Set up Microsoft Entra Connect
Managing user identities across on-premises and cloud environments is critical for ensuring secure access and a smooth user experience.
Integrating your on-premises directories with Microsoft Entra ID makes your users more productive by providing a common identity for accessing both cloud and on-premises resources.
Microsoft Entra Connect, formerly known as Azure AD Connect, is a powerful tool that bridges the gap between your on-premises Active Directory and Microsoft Entra ID (formerly Azure Active Directory).
This synchronization tool is the backbone of hybrid identity solutions, enabling features like single sign-on (SSO), seamless user provisioning, and centralized management of credentials.
In this guide, I will walk you through the step-by-step process of setting up Microsoft Entra Connect, ensuring your organization can unlock the full potential of hybrid identity management.
Microsoft Entra Connect Sync vs. Cloud Sync
When synchronizing on-premises Active Directory with Microsoft Entra ID, you can choose between Microsoft Entra Connect Sync and Cloud Sync. While both achieve directory synchronization, their approaches and use cases differ.
Entra Connect Sync is a robust, server-based tool ideal for complex environments. It supports advanced filtering, multi-forest setups, and authentication options like Password Hash Synchronization (PHS), Pass-Through Authentication (PTA), and federation. It’s best suited for large enterprises needing advanced customization and tight integration.
Cloud Sync, on the other hand, is lightweight and agent-based. Fully managed from the cloud, it simplifies deployment and maintenance. It supports PHS and basic filtering, making it a great choice for small to medium-sized organizations with straightforward requirements.
Use Connect Sync for complex environments and advanced features, and choose Cloud Sync for simplicity and minimal infrastructure overhead.
More about Microsoft Entra Cloud Sync you will find in the following Microsoft Article https://learn.microsoft.com/en-us/entra/identity/hybrid/cloud-sync/what-is-cloud-sync.
Prerequisites for Microsoft Entra Connect
- You need a Microsoft Entra tenant. You get one with an Azure free trial. You can use one of the following portals to manage Microsoft Entra Connect:
- Add and verify the domain you plan to use in Microsoft Entra ID. For example, if you plan to use contoso.com for your users, make sure this domain has been verified and you’re not using only the contoso.onmicrosoft.com default domain.
- A Microsoft Entra tenant allows, by default, 50,000 objects. When you verify your domain, the limit increases to 300,000 objects. If you need even more objects in Microsoft Entra ID, open a support case to have the limit increased even further. If you need more than 500,000 objects, you need a license, such as Microsoft 365, Microsoft Entra ID P1 or P2, or Enterprise Mobility + Security.
Source: https://learn.microsoft.com/en-us/entra/identity/hybrid/connect/how-to-connect-install-prerequisites
Prepare your on-premises data
The IdFix tool provides you the ability to query, identify, and remediate the majority of object synchronization errors in your Windows Server AD forests in preparation for deployment to Microsoft 365.
IdFix can detect several common errors in your Active Directory Domain Services (AD DS) domain. Here are a few examples:
- Missing Attributes: Identifies required fields that are empty or missing information.
- Duplicate Entries: Identifies users or objects that appear more than once.
- Formatting Issues: Detects problems with the format of user attributes, such as incorrect email formats.
- Invalid Characters: Finds characters that are not allowed in certain fields.
I will download and install the tool on a dedicated virtual machine (W2K22) in my vSphere on-premise lab environment.
After the installation run the tool and choose Query as shown below.
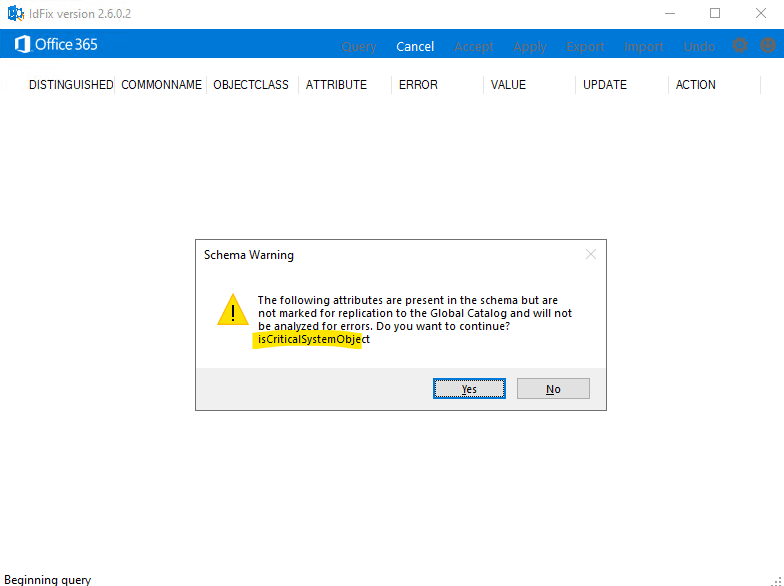
When you encounter a Schema Warning like shown below about attributes not marked for replication in the Global Catalog (GC), it means certain attributes in your directory are configured in a way that they won’t replicate across all domain controllers in your forest.
In Active Directory, the Global Catalog (GC) is a distributed database that stores a subset of AD objects and their attributes for the entire forest.
The warning finally doesn’t meant that these attributes will not by synchronized to Microsoft Entra ID, IdFix will just not analyze them to detect errors.
Confirm with yes.
The following attributes are present in the schema but are not marked for replication to the Global Catalog and will not be analyzed for errors.
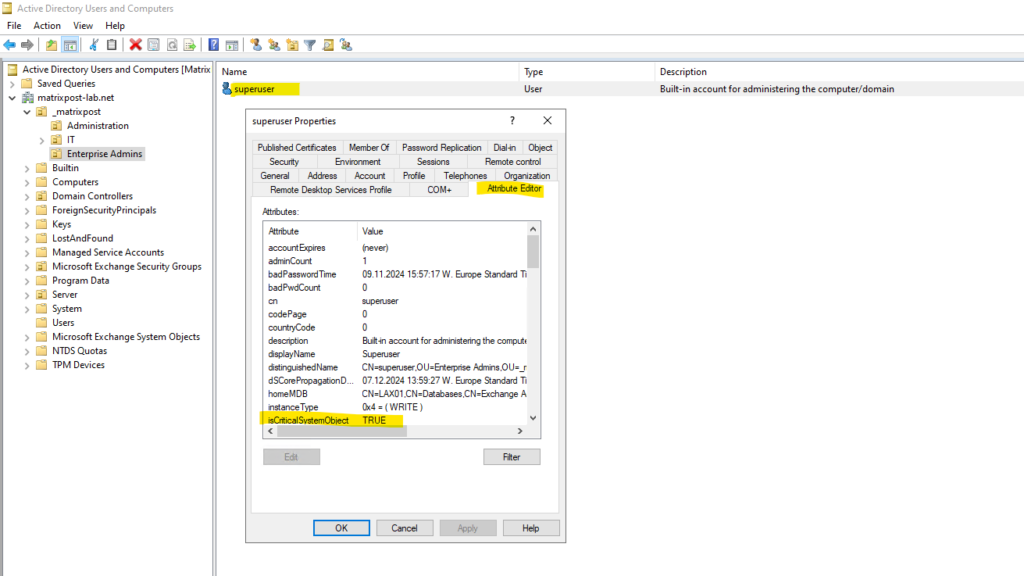
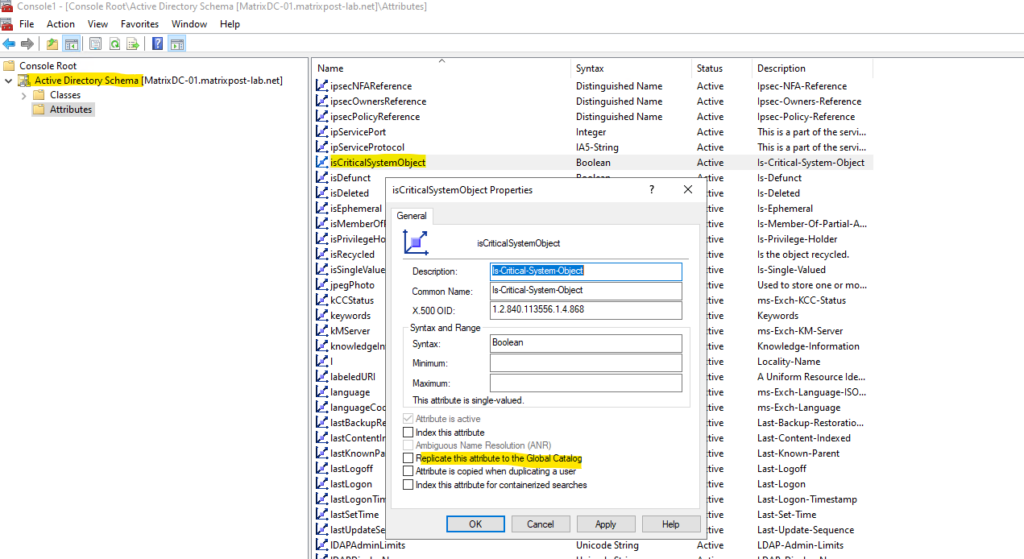
On-premise objects are not synchronized to Microsoft Entra ID when their Active Directory attribute named isCriticalSystemObject is set to true like for the on-premise Active Directory enterprise admin account shown below.
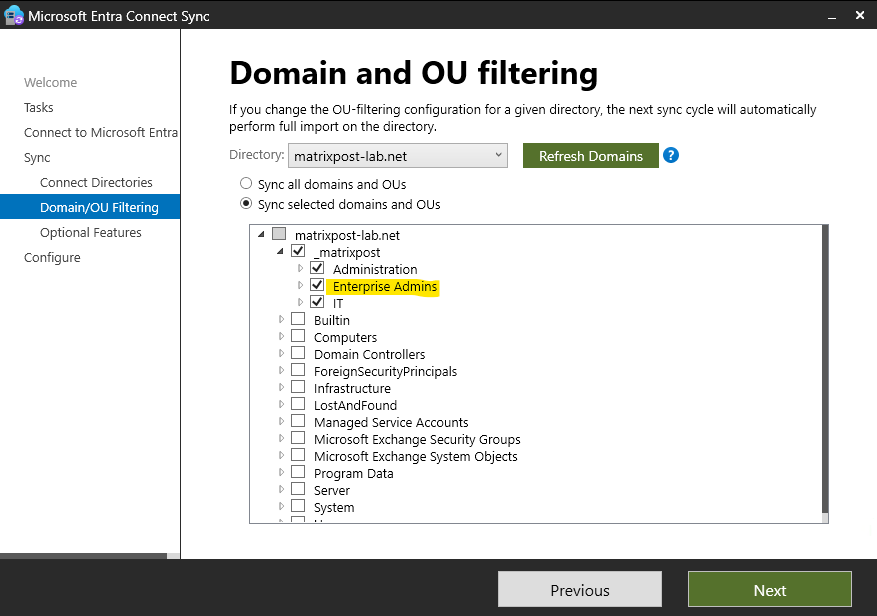
So even if we mark the OU which includes our Active Directory enterprise admin to sync to Microsoft Entra ID, finally these objects will not be synchronized to Microsoft Entra ID.
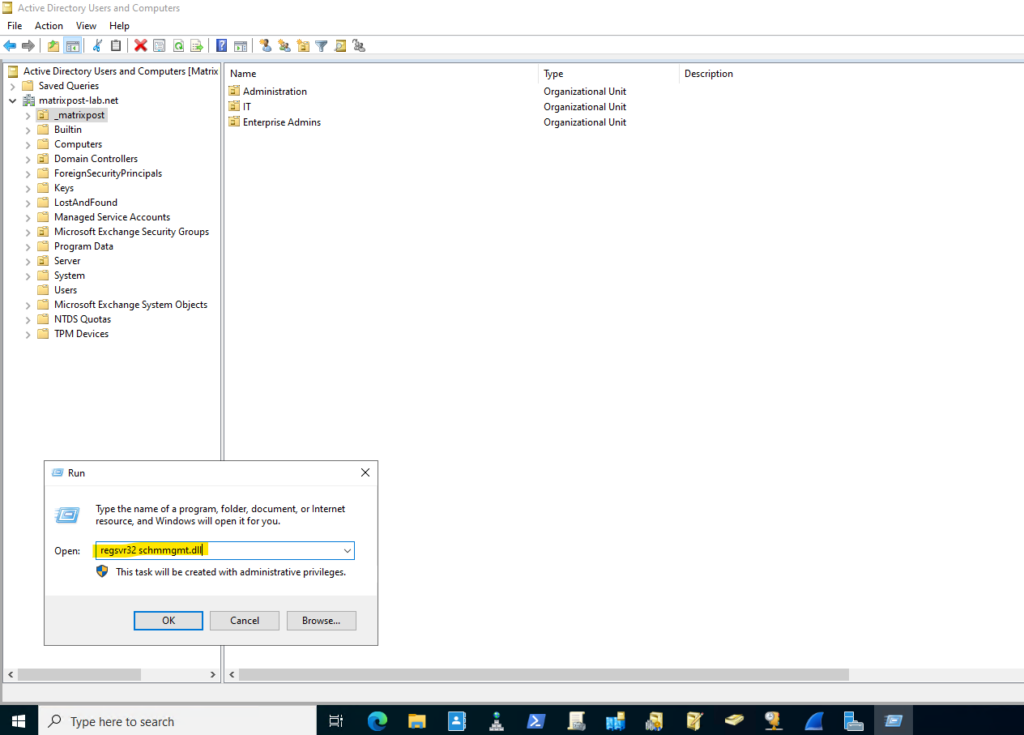
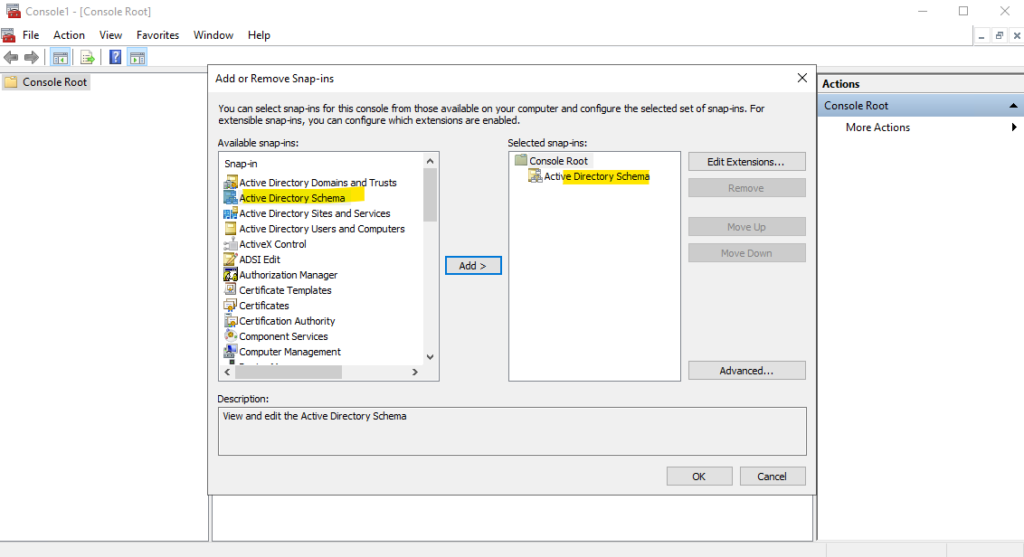
We can use the Active Directory Schema snap-in to adjust and configure which attributes of an Active Directory object will be replicated also to the global catatalog (GC).
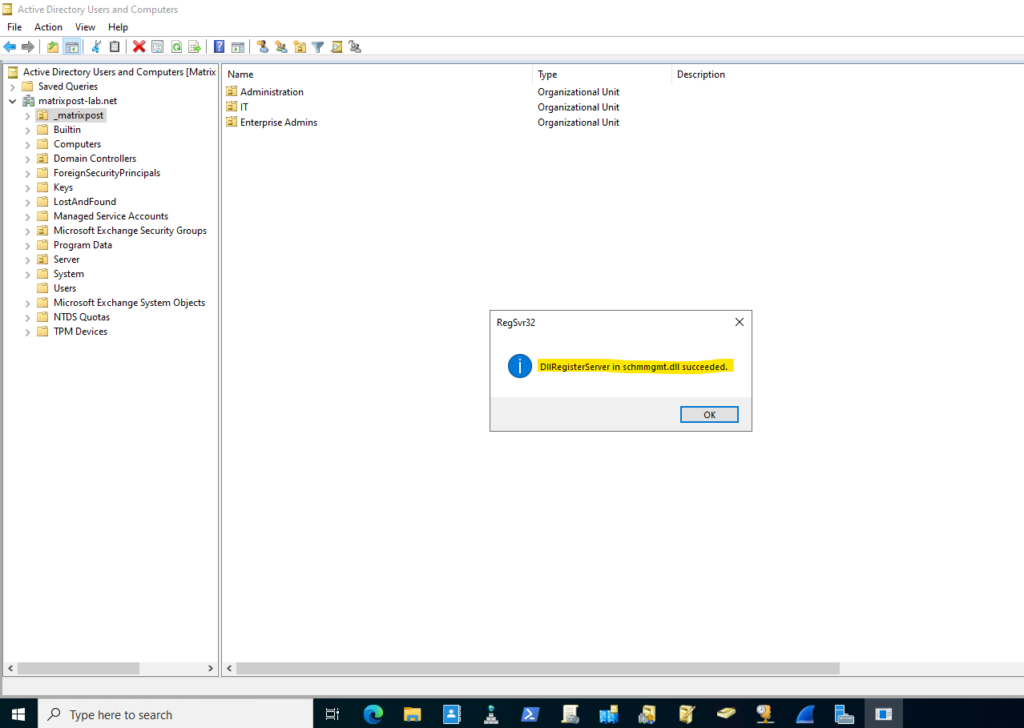
Before we can use the Active Directory Schema snap-in, we first have to register the dynamic link library (DLL) associated with it.
This can be done with the regsvr32 utility using the following command:
regsvr32 schmmgmt.dll
Most of the Active Directory MMC snap-ins do not require that you manually register the associated DLL. Microsoft requires this with the Active Directory Schema snap-in due to the sensitive nature of modifying the schema. This doesn’t actually do much to prevent users from using it, but at least it isn’t available by default. And regardless, only members of the Schema Admins group have permission to modify the schema anyway, so making this snap-in available should not pose much of a risk.
Source: https://www.oreilly.com/library/view/active-directory-cookbook/0596004648/ch10s02.html
The isCriticalSystemObject attribute by default is not replicated to the Global Catalog (GC) because it is primarily used for administrative and operational purposes within the local domain where the object resides.
Replicating it to the GC, which stores a subset of attributes for all objects in the forest, is unnecessary and would only add overhead without delivering significant benefits.
The GC is designed to store only the most essential attributes needed for forest-wide searches and functionality, such as user principal names (userPrincipalName) and email addresses. Including administrative or operational attributes like isCriticalSystemObject would unnecessarily increase replication traffic and storage requirements.
The Global Catalog (GC) server holds the same information as a domain controller. However, the global catalog server also holds a read-only replica of every domain naming context in the forest. T
Thus, a domain controller only knows about the objects in its domain, while a global catalog server knows about objects in its domain and every other domain.
Although the global catalog server knows about all objects from every domain, it only has knowledge of a subset of the attributes for each object.
The objects that are available for replication to a global catalog server are controlled by the Active Directory Schema Manager snap-in.
By default, the first domain controller in a domain is a global catalog server.
Global catalog servers listen on port 3268 (using LDAP) for queries, as well as on the standard LDAP port 389. Port 3269 may also be used on a global catalog server to process requests for global catalog information over Secure Sockets Layer (SSL).
A domain controller can be made into a global catalog server by selecting the option from the Active Directory Sites and Services snap-in.
Source: https://www.sciencedirect.com/topics/computer-science/global-catalog-server
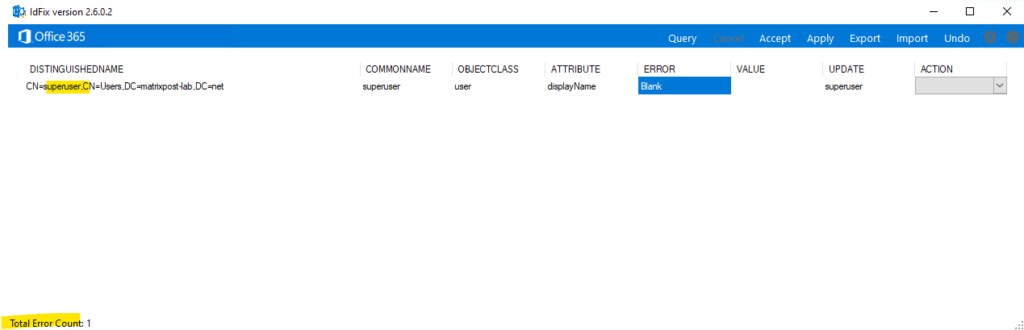
For each error shown up in the IdFix tool you can choose an action:
Remove – The value of the field will be removed (not the complete object!)
Edit – The value in the update field will be used to update the object. You can change the contents of the update field if you want.
Complete – This one is mostly used with duplicate items. Mark the record that you want as Complete and set the action on the other record to Remove
In my case there was a blank display name error for the enterprise admin. After adding it the next run didn’t return any error.
Download Microsoft Entra Connect
In order to install Microsoft Entra Connect on a dedicated virtual machine in my vSphere on-premise lab environment, I will first need to download it.
https://www.microsoft.com/en-us/download/details.aspx?id=47594
Install and Configure Microsoft Entra Connect
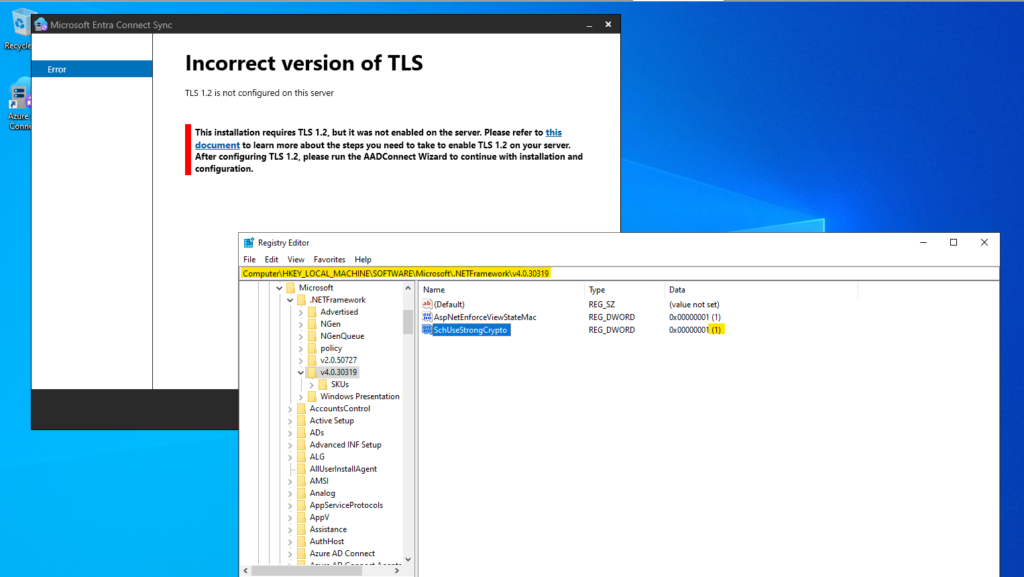
First enable TLS 1.2 on the Server you install Microsoft Entra Connect.
For all operating systems, set this registry key and restart the server.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319\SchUseStrongCrypto = 1
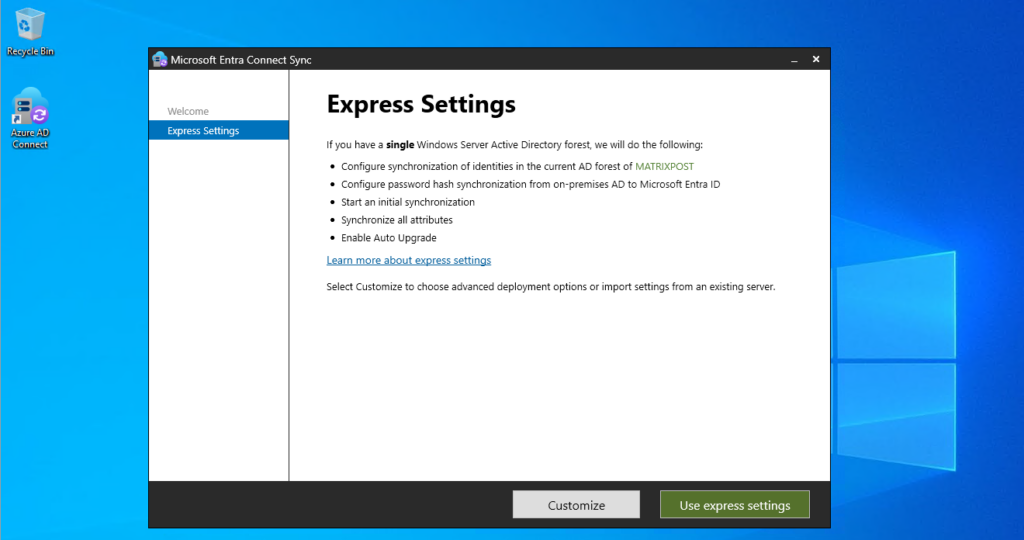
I will use the express settings.
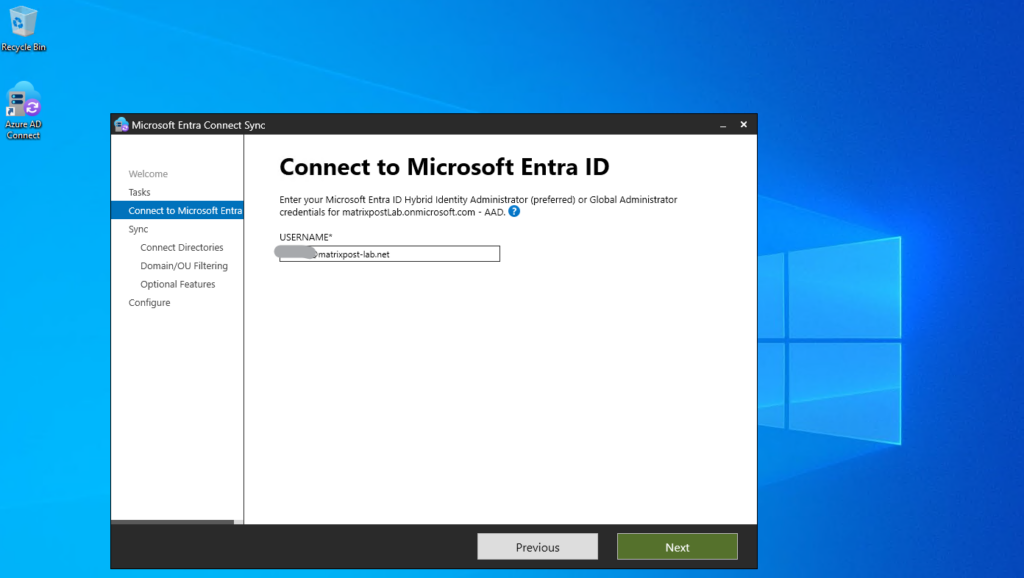
To connect the tool to Microsoft Entra ID, I will user here an native cloud account which has the global administrator role assigned to.
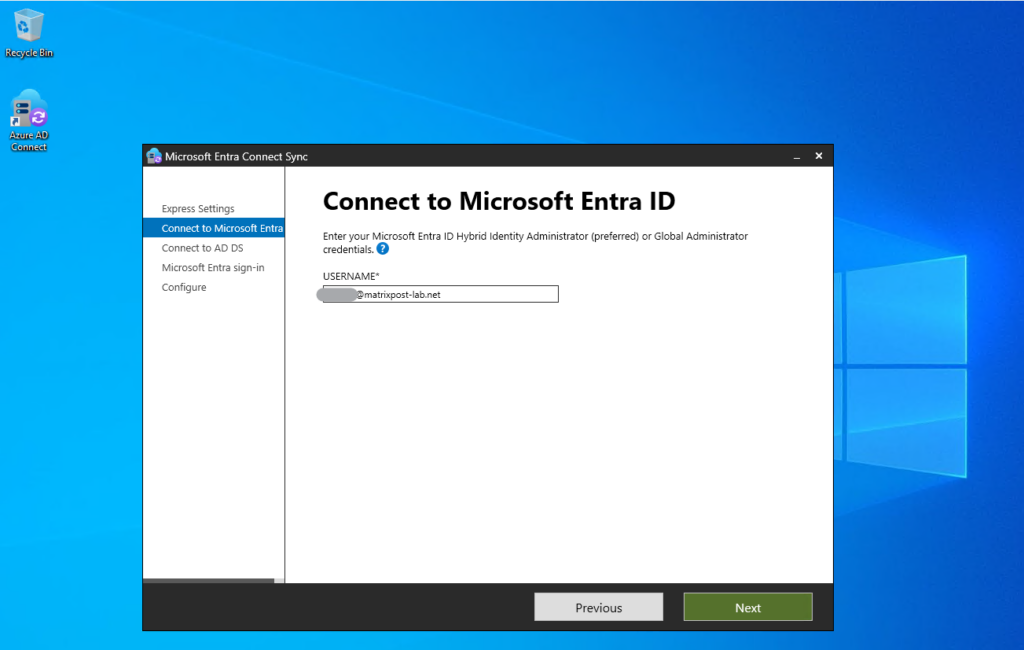
Next we need to enter our on-premise Active Directory enterprise administrator credentials.
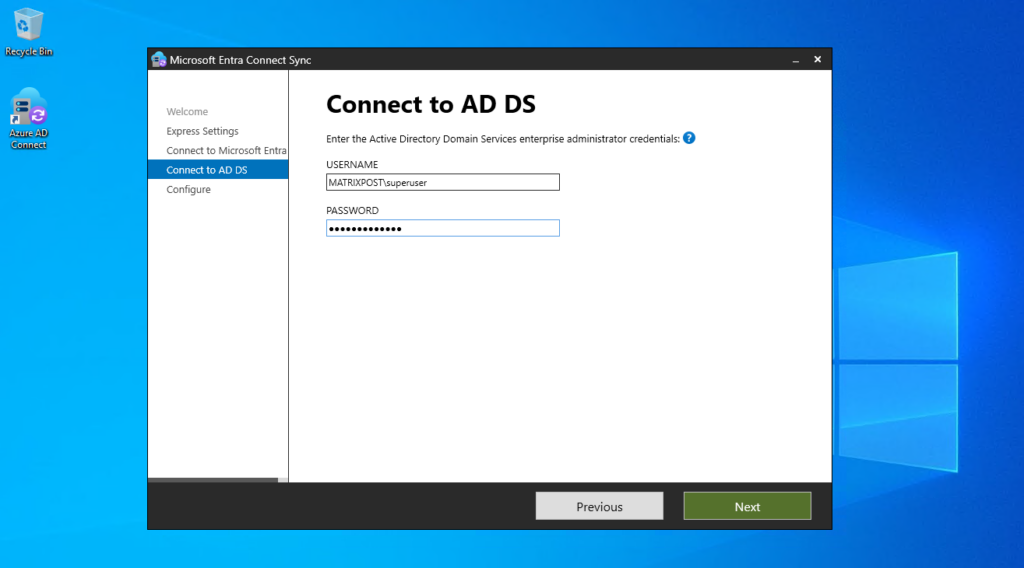
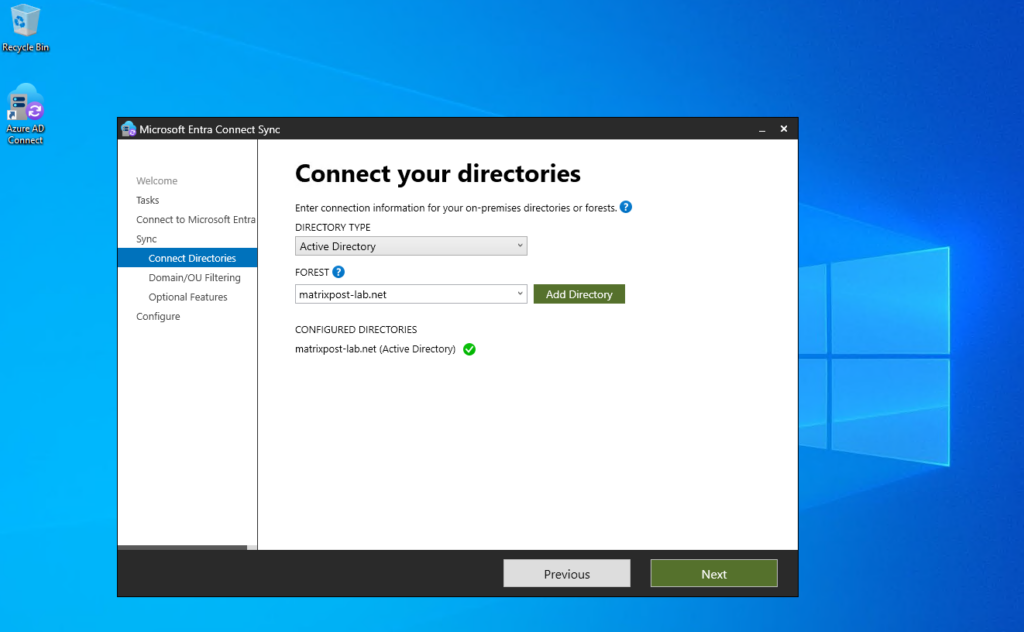
My on-premise Active Directory Domain (matrixpost-lab.net) is already verified in Microsoft Entra ID.
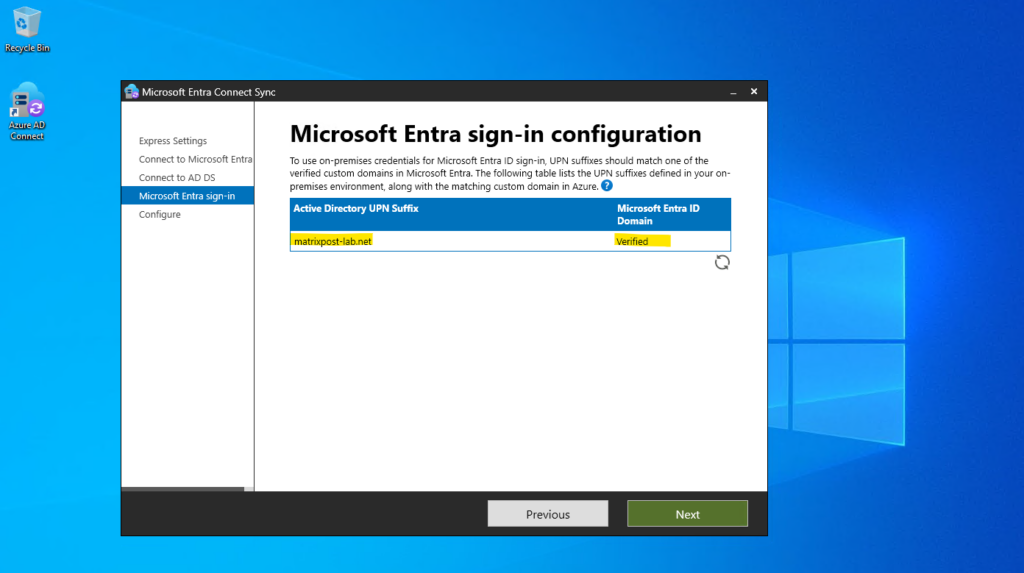
In Azure under Microsoft Entra ID -> Manage -> Custom domain names you need to add your on-premise Active Directory Domain as verified domain.
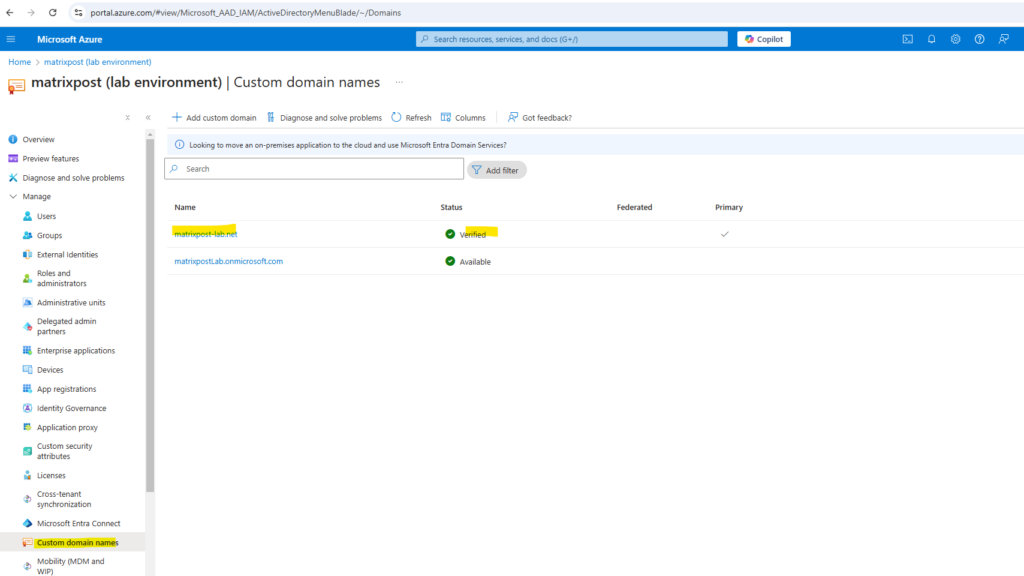
Below you can see my existing native cloud users before the initial Entra Connect synchronization process is triggered.
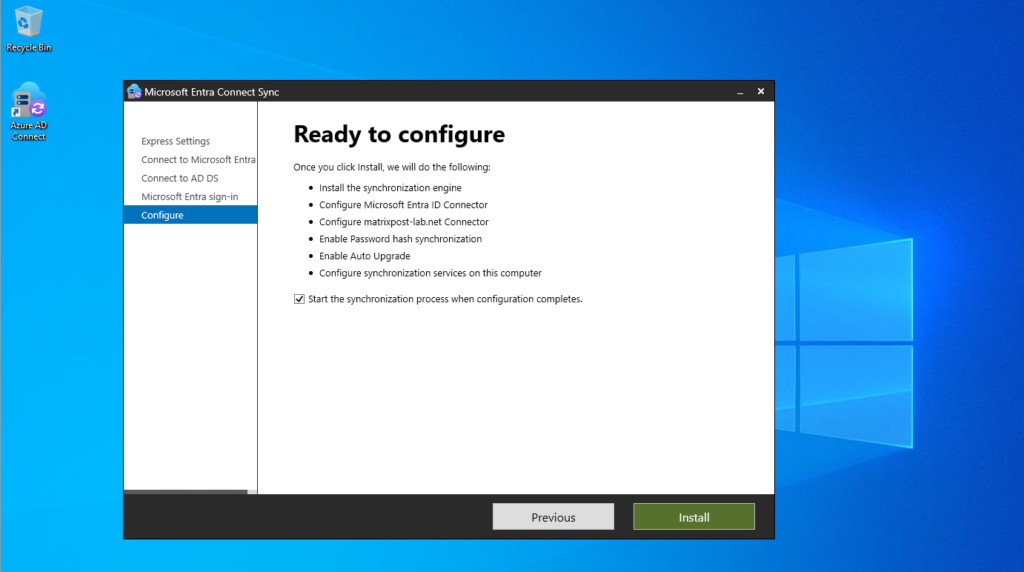
We can now finally trigger the configuration of Entra ID Connect and start the initial synchronization process by clicking below on Install.
!! Note !!
In this case by default all domain and OUs for your on-premise Active Directory will be initial synchronized to Microsoft Entra ID Connect.So best is here to first uncheck below Start the synchronization process when configuration completes and only select the objects you really finally want to synchronize to Microsoft Entra ID Connect.
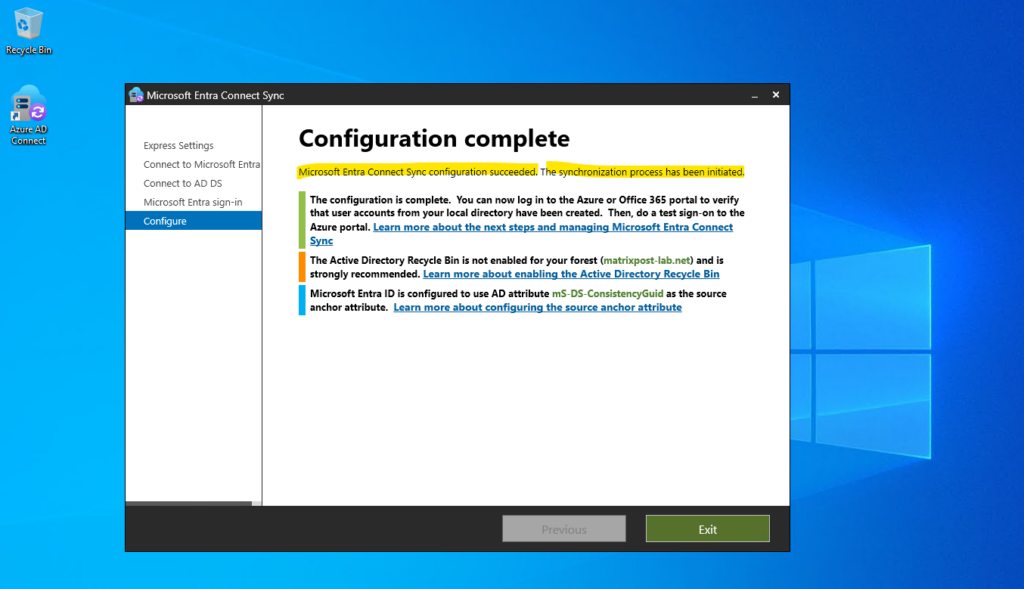
The Active Directory Recycle Bin is not enabled for your forest and is strongly recommended.
We recommend that you enable the Active Directory Recycle Bin feature for your on-premises instances of Active Directory (AD) that are synchronized to Microsoft Entra ID.
If you accidentally deleted an on-premises AD user object and restore it using the feature, Microsoft Entra ID restores the corresponding Microsoft Entra user object.
Source: https://learn.microsoft.com/en-us/entra/identity/hybrid/connect/how-to-connect-sync-recycle-bin
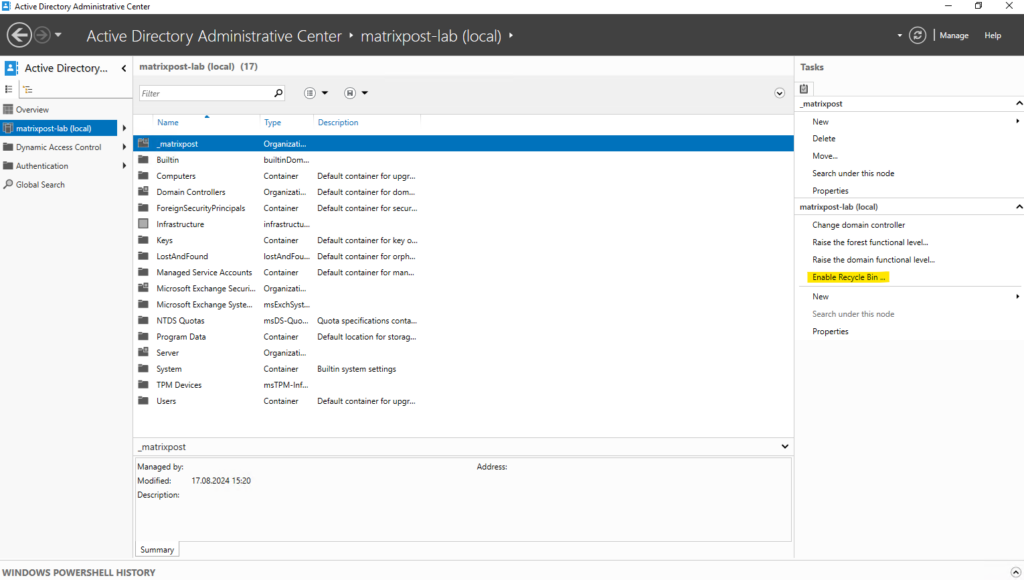
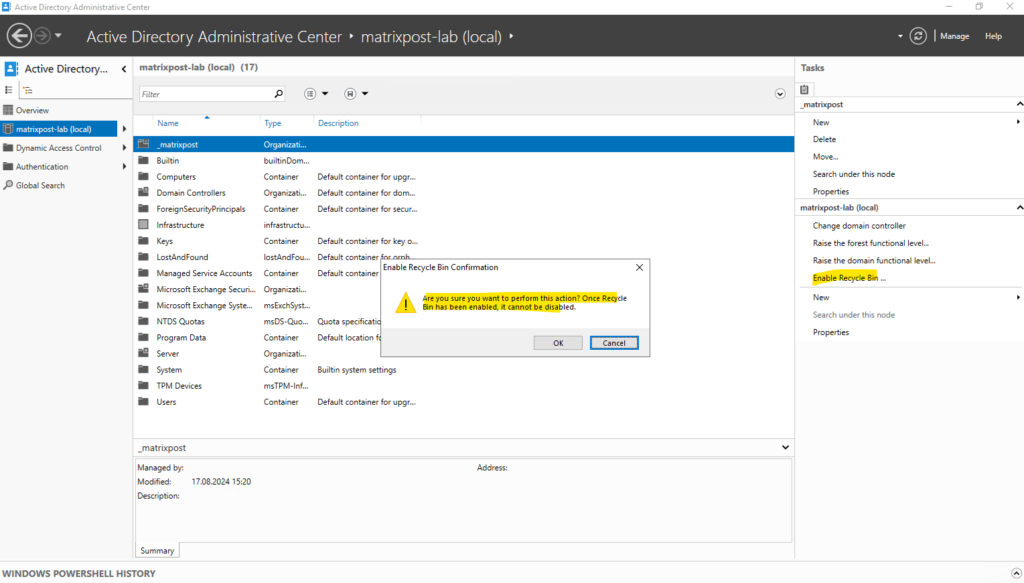
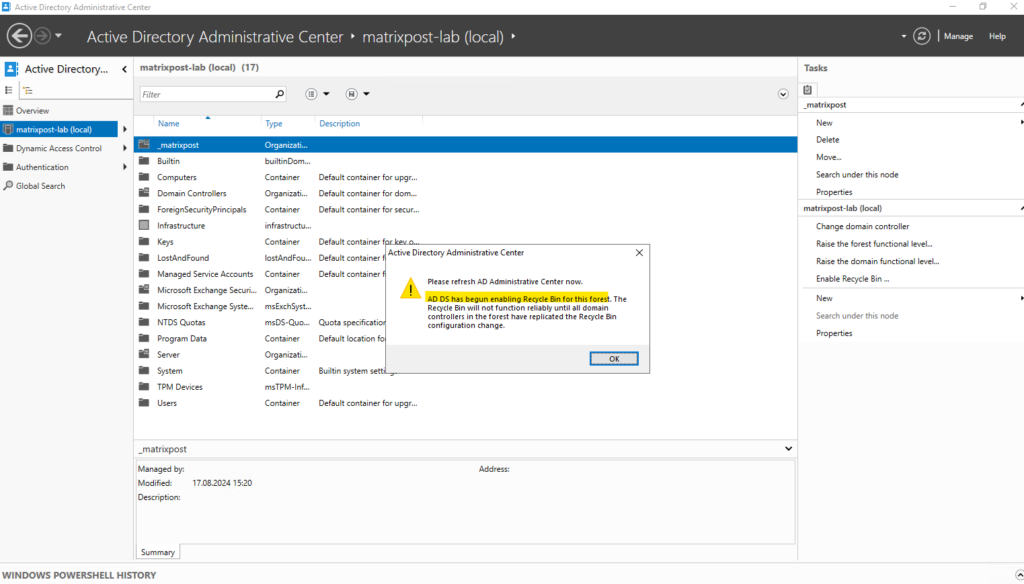
To enable the Active Directory Recycle Bin, open the Active Directory Administrative Center and select the name of your forest in the navigation pane. From the Tasks pane, select Enable Recycle Bin.
The equivalent Active Directory Windows PowerShell cmdlet is:
Enable-ADOptionalFeature
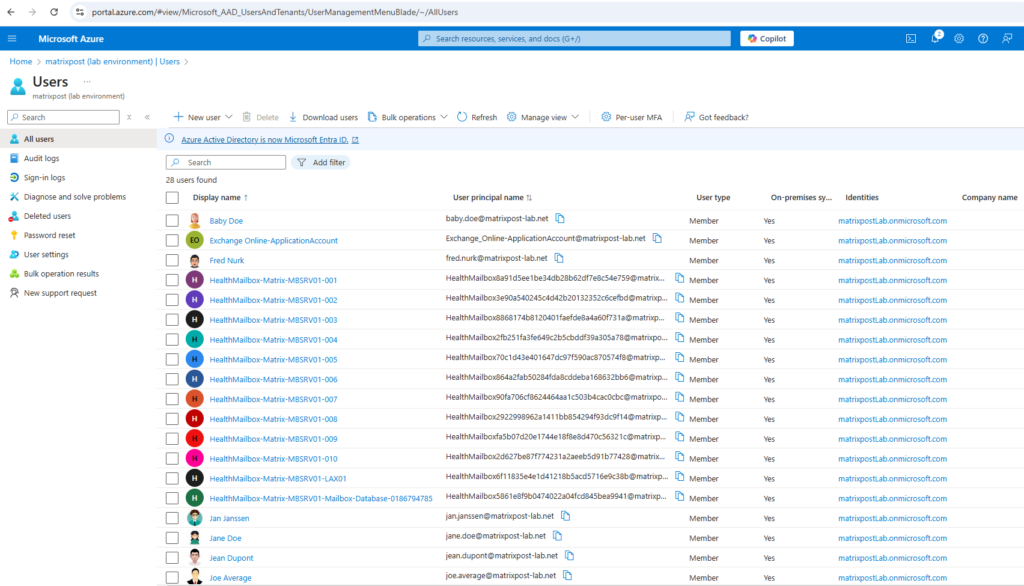
After the initial synchronization process we can see our on-premise accounts also in Azure. Below you can see that also the HealthMailbox accounts from Exchange on-premise was synced to Azure which I actually doesn’t need and want to be synchronized to Azure.
Therefore as mentioned previously its best to first uncheck Start the synchronization process when configuration completes further above and only select the objects you really finally want to synchronize to Microsoft Entra ID Connect.
To exclude them and filter just for accounts we want to synchronize to Azure we need to adjust the configuration as shown below.
Open the Microsoft Entra Connect Sync tool and click on Configure.
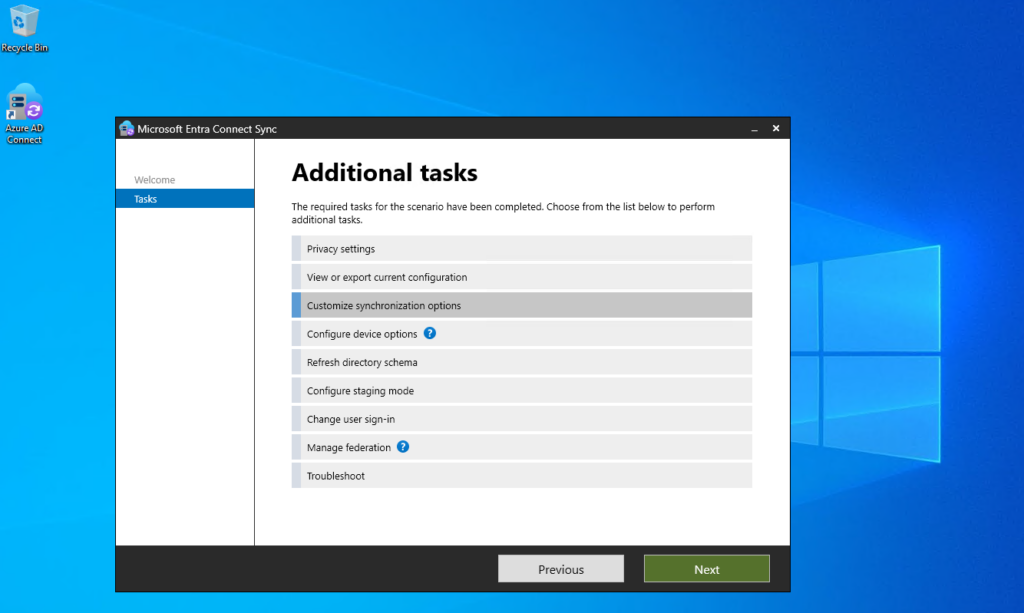
Select Customize synchronization options.
As mentioned by default Sync all domain and OUs are selected below. I will change this now to Sync selected domains and OUs and filter to just sync the OU named _matrixpost as shown below.
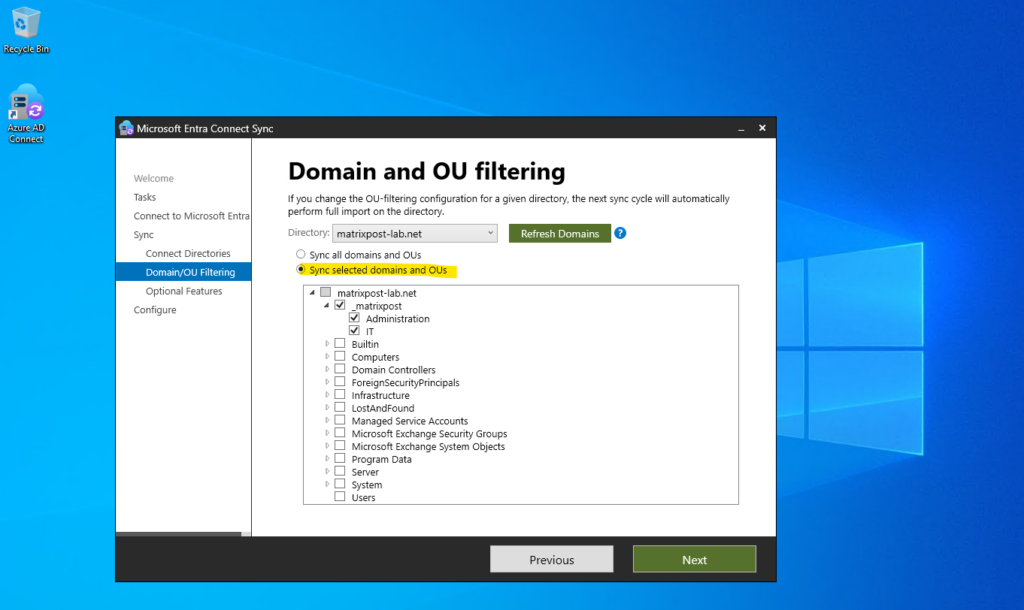
Below I will select Password hash synchronization.
To synchronize your password, Microsoft Entra Connect Sync extracts your password hash from the on-premises Active Directory instance.
Extra security processing is applied to the password hash before it’s synchronized to the Microsoft Entra authentication service. Passwords are synchronized on a per-user basis and in chronological order.
The password hash synchronization process runs every 2 minutes. You can’t modify the frequency of this process. When you synchronize a password, it overwrites the existing cloud password.
When you change an on-premises password, the updated password is synchronized, most often in a matter of minutes. The password hash synchronization feature automatically retries failed synchronization attempts. If an error occurs during an attempt to synchronize a password, an error is logged in your event viewer.
More about here https://learn.microsoft.com/en-us/entra/identity/hybrid/connect/how-to-connect-password-hash-synchronization.
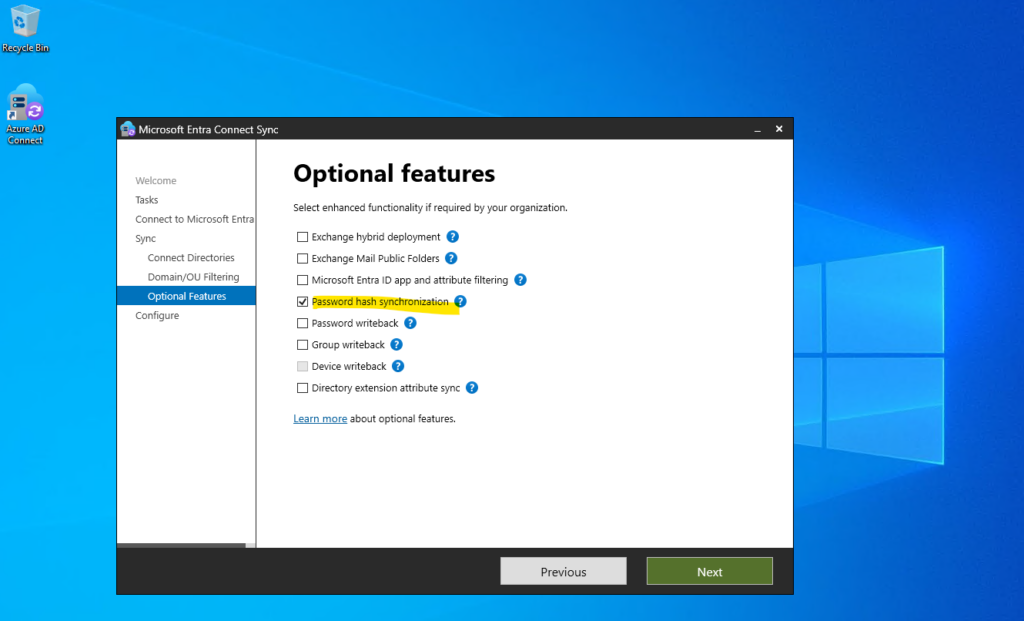
Finally we can click on Configure.
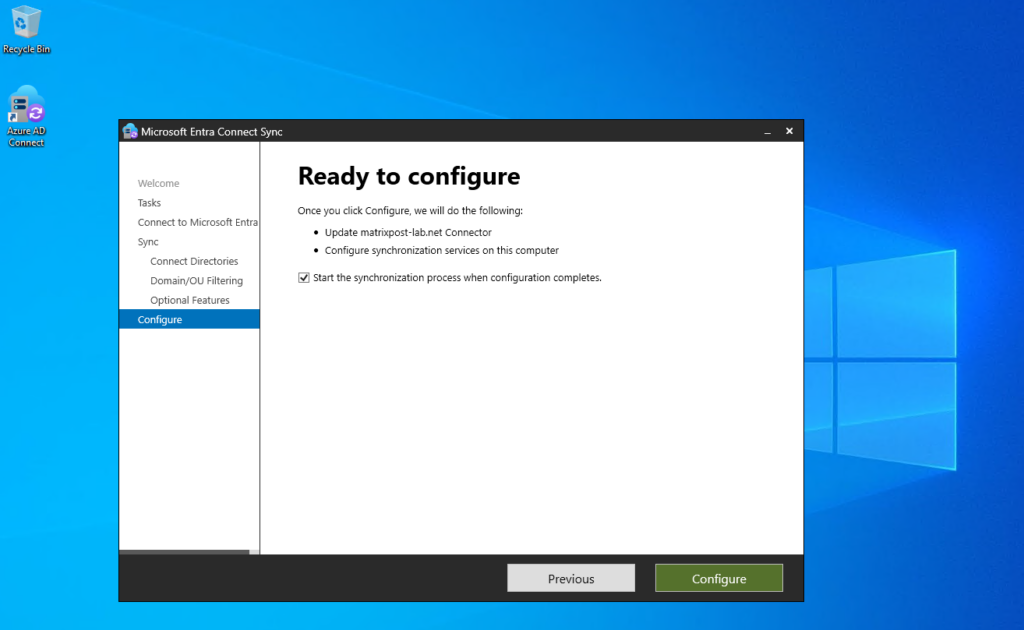
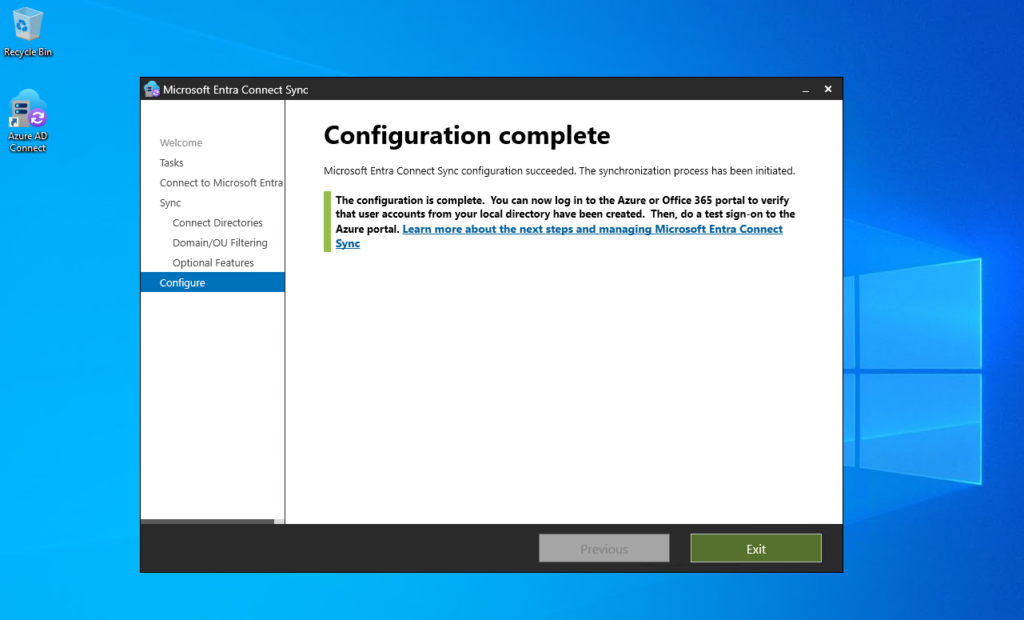
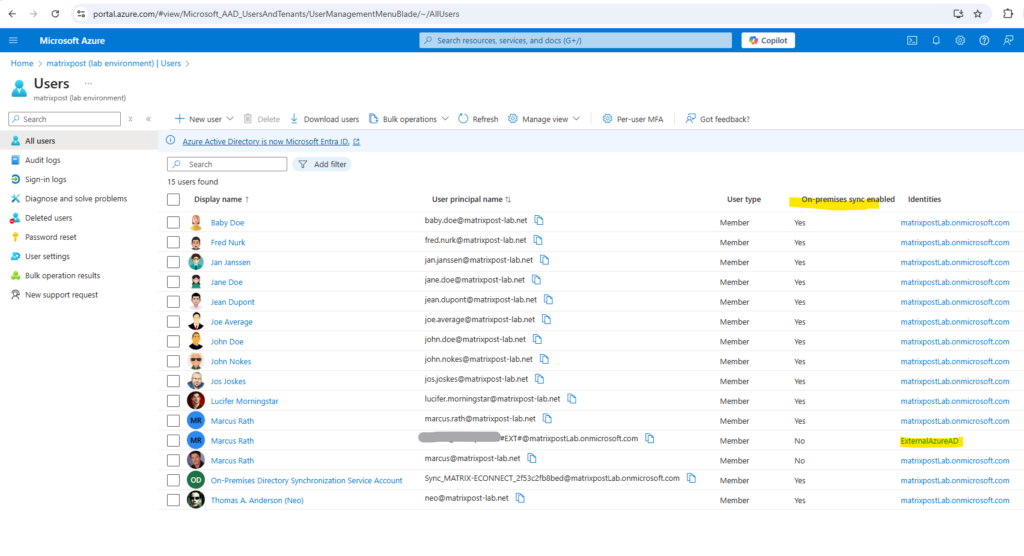
Now back in Azure -> Microsoft Entra ID -> Manage -> Users I will check if the previously by accident synced HealthMailbox accounts from Exchange on-premise will be gone.
Looks good! Now just my on-premise Active Directory accounts within my selected OUs was synced to Azure and Microsoft Entra ID.
From now on we can also authorize our on-premise users for native cloud resources.
A deep dive into the Microsoft Entra Connect Sync Architecture you will find in my following post, at this time it was known and named Azure AD Connect.
Under https://blog.matrixpost.net/?s=azure+ad+connect you will also find more about Microsoft Entra Connect formerly known as Azure AD Connect.
Links
What is Microsoft Entra Connect?
https://learn.microsoft.com/en-us/entra/identity/hybrid/connect/whatis-azure-ad-connectMicrosoft Entra Connect user sign-in options
https://learn.microsoft.com/en-us/entra/identity/hybrid/connect/plan-connect-user-signinPrerequisites for Microsoft Entra Connect
https://learn.microsoft.com/en-us/entra/identity/hybrid/connect/how-to-connect-install-prerequisitesWhat is hybrid identity with Microsoft Entra ID?
https://learn.microsoft.com/en-us/entra/identity/hybrid/whatis-hybrid-identityWhat is Microsoft Entra Cloud Sync?
https://learn.microsoft.com/en-us/entra/identity/hybrid/cloud-sync/what-is-cloud-syncMicrosoft Entra Connect Sync: Understanding the default configuration
https://learn.microsoft.com/en-us/entra/identity/hybrid/connect/concept-azure-ad-connect-sync-default-configurationMicrosoft Entra Connect Sync: Enable Active Directory recycle bin
https://learn.microsoft.com/en-us/entra/identity/hybrid/connect/how-to-connect-sync-recycle-binAdvanced AD DS Management Using Active Directory Administrative Center (Level 200)
https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/get-started/adac/Advanced-AD-DS-Management-Using-Active-Directory-Administrative-Center–Level-200-
Tags In
Related Posts
Latest posts
Deploying NetApp Cloud Volumes ONTAP (CVO) in Azure using NetApp Console (formerly BlueXP) – Part 5 – Backup and Recovery
Follow me on LinkedIn


