Mastering TShark (WireShark) in SUSE Linux Enterprise
TShark, the command-line version of Wireshark, is a powerful tool for capturing and analyzing network traffic on Linux.
TShark offers a lightweight, scriptable alternative to graphical tools, perfect for automation and remote troubleshooting.
In this post, I will cover the basics of using TShark, including installation on SUSE Linux Enterprise, packet capture, filtering, and exporting data, to help you unlock its full potential for network analysis.
Install WireShark on SUSE Linux Enterprise
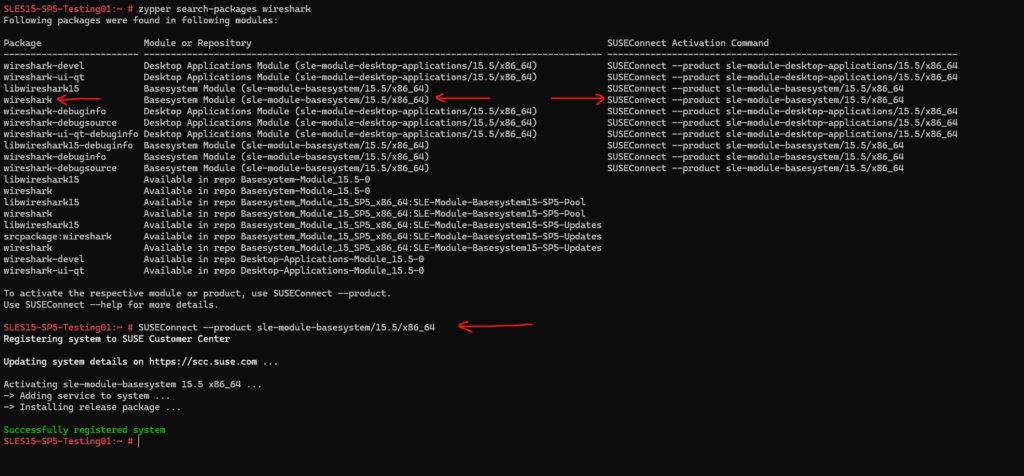
In SUSE Linux Enterprise we can first search for the corresponding package and its module or repository which will include the wireshark package.
Then we can register the module with SUSE’s subscription management system which will also adds the required repositories to our system.
# zypper search-package wireshark # SUSEConnect --product sle-module-basesystem/15.5/x86_64
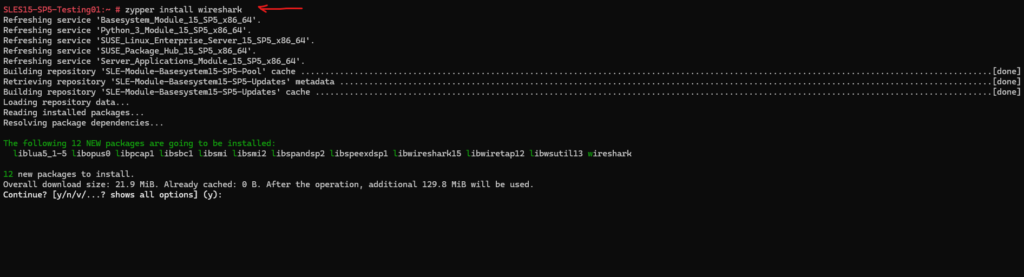
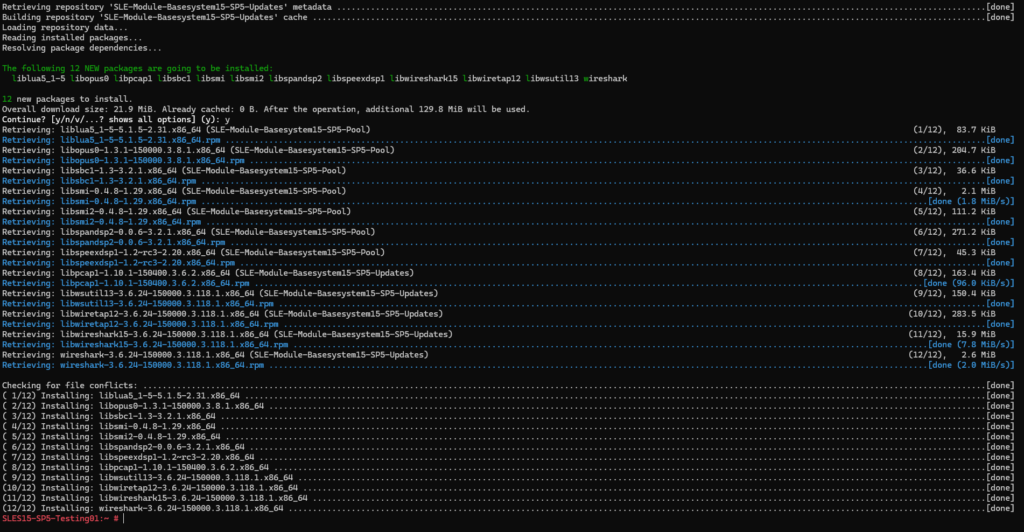
After that we can install the wireshark package which also includes TShark by running:
# zypper install wireshark
Capture Traffic by using TShark
We can now start to capture traffic by using TShark on the Linux command line.
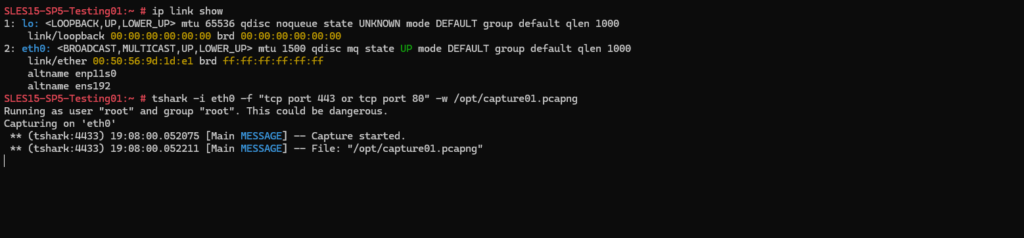
Below for example I will capture TCP traffic on port 80 (HTTP) and 443 (HTTPS) and on the interface eth0. The -f flag is used to set a filter.
The -w flag will set an output file to which the captured packets will written to.
# tshark -i eth0 -f "tcp port 443 or tcp port 80" -w /opt/capture01.pcapng -i <interface>, --interface <interface> name or idx of interface (def: first non-loopback) -f <capture filter> packet filter in libpcap filter syntax -w <outfile|-> write packets to a pcapng-format file named "outfile"
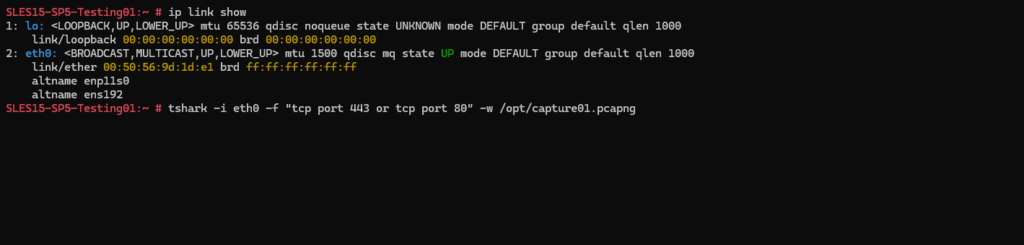
Capturing is started.
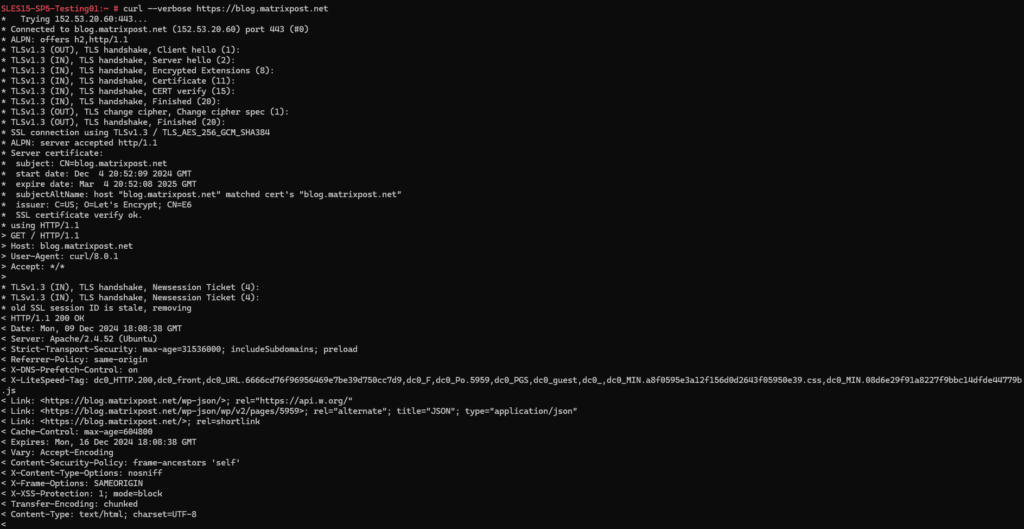
I will now trigger on another SSH session a new HTTPS connection to my blog’s URL to later analyze this traffic in WireShark.
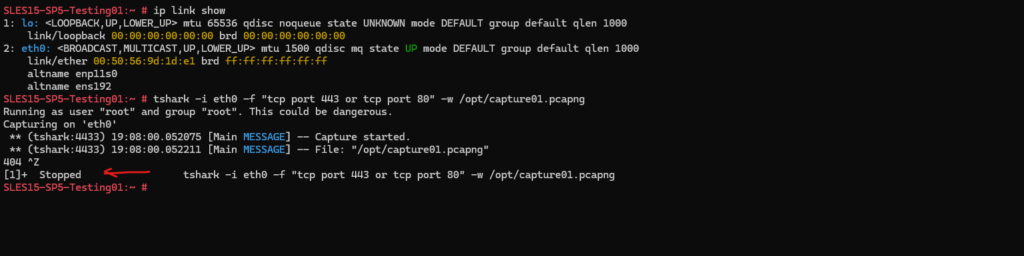
STRG + Z to stop TShark from capturing traffic.
Below we can see the file to which the captured packets were written to by using the -w flag as mentioned further above.
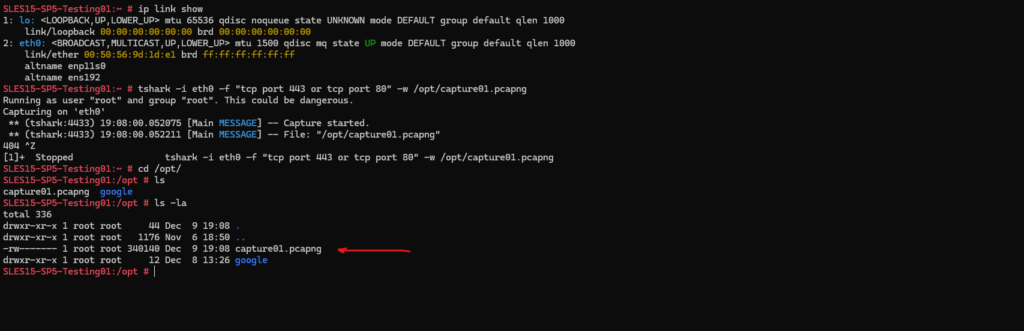
I will now download this file to my local Windows notebook to analyze it by using WireShark.
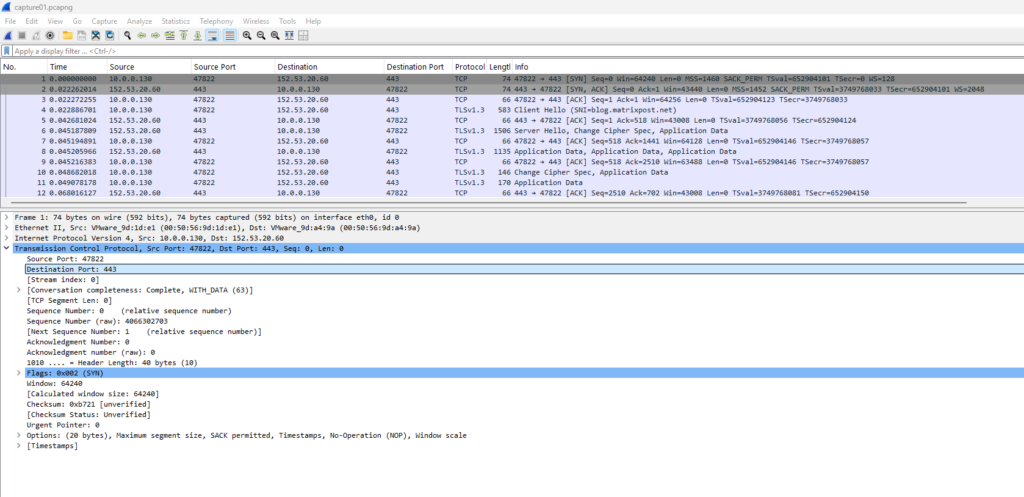
In WireShark we can now analyze this file with our captured traffic. Because the traffic is encrypted by using the HTTPS protocol, unfortunately we can’t see the HTTP traffic here.
In WireShark we can also decrypt HTTPS traffic in case we have access to the SSL certificate’s private key file stored on the destination system. The private key file we then need to add to WireShark (Preferences -> Protocols -> TLS) to finally decrypt the captured packets. Further also Diffie-Hellmann needs to be disabled, there is no way to decrypt data when Diffie-Hellmann is used. The final shared secret to decrypt the traffic will then not send through the initial established HTTPS tunnel and therefore cannot be intercepted by WireShark.
To encrypt HTTPS traffic, the Fiddler tool here is much more suitable, for Linux we need to use Fiddler Everywhere which I will show soon in another post.
More about how to capture with Fiddler you will find on my blog here https://blog.matrixpost.net/?s=fiddler.
Exclude specific protocol from capturing, below for example capture all traffic besides SSH.
By using the -p flag for promiscuous mode we are also able to capture all traffic which hits the NIC we used to capture, regardless of whether they are addressed to the NIC’s specific hardware (MAC) address or not.
In promiscuous mode, the NIC forwards all packets to the operating system, ignoring the destination MAC address.
# tshark -i eth0 -p -f "tcp port not 22" -w /opt/capture1.pcapng
Typically used flags are:
- -i, –interface <interface> -> name or idx of interface
- -f <capture filter> -> packet filter in libpcap filter syntax
- -p, –no-promiscuous-mode -> don’t capture in promiscuous mode
- -w <outfile> -> writes packets to a pcapng-format file named “outfile”. If the output filename has the .gz extension, it will compressed to a gzip archive.
Source: https://www.wireshark.org/docs/wsug_html_chunked/AppToolstshark.html
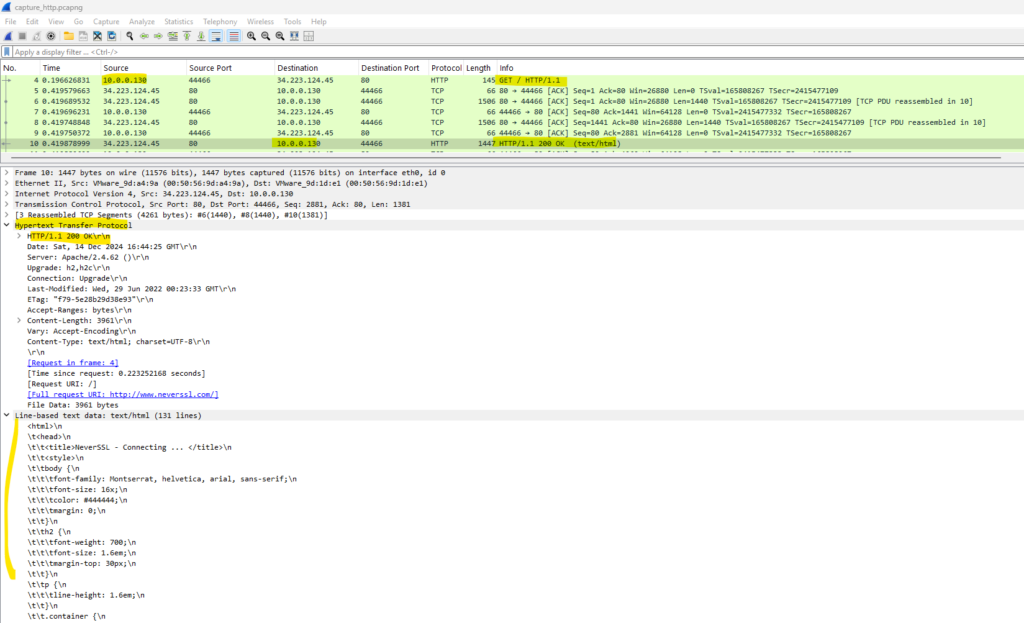
Below I was also capturing traffic from a website which is using just unencrypted HTTP. Because Linux is not as chatty as Windows, I will capture all traffic without filtering and using the -f flag.
# tshark -i eth0 -w /opt/capture_http.pcapng
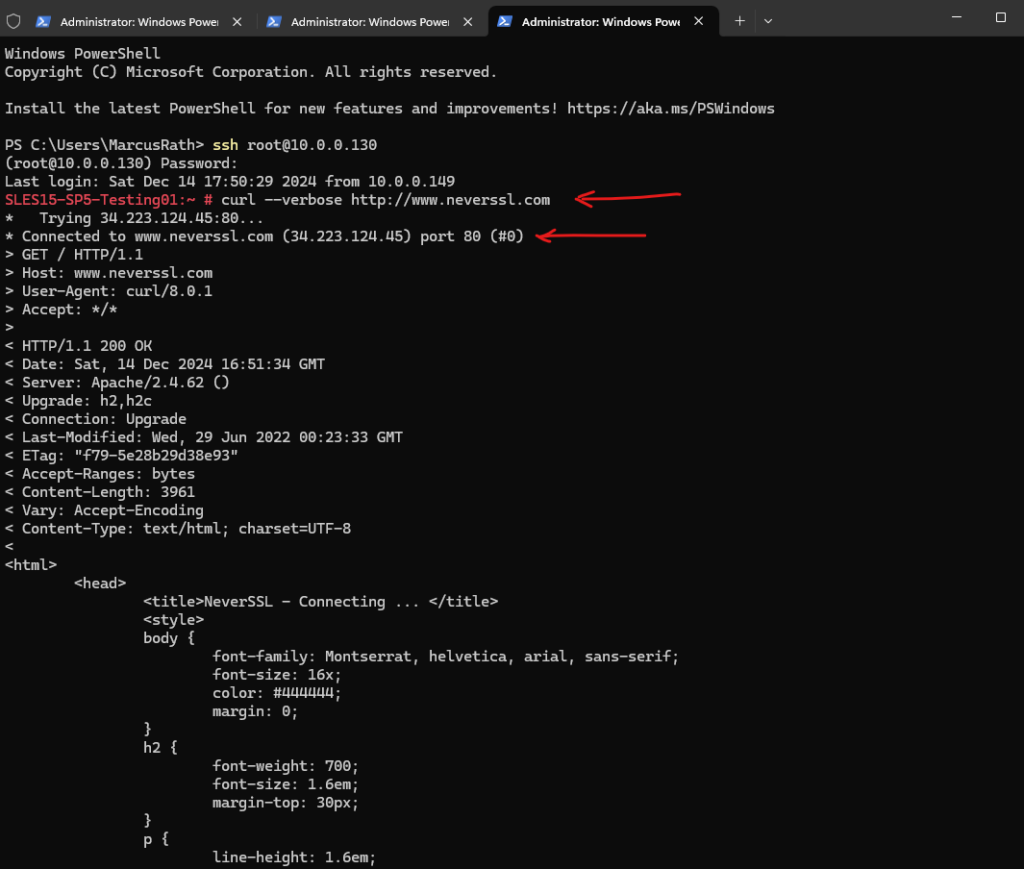
Then I will trigger the HTTP connection to http://www.neverssl.com.
Finally I will download the capture file and open it again in WireShark. Now we can also see the application layer with the HTTP protocol packets in WireShark.
Capture all Traffic from a specific Host
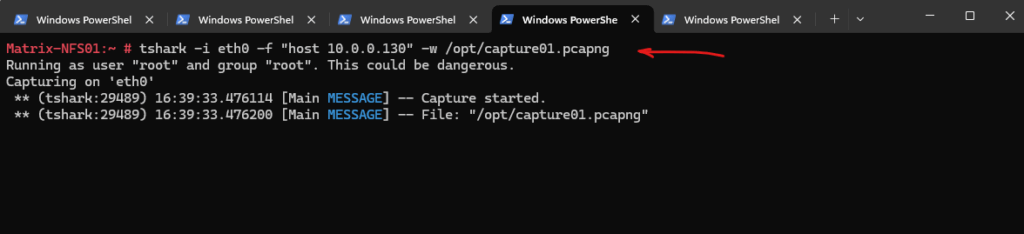
To capture all traffic just from a specific host we can use the host filter below.
# tshark -i eth0 -f "host 10.0.0.130" -w /opt/capture01.pcapng -i <interface>, --interface <interface> name or idx of interface (def: first non-loopback) -f <capture filter> packet filter in libpcap filter syntax -w <outfile|-> write packets to a pcapng-format file named "outfile"
Links
tshark: Terminal-based Wireshark
https://www.wireshark.org/docs/wsug_html_chunked/AppToolstshark.htmltshark(1) Manual Page
https://www.wireshark.org/docs/man-pages/tshark.html


