Using Azure Key Vault for Passwords in Azure Bastion
Managing virtual machine access securely is a critical part of any Azure deployment. Azure Bastion provides a secure, browser-based RDP and SSH connection to your VMs without exposing them to the public internet.
By integrating Azure Key Vault, you can store and manage your VM passwords centrally, allowing Bastion to retrieve credentials on-demand. This approach eliminates the need to handle passwords manually, improves security, and streamlines access management for your team.
More about Azure Bastion and how to set up you will find in my following post.
Introduction
Azure Key Vault allows you to securely store service or application credentials like passwords and access keys as secrets. All secrets in your key vault are encrypted with a software key.
When you use Key Vault, you no longer need to store security information in your applications. Not having to store security information in applications eliminates the need to make this information part of the code.
Examples of secrets that should be stored in Key Vault:
- Client application secrets
- Connection strings
- Passwords
- Access keys (Redis Cache, Azure Event Hubs, Azure Cosmos DB)
- SSH keys
Any other sensitive information, like IP addresses, service names, and other configuration settings, should be stored in Azure App Configuration rather than in Key Vault.
Each individual key vault defines security boundaries for secrets. For a single key vault per application, per region, per environment, we recommend that you provide granular isolation of secrets for an application.
For more information about best practices for Key Vault, see Best practices to use Key Vault.
Create a Key Vault
To demonstrate using Azure Key Vault for passwords in Azure Bastion, I will create a new dedicated key vault therefore.
In the marketplace search for key vault and select the vault below.
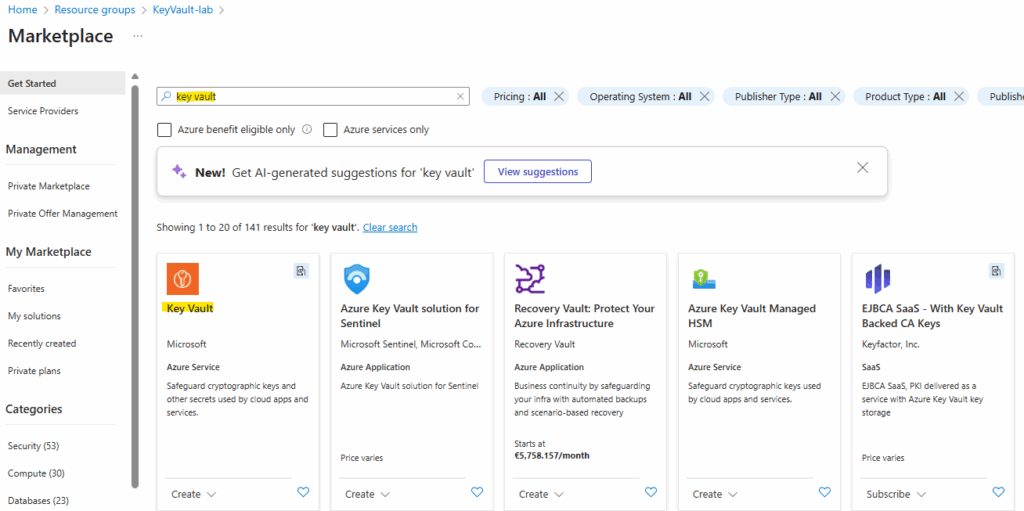
Azure Key Vault has two service tiers: Standard, which encrypts with a software key, and a Premium tier, which includes hardware security module(HSM)-protected keys.
Source: https://learn.microsoft.com/en-us/azure/key-vault/general/overview
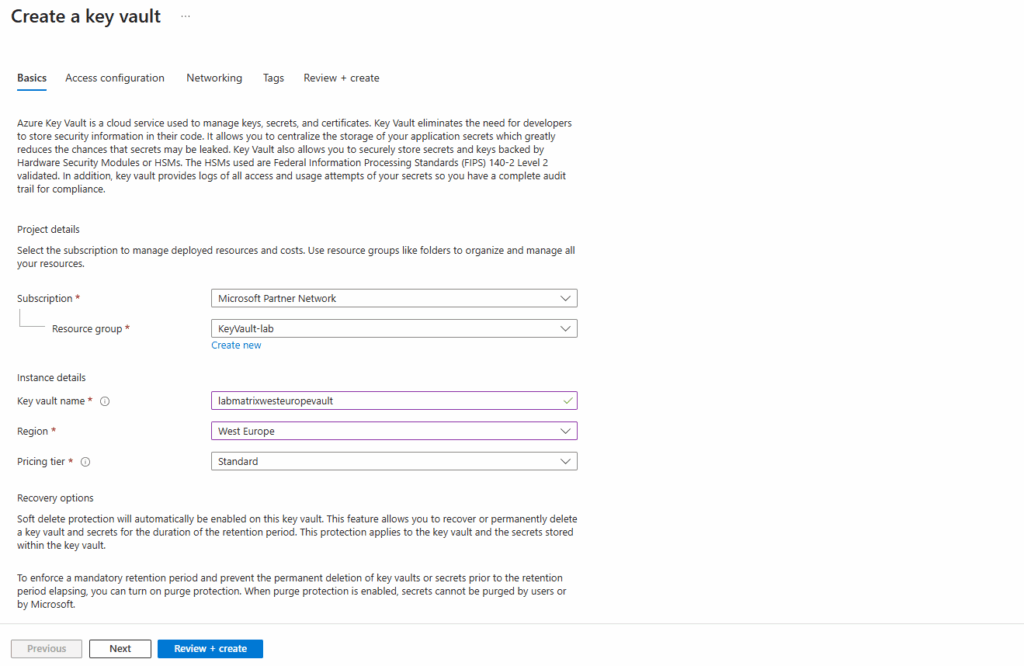
Soft delete protection will automatically be enabled on this key vault. This feature allows you to recover or permanently delete a key vault and secrets for the duration of the retention period. This protection applies to the key vault and the secrets stored within the key vault.
When purge protection is enabled, secrets cannot be purged by users or by Microsoft.
For the permission model I will use Azure role-based access control (default and recommended). We can also check which resources can access our key vault. I will allow all below.
For Azure Bastion we actually doesn’t need to check any of the resource access checkbox below. When using Azure Bastion with Key Vault passwords, Bastion retrieves the secret at runtime, not as part of a VM deployment.
For public access I will allow all networks.
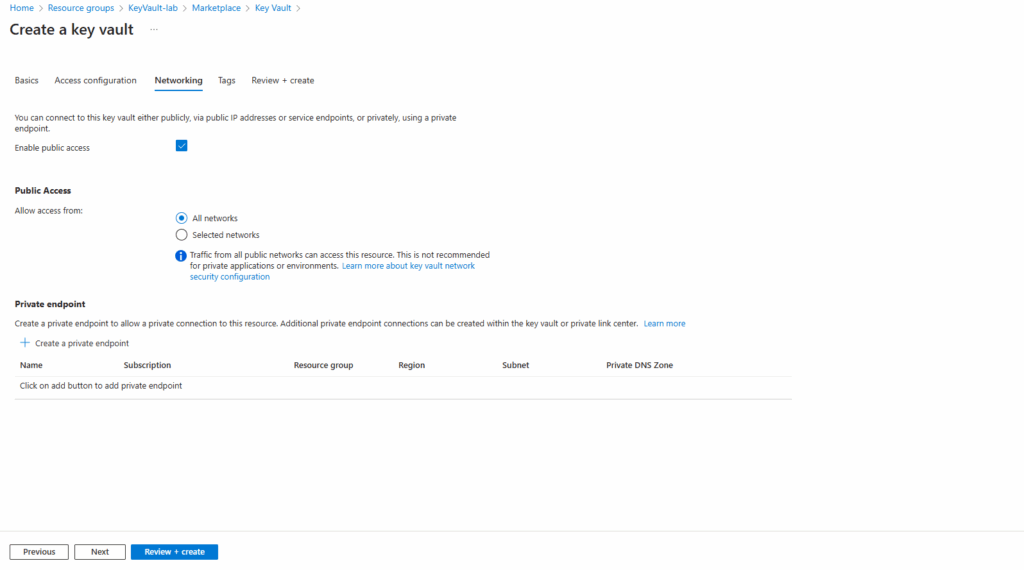
More about private endpoints and configuring DNS for, you will find in my following post.
Click on Create.
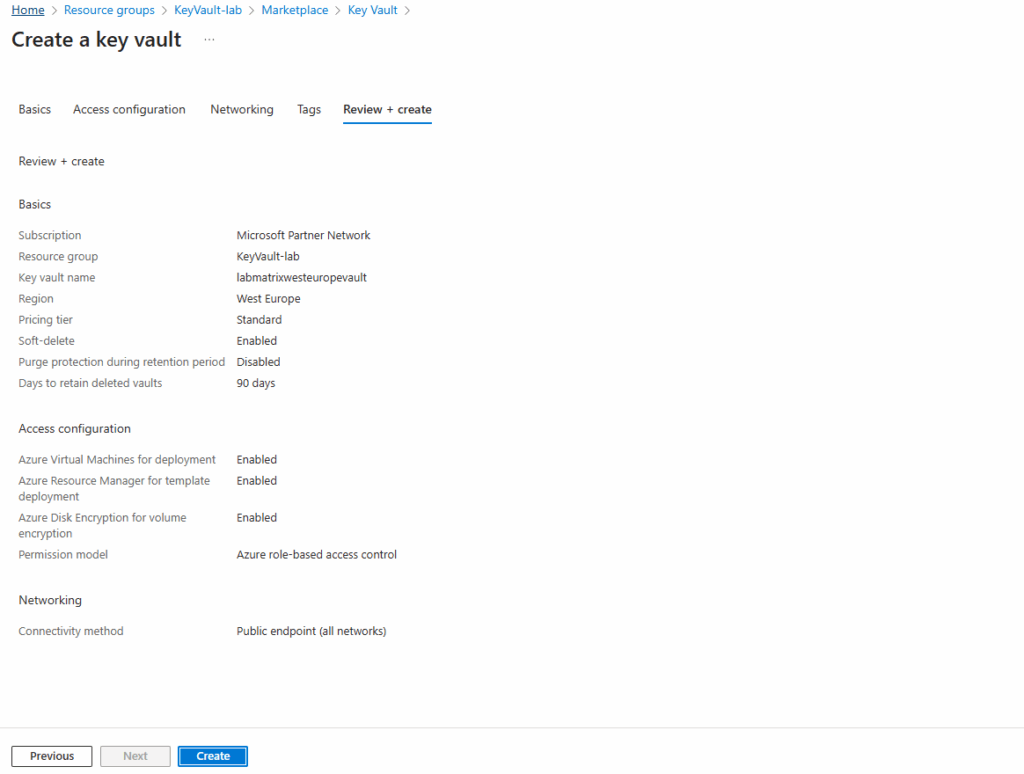
Our new key vault is successfully provisioned.
Create a Key (Password) for Azure Bastion Connections
Below I will store the password for a virtual machine’s local admin user to be later retrieved by Azure Bastion to connect to the virtual machine.
The username we want to use to connect to our virtual machine by using Azure Bastion, we later need to enter still manually.
So far directly after creating the new key vault, I haven’t the permissions to create a new secret.
The operation is not allowed by RBAC. If role assignments were recently changed, please wait several minutes for role assignments to become effective.
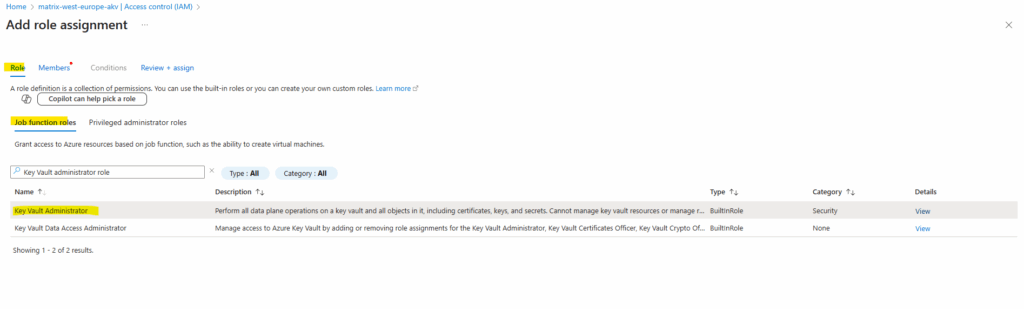
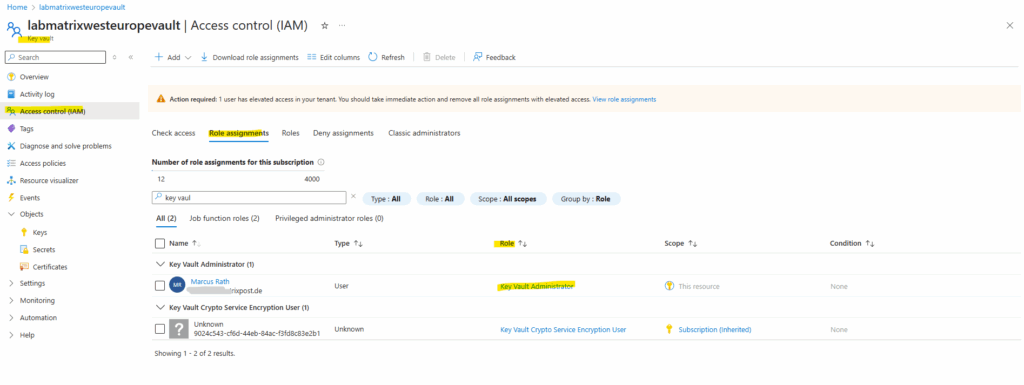
Even my user as owner permissions on the subscription, for the key vault we must assign dedicated the Key Vault administrator role as shown below
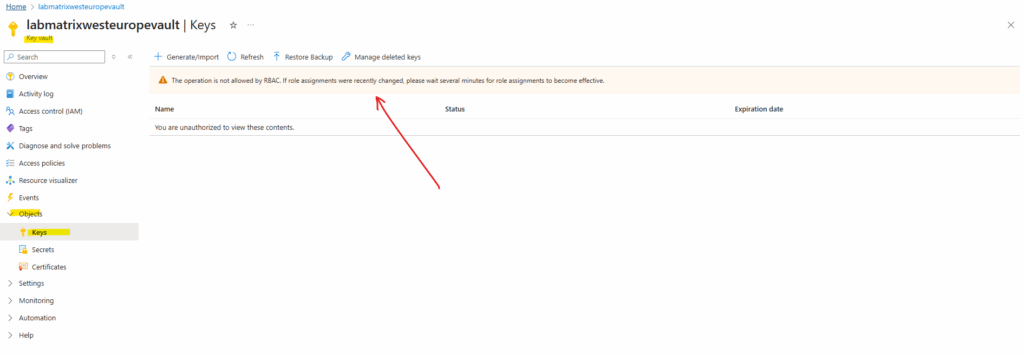
So we first need to assign the Key Vault administrator role to the user which wanted to create a new key.
To create a password secret, on the key vault navigate to Object -> Secrets.
Click on + Generate/Import
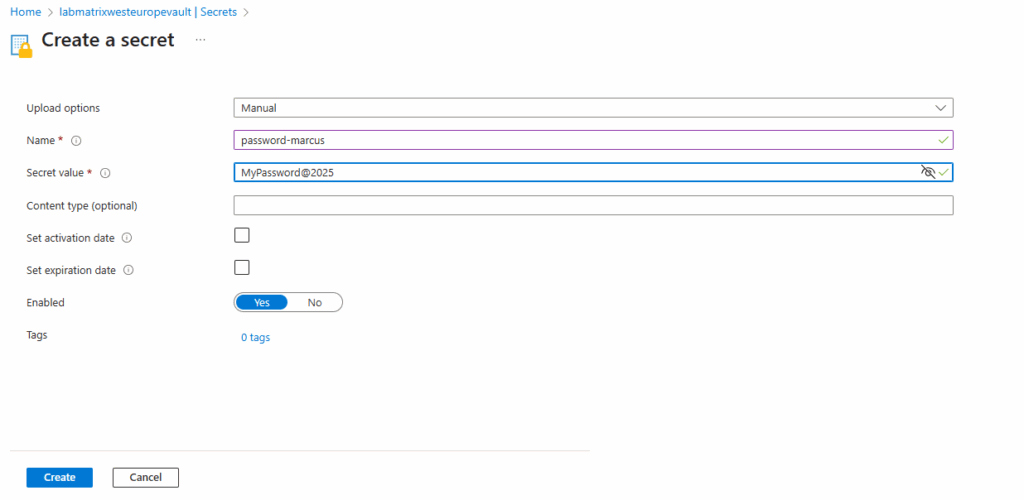
Enter a name for the new password and the password itself under Secret value. Just for demonstration purpose I will use the password here “MyPassword@2025”
I was also already creating a new virtual machine (W2K22) with the local admin user account “marcus”. For this already existing user account on the virtual machine, we now store the corresponding password in our new key vault which later will be retrieved by Azure Bastion at runtime to connect to.
The Activation Date (or “Enabled from” / “Not before”) checkbox in Azure Key Vault is optional. If you set an Activation Date, the secret will not be usable before that date/time. If you leave it blank, the secret is immediately active once created.
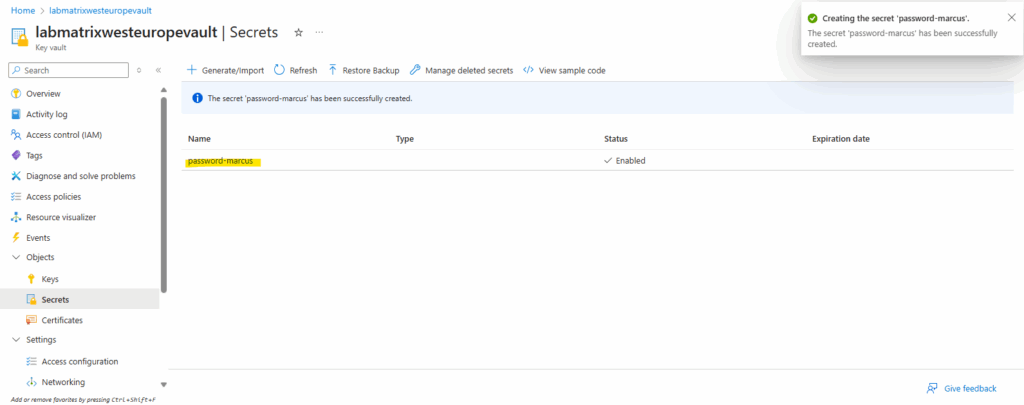
Use these Credentials for Azure Bastion RDP Access
We can now connect to our virtual machine by using the Connect -> Connect via Bastion link as usual.
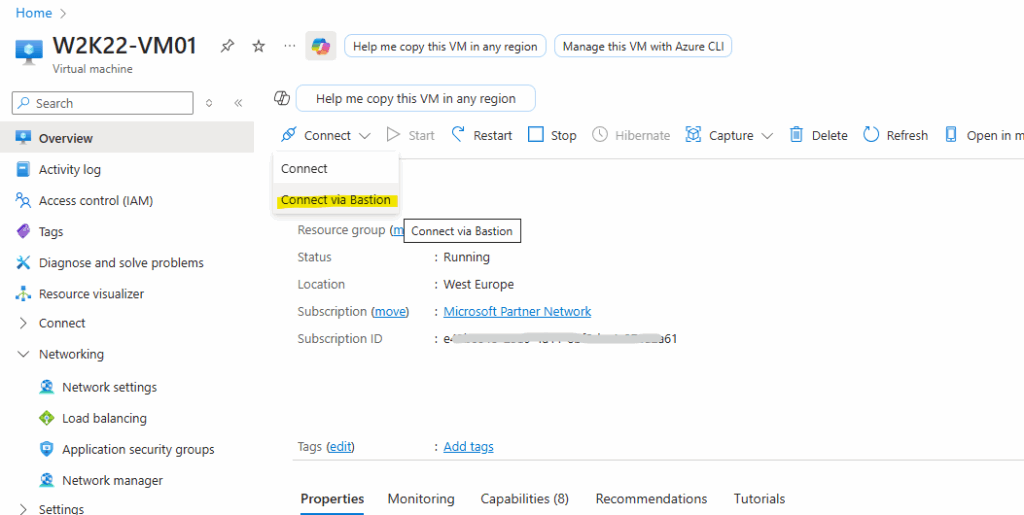
To authenticate to by retrieving the password from our key vault, we need to select below for the Authentication Type here Password from Azure Key Vault.
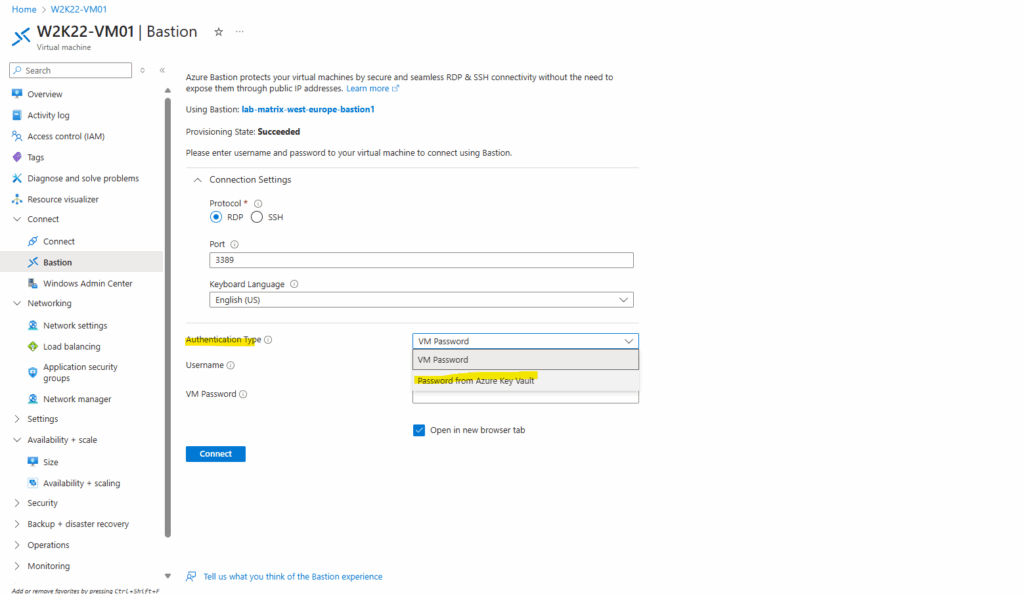
Enter the username (as mentioned the user “marcus” and its password “MyPassword@2025”, I was already set when creating the VM) and select the corresponding key vault we previously stored the password for the local admin user “marcus”.
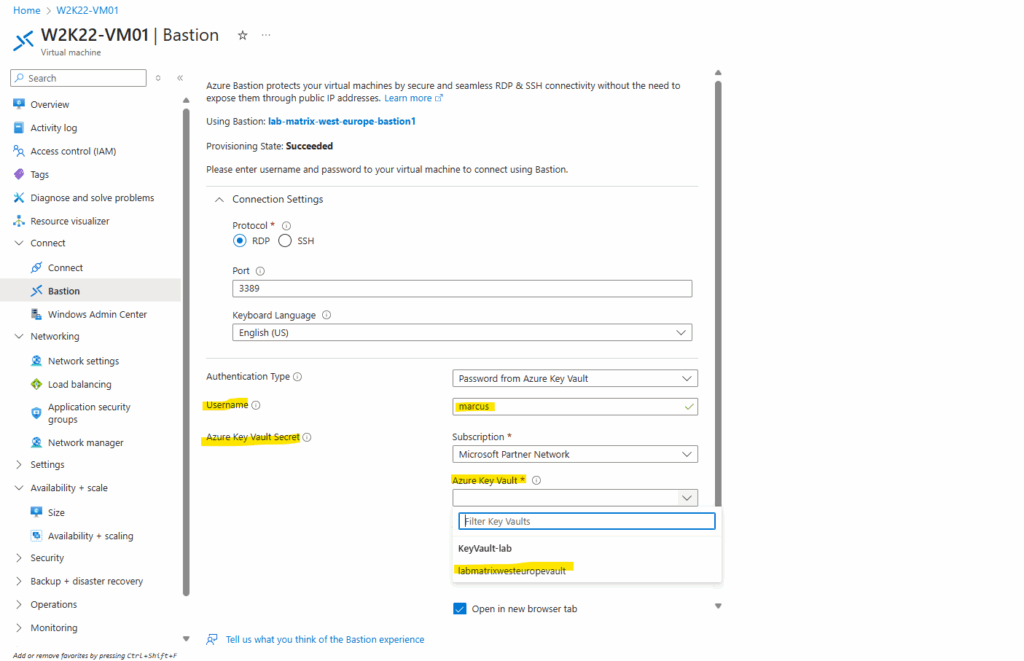
Select the key vault secret which finally stores our password for the local VM user “marcus“.
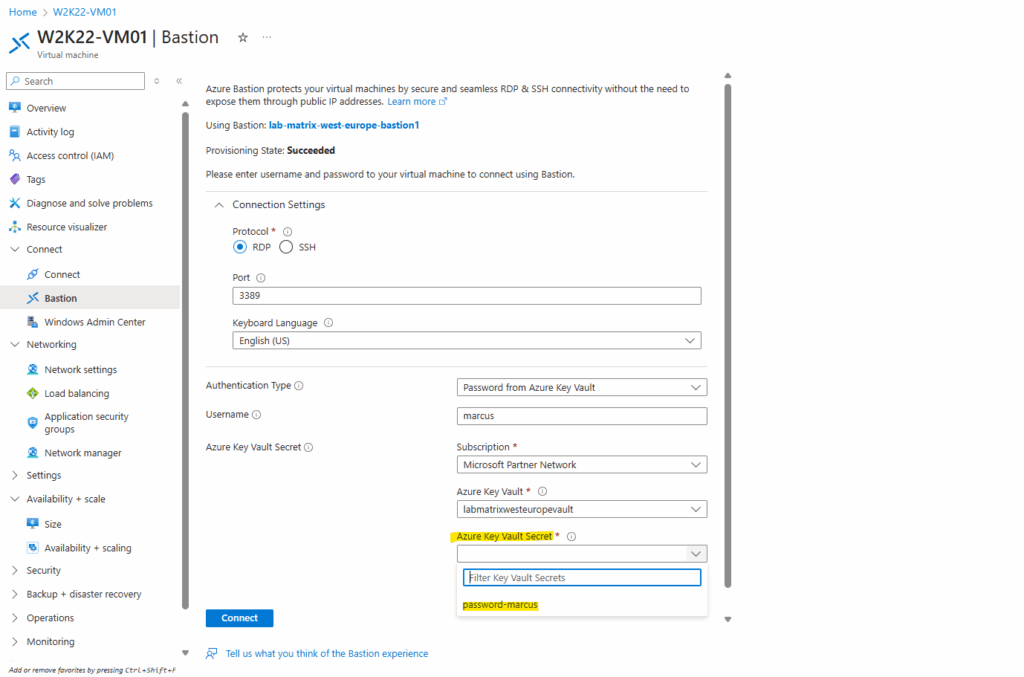
Finally click on Connect.
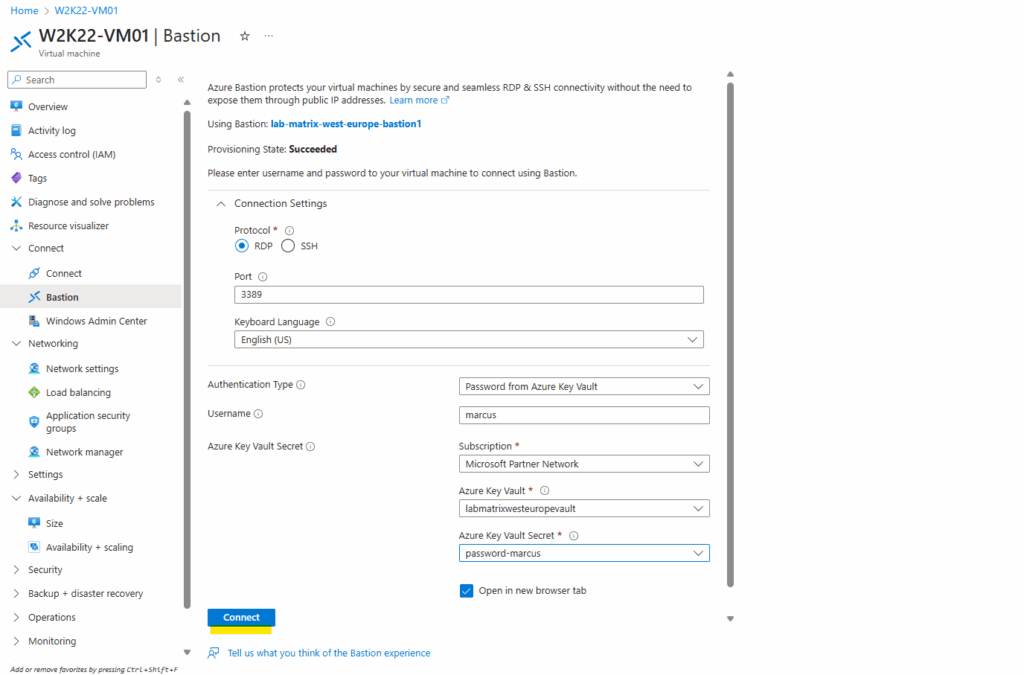
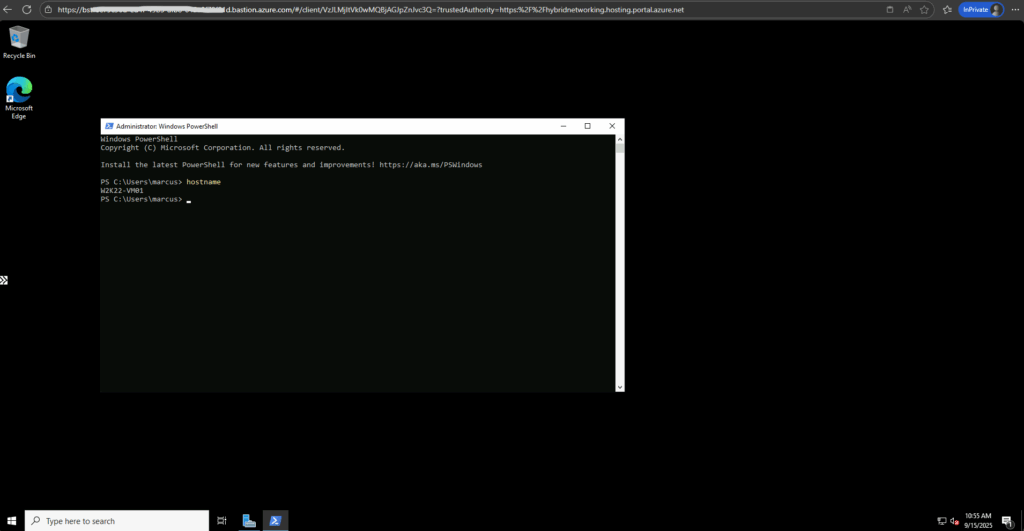
Looks good and works.
Links
Best practices for secrets management in Key Vault
https://learn.microsoft.com/en-us/azure/key-vault/secrets/secrets-best-practicesAuthentication in Azure Key Vault
https://learn.microsoft.com/en-us/azure/key-vault/general/authenticationAbout Azure Key Vault
https://learn.microsoft.com/en-us/azure/key-vault/general/overviewQuickstart: Set and retrieve a secret from Azure Key Vault using Azure CLI
https://learn.microsoft.com/en-us/azure/key-vault/secrets/quick-create-cli


