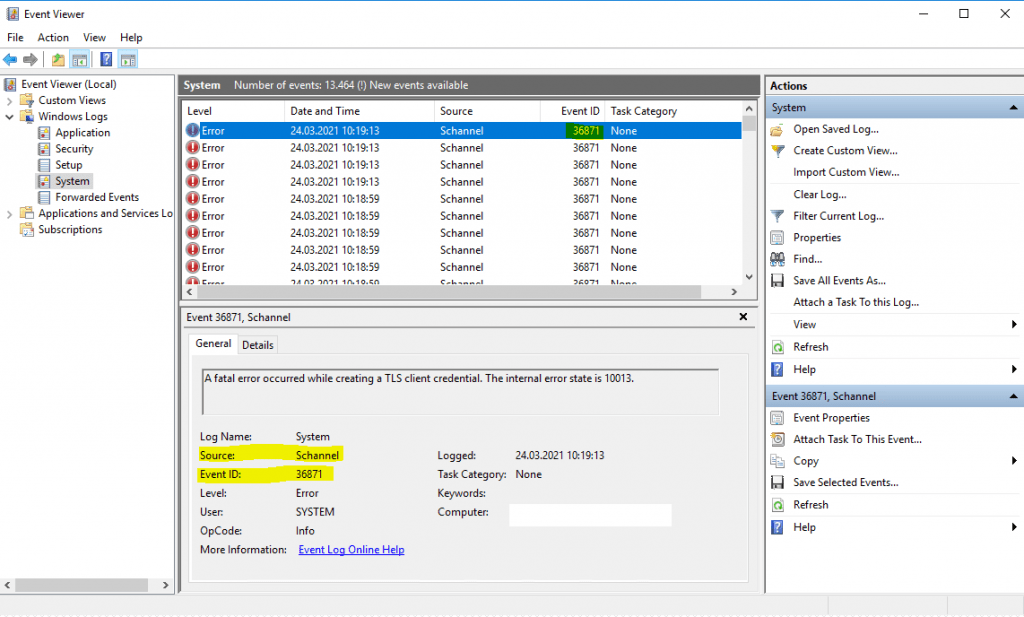
A fatal error occurred while creating a TLS client credential. The internal error state is 10013
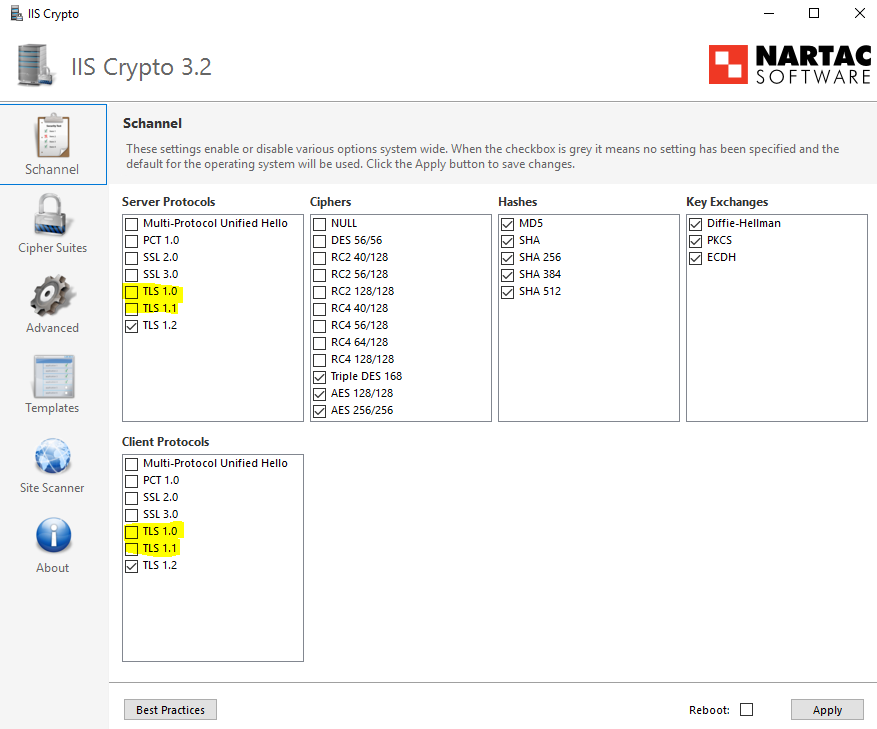
If you have disabled the deprecated server and client protocols TLS 1.0 and TLS 1.1 on your Windows Server as further down for security reasons.
https://www.chromestatus.com/feature/5759116003770368
TLS 1.2 was published ten years ago to address weaknesses in TLS 1.0 and 1.1 and has enjoyed wide adoption since then. These old versions of TLS rely on MD5 and SHA-1, both now broken, and contain other flaws. TLS 1.0 is no longer PCI-DSS compliant and the TLS working group has adopted a document to deprecate TLS 1.0 and TLS 1.1.
Modernizing Transport Security
https://security.googleblog.com/2018/10/modernizing-transport-security.html
IIS Crypto
https://www.nartac.com/Products/IISCrypto/
Restrict the use of certain cryptographic algorithms and protocols in Schannel.dll
https://docs.microsoft.com/en-US/troubleshoot/windows-server/windows-security/restrict-cryptographic-algorithms-protocols-schannel
What is Schannel.dll?
https://www.ssl.com/how-to/choose-the-right-cipher-suites-in-schannel-dll/
Schannel.dll is a library that is the main Microsoft TLS / SSL Security Provider. It stands for Secure Channel and is used by Microsoft Web Servers, including Windows Server 2003, Windows Server 2008, Windows 7, Windows Server 2008 R2 and others, including older ones like Windows XP and Windows NT even.
And after that you will see a bunch of error messages as in the title of this post like this.
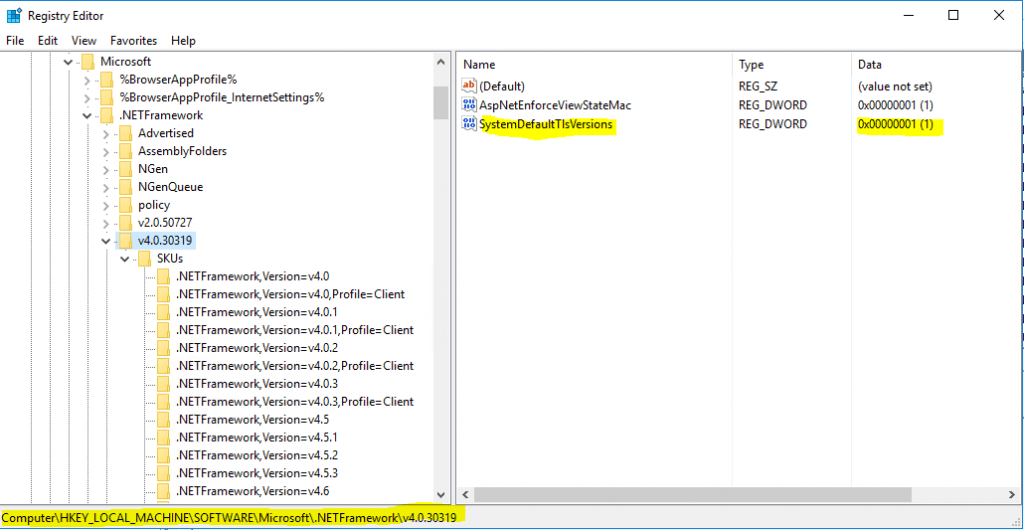
You have to add the following registry DWORD value like follows.
https://docs.microsoft.com/en-us/dotnet/framework/network-programming/tls#systemdefaulttlsversions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319
“SystemDefaultTlsVersions”=dword:00000001
This registry key has a value of type DWORD. A value of 1 causes your app to allow the operating system to choose the protocol. A value of 0 causes your app to use protocols picked by the .NET Framework.
If your app targets .NET Framework 4.7 or later versions, this key defaults to a value of 1. That’s a secure default that we recommend. If your app targets .NET Framework 4.6.1 or earlier versions, the key defaults to 0. In that case, you should explicitly set its value to 1.
To ensure .NET Framework applications remain secure, the TLS version should not be hardcoded. .NET Framework applications should use the TLS version the operating system (OS) supports.
So in case of our error messages, .NET Framework was trying to use one of the disabled TLS 1.0 or TLS 1.1 client protocols. Now after setting SystemDefaultTlsVersions to 1, the operating system is now choosing the right and available protocol instead the .NET Framework itself.
This change is for any version of .NET 4 and 64 Bit Applications.
For versions before .NET 4 you need to add the value in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFrameworkv2.0.50727
After a reboot the error messages should stay out and disappear.
For 32 Bit Applications and .Net 4 and above you need to add the value in HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319 resp. v2.0.50727 for versions before .Net 4.
https://www.advancedinstaller.com/user-guide/registry-wow6432-node.html
The Wow6432Node Registry Key is used by the operating system to display a separate view of HKEY_LOCAL_MACHINESOFTWARE for 32-bit applications that run on 64-bit Windows versions.
When a 32-bit application writes or reads a value under the HKEY_LOCAL_MACHINESOFTWARE<company><product> subkey, the application reads from the HKEY_LOCAL_MACHINESOFTWAREWow6432Node<company><product> subkey.
WoW64 (Windows 32-bit on Windows 64-bit) Subsystem
https://blog.matrixpost.net/wow64-windows-32-bit-on-windows-64-bit-subsystem/
https://docs.microsoft.com/en-us/dotnet/framework/network-programming/tls#systemdefaulttlsversions
The following .REG file sets the registry keys and their variants to their most safe values:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoft.NETFrameworkv2.0.50727] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001 [HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoft.NETFrameworkv4.0.30319] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001 [HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv2.0.50727] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001 [HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv4.0.30319] "SystemDefaultTlsVersions"=dword:00000001 "SchUseStrongCrypto"=dword:00000001
Links
Transport Layer Security (TLS) best practices with the .NET Framework
https://docs.microsoft.com/en-us/dotnet/framework/network-programming/tls
IIS Crypto
https://www.nartac.com/Products/IISCrypto/
Modernizing Transport Security
https://security.googleblog.com/2018/10/modernizing-transport-security.html
Related Posts
Follow me on LinkedIn


