What is Microsoft Entra Global Secure Access (Internet Access)?
In this post I want to take a look at a new service in the Microsoft Entra product family named Microsoft Entra Global Secure Access.
Microsoft Entra Global Secure Access is so far in preview state.
What are preview features
https://learn.microsoft.com/en-us/dynamics365/sales/sales-previews-in-trial
Microsoft Entra Global Secure Access is a unified location in the Microsoft Entra admin center for two services named Microsoft Entra Internet Access and Microsoft Entra Private Access which builds Microsoft’s Security Service Edge solution (SSE).
Microsoft Entra Internet Access secures access to Microsoft 365, SaaS, and public internet apps while protecting users, devices, and data against internet threats.
Microsoft Entra Private Access provides your users – whether in an office or working remotely – secured access to your private, corporate resources.
Microsoft Entra Private Access I will show in detail in the following post.
Introduction
The way people work has changed. Instead of working in traditional offices, people now work from nearly anywhere. With applications and data moving to the cloud, an identity-aware, cloud-delivered network perimeter for the modern workforce is needed. This new network security category is called Security Service Edge (SSE).
Microsoft Entra Internet Access and Microsoft Entra Private Access comprise Microsoft’s Security Service Edge solution. Global Secure Access (preview) is the unifying term used for both Microsoft Entra Internet Access and Microsoft Entra Private Access.
Global Secure Access is the unified location in the Microsoft Entra admin center and is built upon the core principles of Zero Trust to use least privilege, verify explicitly, and assume breach.
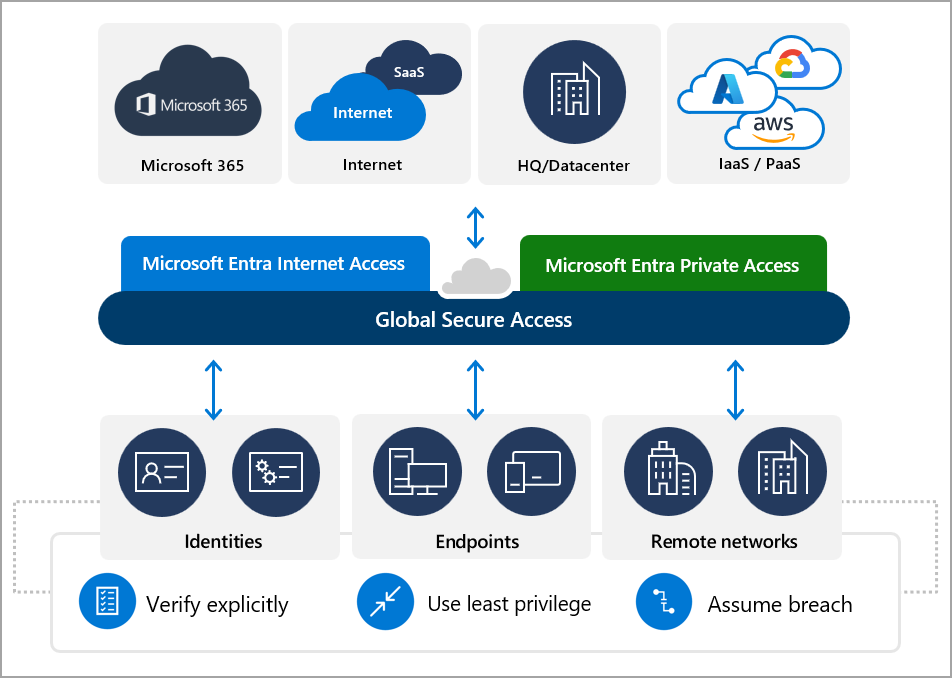
Source: https://learn.microsoft.com/en-us/entra/global-secure-access/overview-what-is-global-secure-access
Global Secure Access is Microsoft’s Security Service Edge solution
Microsoft Entra Internet Access and Microsoft Entra Private Access – coupled with Microsoft Defender for Cloud Apps, our SaaS-security focused Cloud Access Security Broker (CASB) – are uniquely built as a solution that converges network, identity, and endpoint access controls so you can secure access to any app or resource, from anywhere. With the addition of these Global Secure Access products, Microsoft Entra ID simplifies access policy management and enables access orchestration for employees, business partners, and digital workloads.
You can continuously monitor and adjust user access in real time if permissions or risk level changes.
The Global Secure Access features streamline the roll-out and management of the access control capabilities with a unified portal. These features are delivered from Microsoft’s Wide Area Network, spanning 140+ countries and 190+ network edge locations. This private network, which is one of the largest in the world, enables organizations to optimally connect users and devices to public and private resources seamlessly and securely. For a list of the current points of presence, see Global Secure Access points of presence article.
Microsoft Entra Internet Access
Microsoft Entra Internet Access secures access to Microsoft 365, SaaS, and public internet apps while protecting users, devices, and data against internet threats. Best-in-class security and visibility, along with fast and seamless access to Microsoft 365 apps is currently available in public preview. Secure access to public internet apps through the identity-centric, device-aware, cloud-delivered Secure Web Gateway (SWG) of Microsoft Entra Internet Access is in private preview.
Microsoft Entra Private Access
Microsoft Entra Private Access provides your users – whether in an office or working remotely – secured access to your private, corporate resources. Microsoft Entra Private Access builds on the capabilities of Microsoft Entra application proxy and extends access to any private resource, port, and protocol.
Remote users can connect to private apps across hybrid and multicloud environments, private networks, and data centers from any device and network without requiring a VPN. The service offers per-app adaptive access based on Conditional Access policies, for more granular security than a VPN.
Licenses
The preview requires a Microsoft Entra ID P1 license. If needed, you can purchase licenses or get trial licenses. To use the Microsoft 365 traffic forwarding profile, a Microsoft 365 E3 license is recommended. After general availability, Microsoft Entra Private Access and Microsoft Entra Internet Access may require different licenses.
There may be limitations with some features of the Global Secure Access preview, which are defined in the associated articles.
Get started with Global Secure Access
In order to not impact any workload within a production tenant, I will use to demonstrate Global Secure Access in a dedicated lab tenant.
Further as mentioned Global Secure Access is so far in preview state and aren’t meant for production use.
As you can read below under the second point, activation will not impact any workload in your tenant until preview features are enabled. So just activating Global Secure Access will not impact any workloads, but it will indeed impact them when you enable some features like conditional access policies which requires users to use the Global Secure Access client or a configured remote network when they to access Exchange Online and SharePoint Online.
So in order to be able to activate Global Secure Access here, I will first have to assign a trial Microsoft 365 E3 license to my global administrator account in this lab tenant.
Getting a Trial License for Microsoft 365 E3
In my case for Germany I have to pick up now a so called Microsoft 365 E3 EEA (no Teams) license. More about that new license, which only affects business customers in the European Economic Area and Switzerland, you can read in my following post.
Activate Global Secure Access in your tenant
So now after assigning the Microsoft 365 E3 license to my user account, I can activate Global Secure Access by clicking on the Activate button below.
As you can see below, after assigning the license to my user account, the previous message about recommending to use a Microsoft 365 E3 license disappeared and the Activate button is now not greyed out anymore.
Tenant onboarding is in progress.
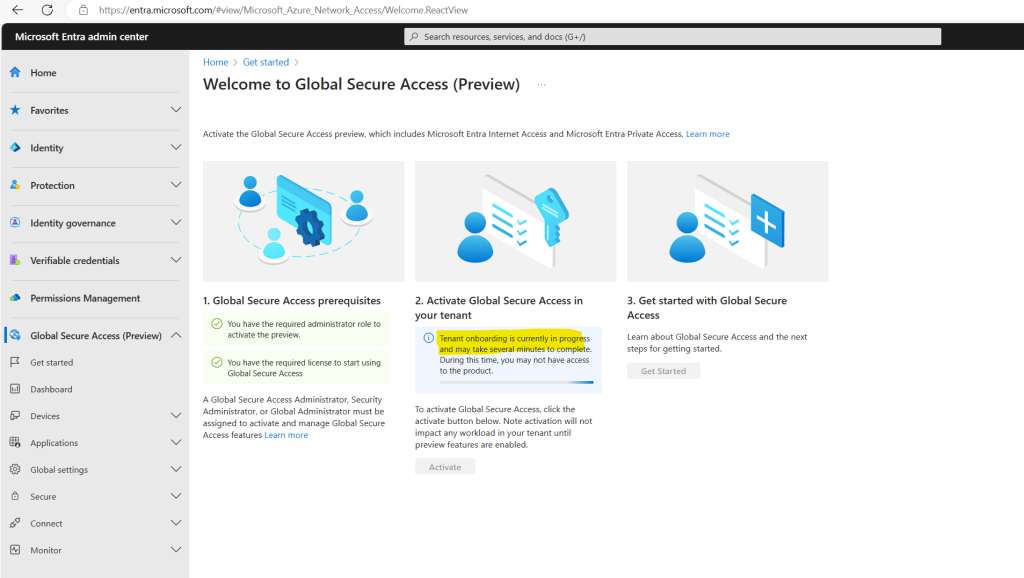
Just a few seconds later tenant onboarding completed successfully.
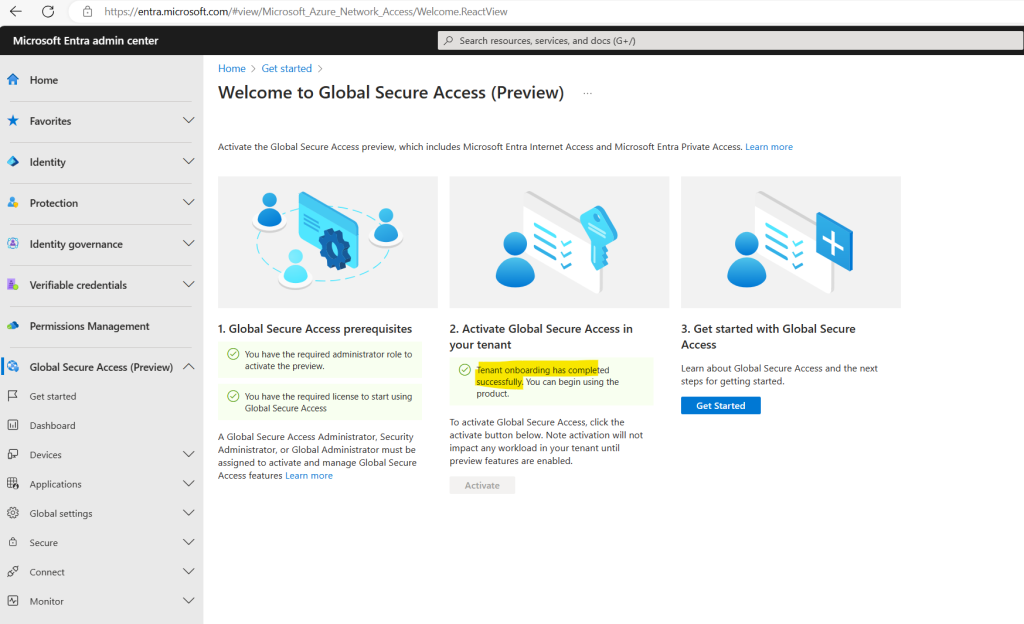
So now I can click on the Get Started button above and will be forwarded to the following page which offers guides about both solutions, Microsoft Entra Internet Access and Microsoft Entra Private Access, unified in the Global Secure Access location in the Microsoft Entra admin center.
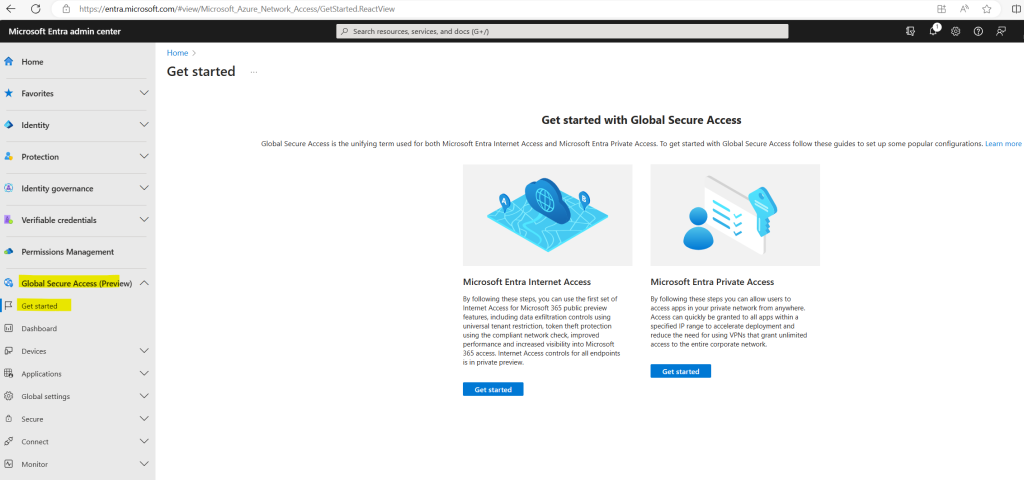
Get started with Microsoft Entra Internet Access https://learn.microsoft.com/en-us/entra/global-secure-access/how-to-get-started-with-global-secure-access#microsoft-entra-internet-access
Get started with Microsoft Entra Private Access https://learn.microsoft.com/en-us/entra/global-secure-access/how-to-get-started-with-global-secure-access#microsoft-entra-private-access
Get started with Microsoft Entra Internet Access
Microsoft Entra Internet Access isolates the traffic for Microsoft 365 applications and resources, such as Exchange Online and SharePoint Online. Users can access these resources by connecting to the Global Secure Access Client or through a remote network, such as in a branch office location.
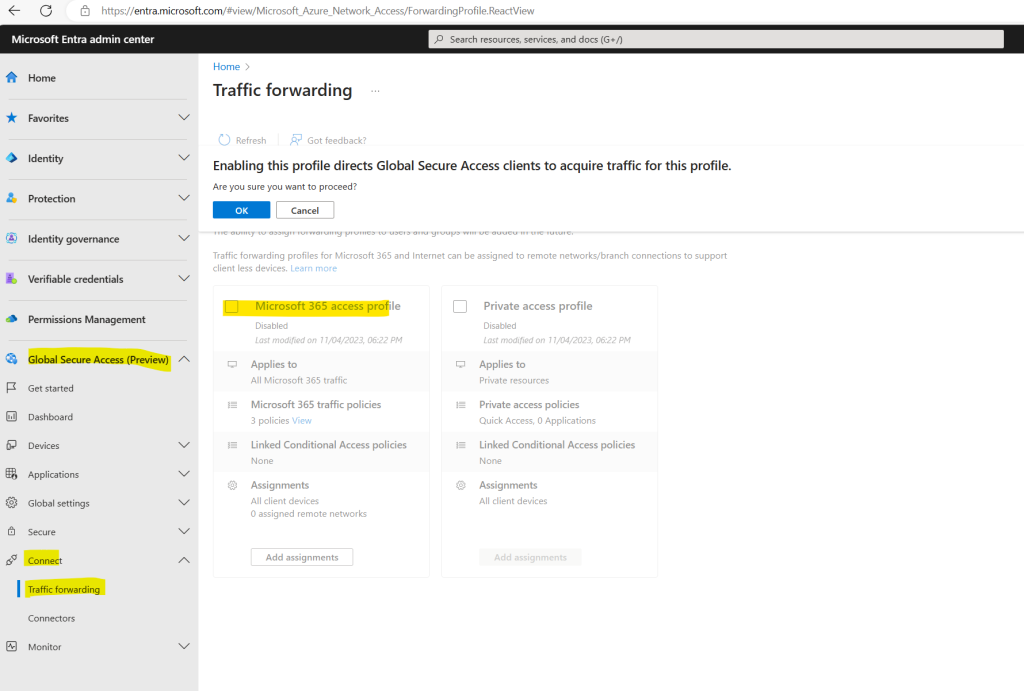
The first step we need to configure is to enable the Microsoft 365 traffic profile.
Enable the Microsoft 365 traffic profile
Sign in to the Microsoft Entra admin center.
Browse to Global Secure Access (preview) > Connect > Traffic forwarding.
Select the checkbox for Microsoft 365 access profile.
Traffic forwarding enables you to configure the type of network traffic to tunnel through the Microsoft Entra Private Access and Microsoft Entra Internet Access services.
When traffic comes through Global Secure Access, the service evaluates the type of traffic first through the Microsoft 365 profile and then through the Private access profile. Any traffic that doesn’t match the first two profiles isn’t forwarded to Global Secure Access.
Once selected, the forwarding profiles are assigned to any device in the tenant that is running the Global Secure Access client. The ability to assign forwarding profiles to users and groups will be added in the future.
To manage the details included in the Microsoft 365 traffic forwarding policy, select the View link for Microsoft 365 traffic policies.
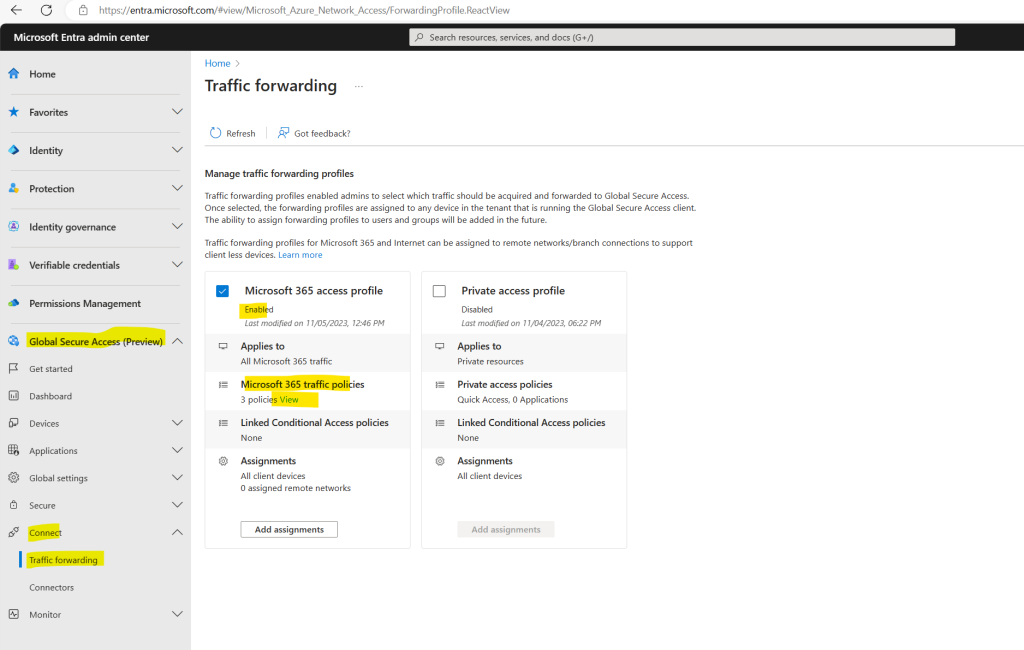
The policy groups are listed, with a checkbox to indicate if the policy group is enabled. Expand a policy group to view all of the IPs and FQDNs included in the group.
The Microsoft 365 traffic forwarding profile includes SharePoint Online, Exchange Online, and Microsoft 365 apps. All of the destinations for these apps are automatically included in the profile. Within each of the three main groups of destinations, you can choose to forward that traffic to Global Secure Access or bypass the service.
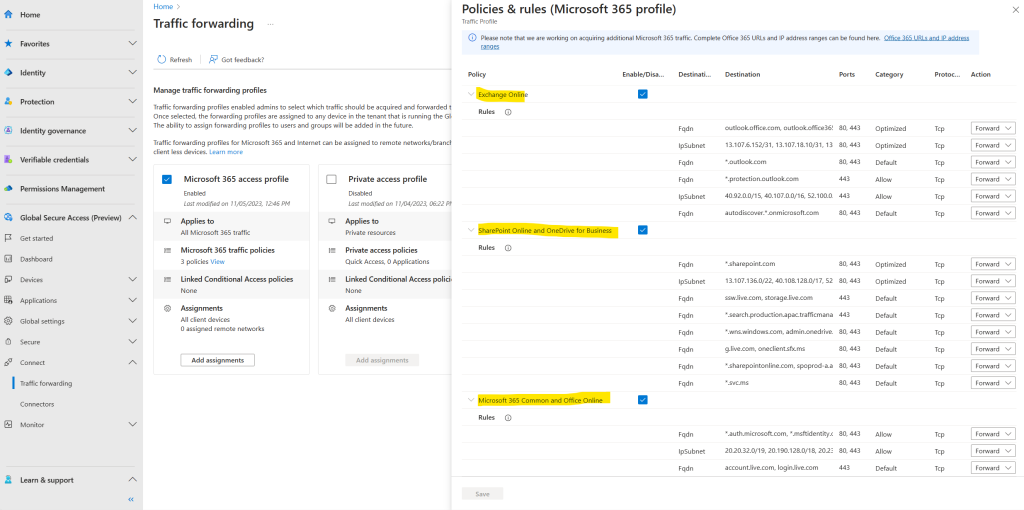
The policy groups include the following details:
- Destination type: FQDN or IP subnet
- Destination: The details of the FQDN or IP subnet
- Ports: TCP or UDP ports that are combined with the IP addresses to form the network endpoint
- Protocol: TCP (Transmission Control Protocol) or UDP (User Datagram Protocol)
- Action: Forward or Bypass
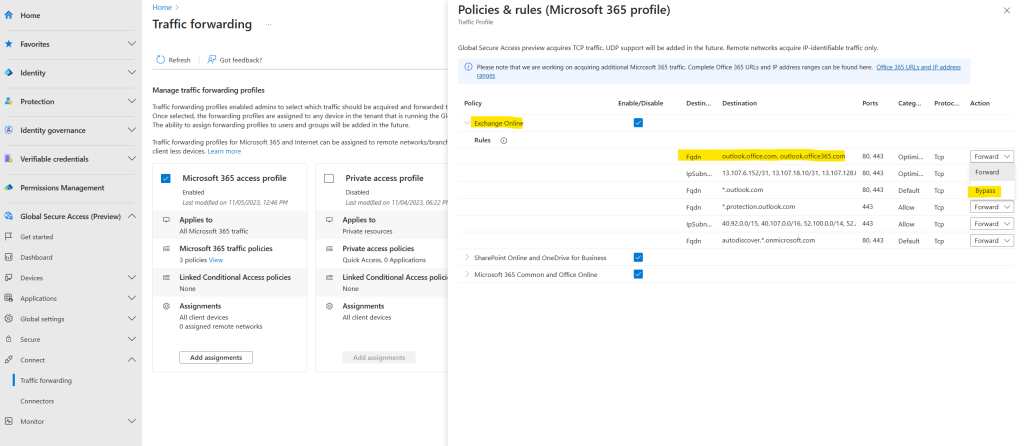
You can choose to bypass certain traffic. Users can still access the site; however, the service doesn’t process the traffic. You can bypass traffic to a specific FQDN or IP address, an entire policy group within the profile, or the entire Microsoft 365 profile itself. If you only need to forward some of the Microsoft 365 resources within a policy group, enable the group then change the Action in the details accordingly.
Here for example I will bypass all traffic destined to the FQDNs outlook.office.com and outlook.office365.com used by Outlook on the web. So traffic for Outlook on the web won’t be forwarded to the service.
If the Global Secure Access client isn’t able to connect to the service (for example due to an authorization or Conditional Access failure), the service bypasses the traffic. Traffic is sent direct-and-local instead of being blocked. In this scenario, you can create a Conditional Access policy for the compliant network check, to block traffic if the client isn’t able to connect to the service.
Linked Conditional Access policies
Conditional Access policies are created and applied to the traffic forwarding profile in the Conditional Access area of Microsoft Entra ID.
If you see “None” in the Linked Conditional Access policies section, there isn’t a Conditional Access policy linked to the traffic forwarding profile. To create a Conditional Access policy, see Universal Conditional Access through Global Secure Access.
Creating a new policy by using the Microsoft Entra admin center.
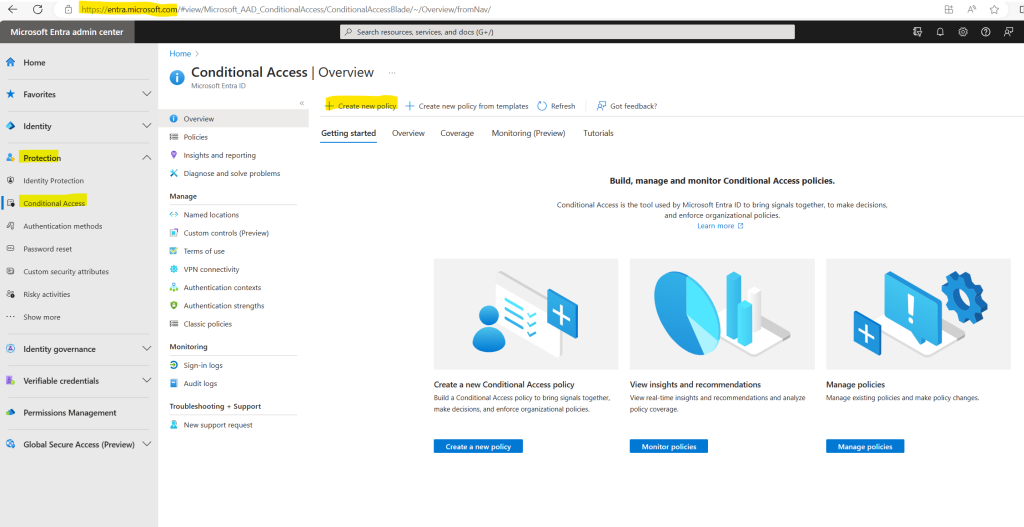
Under Select what this policy applies to select Global Secure Access (Preview)
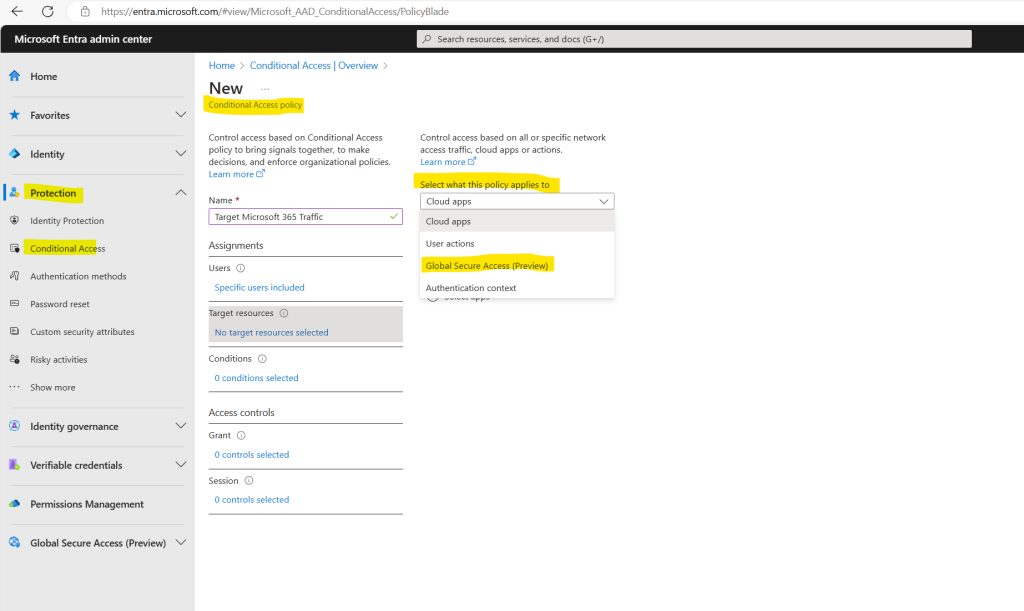
Creating a new policy by using the Microsoft Entra ID blade in the Azure portal.
Microsoft Entra ID -> Security -> Conditional Access
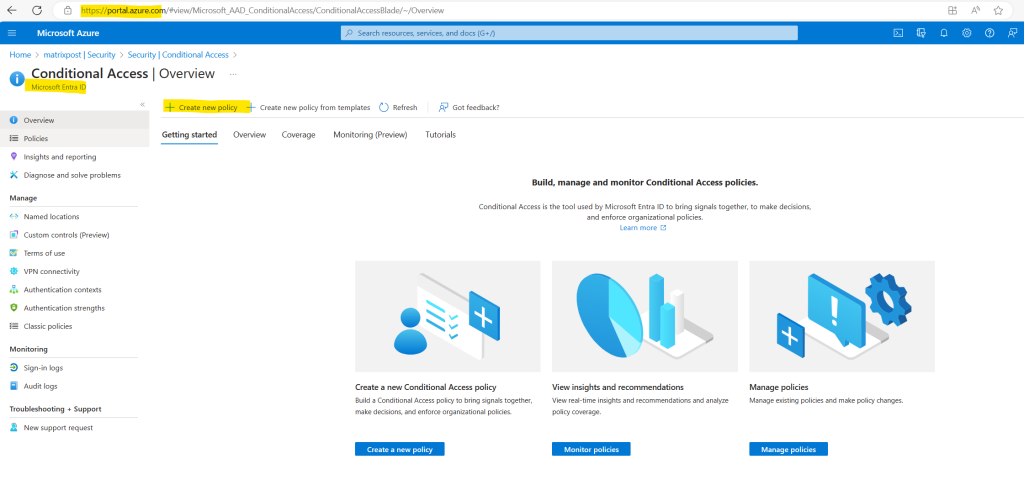
For example, you can create a policy that requires using compliant devices when accessing Microsoft 365 services.
Microsoft 365 remote network assignments
Traffic profiles can be assigned to remote networks, so that the network traffic is forwarded to Global Secure Access without having to install the client on end user devices. As long as the device is behind the customer premises equipment (CPE), the client isn’t required. You must create a remote network before you can add it to the profile. For more information, see How to create remote networks.
To assign a remote network to the Microsoft 365 profile:
Sign in to the Microsoft Entra admin center.
Browse to Global Secure Access (preview) > Traffic forwarding.
Select the Add assignments button for the profile.
Because I so far didn’t first created a remote network, I will get the following error message when clicking on the Add assignments button below
Your tenant has not been onboarded for branch connectivity. Go to remote networks and click the link in the banner to submit the onboarding form.
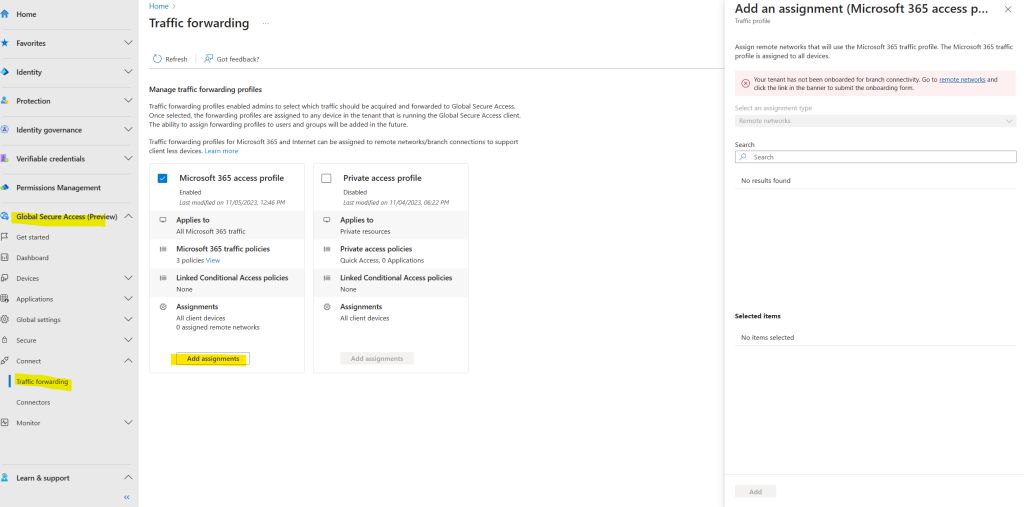
So when clicking on the link above I will get forwarded to the Remote network blade from Global Secure Access (Preview) like shown below.
Before you can set up remote networks, you need to onboard your tenant information with Microsoft.
This one-time process enables your tenant to use remote network connectivity.
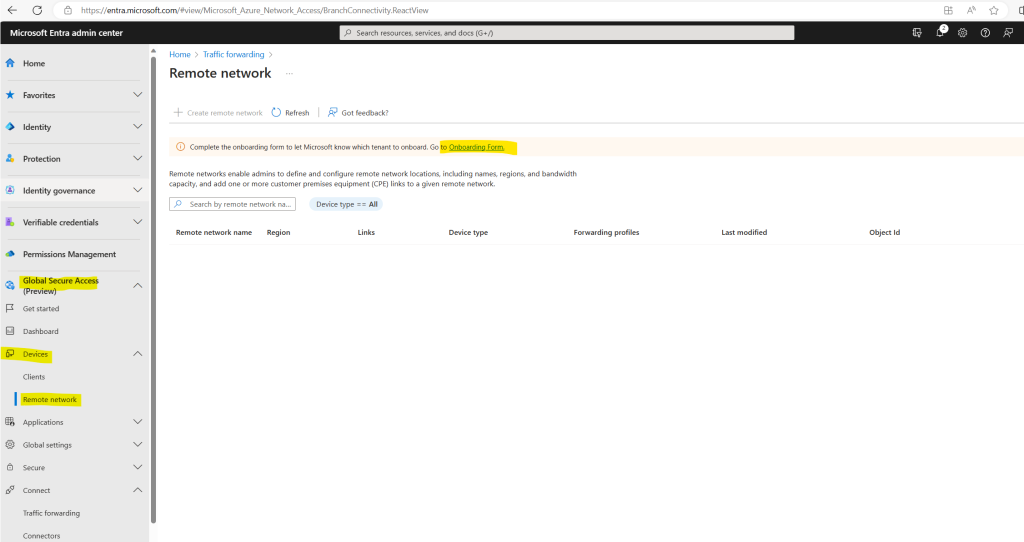
Select the link to the Onboarding form in the message at the top of the page. Review the Tenant ID and remote network region details. I have to switch here to EU.
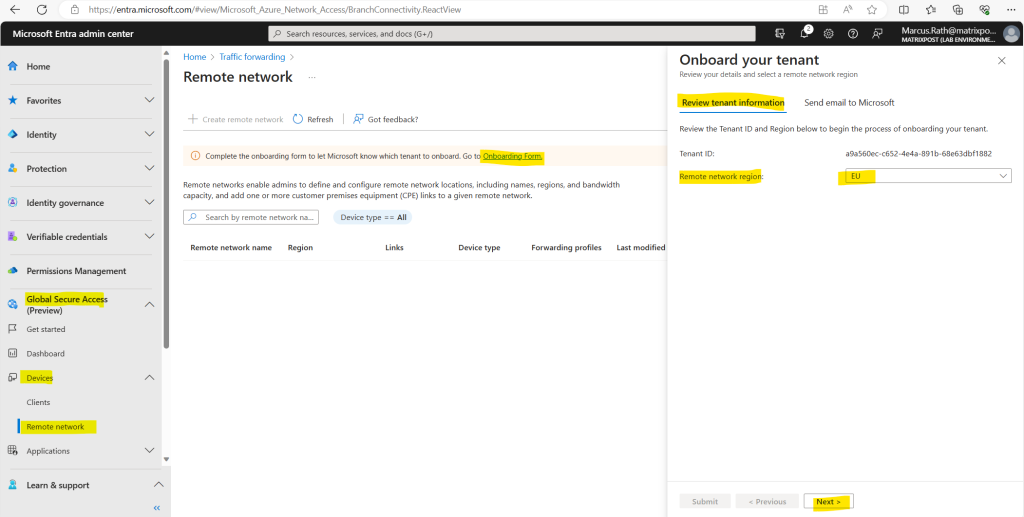
Select the email address link. It sends a pre-drafted email in your default mail client on your device. Send that email to the Global Secure Access team. Once your tenant is processed, we’ll send IPsec tunnel and BGP connectivity details to the email you used.
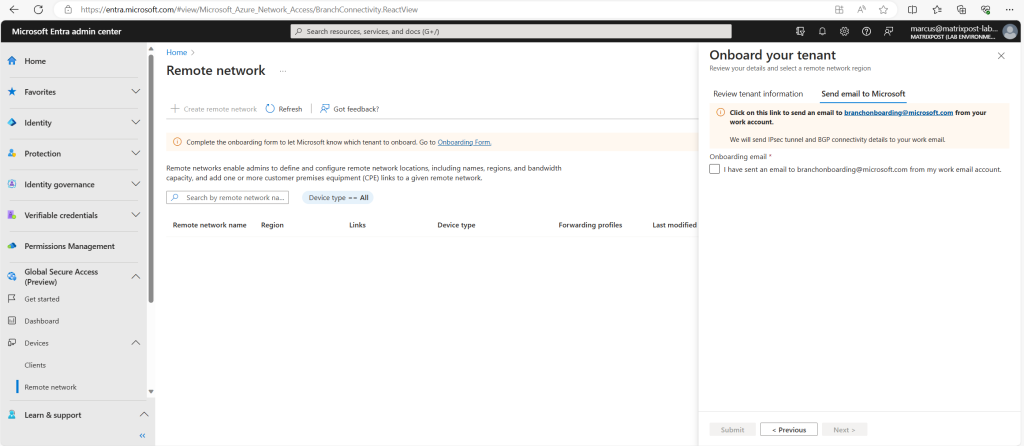
Once the email step is complete, return to this form, select the acknowledgment checkbox, and select the Submit button.
You MUST complete the email step before selecting the checkbox.
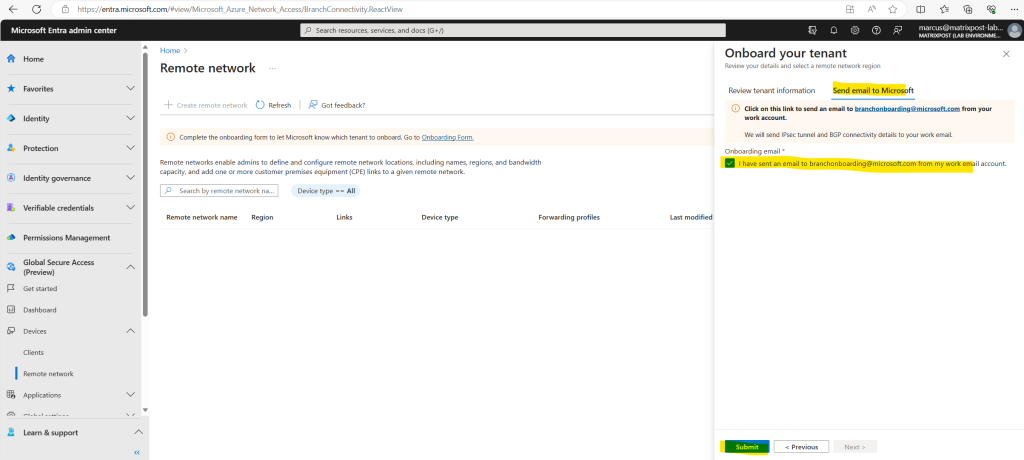
So after sending out this email and submitting the onboarding form I am really curious about how long this process will take to get a reply from Microsoft which should contain my requested information about the tunnel details to setup my remote network with Global Secure Access.
There isn’t any additional costs so far for the preview besides the required licenses below.
The preview requires a Microsoft Entra ID P1 license. If needed, you can purchase licenses or get trial licenses. To use the Microsoft 365 traffic forwarding profile, a Microsoft 365 E3 license is recommended.
After general availability, Microsoft Entra Private Access and Microsoft Entra Internet Access might require different licenses.
!!!! Note !!!!
So far I am still waiting on the reply from Microsoft regarding my requested information on 5. November 2023 about the tunnel details to configure my remote network. I will update this post as far as I get a reply from Microsoft.!!! Update 16. November 2023 !!!
Still waiting for the tunnel details and didn’t get any reply from Microsoft since 5. November 2023.!!! Update 12. December 2023 !!!
Still waiting for the tunnel details and didn’t get any reply on my meanwhile second friendly reminder to send me this information.
Using the Global Secure Access Client for Windows (preview)
The Global Secure Access Client allows organizations control over network traffic at the end-user computing device, giving organizations the ability to route specific traffic profiles through Microsoft Entra Internet Access and Microsoft Entra Private Access. Routing traffic in this method allows for more controls like continuous access evaluation (CAE), device compliance, or multifactor authentication to be required for resource access.
The Global Secure Access Client acquires traffic using a lightweight filter (LWF) driver, while many other security service edge (SSE) solutions integrate as a virtual private network (VPN) connection. This distinction allows the Global Secure Access Client to coexist with these other solutions. The Global Secure Access Client acquires the traffic based on the traffic forwarding profiles you configure prior to other solutions.
Source: https://learn.microsoft.com/en-us/entra/global-secure-access/how-to-install-windows-client
Prerequisites
- The Global Secure Access Client is supported on 64-bit versions of Windows 11 or Windows 10.
- Devices must be either Microsoft Entra joined or Microsoft Entra hybrid joined.
- Microsoft Entra registered devices aren’t supported.
- Local administrator credentials are required for installation.
- The preview requires a Microsoft Entra ID P1 license. If needed, you can purchase licenses or get trial licenses
About known limitations using the Global Secure Access Client you will find here more https://learn.microsoft.com/en-us/entra/global-secure-access/how-to-install-windows-client#known-limitations.
The most current version of the Global Secure Access Client can be downloaded from the Microsoft Entra admin center.
Sign in to the Microsoft Entra admin center as a Global Secure Access Administrator.
Browse to Global Secure Access (Preview) > Devices > Clients.
Select Download.
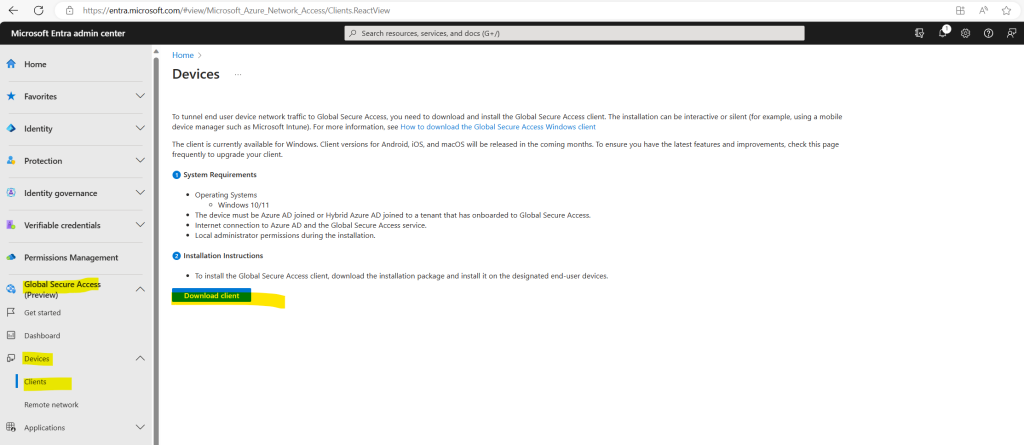
Organizations can install the client interactively, silently with the /quiet switch, or use mobile device management platforms like Microsoft Intune to deploy it to their devices.
About how to enroll Windows Computer into Microsoft Intune you can read my following post.
Copy the Global Secure Access Client setup file to your client machine.
Run the setup file, like GlobalSecureAccessInstaller 1.6.51.0 Accept the software license terms.
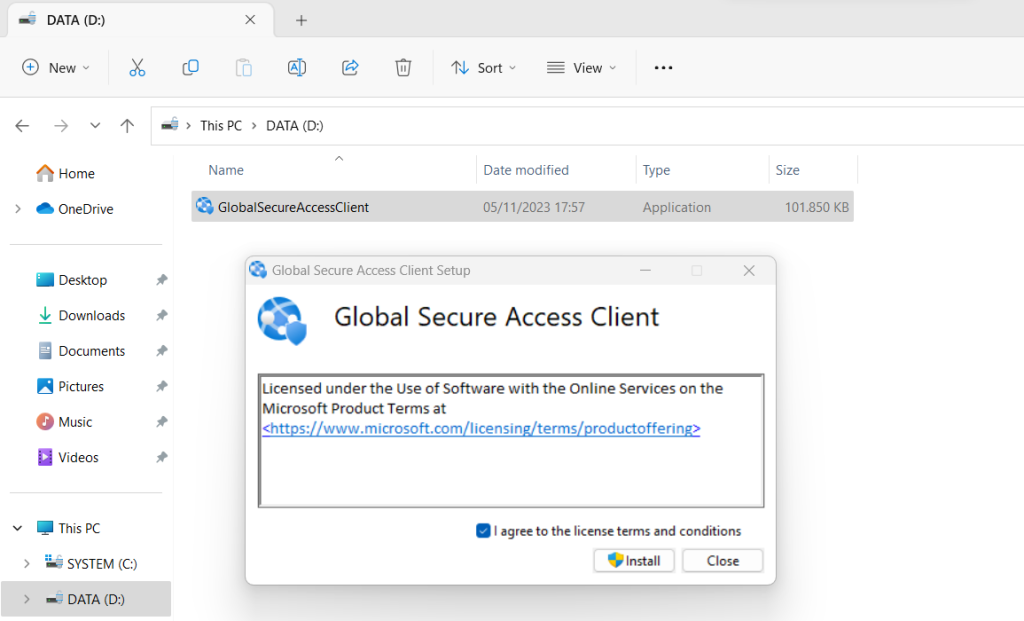
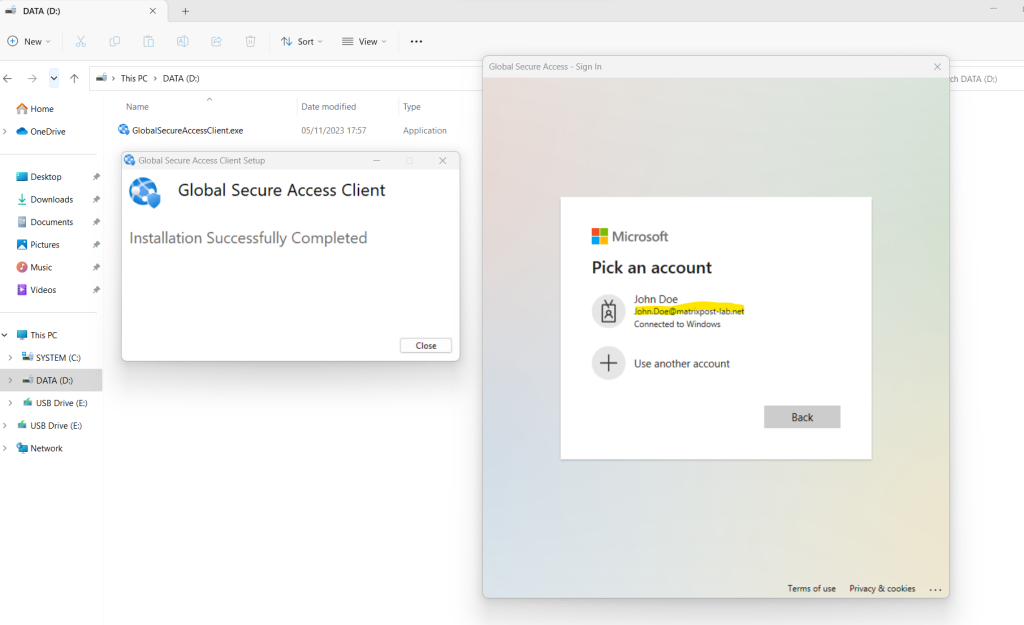
After the client is installed, users are prompted to sign in with their Microsoft Entra credentials.
After users sign in, the connection icon turns green, and moving in Windows 11 the mouse over the icon shows a connected state.
To troubleshoot the Global Secure Access Client, right-click the client icon in the taskbar.
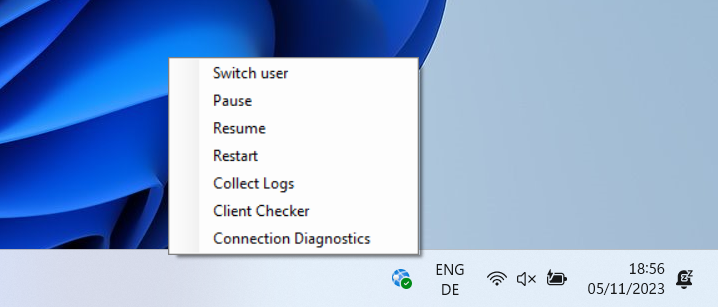
- Switch user
- Forces sign-in screen to change user or reauthenticate the existing user.
- Pause
- This option can be used to temporarily disable traffic tunneling. As this client is part of your organization’s security posture we recommend leaving it running always.
- This option stops the Windows services related to client. When these services are stopped, traffic is no longer tunneled from the client machine to the cloud service. Network traffic behaves as if the client isn’t installed while the client is paused. If the client machine is restarted, the services automatically restart with it.
- Resume
- This option starts the underlying services related to the Global Secure Access Client. This option would be used to resume after temporarily pausing the client for troubleshooting. Traffic resumes tunneling from the client to the cloud service.
- Restart
- This option stops and starts the Windows services related to client.
- Collect logs
- Collect logs for support and further troubleshooting. These logs are collected and stored in C:Program FilesGlobal Secure Access ClientLogs by default.
- These logs include information about the client machine, the related event logs for the services, and registry values including the traffic forwarding profiles applied.
- Collect logs for support and further troubleshooting. These logs are collected and stored in C:Program FilesGlobal Secure Access ClientLogs by default.
- Client Checker
- Runs a script to test client components ensuring the client is configured and working as expected.
- Connection Diagnostics provides a live display of client status and connections tunneled by the client to the Global Secure Access service.
- Summary tab shows general information about the client configuration including: policy version in use, last policy update date and time, and the ID of the tenant the client is configured to work with.
- Hostname acquisition state changes to green when new traffic acquired by FQDN is tunneled successfully based on a match of the destination FQDN in a traffic forwarding profile.
- Flows show a live list of connections initiated by the end-user device and tunneled by the client to the Global Secure Access edge. Each connection is new row.
- Timestamp is the time when the connection was first established.
- Fully Qualified Domain Name (FQDN) of the destination of the connection. If the decision to tunnel the connection was made based on an IP rule in the forwarding policy not by an FQDN rule, the FQDN column shows N/A.
- Source port of the end-user device for this connection.
- Destination IP is the destination of the connection.
- Protocol only TCP is supported currently.
- Process name that initiated the connection.
- Flow active provides a status of whether the connection is still open.
- Sent data provides the number of bytes sent by the end-user device over the connection.
- Received data provides the number of bytes received by the end-user device over the connection.
- Correlation ID is provided to each connection tunneled by the client. This ID allows tracing of the connection in the client logs (event viewer and ETL file) and the Global Secure Access traffic logs.
- Flow ID is the internal ID of the connection used by the client shown in the ETL file.
- Channel name identifies the traffic forwarding profile to which the connection is tunneled. This decision is taken according to the rules in the forwarding profile.
- HostNameAcquisition provides a list of hostnames that the client acquired based on the FQDN rules in the forwarding profile. Each hostname is shown in a new row. Future acquisition of the same hostname creates another row if DNS resolves the hostname (FQDN) to a different IP address.
- Timestamp is the time when the connection was first established.
- FQDN that is resolved.
- Generated IP address is an IP address generated by the client for internal purposes. This IP is shown in flows tab for connections that are established to the relative FQDN.
- Original IP address is the first IPv4 address in the DNS response when querying the FQDN. If the DNS server that the end-user device points to doesn’t return an IPv4 address for the query, the original IP address shows 0.0.0.0.
- Services shows the status of the Windows services related to the Global Secure Access Client. Services that are started have a green status icon, services that are stopped show a red status icon. All three Windows services must be started for the client to function.
- Channels list the traffic forwarding profiles assigned to the client and the state of the connection to the Global Secure Access edge.
- Summary tab shows general information about the client configuration including: policy version in use, last policy update date and time, and the ID of the tenant the client is configured to work with.
Event logs related to the Global Secure Access Client can be found in the Event Viewer under Applications and Services/Microsoft/Windows/Global Secure Access Client/Operational. These events provide useful detail regarding the state, policies, and connections made by the client.
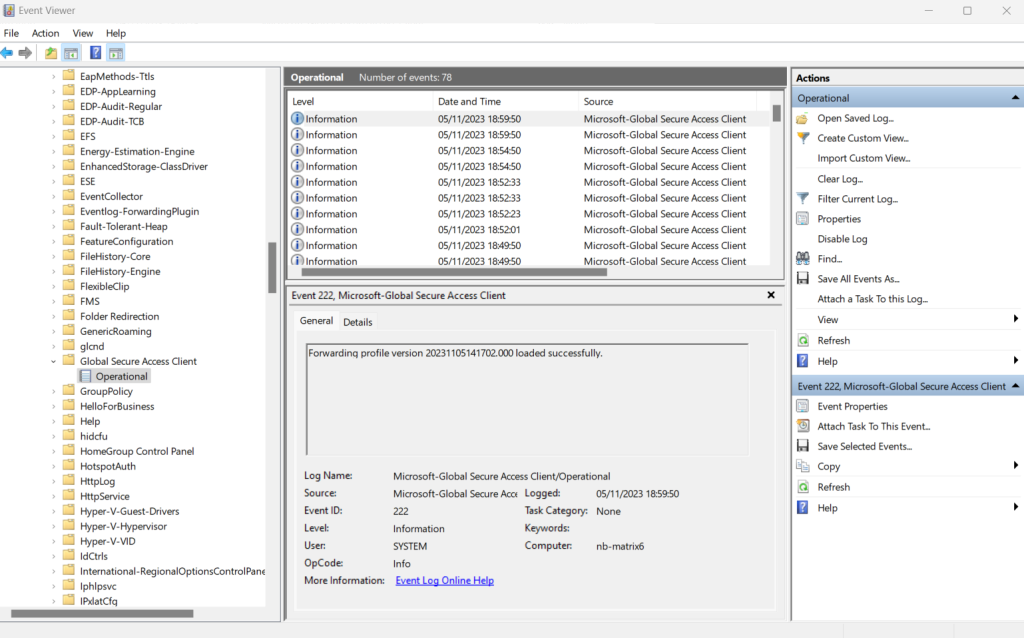
Demonstrate Conditional Access Policies
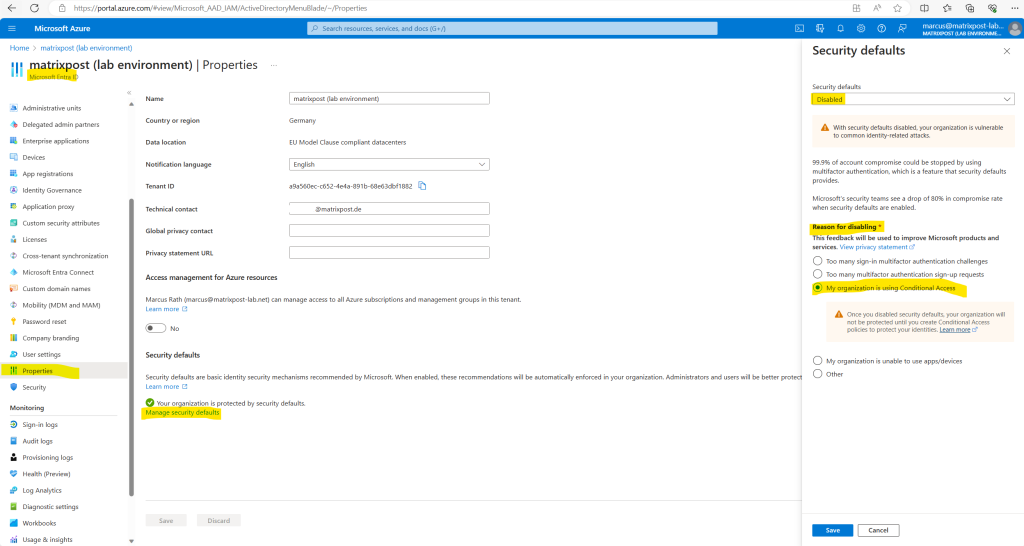
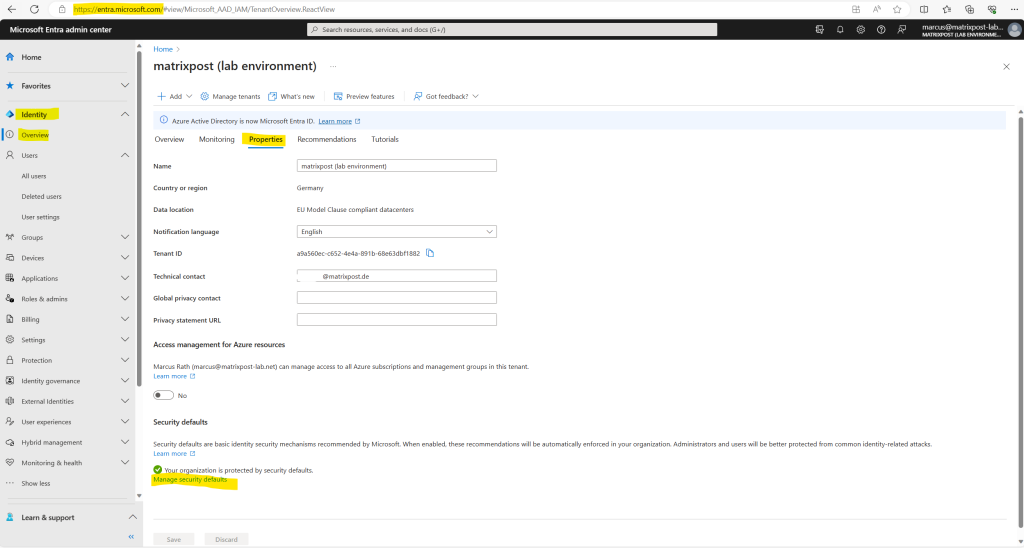
Security defaults must be disabled to enable Conditional Access policy.
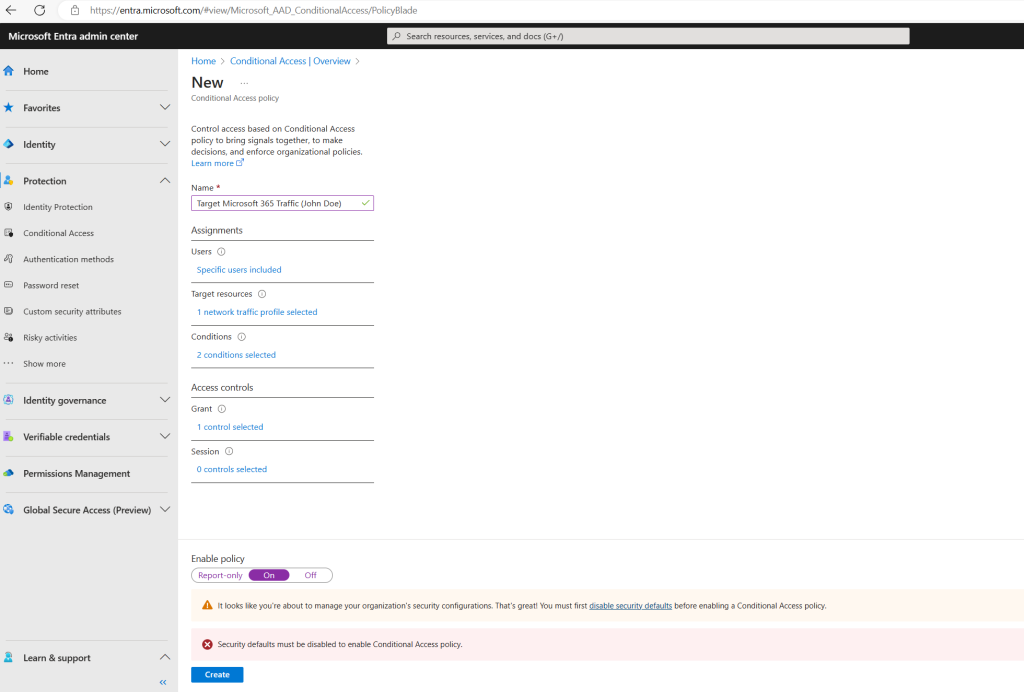
You can enable or disable security defaults either in the Microsoft Entra admin center or the Microsoft Entra ID blade in the Azure portal.
Using the Azure portal and Microsoft Entra ID blade.
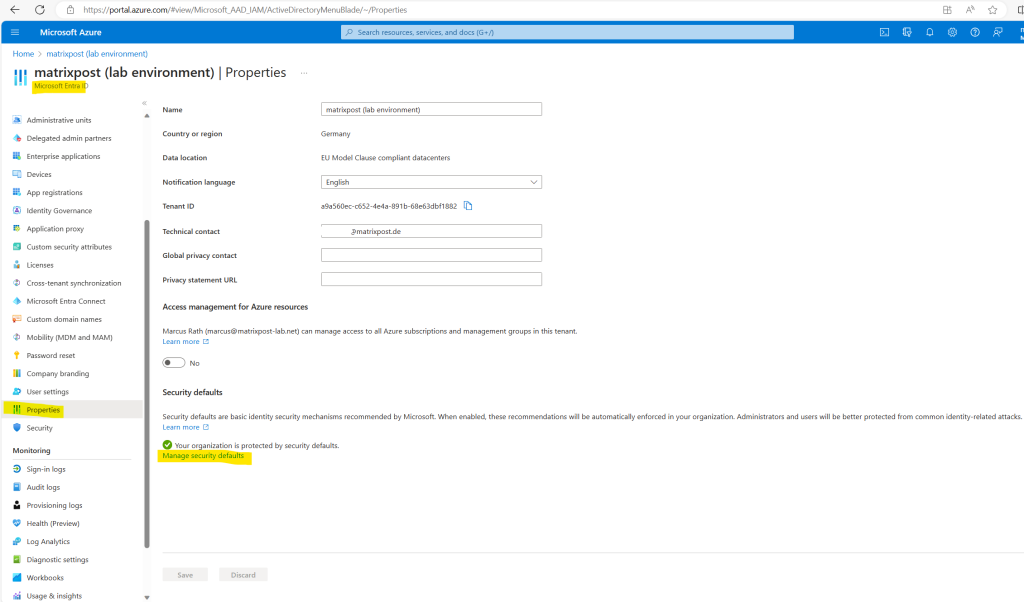
Using the Microsoft Entra admin center.
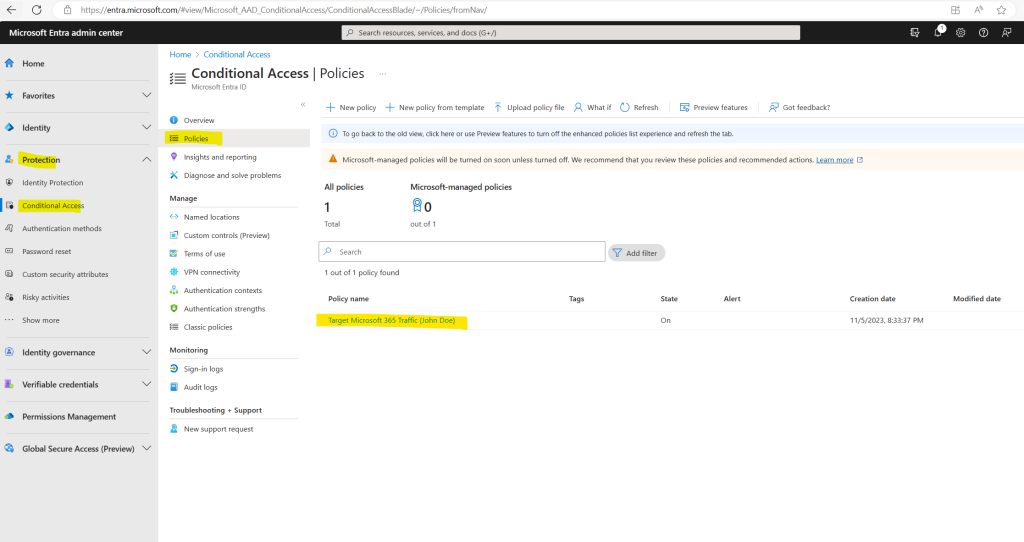
After disabling security defaults I can create the new conditional access policy for Global Secure Access.
From now on you will also under Global Secure Access (Preview) -> Connect -> Traffic forwarding that one conditional access policy is linked to the Microsoft 365 access profile.
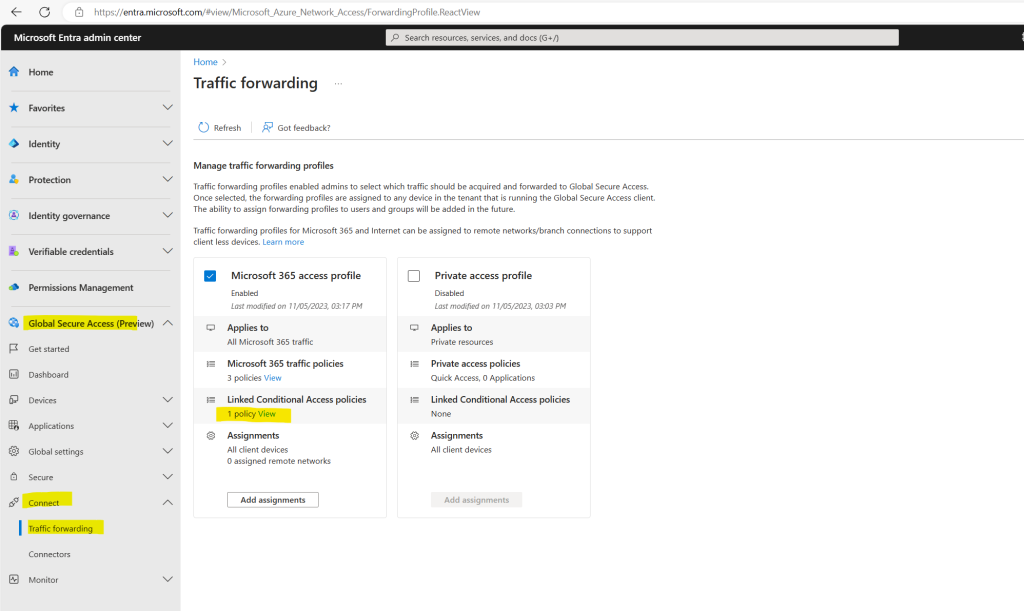
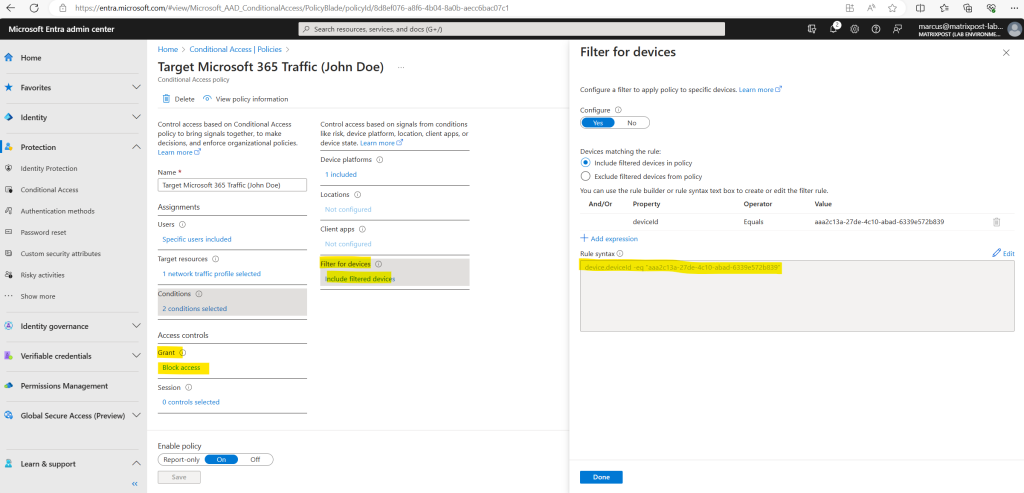
Below for example the conditional access policy filters for the device id aaa2c13a-27de-4c10-abad-6339e572b839 (Notebook from John Doe in the lab environment).
That means when John Doe is trying to connect to the Global Secure Access service by using its notebook, the policy will match and therefore block access to Global Secure Access.
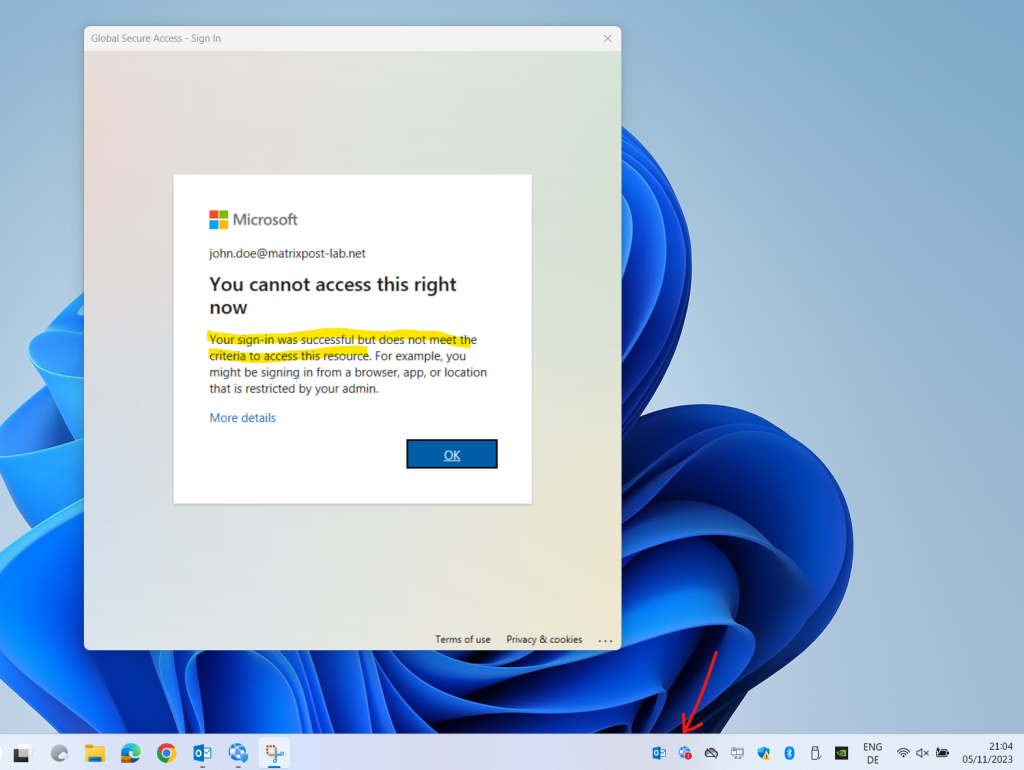
John Doe couldn’t connect and sign-in to the Global Secure Access service from his notebook.
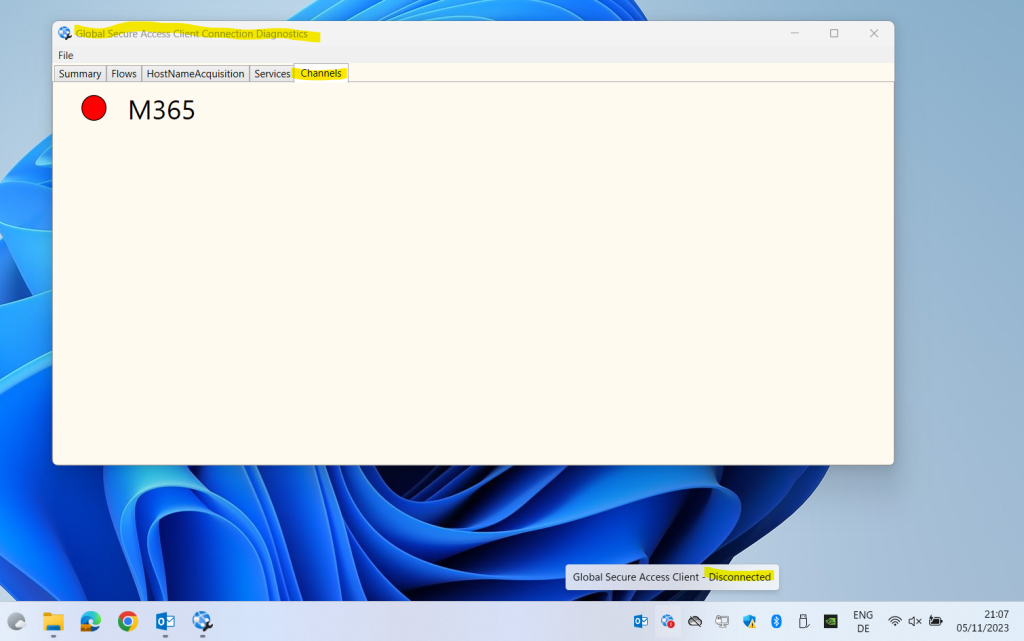
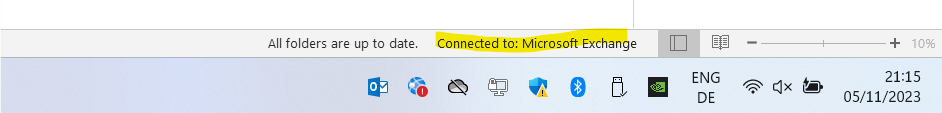
Nevertheless John Doe could still access its Exchange Online mailbox by using Outlook or Outlook on the web.
!!! Note !!!
If the Global Secure Access client isn’t able to connect to the service (for example due to an authorization or Conditional Access failure), the service bypasses the traffic. Traffic is sent direct-and-local instead of being blocked. In this scenario, you can create a Conditional Access policy for the compliant network check, to block traffic if the client isn’t able to connect to the service.
To finally block traffic if the client couldn’t connect to the service, we need to create a conditional access policy for the compliant network check.
Below I will show how to create this conditional access policy for the compliant network check and to finally block access to Microsoft 365 services for Global Secure Access clients they couldn’t connect to the Global Secure Access service.
Enable compliant network check with Conditional Access
Organizations who use Conditional Access along with the Global Secure Access preview, can prevent malicious access to Microsoft apps, third-party SaaS apps, and private line-of-business (LoB) apps using multiple conditions to provide defense-in-depth. These conditions may include device compliance, location, and more to provide protection against user identity or token theft. Global Secure Access introduces the concept of a compliant network within Conditional Access and continuous access evaluation. This compliant network check ensures users connect from a verified network connectivity model for their specific tenant and are compliant with security policies enforced by administrators.
The Global Secure Access Client installed on devices or configured remote network allows administrators to secure resources behind a compliant network with advanced Conditional Access controls. This compliant network makes it easier for administrators to manage and maintain, without having to maintain a list of all of an organization’s locations IP addresses. Administrators don’t need to hairpin traffic through their organization’s VPN egress points to ensure security.
Source: https://learn.microsoft.com/en-us/entra/global-secure-access/how-to-compliant-network
To enable the required setting to allow the compliant network check, an administrator must take the following steps.
Browse to Global Secure Access (Preview) > Global settings > Session management Adaptive access.
Select the toggle to Enable Global Secure Access signaling in Conditional Access.
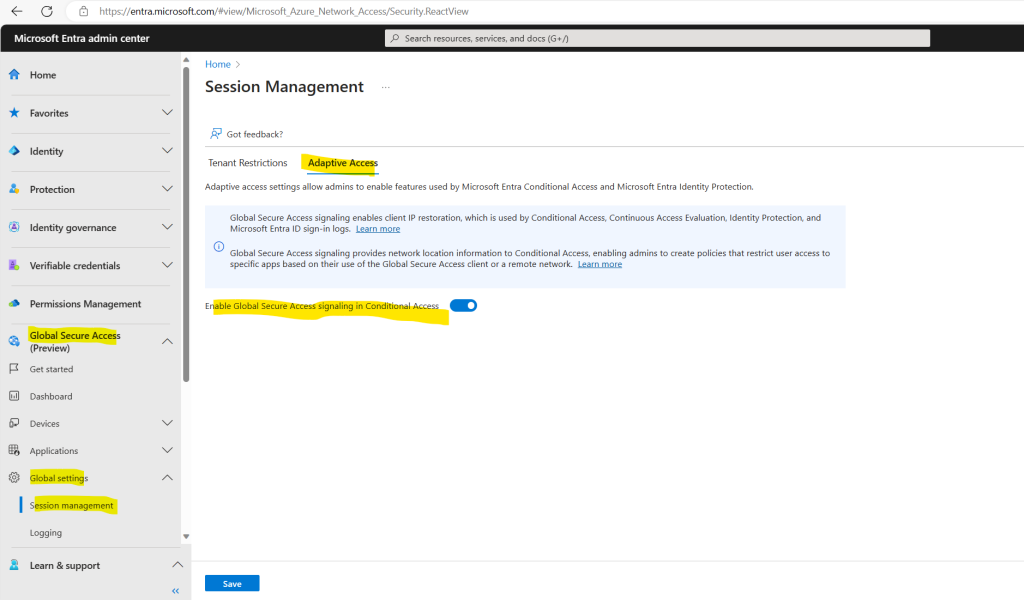
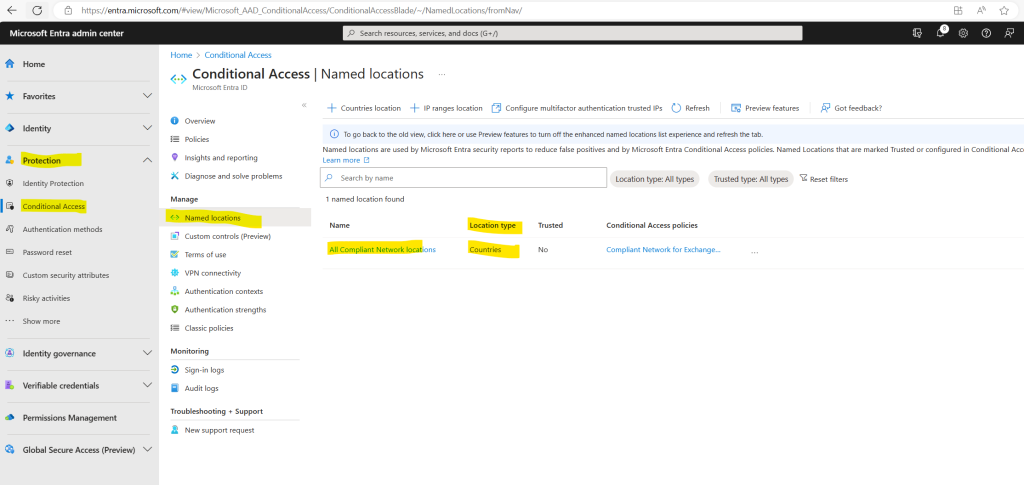
Browse to Protection > Conditional Access > Named locations.
Confirm you have a location called All Compliant Network locations with location type Network Access. Organizations can optionally mark this location as trusted.
Btw. the All Compliant Network locations will be created when enabling above the option Enable Global Secure Access signaling in Conditional Access.
In my case the All Compliant Network locations have a location type with Countries instead of Network Access here. Nevertheless when I have to select this All Compliant Network locations later when creating a correspondent conditional access policy for, I can select it and also the location type then is correct shown up with Network Access, we will see this further down.
So I suppose the reason for is that Global Secure Access is still in preview.
You will also get an error message when clicking on the location as shown below, when trying this in other tenants, I will get btw. the same behavior.
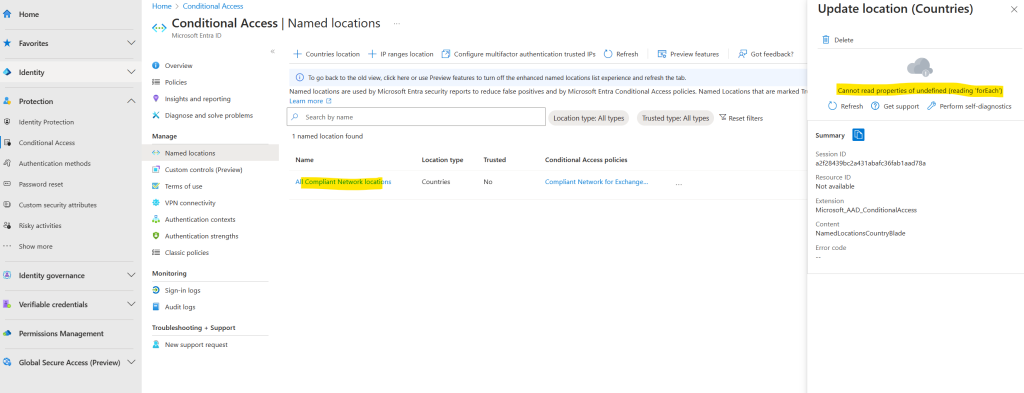
So for now I will ignore this.
Next I will create a new conditional access policy which will use the All Compliant Network locations condition in order to exclude clients from being matched with the policy.
So this new policy requires Exchange Online to be accessed from behind a compliant network as part of the preview.
All clients they will be able to connect to Global Secure Access will therefore be excluded from the policy. If the policy matched for a client, access to Exchange Online will be blocked.
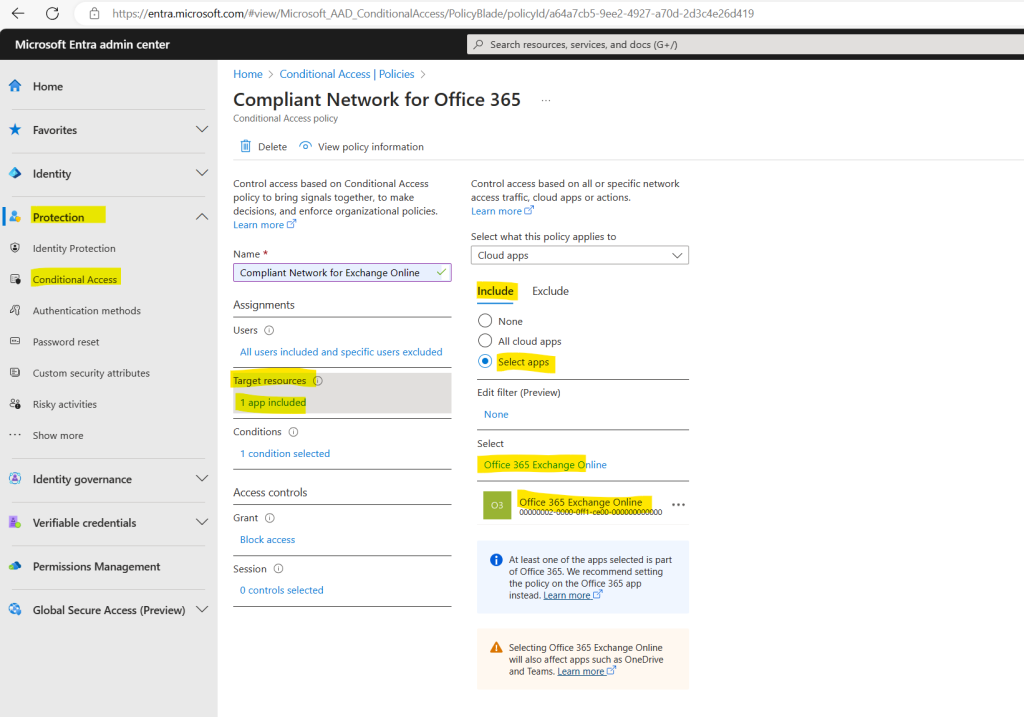
For target resources I will select in the policy Office 365 Exchange Online which will target Exchange Online.
You will see here a message with At least one of the apps selected is part of Office 365. We recommend setting the policy on the Office 365 app instead.
!!! Note !!! Office 365 apps are currently NOT supported, so do not select this option.
A complete list of all services included can be found in the article Apps included in Conditional Access Office 365 app suite.
In the Microsoft Entra admin center select Protection -> Conditional Access -> Policies -> New policy
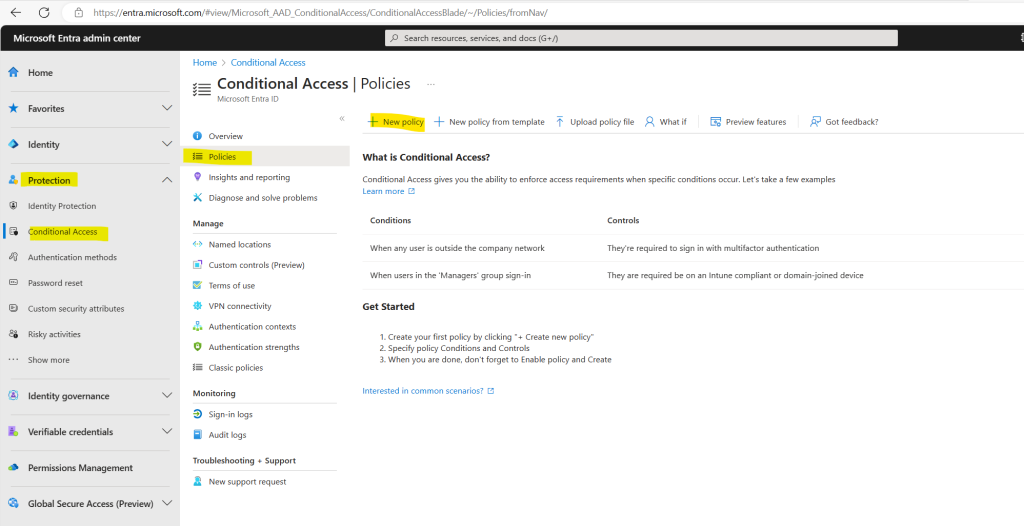
Give your policy a name and under Assignments/Users I will include All users and just exclude my own admin user to prevent I will get locked myself.
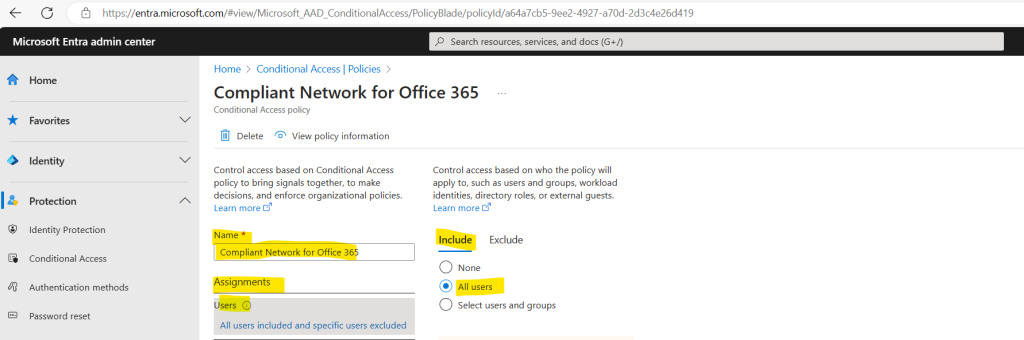
As already mentioned further above, for the target resources I will select here Office 365 Exchange Online.
As already mentioned Office 365 apps are currently NOT supported, so do not select this option!
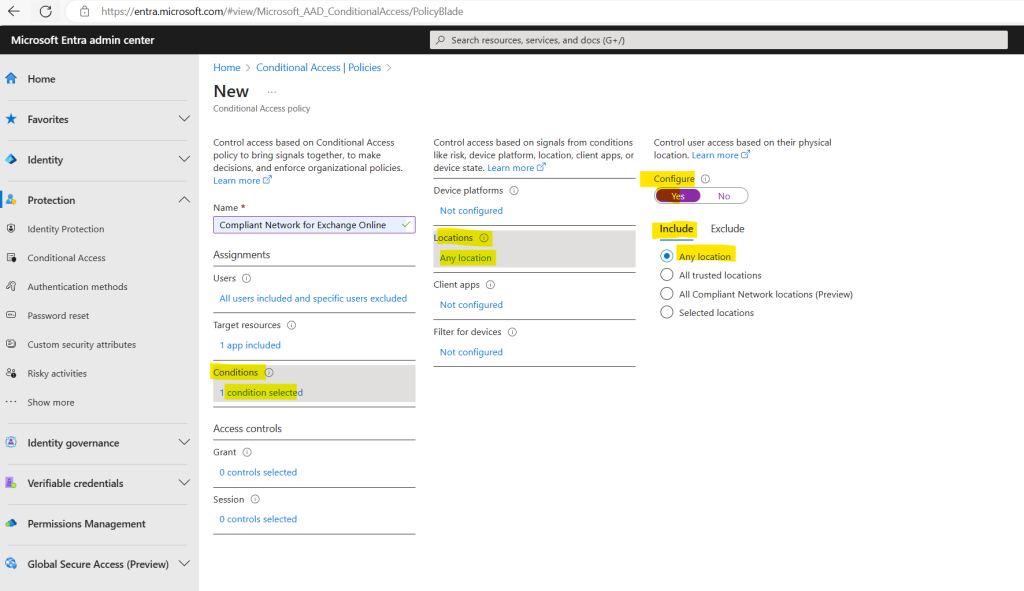
Now it gets interesting by selecting the conditions. Here first enable the configuration and then under Include select Any location.
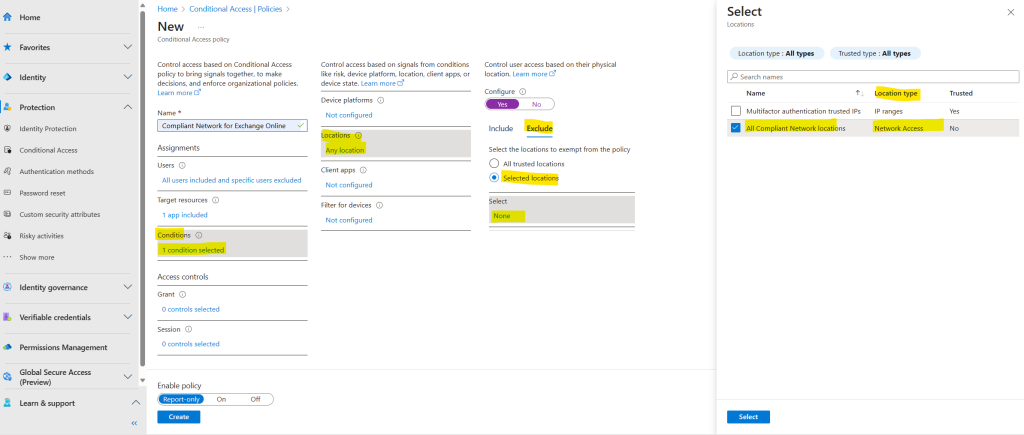
The interesting point is here within the Exclude section from conditions.
First select Selected locations and then the previously mentioned All Compliant Network location. As you can see, here the location type is correct listed with Network Access.
By selecting this location, all clients using the Global Secure Access client or remote network to access the Global Secure Access service, will be excluded from the policy and therefore not blocked to access Exchange Online.
In the next step I will configure under Access control to block access in case the policy is matched for clients, which is the case when they either not using the Global Secure Access client or remote network.
As mentioned, here I will select to block access to Office 365 Exchange Online which is selected for the target resource.
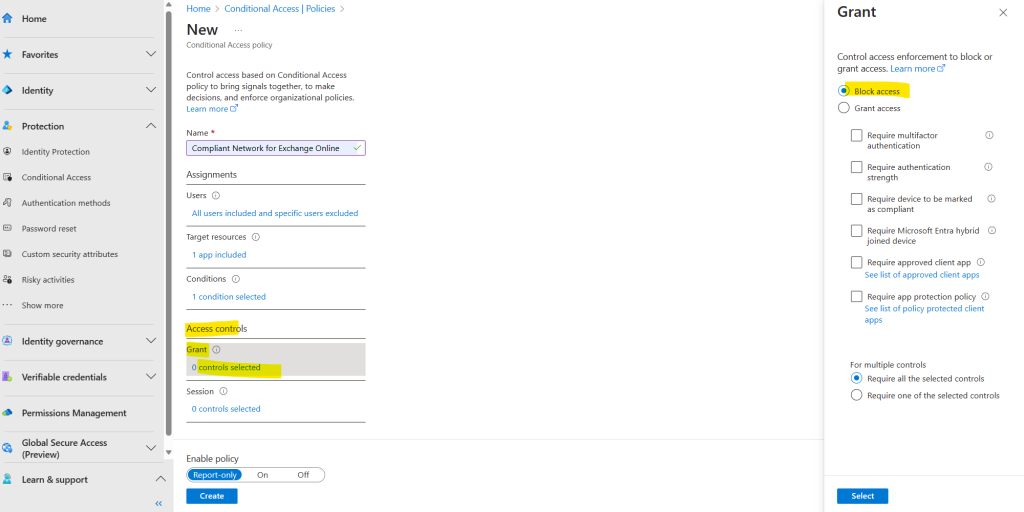
Finally I will enable and create the policy by switching to On and clicking on Create. For a production tenant you can first just report the policy to check the behavior before enabling.
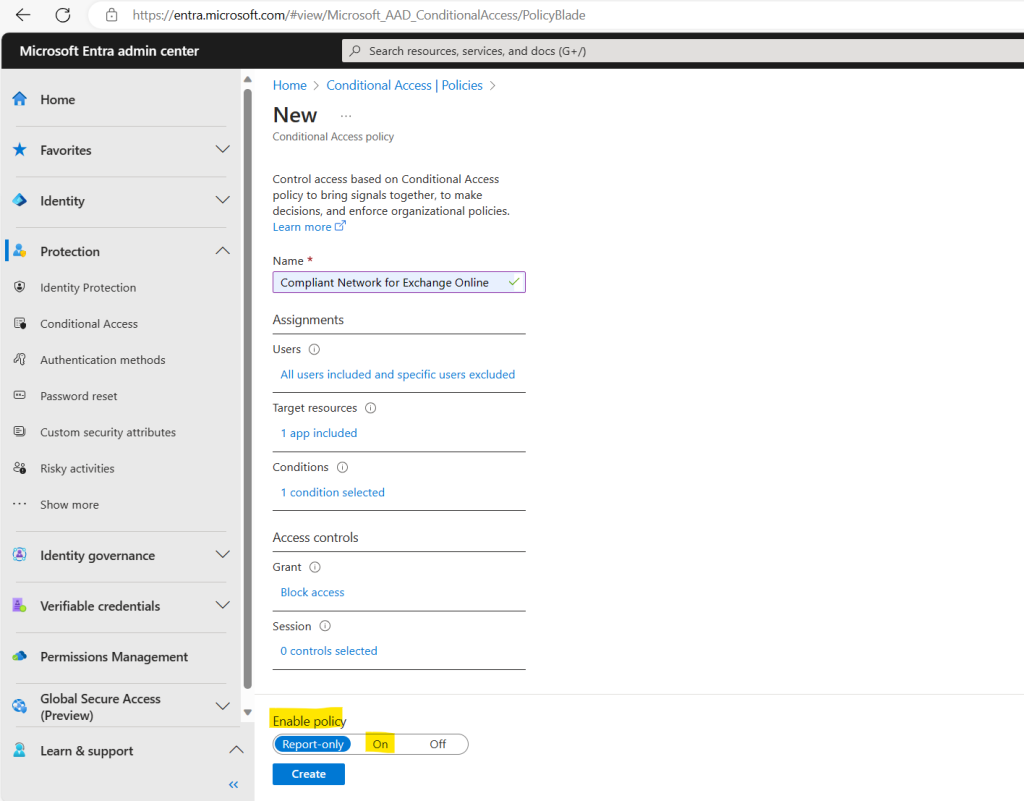
From now on all clients they will not use either the Global Secure Access client or remote network, to first connect to the Global Secure Access service, couldn’t finally access Exchange Online.
In order to check if clients they will not use either of them will gets really blocked, I will pause the Global Secure Access client on John Doe’s notebook and then try to connect to Exchange Online by using Outlook and Outlook on the web.
You will see the result in the next section below.
Testing the compliant network policy
A few minutes later after enabling the new conditional access policy and pause the Global Secure Access client on John Doe’s notebook, access was blocked to Exchange Online by using Outlook as shown below.
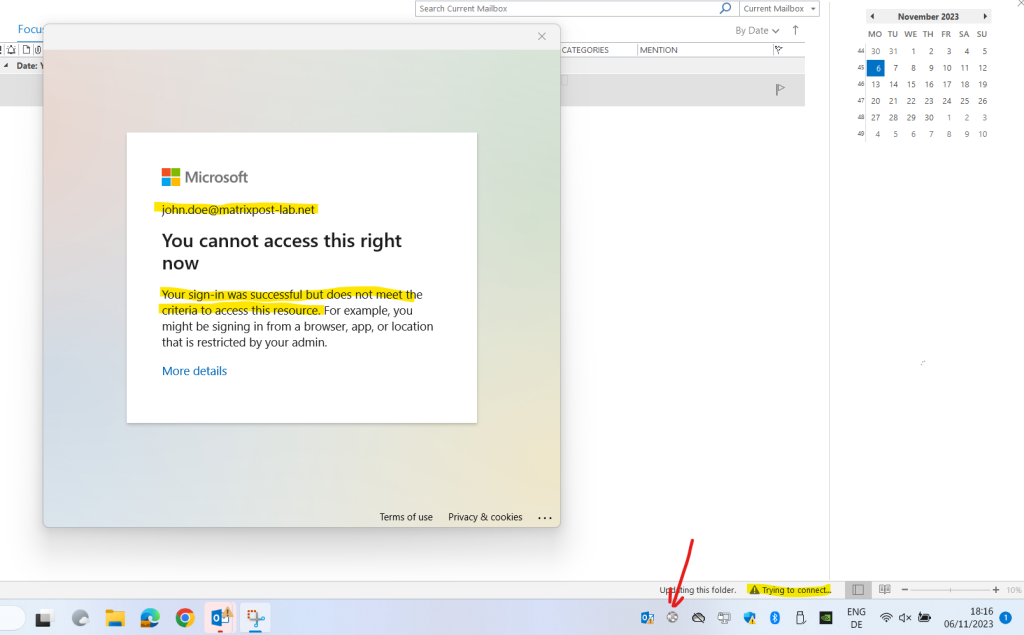
By using the Microsoft Edge browser John Doe was still able to access Exchange Online using Outlook on the web. Only after using an incognito window to eliminate stored cookies including access tokens, access to Exchange Online was finally also in Microsoft Edge blocked.
So this must have to
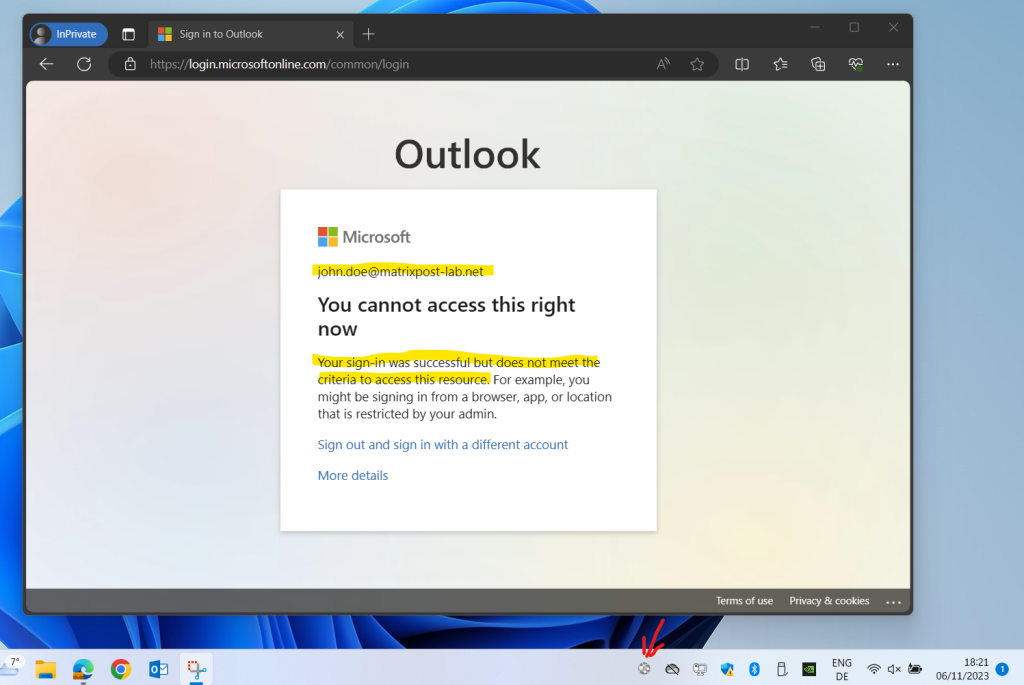
By using the developer tools from the browser you can check which cookies the website will store and you can also delete them here.
Below you can see the OpenIdConnect.token.v1 cookie which stores the ID token from OpenID to access Exchange Online.
The ID token introduced by OpenID Connect is issued by the authorization server, the Microsoft identity platform, when the client application requests one during user authentication. The ID token enables a client application to verify the identity of the user and to get other information (claims) about them.
Source: https://learn.microsoft.com/en-us/entra/identity-platform/v2-protocols-oidc#enable-id-tokens
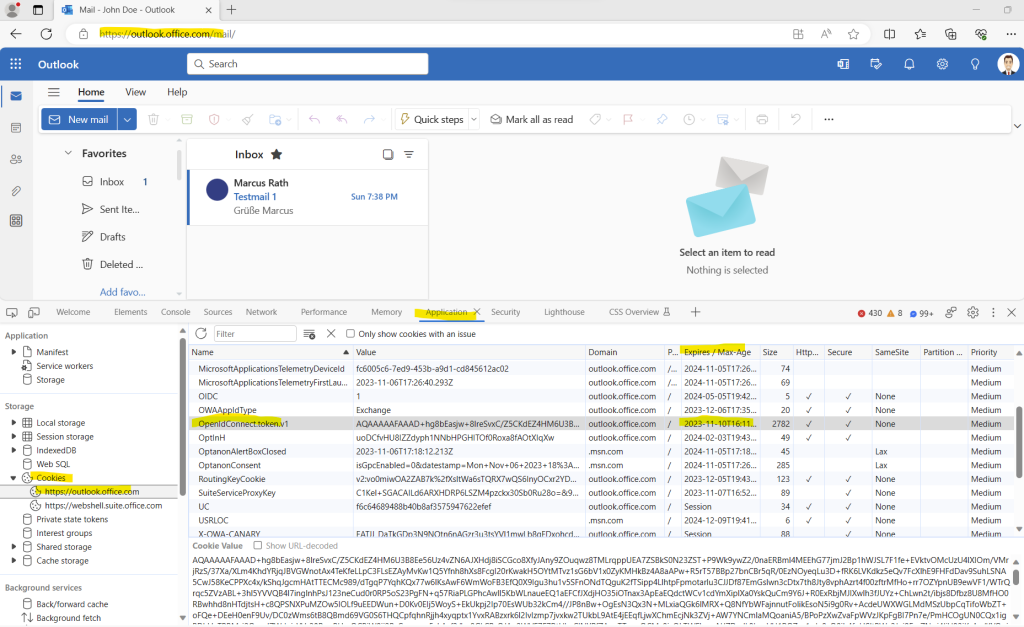
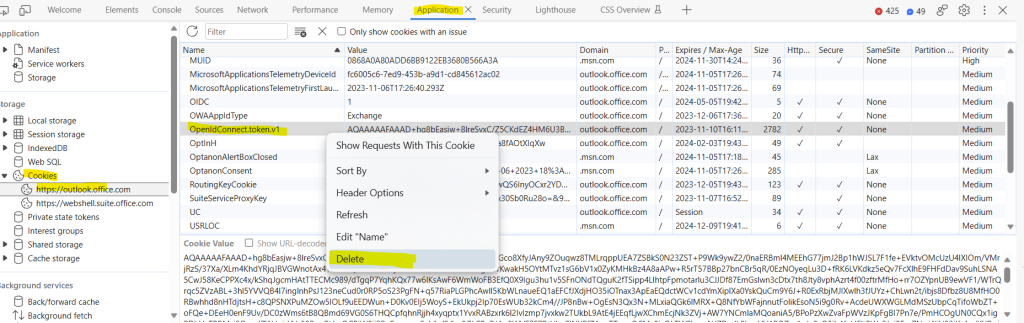
So now I will delete this cookie in order to request a new access token for Exchange Online.
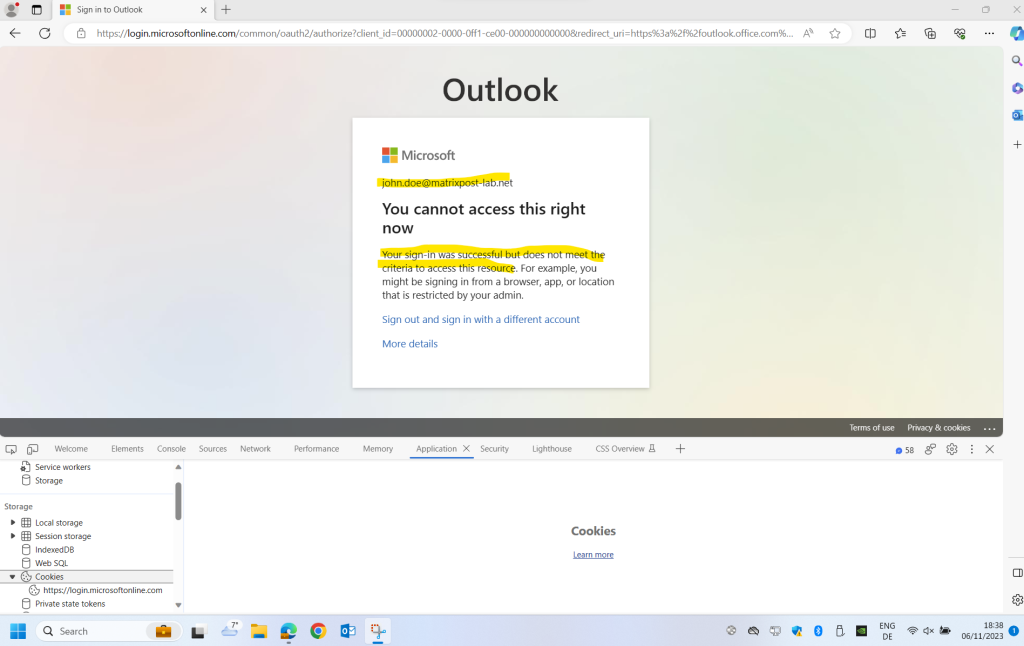
Now finally access to Exchange Online is blocked. So you see when enabling the policy you still have to wait till the clients renewing their access token to get finally blocked.
More about OAuth 2.0 and OpenID Connect you will also find in my blog and the URL below.
https://blog.matrixpost.net/?category=oauth2-0
What is Microsoft Entra?
To see all products included in the unifying brand named Microsoft Entra please take a look at my following post.
Links
Get started with Global Secure Access
https://learn.microsoft.com/en-us/entra/global-secure-access/how-to-get-started-with-global-secure-accessGlobal Secure Access documentation (Microsoft Entra Internet Access and Private Access)
https://learn.microsoft.com/en-us/entra/global-secure-access/Microsoft Entra Internet Access: An Identity-Centric Secure Web Gateway Solution
https://techcommunity.microsoft.com/t5/microsoft-entra-azure-ad-blog/microsoft-entra-internet-access-an-identity-centric-secure-web/ba-p/3922548



