Active Directory Cheat Sheet essential Commands
Active Directory (AD) is the backbone of identity and access management in most enterprise Windows environments.
Whether you’re managing users, diagnosing authentication issues, or querying domain controllers, knowing the right commands can save valuable time.
This cheat sheet provides a concise list of essential AD commands for system administrators, covering domain info, user and group management, trust verification, and troubleshooting tools.
Ideal for quick reference on domain-joined machines, this guide helps streamline common AD tasks from the command line or PowerShell.
I will update this post regularly.
- List all Domain Controllers in the Domain from a Member Server
- Determine if Computer is joined to an Domain (on-premise, Entra ID, Hybrid)
- Determine the Logon Server (Domain Controller) on a Windows Client
- Determine in which OU my Active Directory Domain Joined Computer is placed to
- Determine in which OU my Active Directory User Account is placed to
- Determine FSMO Role Holder
- The trust relationship between this workstation and the primary domain failed
- Links
List all Domain Controllers in the Domain from a Member Server
To list all domain controllers in the domain from a member server, you can use one of the following methods:
PS> nltest /dclist:<domain name> PS> nltest /dclist:matrixpost-lab.net
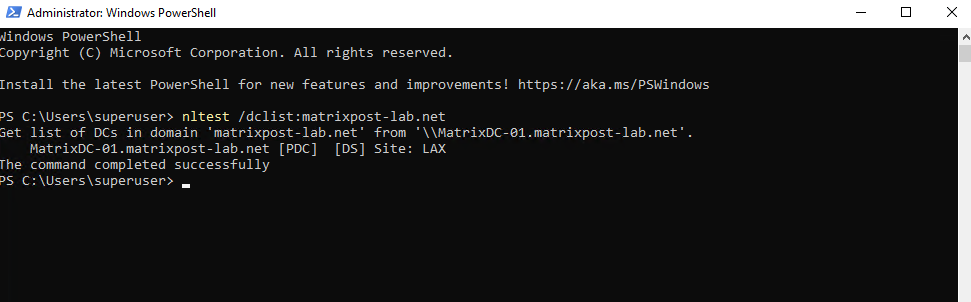
Or by using DNS Query.
> nslookup > set type=SRV _ldap._tcp.dc._msdcs.<YourDomainName>
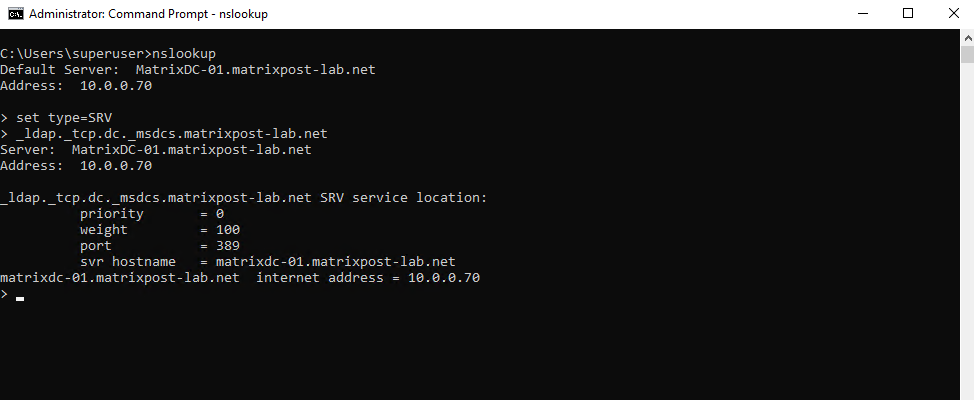
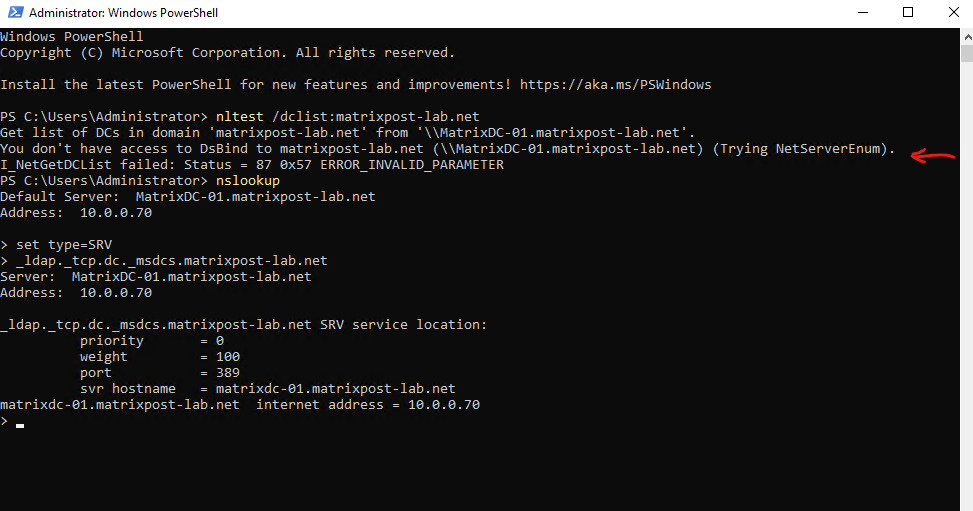
Querying DNS will also work by the way in case you just have a local user account on the domain member server, therefore are not signed in to the domain, in this case the previous nltest /dclist command will fail like shown below.
You don’t have access to DsBind to matrixpost-lab.net (\MatrixDC-01.matrixpost-lab.net) (Trying NetServerEnum).
I_NetGetDCList failed: Status = 87 0x57 ERROR_INVALID_PARAMETER
Determine if Computer is joined to an Domain (on-premise, Entra ID, Hybrid)
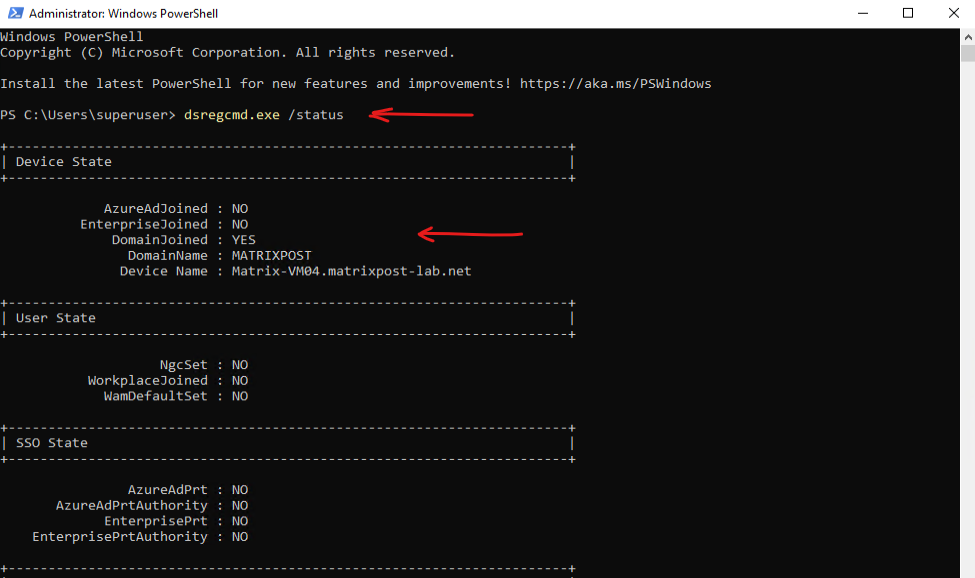
To quickly determine if a computer is joined to a domain (on-premise, Entra ID or hybrid) we can execute the following command in the PowerShell or CMD with elevated Administrator rights.
The dsregcmd.exe /status command is a useful diagnostic tool in Windows for checking the device’s Entra ID join status and related registration details. It provides information such as domain join type, user state, SSO (Single Sign-On) status, and other relevant Entra ID connectivity details. This command is particularly helpful for troubleshooting authentication, device registration, and hybrid join issues in enterprise environments. Running it displays a summary of the device’s Entra ID and domain registration state.
> dsregcmd.exe /status
Determine the Logon Server (Domain Controller) on a Windows Client
When a Windows computer joins a domain, it authenticates against a Domain Controller (DC), known as the logon server. There are several ways to find the Logon Server against the client authenticated.
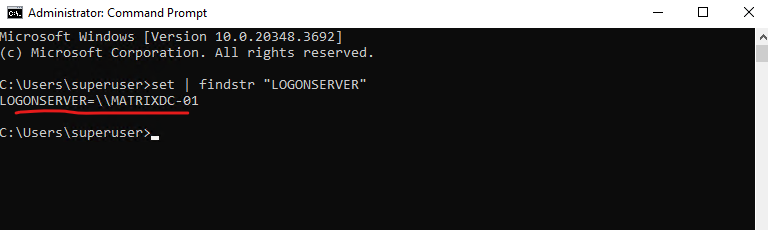
By using the legacy CMD command set, just works when using the CMD (Command Prompt).
> set | findstr "LOGONSERVER"
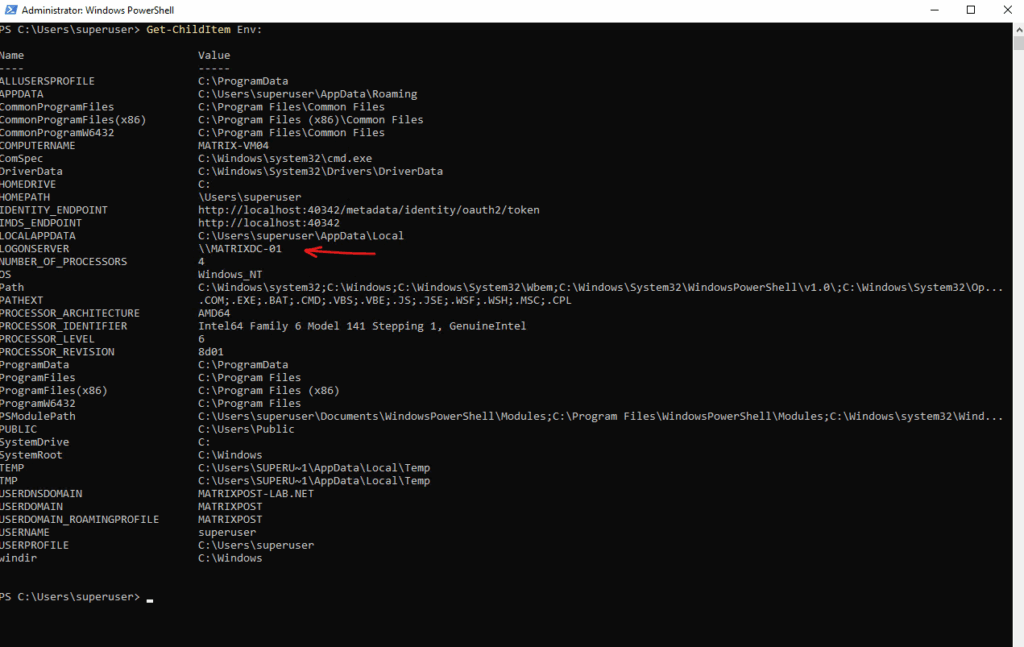
The PowerShell equivalent is.
PS> Get-ChildItem Env:
PS> Get-ChildItem Env: | Where-Object { $_.Name -like "*LOGON*" -or $_.Name -like "*DOMAIN*" -or $_.Name -like "*USER*" }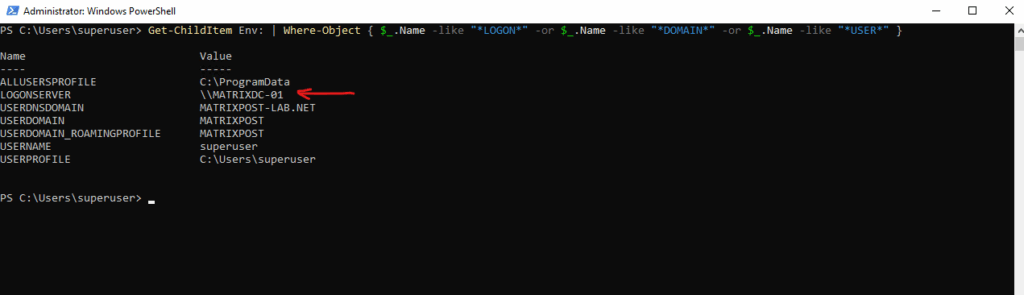
By using the nltest command/utility used for testing and troubleshooting Active Directory (AD) domain relationships, trust configurations, and Domain Controller (DC) communications.
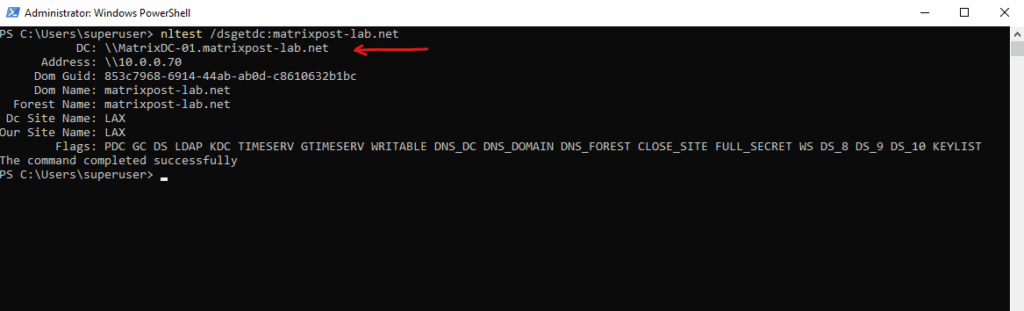
PS> nltest /dsgetdc:YOURDOMAIN.COM
Below the DC: \\MatrixDC-01.matrixpost-lab.net show the logon server which was used by the client.
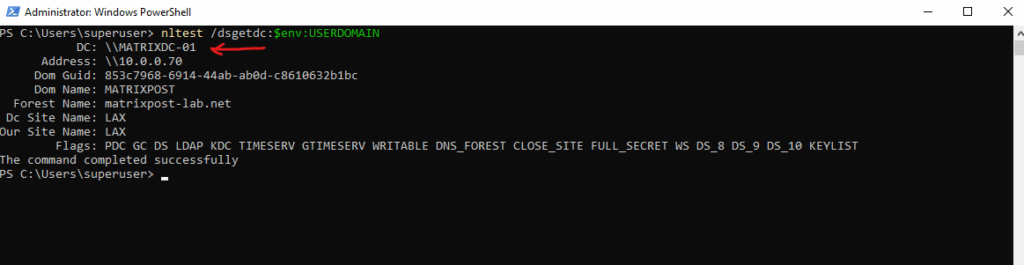
PS> nltest /dsgetdc:$env:USERDOMAIN
Determine in which OU my Active Directory Domain Joined Computer is placed to
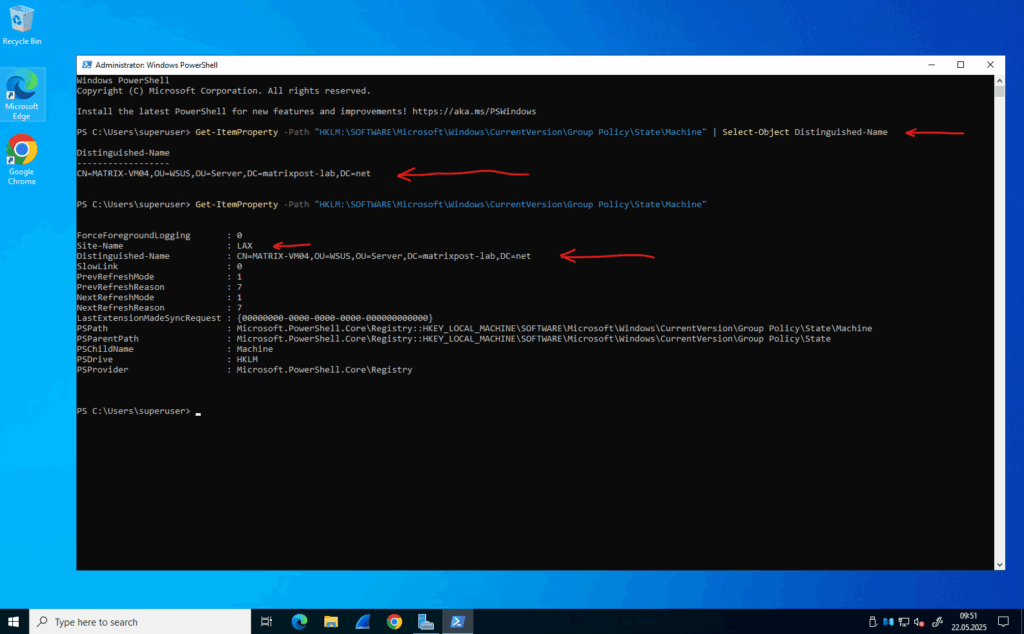
To determine directly on a Active Directory domain joined computer in which OU it is placed to, we can run the following PowerShell command.
PS> Get-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy\State\Machine" | Select-Object Distinguished-Name PS> Get-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy\State\Machine"
Determine in which OU my Active Directory User Account is placed to
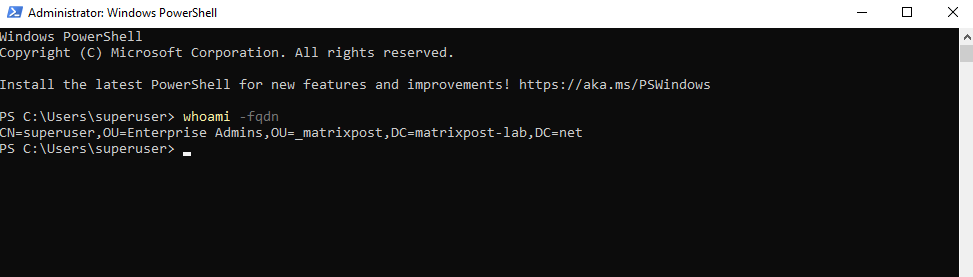
We can run the following command which displays the user name in Fully Qualified
Distinguished Name (FQDN) format.
> whoami -fqdn
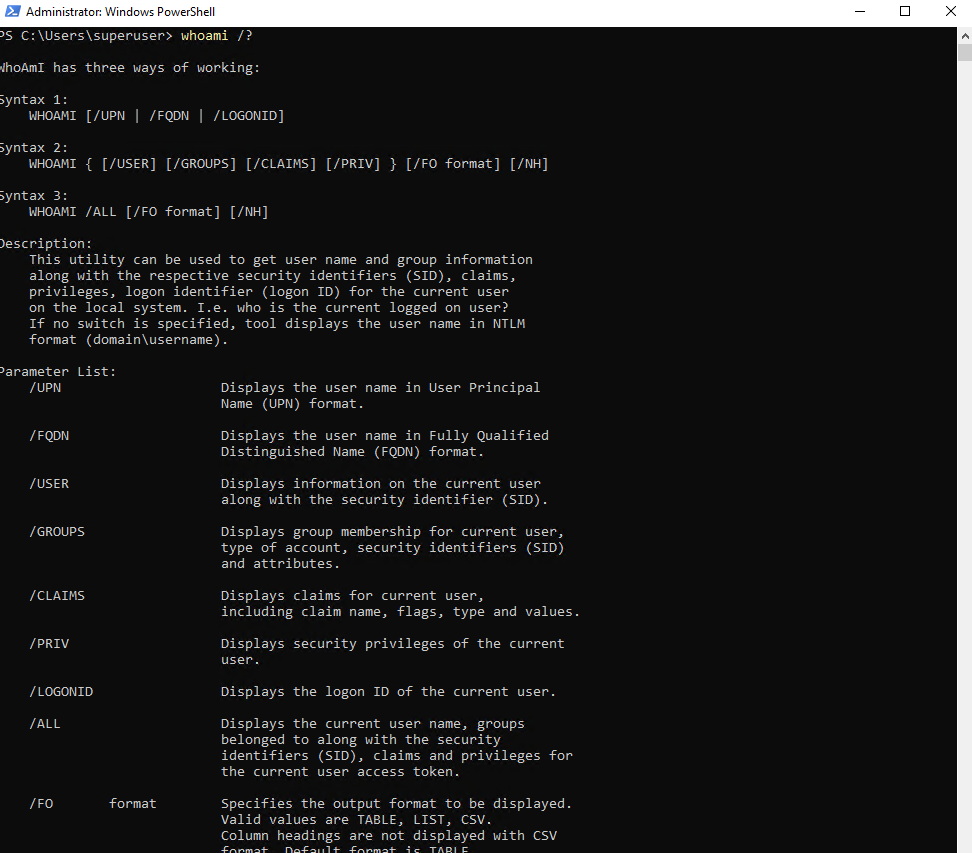
More you will find by display the help information for the whoami command.
> whoami /?
More about general essential Windows commands you will find in my following post.
Determine FSMO Role Holder
In Active Directory, certain tasks can only be performed by specific domain controllers called FSMO role holders. There are 5 such roles, each responsible for critical operations like schema updates, domain additions, time synchronization, and object creation.
FSMO role (Flexible Single Master Operation role)
To determine which specific domain controller holds which specific FSMO role we can run the following two commands. So in my lab environment I have so far just one domain controller running and therefore is holding all 5 FSMO roles.
PS> Get-ADDomain | Select-Object InfrastructureMaster, RIDMaster, PDCEmulator PS> Get-ADForest | Select-Object DomainNamingMaster, SchemaMaster
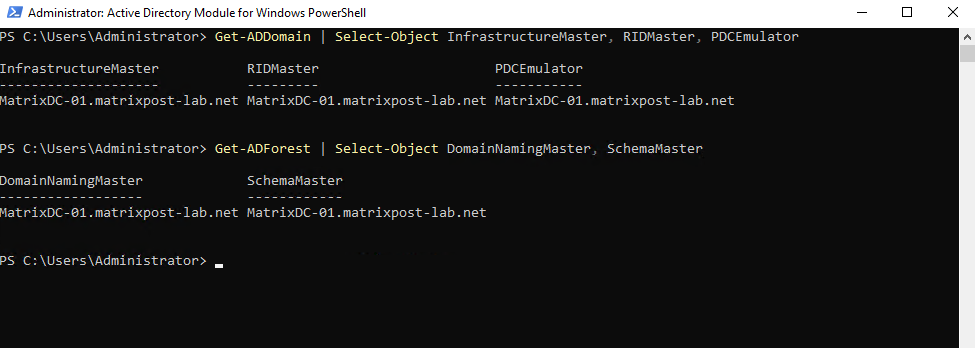
Forest-wide roles (1 per forest)
- Schema Master ==> Controls changes to the AD schema (e.g., extending for Exchange/Skype/Defender). Rarely used, but critical during schema updates.
- Domain Naming Master ==> Handles adding/removing domains in the forest. Only needed when creating or deleting domains.
Domain-wide roles (1 per domain)
- PDC Emulator ==> Most important role. Acts as: Time source for the domain, Handles password changes and authentication fallback, Legacy NT4 compatibility. Usually the busiest FSMO role.
- RID Master ==> Issues unique ID pools (RIDs) to DCs so they can create security principals (users, groups, computers). Without it, you can’t create new objects once the pool is exhausted.
- Infrastructure Master ==>Updates references to objects across domains (group memberships etc.). Important only in multi-domain forests.
The trust relationship between this workstation and the primary domain failed
Links
Set command
https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/set_1


