Network Security Groups (NSG) vs. Application Security Groups (ASG)
In Azure you can use a network security group to filter network traffic between Azure resources in an Azure virtual network (VNet).
These network security groups you can associate either to a virtual network subnet or directly to a network interface in a virtual machine. The same network security group can be associated to as many subnets and network interfaces as you choose.
The network security group contains security rules (inbound & outbound) to allow or deny network traffic.
On the other side an application security group can be used within a network security group and its inbound and outbound security rules as source or destination. The application security group can be associated with a virtual machine and therefore you can group virtual machines and define network security policies based on those groups.
To see both in action and understand the differences between them, I will use a virtual network with a subnet and two virtual machines to filter network traffic just for these virtual machines within the subnet.
First I was creating a network security group named nsgWebVMs as shown below. So far inbound HTTP and HTTPS network traffic is allowed from any source and to any destination.
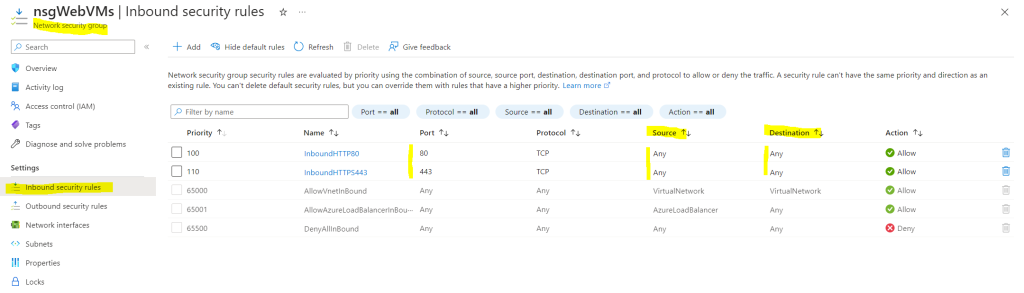
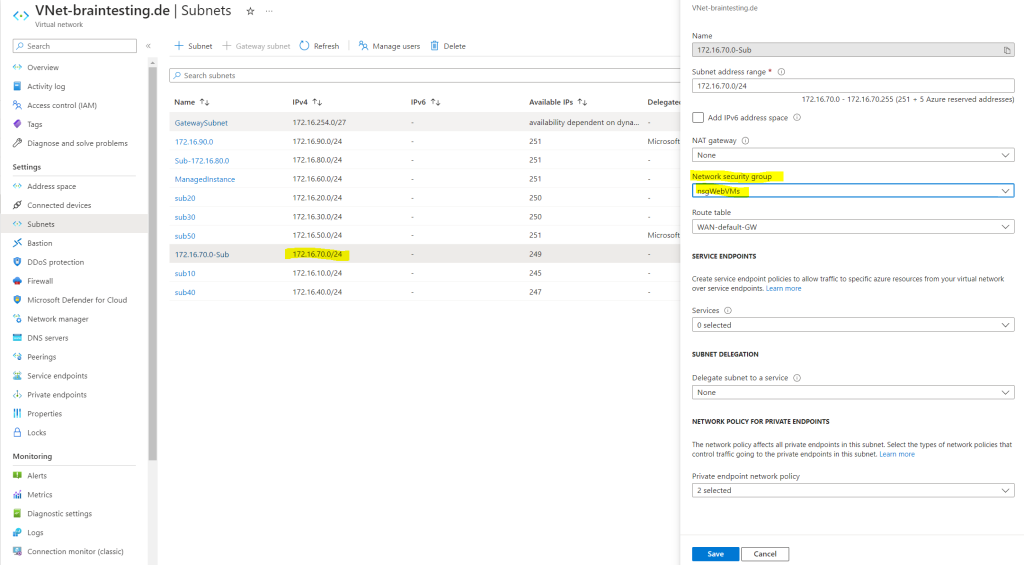
Next I will associate this network security group with the subnet 172.16.70.0/24 where my two virtual machines are running inside.
From now on for all Azure resources in this subnet, not just for the both virtual machines, port HTTP 80 and HTTPS 443 are open.
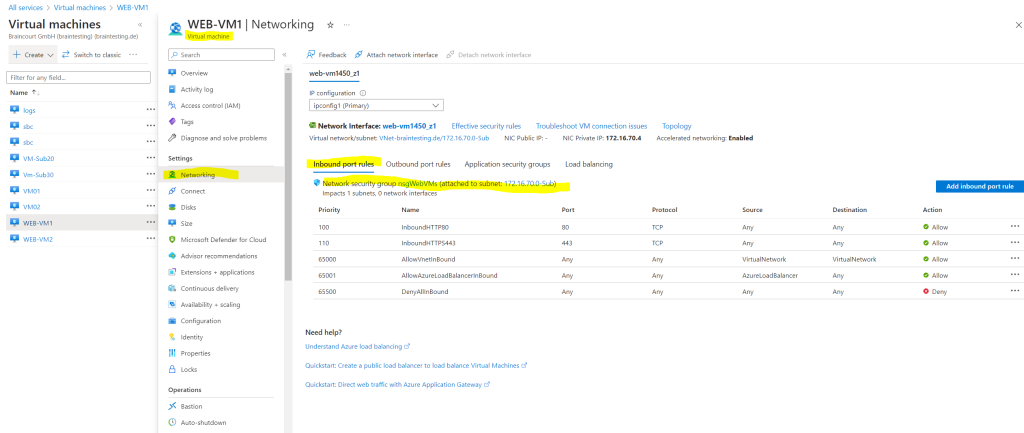
You can also see in the virtual machines networking menu, that the network security group named nsgWebVMs is attached to the subnet and therefore also valid for all virtual machines within this subnet.
We can now use an application security group to restrict e.g. network traffic for the subnet and only allow port HTTP 80 and HTTPS 443 inbound for the two virtual machines instead for the whole subnet.
Therefore I will first create a new application security group named asgWebTraffic as shown below.
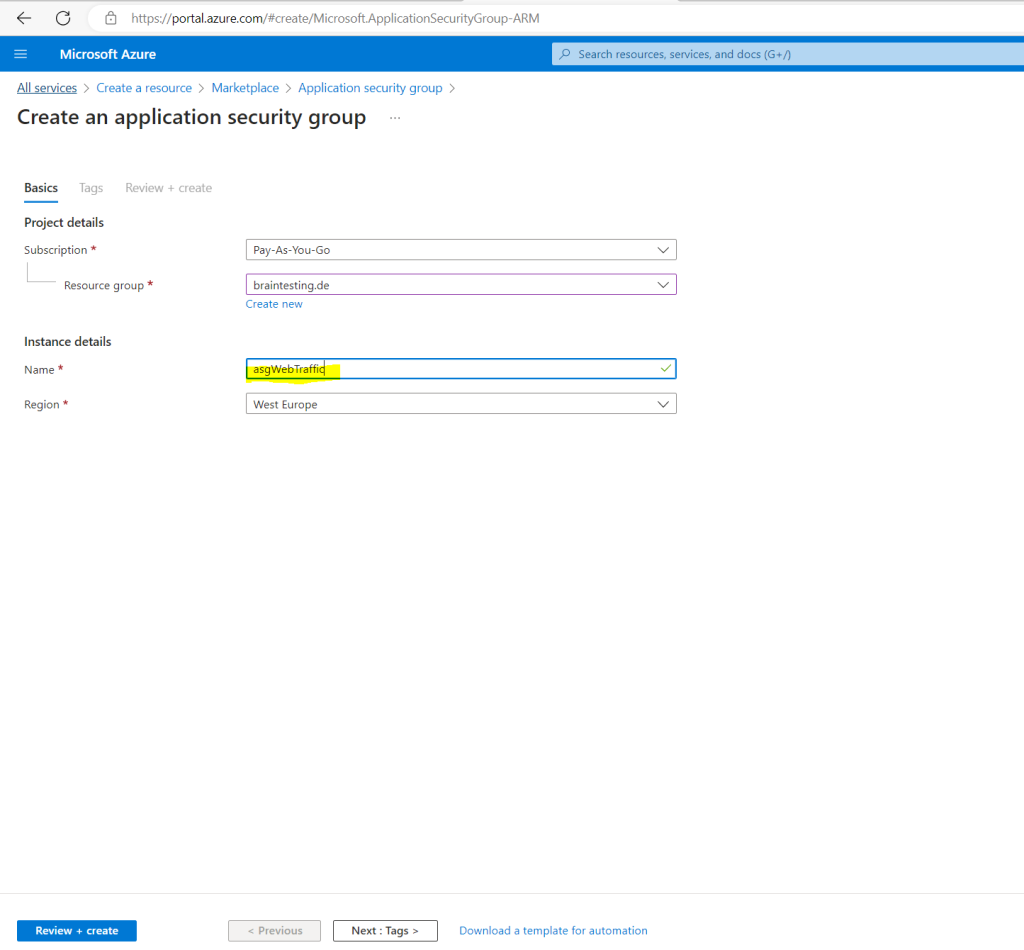
The application security group we can then associate with our network security group and its inbound security rules as shown below.
First I will change the inbound http port 80 security rule.
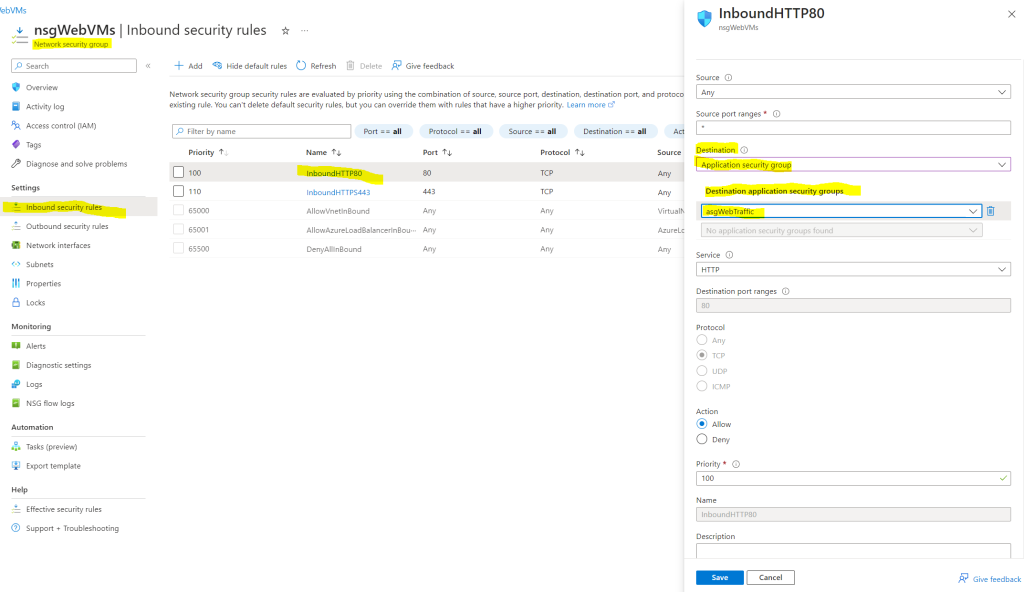
The same I will do for the inbound https port 443 security rule.
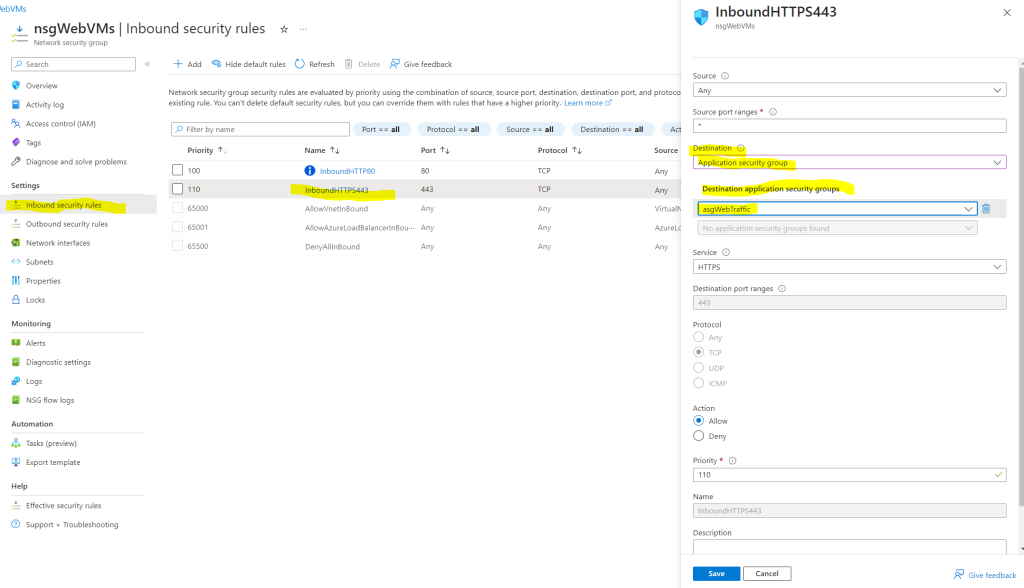
Finally our network security group and its inbound security rules will looks like this. From now on only virtual machines in our subnet, which are associated with the new application security group named asgWebTraffic, will be able to receive network traffic from any source including the internet for http and https.
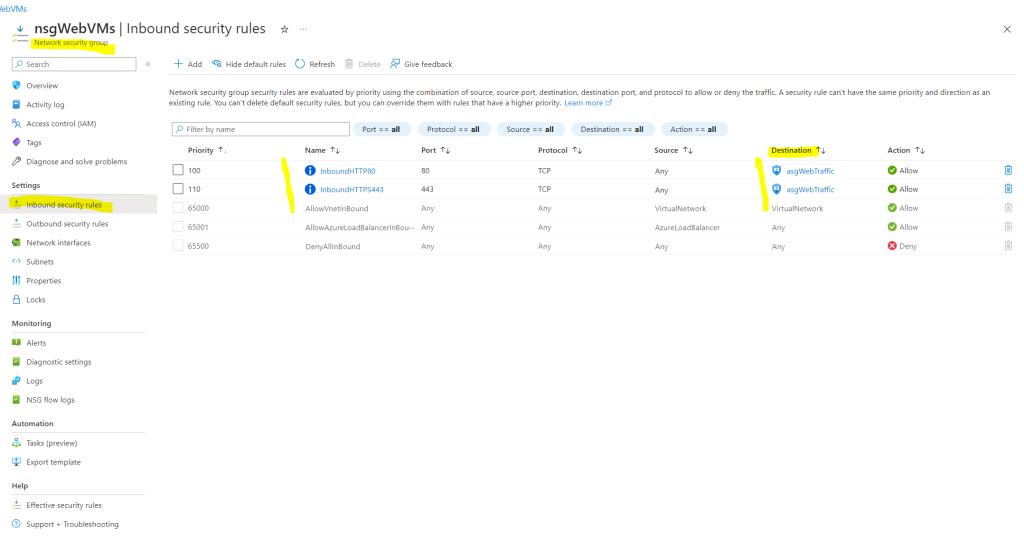
So the last step is to associate the new application security group to both virtual machines we want to be able to connect from the internet using http and https.
We can associate an application security group to a virtual machine within the networking menu from the virtual machine and here in the Application security groups tab as shown below.
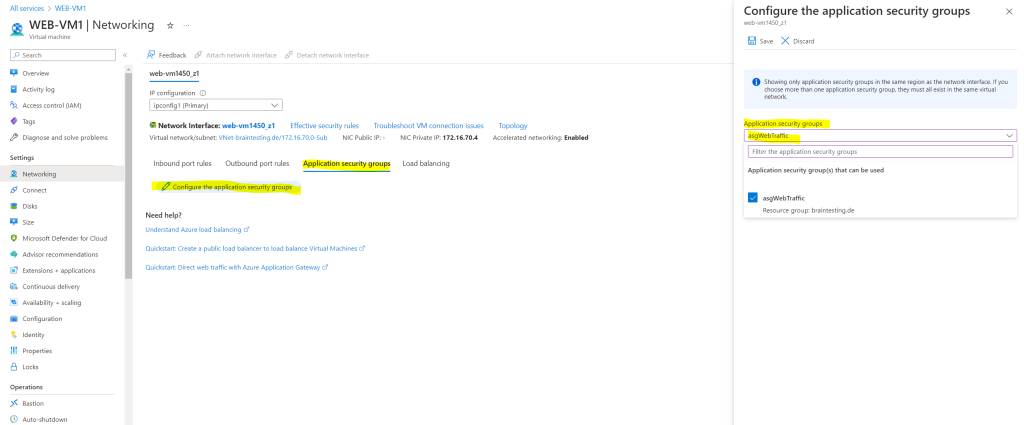
Application security group is assigned to the virtual machine.
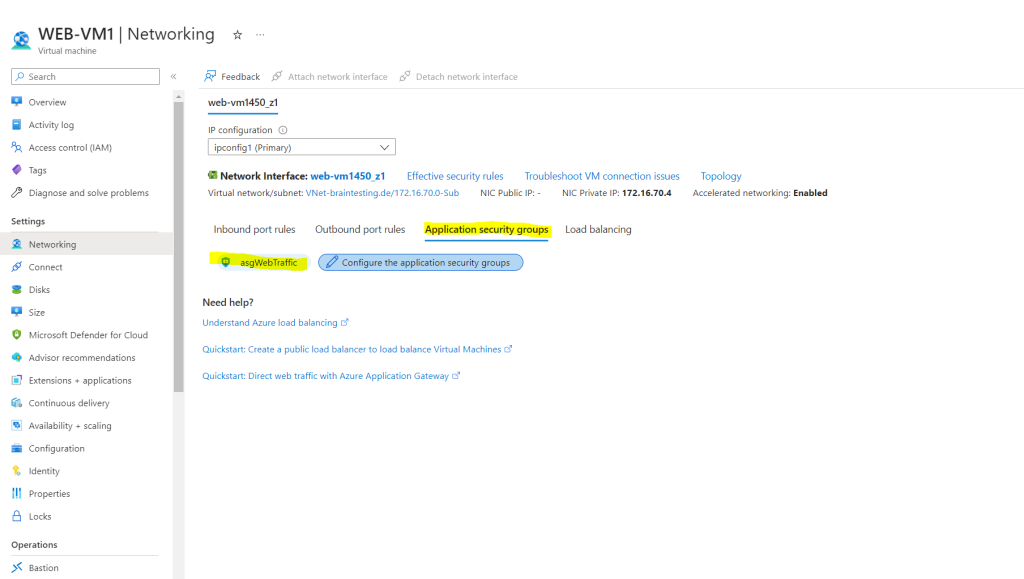
Application security groups enable you to configure network security as a natural extension of an application’s structure, allowing you to group virtual machines and define network security policies based on those groups. You can reuse your security policy at scale without manual maintenance of explicit IP addresses. The platform handles the complexity of explicit IP addresses and multiple rule sets, allowing you to focus on your business logic.
Source: https://learn.microsoft.com/en-us/azure/virtual-network/application-security-groups
So finally Application security groups (ASG) helps to simplify the management of Network security groups (NSG) and its inbound and outbound security rules.
Links
Network security groups
https://learn.microsoft.com/en-us/azure/virtual-network/network-security-groups-overviewApplication security groups
https://learn.microsoft.com/en-us/azure/virtual-network/application-security-groups
Follow me on LinkedIn


