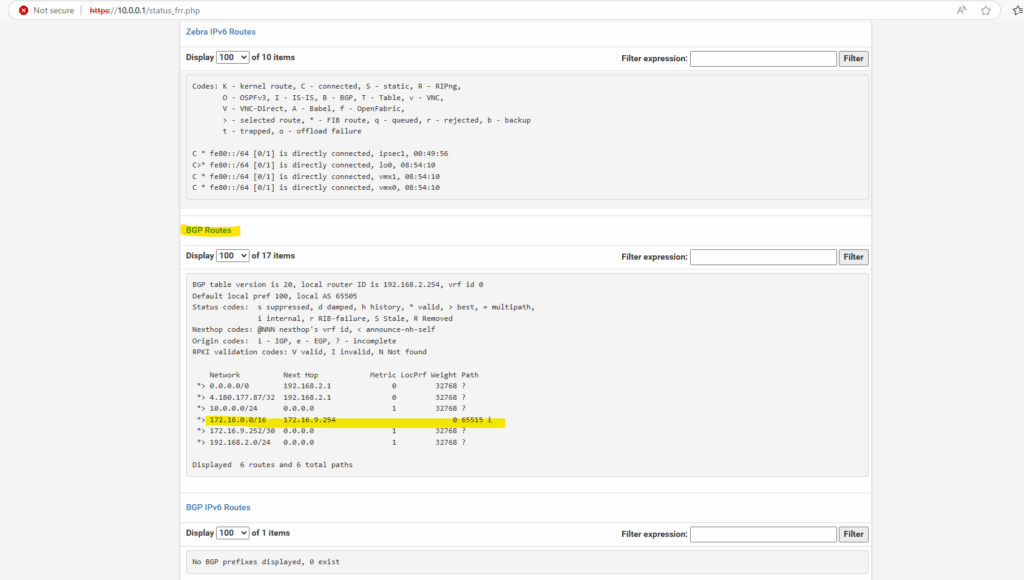
Testing if I can already access the storage account and blob storage by using TCP port 22 used by SFTP, looks good.
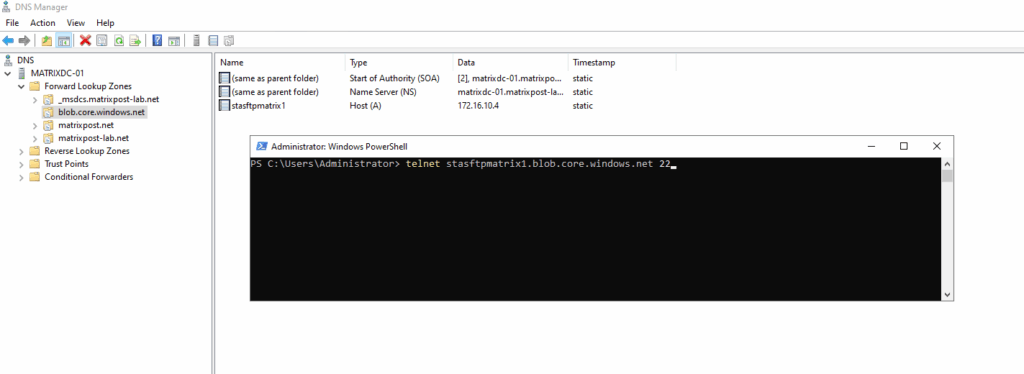
Or by using the good old telnet tool.
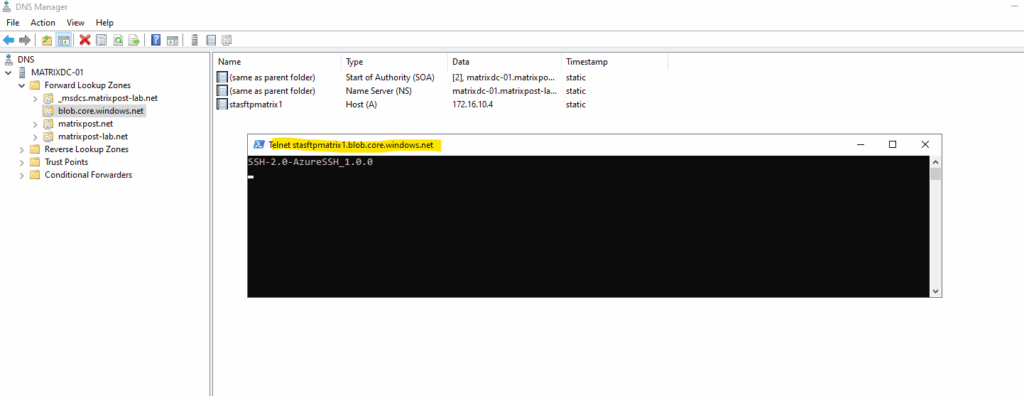
We can now configure SFTP on our new storage account as shown in my last post and section https://blog.matrixpost.net/set-up-an-azure-storage-account-and-blob-storage-for-sftp-access/#configure_sftp.
Links
Use private endpoints for Azure Storage
https://learn.microsoft.com/en-us/azure/storage/common/storage-private-endpointsSSH File Transfer Protocol (SFTP) support for Azure Blob Storage
https://learn.microsoft.com/en-us/azure/storage/blobs/secure-file-transfer-protocol-supportEnable or disable SSH File Transfer Protocol (SFTP) support in Azure Blob Storage
https://learn.microsoft.com/en-us/azure/storage/blobs/secure-file-transfer-protocol-support-how-to?tabs=azure-portalConnect to Azure Blob Storage by using the SSH File Transfer Protocol (SFTP)
https://learn.microsoft.com/en-us/azure/storage/blobs/secure-file-transfer-protocol-support-connectAzure Blob Storage pricing
https://azure.microsoft.com/en-us/pricing/details/storage/blobs/


