Sysinternals and its PsExec Tool
Today I was running into an issue where I couldn’t connect to a bare-metal remote server in the branch office by using the Remote Desktop Protocol (RDP). I could ping the server and I was pretty sure that Remote Desktop is enabled.
Telnet to rdp port 3389 failed and also nmap revealed no open tcp port 3389.
One tool you can use to investigate and solve such issues is PsExec, below I will show how you can use PsExec to control a remote computer.
- Using PsExec to investigate and solve Remote Desktop Issues
- Prerequisites that PsExec will work
- Useful commands you can execute on Remote Computers
- Restart a Remote Computer
- Enable Remote Desktop on a Remote Computer
- Enable or Disable Firewall on a Remote Computer
- Open Firewall Ports on a Remote Computer
- Determine active User Sessions on a Remote Computer and logging them off
- List Logical Volumes from a Remote Computer
- Get Serial and Model Number from a Remote Computer
- Copy Files from a Remote Computer
- Terminate stucking Hyper-V VMs from remote
- Terminate a Process on a Remote Computer
- Links
Using PsExec to investigate and solve Remote Desktop Issues
Finally the issue was, that on the remote server by accident not the internal DNS servers from the Active Directory domain was set, but instead the public DNS servers from Google (8.8.8.8 and 8.8.4.4).
Therefore the remote server couldn’t determine and connect to the internal domain controllers anymore and classified mistakenly the internal network as guest or public network, which then restricts network access and blocked remote desktop.
Windows Firewall Profiles
Windows Firewall offers three firewall profiles: domain, private and public. The domain profile applies to networks where the host system can authenticate to a domain controller.Source: https://learn.microsoft.com/en-us/previous-versions/windows/desktop/ics/windows-firewall-profiles
In the first place I had no clue, if remote desktop is really enabled, if the Remote Desktop Services (TermService) service is running or if there is a problem with the firewall settings.
In such cases, if I have no other options to connect to a remote bare-metal server and also remote management solutions like IMM for IBM/Lenovo server or iDRAC for Dell server won’t work, I try to connect to the server by using PsExec from the Sysinternals suite.
Sysinternals
https://learn.microsoft.com/en-us/sysinternals/Download https://learn.microsoft.com/en-us/sysinternals/downloads/
PsExec
is a light-weight telnet-replacement that lets you execute processes on other systems, complete with full interactivity for console applications, without having to manually install client software. PsExec’s most powerful uses include launching interactive command-prompts on remote systems and remote-enabling tools like IpConfig that otherwise do not have the ability to show information about remote systems.
https://learn.microsoft.com/en-us/sysinternals/downloads/psexec
More about Dell iDRAC and IBM/Lenovo IMM you will find in my following posts.
To connect to a remote server you can use the following command.
PsExec.exe \<hostname or IP> cmd
In this case PsExec will use the credentials you are logged in on the computer you are running the command.
You can also specify alternative credentials by using the -u flag for the username and -p for password. Further since version 2.3+ also the -i flag is required.
PsExec.exe -i \hostname -u <domainusername> -p <password> cmd
This flag is required when attempting to run console applications interactively (with redirected standard IO).
Source: https://learn.microsoft.com/en-us/sysinternals/downloads/psexec
In my case as I told you, that finally the issue was because of the missing internal DNS servers, I also couldn’t connet with PsExec by using domain credentials.
Fortunately I am using for local user accounts in my network the Local Administrator Password Solution (LAPS), therefore I was knowing the password from the local administrator user.
Local Administrator Password Solution (LAPS)
The “Local Administrator Password Solution” (LAPS) provides management of local account passwords of domain joined computers. Passwords are stored in Active Directory (AD) and protected by ACL, so only eligible users can read it or request its reset.
https://www.microsoft.com/en-us/download/details.aspx?id=46899
Below you see for example how it looks like, when you connect to a remote computer by using PsExec, I didn’t specified here alternative credentials, because I was already logged in to the computer where I am running PsExec, as organization admin and therefore have full administrative rights on the remote computer.
I am always first enter the hostname command to verify I am really logged in to the remote computer I wanted to connect.
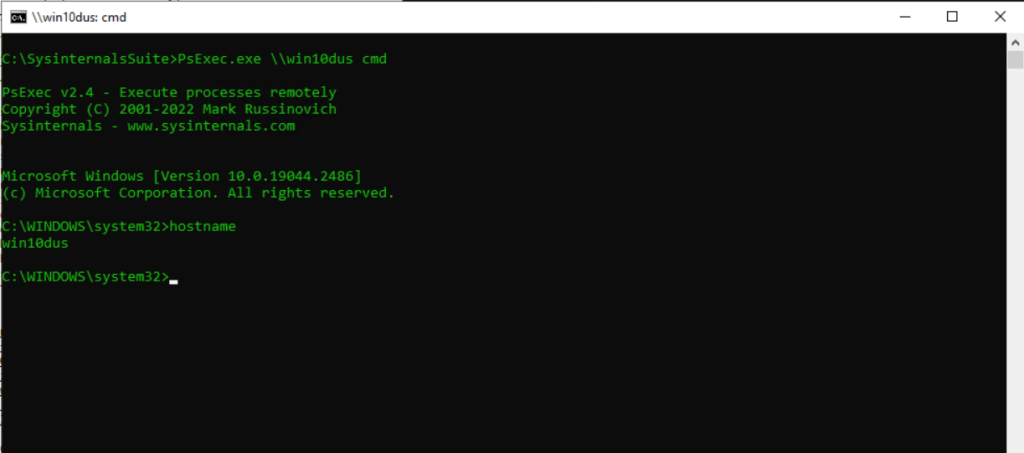
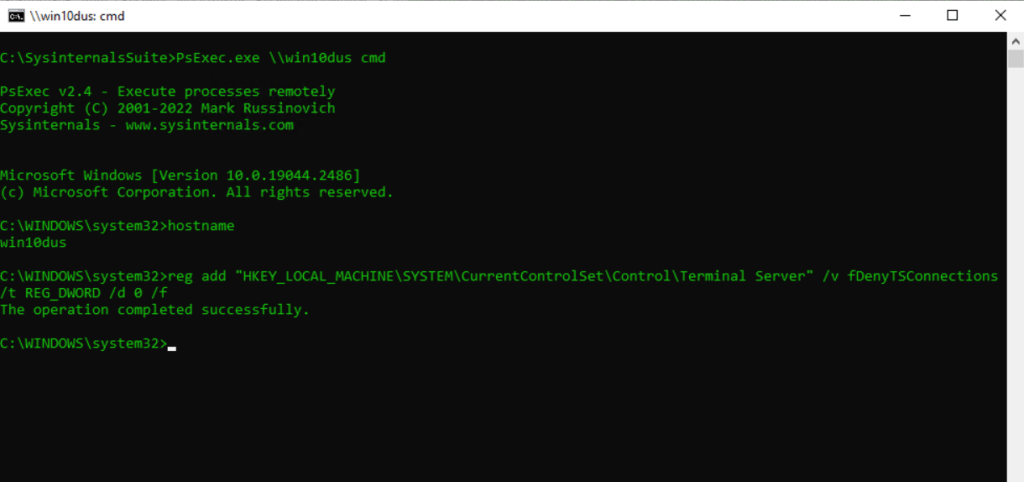
Then I was first enter the following command to enable Remote Desktop in case it is not already enabled.
reg add “HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal Server” /v fDenyTSConnections /t REG_DWORD /d 0 /f
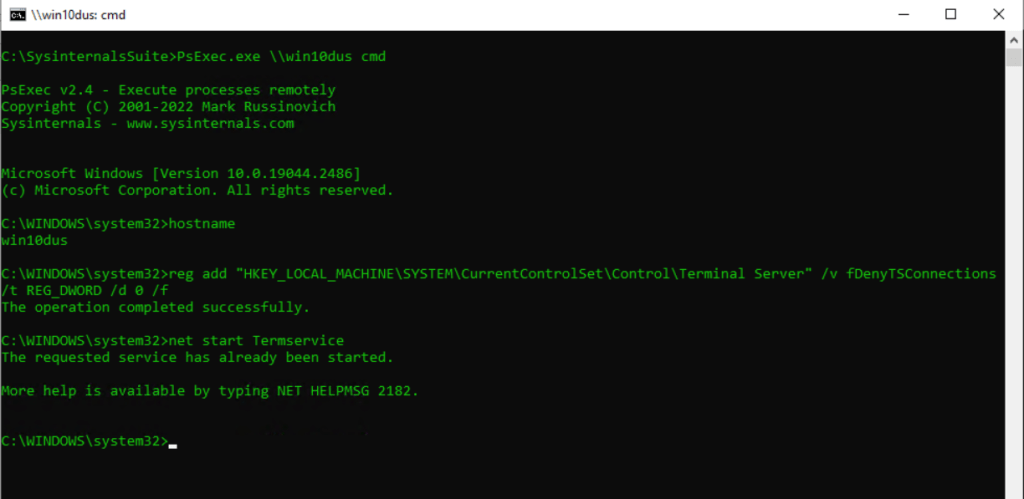
Next I wanted to start the Remote Desktop Services (Termservice) service in case it is not started. In my case it was already started.
net start Termservice
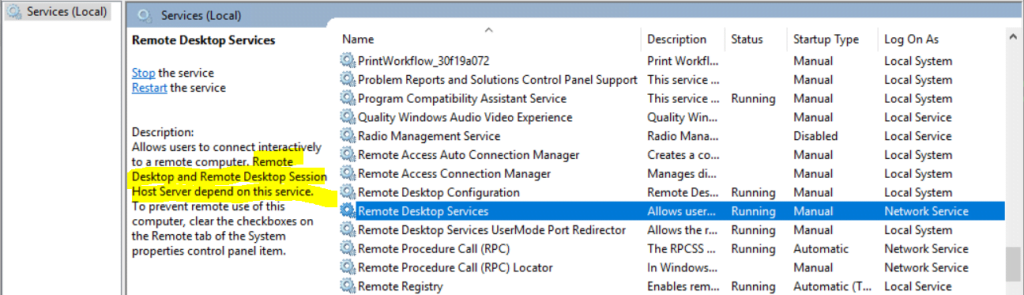
Finally I was also opening on the firewall RDP Port tcp 3389 if not already open.
netsh advfirewall firewall set rule group=”remote desktop” new enable=Yes
or
netsh advfirewall firewall add rule name= “Open Port 3389” dir=in action=allow protocol=TCP localport=3389Old depricated command but still working:
netsh firewall set service type = remotedesktop mode = enableUse netsh advfirewall firewall instead of netsh firewall to control Windows Firewall behavior
https://learn.microsoft.com/en-us/troubleshoot/windows-server/networking/netsh-advfirewall-firewall-control-firewall-behavior
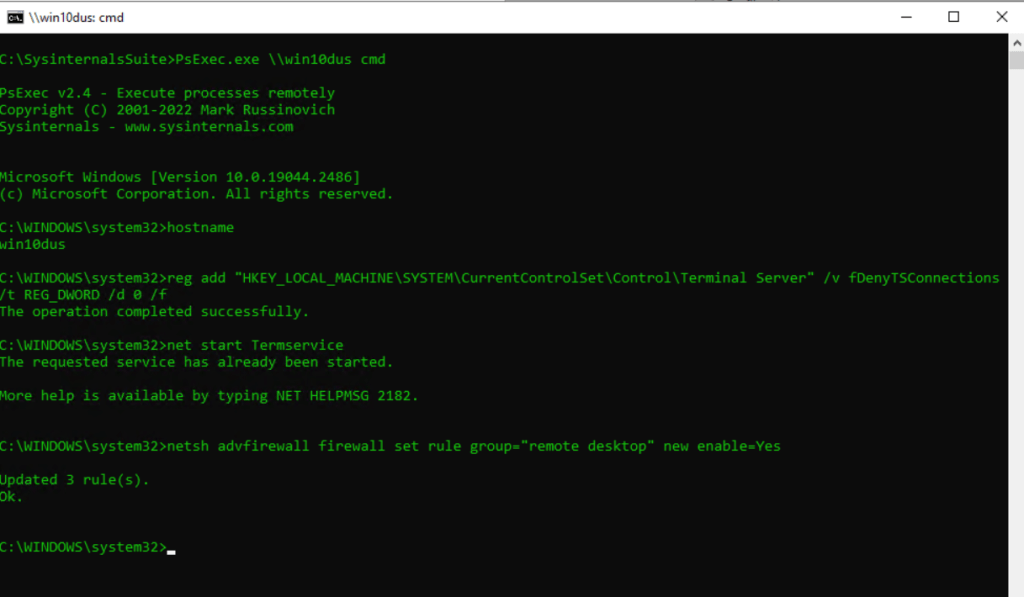
As I mentioned at the beginning, the firewall and closed tcp port 3389 for remote desktop was finally the issue I couldn’t connect to the server. The server classified the internal network as guest or public network and therefore restricted the firewall settings for.
The server couldn’t determine and connect to the internal domain controllers because of the wrong DNS server settings on the network adatper and therefore mistakenly classified this network as guest or public.
Prerequisites that PsExec will work
There are some prerequisites in order you can use PsExec to connect to a remote computer. One of course are valid credentials on the remote computer.
- TCP port 445 SMB must be open in the firewall.
- TCP port 135 RPC Endpoint Mapper must be open in the firewall.
- Server (LanmanServer) service must be running.
Useful commands you can execute on Remote Computers
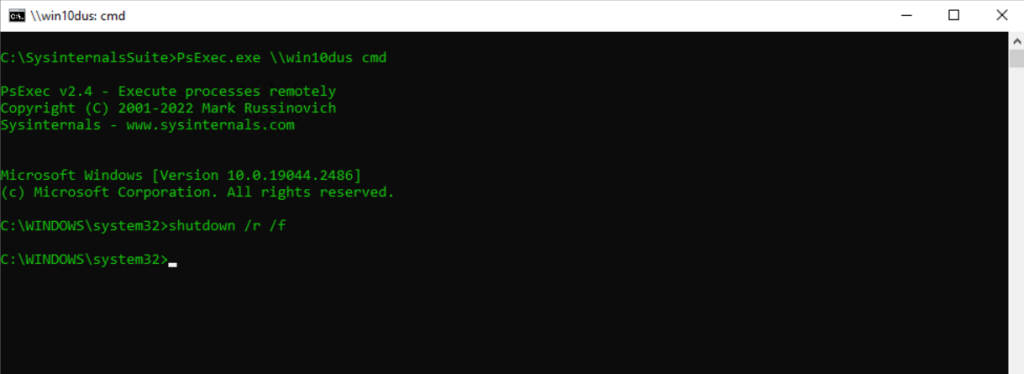
Restart a Remote Computer
PsExec.exe \hostname cmd
shutdown /r /f/r Restarts the computer after shutdown.
/f Forces running applications to close without warning users.shutdown
https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/shutdown
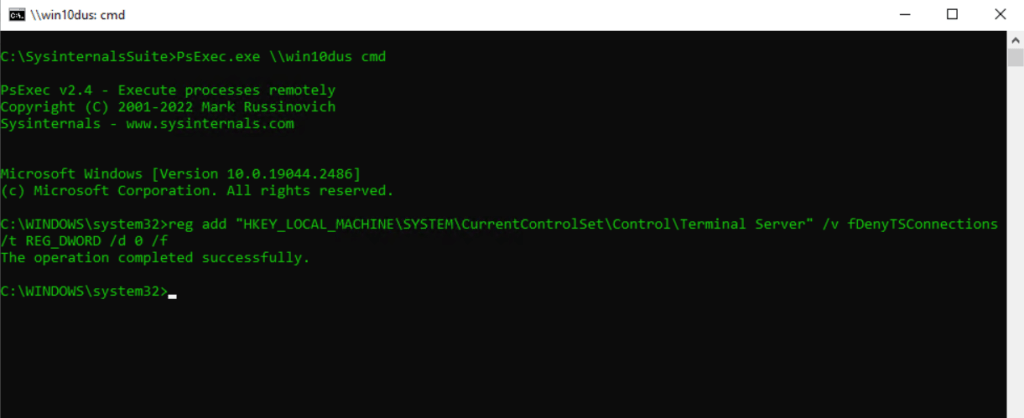
Enable Remote Desktop on a Remote Computer
PsExec.exe \hostname cmd
reg add “HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal Server” /v fDenyTSConnections /t REG_DWORD /d 0 /f
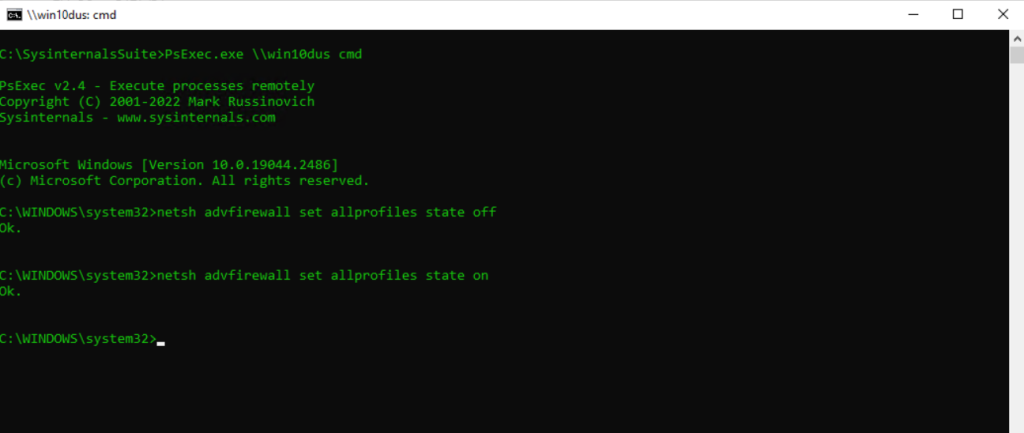
Enable or Disable Firewall on a Remote Computer
netsh advfirewall set allprofiles state off
netsh advfirewall set allprofiles state on
Open Firewall Ports on a Remote Computer
PsExec.exe \hostname cmd
netsh advfirewall firewall add rule name= “Open Port 80” dir=in action=allow protocol=TCP localport=80Old depricated command but still working:
netsh firewall add portopening TCP 80 “Open Port 80”Use netsh advfirewall firewall instead of netsh firewall to control Windows Firewall behavior
https://learn.microsoft.com/en-us/troubleshoot/windows-server/networking/netsh-advfirewall-firewall-control-firewall-behavior
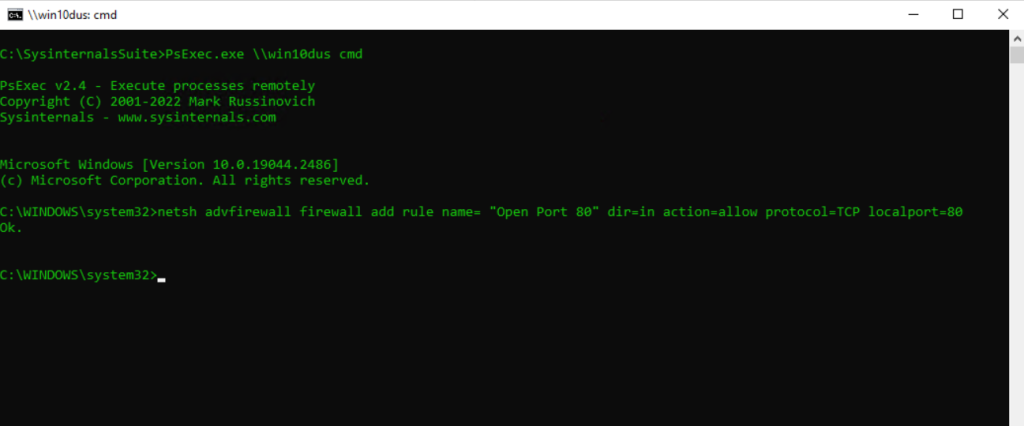
Determine active User Sessions on a Remote Computer and logging them off
PsExec.exe \hostname cmd
query session
logoff <session ID>query session
https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/query-sessionlogoff
https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/logoff
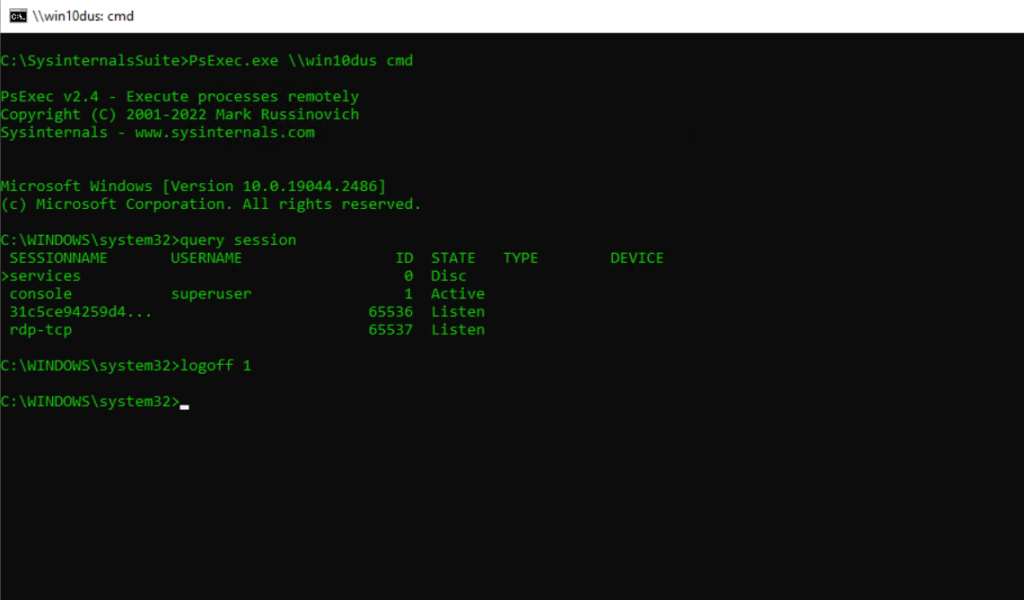
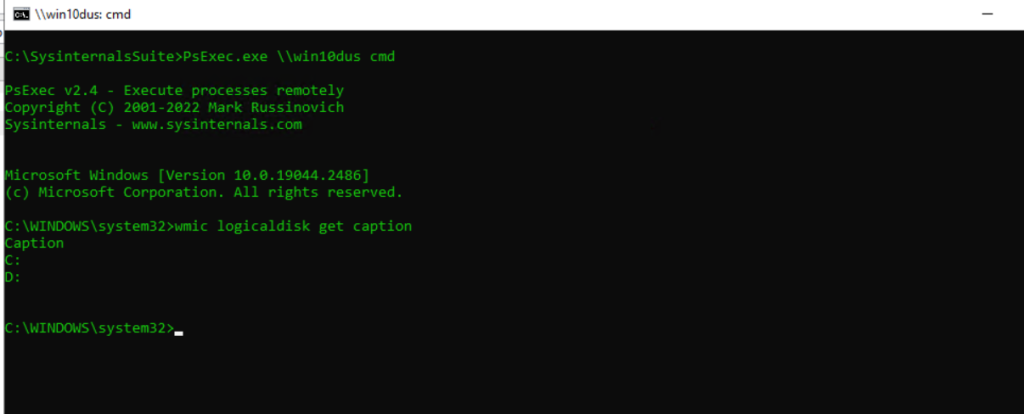
List Logical Volumes from a Remote Computer
PsExec.exe \hostname cmd
wmic logicaldisk get caption
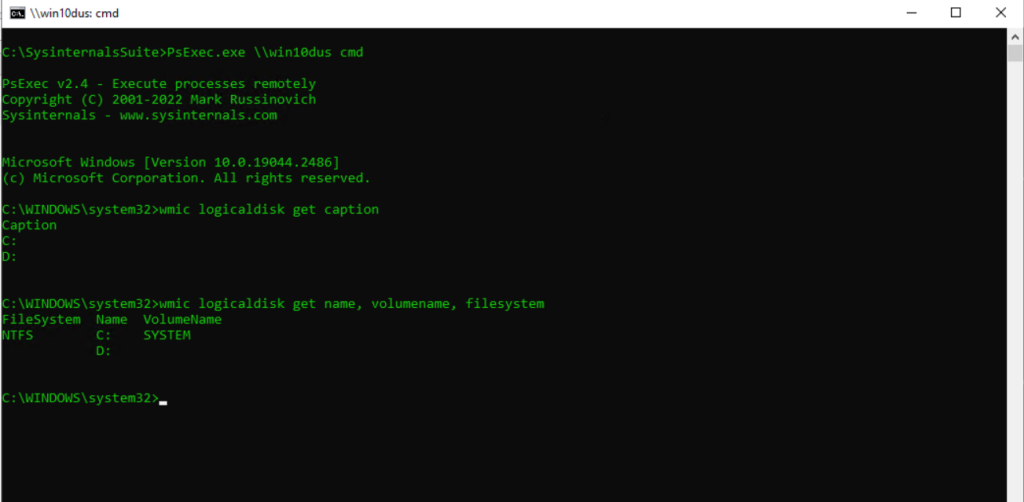
wmic logicaldisk get name, volumename, filesystem
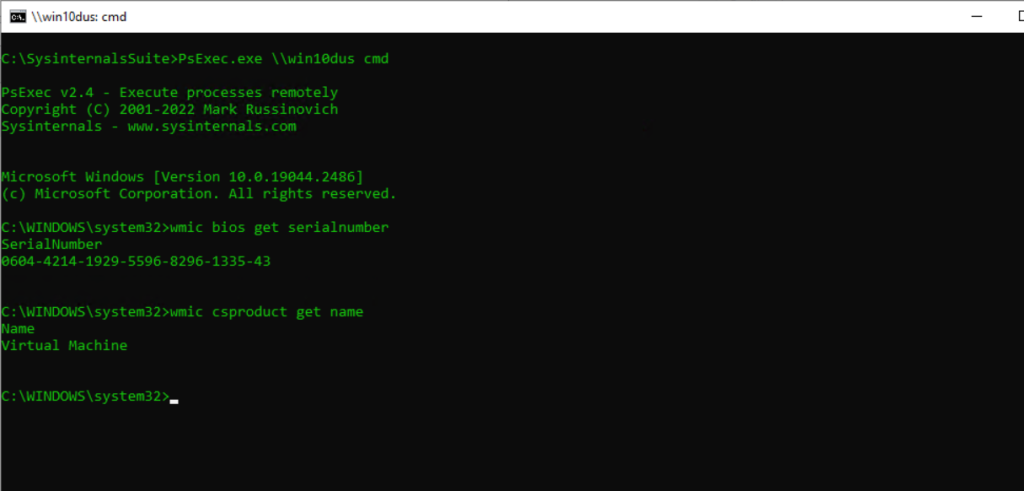
Get Serial and Model Number from a Remote Computer
PsExec.exe \hostname cmd
wmic bios get serialnumber
wmic csproduct get name
Copy Files from a Remote Computer
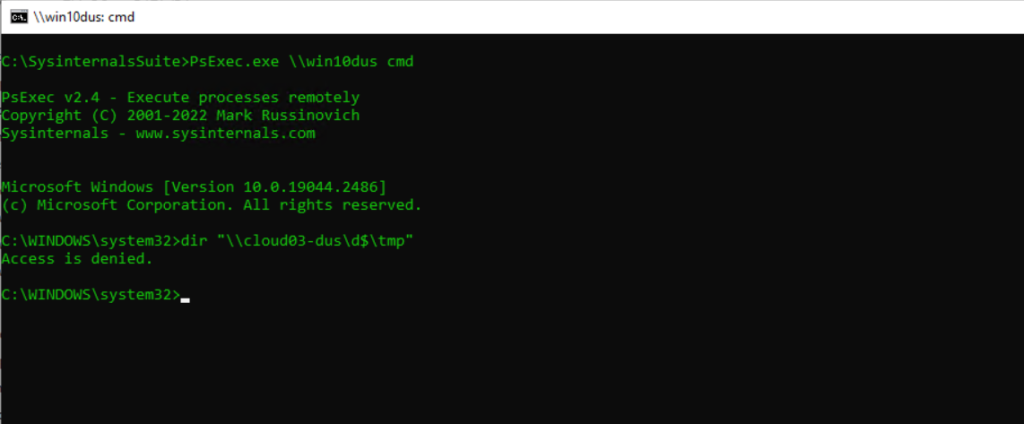
In case you want to use admin shares like d$ for the destination, you need to connect to the remote computer by explicitly using the -u user and -p password flags.
Below I am connecting to the remote computer without explicitly entering the user and password as I am still logged on as organization admin to the computer where I am executing the command.
Nevertheless I get an Access is denied by trying to connect to the admin share. Using the -u and -p flag and of course an user which has permissions to access the share will work.
Further since version 2.3+ also the -i flag.
This flag is required when attempting to run console applications interactively (with redirected standard IO).
Source: https://learn.microsoft.com/en-us/sysinternals/downloads/psexec
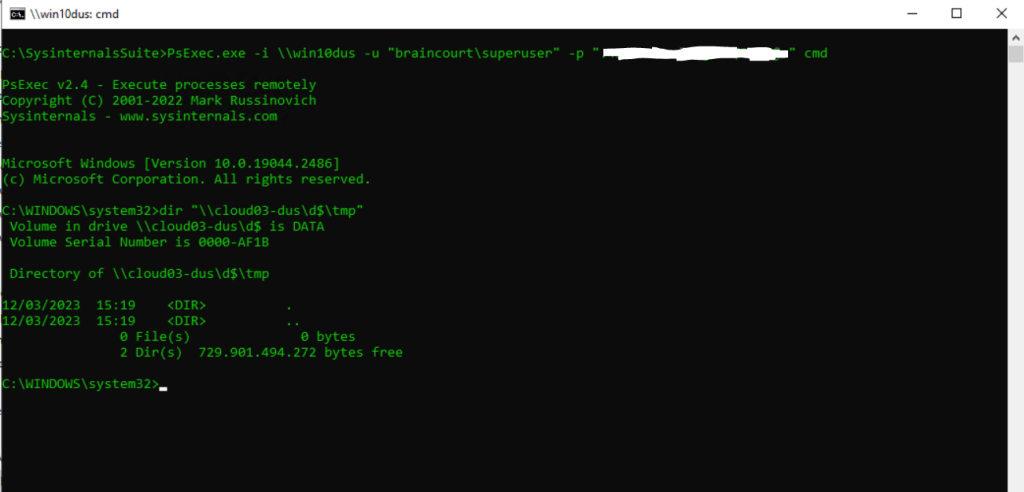
PsExec.exe -i \hostname -u <domainusername> -p <password> cmd
PsExec.exe -i \hostname -u <domainusername> -p <password> cmd
xcopy “C:FilesFolder 1” “cloud03-dusd$tmp” /s /f/s = copy all the files, subfolders, and files contained in the subfolders
/f = see every detail about what files are being copied as they’re being copiedxcopy
https://learn.microsoft.com/en-us/windows-server/administration/windows-commands/xcopy
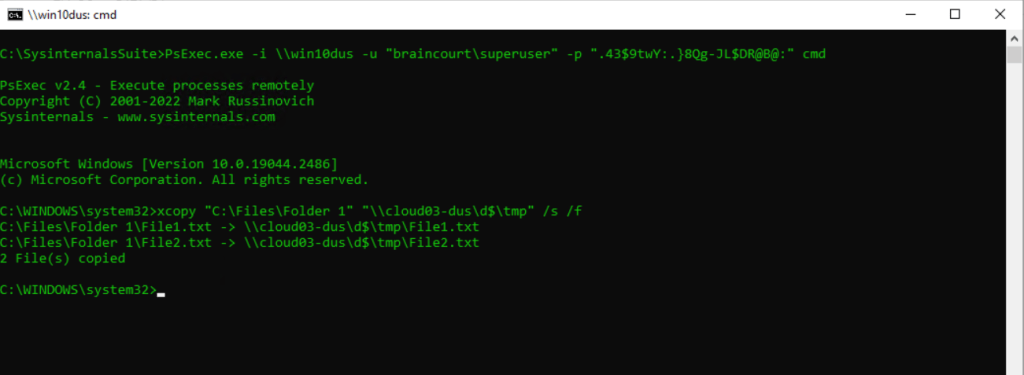
In the example above, I will copy the folder and all subfolders and files from “C:FilesFolder 1” on the remote computer, to the following UNC path “cloud03-dusd$tmp”.
cloud03-dus is a member server in the internal network.
Terminate stucking Hyper-V VMs from remote
Sometimes when you restart your Hyper-V Server without first shutting down all of your running VMs, the Hyper-V server possibly stuck at shutdown and here exactly at
Shutting down service: Hyper-V Virtual Machine Management.
The reason for is, that the host first tries to shutdown all VMs like shown on the screenshot below.
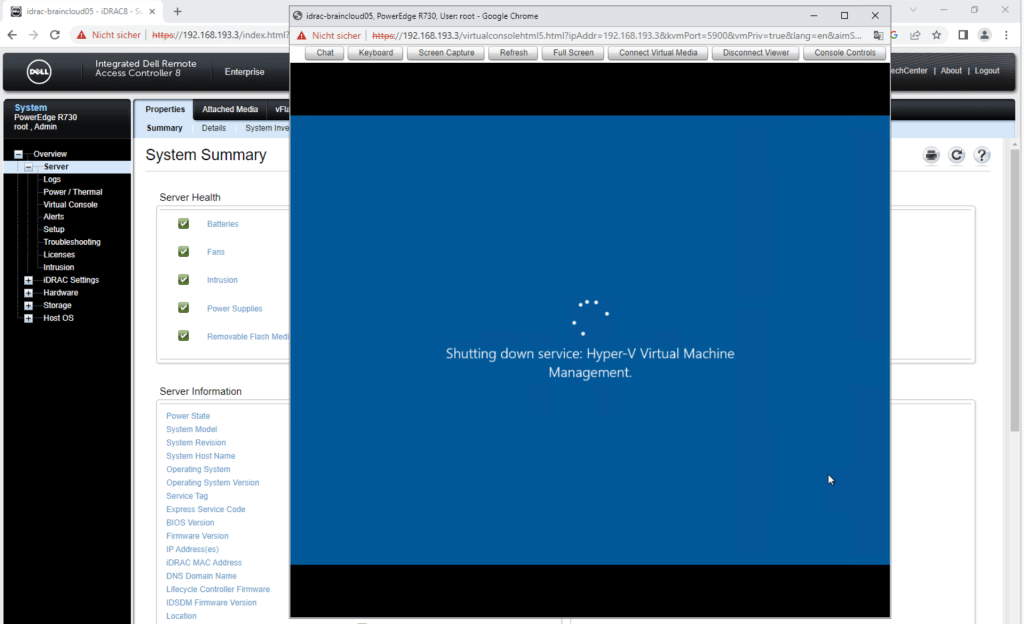
In case some VMs couldn’t be shutdown, the Hyper-V Server stucks here with its own shutdown.
As a final workaround you can terminate all VM processes to be able to finally shutdown and reboot your Hyper-V server as follows.
#determine all running VM processes, each VM is running within a vmwp.exe process
tasklist | findstr “vmwp.exe”
#terminate all these processes
taskkill /F /PID 7724 /PID 5388 /PID 7812 ………….
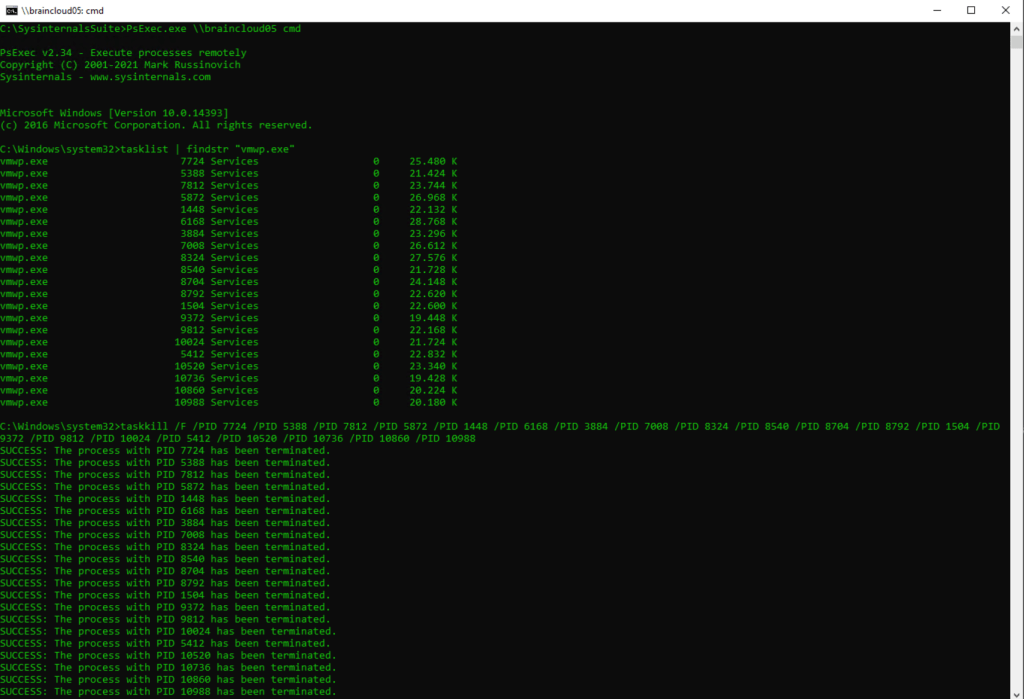
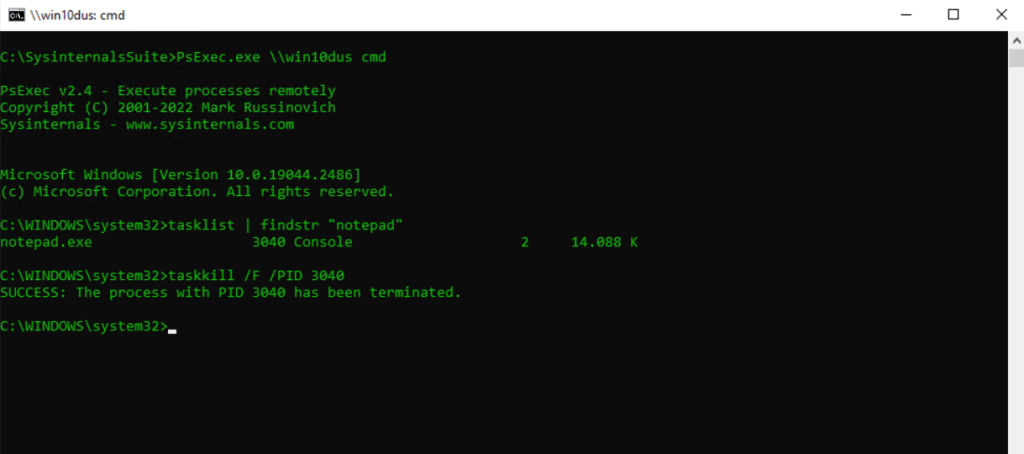
Terminate a Process on a Remote Computer
PsExec.exe \hostname cmd
tasklist | findstr “notepad”
taskkill /F /PID <process identifier>
Links
Sysinternals
https://learn.microsoft.com/en-us/sysinternals/PsExec
https://learn.microsoft.com/en-us/sysinternals/downloads/psexecWhat is Windows LAPS?
https://learn.microsoft.com/en-us/windows-server/identity/laps/laps-overviewUse netsh advfirewall firewall instead of netsh firewall to control Windows Firewall behavior
https://learn.microsoft.com/en-us/troubleshoot/windows-server/networking/netsh-advfirewall-firewall-control-firewall-behavior#command-example-8-enable-specific-servicesWindows Firewall Profiles
https://learn.microsoft.com/en-us/previous-versions/windows/desktop/ics/windows-firewall-profiles



