Set up Split-Brain DNS in Active Directory
In this post we will see how we can set up split-brain DNS for Active Directory integrated DNS server and zones by using zone scopes and DNS Policy.
In past this scenario required to maintain two different DNS servers, each providing services to each set of users, internal and external. Another configuration scenario for split-brain deployment is Selective Recursion Control for DNS name resolution.
Split-brain DNS is a network configuration strategy used to manage how domain names are resolved differently depending on the network location of the user. In essence, it allows different IP addresses to be returned for the same domain name based on whether the DNS request originates from within an internal network (e.g., a corporate intranet) or from an external network (e.g., the public internet).
This approach helps organizations maintain separate internal and external resources, enhance security, and ensure that sensitive internal services are not exposed to the outside world.
Introduction
In a split-brain DNS deployment you have two versions of a single zone – one for the internal users on your organization intranet, and one for the external users, who are typically users on the Internet.
In past this scenario required that DNS administrators maintain two different DNS servers, each providing services to each set of users, internal and external. If only a few records inside the zone were split-brained or both instances of the zone (internal and external) were delegated to the same parent domain, this became a management conundrum.
Another configuration scenario for split-brain deployment is Selective Recursion Control for DNS name resolution. In some circumstances, the Enterprise DNS servers are expected to perform recursive resolution over the Internet for the internal users, while they also must act as authoritative name servers for external users, and block recursion for them.
Source: https://learn.microsoft.com/en-us/windows-server/networking/dns/deploy/split-brain-dns-deployment
Configure a second Interface on the Domain Controller (DNS Server)
For split-brain DNS in Active Directory we need two network interfaces or at least two different IP addresses on which the DNS server is listening for incoming DNS queries.
I will use here a second network interface on which I will assign a further IP address which is later used to resolve DNS queries from external clients. Adjust this to your environment and how access to the DNS server from external clients is finally implemented.
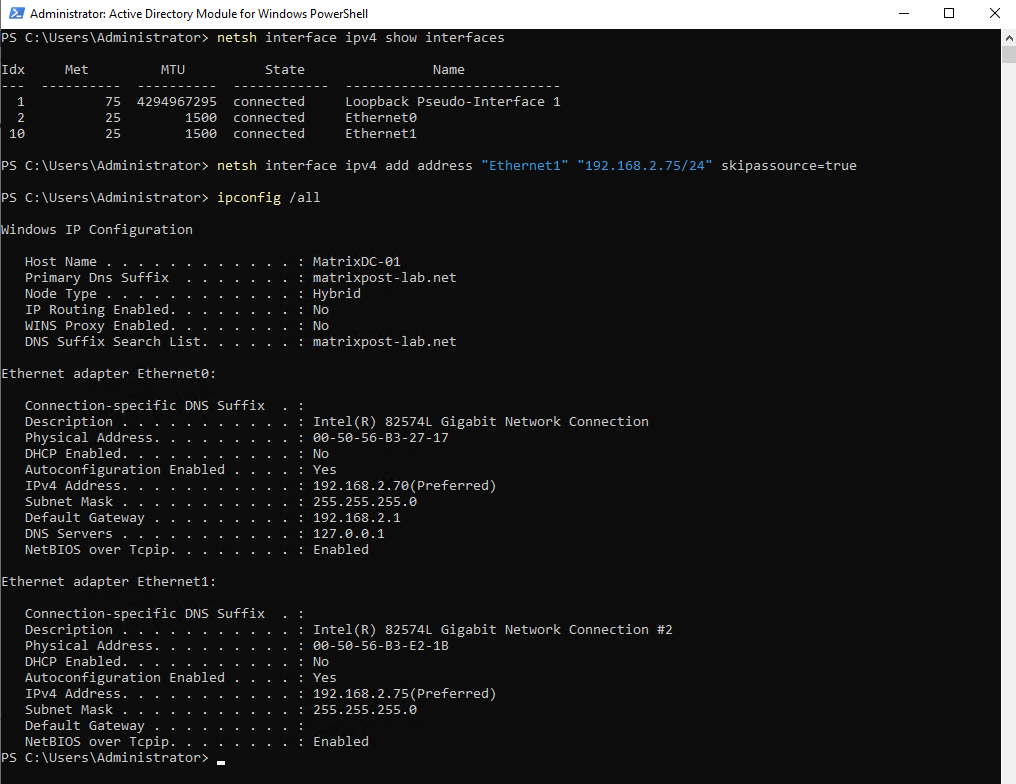
> netsh interface ipv4 show interfaces > netsh interface ipv4 add address "Ethernet1" "192.168.2.75/24" skipassource=true
If SkipAsSource is set to true, then that IP address will not be registered in DNS and will not be used for host initiated outgoing communications
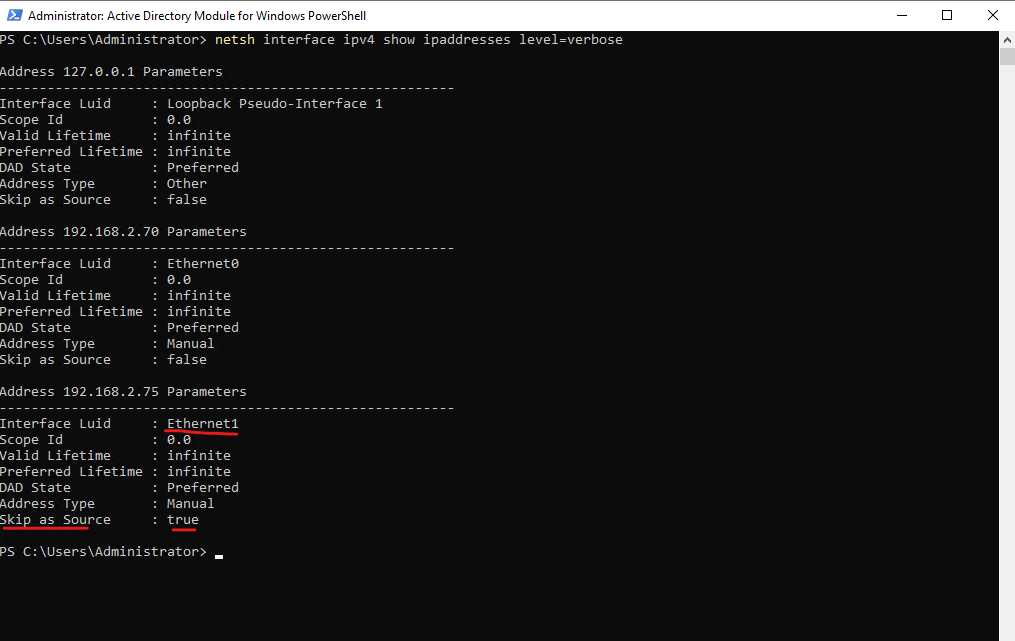
> netsh interface ipv4 show ipaddresses level=verbose
Configure DNS Policy for Split-Brain DNS in Active Directory
To add a new Active Directory integrated zone we can use either the DNS Manager or the following PowerShell cmdlet.
> Add-DnsServerPrimaryZone -Name "contoso.com" -ReplicationScope "Domain" -PassThru
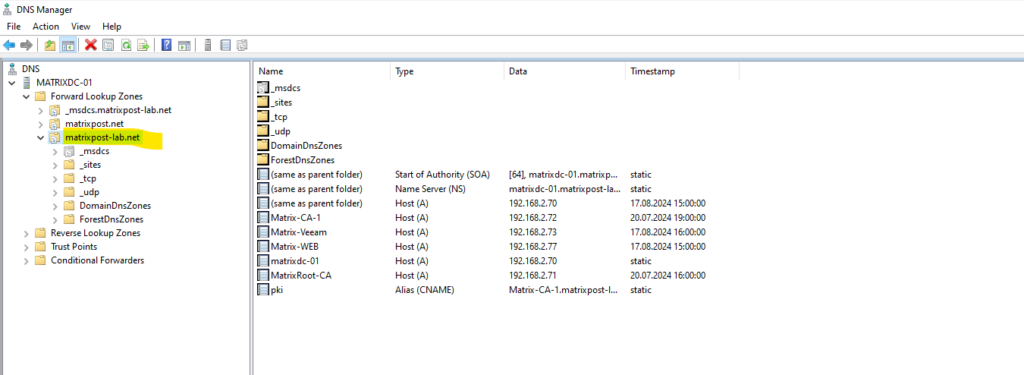
In my case I have already an existing Active Directory integrated zone for which I want to set up split-brain DNS.
Create the Scopes of the Zone
A zone scope is a unique instance of the zone. A DNS zone can have multiple zone scopes, with each zone scope containing its own set of DNS records. The same record can be present in multiple scopes, with different IP addresses or the same IP addresses.
Because you are adding this new zone scope in an Active Directory integrated zone, the zone scope and the records inside it will replicate via Active Directory to other replica servers in the domain.
By default a zone scope exists in every DNS zone. This zone scope has the same name as the zone itself and legacy DNS operations work on this scope.
So in my case the Active Directory DNS zone is matrixpost-lab.net, therefore also the zone scope is named matrixpost-lab.net.
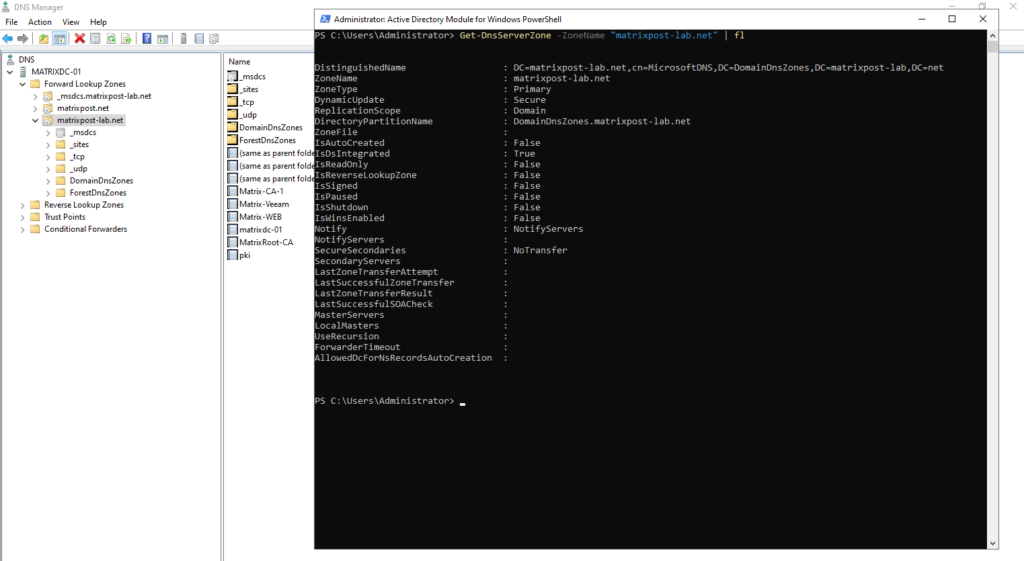
Get-DnsServerZoneScope -ZoneName "matrixpost-lab.net"
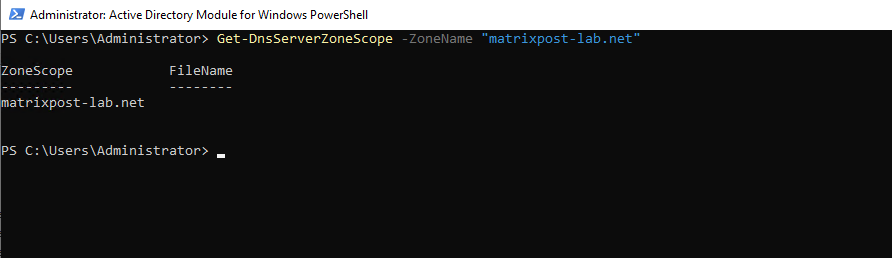
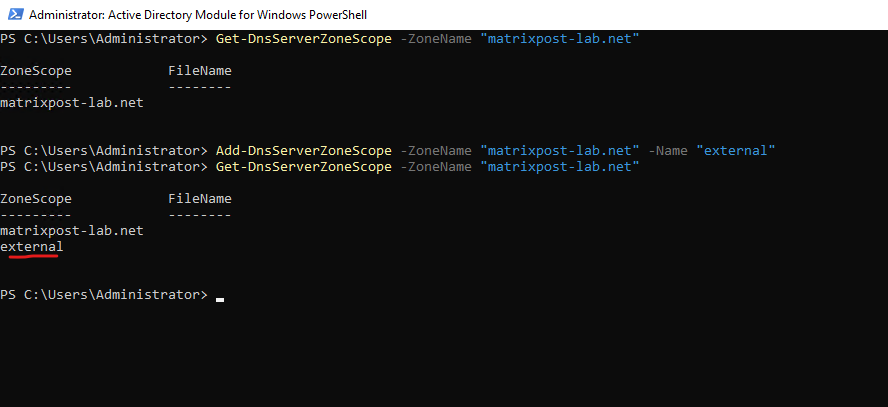
To create now a new zone scope on the DNS server which will include my external records we can use the following PowerShell cmdlet.
> Add-DnsServerZoneScope -ZoneName "matrixpost-lab.net" -Name "external"
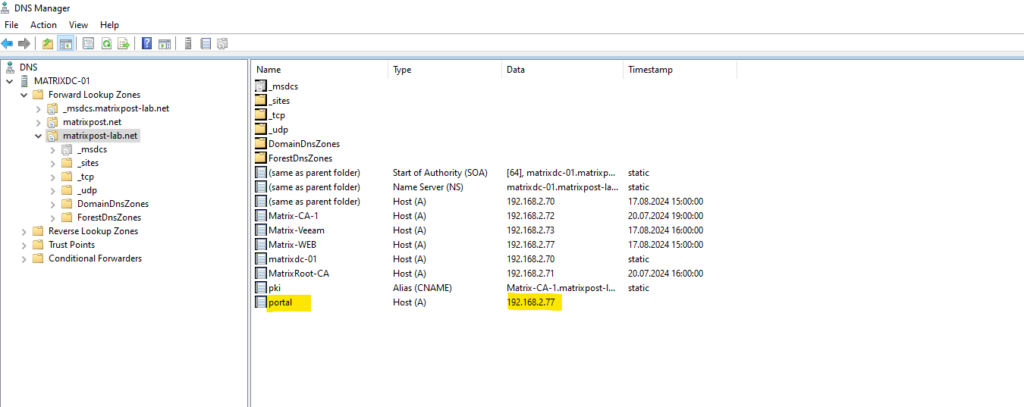
Add Records to the Zone Scopes
The next step is to add the records representing the web server host into the two zone scopes – external and default (for internal clients).
The –ZoneScope parameter is not included when the record is added to the default zone scope. This action is same as adding records to a normal zone.
> Add-DnsServerResourceRecord -ZoneName "matrixpost-lab.net" -A -Name "portal" -IPv4Address "152.53.20.60" -ZoneScope "external" > Add-DnsServerResourceRecord -ZoneName "matrixpost-lab.net" -A -Name "portal" -IPv4Address "192.168.2.77”
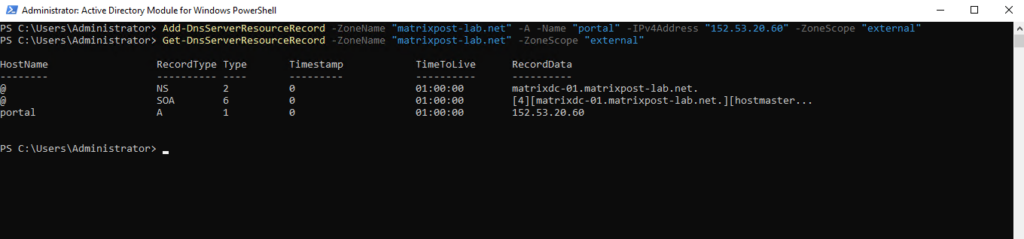
To remove records from a specific zone scope you can use the following PowerShell cmdlet.
> Remove-DnsServerResourceRecord -ZoneName "matrixpost-lab.net" -ZoneScope "external" -RRType "A" -Name "portal"
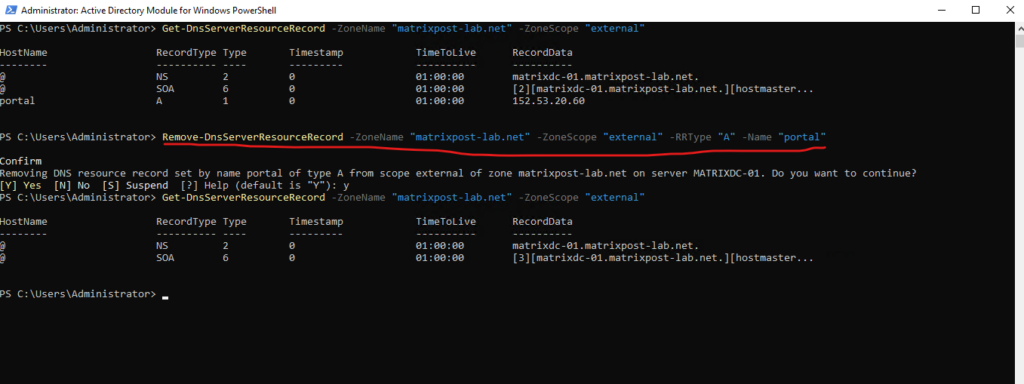
To remove a zone scope use the following cmdlet.
> Remove-DnsServerZoneScope -ZoneName "matrixpost-lab.net" -Name "external" -Force -PassThru
Create the DNS Policies
After you have identified the server interfaces for the external network and internal network and you have created the zone scopes, you must create DNS policies that connect the internal and external zone scopes.
Below I will also use the server interface parameter to to differentiate between internal and external clients. My internal interface is using the IP 192.168.2.70/24 and the external interface 192.168.2.75/24.
This example uses the server interface (the -ServerInterface parameter in the example command below) as the criteria to differentiate between the internal and external clients. Another method to differentiate between external and internal clients is by using client subnets as a criteria.
If you can identify the subnets to which the internal clients belong, you can configure DNS policy to differentiate based on client subnet.
For information on how to configure traffic management using client subnet criteria, see Use DNS Policy for Geo-Location Based Traffic Management with Primary Servers.
After you configure policies, when a DNS query is received on the public interface, the answer is returned from the external scope of the zone.
No policies are required for mapping the default internal zone scope.
> Add-DnsServerQueryResolutionPolicy -Name "SplitBrainZonePolicy" -Action ALLOW -ServerInterface "eq,192.168.2.75" -ZoneScope "external,1" -ZoneName matrixpost-lab.net
192.168.2.75 is the IP address on the public network interface.
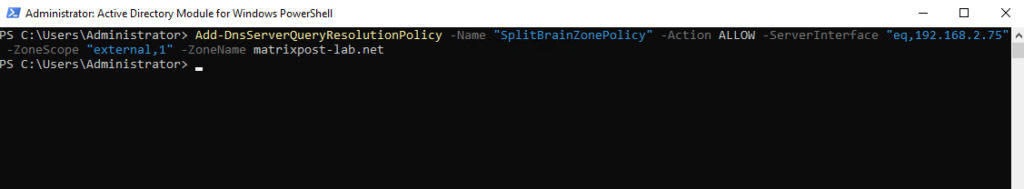
Now the DNS server is configured with the required DNS policies for a split-brain name server with an Active Directory integrated DNS zone.
You can create thousands of DNS policies according to your traffic management requirements, and all new policies are applied dynamically – without restarting the DNS server – on incoming queries.
To determine the policies for query resolution from a DNS server we can use the following cmdlet.
> Get-DnsServerQueryResolutionPolicy -ZoneName "matrixpost-lab.net" | fl
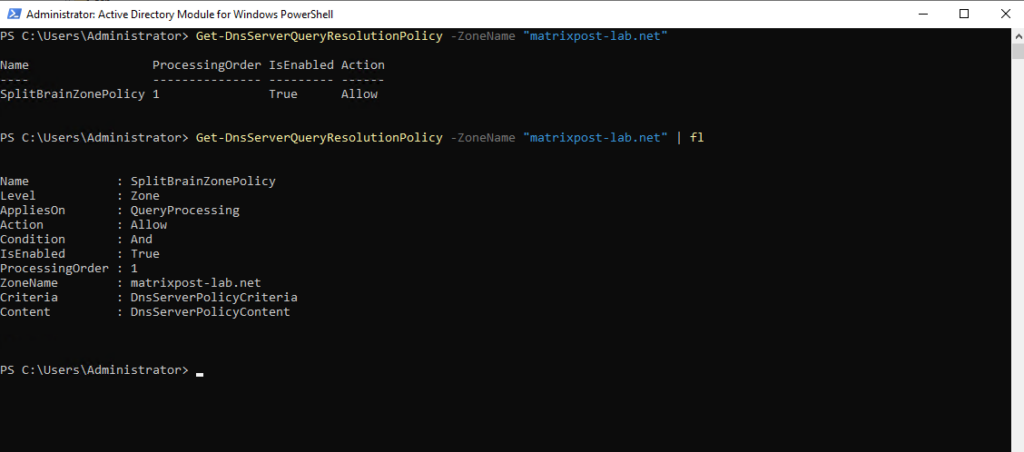
Testing Split-Brain DNS
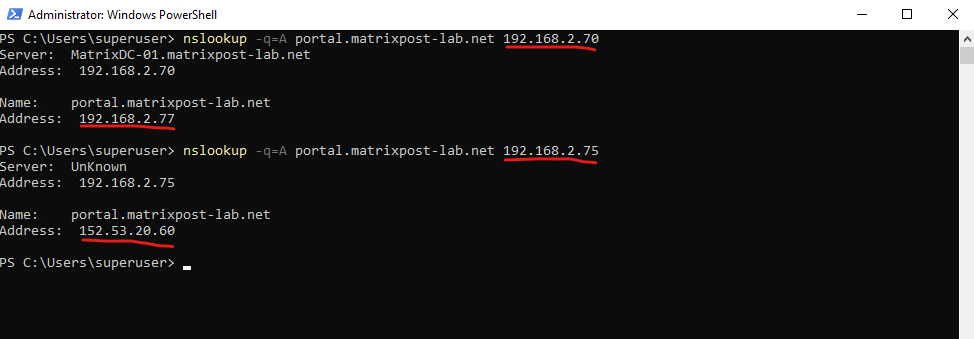
To test if split-brain DNS finally is working, in case of using previously the server interface parameter for the policy, we can here now just use the nslookup tool as shown below, I will first query here the internal interface with the IP 192.168.2.70 of the DNS server and then the external interface with the IP 192.168.2.75.
For the query on the external interface I will get correctly the public IP address back.
> nslookup -q=A portal.matrixpost-lab.net 192.168.2.70 > nslookup -q=A portal.matrixpost-lab.net 192.168.2.75
Links
Use DNS Policy for Split-Brain DNS in Active Directory
https://learn.microsoft.com/en-us/windows-server/networking/dns/deploy/dns-sb-with-adUse DNS Policy for Split-Brain DNS Deployment
https://learn.microsoft.com/en-us/windows-server/networking/dns/deploy/split-brain-dns-deploymentReviewing DNS Concepts
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/plan/reviewing-dns-conceptsAdd-DnsServerQueryResolutionPolicy
https://learn.microsoft.com/en-us/powershell/module/dnsserver/add-dnsserverqueryresolutionpolicy?view=windowsserver2022-psUse DNS Policy for Geo-Location Based Traffic Management with Primary Servers
https://learn.microsoft.com/en-us/windows-server/networking/dns/deploy/primary-geo-location


