How to install Root Certificates on Linux
In this post, I will walk you through the process of installing root certificates on Linux. From placing the certificate in the appropriate directory to finally updating the trusted certificate store.
Whether you’re adding a corporate certificate or a third-party CA, these steps are straightforward and essential for maintaining a reliable Linux environment.
Install Root Certificates on SUSE Linux Enterprise Server and Ubuuntu
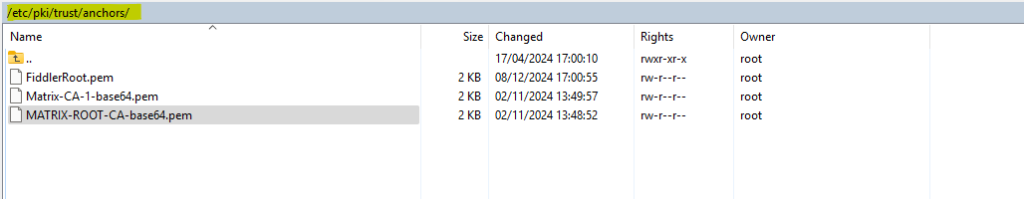
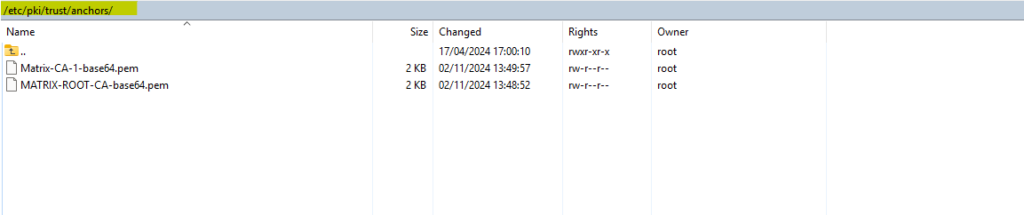
To install root certificates in SUSE Linux Enterprise Server, we first need to copy them into the /etc/pki/trust/anchors/ folder.
The same also for intermediate certificates issued by a so called Subordinate CA.
The certificates needs to be in PEM format and the file extension like .pem, .cert or something different, SUSE doesn’t really care about and finally accept all.
For Ubuntu these certificates also needs to be in PEM format but here they need the file extension to be .crt and must be copied to a different path /usr/local/share/ca-certificates.
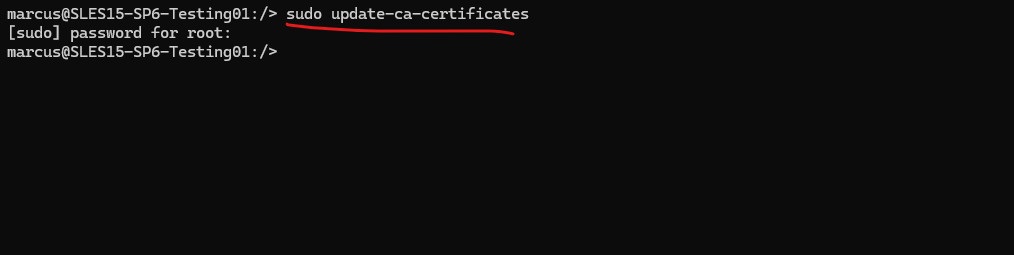
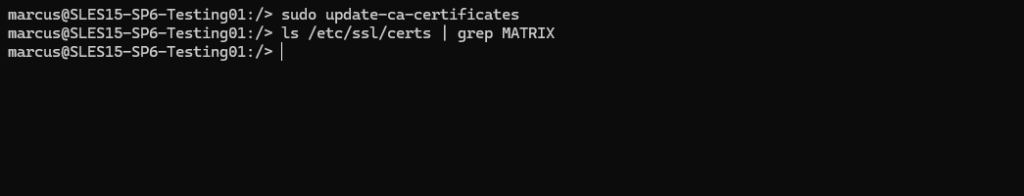
Now we need to run the following command, this command also works for Ubuntu.
update-ca-certificates is a program that updates the directory /etc/ssl/certs to hold SSL certificates and generates ca-certificates.crt, a concatenated single-file list of certificates.
Source: https://manpages.ubuntu.com/manpages/xenial/man8/update-ca-certificates.8.html
# sudo update-ca-certificates
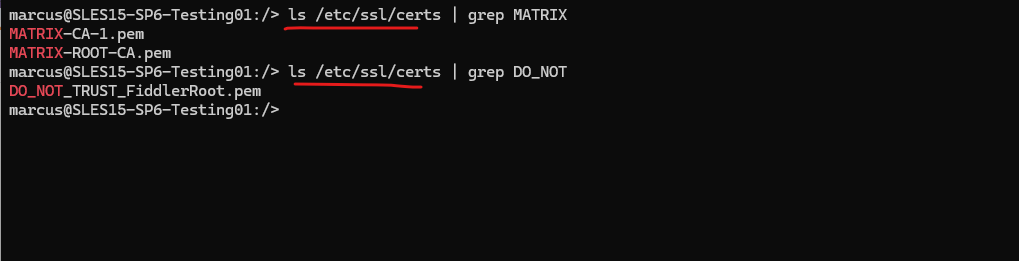
Below we can check if the certificate was installed successfully in /etc/ssl/certs, also the same in Ubuntu.
# ls /etc/ssl/certs | grep MATRIX
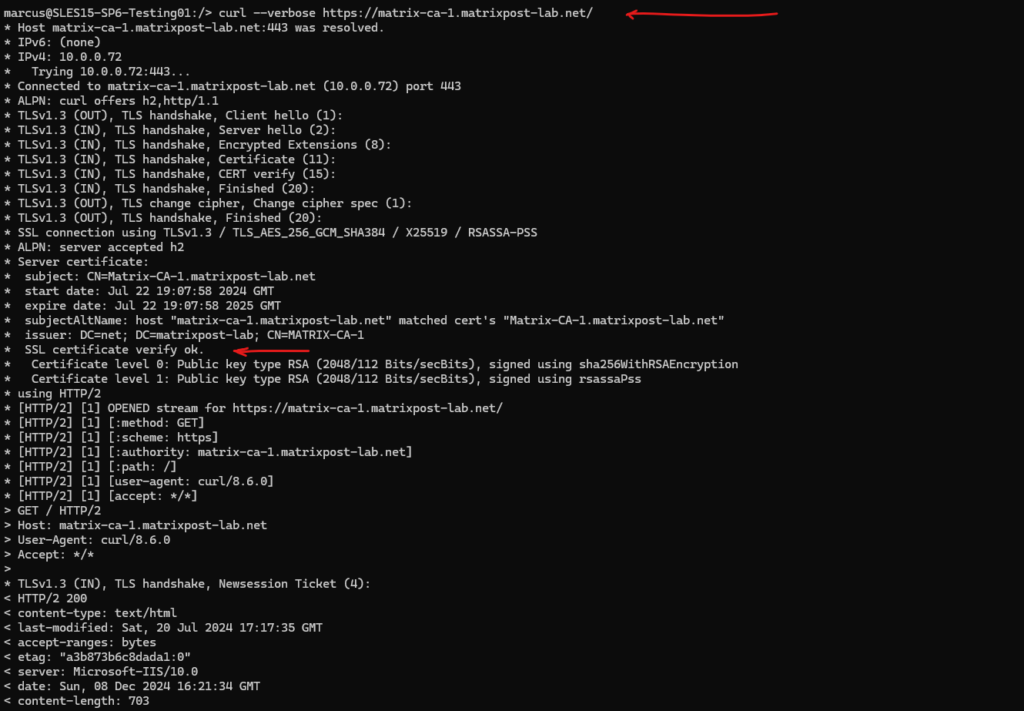
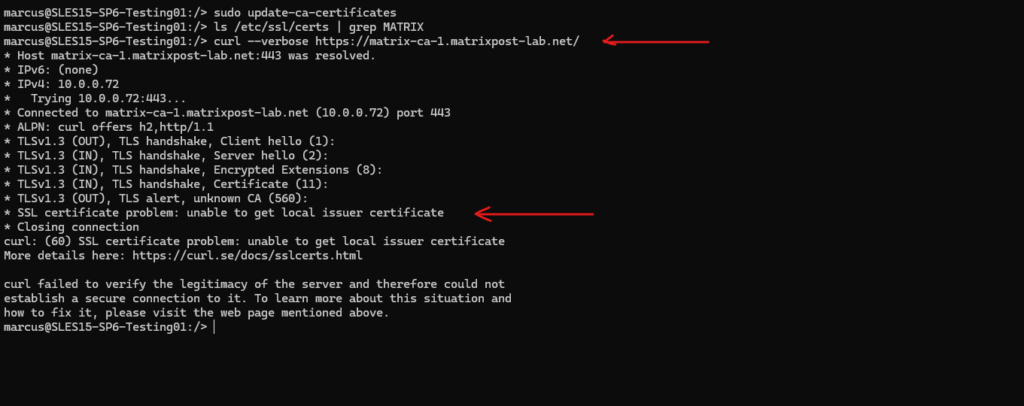
Finally we can also check if the root certificate was installed successfully by using the curl command to connect to a web server and web site which is using a certificate issued by the CA we installed its root certificate.
Looks good!
# curl --verbose https://matrix-ca-1.matrixpost-lab.net/
Deinstall Root Certificates
To uninstall our previously installed root certificates, we just need to remove them in /etc/pki/trust/anchors and finally run the sudo update-ca-certificates command again.
We can check if the root certificate was removed successfully by listing all certificates in /etc/ssl/certs and filter for the name.
Looks good and doesn’t find it anymore.
Finally we can also check if the root certificate was removed successfully by using the curl command again.
Install Root Certificates on Red Hat Linux Enterprise (RHEL), Oracle Linux, CentOS and Fedora
Below I will show this on Red Hat Linux Enterprise (RHEL) 9.4, finally the steps are also the same for Oracle Linux, CentOS and Fedora.
Under /etc/pki/ca-trust/source there is a README file in which the steps are explained. We just need to copy the certificate in PEM or DER file format to the list of CAs trusted on the system.
So we need to copy it to the /etc/pki/ca-trust/source/anchors/ subdirectory and run the update-ca-trust command.
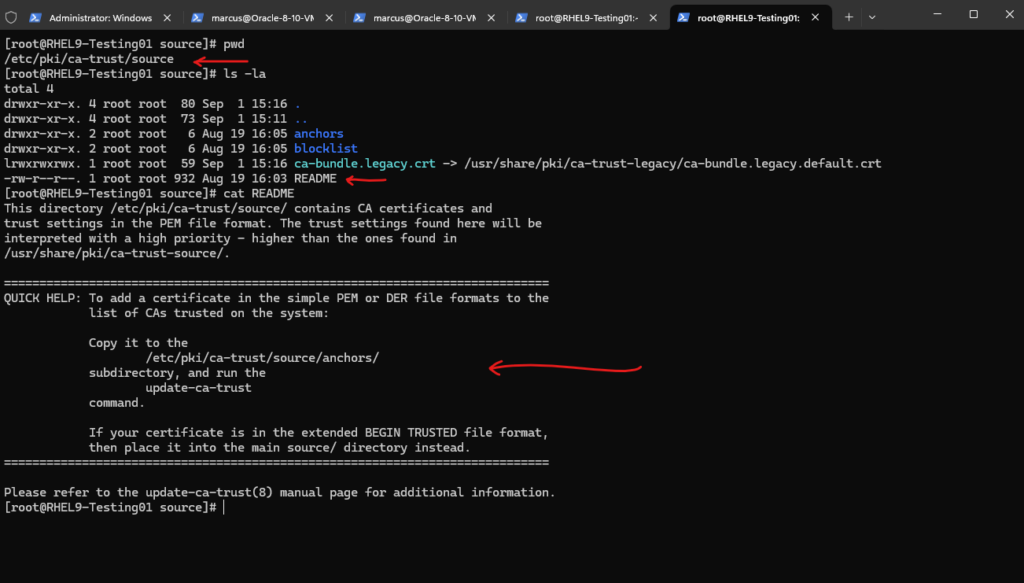
As also mentioned above in the README file, if your certificate is in the extended BEGIN TRUSTED file format, then place it into the main source/ directory instead.
Extended BEGIN TRUSTED file format means it is encoded with additional metadata such as trust settings, which is used by some systems or tools (like OpenSSL or certain embedded Linux environments). These certificates typically look like this:
-----BEGIN TRUSTED CERTIFICATE----- <Encoded certificate data> <Metadata or trust attributes> -----END TRUSTED CERTIFICATE-----
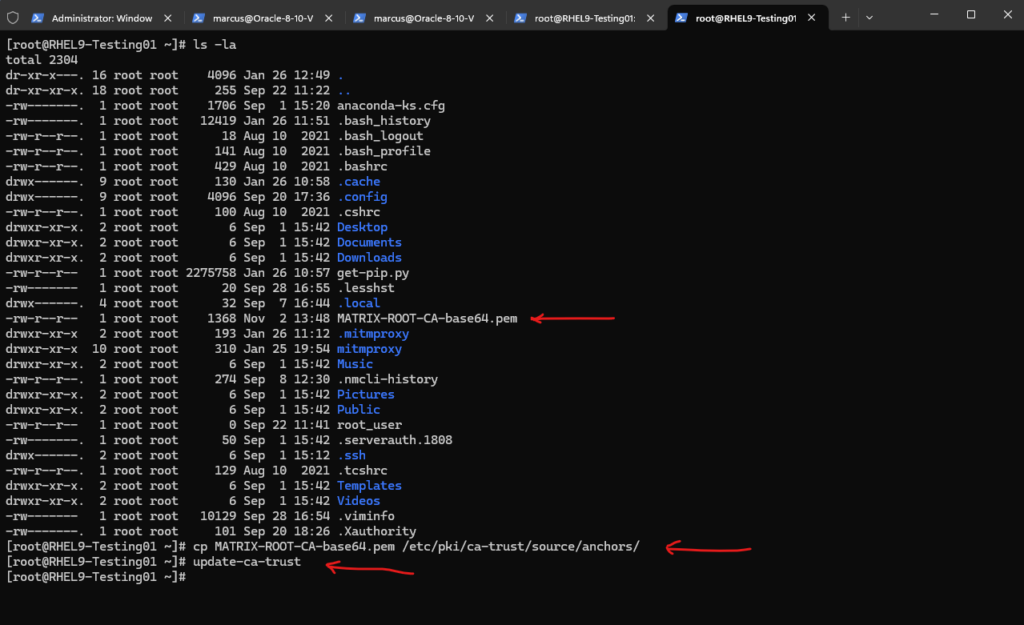
So I will now copy the root CA from my own on-premise PKI to the /etc/pki/ca-trust/source/anchors/ subdirectory and then run the update-ca-trust command. Further also for the intermediate certificate from my PKI I need to do the same.
# cp MATRIX-ROOT-CA-base64.pem /etc/pki/ca-trust/source/anchors/ # update-ca-trust
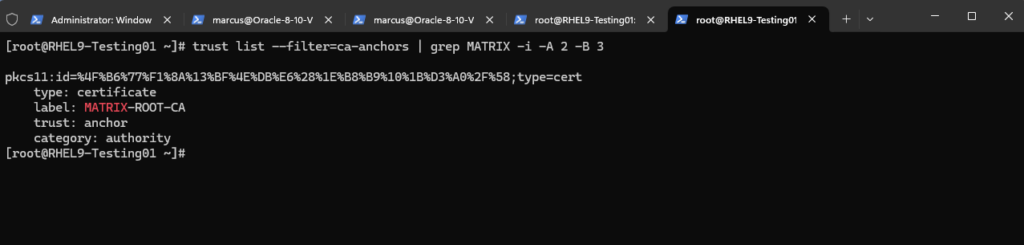
We can also verify whether a CA can be trusted by looking at the anchor value in the trust key:
# trust list --filter=ca-anchors | grep MATRIX -i -A 2 -B 3
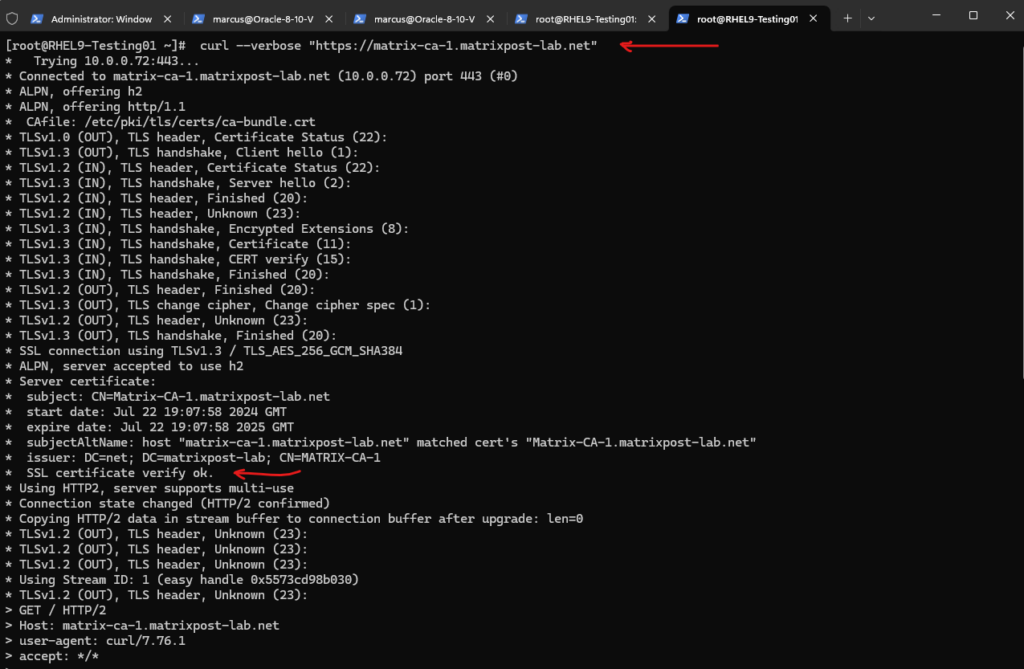
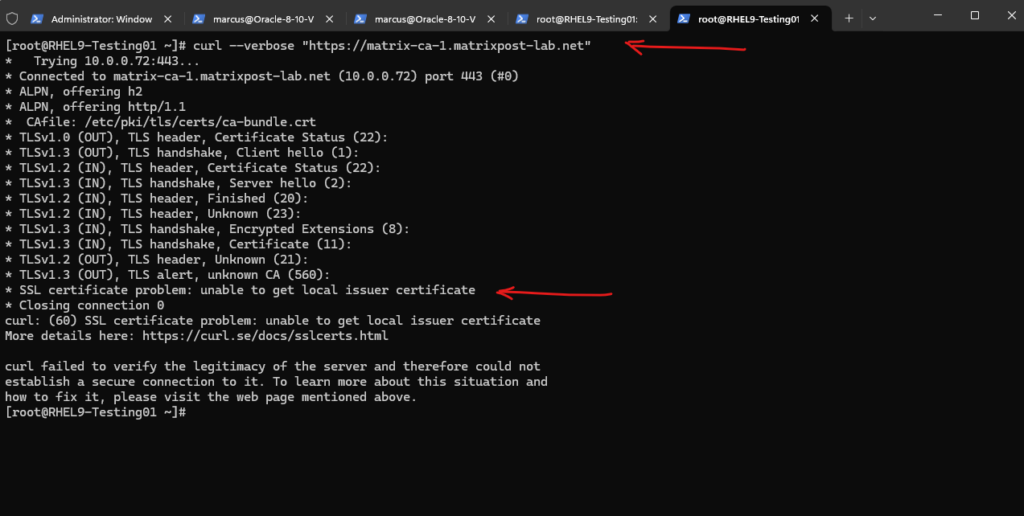
Finally we can also check if the root certificate was installed successfully by using the curl command to connect to a web server and web site which is using a certificate issued by the CA we installed its root certificate.
Looks good!
# curl --verbose "https://matrix-ca-1.matrixpost-lab.net"
Deinstall Root Certificates
To uninstall our previously installed root certificates, we just need to remove them in /etc/pki/ca-trust/anchors and finally run the sudo update-ca-trust command again.
# sudo rm /etc/pki/ca-trust/source/anchors/MATRIX-ROOT-CA-base64.pem # sudo rm /etc/pki/ca-trust/source/anchors/Matrix-CA-1-base64.pem # sudo update-ca-trust
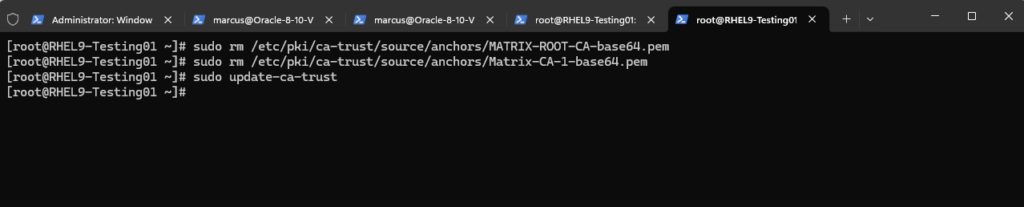
Finally we can also check if the root certificate was removed successfully by using the curl command again.
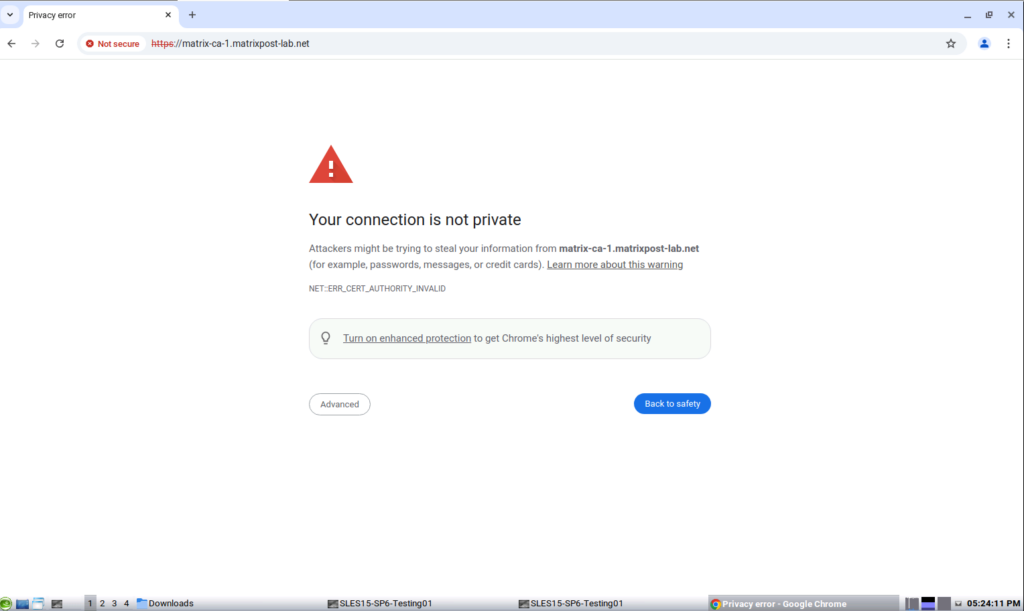
Install Root Certificates on Chrome running on Linux
For Linux, Chrome uses its own certificate store. You can import your Root CA’s in Chrome directly.
In Chrome open Settings -> Privacy and security -> Security -> Manage certificates -> Authorities
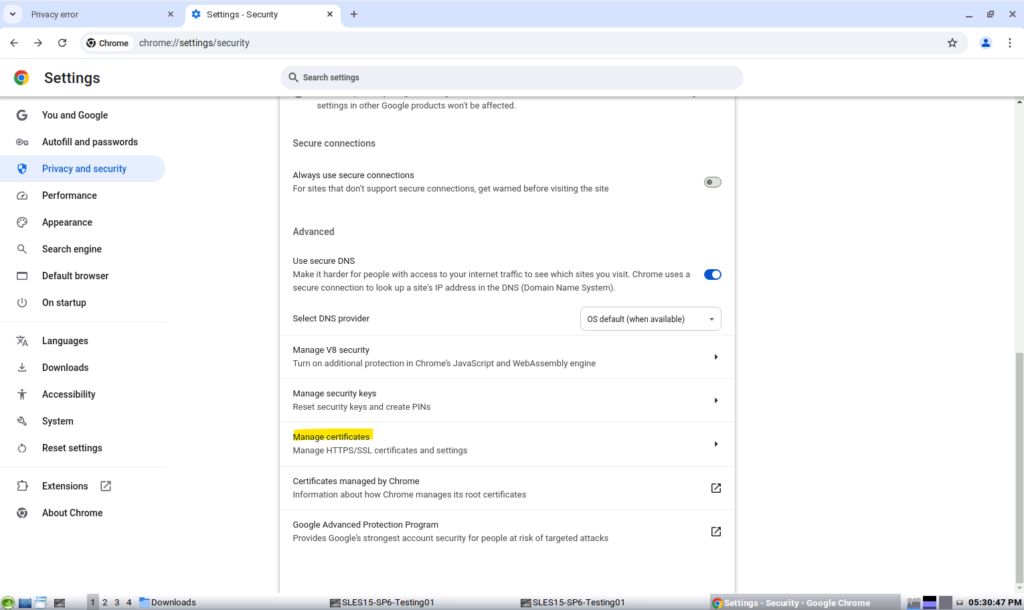
Click on Import and select the desired root certificates.
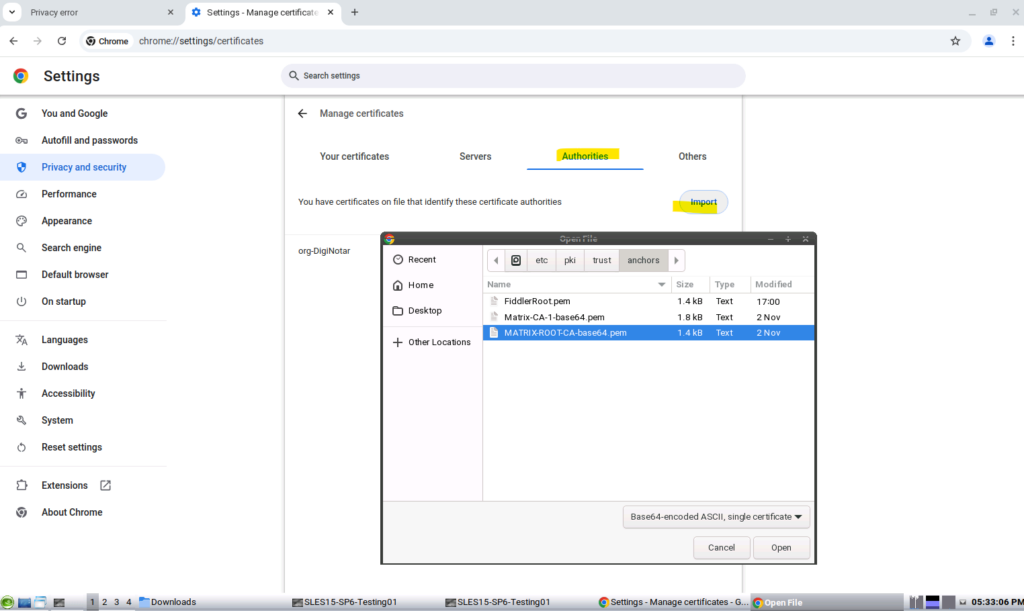
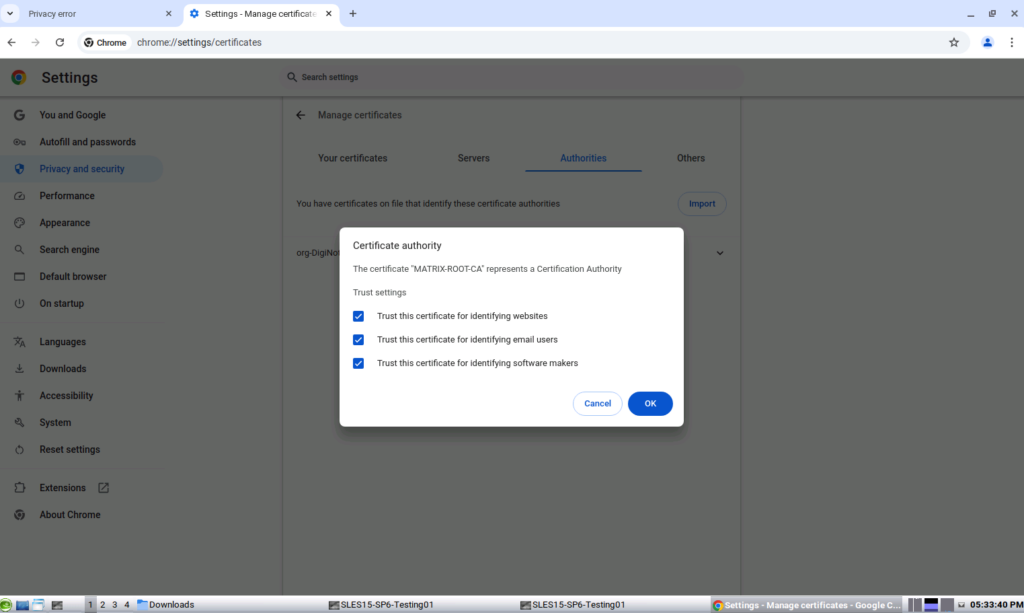
Select which Trust settings you want to allow for the CA.
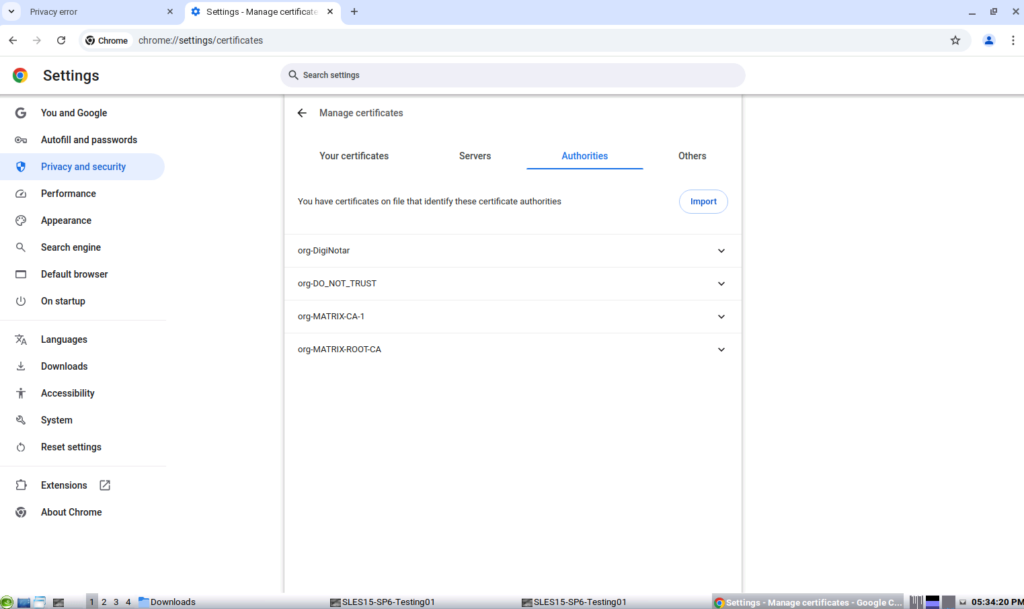
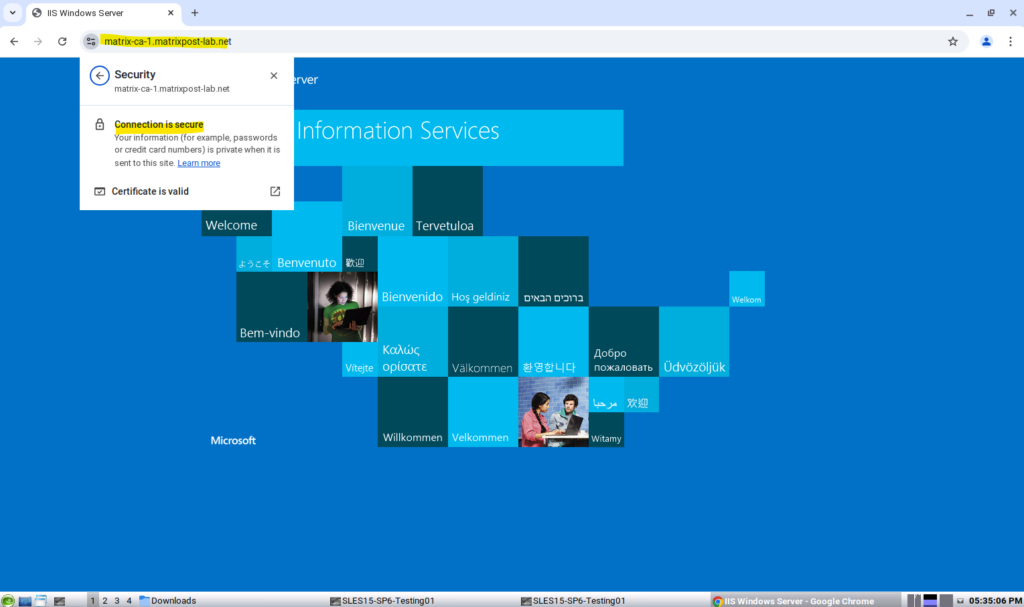
Looks good!
About how to set up your own PKI you can also read my following post.
Links
update-ca-certificates
https://manpages.ubuntu.com/manpages/xenial/man8/update-ca-certificates.8.htmlHow to configure your CA trust list in Linux
https://www.redhat.com/en/blog/configure-ca-trust-list


