Mastering Azure Managed Identities
Managing credentials securely is a crucial aspect of building applications in the cloud. Azure Managed Identities simplify this process by providing an automatically managed identity for workloads running in Azure, enabling seamless authentication to Azure services without the need for storing or managing secrets.
Managed identities are not designed for authenticating to services outside the Azure ecosystem, such as third-party APIs, on-premises systems, or services running on other cloud platforms like AWS or Google Cloud.
For applications/scripts running outside the Azure tenant and needing to authenticate to Entra ID, we can use service principals and shown in my following post.
In this post, we will see how to create and use Azure Managed Identities to access Azure services.
I can also recommend to watch John Savill’s Deep Dive about Microsoft Azure Managed Identity shown here https://www.youtube.com/watch?v=rC1TV0_sIrM.
Further you can also read my following post about Azure Service Principals.
- Basics about using Managed Identities to access Azure Resources
- Azure services and resource types that supporting using managed identities
- What are managed identities for Azure resources?
- Create a Managed Identity
- Assign a Managed Identity to a Resource
- Authenticate to Azure Resources by using these Managed Identities
- Troubleshooting
- Links
Basics about using Managed Identities to access Azure Resources
An Azure resource like for example a virtual machine can have multiple user managed Identities.
In contrast it can only have one system assigned managed identity.
Further a resource can also have a system assigned managed identity plus a user assigned managed identity or multiple.
When the source resource like a virtual machine wants to connect to another resource (destination), e.g. a storage account, it can specify the manged identity which should be used to access the resource (e.g storage account).
When you don’t specify a manged identity to use:
- If the source resource has a system assigned managed identity, it will always by default use this identity to connect to the destination resource, also in case one or multiple user assigned managed identities are assigned to.
- If the source resource doesn’t have a system assigned managed identity but one user assigned managed identity, it will use by default this identity to connect to the destination resource.
- If the source resource doesn’t have a system assigned managed identity but multiple user assigned managed identities, we need to specify which user assigned managed identity should be used to connect to the destination resource.
When using a system assigned managed identity and when using a user assigned managed identity?
A system assigned managed identity is tightly coupled to a single Azure resource. When you enable it on a resource (like a VM, App Service, or Function App).
The lifecycle of the identity is tied to the resource. If the resource is deleted, the identity is also deleted automatically.
A user assigned managed identity is a standalone resource in Azure that you can create once and assign to multiple Azure resources as needed. Its lifecycle is independent of the resources that use it.
When you need the same identity across multiple resources (e.g., multiple VMs or apps connecting to the same Key Vault).
Azure services and resource types that supporting using managed identities
You will find a list in the following article by Microsoft https://learn.microsoft.com/en-us/entra/identity/managed-identities-azure-resources/managed-identities-status.
What are managed identities for Azure resources?
At a high level, there are two types of identities: human and machine/non-human identities.
Machine / non-human identities consist of device and workload identities. In Microsoft Entra, workload identities are applications, service principals, and managed identities. For more information on workload identities, see workload identities.
A managed identity is an identity that can be assigned to an Azure compute resource (Virtual Machine (VM), Virtual Machine Scale Set (VMSS), Service Fabric Cluster, Azure Kubernetes cluster) or any App hosting platform supported by Azure.
Once a managed identity is assigned on the compute resource, it can be authorized, directly or indirectly, to access downstream dependency resources, such as a storage account, SQL database, CosmosDB, and so on.
Managed identity replaces secrets such as access keys or passwords. In addition, managed identities can replace certificates or other forms of authentication for service-to-service dependencies.
Here are some of the benefits of using managed identities:
- You don’t need to manage credentials. Credentials aren’t even accessible to you.
- You can use managed identities to authenticate to any resource that supports Microsoft Entra authentication, including your own applications.
- Managed identities can be used at no extra cost.
Source: https://learn.microsoft.com/en-us/entra/identity/managed-identities-azure-resources/overview
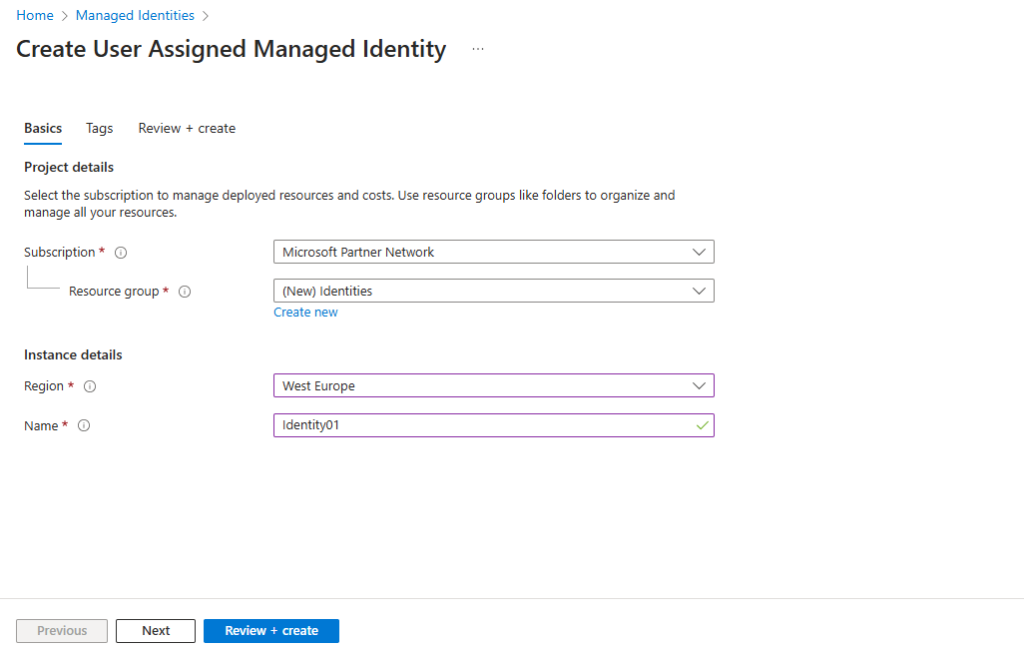
Create a Managed Identity
To create a user-assigned managed identity, your account needs the Managed Identity Contributor role assignment.
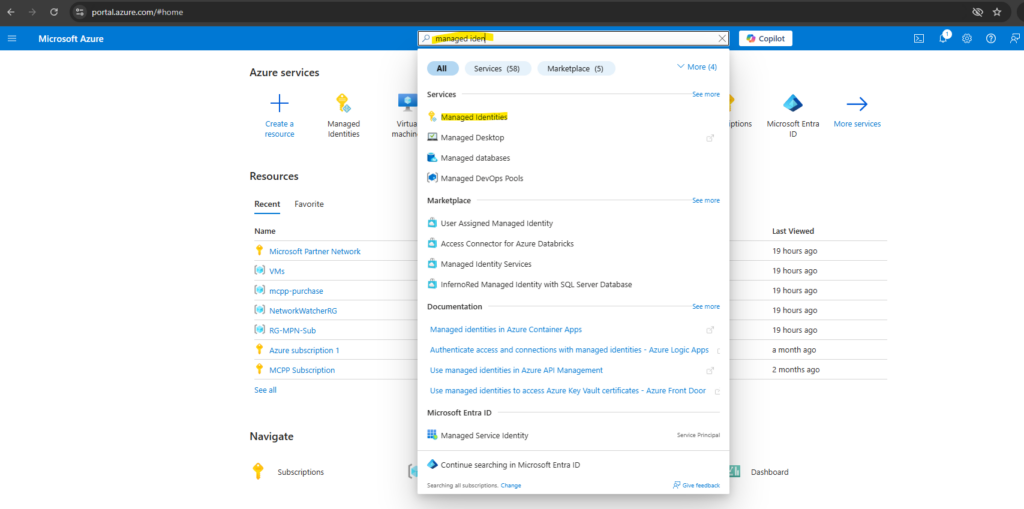
In the search box, enter Managed Identities. Under Services, select Managed Identities.
To list or read a user-assigned managed identity, your account needs to have either Managed Identity Operator or Managed Identity Contributor role assignments.
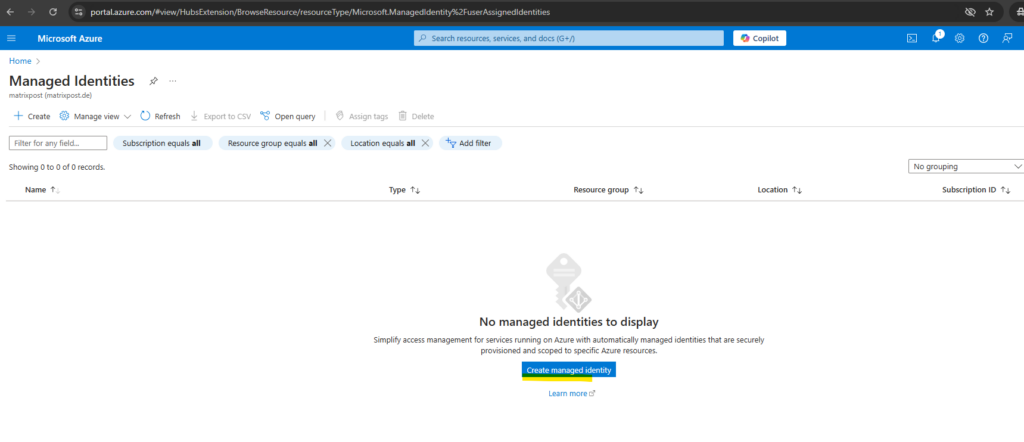
In the search box, enter Managed Identities. Under Services, select Managed Identities.
A list of the user-assigned managed identities for your subscription is returned. To see the details of a user-assigned managed identity, select its name.
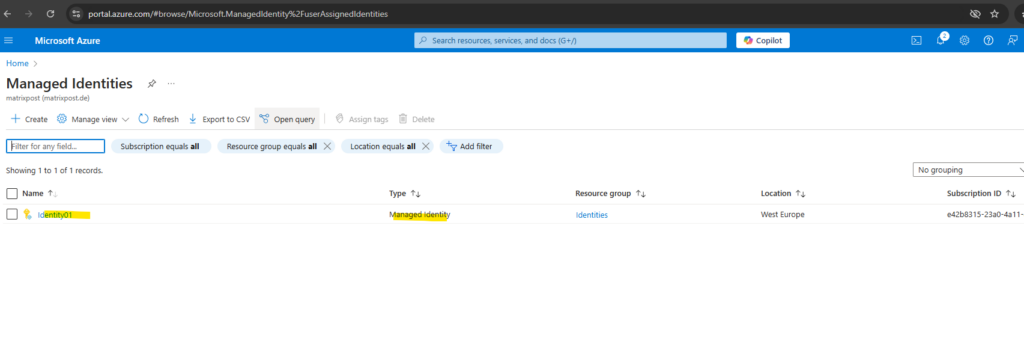
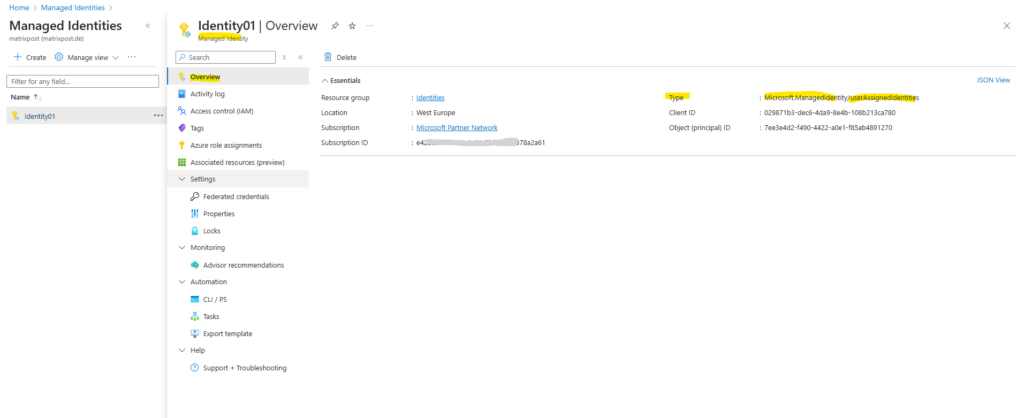
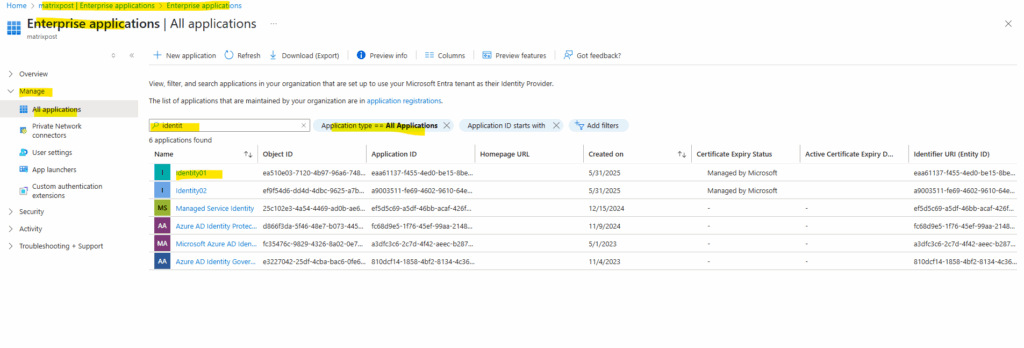
Because a managed identity is a special type of service principal, we can also find our newly created managed identity in Entra ID under Manage -> Enterprise applications -> All Applications as shown below.
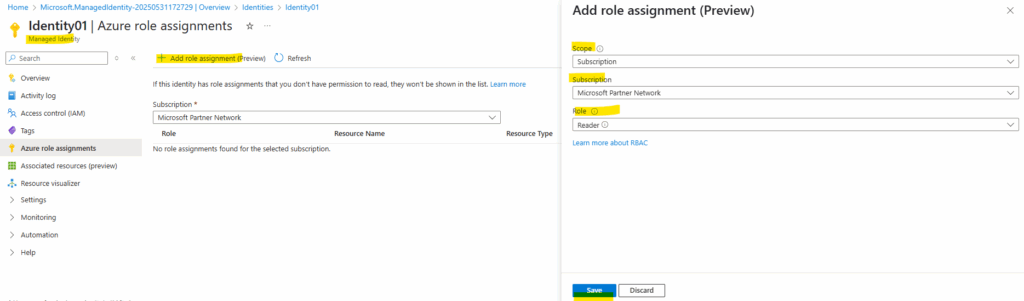
We can now assign permissions and Azure roles as usual like for service principals and user accounts.
Here for example I will assign the reader role for a subscription to the managed identity.
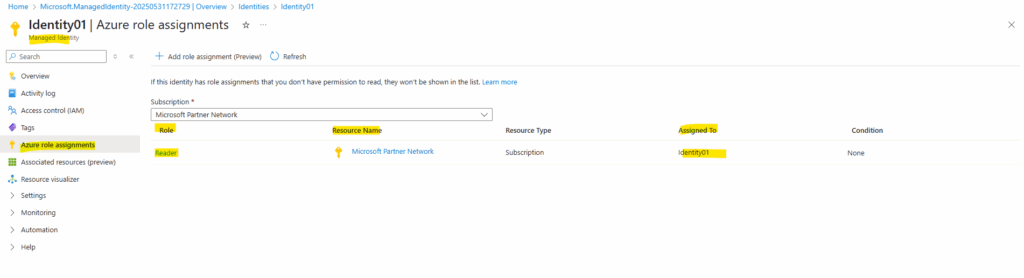
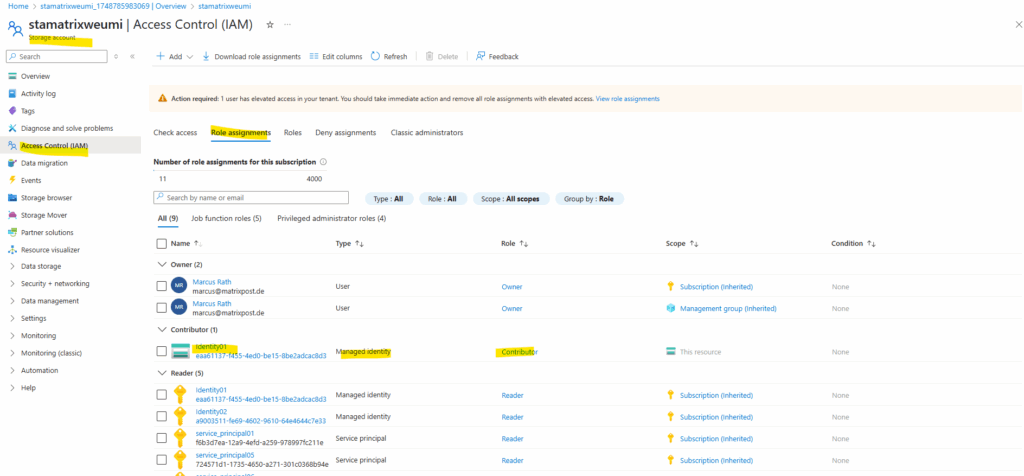
Also I will assign permissions for the managed identity on a resource like a storage account below.
I will assign here the contributor role. As we can see also below, all resources within the subscription we assigned previously the reader role, will inherit this permissions to the resources.
Assign a Managed Identity to a Resource
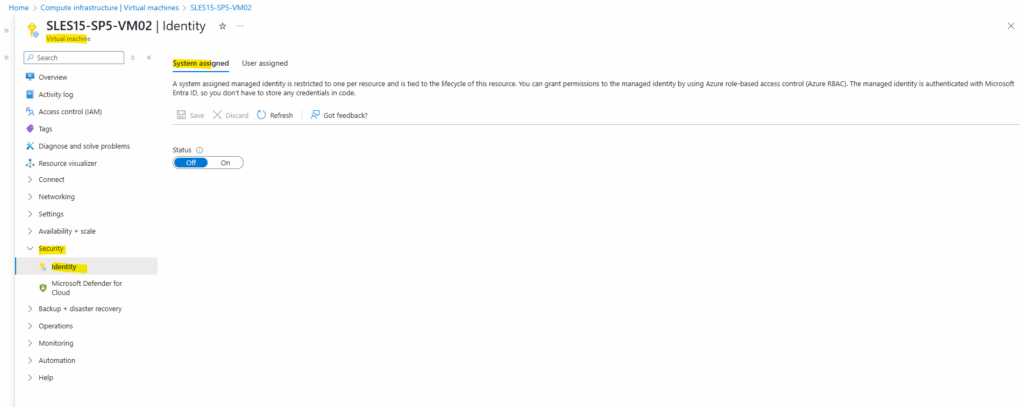
For a virtual machine we can assign the managed identities under Security -> Identity.
Here we have a tab for the system assigned and for the user assigned.
First I will enable the system assigned managed identity. Here we just need to toggle it on.
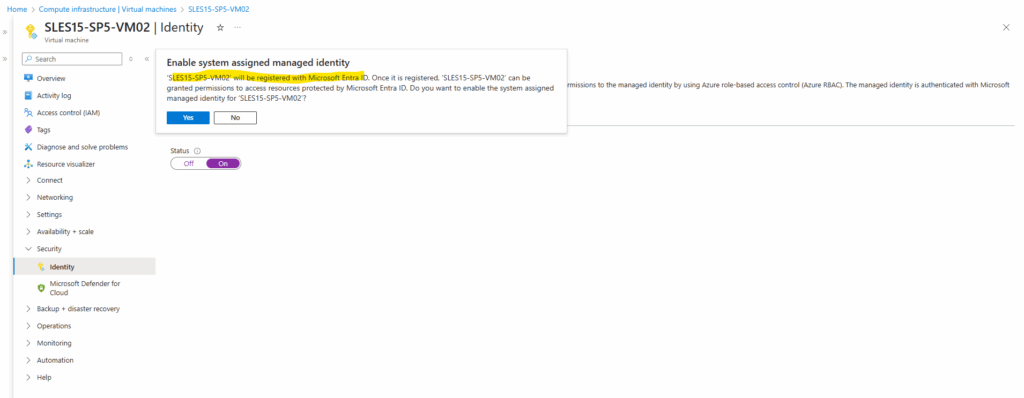
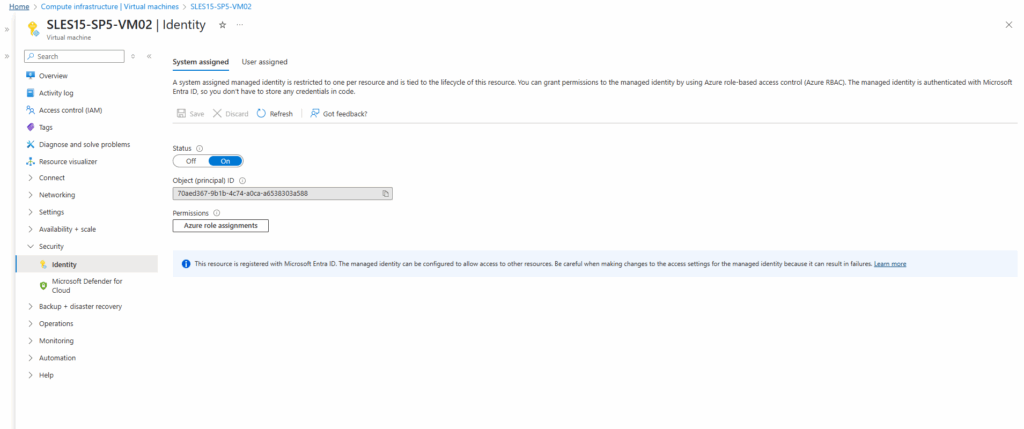
After the VM is registered with its system managed identity in Entra ID, we can also assign permissions to on e.g. a storage account.
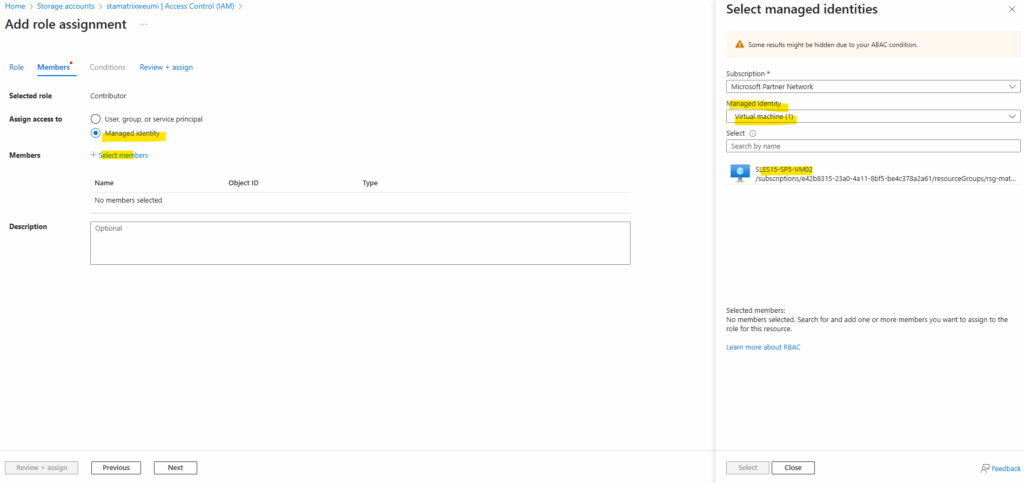
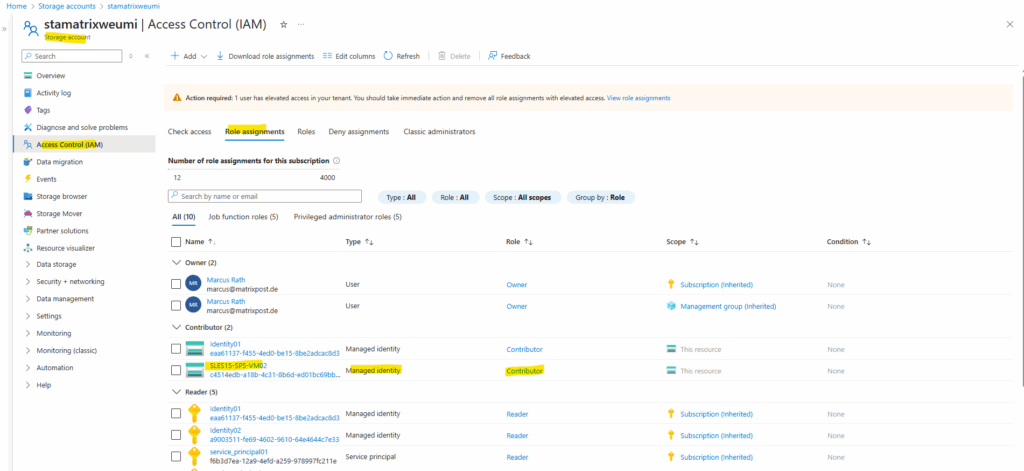
Back on the virtual machine, on the user assigned tab we can add and assign our created user managed identities to the virtual machine.
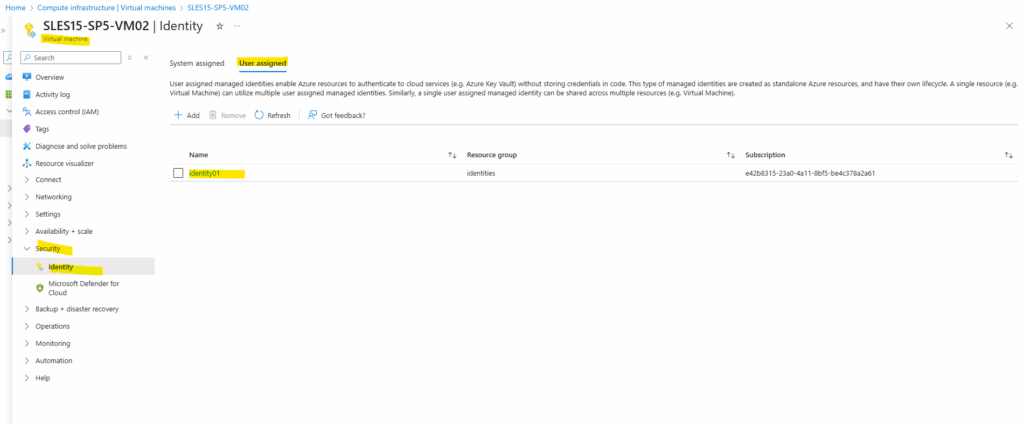
Authenticate to Azure Resources by using these Managed Identities
Below I will demonstrate accessing a resource (storage account) from a virtual machine by using these managed identities.
First by using the Azure CLI on the virtual machine and then by using Azure PowerShell.
Sign in by using Azure CLI
About how to install Azure CLI on Linux you can read my following post.
By using a System assigned Identity
To sign in with a system assigned identity we can use the following command. By just using the -Identity flag below by default the system assigned identity is used to authenticate to Entra ID.
To get the current account info like the Get-AzContext command in Azure PowerShell, we can run.
# az account show
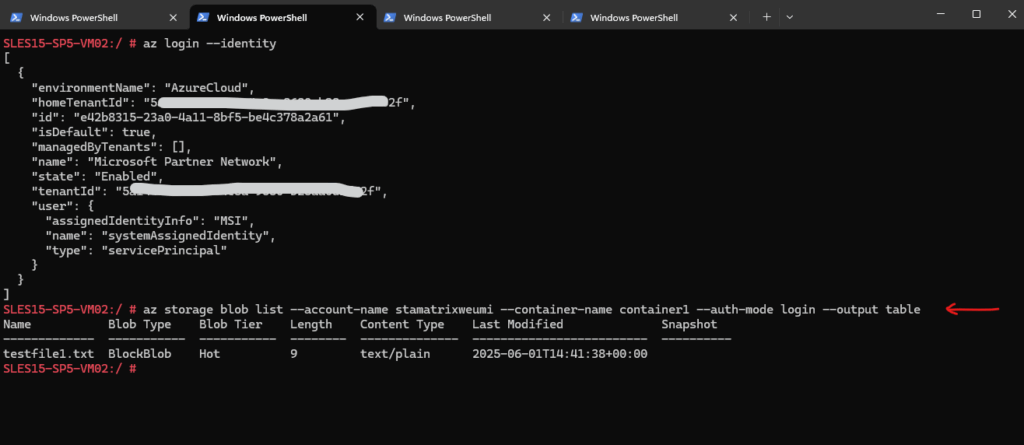
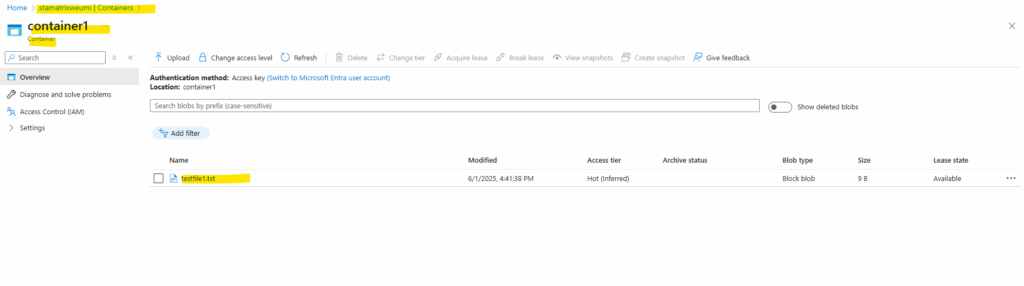
Next I will try to access the storage account and download a blob file from a container.
First I will list the storage account’s blobs.
# az storage blob list --account-name stamatrixweumi --container-name container1 --auth-mode login --output table
Use the az storage blob download command to download the blob.
# az storage blob download --account-name stamatrixweumi --container-name container1 --name testfile1.txt --file /testing/testfile1.txt --auth-mode login
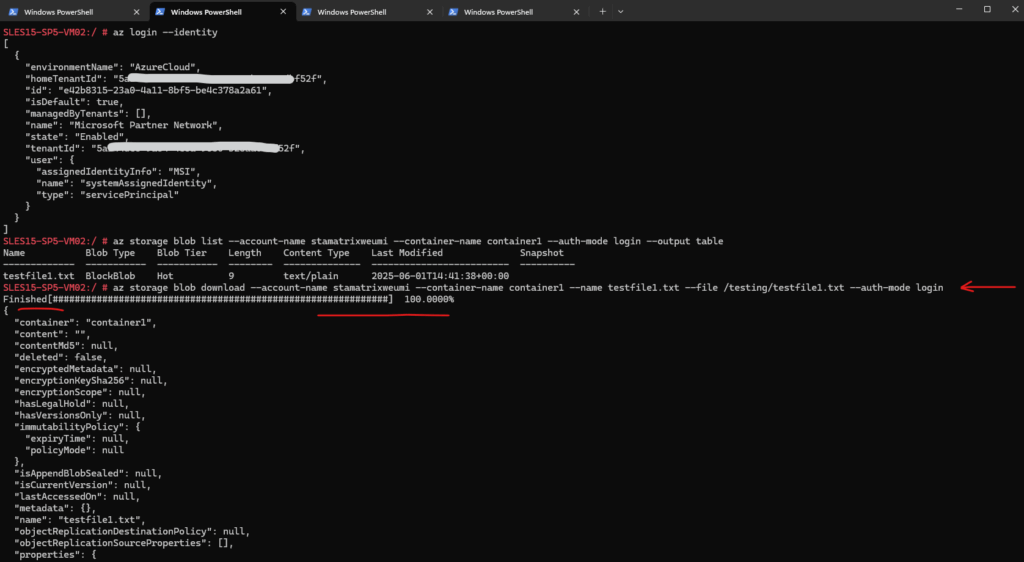
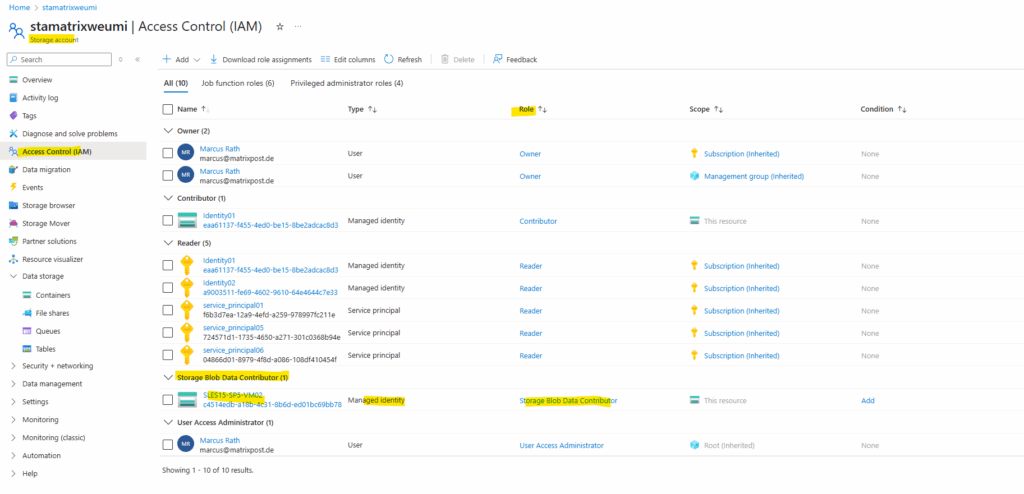
To access the storage account and its blob storage, I was assigning the Storage Blob Data Contributor role to the system assigned identity of the virtual machine.
By using a User assigned Identity
To sign in with a user assigned identity we can use the following command. Here in addition to the -Identity flag we also use the -username flag to set the user assigned identity we want to use to authenticate to Entra ID.
# az login --identity --username <user-assigned-managed-identity-client-id>
Accessing the storage account, list the files and download it is finally the same as previously when using the system assigned identity.

Sign in by using Azure PowerShell
About how to install PowerShell and Azure PowerShell (Az Modules) on Linux you can read my following post.
By using a System assigned Identity
To sign in with a system assigned identity we can use the following command. By just using the -Identity flag below by default the system assigned identity is used to authenticate to Entra ID.
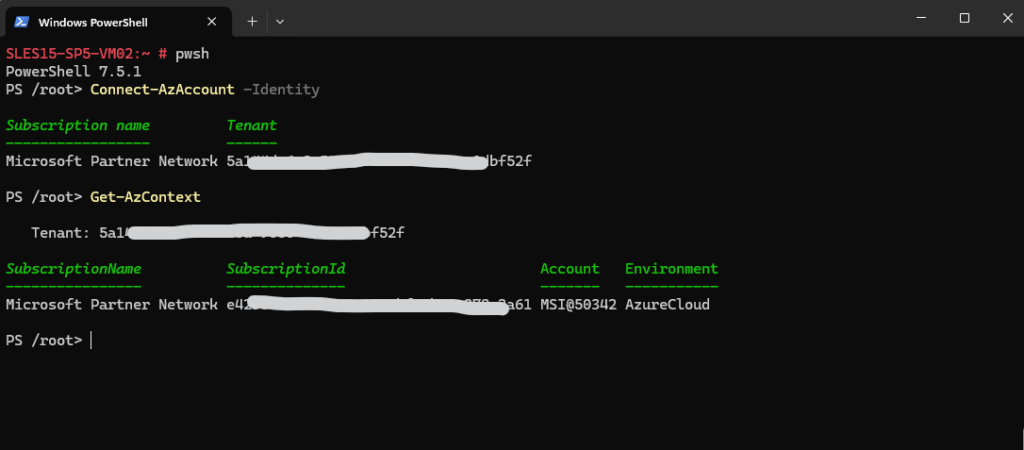
PS> Connect-AzAccount -Identity PS> Get-AzContext
The Get-AzContext cmdlet in Azure PowerShell is used to display the current active Azure context. This context includes details such as: The current subscription, The current account used for authentication, The tenant (directory) information, The environment (e.g., AzureCloud)
When using system assigned identity, the Get-AzContext command will show for the Account always MSI@50342.
Next I will try to access the storage account and download a blob file from a container.
PS> $storagecontext = New-AzStorageContext -StorageAccountName 'stamatrixweumi' -UseConnectedAccount PS> Get-AzStorageBlobContent -Container 'container1' -Blob 'testfile1.txt' -Destination "/testing/" -Context $storagecontext
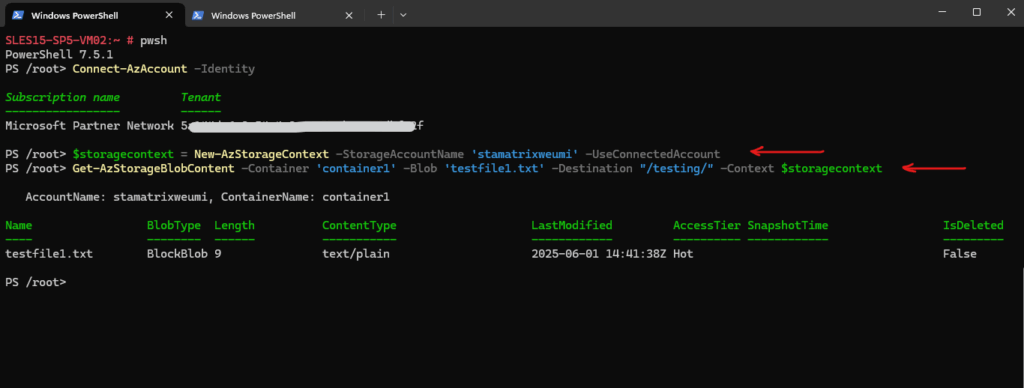
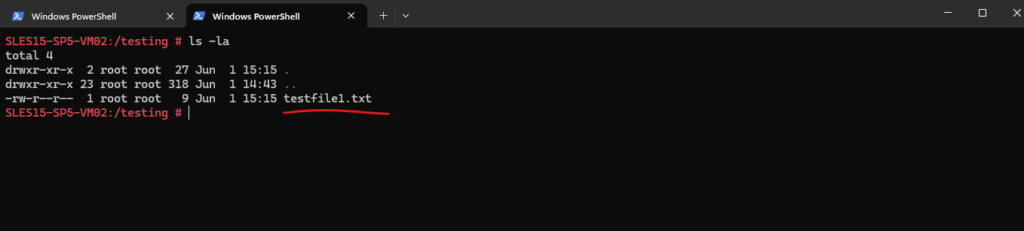
To access the storage account and its blob storage, I was assigning the Storage Blob Data Contributor role to the system assigned identity of the virtual machine.


By using a User assigned Identity
To sign in with a user assigned identity we can use the following command. Here in addition to the -Identity flag we also use the -AccountId flag to set the user assigned identity we want to use to authenticate to Entra ID.
In case the virtual machine has just a user assigned identity and no system assigned, we can also use just the -Identity flag.
PS> Connect-AzAccount -Identity -AccountId <client-id-of-user-assigned-managed-identity>
For the Account when executing the Get-AzContext command, this time we can see the service principal ID of the user assigned identity.
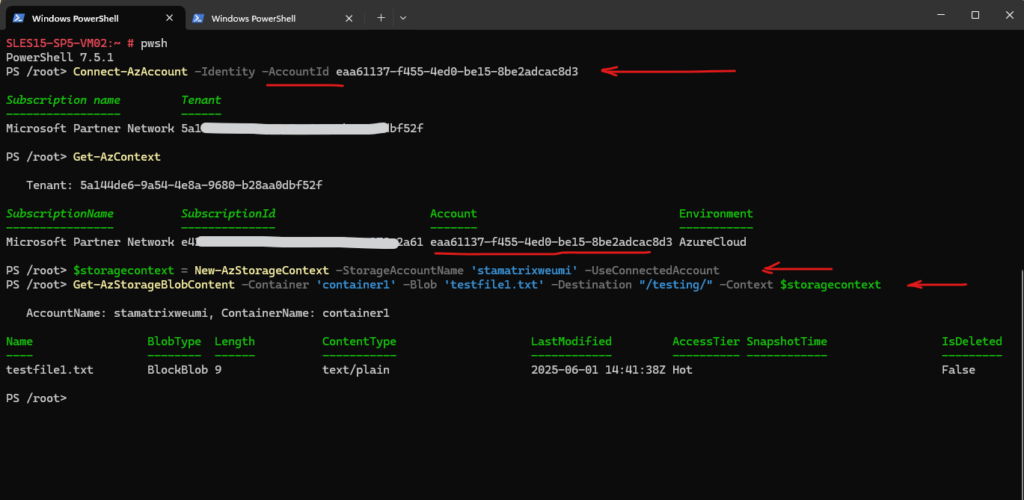
Troubleshooting
WARNING: Unable to acquire token for tenant ‘organizations’ with error ‘ManagedIdentityCredential authentication unavailable. Multiple attempts
failed to obtain a token from the managed identity endpoint.’
The -Identity parameter uses the Azure Instance Metadata Service (IMDS) at http://169.254.169.254 to request tokens.
This means the command must run from within the resource that has the Managed Identity enabled (e.g., inside an Azure VM, Function, App Service).
If you’re running this command locally or from a non-Azure machine, it will not work and you will run into this error.
Further when the virtual machine is running in Azure but you will using here for the AccountId parameter the Client ID of a managed identity which is so far not assigned to the virtual machine, you will also run into this errro.
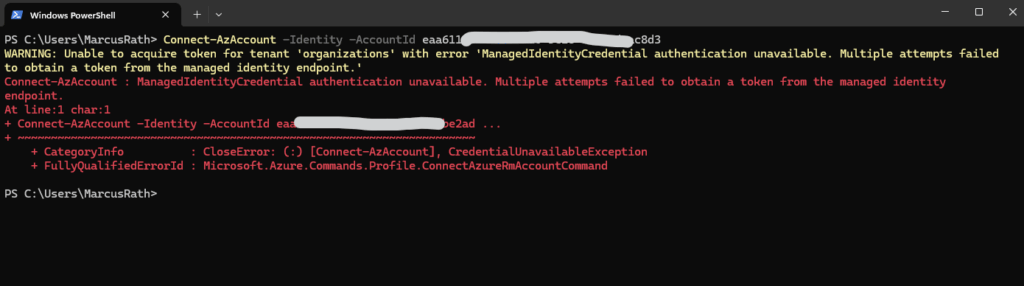
The resource must reach the metadata service at 169.254.169.254. No firewall rules or custom routes should block this access. In some cases, a custom NAT gateway or network settings may break access to IMDS.
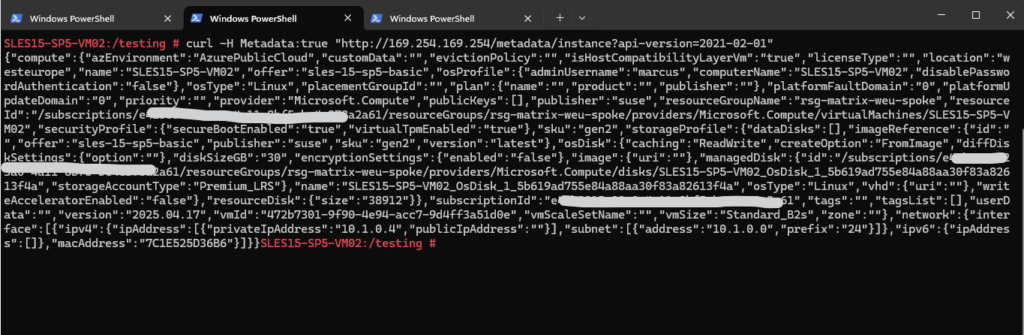
Test it on the resource:
> curl -H Metadata:true "http://169.254.169.254/metadata/instance?api-version=2021-02-01"
You should see instance metadata in JSON format like below.
Links
Azure services and resource types supporting managed identities
https://learn.microsoft.com/en-us/entra/identity/managed-identities-azure-resources/managed-identities-statusMicrosoft Azure Managed Identity Deep Dive (John Savill)
https://www.youtube.com/watch?v=rC1TV0_sIrMHow to use managed identities for Azure resources on an Azure VM to acquire an access token
https://learn.microsoft.com/en-us/entra/identity/managed-identities-azure-resources/how-to-use-vm-tokenHow managed identities for Azure resources work with Azure virtual machines
https://learn.microsoft.com/en-us/entra/identity/managed-identities-azure-resources/how-managed-identities-work-vm
Tags In
Related Posts
Follow me on LinkedIn


