How to run Azure VMs in Safe Mode – RDP Service not available in Safe Mode – Using the Serial Console and Special Administration Console (SAC) for Azure VMs
For Azure virtual machines you doesn’t have a real GUI console like for Hyper-V or vSphere in on-premises environments. In case you need to boot a Windows virtual machine in safe mode for whatever reason like performing some tasks you are just able to do in safe mode, you are not able to connect to the desktop by using a GUI console or RDP and first need to exit safe mode again.
!! Note !!
Before enabling safe boot below for an Azure virtual machine, first check if the Emergency Management Services (EMS) and its Special Administration Console (SAC) is enabled and working for the Azure VM as shown further down.
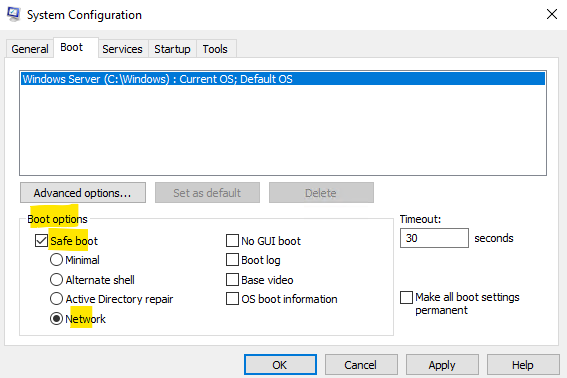
The RDP service is not available in Safe Mode. Only essential system programs and services are loaded when the VM boots into Safe Mode. This applies for the two different versions of Safe Mode which are Safe Boot minimal and Safe Boot with connectivity.
In case the Emergency Management Services (EMS) and its Special Administration Console (SAC) is not enabled for your Azure VM and working, the only way to exit safe mode again to finally be able to boot the VM successfully, is by repairing the VM offline as shown in my following post.
To perform tasks in Safe Mode and also exit Safe Mode later we can use in Azure the serial console which provides a text-based console for virtual machines (VMs) and virtual machine scale set instances running either Linux or Windows.
Serial Console connects to the ttyS0 or COM1 serial port of the VM or virtual machine scale set instance, providing access independent of the network or operating system state. The serial console can be accessed by using the Azure portal or Azure CLI and is allowed only for those users who have an access role of Contributor or higher to the VM or virtual machine scale set.
Regions
Serial Console is available in the following regions:
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/serial-console-overview#regionsFor serial console documentation for Linux, see Azure Serial Console for Linux.
Prerequisites to use the Azure Serial Console
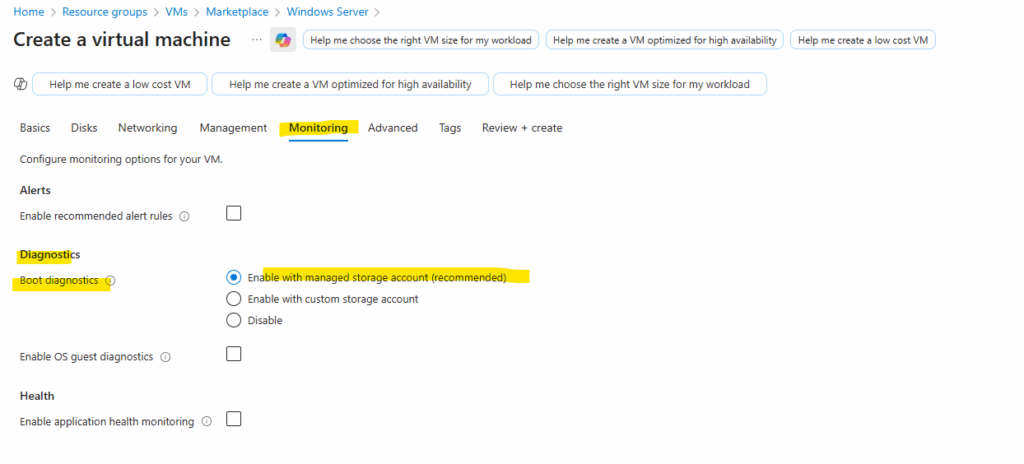
The VM or virtual machine scale set instance must have boot diagnostics enabled.
When you create a VM in the Azure portal, the default setting is to have boot diagnostics enabled using a managed storage account.
Serial Console is compatible with a managed boot diagnostics storage account.
Your VM or virtual machine scale set instance must use the resource management deployment model. Classic deployments aren’t supported.
Your account that uses serial console must have the Virtual Machine Contributor role for the VM and the boot diagnostics storage account
Your VM or virtual machine scale set instance must have a password-based user. You can create one with the reset password function of the VM access extension. Select Reset password from the Help section.
Performing Tasks in Safe Boot Mode by using the Serial Console and SAC
As already mentioned, to perform tasks in Safe Mode for an Azure virtual machine, we can use the serial console in the Azure portal in order to connect to the Special Administration Console (SAC) which is enabled in Azure by default on newer Windows Server images (since February 2018).
SAC is an operating system component that runs in kernel mode and displays the following prompt when you establish an out-of-band connection to a computer that is running Emergency Management Services:
SAC>
In addition to providing a variety of commands that support remote management, SAC provides access to the Windows command prompt and to Setup logs. When you use SAC, you can create multiple user sessions or channels and switch among them so that you can use SAC commands while concurrently running command-line commands or viewing Setup logs.
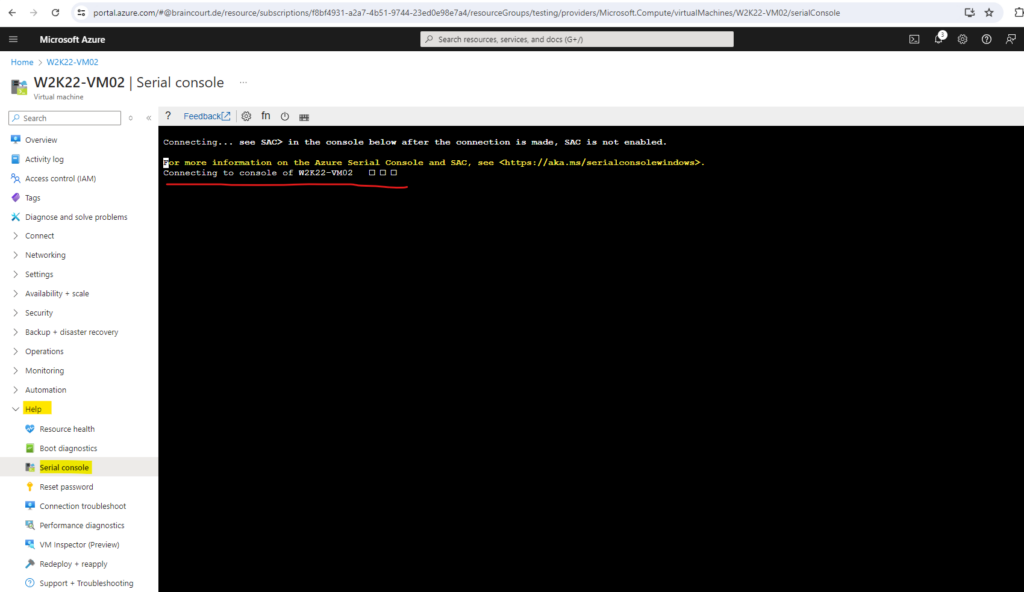
In the Azure portal and the virtual machine blade navigate to Help -> Serial Console.
In case boot diagnostics is enabled you will get connected to the serial console.
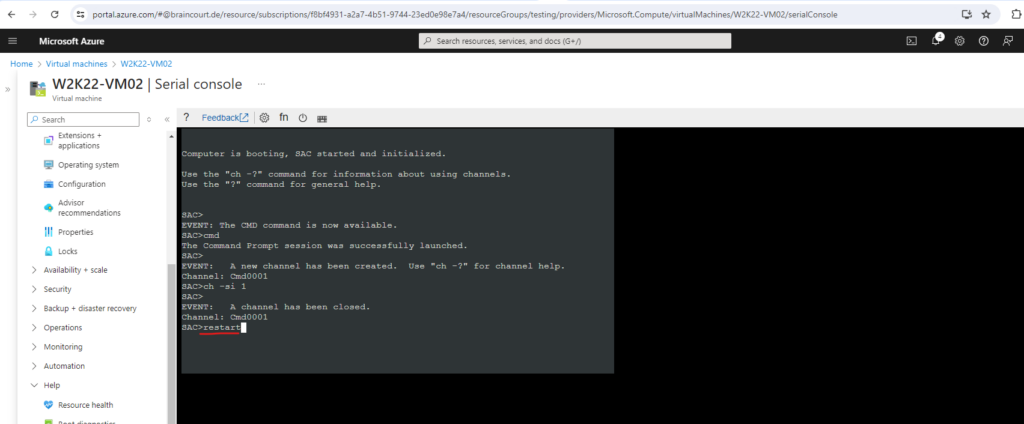
Enter the following commands to finally open an administrator command prompt (CMD).
SAC>cmd SAC>ch CMD is on channel 1. Switch to a channel by its number SAC>ch -si 1
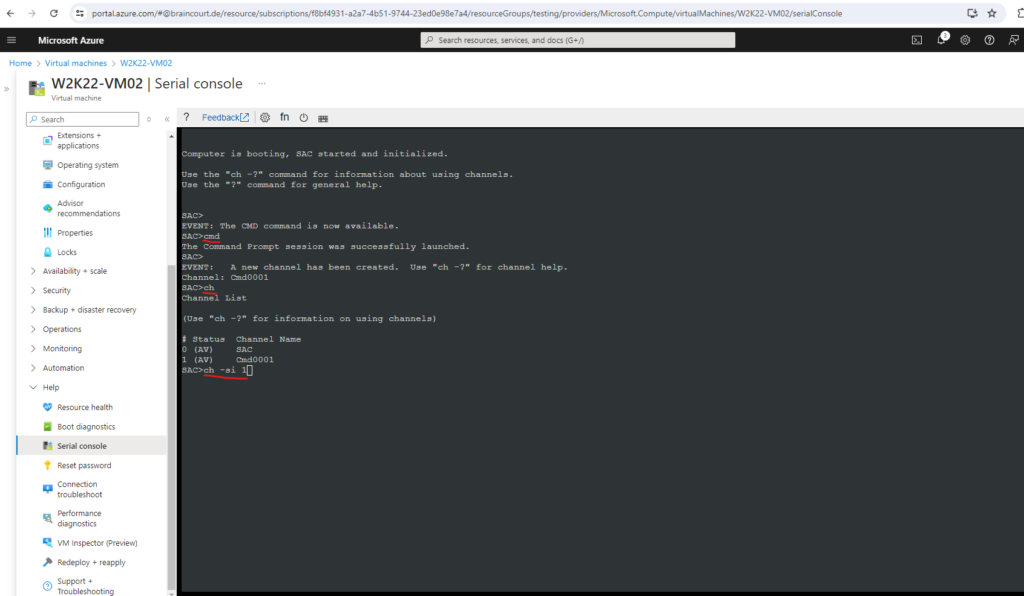
Press Enter to view and switch to the CMD channel.
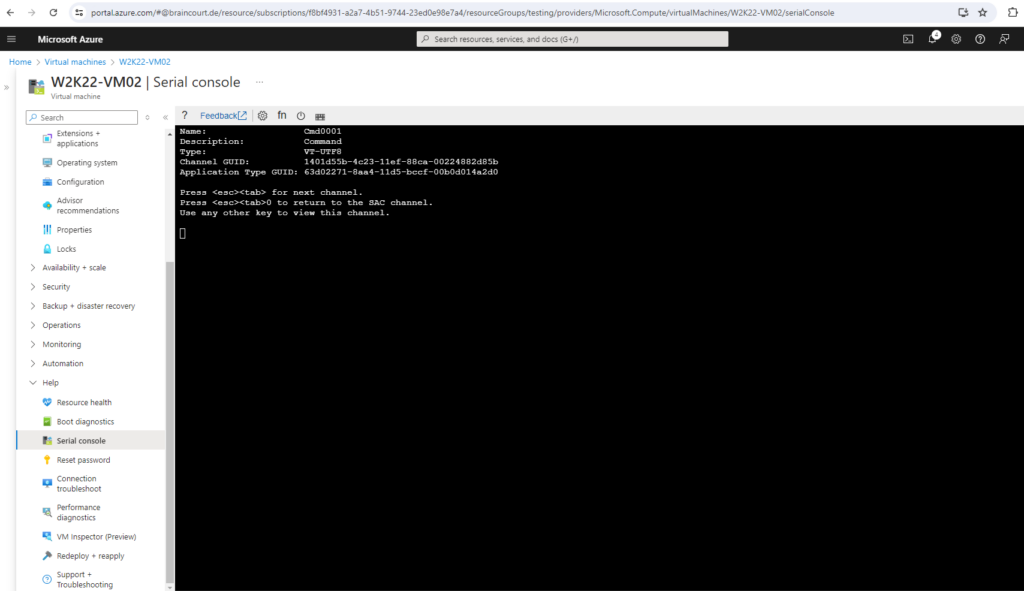
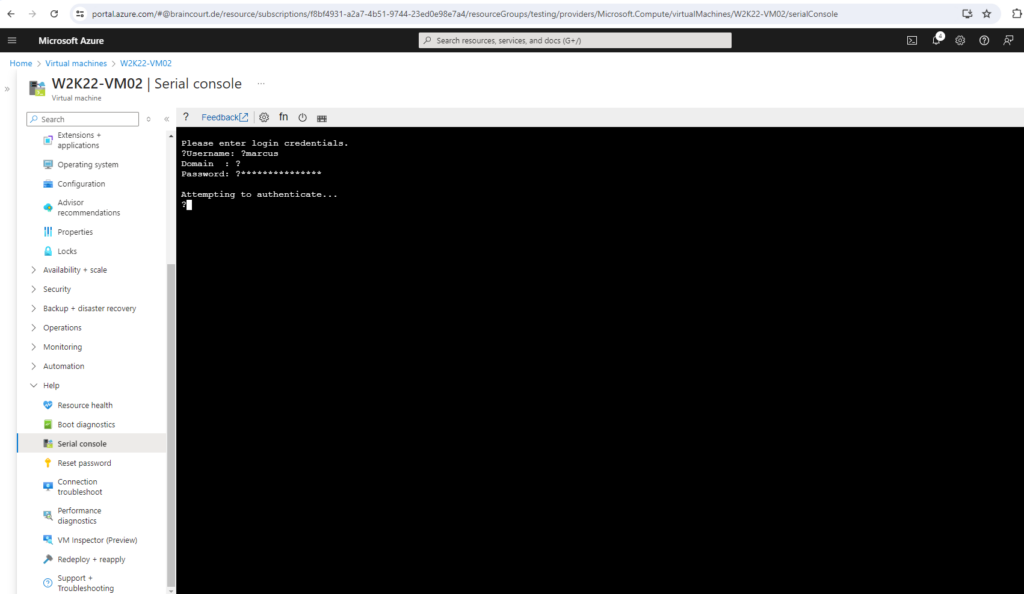
Enter the credentials for the built-in-administrator account.
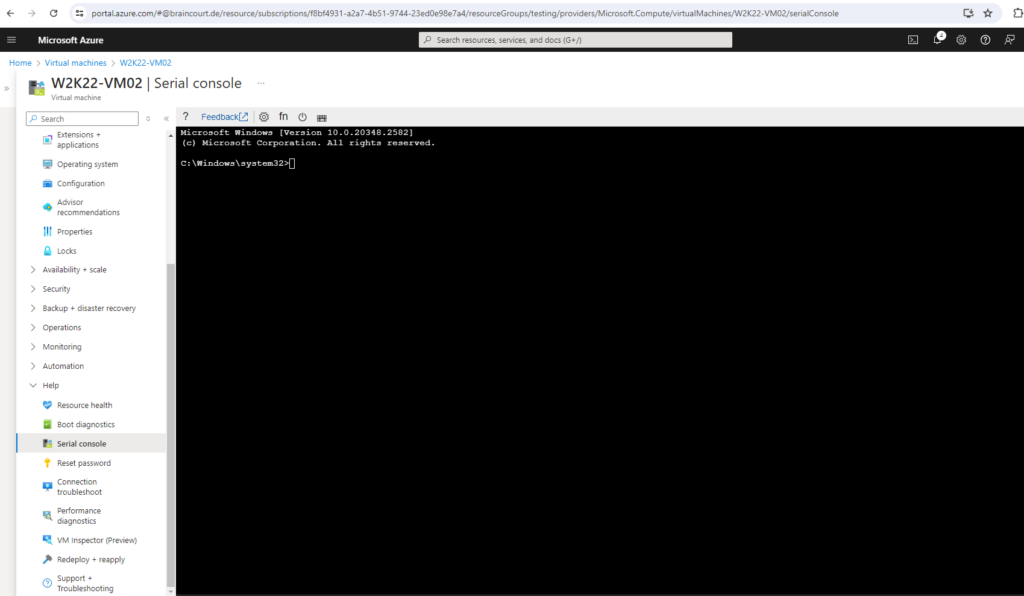
We are now connected with an administrator command prompt (CMD) for our virtual machine.
The CMD you access via SAC is the same cmd.exe you use when connected via RDP. All the same commands and tools are available, including the ability to launch PowerShell from that CMD instance.
That is a major difference between SAC and the Windows Recovery Environment (WinRE) in that SAC is letting you manage your running OS, where WinRE boots into a different, minimal OS. While Azure VMs do not support the ability to access WinRE, with the serial console feature, Azure VMs can be managed via SAC.
Because SAC is limited to an 80×24 screen buffer with no scroll back, add | more to commands to display the output one page at a time. Use <spacebar> to see the next page, or <enter> to see the next line.
Because of SAC’s limited screen buffer, longer commands may be easier to type out in a local text editor and then pasted into SAC.
So from here we can also start a PowerShell instance by just enter PowerShell in the CMD instance and press Enter.
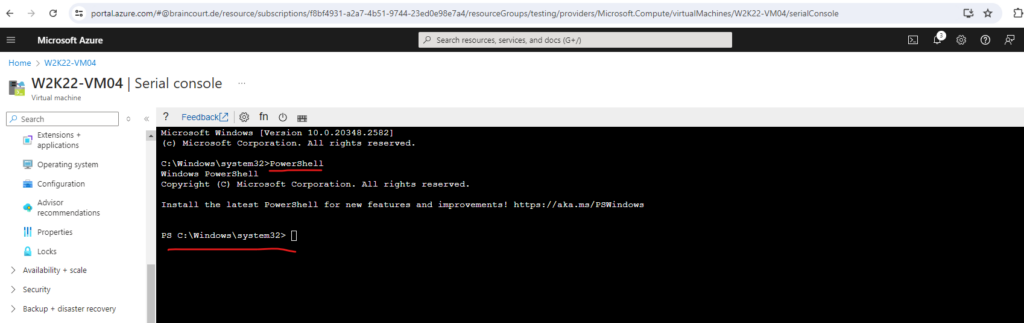
After performing some tasks in Safe Mode we can later exit Safe Mode by using the BCDEdit command-line tool.
BCDEdit Command-Line Options
Boot Configuration Data (BCD) files provide a store that is used to describe boot applications and boot application settings.BCDEdit is a command-line tool for managing BCD. It can be used for a variety of purposes, including creating new stores, modifying existing stores, and adding boot menu options.
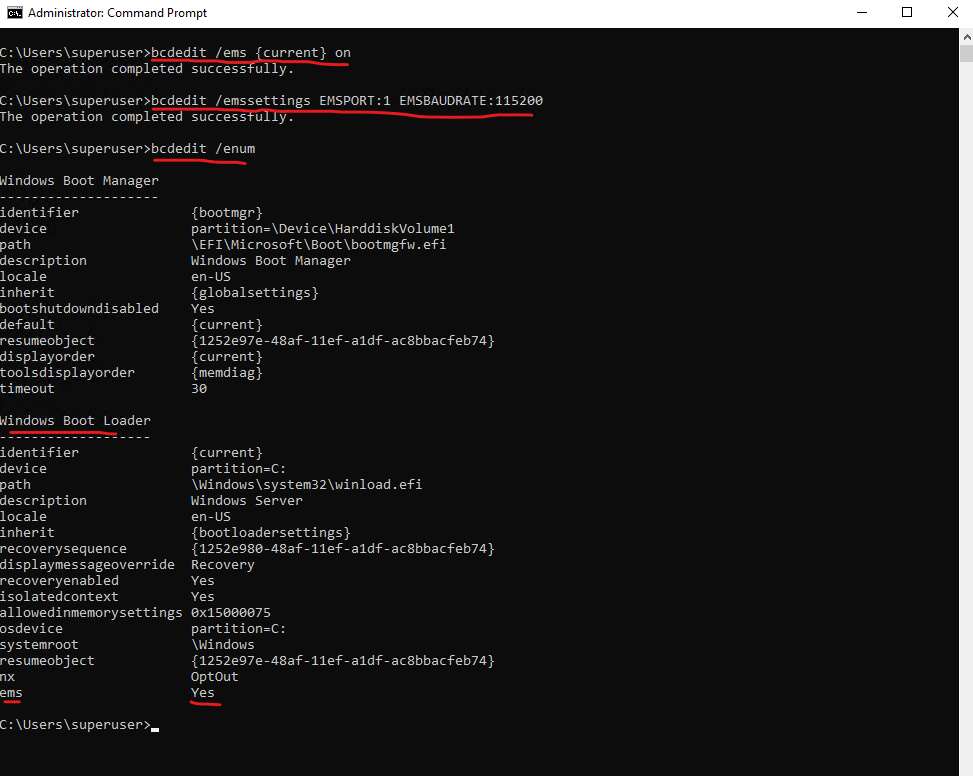
To check the Safe Mode state we can use the following command:
bcdedit /enum
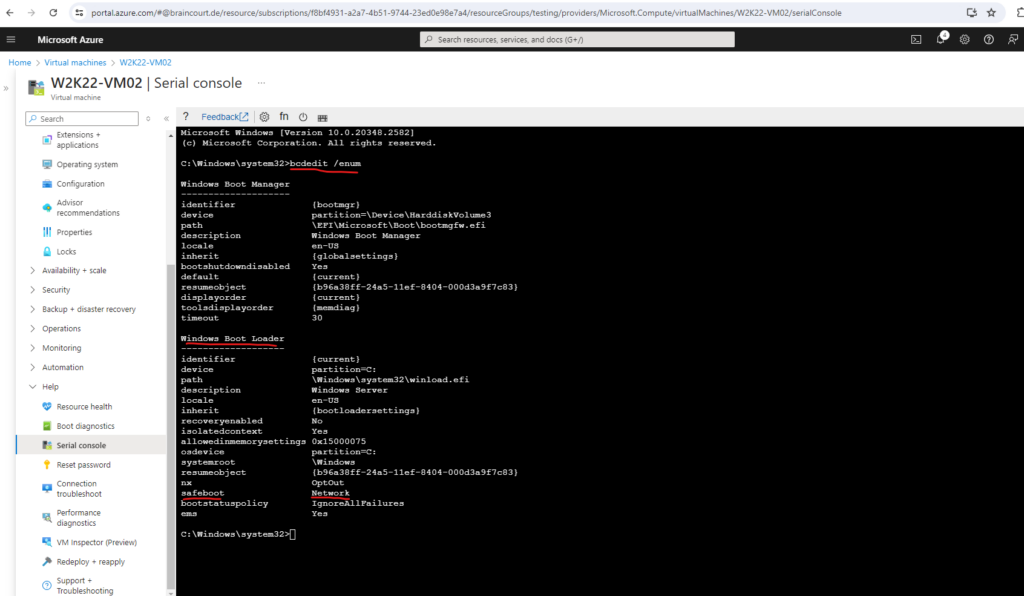
Delete the safeboot flag, so the VM will boot into normal mode again:
bcdedit /deletevalue {current} safeboot
Also check the boot configuration afterwards to make sure that the safeboot flag is removed:
bcdedit /enum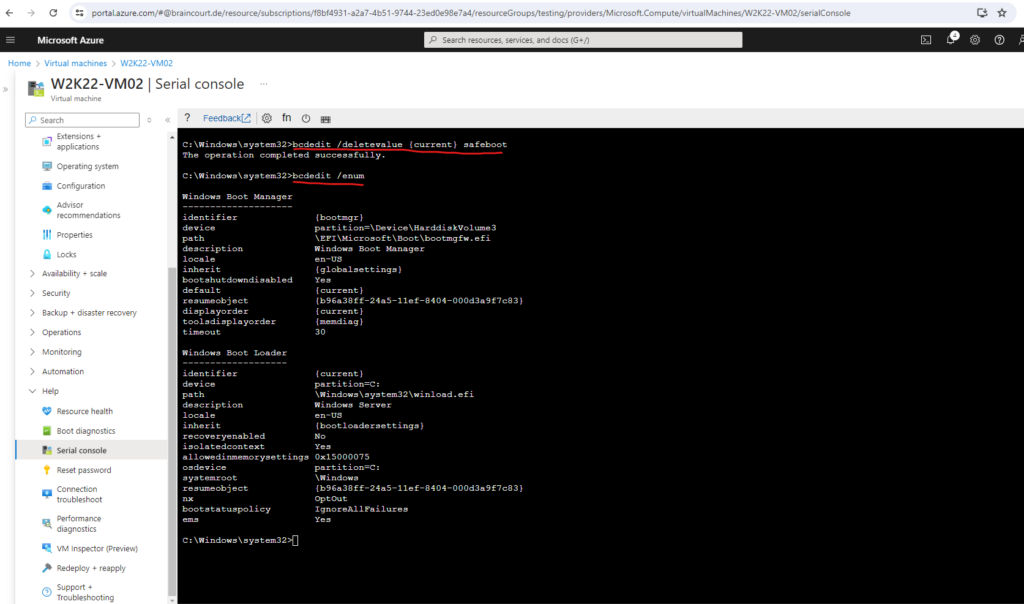
Finally exit the CMD as usual by enter the exit command.
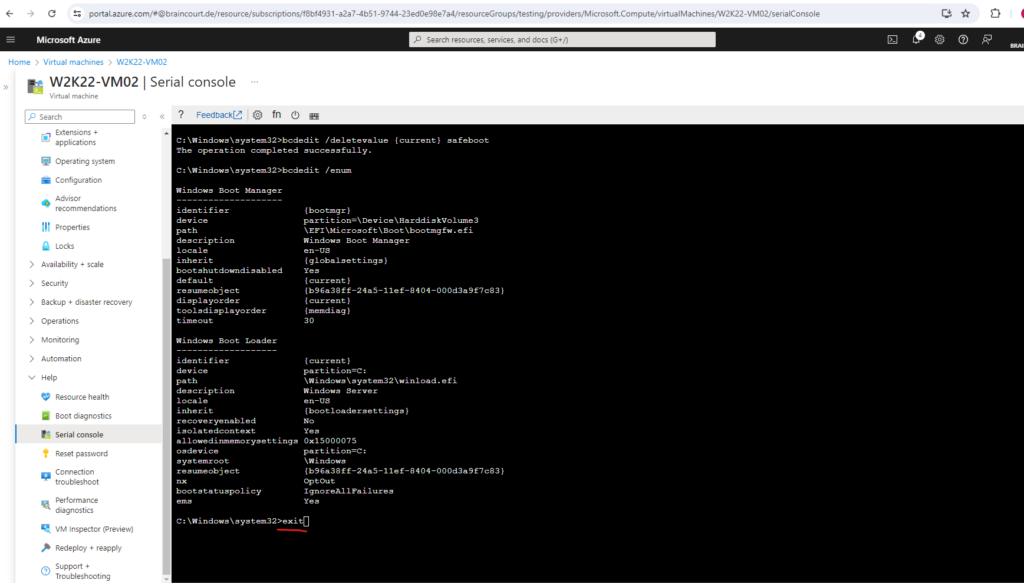
Press the tab key to go back to the SAC console.
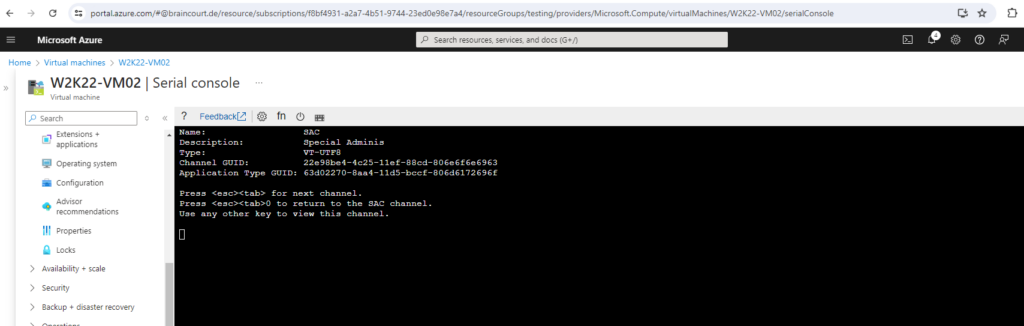
And finally enter restart in the SAC console to boot Windows in normal mode.
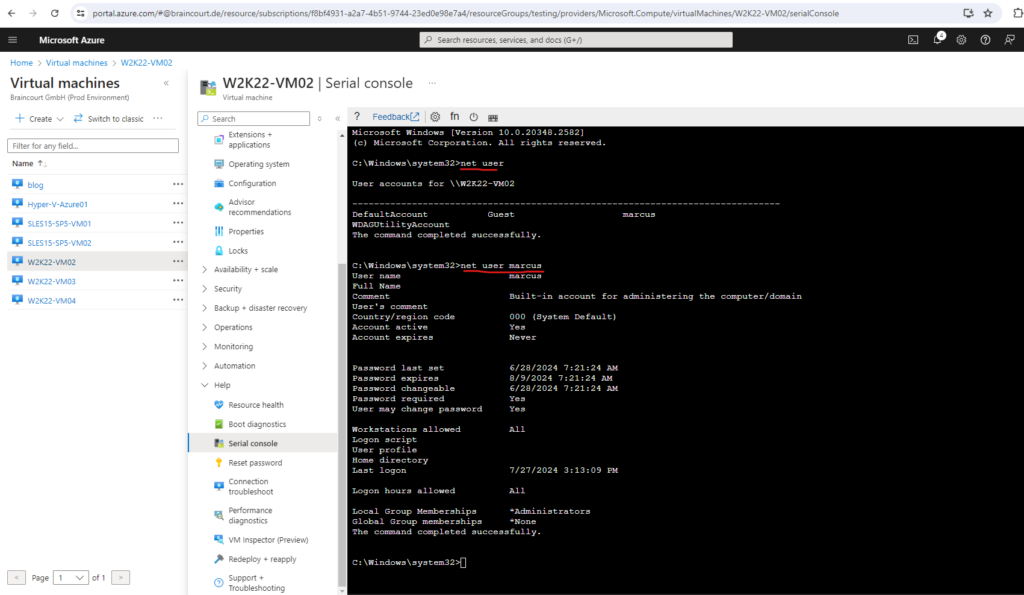
As already mentioned finally we have here an administrator command prompt (CMD) and can perform some tasks like for example changing passwords for local user accounts. This can be done of course much better directly on the desktop but just as an example.
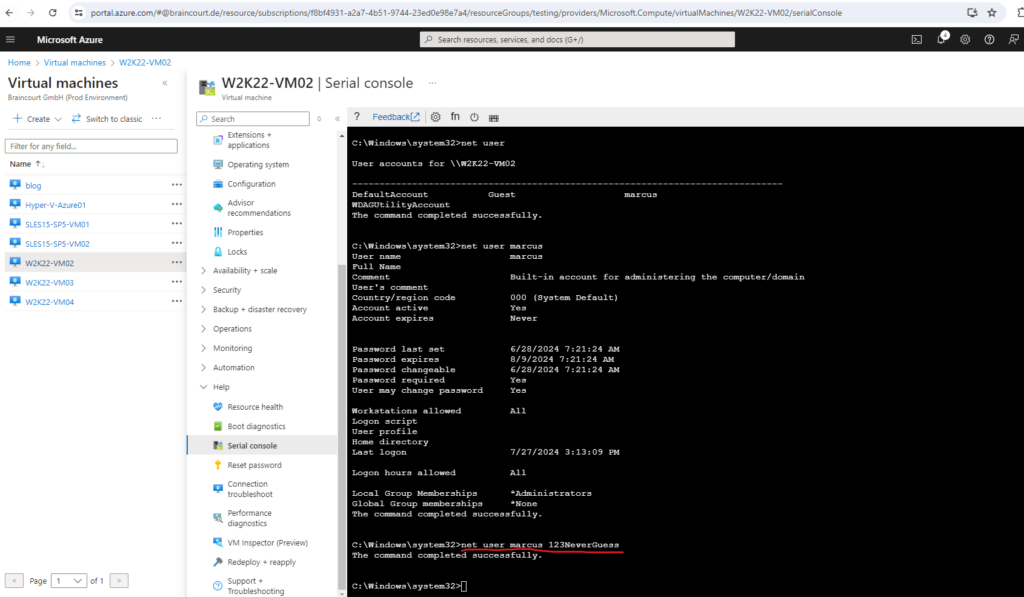
Set a new password for a local user.
About using an administrator command prompt (CMD) to reset passwords even for domain accounts you can also read my following post which describes how to get privileged access to a domain controller (provided we have physical access to) by using the notorious Utilman Hack.
https://blog.matrixpost.net/domain-controller-protection-via-bitlocker-drive-encryption/
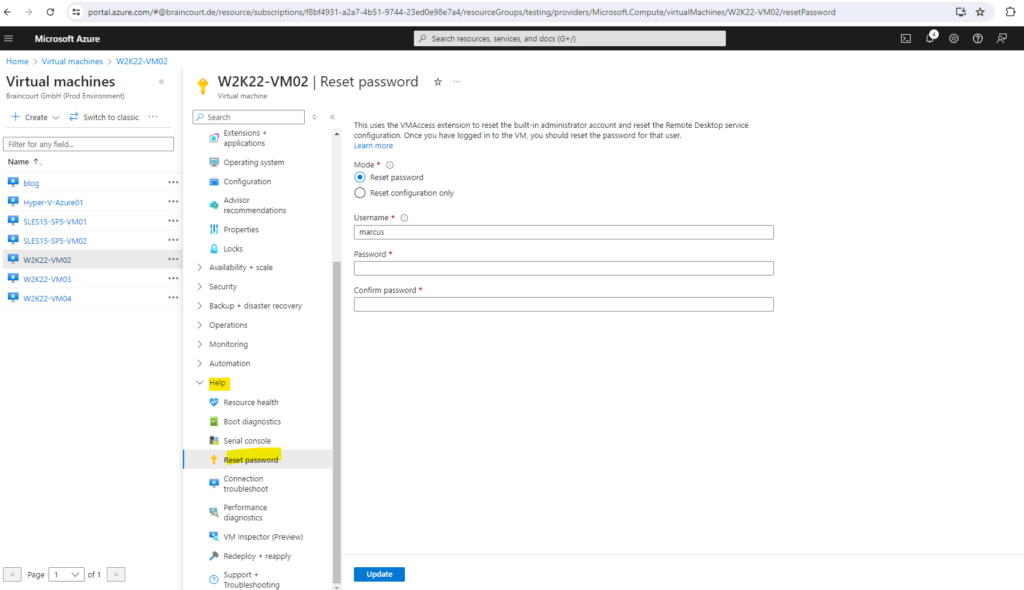
In case you forgot the password for the built-in-administrator account and can’t authenticate to sign-in to the CMD, you can reset this in the Azure Portal and the virtual machines blade under Help -> Reset password,
More examples of common tasks you can perform here by using the administrator command prompt (CMD) or PowerShell you will find in the following article by Microsoft.
Windows Commands – CMD and PowerShell
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/serial-console-cmd-ps-commands
Troubleshooting
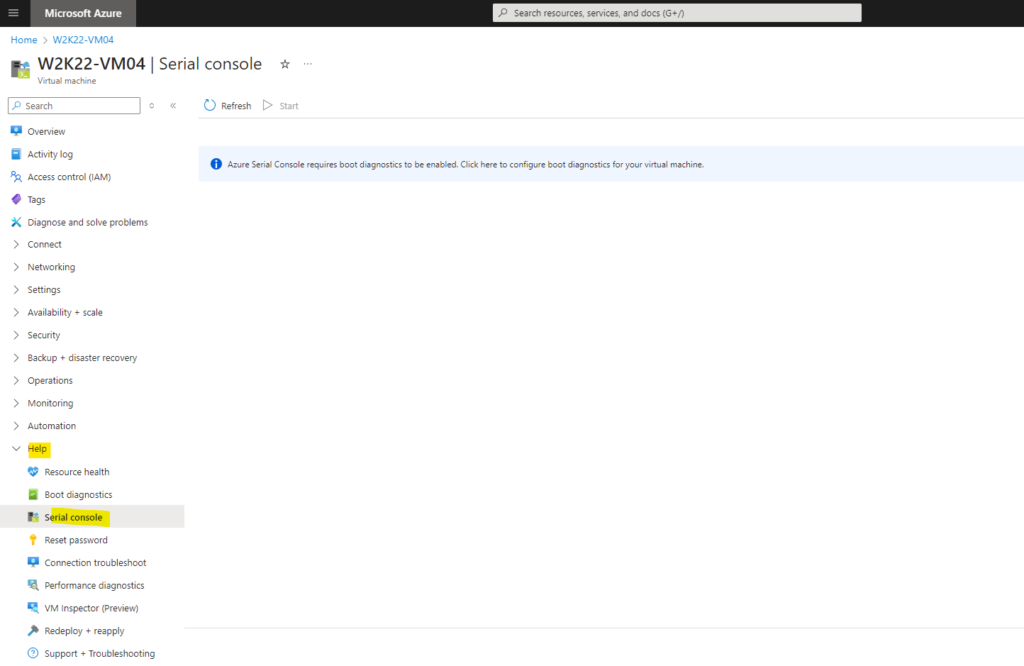
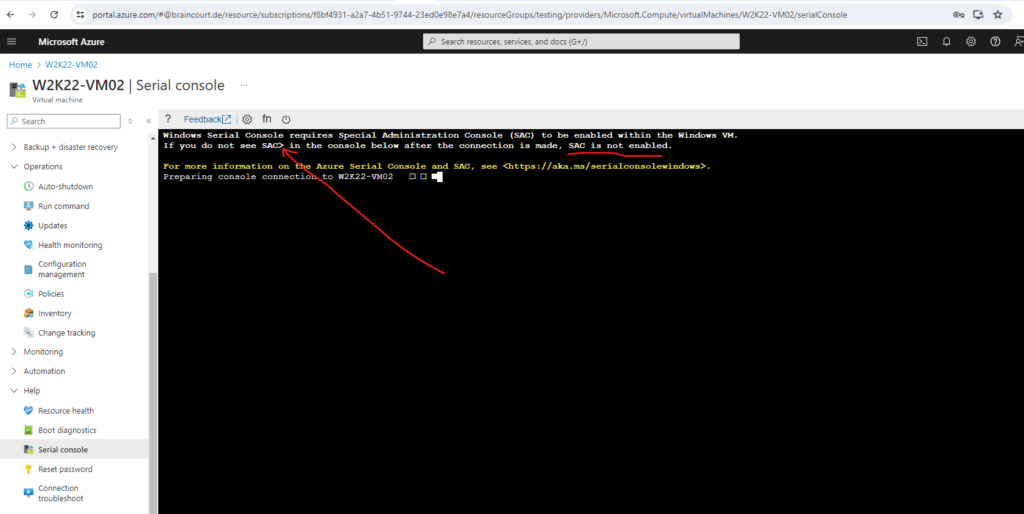
If you are not seeing anything in the serial console, make sure that boot diagnostics is enabled on your VM or virtual machine scale set. Further the Emergency Management Services (EMS) must be enabled on Windows to be able to access the Special Administration Console (SAC).
Newer Windows Server images on Azure have Special Administration Console (SAC) enabled by default.
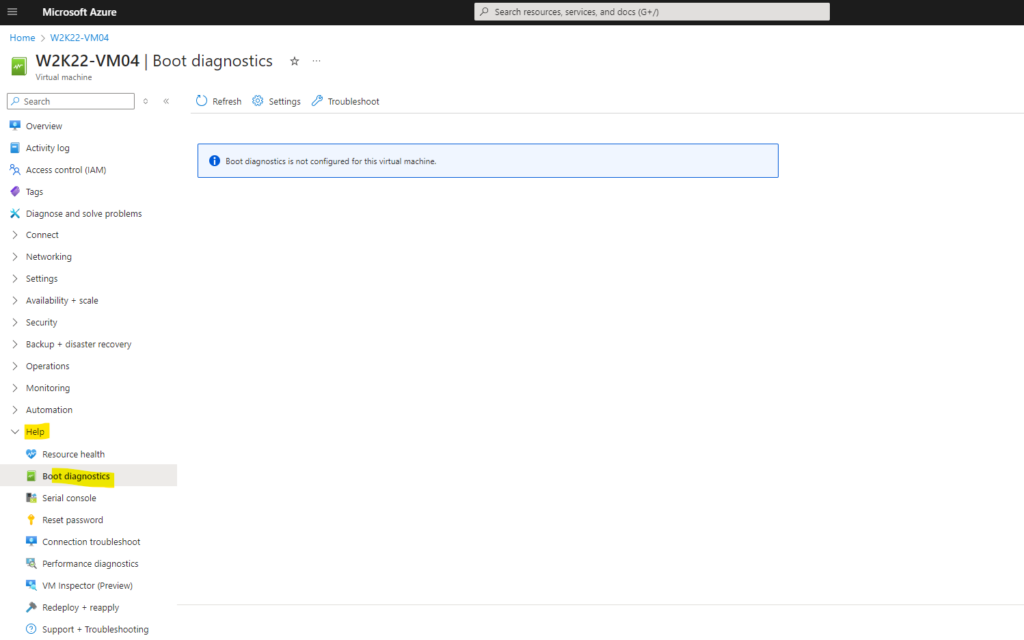
In case boot diagnostics and therefore also the serial console is not enabled for your virtual machine it will looks like below.
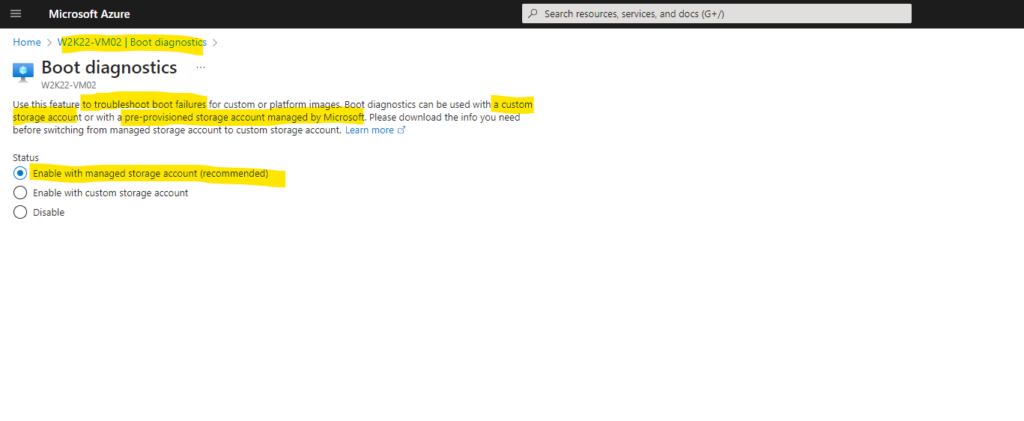
Enable Boot Diagnostics in the Azure portal
Managed boot diagnostics can be enabled through the Azure portal, CLI and ARM Templates.
When you create a VM in the Azure portal, the default setting is to have boot diagnostics enabled using a managed storage account as shown on the screenshot below. Navigate to the Monitoring tab during the VM creation to view it.
Use this feature to troubleshoot boot failures for custom or platform images. Boot diagnostics with managed storage account significantly improves creation time of Virtual machines by using pre-provisioned storage accounts managed by Microsoft. Learn more
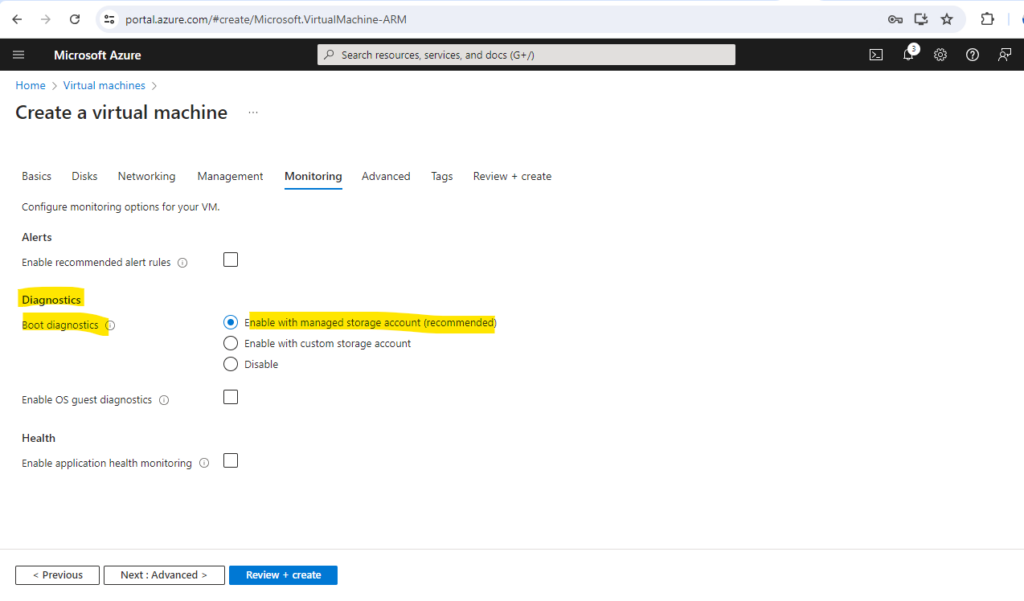
Enable Boot Diagnostics using Azure CLI
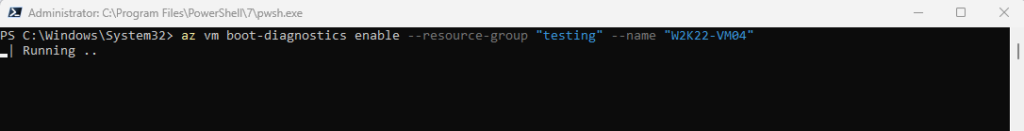
We can also enable or disable boot diagnostics and the serial console by using the Azure CLI and the following cmdlet.
az vm boot-diagnostics enable --resource-group "testing" --name "W2K22-VM04"
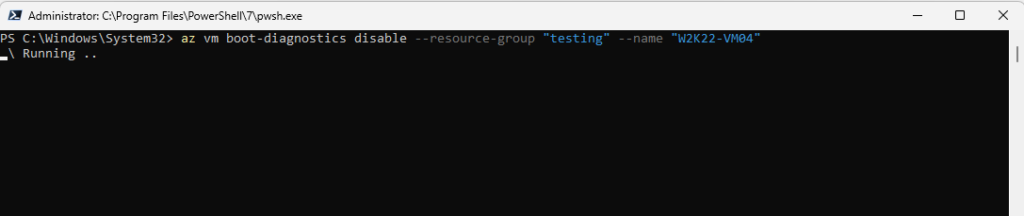
To disable boot diagnostics we can run the following cmdlet.
az vm boot-diagnostics disable --resource-group "testing" --name "W2K22-VM04"
Enable Serial Console functionality for Windows Server lower than
Further Emergency Management Services (EMS) must be enabled on Windows in order to access the Special Administration Console (SAC).
Newer Windows Server images on Azure have Special Administration Console (SAC) enabled by default. SAC is supported on server versions of Windows but isn’t available on client versions (for example, Windows 10, Windows 8, or Windows 7).
For older Windows Server images (created before February 2018), you can automatically enable the serial console through the Azure portal’s run command feature. In the Azure portal, select Run command, then select the command named EnableEMS from the list.
bcdedit /ems '{current}' on
bcdedit /emssettings EMSPORT:1 EMSBAUDRATE:115200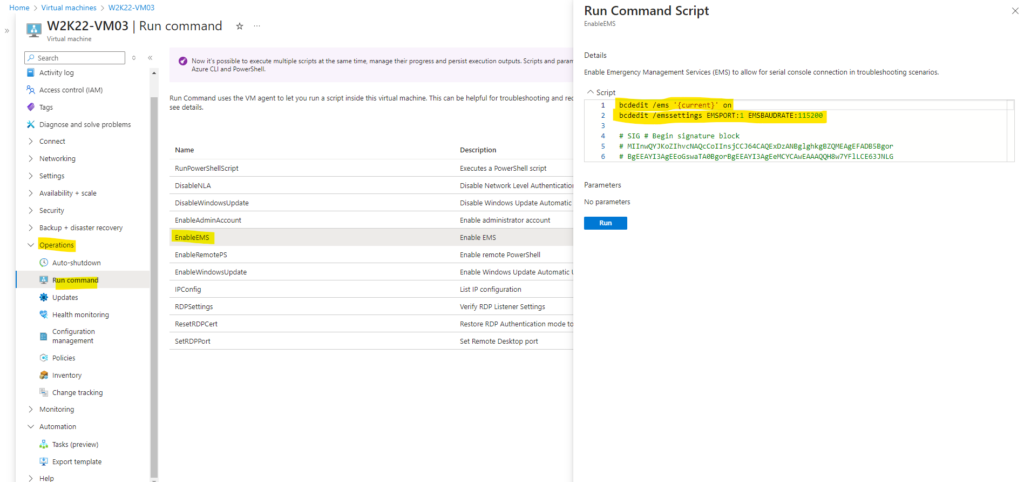
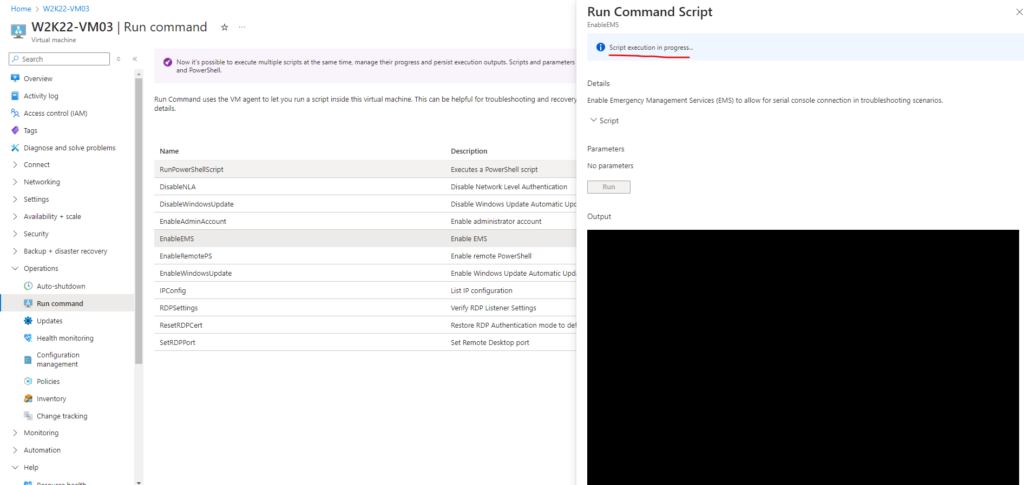
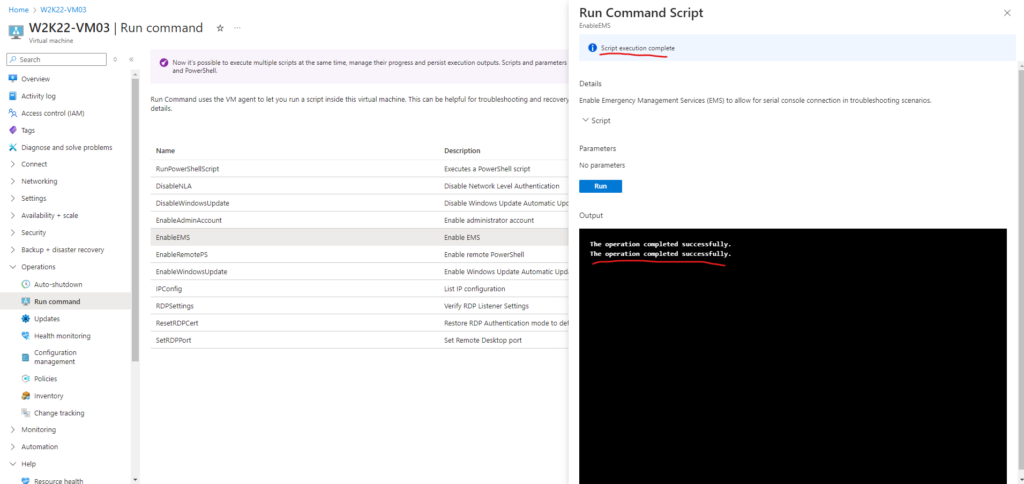
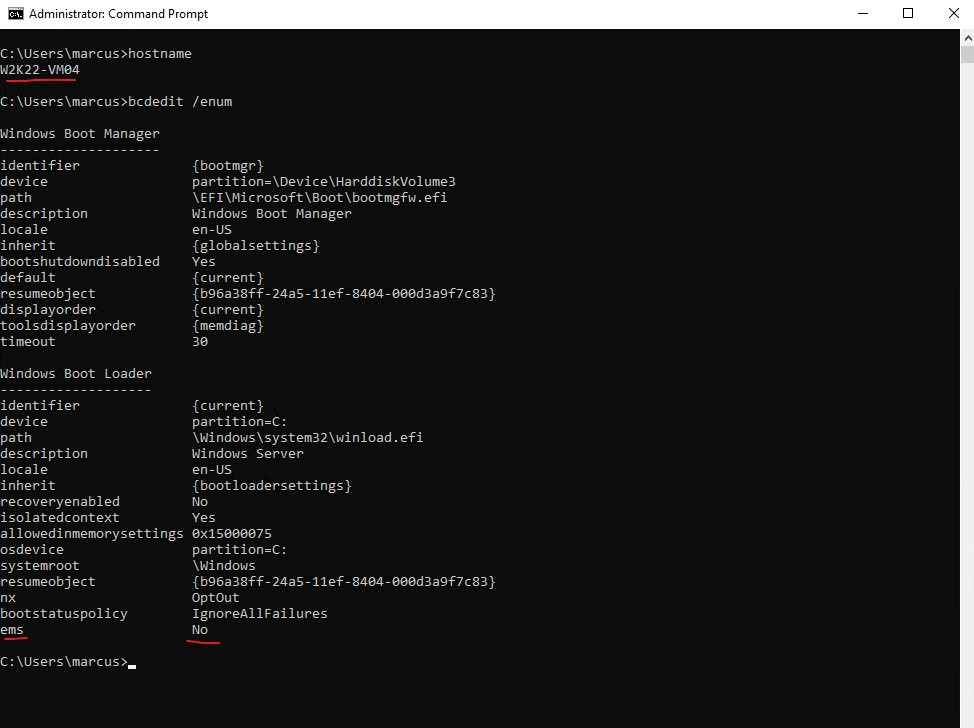
The same we can of course also perform when we logged in to a Windows computer by using the CMD as shown below. To check the status you can run bcdedit /enum.
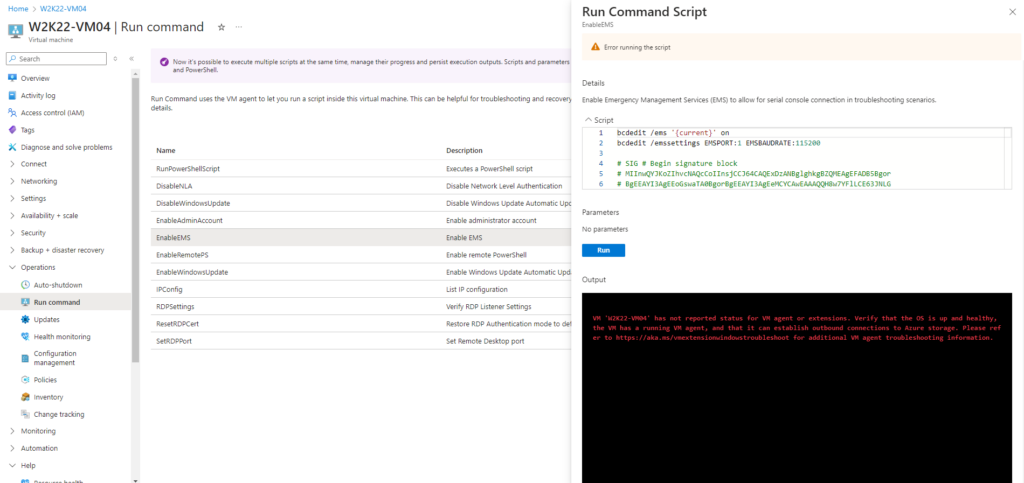
In case you have already rebooted the VM in safe mode and so far not enabled EMS, you can’t enable the Emergency Management Services (EMS) and its Special Administration Console (SAC) anymore online by using the run commands.
In that case you will run into the following error below and the only way to exit safe mode again is by repairing the VM offline as shown in my following post.
Disable Emergency Management Services (EMS)
To disable the Emergency Management Services (EMS) and its Special Administration Console (SAC) on Windows we can use the following command within the CMD or PowerShell when directly logged on to the computer.
bcdedit /ems off
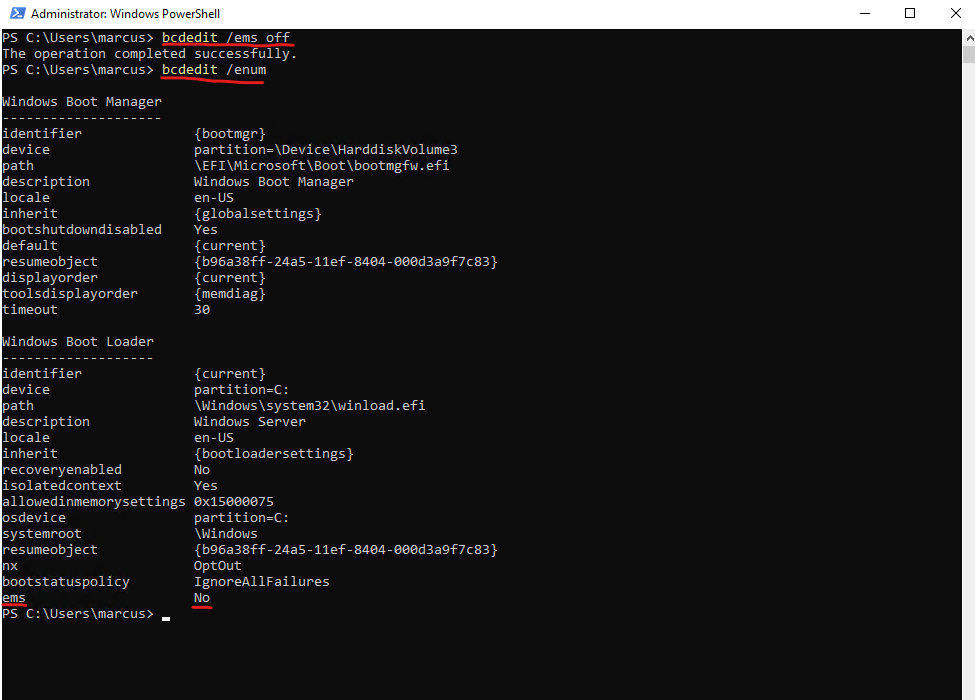
After rebooting the virtual machine we still can access the serial console but from now on not the Special Administration Console (SAC) anymore.
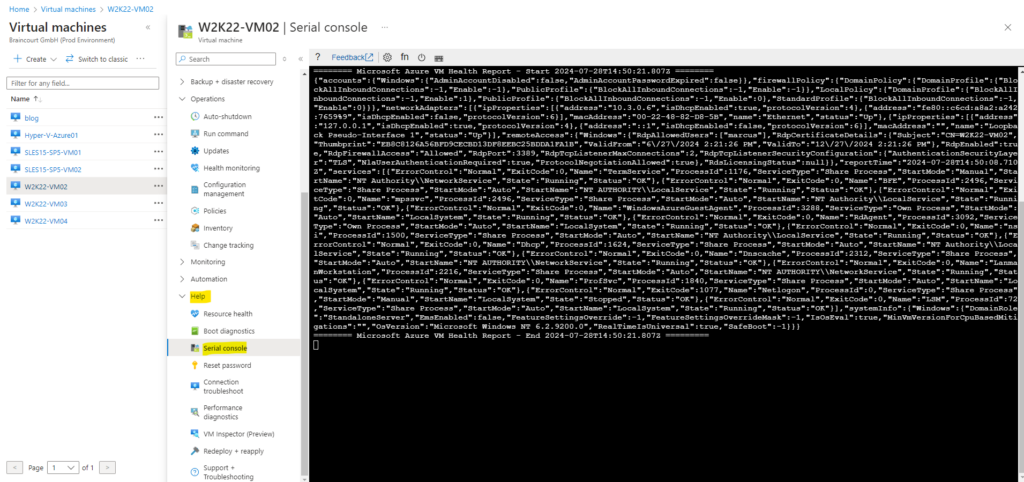
We can also use the Azure portal and the virtual machine blade and fire up a run command as shown below.
Operations -> Run command
bcdedit /ems off
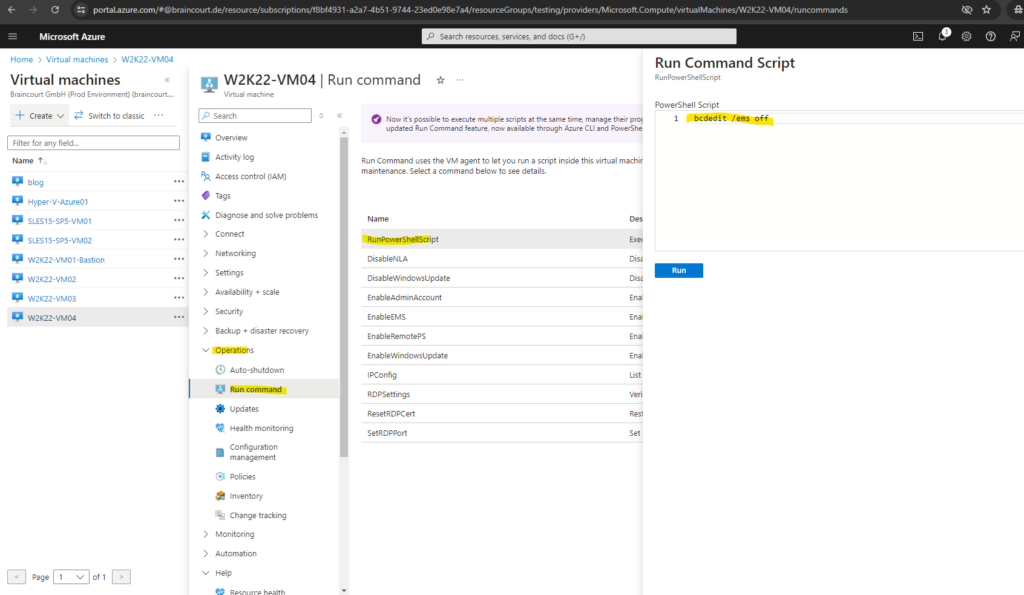
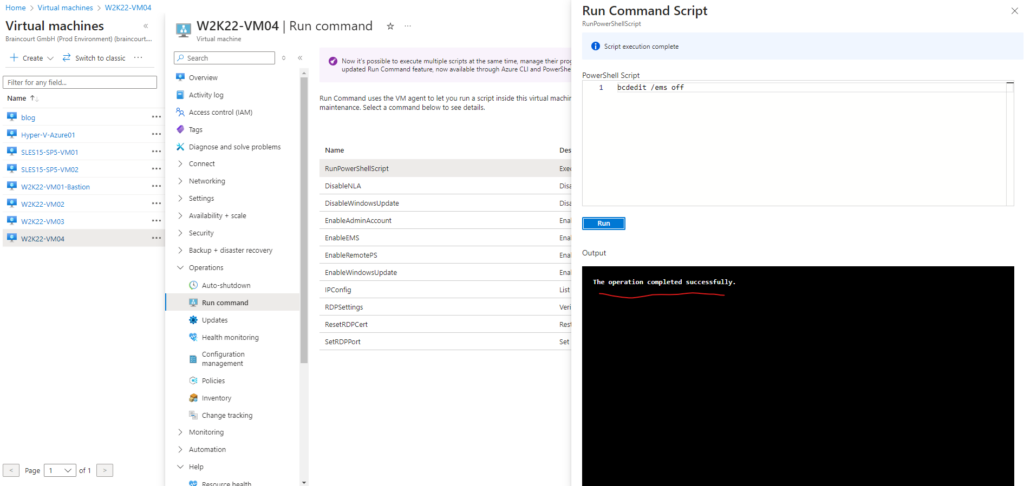
Emergency Management Services (EMS) is also disabled successfully.
About how to access the SAC on GCP virtual machines you can read my following post.
About how to access the SAC on VMware vSphere virtual machines you can read my following post.
Links
Cannot RDP to a VM because the VM boots into Safe Mode
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/troubleshoot-rdp-safe-modeBCDEdit Options Reference
https://learn.microsoft.com/en-us/windows-hardware/drivers/devtest/bcd-boot-options-referenceBCDEdit Command-Line Options
https://learn.microsoft.com/en-us/windows-hardware/manufacture/desktop/bcdedit-command-line-options?view=windows-11Azure Serial Console
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/serial-console-overviewAzure Serial Console for Windows
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/serial-console-windowsAzure Serial Console for Linux
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/linux/serial-console-linuxSpecial Administration Console (SAC)
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/cc787940(v=ws.10)Common scenarios for accessing the serial console
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/serial-console-windows#common-scenarios-for-accessing-the-serial-consoleRunning Remote Commands
https://learn.microsoft.com/en-us/powershell/scripting/security/remoting/running-remote-commands?view=powershell-7.4Azure boot diagnostics
https://learn.microsoft.com/en-us/azure/virtual-machines/boot-diagnosticsExit safe mode remotely
https://serverfault.com/questions/1092450/exit-safe-mode-remotelyAccess Serial Console for Virtual Machine Scale Sets via Azure portal
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/serial-console-overview#access-serial-console-for-virtual-machine-scale-sets-via-azure-portalWindows Commands – CMD and PowerShell
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/serial-console-cmd-ps-commands
Tags In
Related Posts
Latest posts
Mastering Nested Junction Paths: Qtrees and Export Policies in NetApp Cloud Volumes ONTAP (CVO)
Follow me on LinkedIn


