AWS – Organizations and Control Tower
In this post I just want to summarize some information about what is an organization and control tower in AWS. These topics are well documented in AWS.
First we will see what are AWS organizations?
AWS Organizations
AWS Organizations is an account management service that lets you consolidate multiple AWS accounts into an organization that you create and centrally manage. With Organizations, you can create member accounts and invite existing accounts to join your organization. You can organize those accounts into groups and attach policy-based controls.
Source: https://docs.aws.amazon.com/controltower/latest/userguide/organizations.html
AWS Organizations includes account management and consolidated billing capabilities that enable you to better meet the budgetary, security, and compliance needs of your business. As an administrator of an organization, you can create accounts in your organization and invite existing accounts to join the organization.
Source: https://docs.aws.amazon.com/organizations/latest/userguide/orgs_introduction.html
When you create a new single account it is automatically designated as the management account. When you now want to open as root user from this account the service AWS Organizations, you will see the following page where you first need to create an organization.
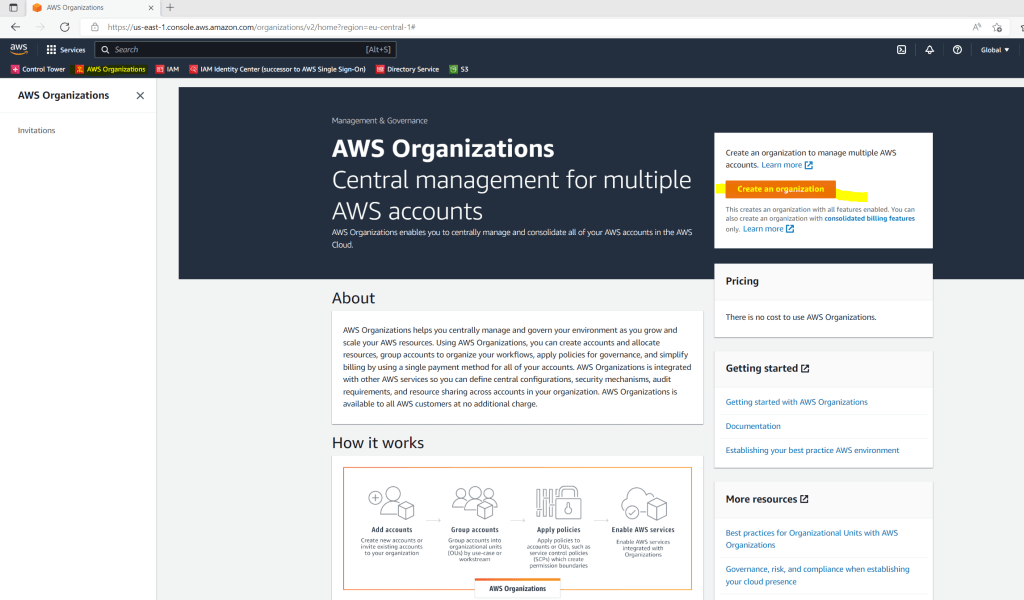
By creating an organization it will also create a root container for it.
The root container is the parent container for all the accounts for your organization. If you apply a policy to the root, it applies to all organizational units (OUs) and accounts in the organization.
Currently, you can have only one root. AWS Organizations automatically creates it for you when you create an organization.
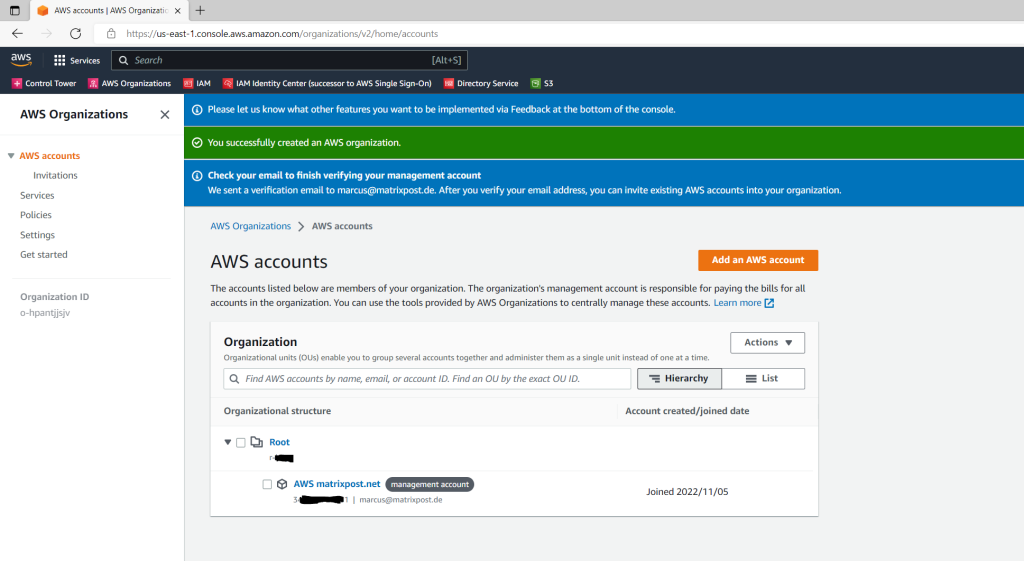
So far I just had one account which is by default the management account in AWS .
Best practices for the management account
https://docs.aws.amazon.com/organizations/latest/userguide/orgs_best-practices_mgmt-acct.html
We recommend that you use the management account and its users and roles only for tasks that can be performed only by that account. Store all of your AWS resources in other AWS accounts in the organization and keep them out of the management account. The one exception is that we do recommend that you enable AWS CloudTrail and keep relevant CloudTrail trails and logs in the management account.
One important reason to keep your resources in other accounts is because Organizations service control policies (SCPs) do not work to restrict any users or roles in the management account. The management account isn’t affected by any SCP. You can’t limit what users and roles in the management account can do by applying SCPs. SCPs affect only member accounts.
Separating your resources from your management account also help you to understand the charges on your invoices.
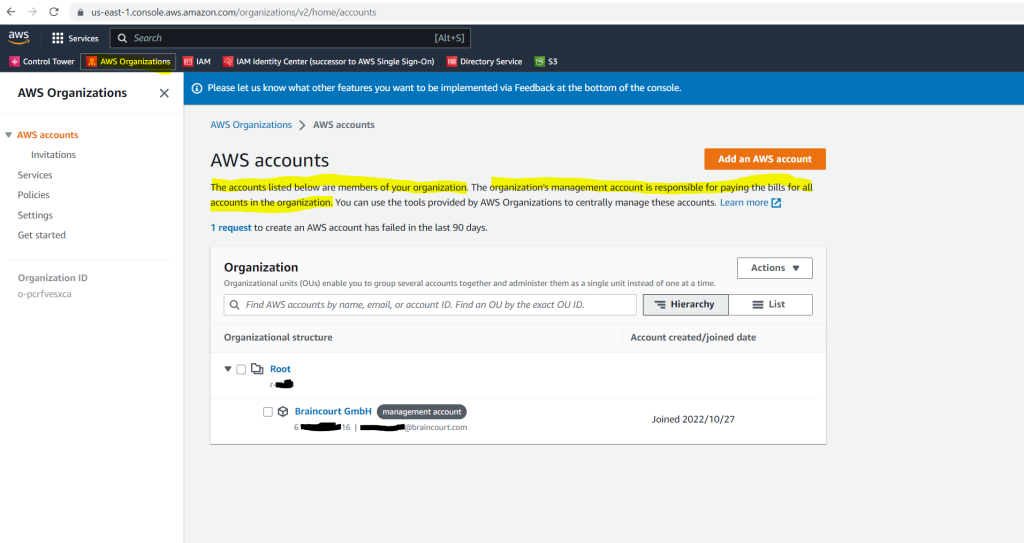
To test using AWS Organiziations I will add a further account named braintesting which is then a normal member account.
Root is the parent organizational unit (OU) for all accounts and other OUs in your organization. When you apply a policy to the root, it applies to every OU and account in the organization.
I will click here on Add an AWS account
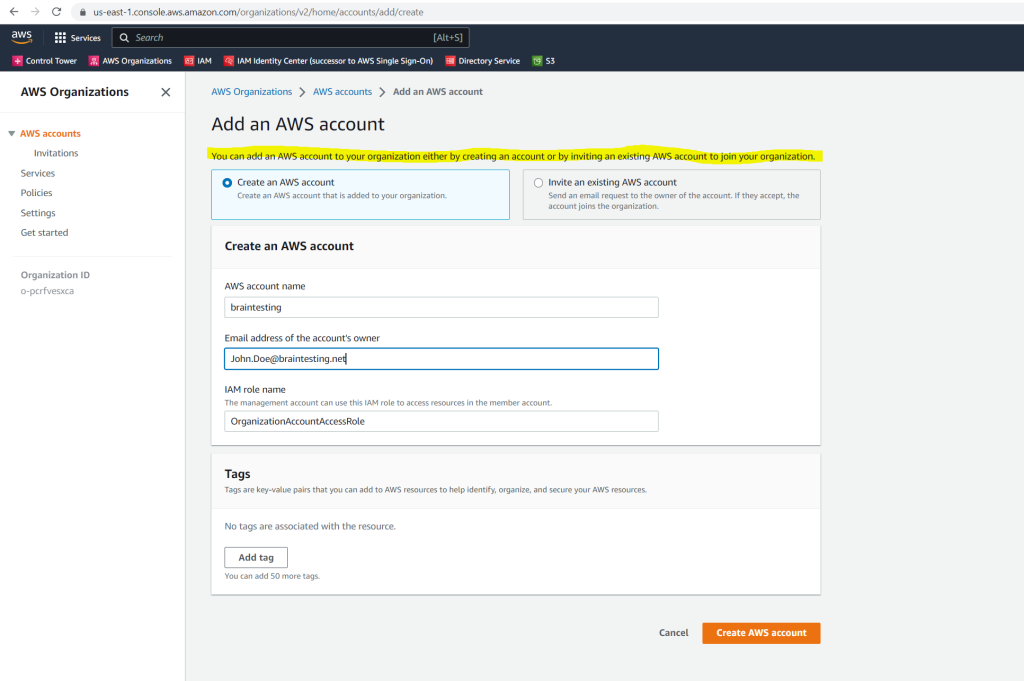
You can also add to your organization an existing AWS account, in my case I will create a new AWS account. For the account owner I will using a testuser from my on-premise and Microsoft Azure Cloud network.
By default, if you create a member account as part of your organization, AWS automatically creates a role in the account that grants administrator permissions to IAM users in the management account who can assume the role. By default, that role is named OrganizationAccountAccessRole. For more information, see Accessing a member account that has a management account access role.
After creating the account, the account owner will get an email like shown below.

So from now on at AWS Organizations I had two accounts, the management account and one member account (braintesting).
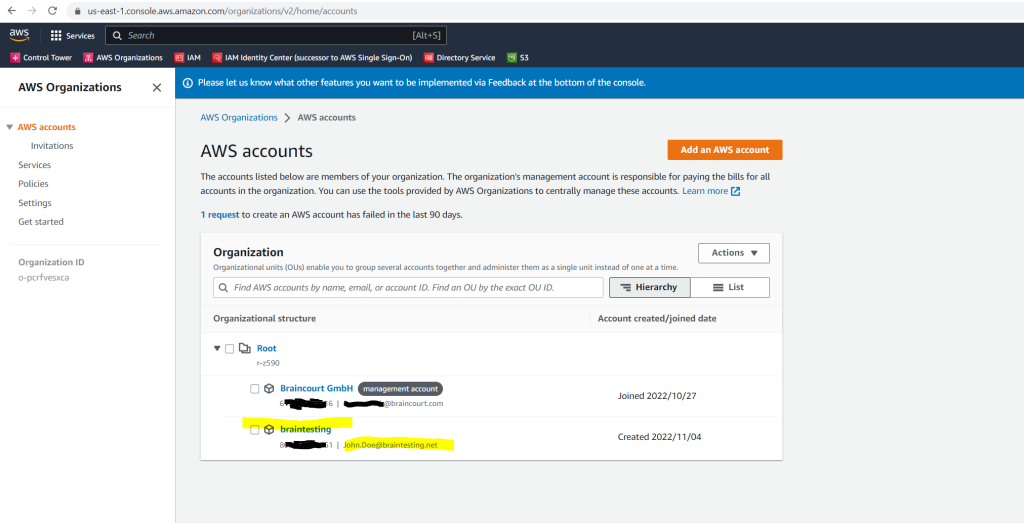
So first I will create two new OUs to put the accounts in, one for production accounts and one for testing accounts (LAB environments).
By doing this I can apply different policies to each of them.
Regarding the previously further above mentioned best practices for the management account, you may also want to create a separate OU just for the management account.
Best practices for the management account
https://docs.aws.amazon.com/organizations/latest/userguide/orgs_best-practices_mgmt-acct.html
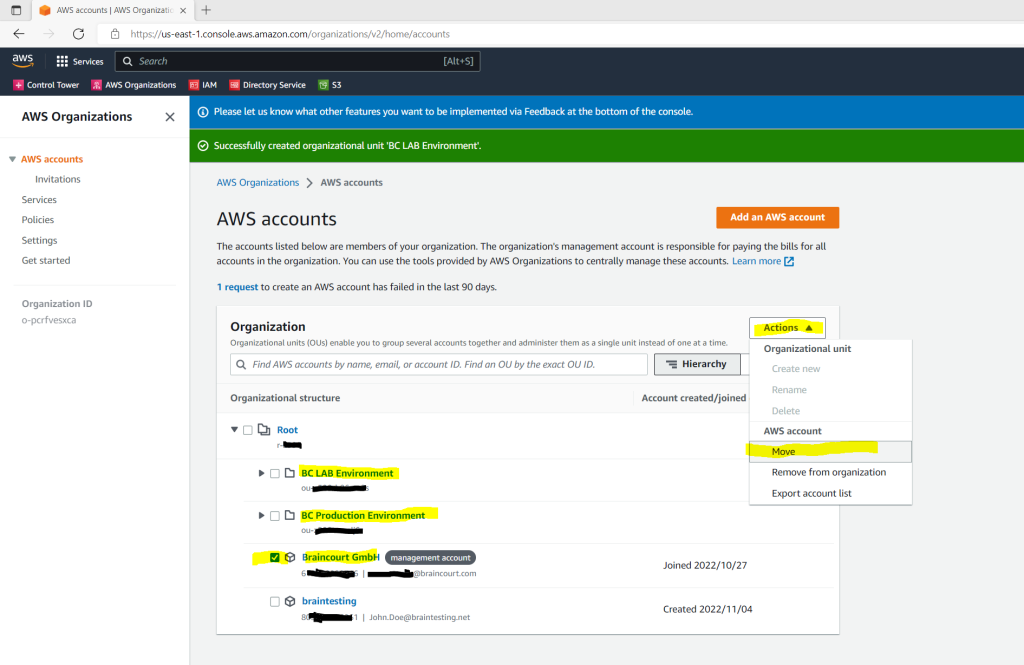
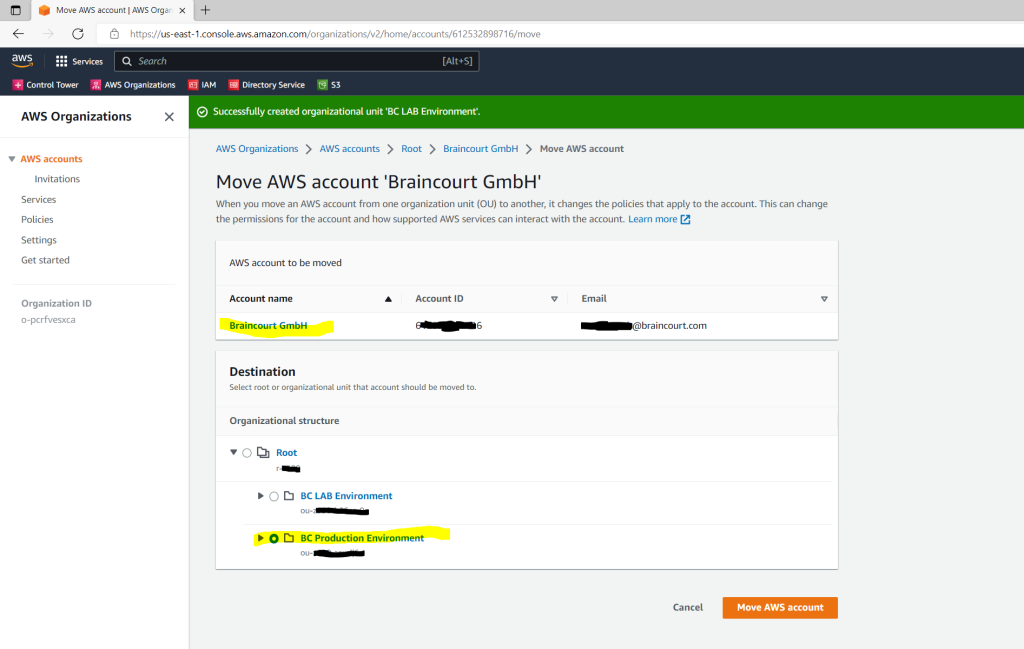
Finally my organization hierarchy will looks like this.
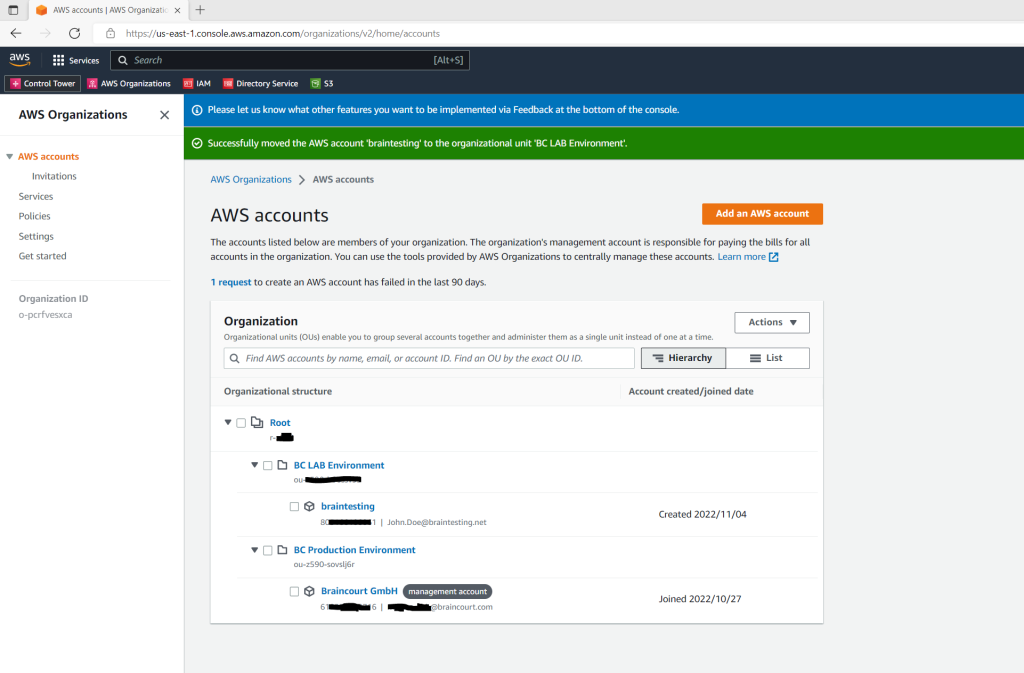
Back to the newly created member account.
How can I now access this member account as the root user john.doe@braintesting.net now?
When you create a new account, AWS Organizations initially assigns a password to the root user that is a minimum of 64 characters long. All characters are randomly generated with no guarantees on the appearance of certain character sets. You can’t retrieve this initial password. To access the account as the root user for the first time, you must go through the process for password recovery.
To request a new password for the root user of the member account
Go to the Sign in page of the AWS console at https://console.aws.amazon.com/
If the Sign in page shows three text boxes for Account ID or alias, IAM user name, and Password, choose Sign in using root account credentials.
Here I will enter the email address from the member account owner I set previoulsy.
Choose Forgot your password?
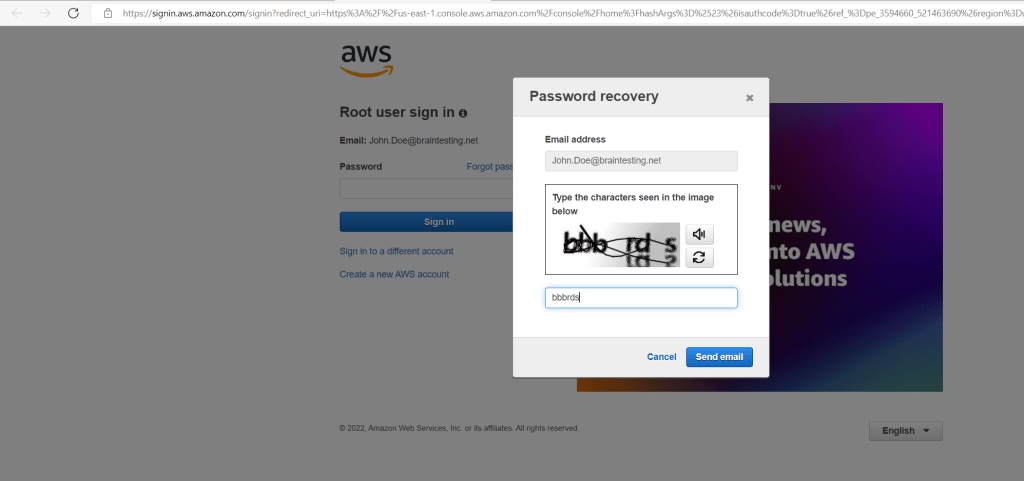
Enter the information that is required to reset the password to a new one that you provide. To do this, you must be able to access incoming mail sent to the email address that is associated with the account.
In the email you can click on the provided link to reset the password.
AWS Organizations terminology and concepts
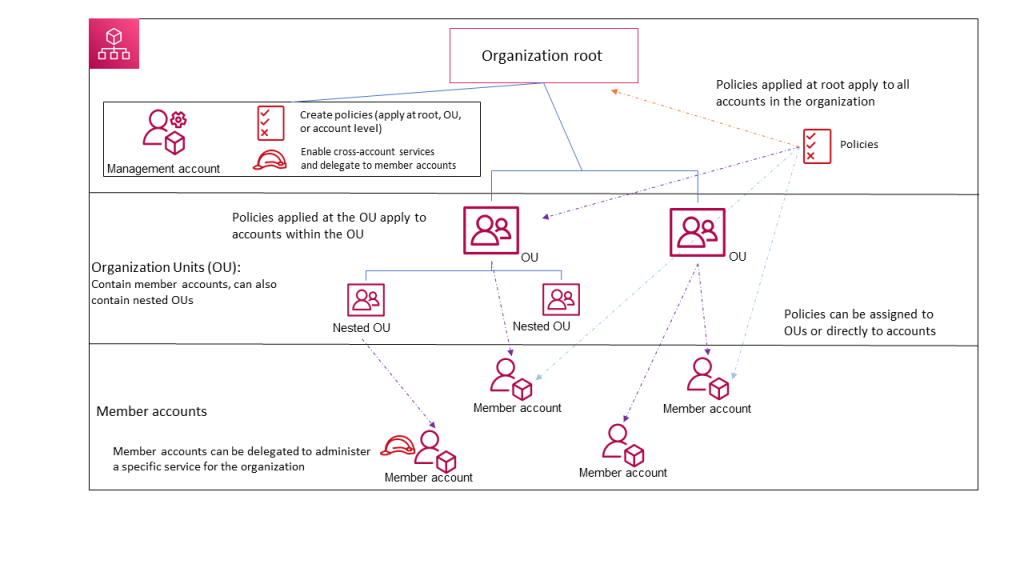
The following diagram shows a basic organization that consists of five accounts that are organized into four organizational units (OUs) under the root. The organization also has several policies that are attached to some of the OUs or directly to accounts. For a description of each of these items, refer to the definitions in this topic.
Source: https://docs.aws.amazon.com/organizations/latest/userguide/orgs_getting-started_concepts.html
Organization
An entity that you create to consolidate your AWS accounts so that you can administer them as a single unit. You can use the AWS Organizations console to centrally view and manage all of your accounts within your organization. An organization has one management account along with zero or more member accounts. You can organize the accounts in a hierarchical, tree-like structure with a root at the top and organizational units nested under the root. Each account can be directly in the root, or placed in one of the OUs in the hierarchy. An organization has the functionality that is determined by the feature set that you enable.
Root
The parent container for all the accounts for your organization. If you apply a policy to the root, it applies to all organizational units (OUs) and accounts in the organization.
Currently, you can have only one root. AWS Organizations automatically creates it for you when you create an organization.
Organizational unit (OU)
A container for accounts within a root. An OU also can contain other OUs, enabling you to create a hierarchy that resembles an upside-down tree, with a root at the top and branches of OUs that reach down, ending in accounts that are the leaves of the tree. When you attach a policy to one of the nodes in the hierarchy, it flows down and affects all the branches (OUs) and leaves (accounts) beneath it. An OU can have exactly one parent, and currently each account can be a member of exactly one OU.
Account
An account in Organizations is a standard AWS account that contains your AWS resources and the identities that can access those resources.
An AWS account isn’t the same thing as a user account. An AWS user is an identity that you create using AWS Identity and Access Management (IAM) and takes the form of either an IAM user with long-term credentials, or an IAM role with short-term credentials. A single AWS account can, and typically does contain many users and roles.
There are two types of accounts in an organization: a single account that is designated as the management account, and one or more member accounts.
- The management account is the account that you use to create the organization. From the organization’s management account, you can do the following:
- Create accounts in the organization
- Invite other existing accounts to the organization
- Remove accounts from the organization
- Manage invitations
- Apply policies to entities (roots, OUs, or accounts) within the organization
- Enable integration with supported AWS services to provide service functionality across all of the accounts in the organization.
- Member accounts make up all of the rest of the accounts in an organization. An account can be a member of only one organization at a time. You can attach a policy to an account to apply controls to only that one account.
More about at https://docs.aws.amazon.com/organizations/latest/userguide/orgs_getting-started_concepts.html
AWS Organization Feature Sets
AWS Organizations has two available feature sets:
- All features – This feature set is the preferred way to work with AWS Organizations, and it includes Consolidating Billing features. When you create an organization, enabling all features is the default. With all features enabled, you can use the advanced account management features available in AWS Organizations such as integration with supported AWS services and organization management policies.
- Consolidated Billing features – All organizations support this subset of features, which provides basic management tools that you can use to centrally manage the accounts in your organization.
If you create an organization with consolidated billing features only, you can later enable all features.
Source: https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_org_support-all-features.html
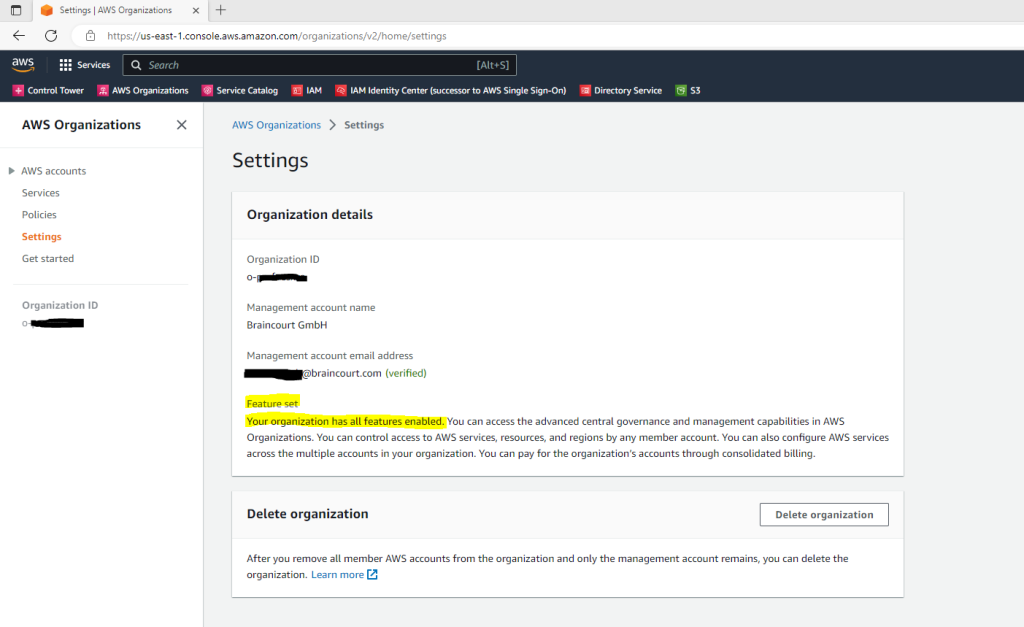
At the AWS Organizations page under Settings you can check if All features is enabled, if not you can also enable it here.
Control Tower
Now we want see what is the AWS Control Tower?
You can use AWS Control Tower to set up a multi-account environment in AWS within a few clicks.
AWS Control Tower is orchestrating the capabilities of several other AWS services, including AWS Organizations, AWS Service Catalog, and AWS IAM Identity Center (successor to AWS Single Sign-On), to build a landing zone in less than an hour.
Orchestrating AWS Control Tower extends the capabilities of AWS Organizations
To prevent your organizations and accounts from drifting, which deviates from best practices, AWS Control Tower applies preventive and detective controls (guardrails). For example, you can use guardrails to ensure that security protocols and required cross-account access permissions are created, not changed.
If you host more than a handful of accounts, it’s beneficial to have an orchestration layer that makes account provisioning and management easier. You can use AWS Control Tower as the primary method of provisioning accounts and infrastructure. AWS Control Tower makes it easier to comply with corporate standards, meet regulatory requirements, and follow best practices.
In short, AWS Control Tower offers the easiest way to set up and govern a secure, compliant, multi-account AWS environment based on best practices established by working with thousands of enterprises.
AWS Control Tower has the following features:
- Landing zone – A landing zone is a well-architected, multi-account environment that’s based on security and compliance best practices. It is the enterprise-wide container that holds all of your organizational units (OUs), accounts, users, and other resources that you want to be subject to compliance regulation. A landing zone can scale to fit the needs of an enterprise of any size.
- Controls – A control (sometimes called a guardrail) is a high-level rule that provides ongoing governance for your overall AWS environment. It’s expressed in plain language. Two kinds of controls exist: preventive and detective. Three categories of guidance apply to the two kinds of controls: mandatory, strongly recommended, or elective. For more information about controls, see How Controls Work.
- Account Factory – An Account Factory is a configurable account template that helps to standardize the provisioning of new accounts with pre-approved account configurations. AWS Control Tower offers a built-in Account Factory that helps automate the account provisioning workflow in your organization. For more information, see Provision and manage accounts with Account Factory.
- Dashboard – The dashboard offers continuous oversight of your landing zone to your team of central cloud administrators. Use the dashboard to see provisioned accounts across your enterprise, controls enabled for policy enforcement, controls enabled for continuous detection of policy non-conformance, and noncompliant resources organized by accounts and OUs.
Source: https://docs.aws.amazon.com/de_de/controltower/latest/userguide/what-is-control-tower.html
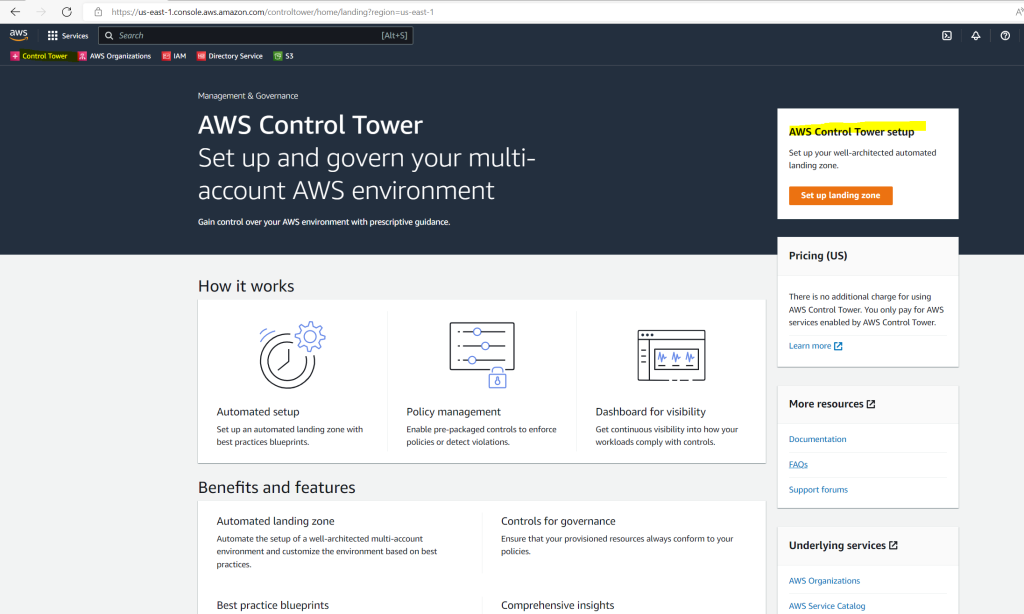
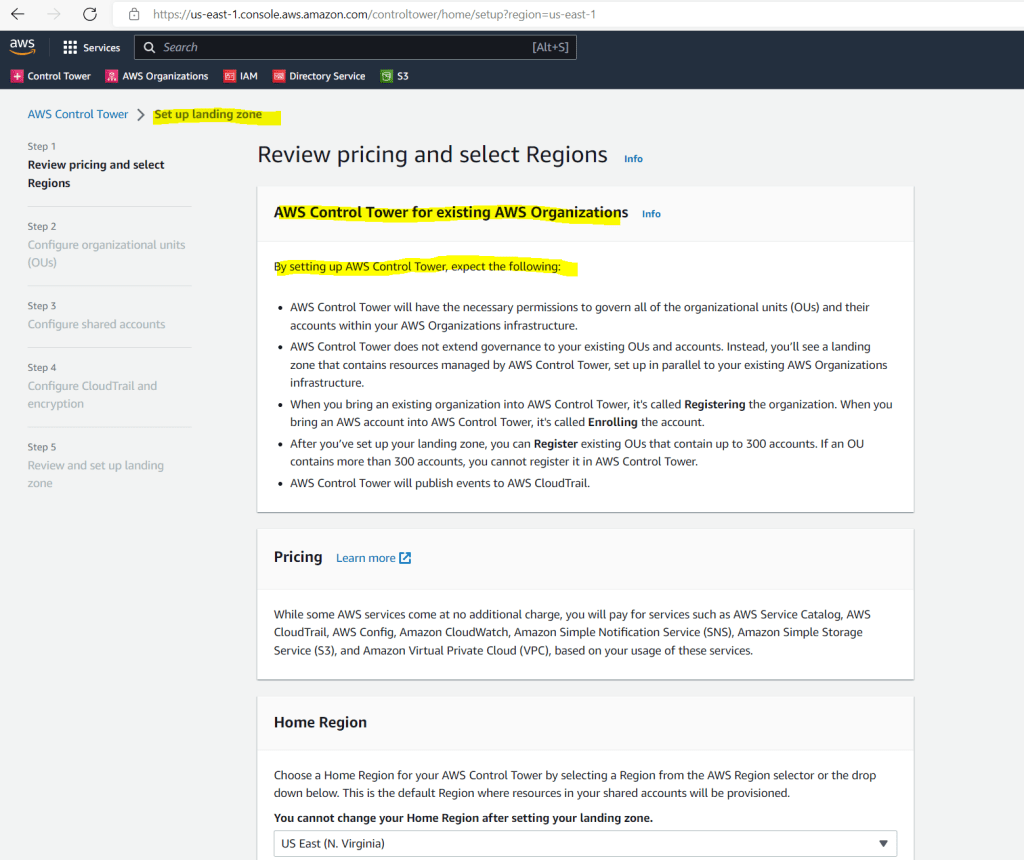
By opening the first time the control tower, we see the following page where we first need to set up a landing zone.
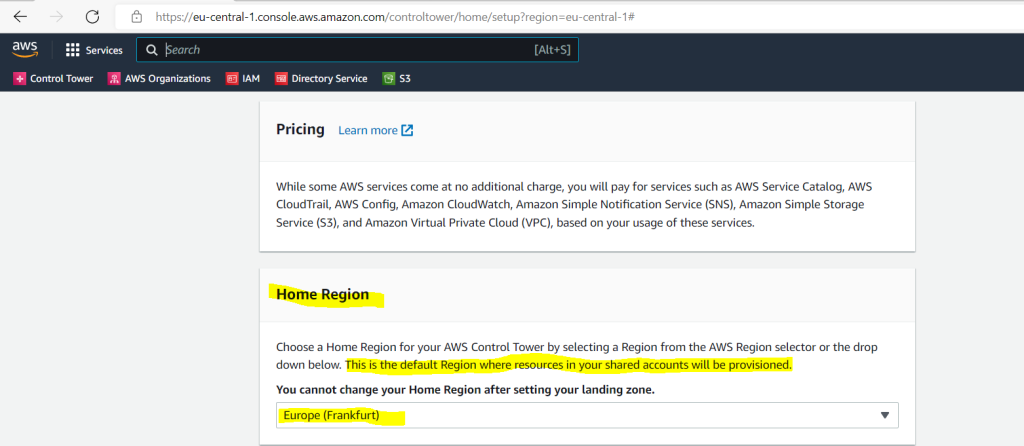
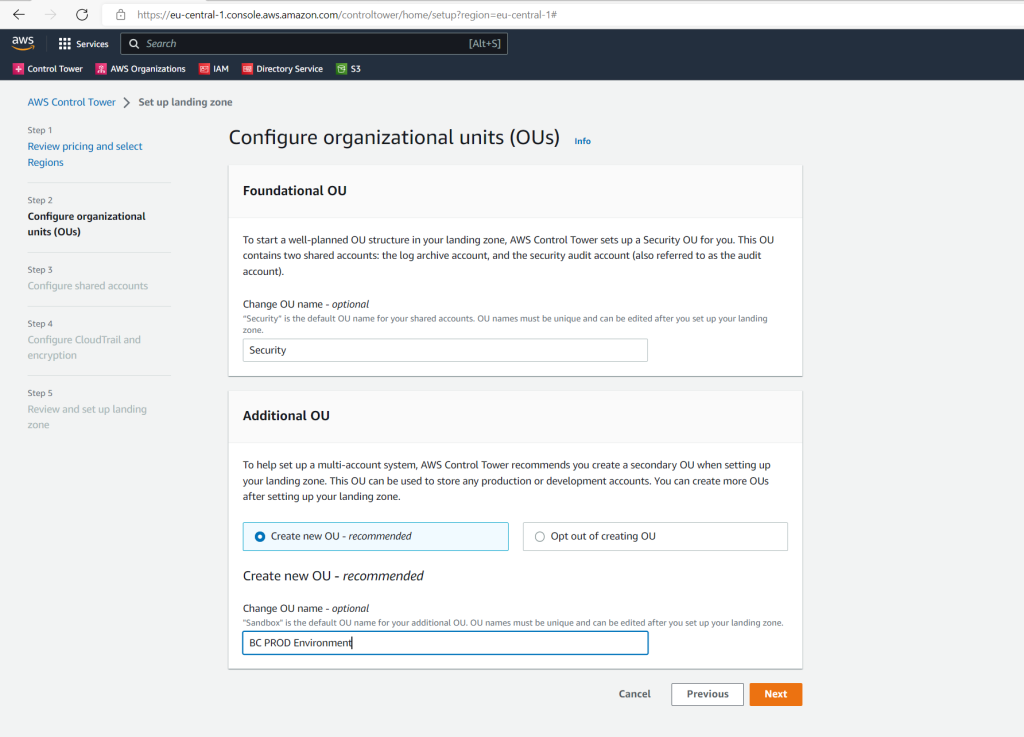
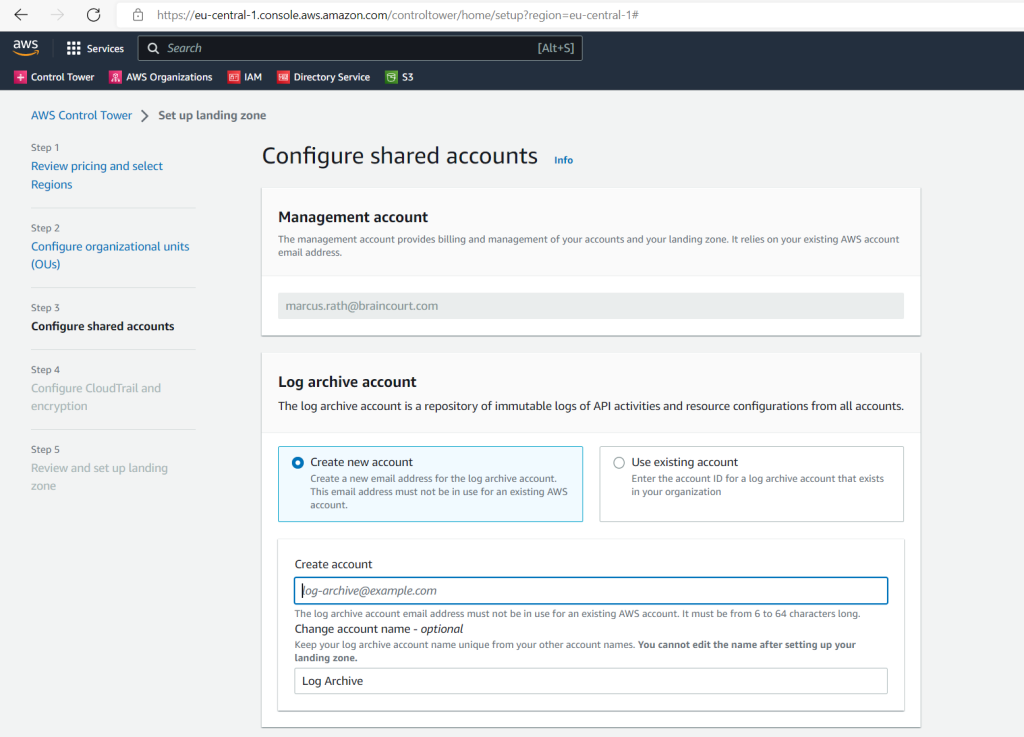
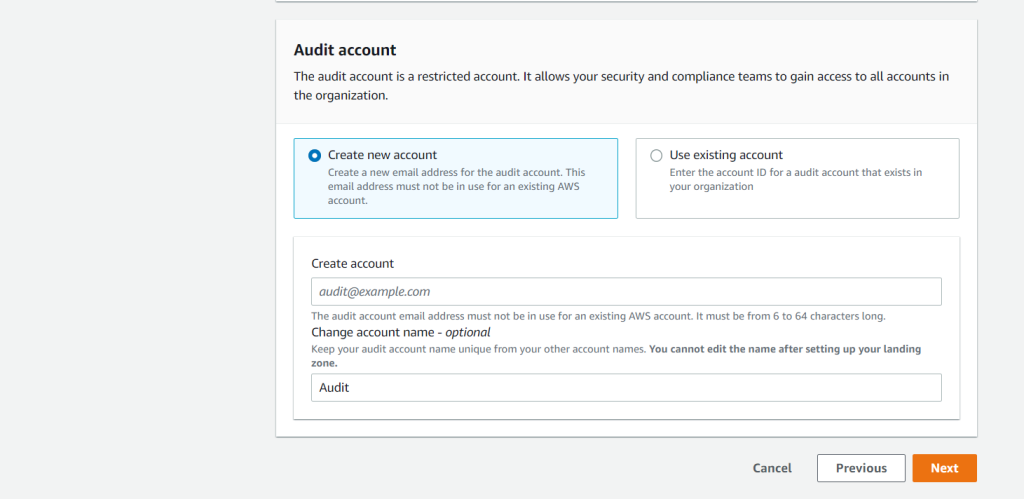
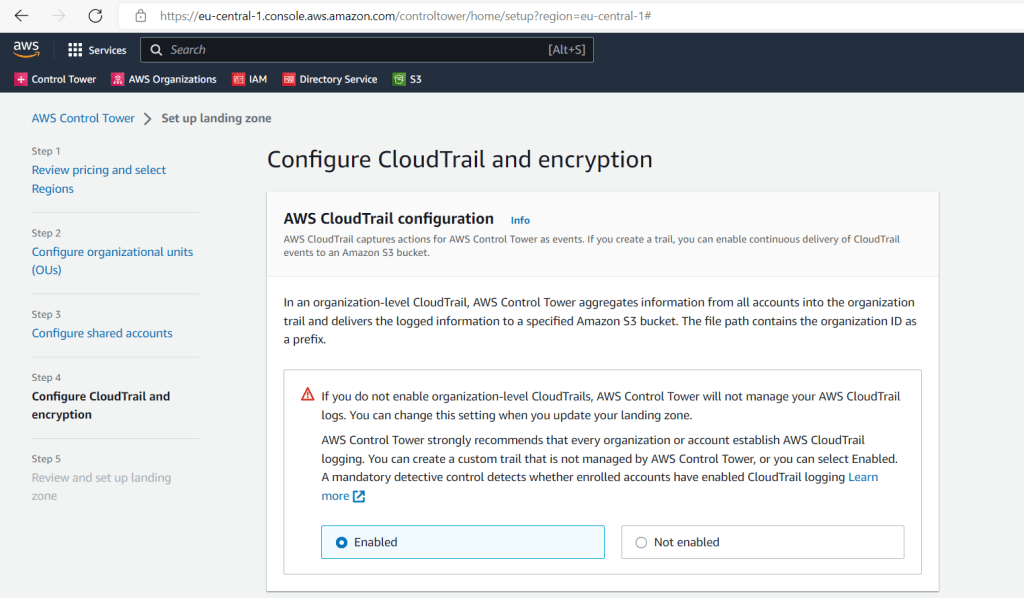
The KMS key must have permissions for AWS CloudTrail and AWS Config. Multi-region keys are not supported.
You can copy and paste the following example policy statement. Alternatively, for an existing key, you can ensure that your KMS key has these minimum permissions by adding them to your own existing policy. You can add these lines as a group in a single JSON statement, or if you prefer, you can incorporate them line by line into your policy’s other statements.
{
"Sid": "Allow CloudTrail and AWS Config to encrypt/decrypt logs",
"Effect": "Allow",
"Principal": {
"Service": [
"cloudtrail.amazonaws.com",
"config.amazonaws.com"
]
},
"Action": [
"kms:GenerateDataKey",
"kms:Decrypt"
],
"Resource": "*"
}Optionally configure AWS KMS keys
https://docs.aws.amazon.com/controltower/latest/userguide/configure-kms-keys.html#kms-key-policy-update
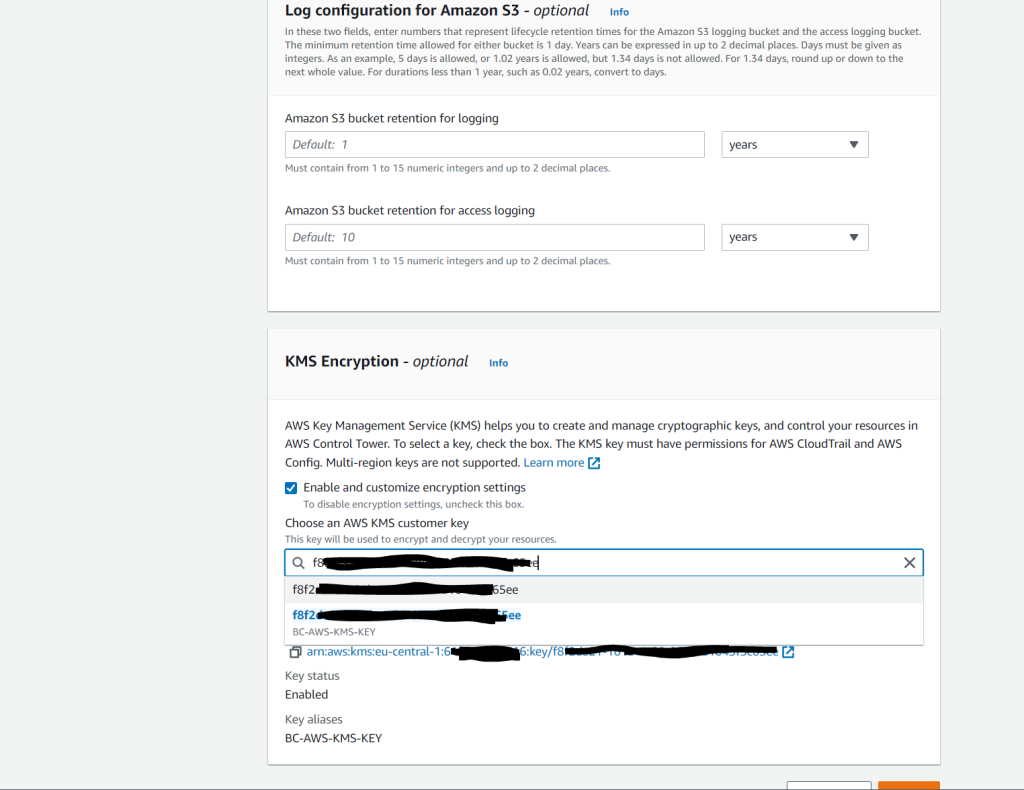
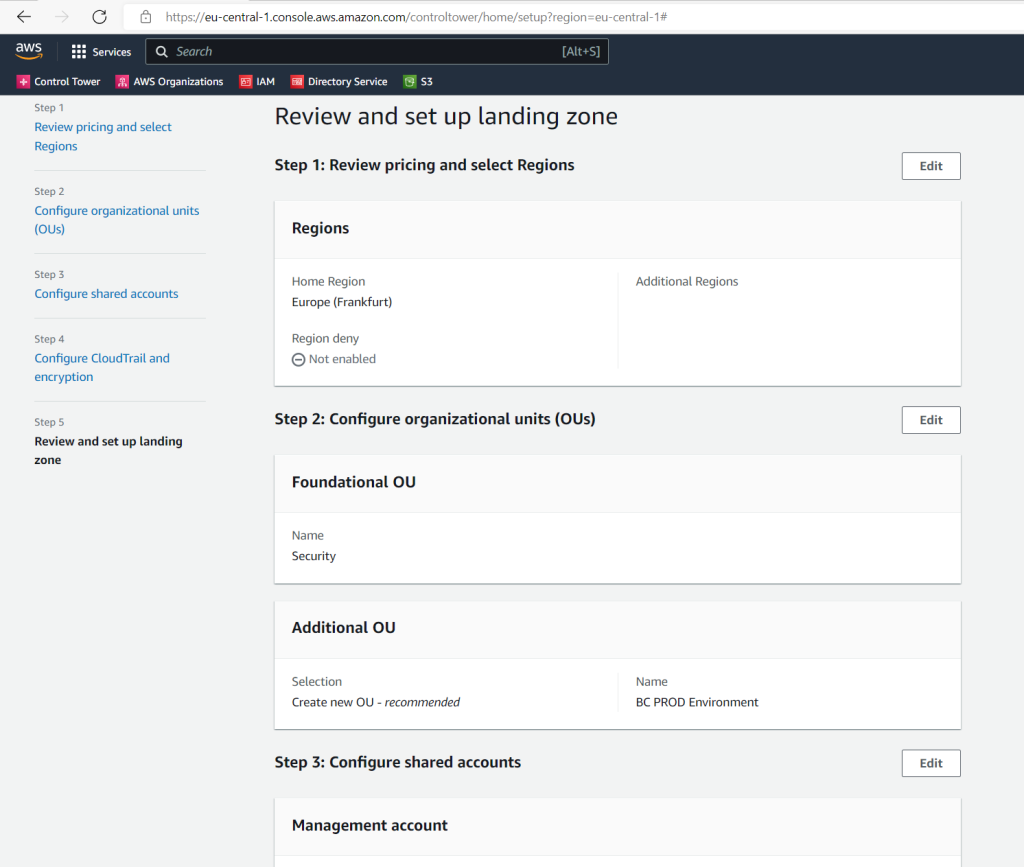
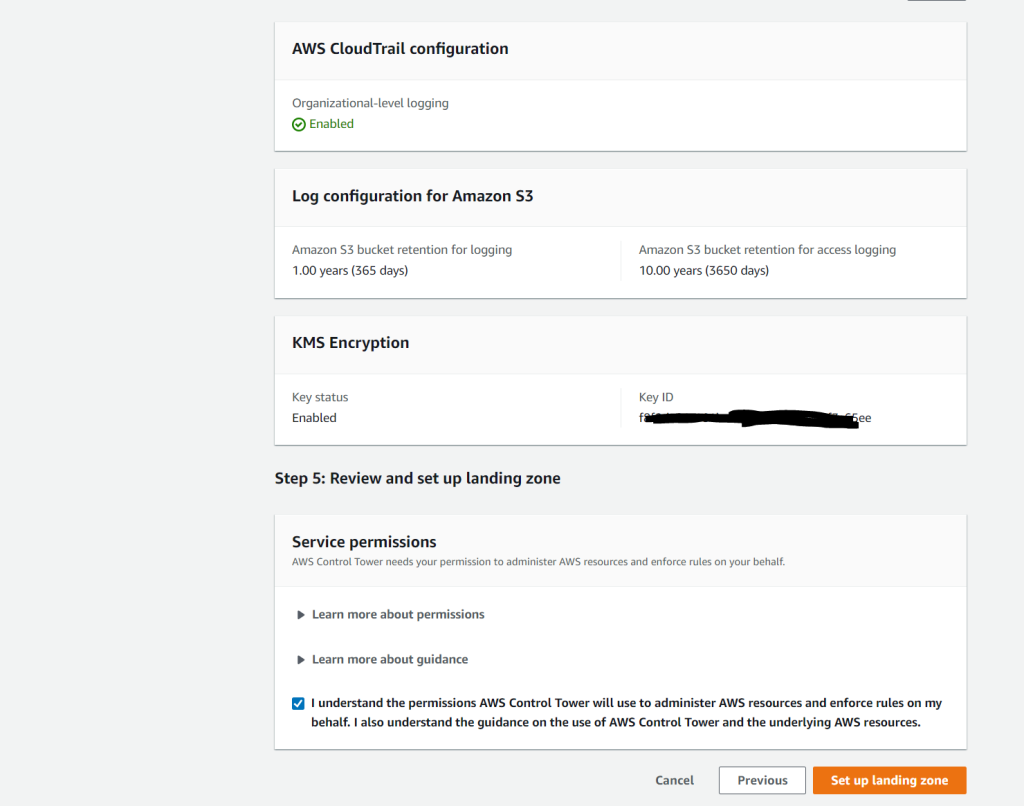
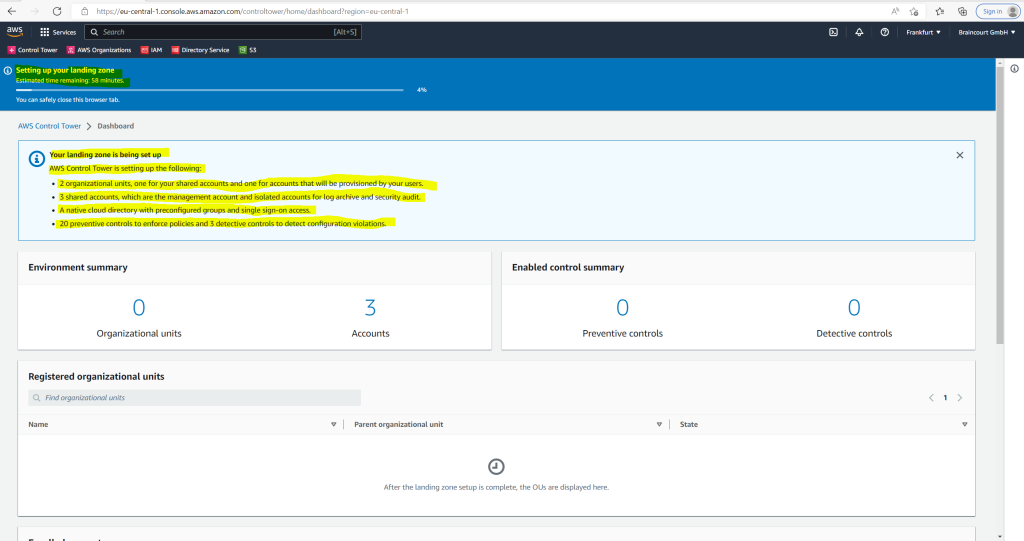
Finally your landing zone is being set up
Nearly an hour later as mentioned the landing zone creation has finished.
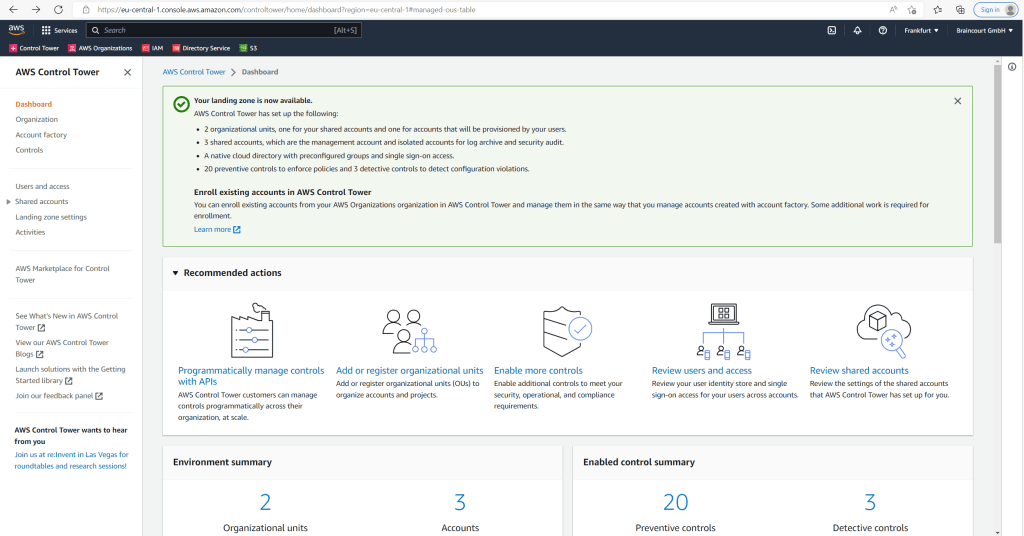
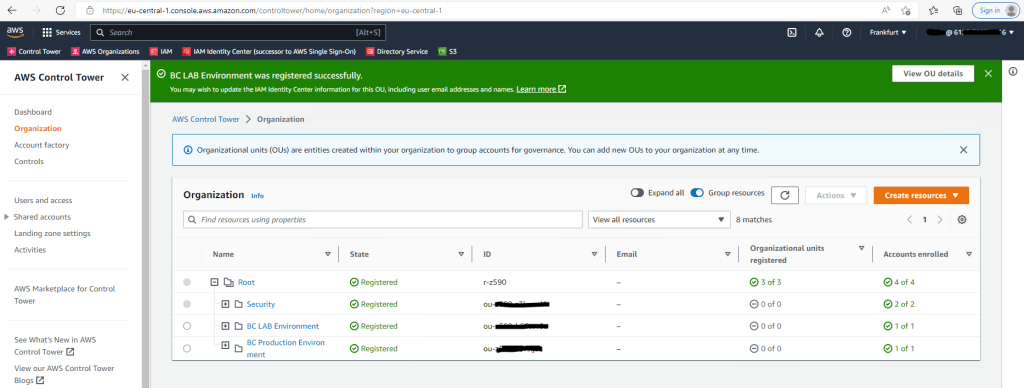
BTW. if you remember previously for AWS Organizations, I created already two OUs to manage my prod and lab environement, they both wouldn’t be registered automatically in AWS Control Tower when setting up the landing zone.
You can do this later in AWS Control Tower in the navigation bar under Organization, click on your OU and after that on the Register OU button as follows.
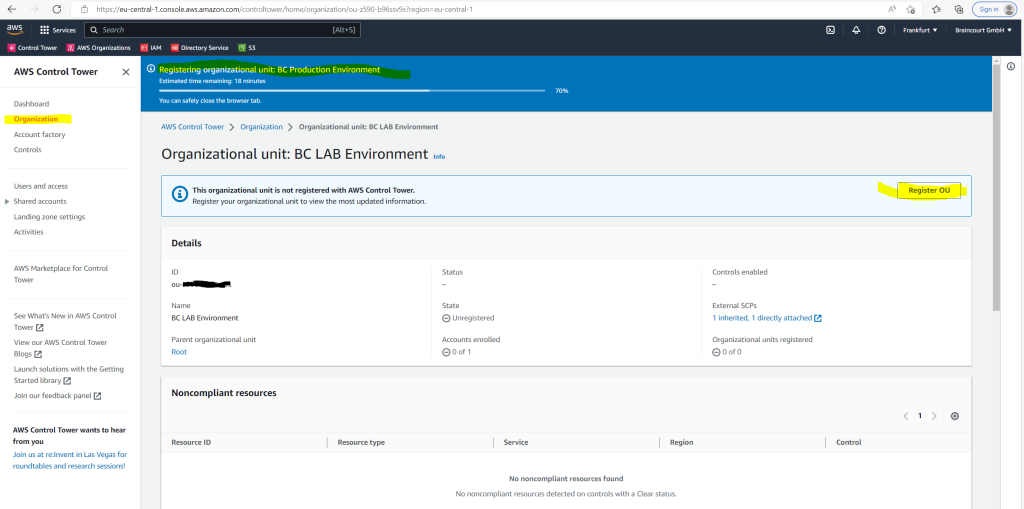
In case you encounter the following issue and error for registering an existing OU.
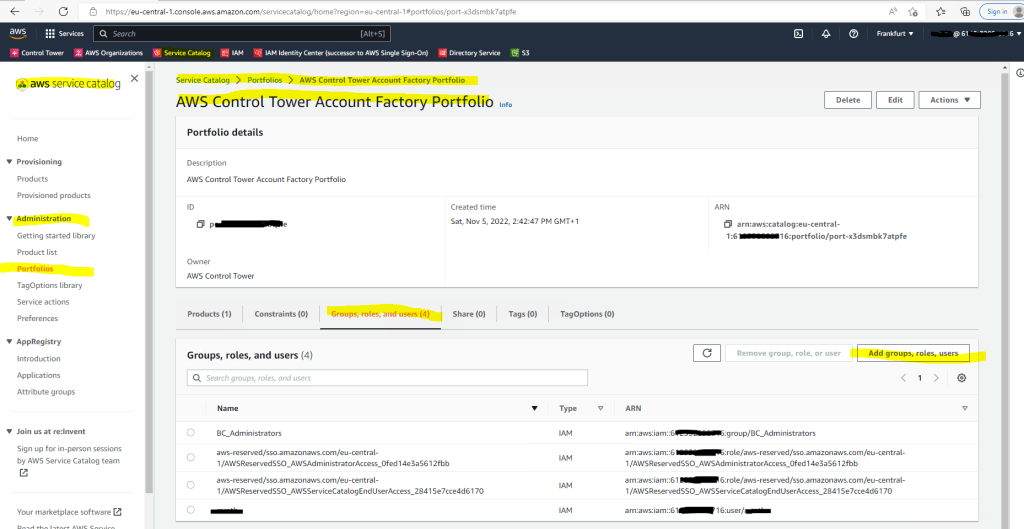
Prerequisites check failed – Add the IAM user to the AWS Service Catalog portfolio before registering your OU
You need to enter your IAM user as follows to the AWS Service Catalog portfolio
Service Catalog –> Portfolios –> AWS Control Tower Account Factory Portfolio –> Groups, roles, and users –> Add group, roles, users
Links
What Is AWS Control Tower?
https://docs.aws.amazon.com/controltower/latest/userguide/what-is-control-tower.htmlWhat is AWS Organizations?
https://docs.aws.amazon.com/organizations/latest/userguide/orgs_introduction.htmlManage Accounts Through AWS Organizations
https://docs.aws.amazon.com/controltower/latest/userguide/organizations.htmlBest practices for member accounts
https://docs.aws.amazon.com/organizations/latest/userguide/best-practices_member-acct.htmlAWS Control Tower FAQs
https://aws.amazon.com/controltower/faqs/
Related Posts
Follow me on LinkedIn


