Enroll Windows Computer into Microsoft Intune
Microsoft Intune is a cloud-based endpoint management solution. It manages user access and simplifies app and device management across your many devices, including mobile devices, desktop computers, and virtual endpoints.
You can manage users and devices, including devices owned by your organization and personally owned devices (BYOD). Microsoft Intune supports Android, Android Open Source Project (AOSP), iOS/iPadOS, macOS, and Windows client devices. With Intune, you can use these devices to securely access organization resources with policies you create.
Source: https://learn.microsoft.com/en-us/mem/intune/fundamentals/what-is-intune
Below we will see the separate steps to enroll a Windows 10 computer into Intune.
Deploy Intune
First if not set by default, we need to enable Intune as the MDM authority which will be used to manage our devices.
Sign in to the Microsoft Intune admin center (formerly Microsoft Endpoint Manager (MEM)), and sign up for Intune. If you have an existing subscription, you can also sign in to it.
Set Intune Standalone as the MDM authority.
The mobile device management (MDM) authority setting determines how you manage your devices. As an IT admin, you must set an MDM authority before users can enroll devices for management. You should also be assigned an Intune license to to set the MDM Authority.
Source: https://learn.microsoft.com/en-us/mem/intune/fundamentals/mdm-authority-set
In the Microsoft Intune admin center, select the orange banner to open the Mobile Device Management Authority setting.
The orange banner is only displayed if you haven’t yet set the MDM authority.
When I was clicking on the orange banner, I was running into the following error.
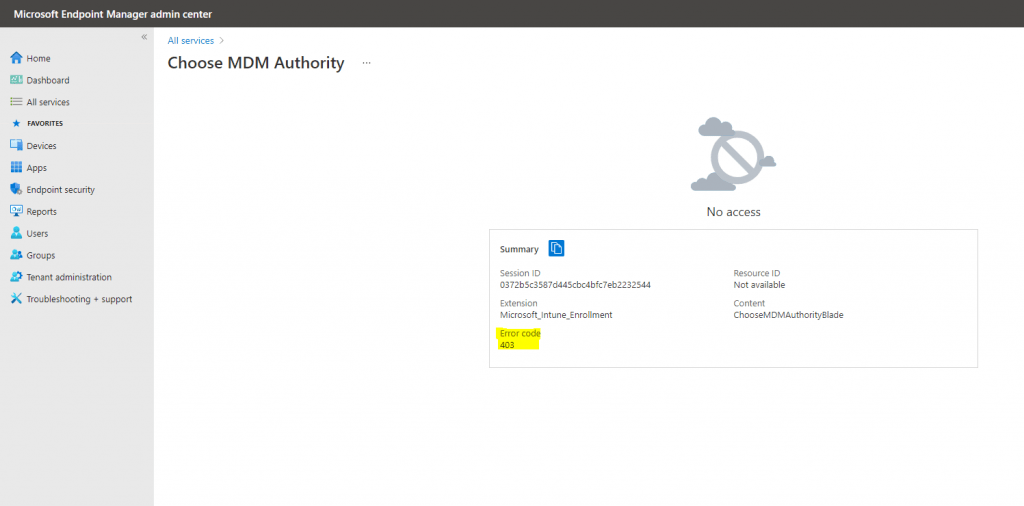
The reason for is that you first need a valid license for Microsoft Intune assigned to your logged-in user. After purchasing and assigning the Enterprise Mobility + Security E3 license which includes Intune it works and also the Connector status appears now healthy.
Microsoft Intune licensing
https://learn.microsoft.com/en-us/mem/intune/fundamentals/licensesDevice-only licenses
https://learn.microsoft.com/en-us/mem/intune/fundamentals/licenses#device-only-licensesUnlicensed admins
You can give administrators access to Microsoft Endpoint Manager without them requiring an Intune license. This feature applies to any administrator, including Intune administrators, global administrators, Azure AD administrators, and so on. Other features or services, such as those in Azure Active Directory (AD) Premium, may require a license for the administrator.Source: https://learn.microsoft.com/en-us/mem/intune/fundamentals/unlicensed-admins
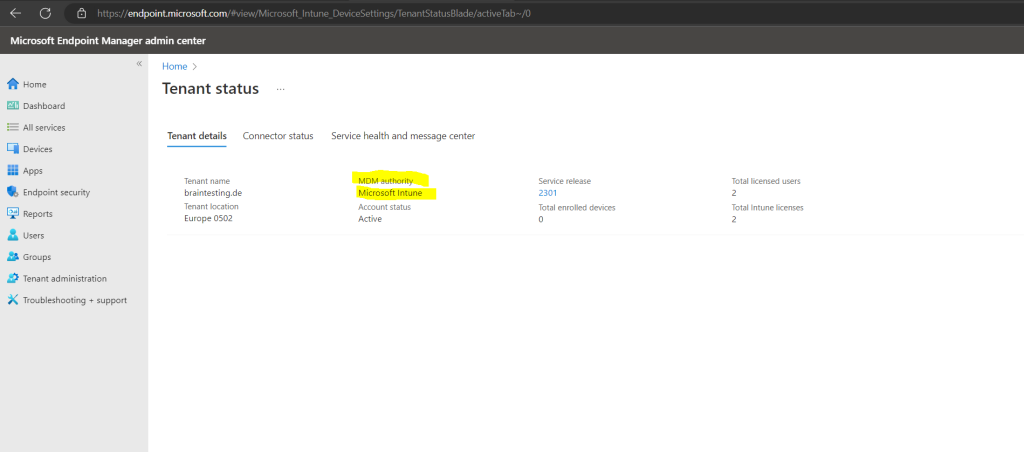
Basically, the MDM authority is automatically set to Intune for the newest tenant service release.
If the MDM authority is unknow, please make sure you have purchased an Intune license.
To check the MDM authority click on Active.
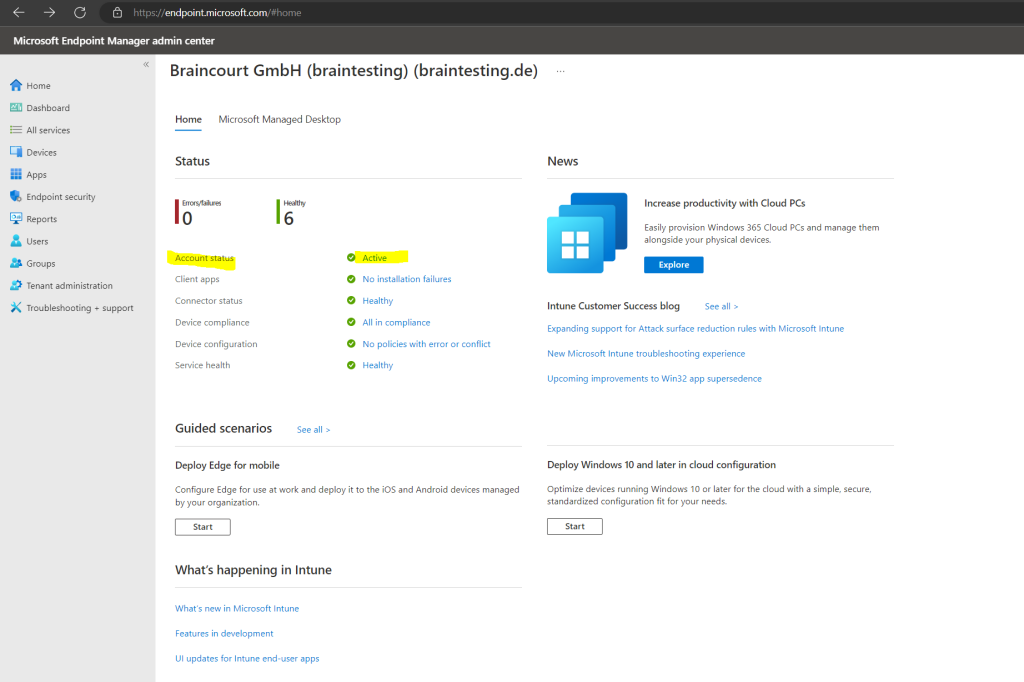
To manage devices in Intune, devices must first be enrolled in the Intune service. Both personally owned and corporate-owned devices can be enrolled for Intune management.
You have the following options when enrolling Windows devices:
Source: https://learn.microsoft.com/en-us/mem/intune/fundamentals/deployment-guide-enrollment-windows
For Windows Autopilot and co-management you can read my following posts.
Enroll devices in Microsoft Intune
There are two ways to get devices enrolled in Intune:
- Users can self-enroll their Windows PCs
- Admins can configure policies to force automatic enrollment without any user involvement
Source: https://learn.microsoft.com/en-us/mem/intune/enrollment/windows-enrollment-methods
For self-enroll the user can either join its device to Azure AD in case of a corporate device or just register it to Azure AD if its a personally owned devices (BYOD). Below we will see both methods and at least how to enforce automatic enrollment by using group policies.
Windows Automatic Enrollment
Automatic enrollment lets users enroll their Windows devices in Intune.
To enroll, users add their work account to their personally owned devices or join corporate-owned devices to Azure Active Directory.
In the background, the device registers and joins Azure Active Directory. Once registered, the device is managed with Intune.
Verify that auto-enrollment is activated for those users who are going to enroll the devices into Mobile Device Management (MDM) with Intune. For more information, see Azure AD and Microsoft Intune: Automatic MDM enrollment in the new Portal.
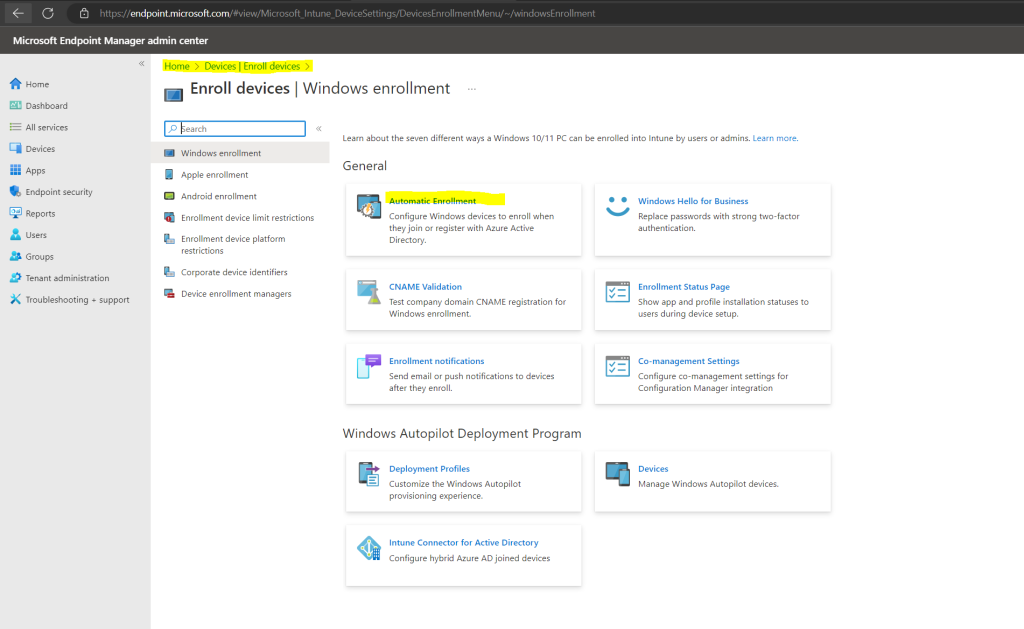
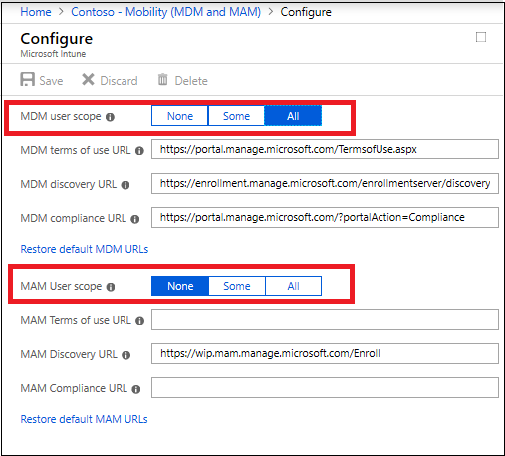
To enable automatic enrollment for Windows BYOD devices to an MDM: configure the MDM user scope to All (or Some, and specify a group) and configure the MAM user scope to None (or Some, and specify a group – ensuring that users are not members of a group targeted by both MDM and MAM user scopes).
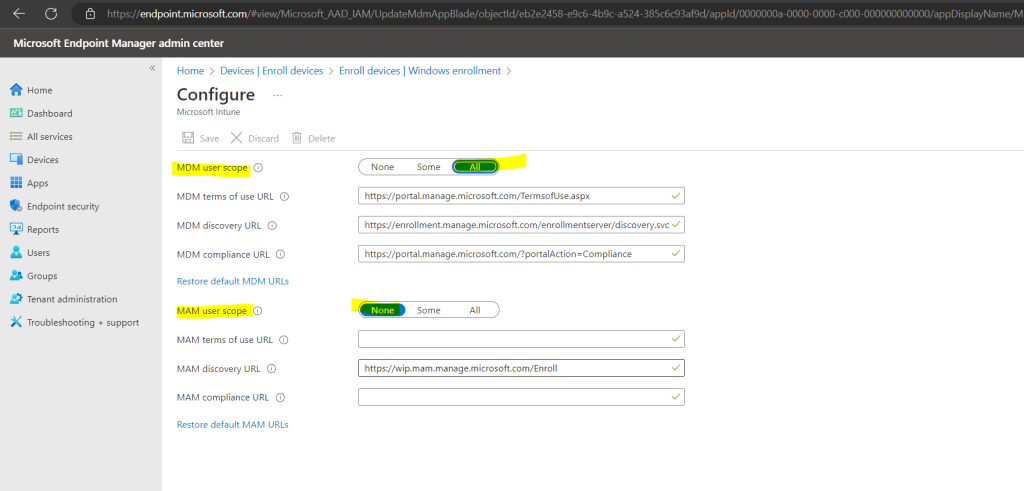
Difference between MDM and MAM
Mobile device management or MDM
Microsoft 365 Business Premium lets you set up policies that protect data on your Windows 10 and 11 devices. When a device is under mobile device management, you control the entire device, and can wipe data from it, and also reset it to factory settings.Mobile application management or MAM
Mobile application management lets you control your business data in your users personal devices, such as iPhones and Androids, and their personal Windows computers. You can use application management policies to prevent your users from copying business data from Office apps to their personal apps. You can also remove all data from the Office apps on their personal devices.Source: https://learn.microsoft.com/en-us/microsoft-365/business/ui/mam-and-mdm?view=o365-worldwide
For Windows BYOD devices, the MAM user scope takes precedence if both the MAM user scope and the MDM user scope (automatic MDM enrollment) are enabled for all users (or the same groups of users). The device will not be MDM enrolled, and Windows Information Protection (WIP) Policies will be applied if you have configured them.
If your intent is to enable automatic enrollment for Windows BYOD devices to an MDM: configure the MDM user scope to All (or Some, and specify a group) and configure the MAM user scope to None (or Some, and specify a group – ensuring that users are not members of a group targeted by both MDM and MAM user scopes).
For corporate devices, the MDM user scope takes precedence if both MDM and MAM user scopes are enabled. The device will get automatically enrolled in the configured MDM.
Join corporate-owned devices to Azure Active Directory to enroll into Intune
Joins the device with Azure Active Directory and enables users to sign in to Windows with their Azure AD credentials. If Auto Enrollment is enabled, the device is automatically enrolled in Intune.
The benefit of auto enrollment is a single-step process for the user. Otherwise, they’ll have to enroll separately through MDM only enrollment and reenter their credentials. Users enroll this way either during initial Windows OOBE or from Settings. The device is marked as a corporate owned device in Intune.
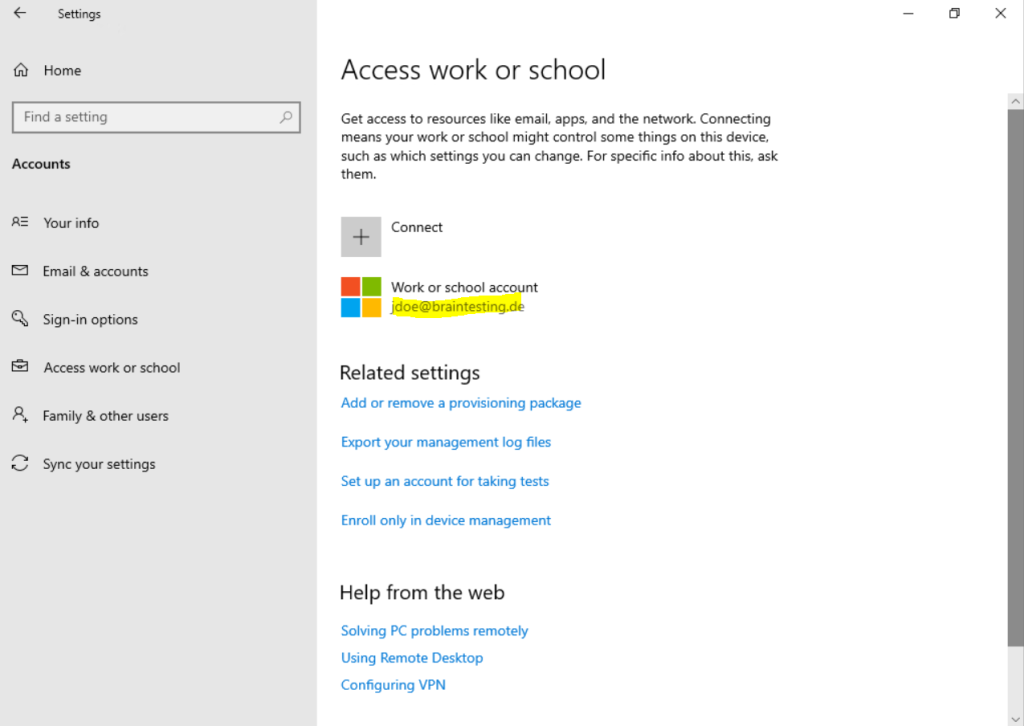
From Settings you need navigate to Accounts –> Access work or school as shown below.
Click on Connect.
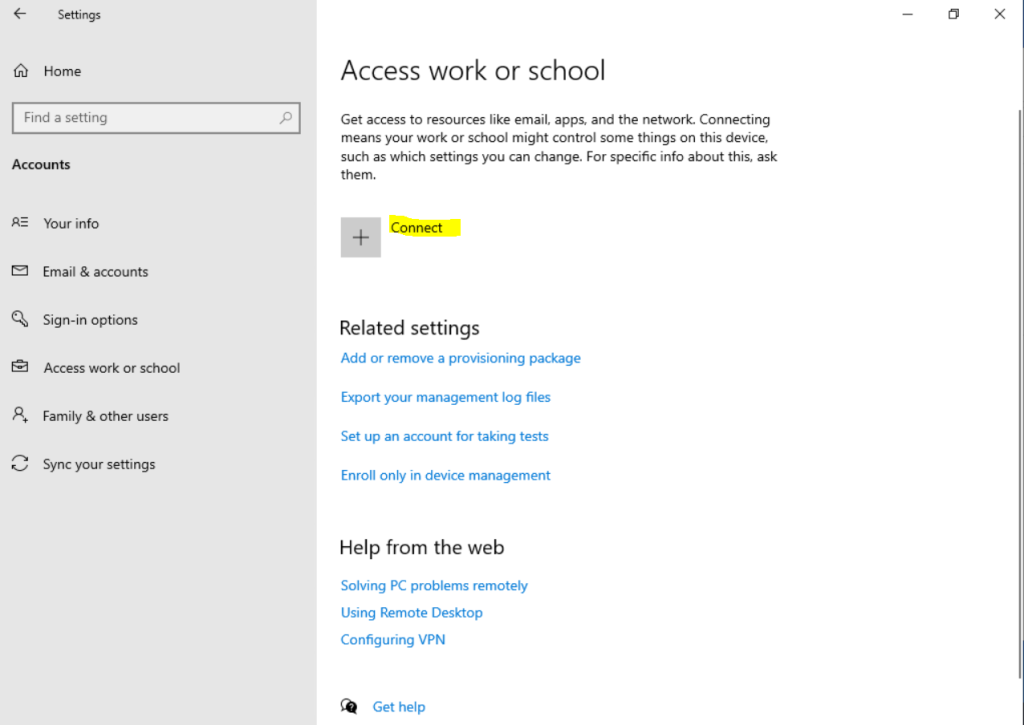
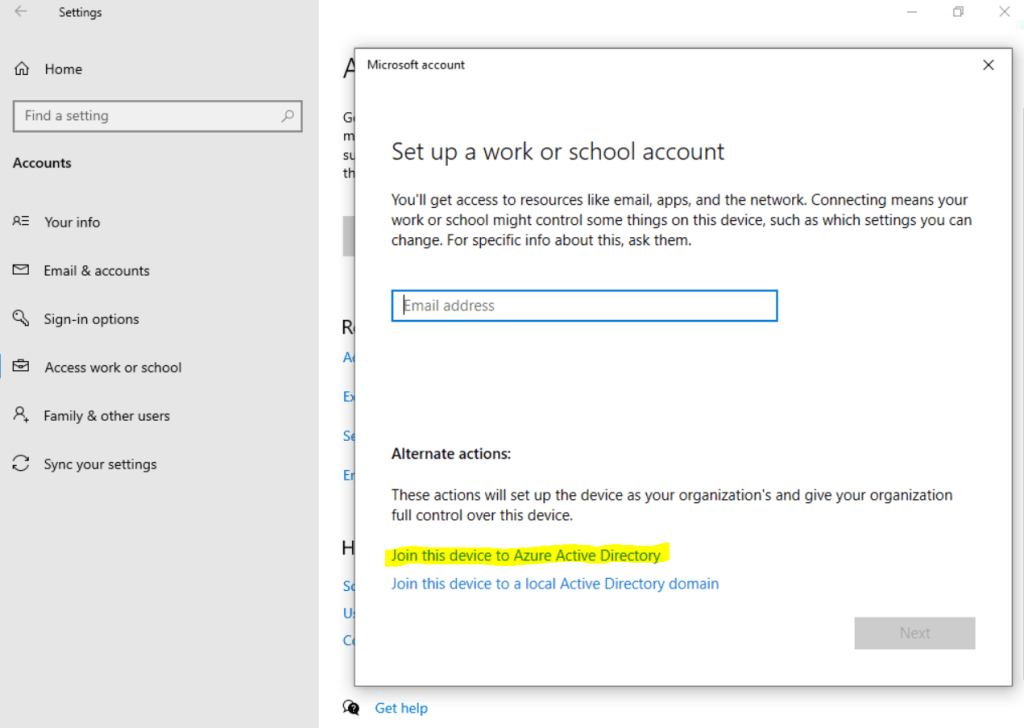
Here just click on the link Join this device to Azure Active Directory.
Do not enter here your email address and click on Next, this would just register the device to Azure AD but not join it.
Further down we will also see how to register the device to Azure AD which you usually just want to do for your personally owned devices (BYOD)
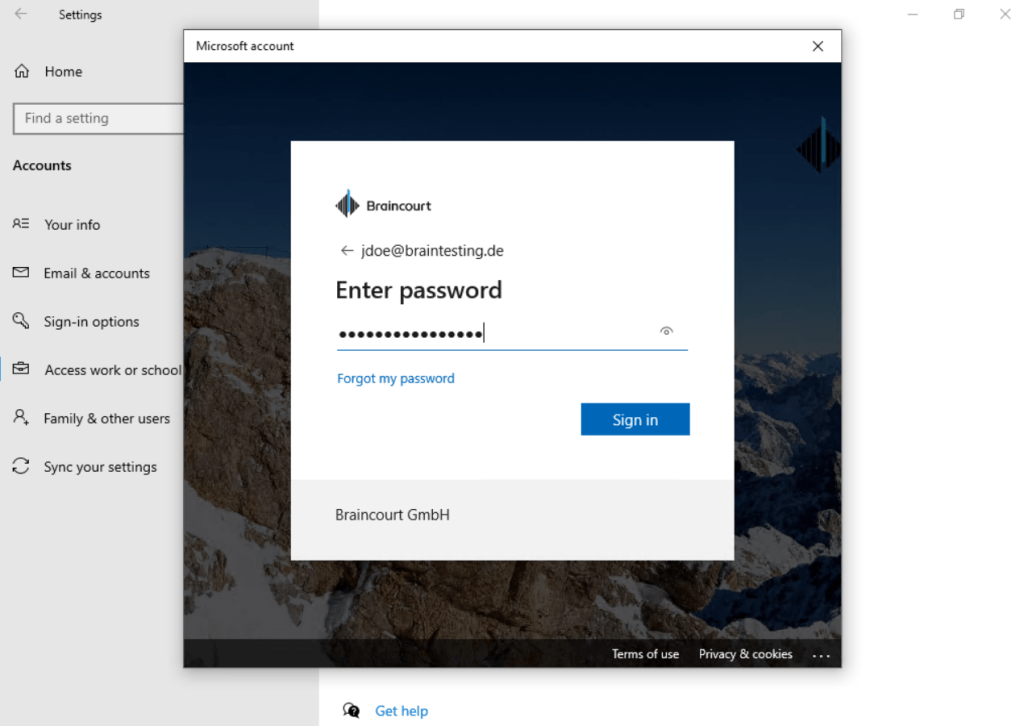
Click on Join
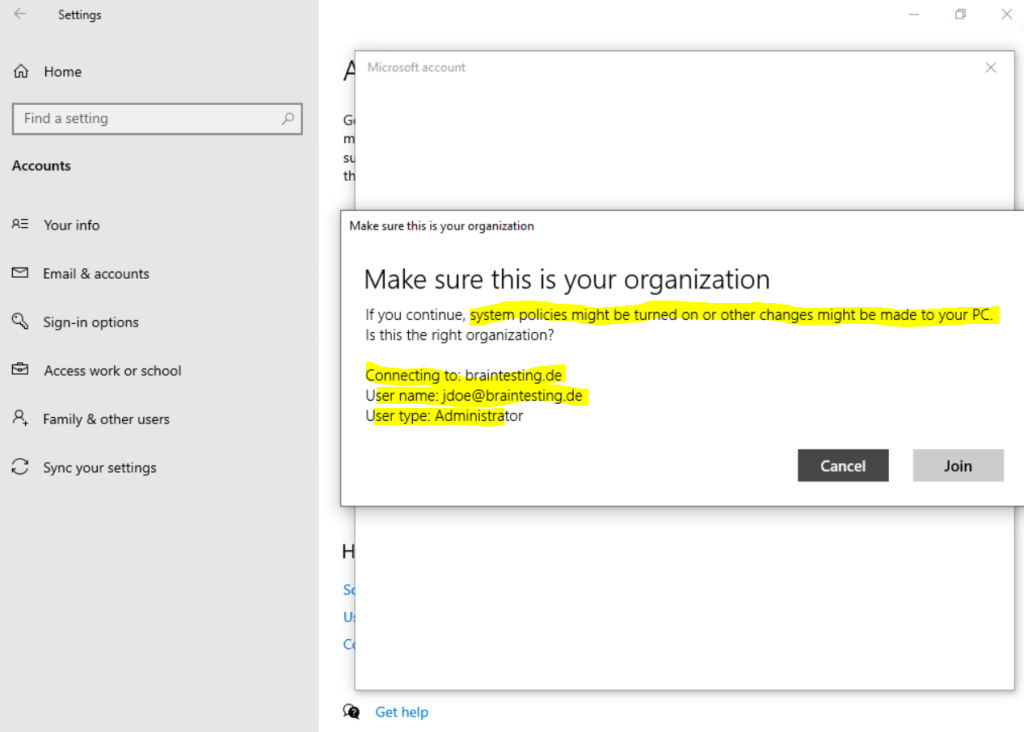
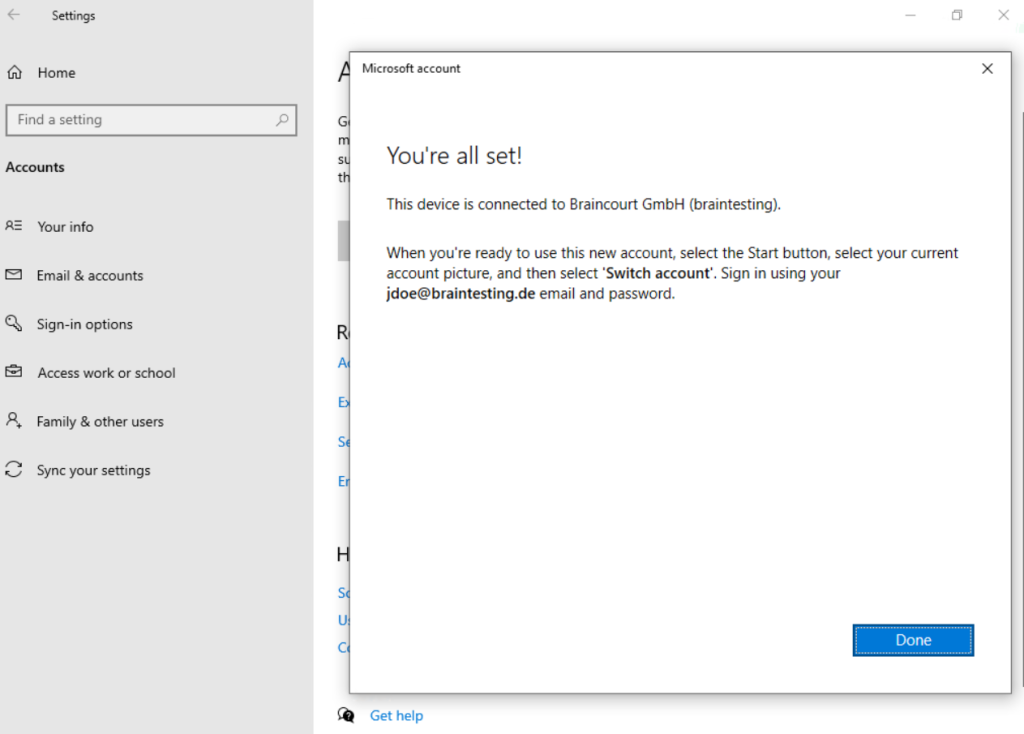
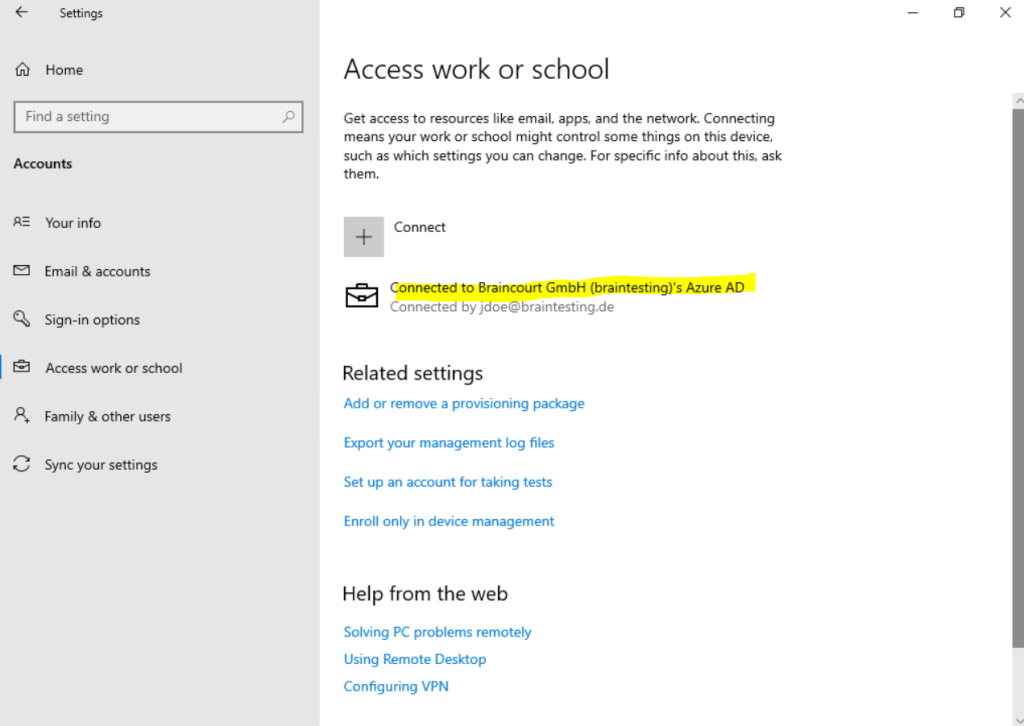
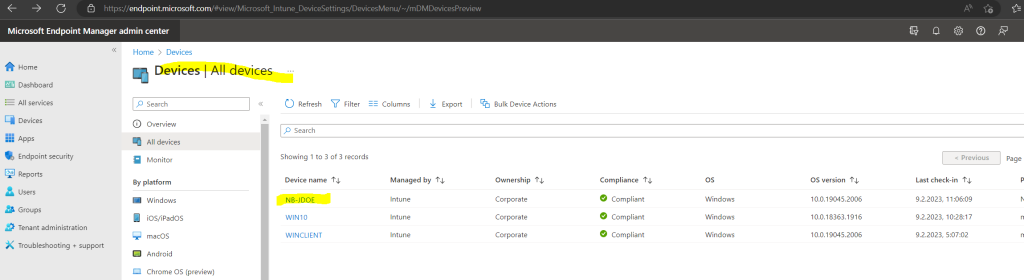
After joining the computer to Azure AD you will find it in your Azure AD under Devices.
As you can see so far it is not enrolled into Intune, this will take a few more seconds or minutes.
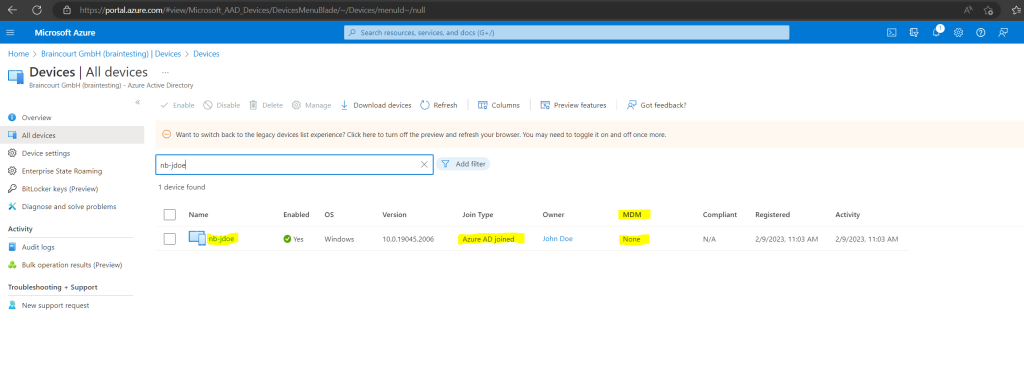
A few seconds later it was enrolled into Intue.
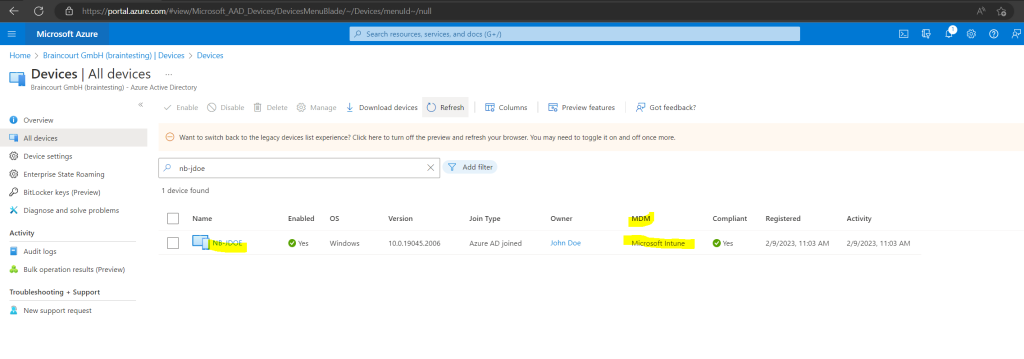
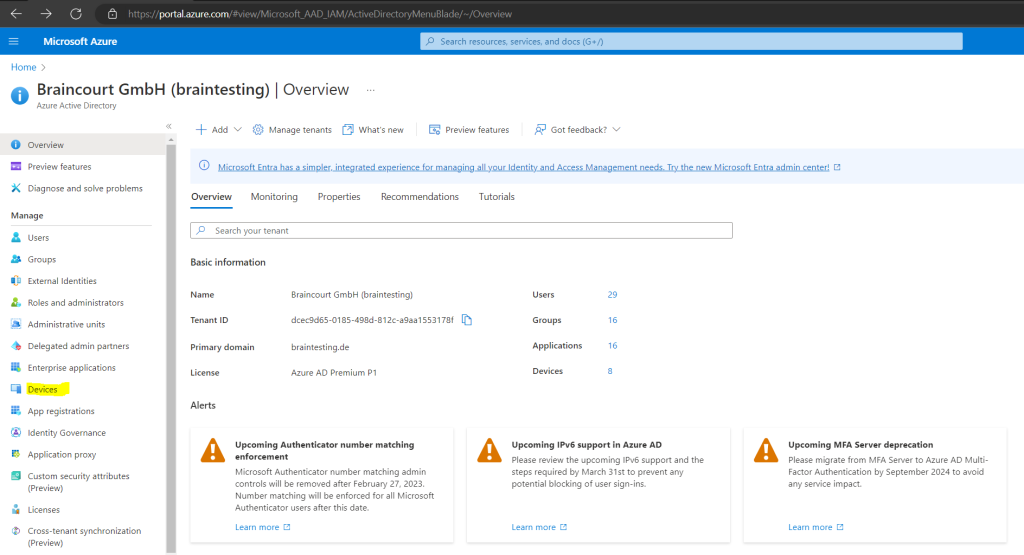
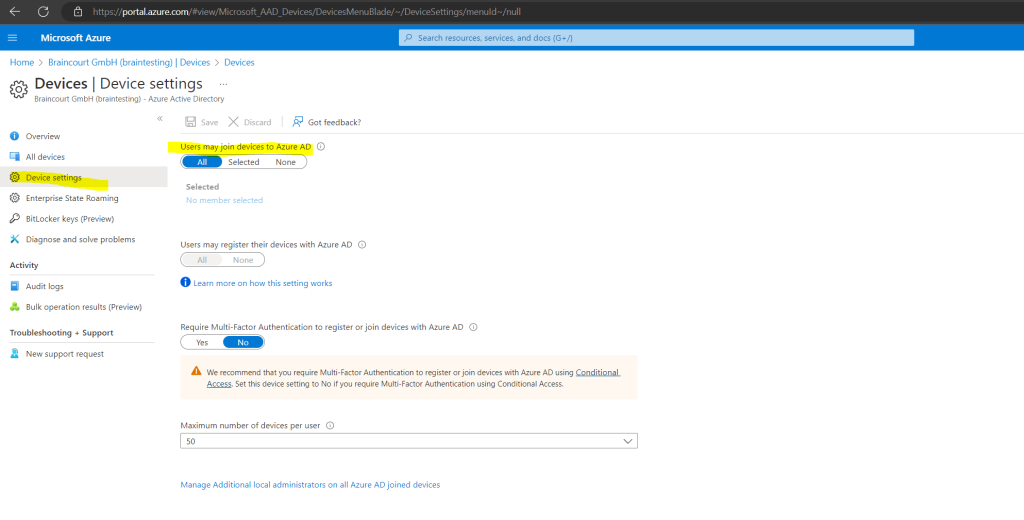
By default all users can can register their devices as Azure AD joined devices
This setting enables you to select the users who can register their devices as Azure AD joined devices. The default is All.
Select the users and groups that are allowed to join devices to Azure AD. This setting is only applicable to Azure AD join on Windows 10. This setting does not apply to hybrid Azure AD joined devices, Azure AD joined VMs in Azure and Azure AD joined devices using Windows Autopilot self-deployment mode as these methods work in a userless context.
Register personally owned devices (BYOD) to Azure Active Directory to enroll into Intune
As mentioned below we will see how to register your personally owned devices (BYOD) to Azure AD and to enroll them also into Intune.
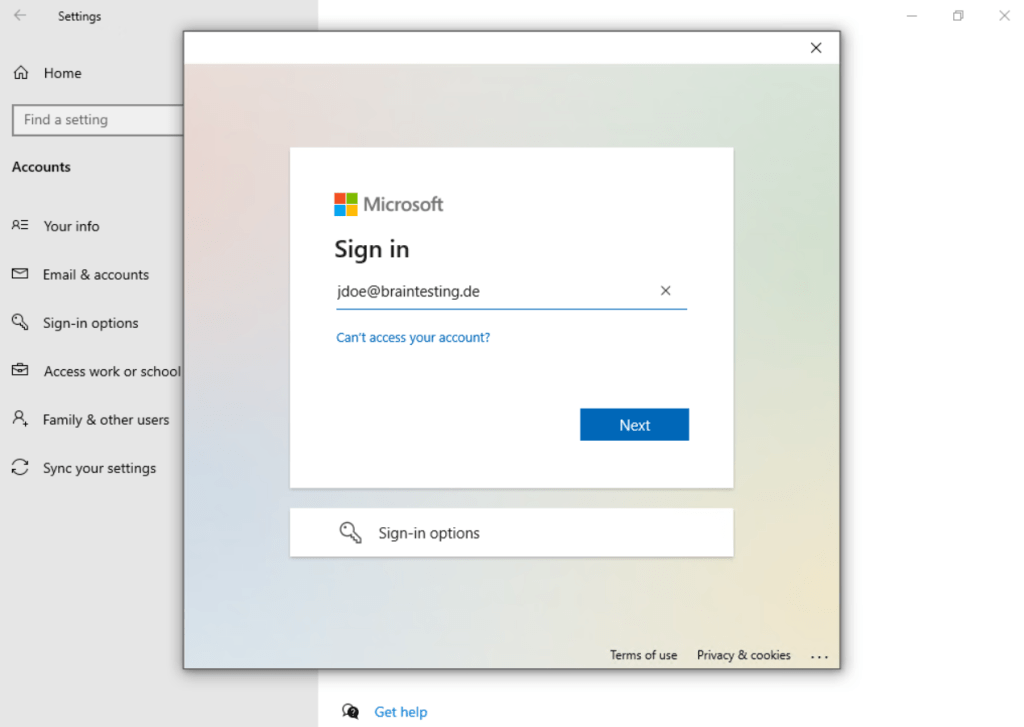
Click also on Connect like before for joining the device to Azure AD.

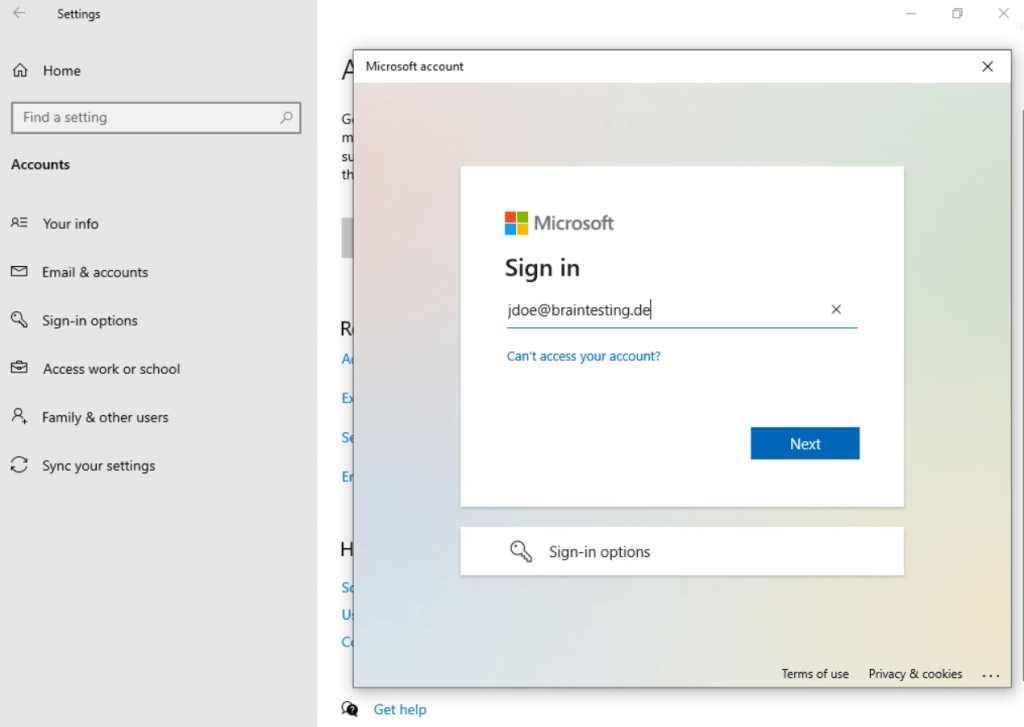
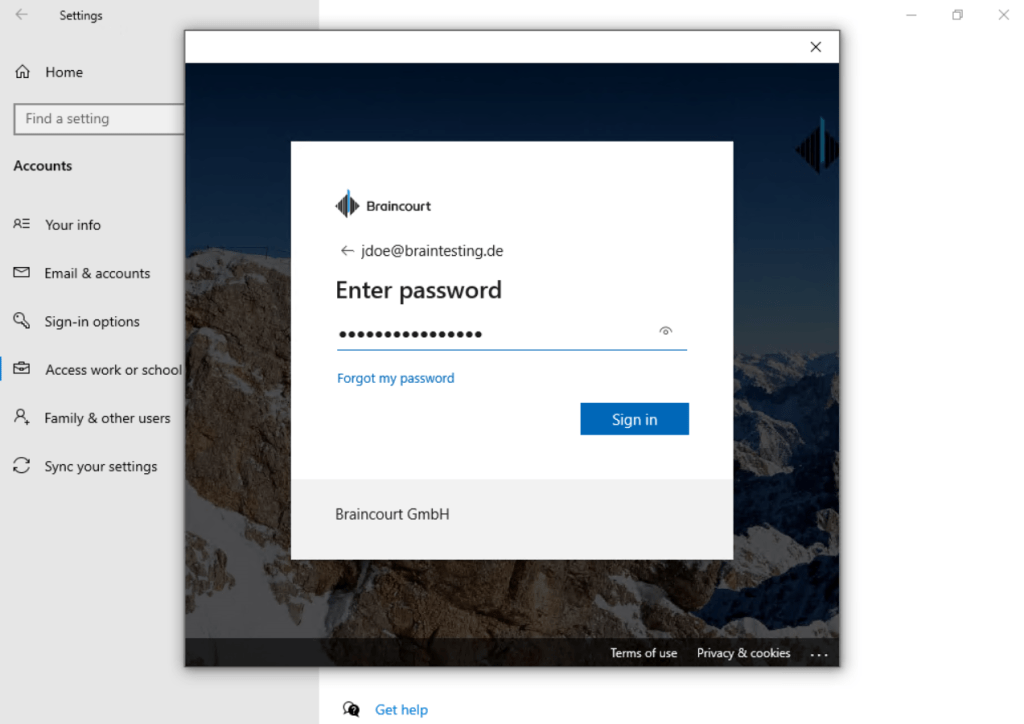
This time we enter our Microsoft 365 email address and click on Next.
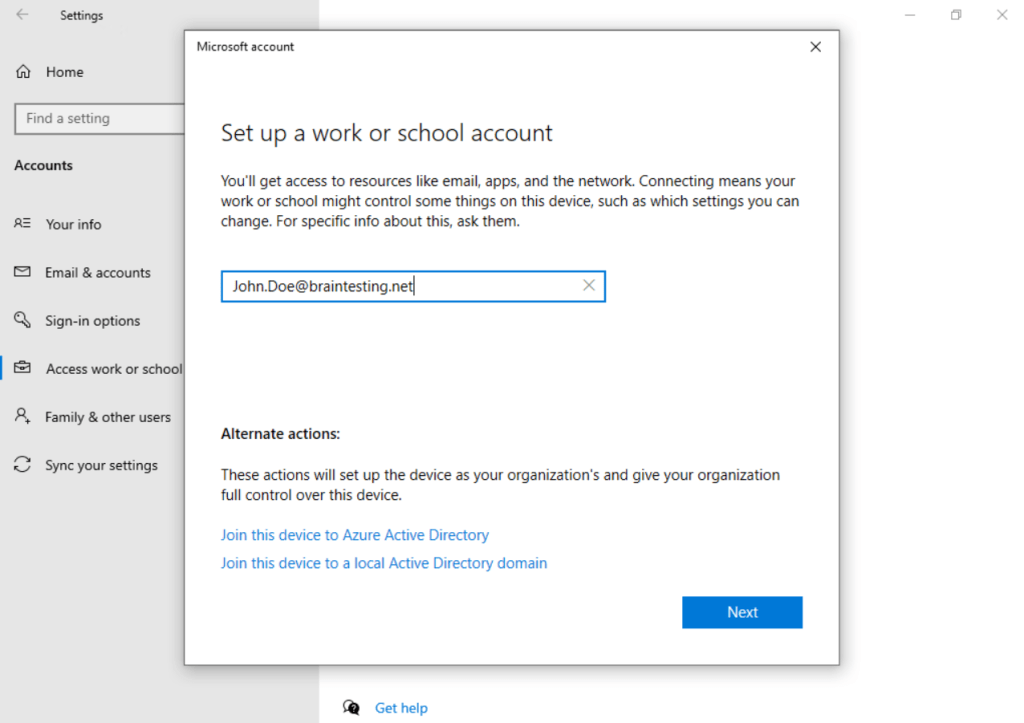
Enter your username if different from the email address.
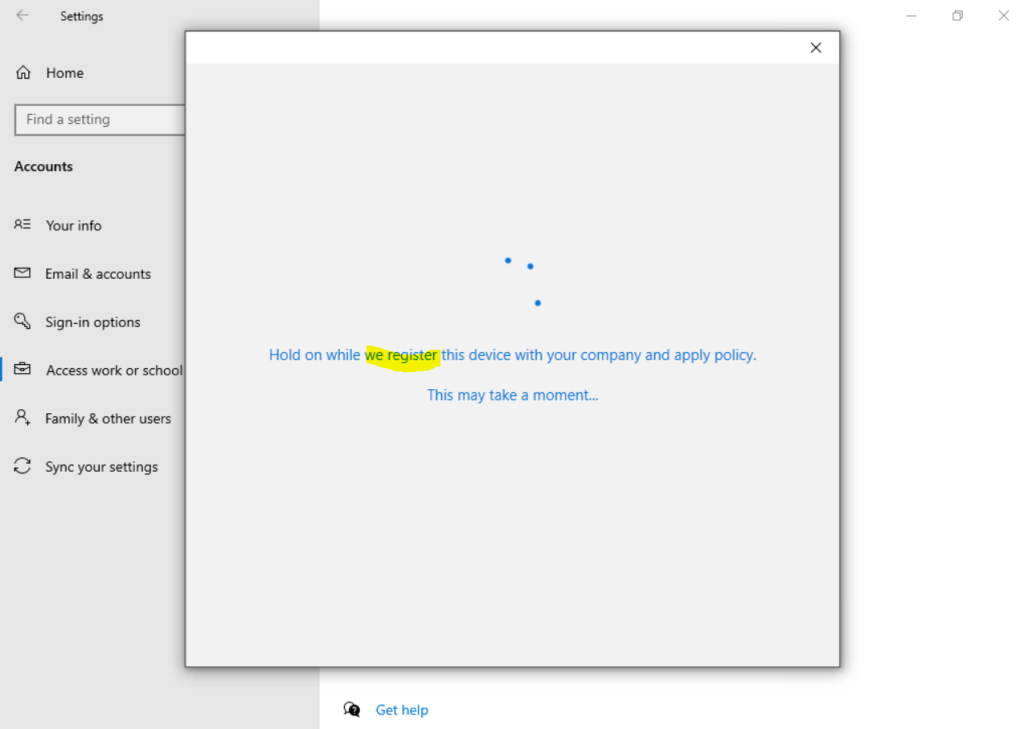
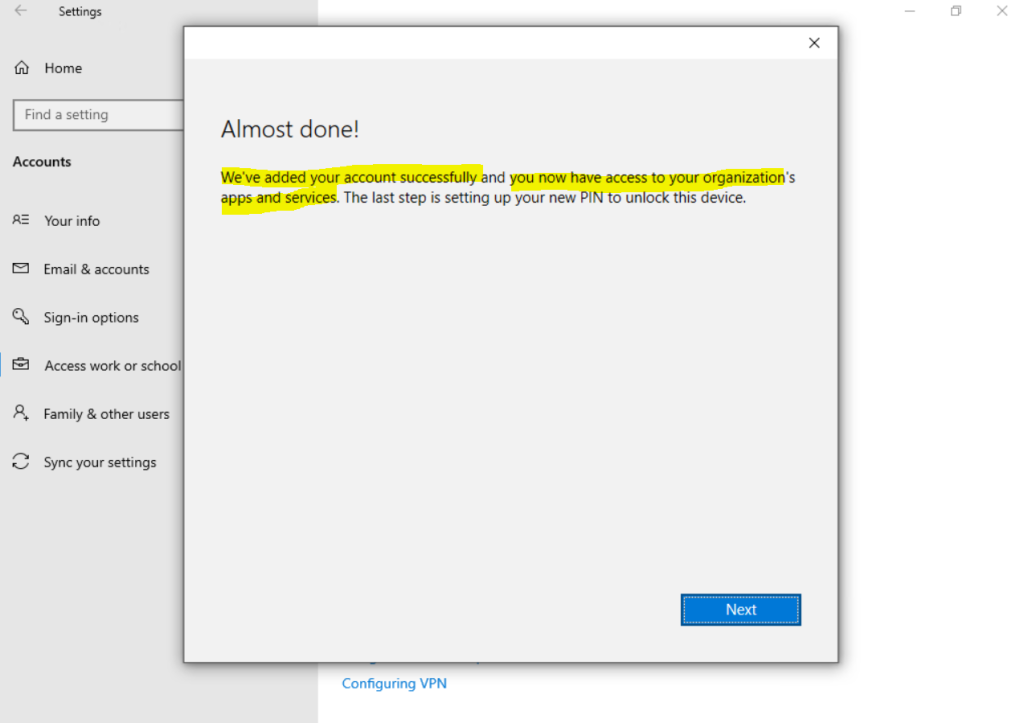
As you can see the device will be registered to our Azure AD.
In order to de-register just click on the account and a button to disconnect will appear.
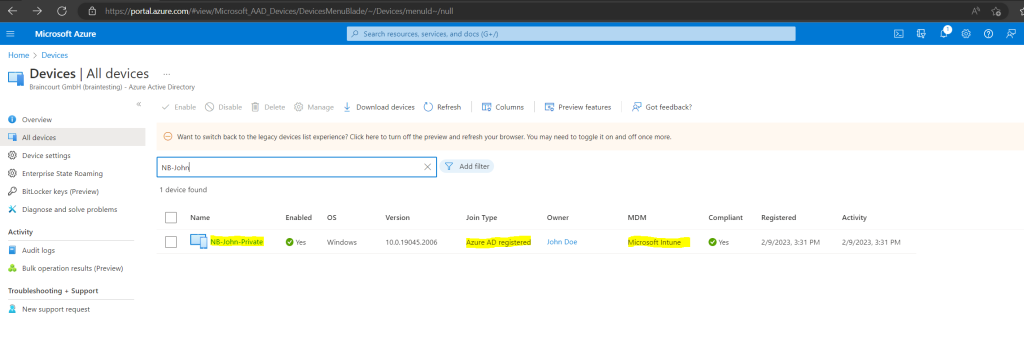
The personally owned devices (BYOD) will also shown up in your Azure AD under All Devices with the Join Type Azure AD registered.
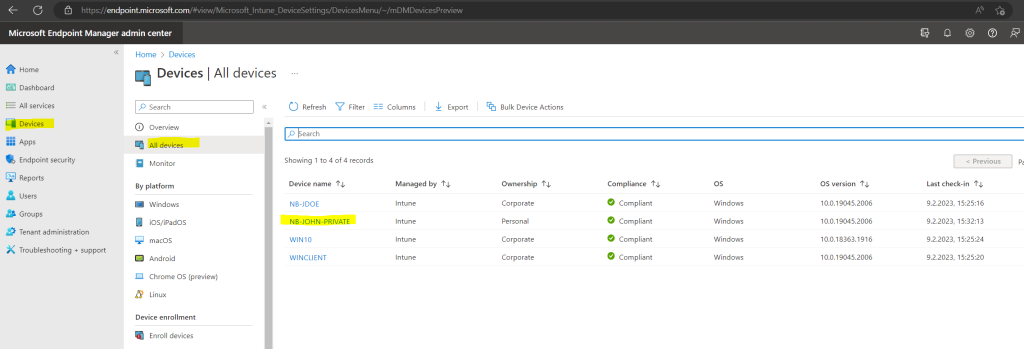
Here you can see that the device because of the auto-enrollment settings is also enrolled into Intune.
Further you can see that the device becomes the ownership Personal because it is not joined to Azure AD and just registered.
auto-enrollment settings.

Enroll a Windows 10 device automatically using Group Policy
Auto-enrollment into Intune via Group Policy is valid only for devices that are hybrid Azure AD joined. This condition means that the device must be joined into both local Active Directory and Azure Active Directory. To verify that the device is hybrid Azure AD joined, run dsregcmd /status from the command line.
Starting in Windows 10, version 1709, you can use a Group Policy to trigger auto-enrollment to Mobile Device Management (MDM) for Active Directory (AD) domain-joined devices.
The enrollment into Intune is triggered by a group policy created on your local AD and happens without any user interaction. This cause-and-effect mechanism means you can automatically mass-enroll a large number of domain-joined corporate devices into Microsoft Intune. The enrollment process starts in the background once you sign in to the device with your Azure AD account.
Requirements:
- Active Directory-joined PC running Windows 10, version 1709 or later
- The enterprise has configured a mobile device management (MDM) service
- The on-premises Active Directory must be integrated with Azure AD (via Azure AD Connect)
- The device shouldn’t already be enrolled in Intune using the classic agents (devices managed using agents will fail enrollment with error 0x80180026)
- The minimum Windows Server version requirement is based on the Hybrid Azure AD join requirement. For more information, see How to plan your hybrid Azure Active Directory join implementation.
When the auto-enrollment Group Policy is enabled, a task is created in the background that initiates the MDM enrollment. The task will use the existing MDM service configuration from the Azure Active Directory information of the user. If multi-factor authentication is required, the user will get a prompt to complete the authentication. Once the enrollment is configured, the user can check the status in the Settings page.
In Windows 10, version 1709 or later, when the same policy is configured in Group Policy and MDM, Group Policy policy takes precedence over MDM. Since Windows 10, version 1803, a new setting allows you to change precedence to MDM. For more information, see Windows 10 Group Policy vs. Intune MDM Policy who wins?.
For bring-your-own devices (BYOD devices), the Mobile Application Management (MAM) user scope takes precedence if both MAM user scope and MDM user scope (automatic MDM enrollment) are enabled for all users (or the same groups of users). The device will use Windows Information Protection (WIP) Policies (if you configured them) rather than being MDM enrolled.
For corporate-owned devices, the MDM user scope takes precedence if both scopes are enabled. The devices get MDM enrolled.
Some tenants might have both Microsoft Intune and Microsoft Intune Enrollment under Mobility. Make sure that your auto-enrollment settings are configured under Microsoft Intune instead of Microsoft Intune Enrollment.
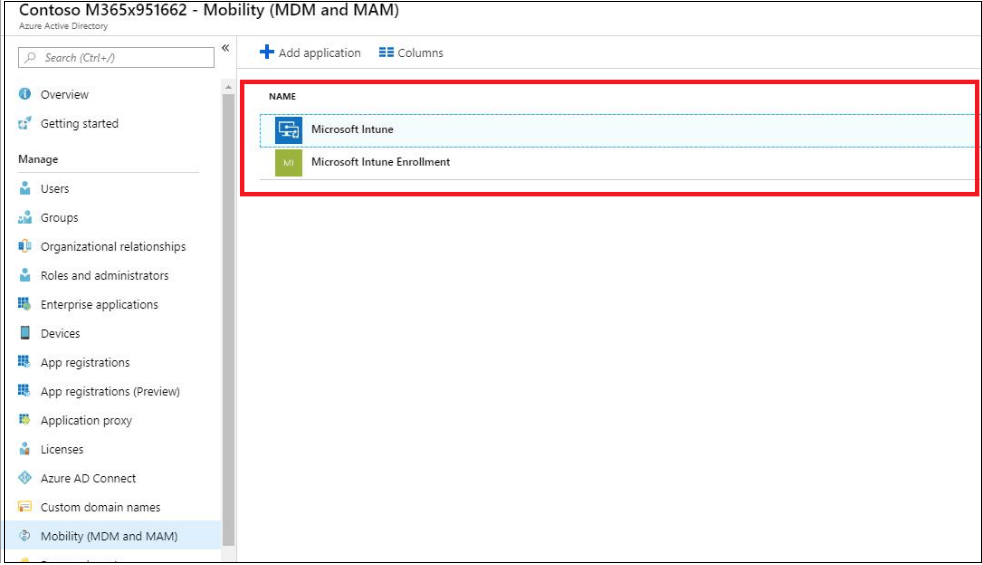
Verify that auto-enrollment is activated for those users who are going to enroll the devices into Mobile Device Management (MDM) with Intune. For more information, see Azure AD and Microsoft Intune: Automatic MDM enrollment in the new Portal.
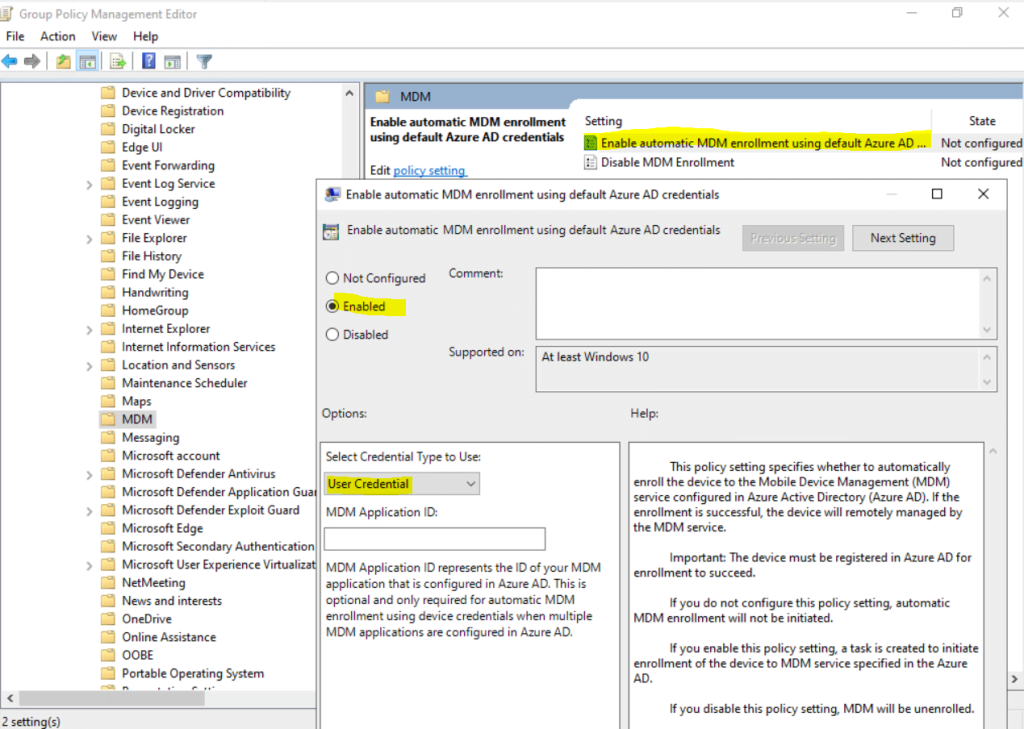
Enable the Group Policy
Computer Configuration –> Policies –> Administrative Templates –> Windows Components –> MDM –> Enable automatic MDM enrollment using default Azure AD credentials.
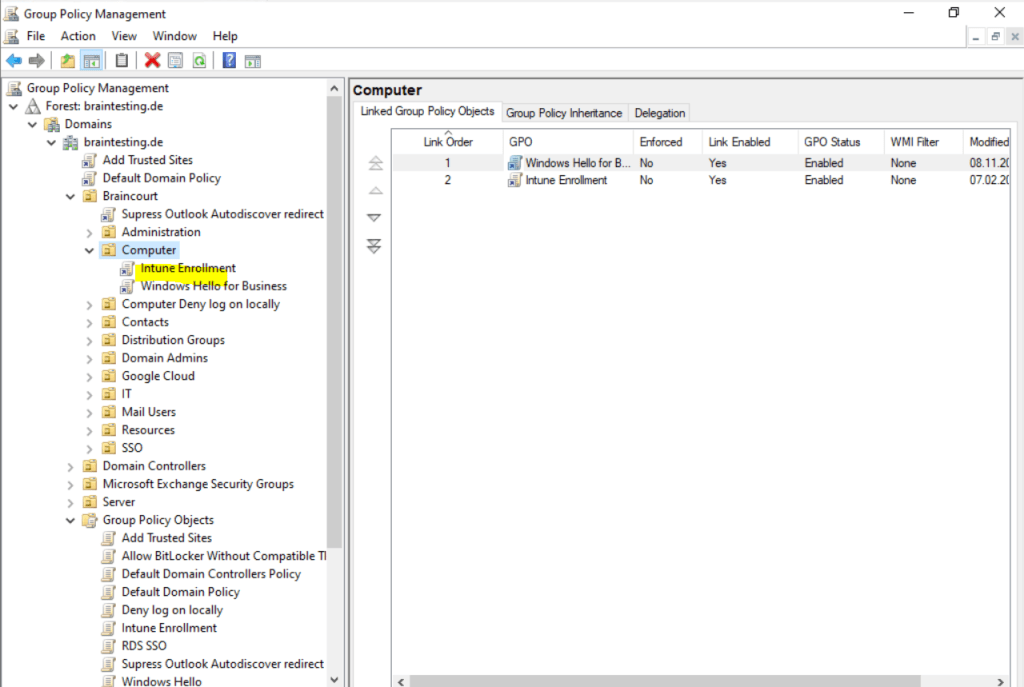
Link the Group Policy to the OUs with the computers who should auto-enroll into Intune.
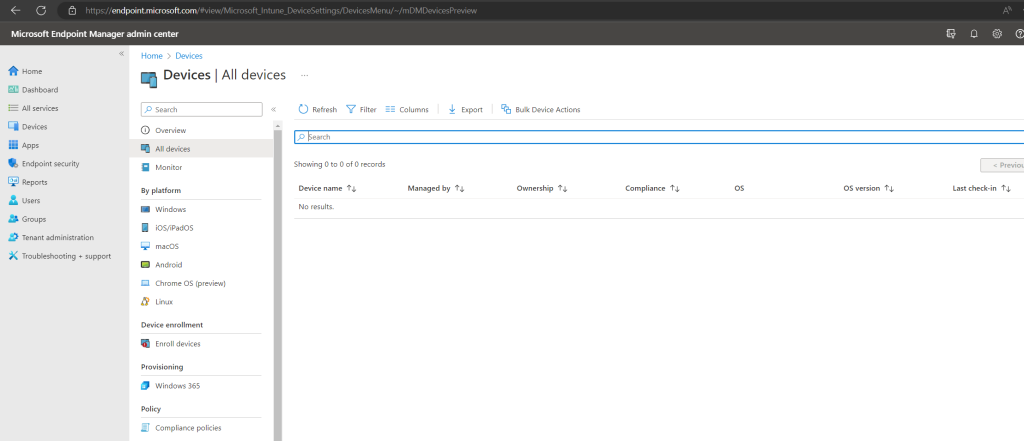
So far no computers enrolled into Intunes.
My Computer win10 which is homed in the Computer OU shown above where we linked the new Group Policy with Enable automatic MDM enrollment .
So far no MDM is assigned.
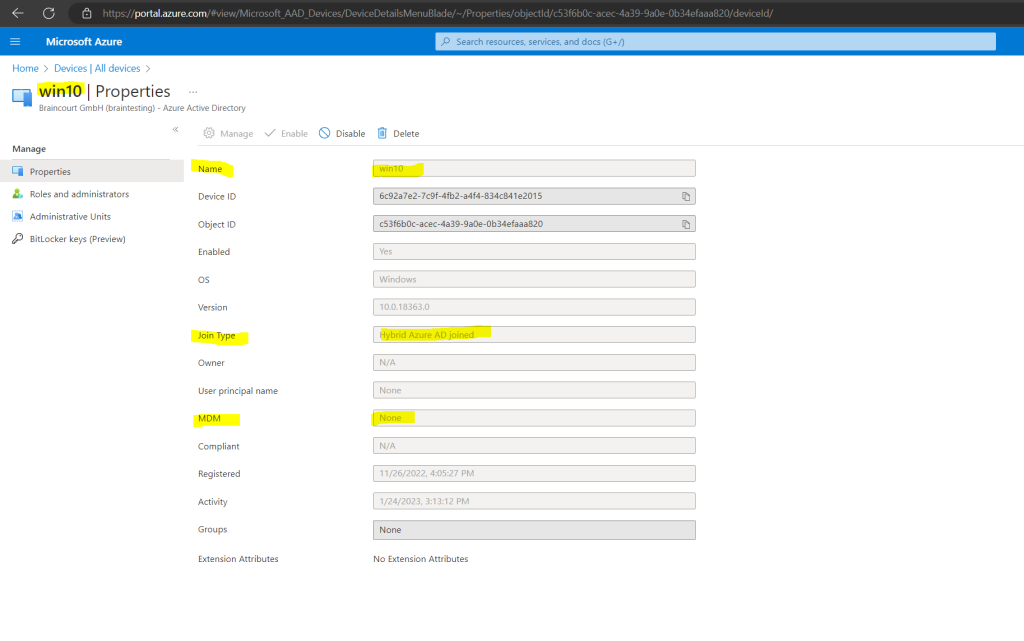
When a group policy refresh occurs on the win10, a task is created and scheduled to run every 5 minutes for the duration of one day. The task is called Schedule created by enrollment client for automatically enrolling in MDM from Azure Active Directory.
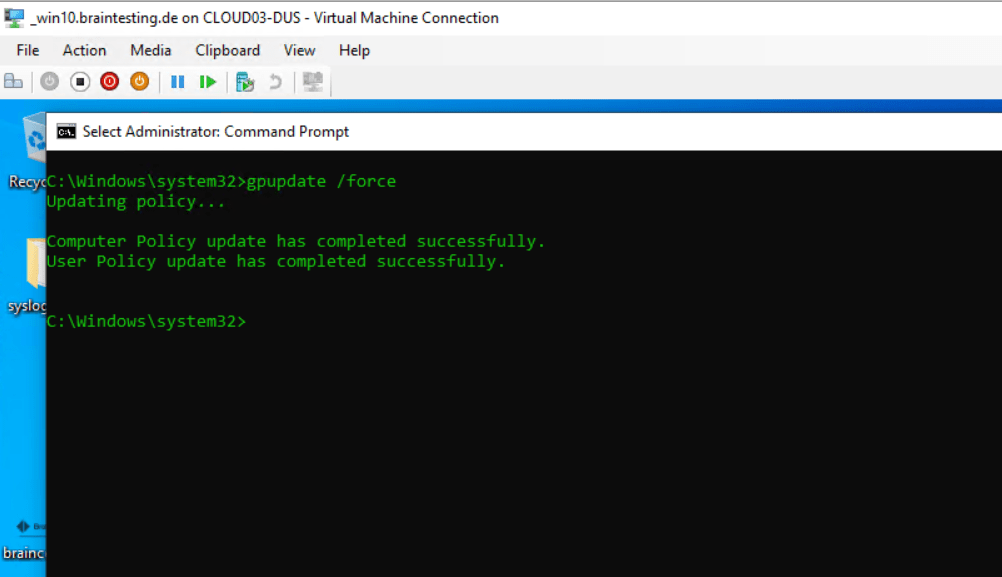
In Task Scheduler Library, open Microsoft > Windows , then select EnterpriseMgmt.
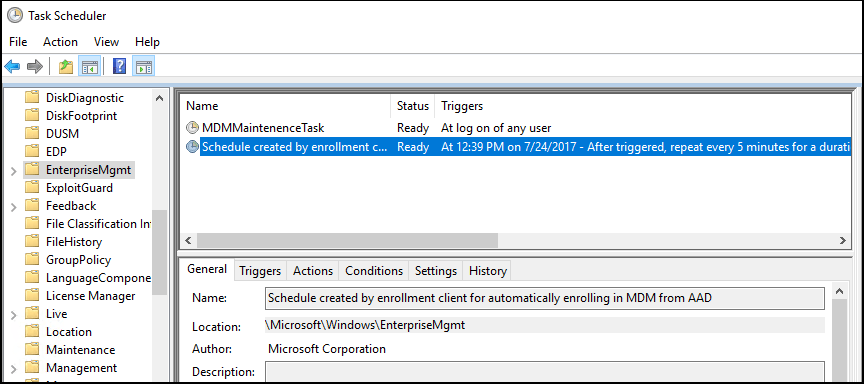
After a view minutes the computer win10 is enrolled in Intune.
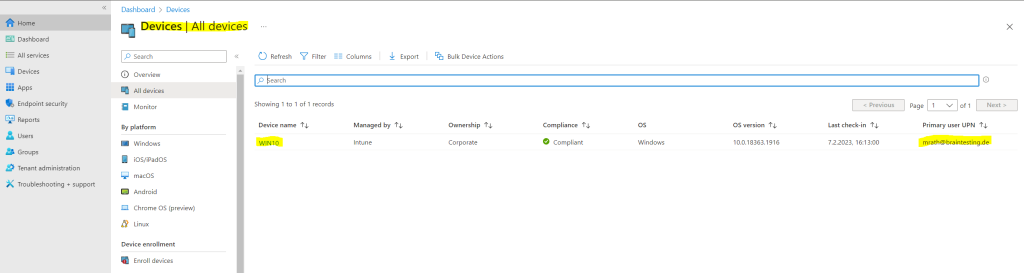
How to enroll already Microsoft Entra joined (former Azure AD joined) Devices to Microsoft Intune
Devices that are already Microsoft Entra joined (former Azure AD joined), before you have enabled MDM auto-enrollment in your tenant, will unfortunately after enabling MDM auto-enrollment not enroll automatically in Microsoft Intune.
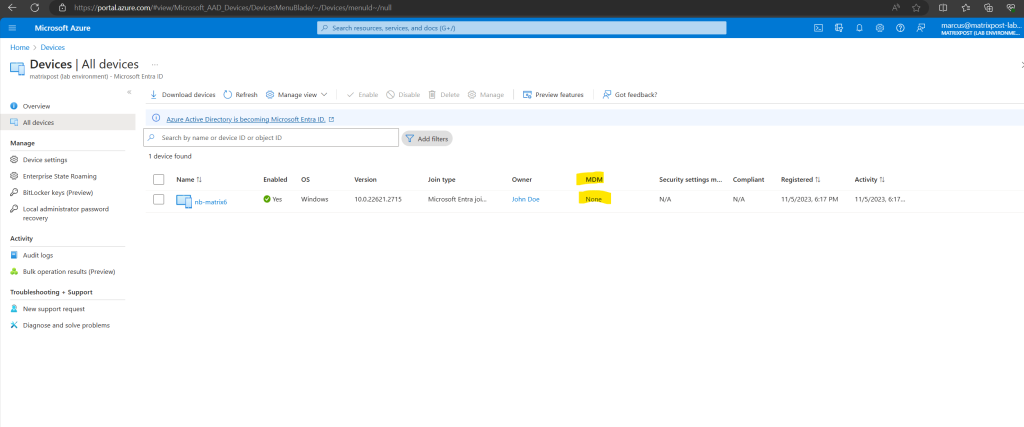
When you enable MDM auto-enrollment like shown below and now a user with an eligible license for Microsoft Intune like Enterprise Mobility + Security E3 will join its device to Microsoft Entra ID, the device will automatically enroll in Microsoft Intune.
Use MDM auto-enrollment to manage enterprise data on your employees’ Windows devices. MDM auto-enrollment will be configured for Microsoft Entra joined devices and bring your own device scenarios.
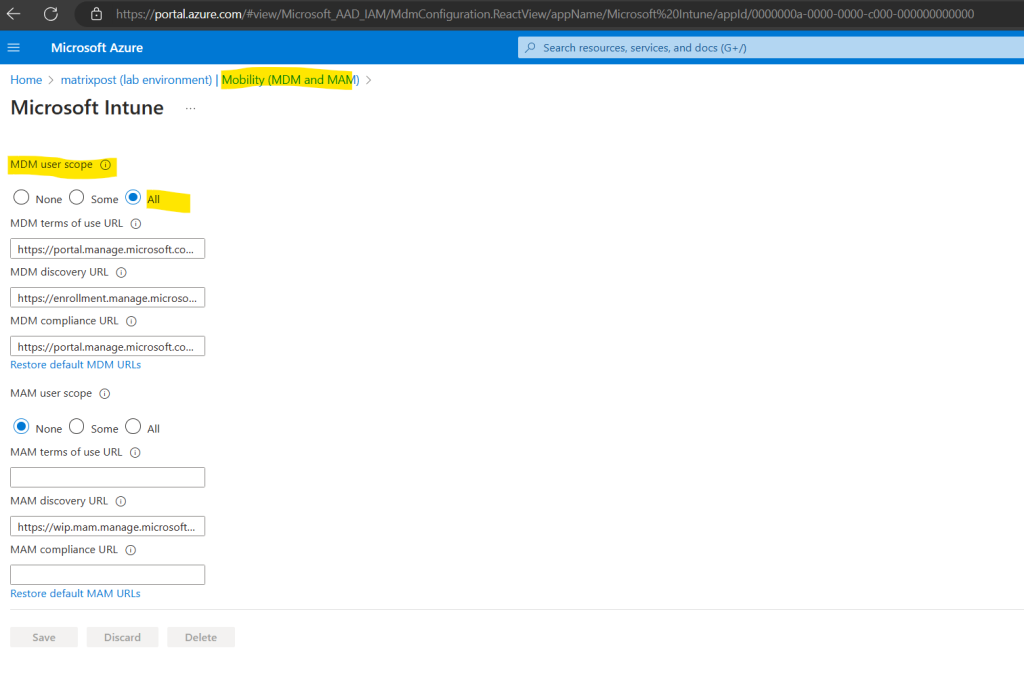
As mentioned in case you will enable MDM auto-enrollment after you have already joined some devices to Microsoft Entra ID, these devices will unfortunately not triggered by default to enroll automatically to Microsoft Intune.
There is a post about how you can nevertheless enroll these already Microsoft Entra joined devices to Microsoft Intune by firing up a little PowerShell script on these devices which leverages the C:Windowssystem32deviceenroller.exe. Below I will refer to this post.
We first need to allow the script can be executed on the affected devices by adjusting the execution policy.
about_Execution_Policies
https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_execution_policies?view=powershell-7.3
The script itself needs to be executed with system context, therefore we can fortunately use the PsExec tools from the Sysinternals suite.
More about Sysinternals and its PsExec tool you can find in my following post https://blog.matrixpost.net/sysinternals-and-its-psexec-tool/.
Copy the following PowerShell script to the affected device. I was saving the script for example as AutoEnrollMDM.ps1 to the device I wanted to enroll to Microsoft Intune.
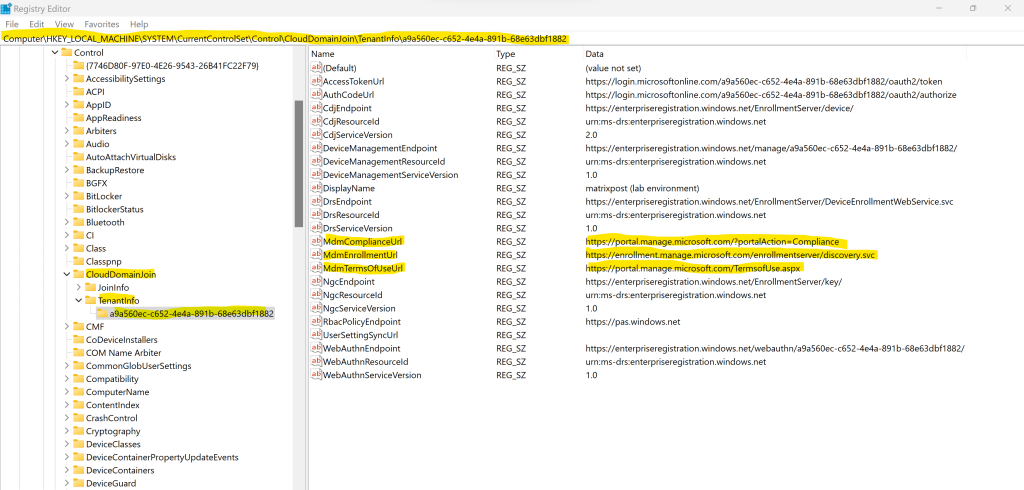
The script is first checking if the Microsoft Entra joined registry settings including the Tenant ID and MDM Enrollment URL is already set for the affected device. These registry settings should be set when joining the device to Microsoft Entra ID (former Azure AD). If not already set, the script will try to set the MDM Enrollment URL in the registry which is then later used by the C:Windowssystem32deviceenroller.exe in order to enroll the device in Microsoft Intune.
# Set MDM Enrollment URL's
$key = 'SYSTEMCurrentControlSetControlCloudDomainJoinTenantInfo*'
try{
$keyinfo = Get-Item "HKLM:$key"
}
catch{
Write-Host "Tenant ID is not found!"
exit 1001
}
$url = $keyinfo.name
$url = $url.Split("")[-1]
$path = "HKLM:SYSTEMCurrentControlSetControlCloudDomainJoinTenantInfo$url"
if(!(Test-Path $path)){
Write-Host "KEY $path not found!"
exit 1001
}else{
try{
Get-ItemProperty $path -Name MdmEnrollmentUrl
}
catch{
Write_Host "MDM Enrollment registry keys not found. Registering now..."
New-ItemProperty -LiteralPath $path -Name 'MdmEnrollmentUrl' -Value 'https://enrollment.manage.microsoft.com/enrollmentserver/discovery.svc' -PropertyType String -Force -ea SilentlyContinue;
New-ItemProperty -LiteralPath $path -Name 'MdmTermsOfUseUrl' -Value 'https://portal.manage.microsoft.com/TermsofUse.aspx' -PropertyType String -Force -ea SilentlyContinue;
New-ItemProperty -LiteralPath $path -Name 'MdmComplianceUrl' -Value 'https://portal.manage.microsoft.com/?portalAction=Compliance' -PropertyType String -Force -ea SilentlyContinue;
}
finally{
# Trigger AutoEnroll with the deviceenroller
try{
C:Windowssystem32deviceenroller.exe /c /AutoEnrollMDM
Write-Host "Device is ready for Autopilot enrollment now!"
exit 0
}
catch{
Write-Host "Something went wrong (C:Windowssystem32deviceenroller.exe)"
exit 1001
}
}
}
exit 0Working with registry entries
https://learn.microsoft.com/en-us/powershell/scripting/samples/working-with-registry-entries
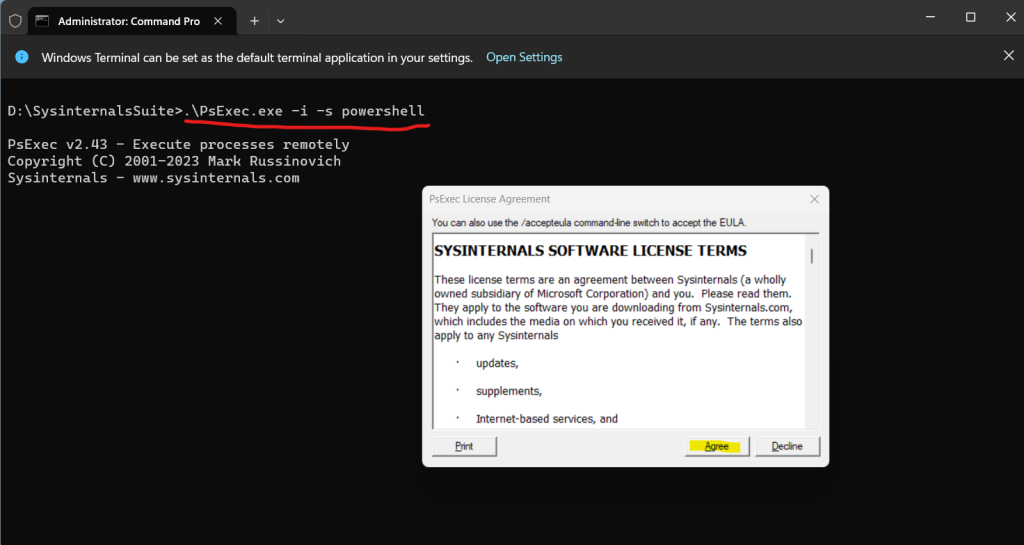
In order to start a new PowerShell session which runs under the system account we can now use the PsExec tool like shown below.
> PsExec.exe -i -s powershell
Source: https://learn.microsoft.com/en-us/sysinternals/downloads/psexec#using-psexec
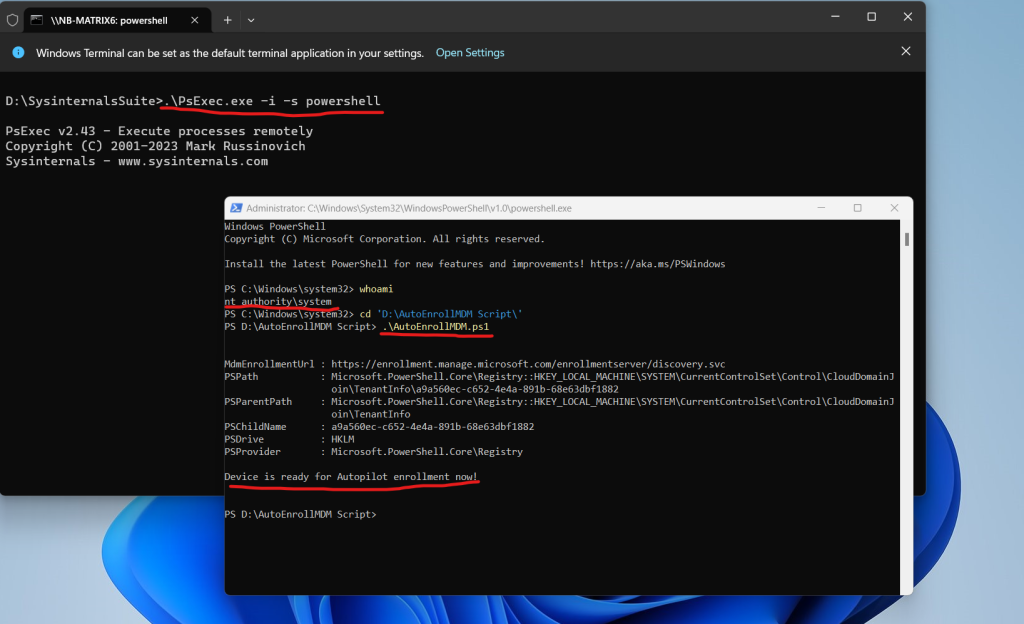
By using the whoami command you can check if the process is really running under the system account. Finally we can run the script to auto-enroll the device to Microsoft Intune.
In case you are also interested in Windows Autopilot, you can read my following post https://blog.matrixpost.net/set-up-windows-autopilot/.
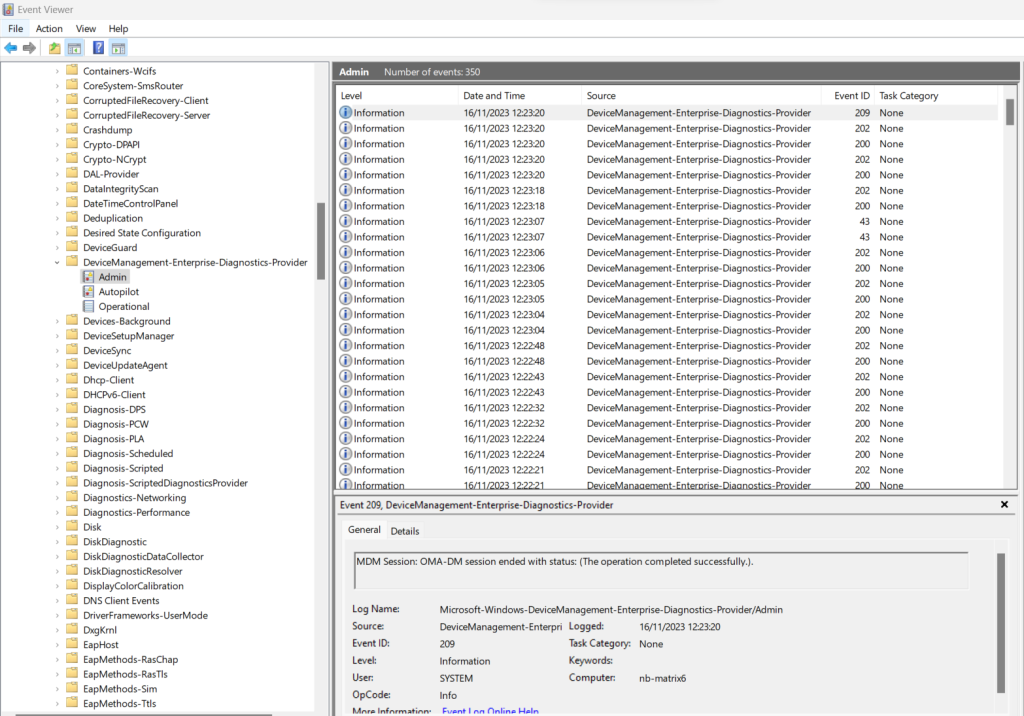
In case something went wrong you can also analyze the corresponding logs under Event Viewer -> Applications and Services Logs -> Microsoft -> Windows -> DeviceManagement-Enterprise-Diagnostics-Provider.
In my case I was first getting an error regarding device credentials, but after running the script a second time, the device enrolled immediately in Microsoft Intune.
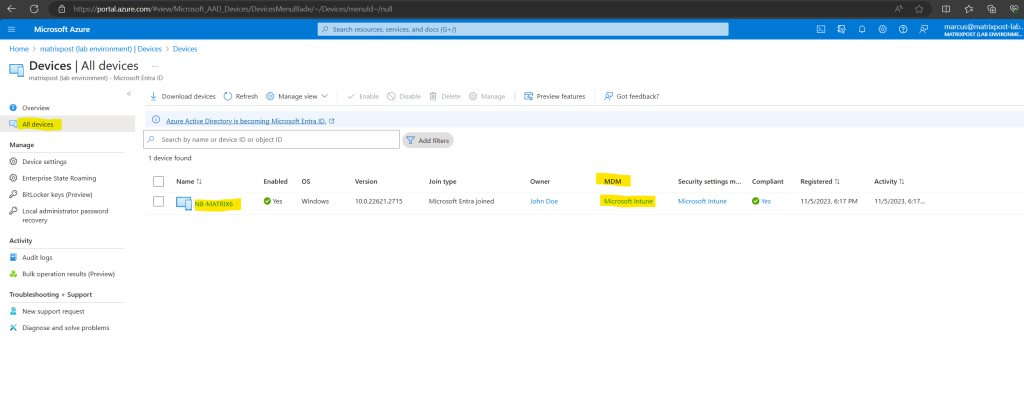
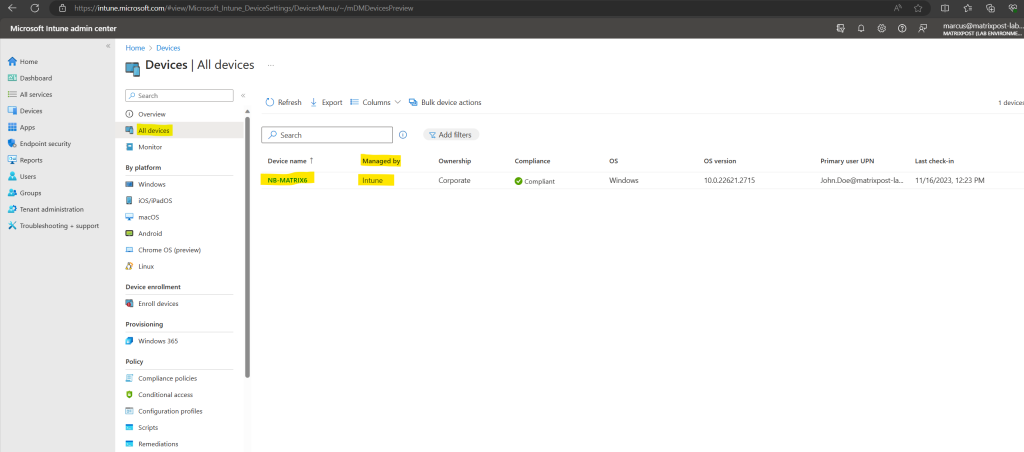
The device is shown up in Microsoft Intune immediately after running the script.
Links
Microsoft Intune securely manages identities, manages apps, and manages devices
https://learn.microsoft.com/en-us/mem/intune/fundamentals/what-is-intuneManage your devices and control device features in Microsoft Intune
https://learn.microsoft.com/en-us/mem/intune/fundamentals/manage-devicesEndpoint Management at Microsoft
https://learn.microsoft.com/en-us/mem/endpoint-manager-overviewDeployment guide: Setup or move to Microsoft Intune
https://learn.microsoft.com/en-us/mem/intune/fundamentals/deployment-guide-intune-setupDeployment guidance: Enroll devices in Microsoft Intune
https://learn.microsoft.com/en-us/mem/intune/fundamentals/deployment-guide-enrollment



