How to onboard on-premise Server to Azure Arc
Managing diverse infrastructure across on-premises data centers, edge locations, and multiple cloud providers can be complex.
This is where Azure Arc comes in. Microsoft Azure Arc extends the power of Azure management and security to any infrastructure, whether it’s running on-premises, in AWS, Google Cloud, or at the edge.
With Azure Arc, businesses can centrally manage, secure, and govern servers, Kubernetes clusters, databases, and even AI workloads – bringing a unified cloud experience to any environment.
In this post I want to show step by step how you can onboard and connect your on-premise Windows Server machines (bare metal or virtual machines) to Azure Arc.
Azure Arc-enabled servers lets you manage Windows and Linux physical servers and virtual machines hosted outside of Azure, on your corporate network, or other cloud provider. For the purposes of Azure Arc, these machines hosted outside of Azure are considered hybrid machines. The management of hybrid machines in Azure Arc is designed to be consistent with how you manage native Azure virtual machines, using standard Azure constructs such as Azure Policy and applying tags.
When a hybrid machine is connected to Azure, it becomes a connected machine and is treated as a resource in Azure. Each connected machine has a Resource ID enabling the machine to be included in a resource group.
To connect hybrid machines to Azure, you install the Azure Connected Machine agent on each machine.
Source: https://learn.microsoft.com/en-us/azure/azure-arc/servers/overview
We also need to onboard our on-premise machines to Azure Arc in case we want to protect them by using Microsoft Defender for Cloud resp. Microsoft Defender for Servers. More about how to onboard them to Microsoft Defender for Servers you will find in my following post.
Onboarding Windows on-premise Server to Azure Arc
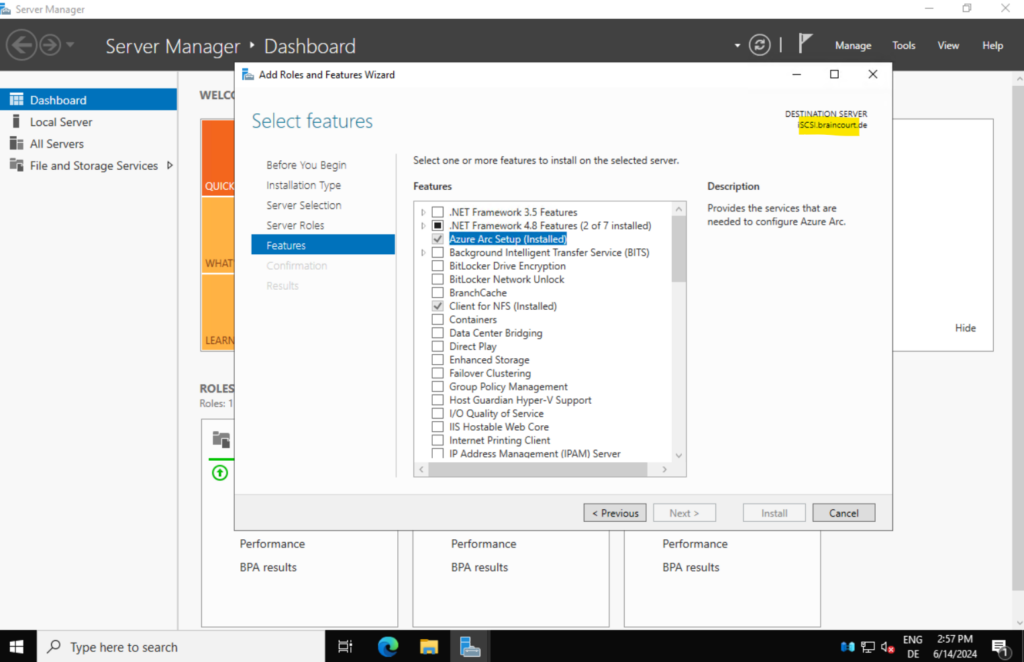
We can onboard Windows Server 2022 and later directly to Azure Arc by using a graphical wizard installed as a feature by default.
The Azure Arc Setup wizard is launched from a system tray icon at the bottom of the Windows Server machine when the Azure Arc Setup feature is enabled. This feature is enabled by default. Alternatively, you can launch the wizard from a pop-up window in the Server Manager or from the Windows Server Start menu.
Source: https://learn.microsoft.com/en-us/azure/azure-arc/servers/onboard-windows-server
For Windows Server 2022, Azure Arc Setup is an optional component that can be removed using the Remove Roles and Features Wizard. For Windows Server 2025 and later, Azure Arc Setup is a Features On Demand. Essentially, this means that the procedures for removal and enablement differ between OS versions.
Source: https://learn.microsoft.com/en-us/azure/azure-arc/servers/onboard-windows-server
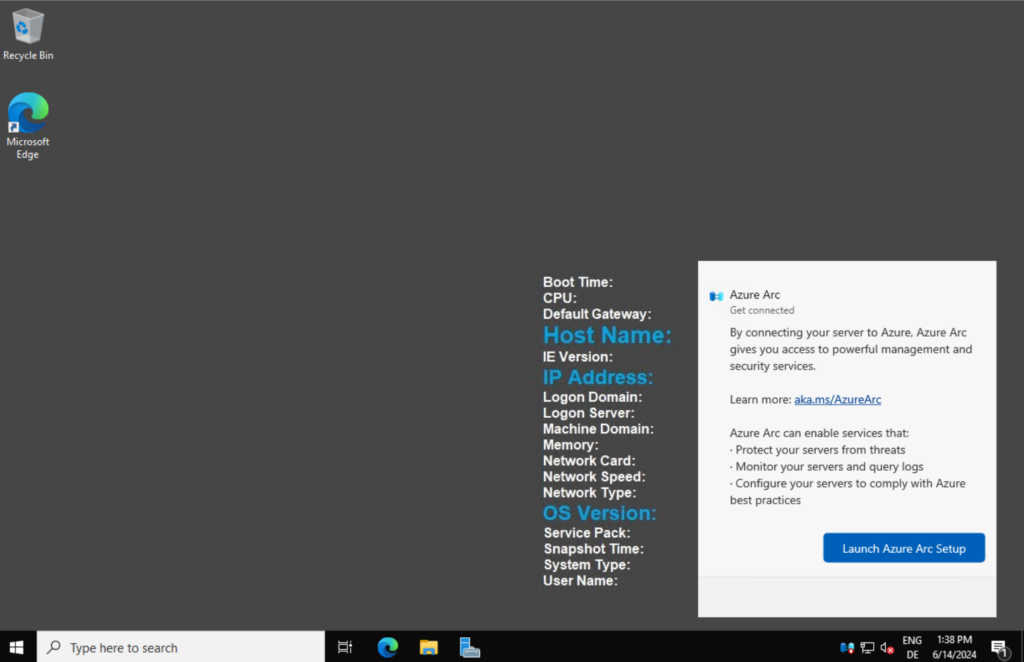
Launch the Azure Arc Setup wizard from the system tray icon as show below.
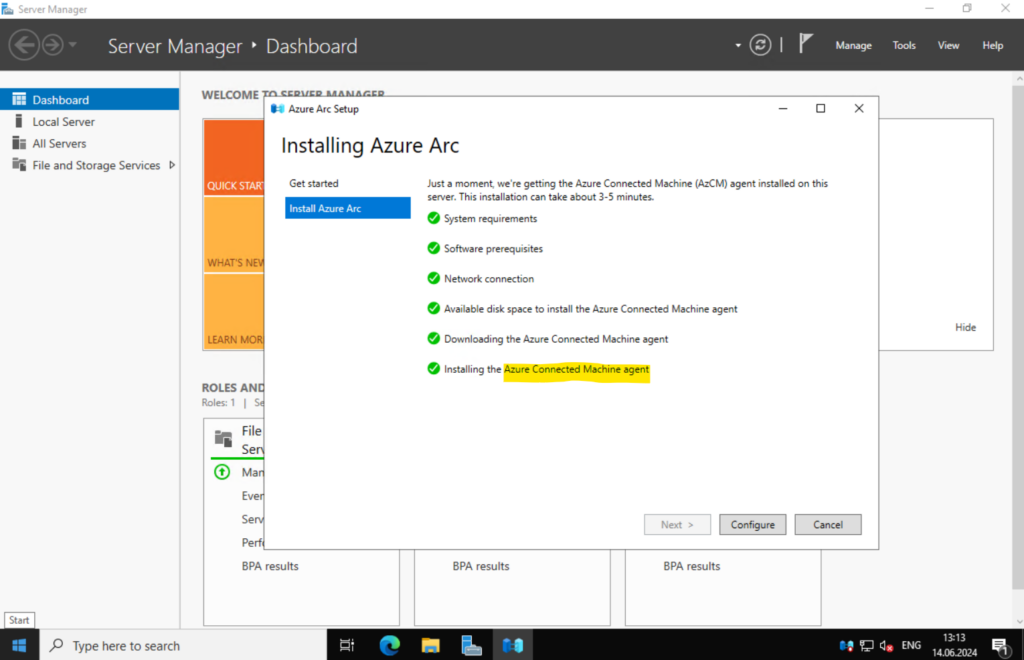
The wizard automatically checks for the prerequisites necessary to install the Azure Connected Machine agent on your Windows Server machine. Once this process completes and the agent is installed, select Configure.
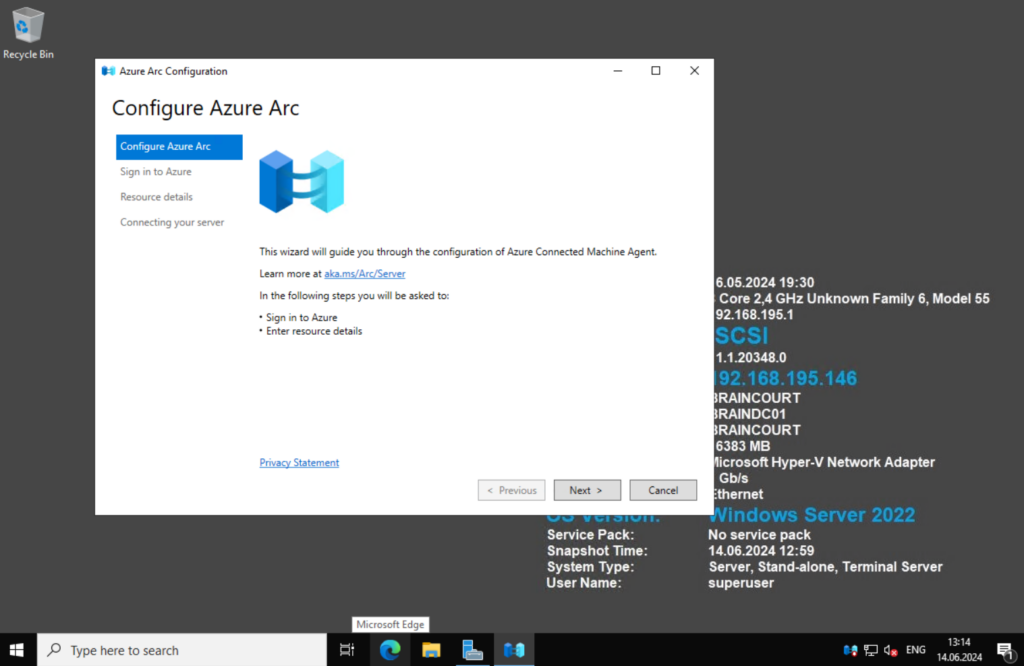
Sign-in to Azure by selecting the applicable Azure cloud, usually you will need to select Azure Global, and then selecting Sign in to Azure. You’ll be asked to provide your sign-in credentials.
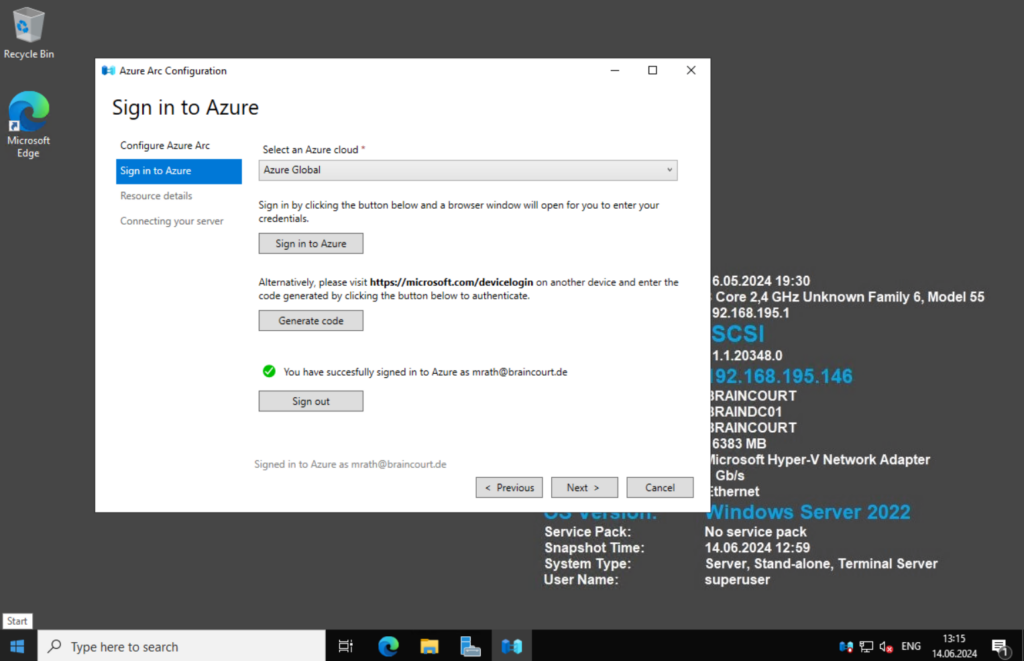
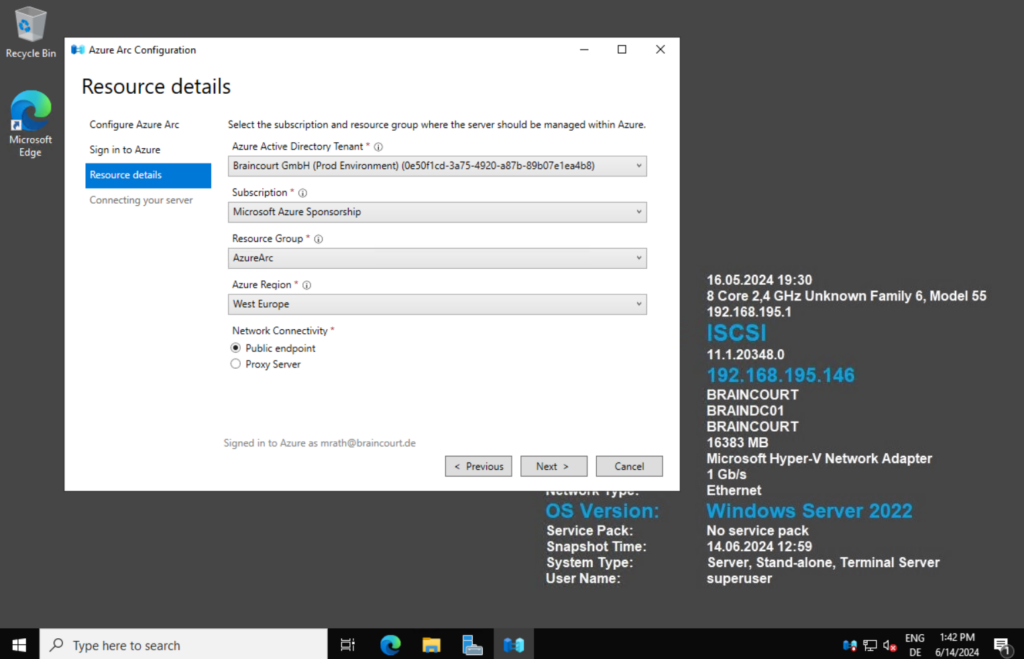
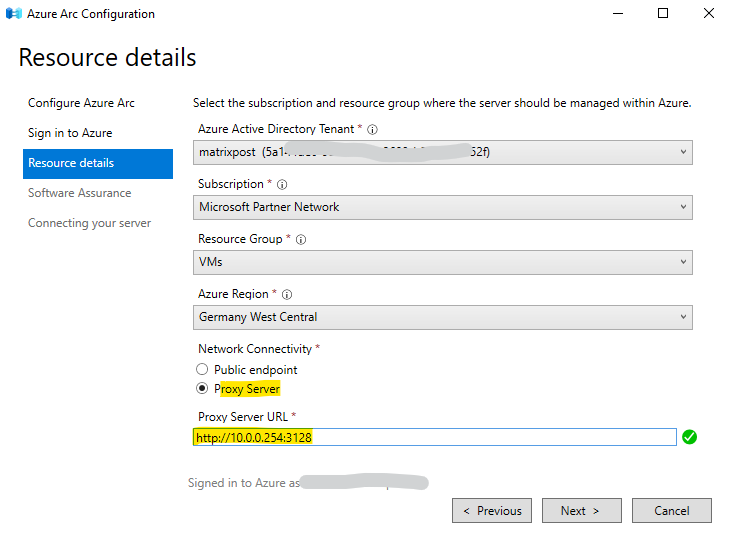
Besides the selecting our Azure tenant, subscription, resource group and region for our Azure Arc- enabled server we also need to select how the server will connect to Azure.
In my case where I have so for in my lab environment neither a site-to-site VPN nor a Azure ExressRoute, I can just choose below between a public endpoint or a proxy server which finally both will connect my server through the public internet.
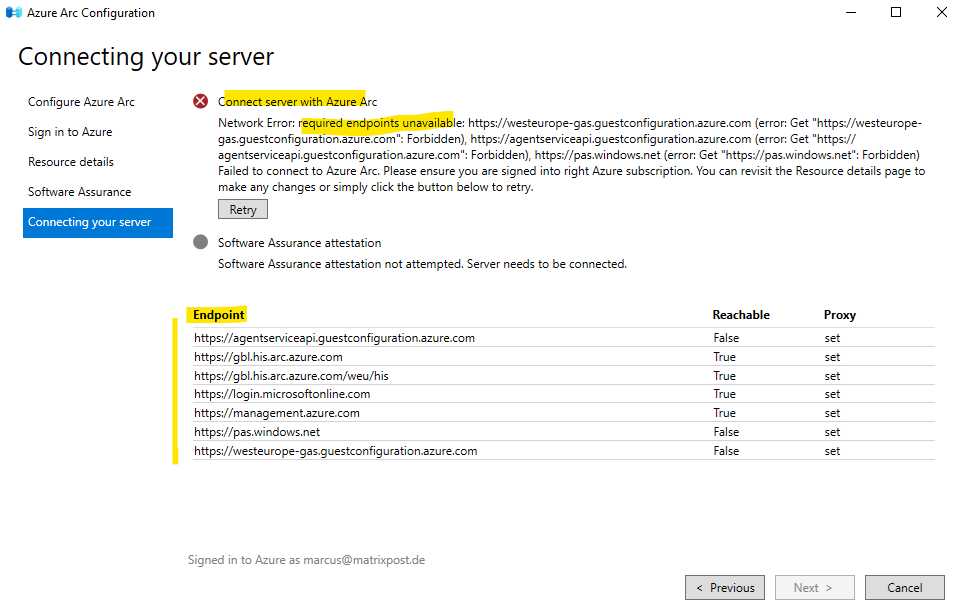
Below for example I wanted to connect an on-premise server which is configured to use a proxy to access the internet. Therefore I need to select the proxy server also on the Azure Arc Setup wizard.
In the following Microsoft article you will find all URLs under Azure Arc-enabled servers that must be available in order to install and use the Connected Machine agent.
Azure Arc network requirements
https://learn.microsoft.com/en-us/azure/azure-arc/network-requirements-consolidated?tabs=azure-cloud#urls
To check if network connectivity for the Azure Connected Machine agent is blocked you can also use the azcmagent CLI tool.
> azcmagent.exe check --location "westeurope"
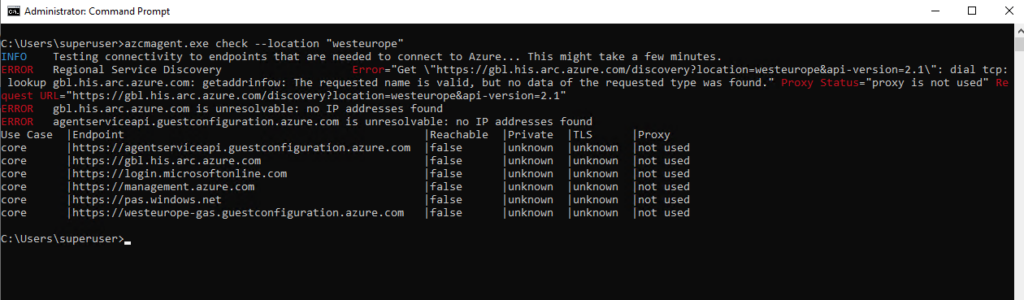
So when using a HTTP proxy, we first need to allow the required endpoints on the proxy.
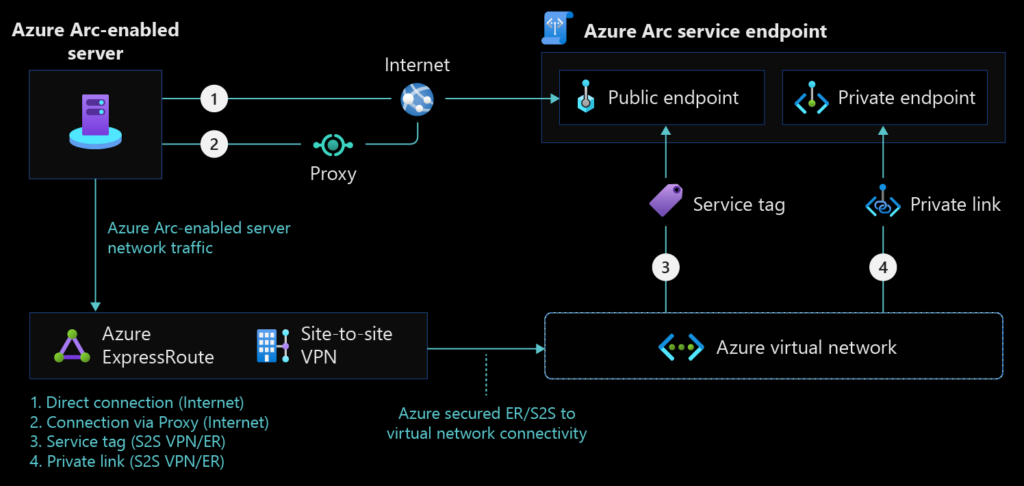
Azure Arc-enabled server also supports a site-to-site VPN or Azure ExpressRoute as shown in the figure below.
Use Azure Private Link to securely connect servers to Azure Arc
https://learn.microsoft.com/en-us/azure/azure-arc/servers/private-link-security
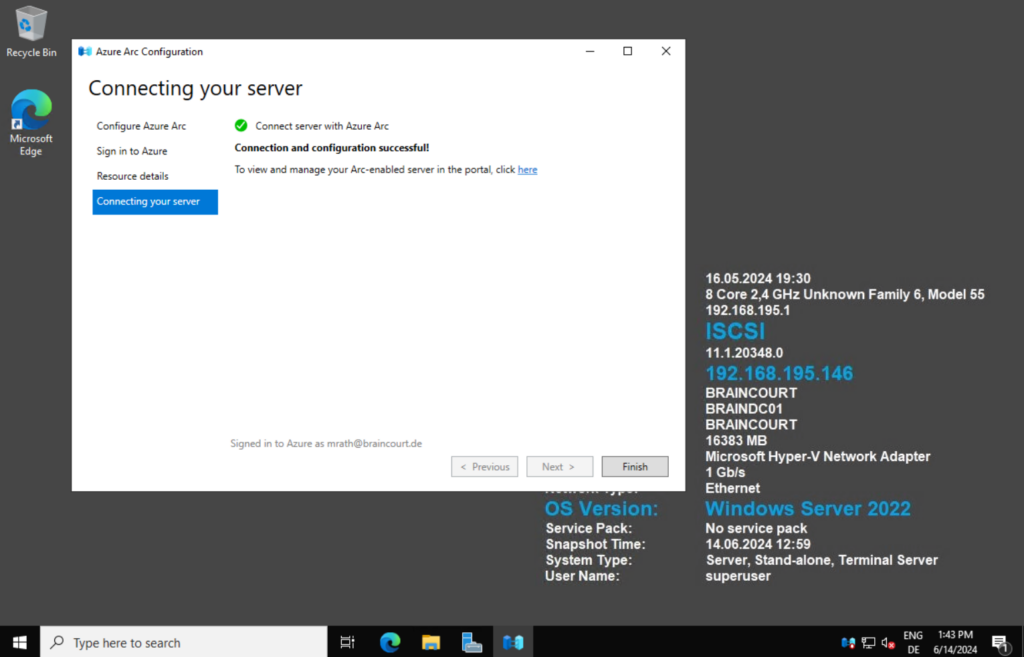
Once the configuration completes and your machine is onboarded to Azure Arc, select Finish.
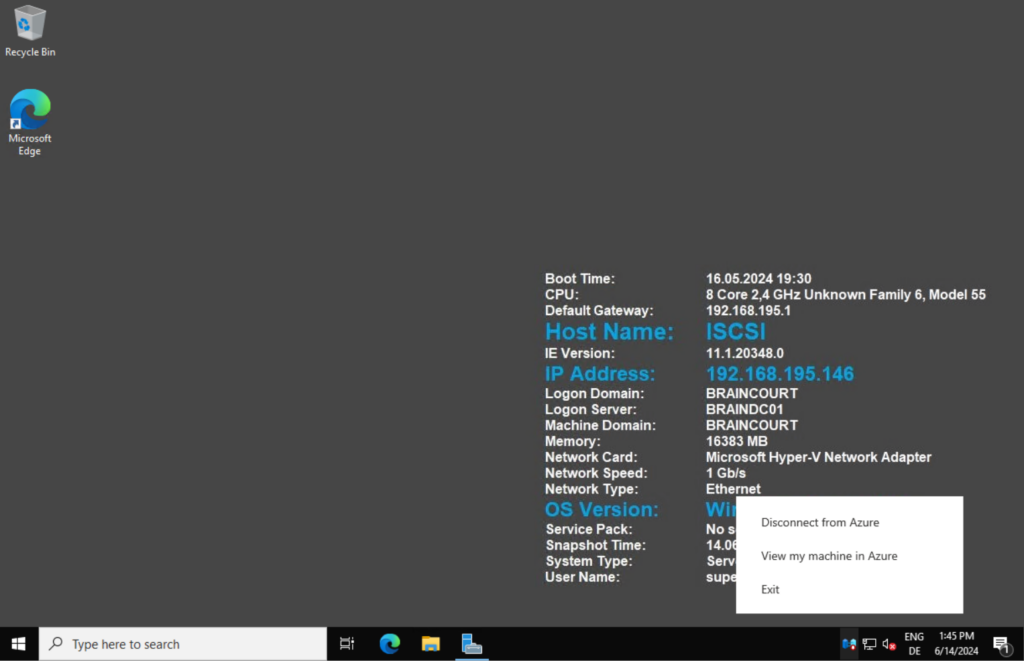
When the on-premise server finally is connected to Azure Arc, the icon in the system tray changes like shown below. Further you will see the status of the server in the Azure Arc Management field of the Server Manager on Windows Server 2022 or later.
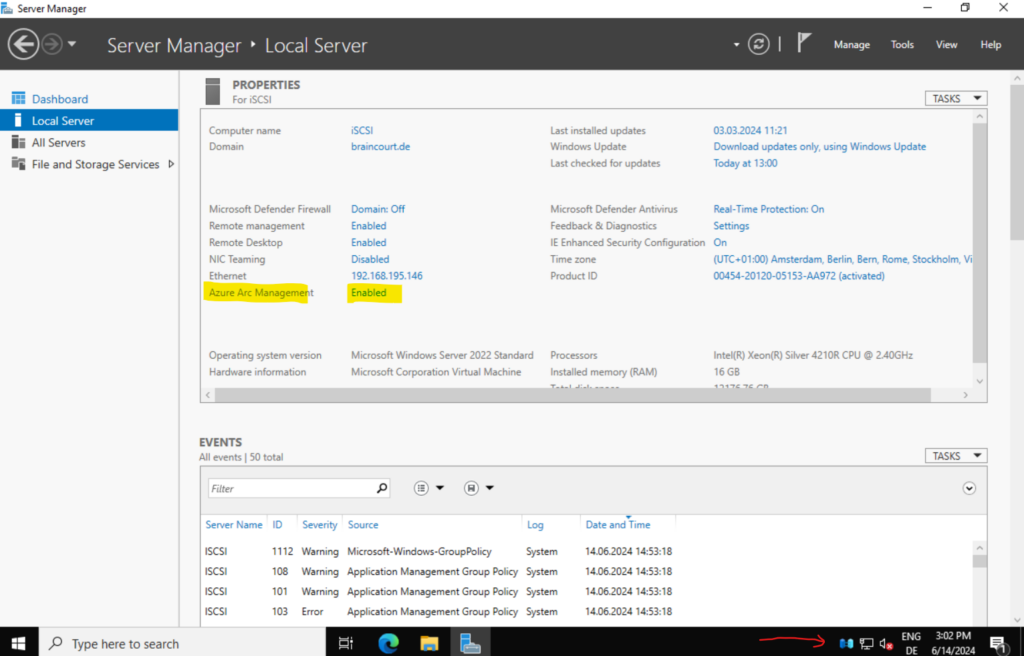
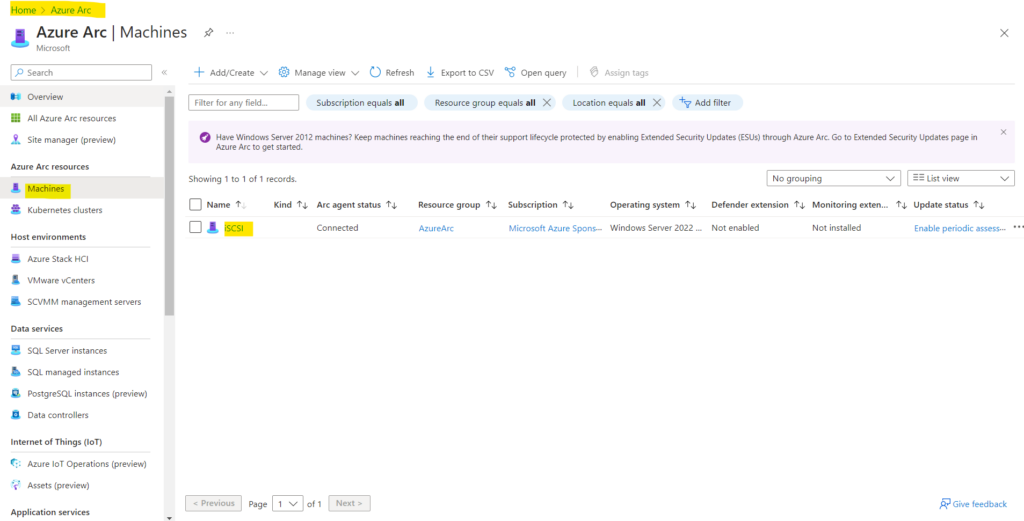
Onboarding Linux on-premise Server to Azure Arc
In the Azure portal navigate to Navigate to Machines – Azure Arc.
On the Machines – Azure Arc page, select Add/Create at the upper left, and then select Add a machine from the drop-down menu.
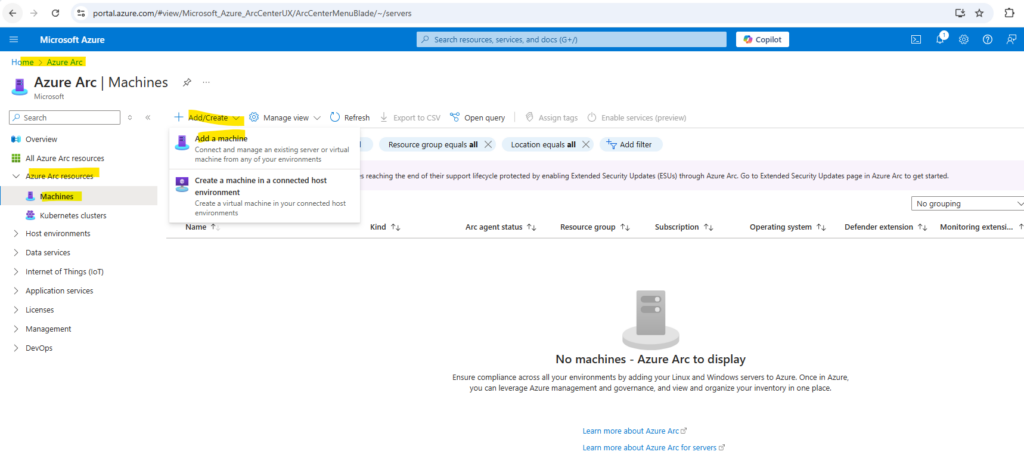
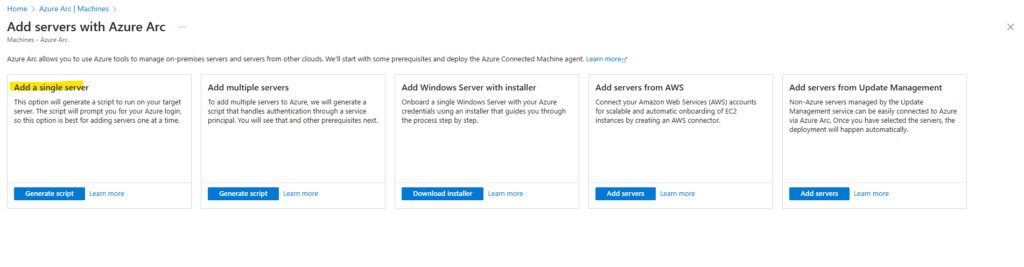
On the Add servers with Azure Arc page, select either the Add a single server or Add multiple servers depending on your deployment scenario, and then select Generate script.
Select Add a single server below. Click on Generate script.
About how to add multiple servers you can read my following post https://blog.matrixpost.net/how-to-onboard-on-premise-server-to-azure-arc-by-using-a-site-to-site-ipsec-vpn-and-azure-arc-private-link-scope/#adding_multiple_servers. Here I will show how to onboard them by using Azure Arc Private Link Scope but the process to add multiple servers are finally the same for using a public endpoint like here instead a private endpoint like shown in this post.
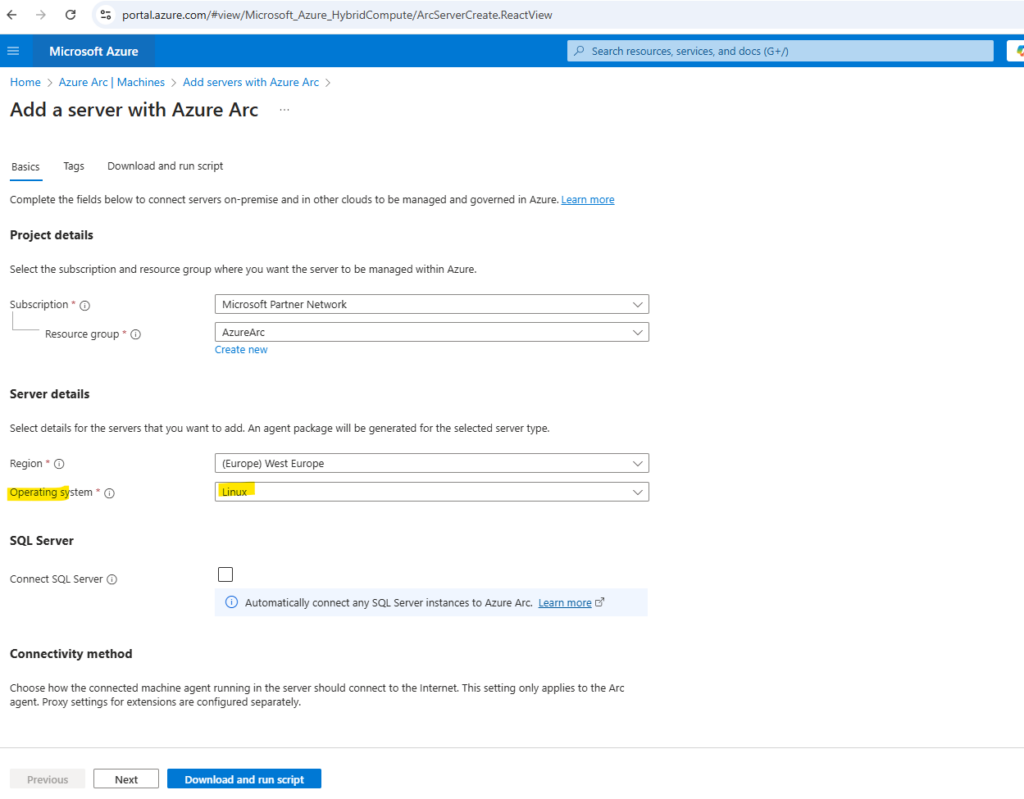
Under Operating System we can choose between Windows and Linux. We want to onboard a Linux machine below.
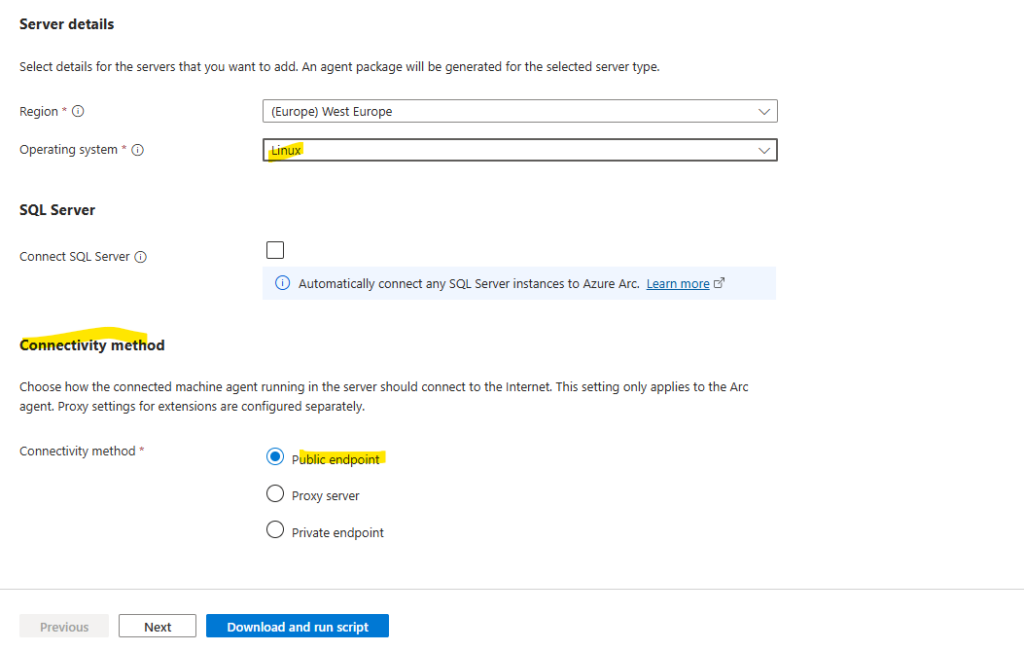
At the bottom of the Basics tab we can configure the connectivity method for the Azure Connected Machine agent.
We will use here a public endpoint to connect to Azure Arc. In case our client machine is connected to the Internet by using a proxy server, we can choose below Proxy Server.
About connecting through a private endpoint by routing the traffic to Azure Arc through a S2S VPN tunnel or express route, you can read my following post.
Finally we can download the OnboardingScript.sh for Linux.
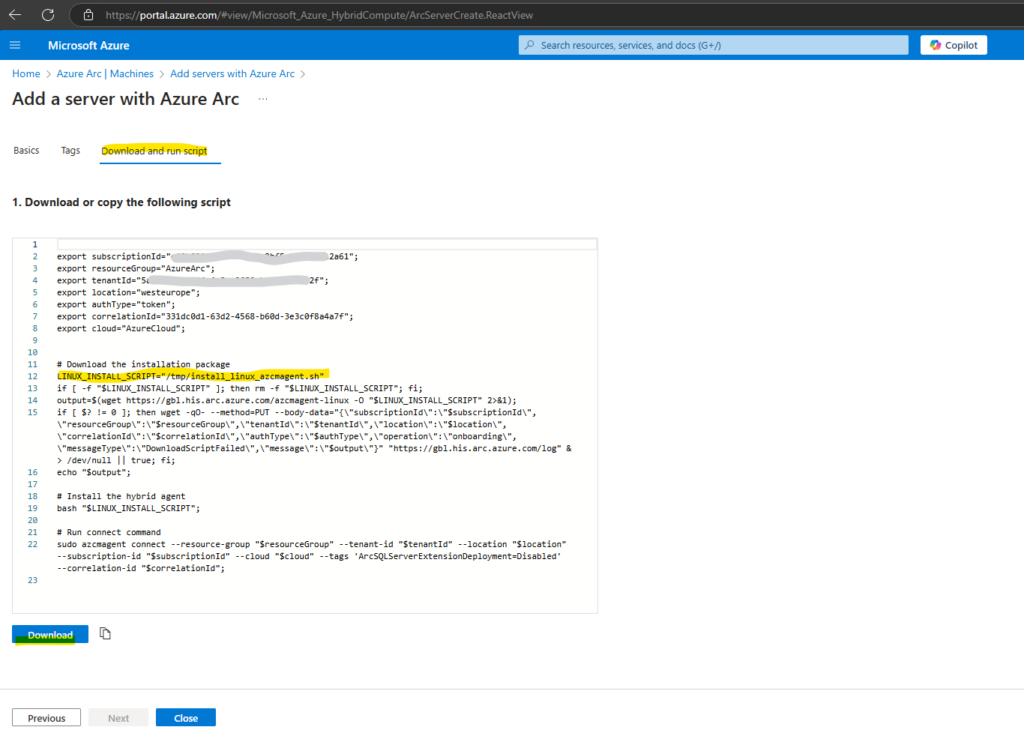
After downloading the OnboardingScript.sh script from Azure Arc, we need to upload this script to our Linux machine we want to connect to Azure Arc.
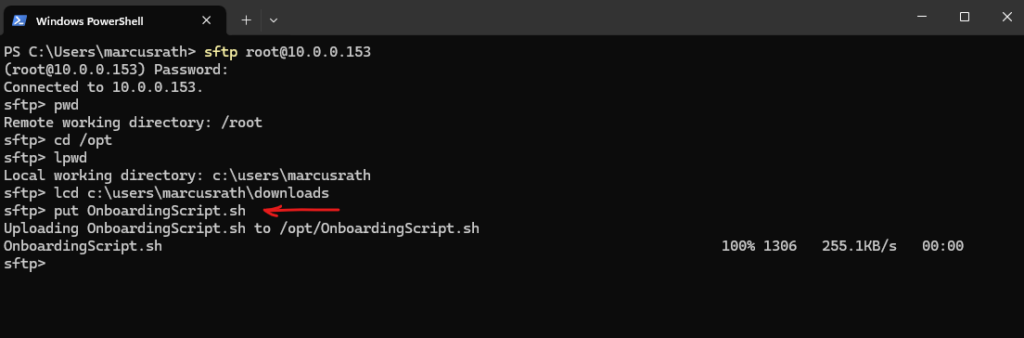
We can now either just run bash OnboardingScript.sh or first make the script explicitly executable to use ./OnboardingScript.sh.
More about using different methods to execute a shell script in Linux you will find in my following post https://blog.matrixpost.net/linux-executing-shell-scripts-different-ways/.
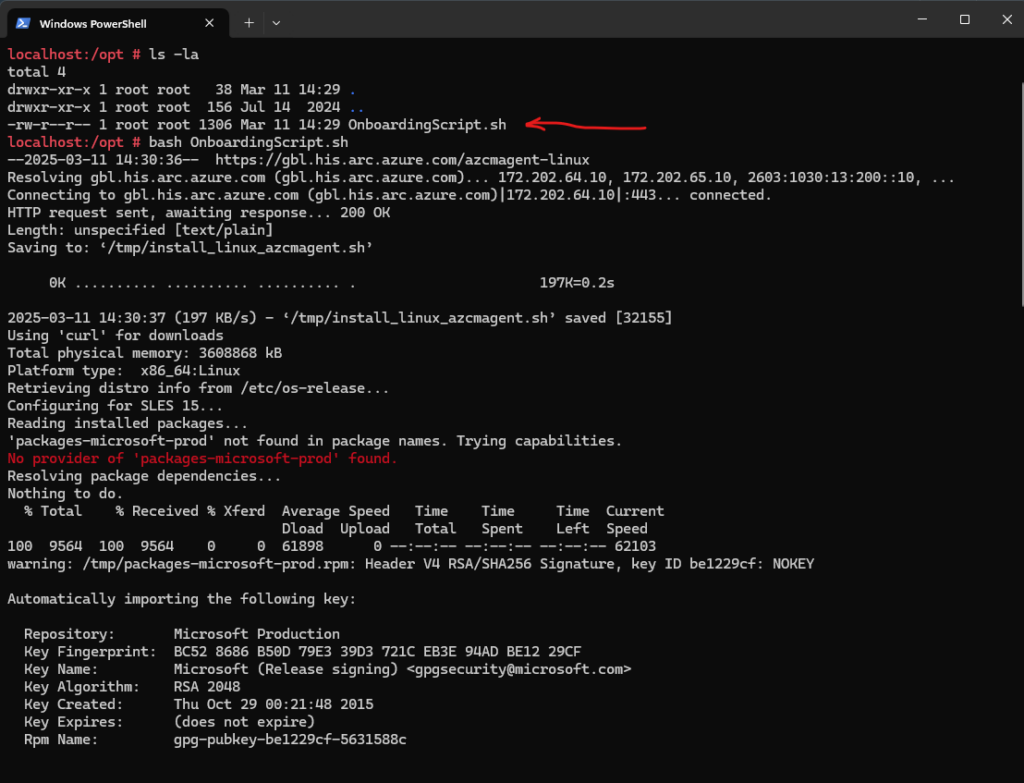
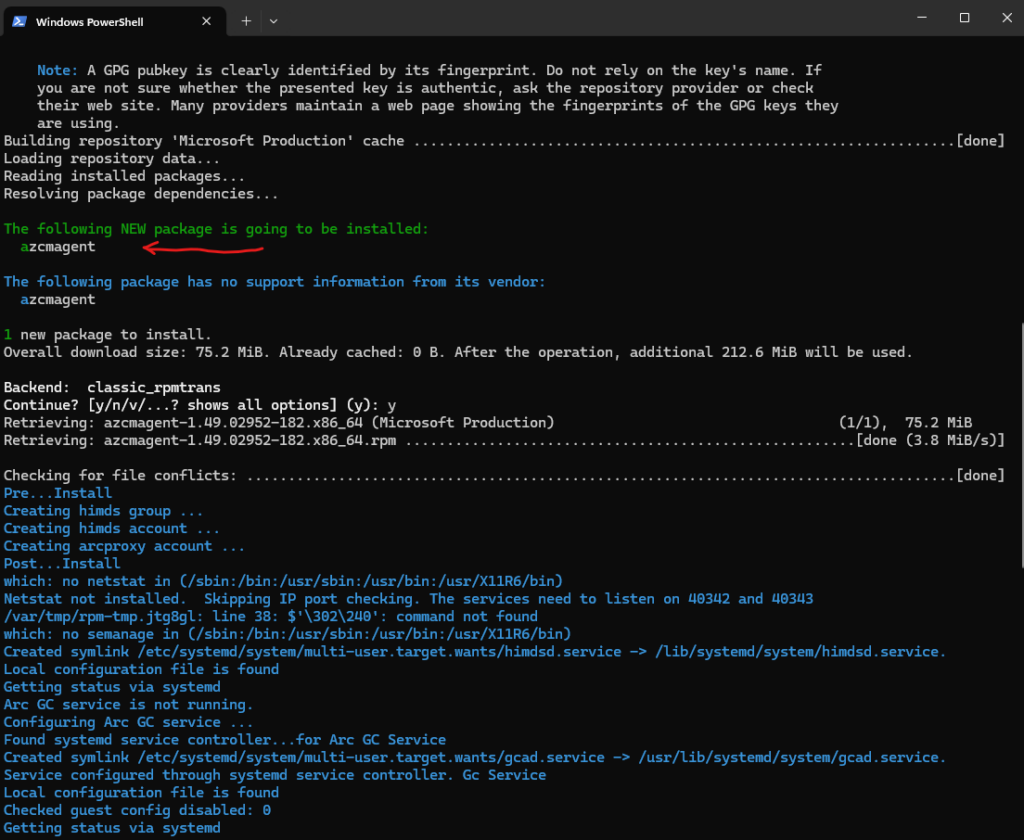
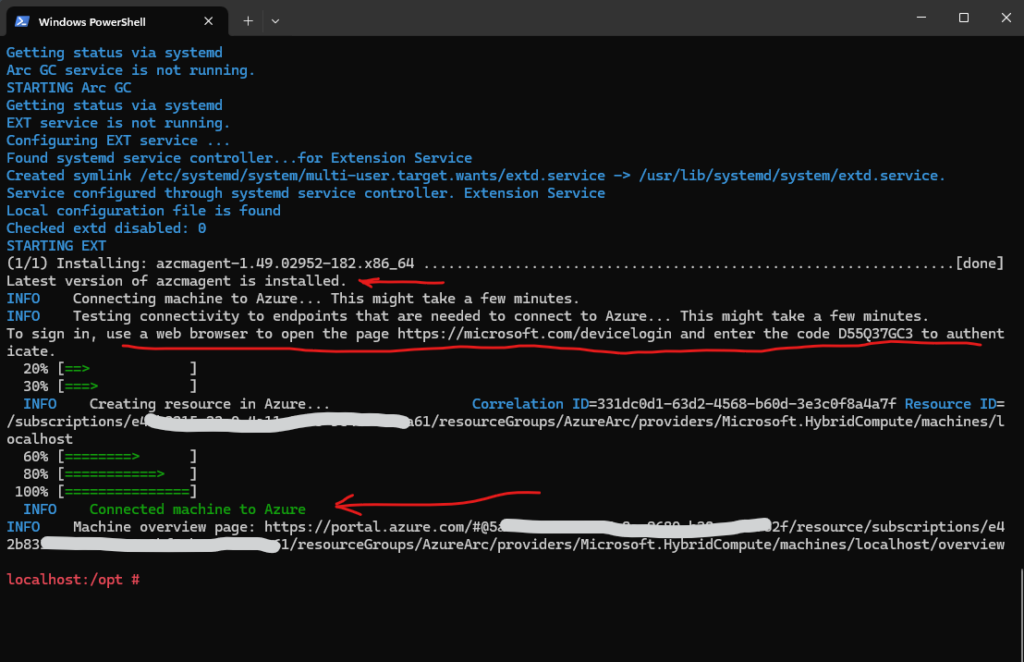
Looks good besides I forgot to rename the hostname of this virtual machine and now appears in Azure Arc as localhost.
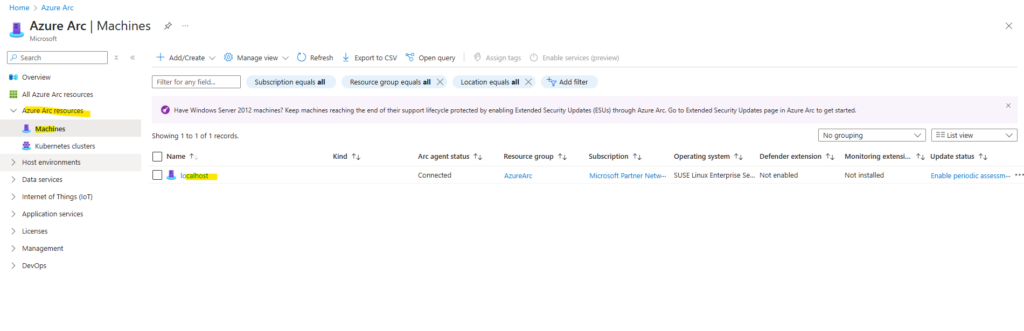
The Azure Arc-enabled servers deployment script generated in the portal downloads the latest version.
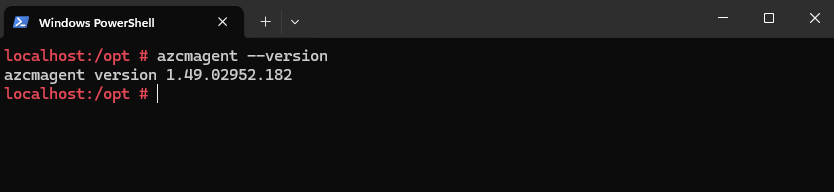
The version of the Azure Connected Machine agent you can determine by running the following command on the affected server.
# azcmagent --version
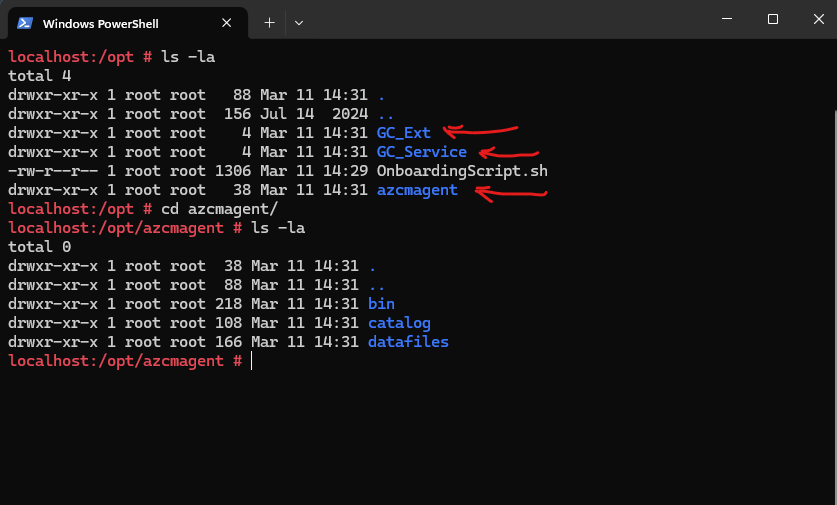
Finally the following three new folders will be created during the installation, so do not delete them by accident.
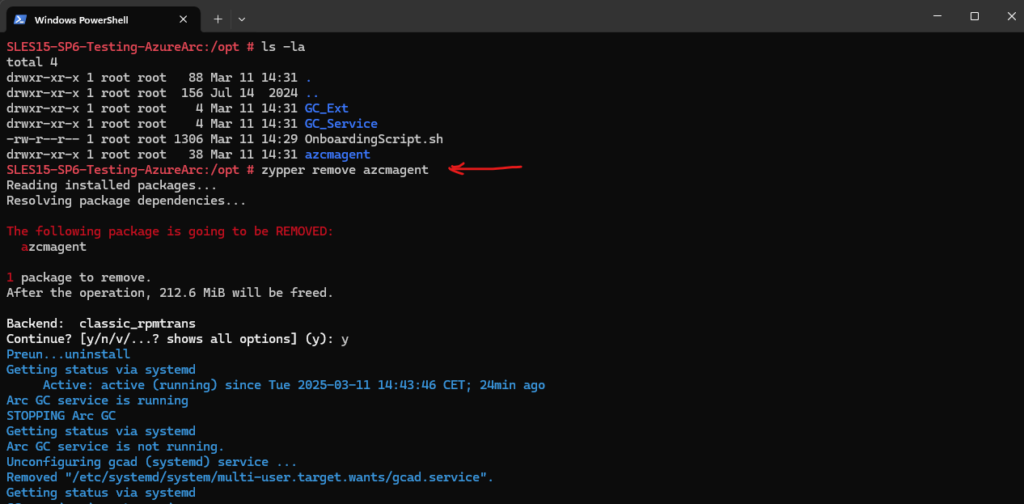
To remove the agent we can use on SLES the zypper command.
# zypper remove azcmagent
Onboarding Windows on-premise Server to Azure Arc by using a Deployment Script
For Windows Server 2019 and before we can use a deployment script generated directly in the Azure portal as shown below.
The script to automate the download and installation, and to establish the connection with Azure Arc, is available from the Azure portal.
On the Azure Arc – Machines page, select Add/Create at the upper left, and then select Add a machine from the drop-down menu.
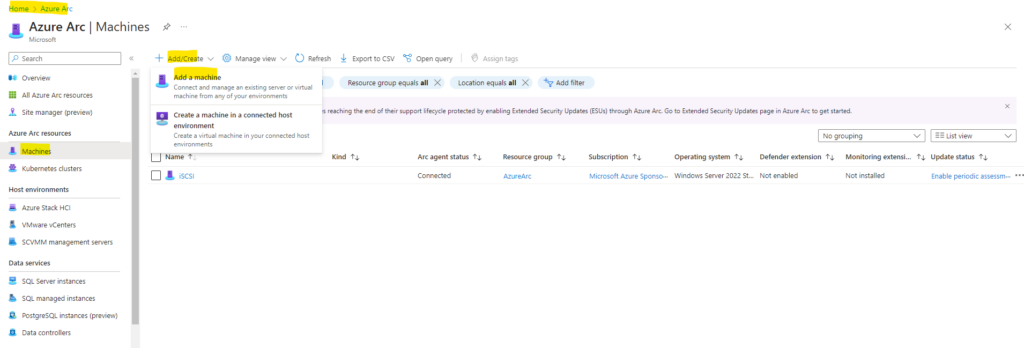
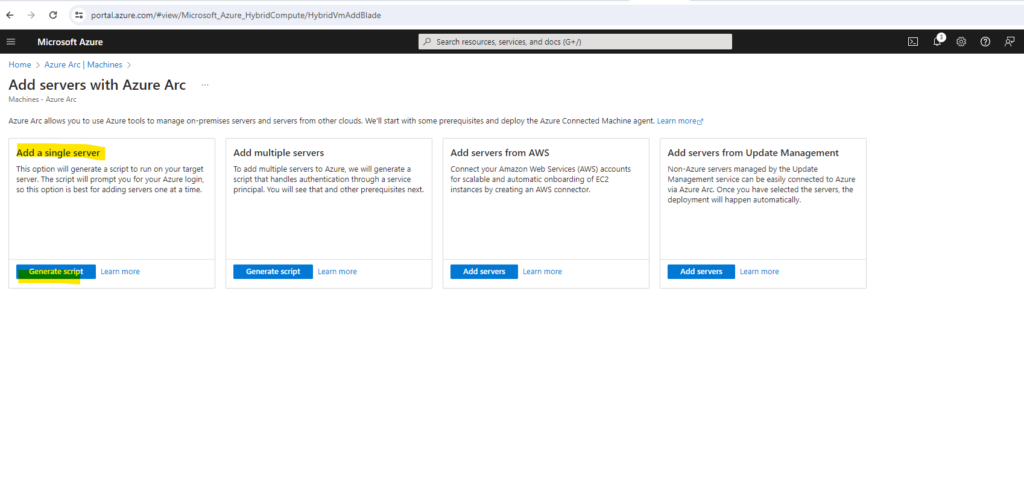
On the Add servers with Azure Arc page, under the Add a single server tile, select Generate script.
About how to add multiple servers you can read my following post https://blog.matrixpost.net/how-to-onboard-on-premise-server-to-azure-arc-by-using-a-site-to-site-ipsec-vpn-and-azure-arc-private-link-scope/#adding_multiple_servers. Here I will show how to onboard them by using Azure Arc Private Link Scope but the process to add multiple servers are finally the same for using a public endpoint like here instead a private endpoint like shown in this post.
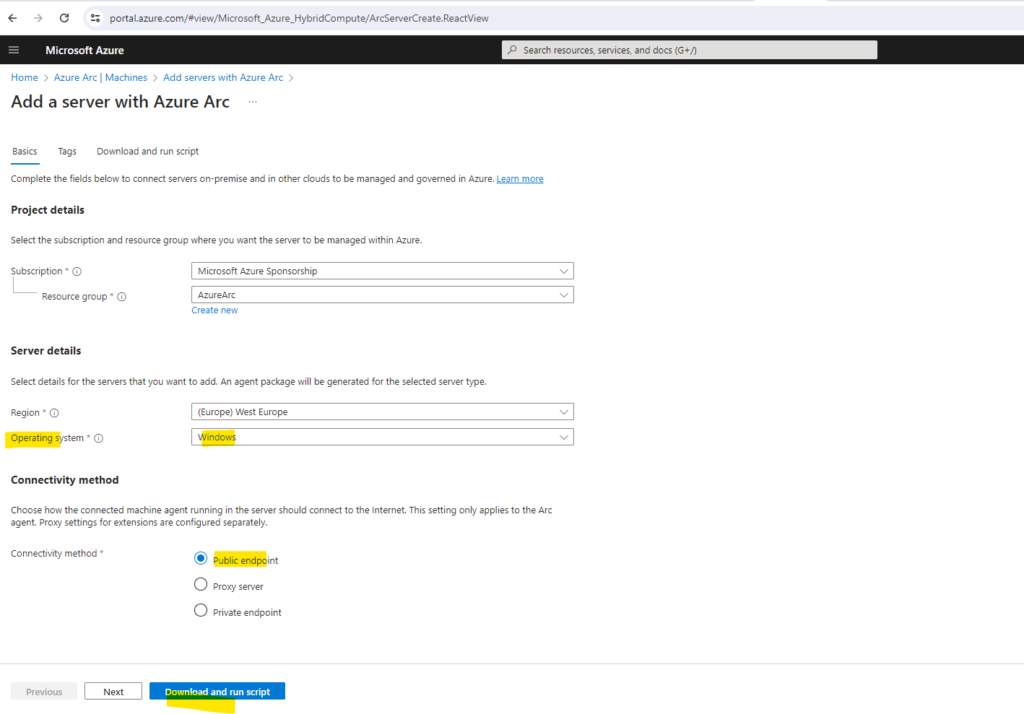
Select a resource group, region and operating system. Further select the connectivity method for your on-premise server and finally click on Download and run script.
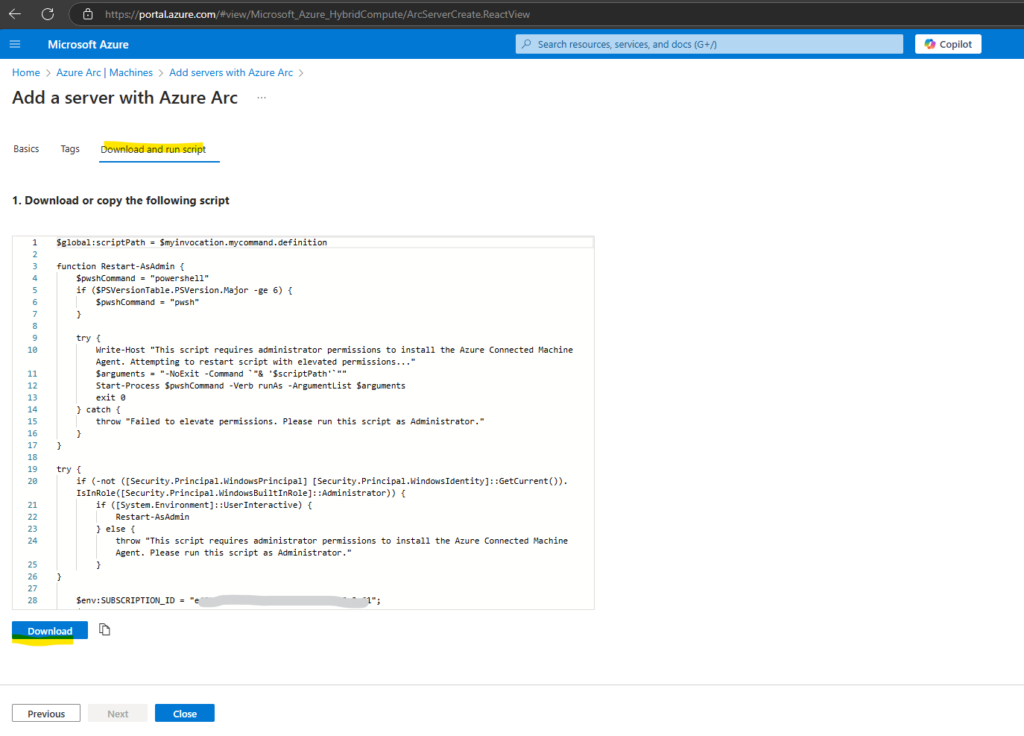
Finally we can download the OnboardingScript.ps1 for Windows.
After downloading the OnboardingScript.ps1 PowerShell script from Azure Arc, we need to upload this script to our Windows machine we want to connect to Azure Arc.
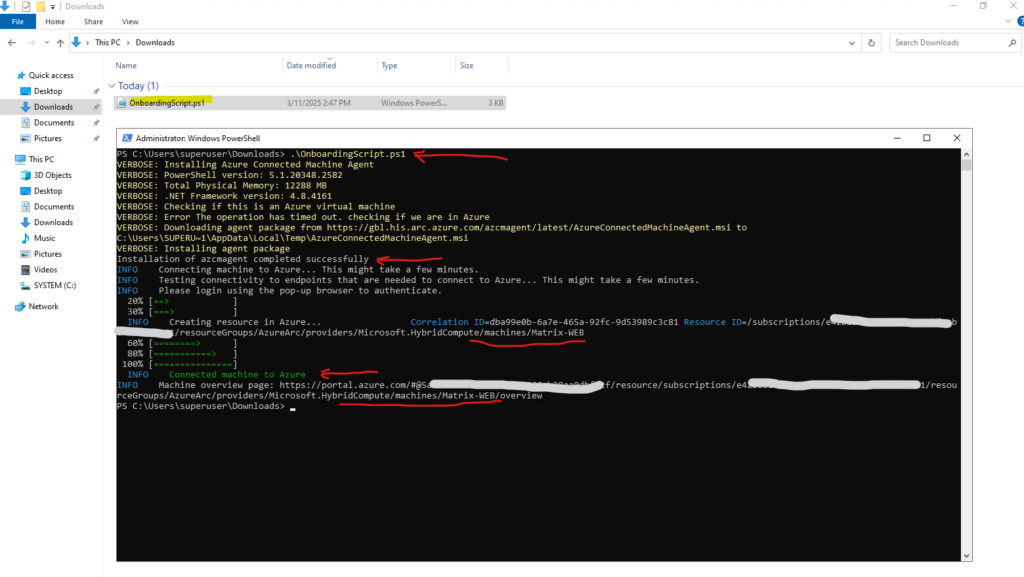
After you install the agent and configure it to connect to Azure Arc-enabled servers, go to the Azure portal to verify that the server has successfully connected.
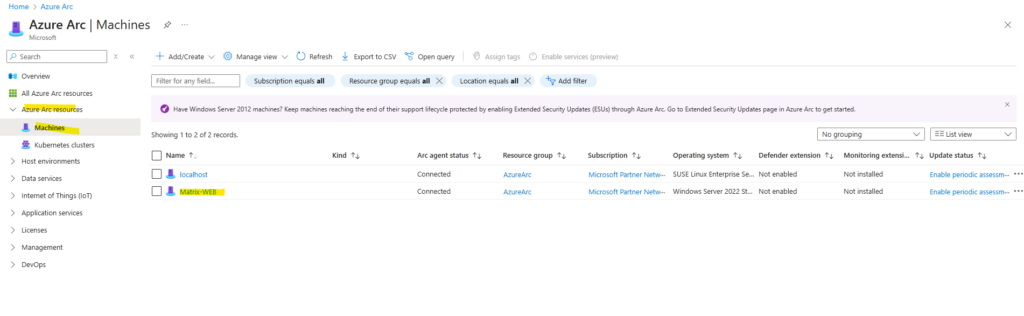
Determine if a Machine is connected to Azure Arc
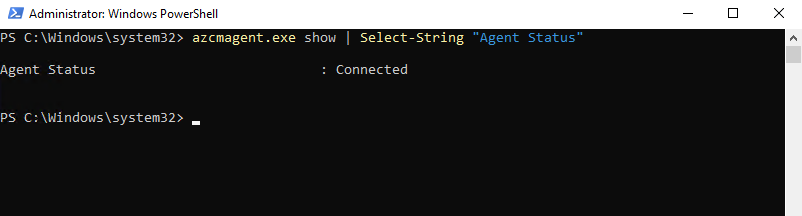
On Windows
Run the following command in the PowerShell console.
When the output is Connected the machine is connected to Azure Arc.
PS> azcmagent.exe show | Select-String "Agent Status" or just the following command to show all details PS> azcmagent.exe show The binary is located under 'C:\Program Files\AzureConnectedMachineAgent\azcmagent.exe'
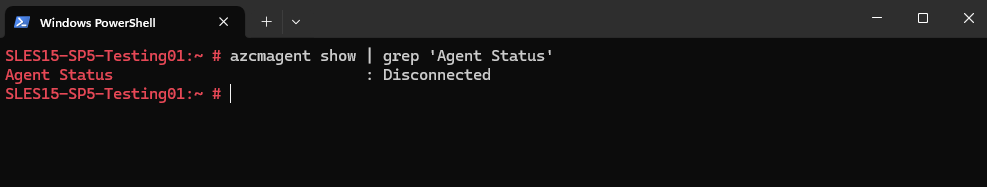
On Linux
Enter the following command in the shell.
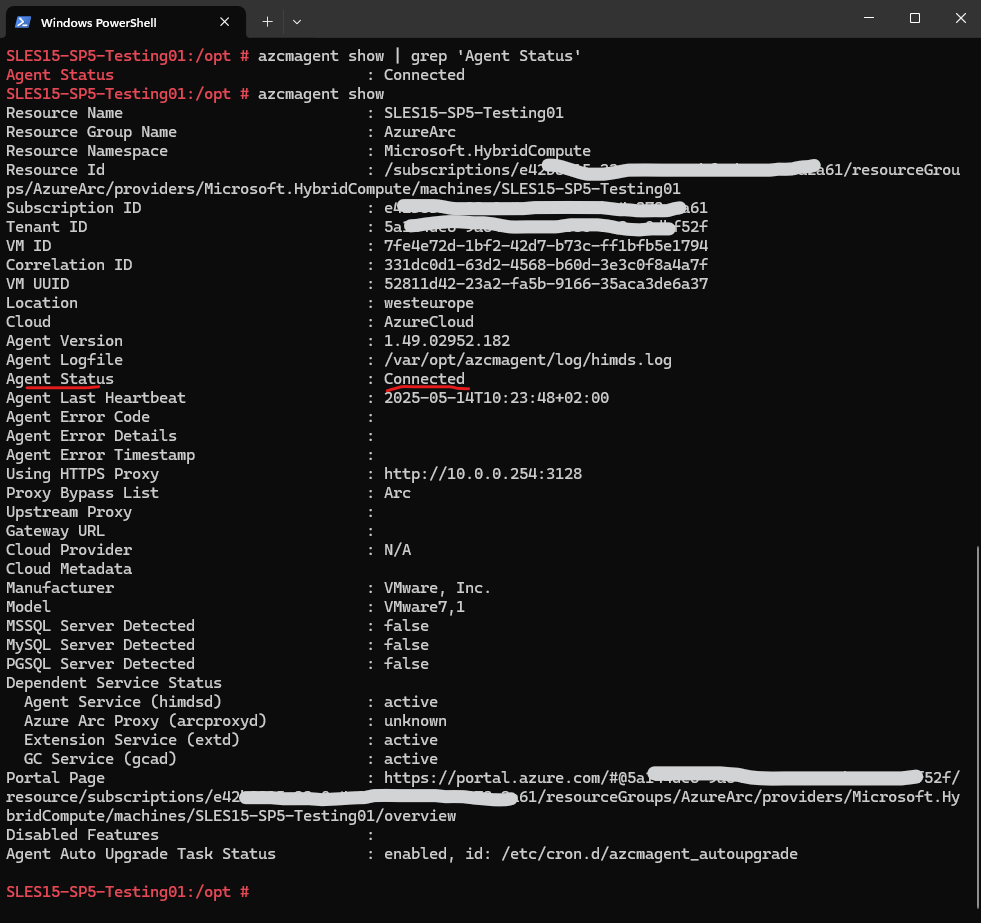
When the output is Connected the machine is connected to Azure Arc.
# azcmagent show | grep 'Agent Status'
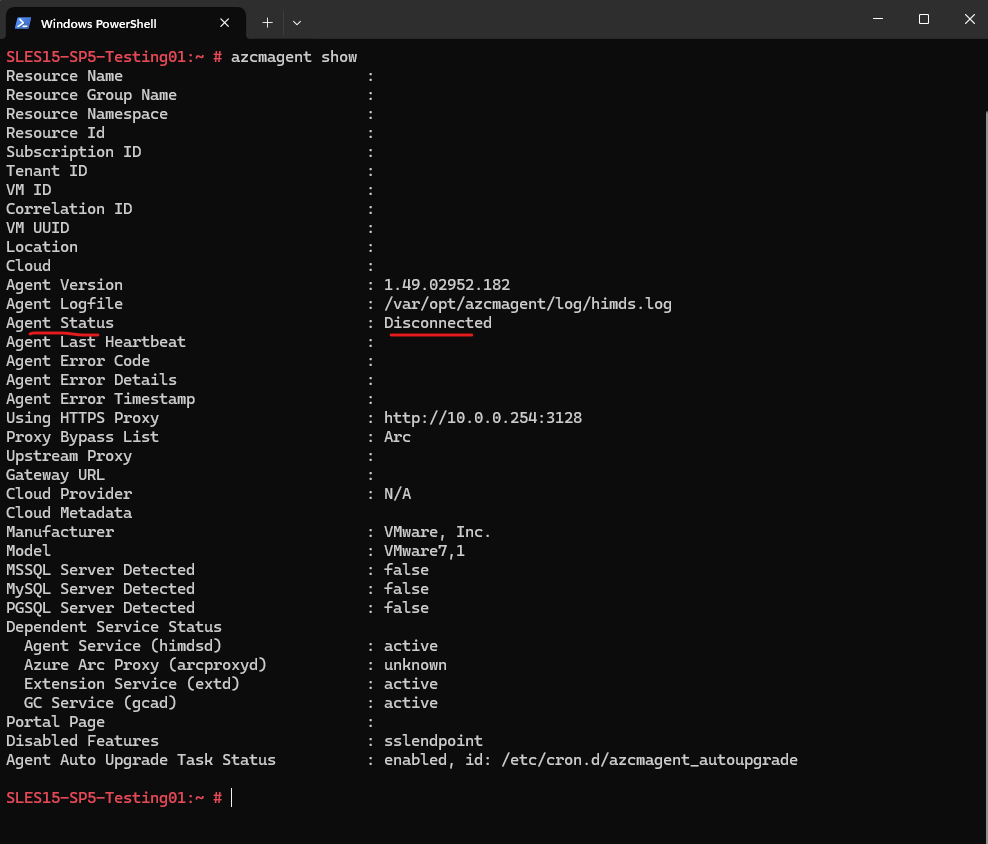
On a connected machine.
Links
What is Azure Arc-enabled servers?
https://learn.microsoft.com/en-us/azure/azure-arc/servers/overviewConnect hybrid machines to Azure using a deployment script
https://learn.microsoft.com/en-us/azure/azure-arc/servers/onboard-portal#generate-the-installation-script-from-the-azure-portalOverview of Azure Connected Machine agent
https://learn.microsoft.com/en-us/azure/azure-arc/servers/agent-overview


