Mastering Azure Update Manager – Part 1
Today we will see how we can onboard machines to Azure Update Manger, a comprehensive, cloud-native service provided by Microsoft Azure to manage patching and updating operating systems across virtual machines (VMs) and physical servers in a centralized manner.
It automates the discovery, deployment, and monitoring of updates for both, Windows and Linux systems, ensuring that machines remain secure and up-to-date with the latest patches.
As John Savill already mentioned in his great video about Azure Update Manager, patching is not the most exciting technology but it is critical.
By leveraging Azure Update Manager, organizations can maintain compliance, minimize security risks, and reduce downtime through automated or manual scheduling of updates, all within the Azure ecosystem or across hybrid and multi-cloud environments.
This service simplifies the complex process of update management and provides visibility into patching compliance through detailed reports and dashboards.
This part will cover how to update machines on a per machine level by using the Update Settings or just on demand. This is fine for a small number of machines we want to manage by Azure Update Manager.
In Part 2 we will see how we can onboard machines at scale to Azure Update Manager by using Azure Policy. Further we will see how we can create pre and post events for the update process.
In Part 3 I will focus on how to updating SUSE Linux Enterprise by using the Azure Update Manager.
In Part 4 will see how to get notified about patch installation states (like e.g. Succeeded or Failed) per email by using Azure Monitor alerts. Further we will see how to use the Azure Resource Graph Explorer to manually trigger custom queries for Azure Update Manager to see patching results.
Version 1 vs. Edition 2023 and later
Version 1 (aka Azure Automation Update Management)
Azure Update Manger version 1 was build on Log Analytics Work Space and using Azure Automation (Hybrid Runbook Worker). No Azure-Arc was required.
- just basic scheduling available
- no granular RBAC roles
The Azure Log Analytics agent, also known as the Microsoft Monitoring Agent (MMA) will be retired in August 2024. Azure Automation Update management solution relies on this agent and might encounter issues once the agent is retired. It doesn’t work with Azure Monitoring Agent (AMA) either.
Therefore, if you’re using Azure Automation Update management solution, you’re encouraged to move to Azure Update Manager for their software update needs. All capabilities of Azure Automation Update Management Solution will be available on Azure Update Manager before the retirement date. Follow the guidance to move update management for your machines to Azure Update Manager.
Edition 2023 and later
Azure Update Manger version 2 is based on the Azure Resource Graph instead of Log Analytics Work Space and Azure Automation.
Because here no Azure Automation and Hybrid Runbook Worker is used, version 2 is extension based. For Azure VMs we can use natively these extensions. For other machines than Azure VMs we need Azure-Arc enabled Server OS.
Azure-Arc basically is free when not using the separate additional capabilities for which we need to pay like Defender for Cloud for Azure-Arc enabled machines.
Edition 2023 and later supports:
- rich scheduling
- VM-Level RBAC
Source: https://www.youtube.com/watch?v=LVmNh5YgBOQ
Prerequisites
For Windows machines, you must allow traffic to any endpoints required by the Windows Update agent.
You can find an updated list of required endpoints in issues related to HTTP Proxy. If you have a local WSUS deployment, you must allow traffic to the server specified in your WSUS key.
Windows Update uses WinHttp with Partial Range requests (RFC 7233) to download updates and applications from Windows Update servers or on-premises WSUS servers. Therefore proxy servers on the network must support HTTP RANGE requests. If a proxy was configured in Internet Explorer (User level) but not in WinHTTP (System level), connections to Windows Update will fail.
Ensure that devices can reach necessary Windows Update endpoints through the firewall. For example, for Windows 10, version 2004, the following protocols must be able to reach these respective endpoints:
| Protocol | Endpoint URL |
|---|---|
| TLS 1.2 | *.prod.do.dsp.mp.microsoft.com |
| HTTP | emdl.ws.microsoft.com |
| HTTP | *.dl.delivery.mp.microsoft.com |
| HTTP | *.windowsupdate.com |
| HTTPS | *.delivery.mp.microsoft.com |
| TLS 1.2 | *.update.microsoft.com |
| TLS 1.2 | tsfe.trafficshaping.dsp.mp.microsoft.com |
Source: https://learn.microsoft.com/en-us/azure/update-manager/prerequisites
FQDN tags overview
For example, to manually allow Windows Update network traffic through your firewall, you need to create multiple application rules per the Microsoft documentation. Using FQDN tags, you can create an application rule, include the Windows Updates tag, and now network traffic to Microsoft Windows Update endpoints can flow through your firewall.
Source: https://learn.microsoft.com/en-us/azure/firewall/fqdn-tags
For SUSE Linux Enterprise Server updates you will find in Part 3 more about the required endpoints the machine needs to allow traffic to.
Determined Endpoints by using HTTP Proxy Logs
In case you want to test the connection to the required endpoints mentioned above, I was capturing the full FQDNs by using a HTTP proxy.
We can test connectivity by using telnet, Test-NetConnection or just its shortcut tnc.
PS> tnc -ComputerName download.windowsupdate.com -Port 80
Traffic used by Azure Update Manager Assessment
v10.events.data.microsoft.com:443 ==> The domain v10.events.data.microsoft.com is associated with Microsoft's telemetry and event logging services. The domain is also used in conjunction with Windows Update and other Microsoft services for tracking updates, patches, and ensuring the system is running the latest security and feature updates. fe2cr.update.microsoft.com:443 ==> The domain fe2cr.update.microsoft.com is associated with Microsoft's update infrastructure, specifically for delivering updates related to the Windows operating system and other Microsoft products. fe3cr.delivery.mp.microsoft.com:443 ==> The domain fe3cr.delivery.mp.microsoft.com is associated with Microsoft's Delivery Optimization service and is primarily used for delivering Windows updates and Microsoft Store app updates across multiple devices in a more efficient way.
Traffic used by Azure Update Manager running Update
fe2cr.update.microsoft.com:443 v10.events.data.microsoft.com:443 fe3cr.delivery.mp.microsoft.com:443 geo.prod.do.dsp.mp.microsoft.com:443 ==> The domain geo.prod.do.dsp.mp.microsoft.com is part of Microsoft's Delivery Optimization (DO) service infrastructure, which is responsible for delivering Windows updates and app updates in an efficient manner, often using peer-to-peer (P2P) sharing to reduce the load on Microsoft's servers and improve update speeds, especially in large networks. download.windowsupdate.com:80 ==> The domain download.windowsupdate.com is associated with Microsoft's Windows Update service, specifically for downloading Windows updates and patches. This domain is one of the primary locations from which your system retrieves updates such as security patches, feature updates, driver updates, and other critical updates for the Windows operating system. au.download.windowsupdate.com:80 ==> The domain au.download.windowsupdate.com is another domain associated with Microsoft's Windows Update service. Specifically, it plays a role in downloading Windows operating system updates from Microsoft's servers. Automatic Delivery of Updates: au.download.windowsupdate.com handles the background download of updates. Once Windows Update detects that new updates are available, the system uses this domain to retrieve the update files automatically. cp601.prod.do.dsp.mp.microsoft.com:443 kv601.prod.do.dsp.mp.microsoft.com:443
Traffic used by Azure Update Manager Assessment for Azure Arc enabled VMs
slscr.update.microsoft.com:443 v10.events.data.microsoft.com:443 download.windowsupdate.com:80
Traffic used by Azure Update Manager Updates for Azure Arc enabled VMs
v10.events.data.microsoft.com:443 geo.prod.do.dsp.mp.microsoft.com:443 download.windowsupdate.com:80 au.download.windowsupdate.com:80 settings-win.data.microsoft.com:443 ==> The domain settings-win.data.microsoft.com is part of Microsoft's data collection and telemetry infrastructure. It is used by Windows operating systems to send diagnostic and usage data to Microsoft in order to improve the product, troubleshoot issues, and enhance performance. kv801.prod.do.dsp.mp.microsoft.com:443 cp801.prod.do.dsp.mp.microsoft.com:443 v20.events.data.microsoft.com:443 www.msftconnecttest.com:80 ==> The domain www.msftconnecttest.com is part of Microsoft's Network Connectivity Status Indicator (NCSI) infrastructure. It is used to test and verify internet connectivity on Windows devices.
Monitoring
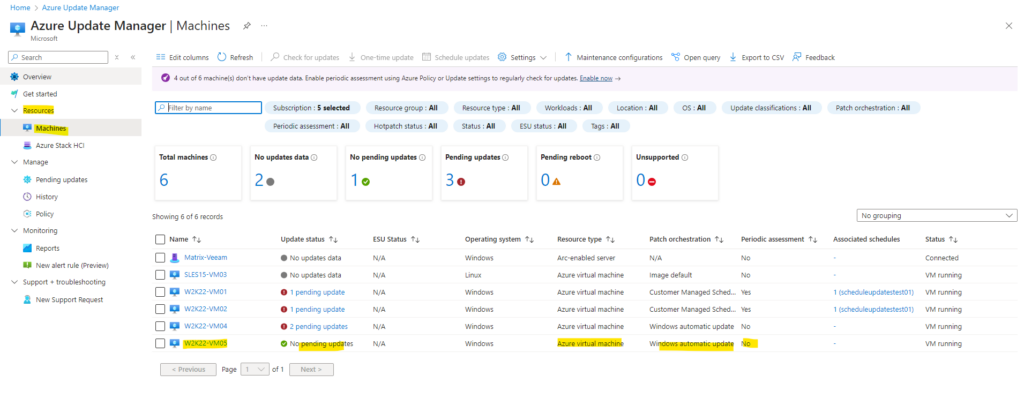
To navigate to the Azure Update Manager, we can just search for updates in the Azure Portal and will find it here as shown below.
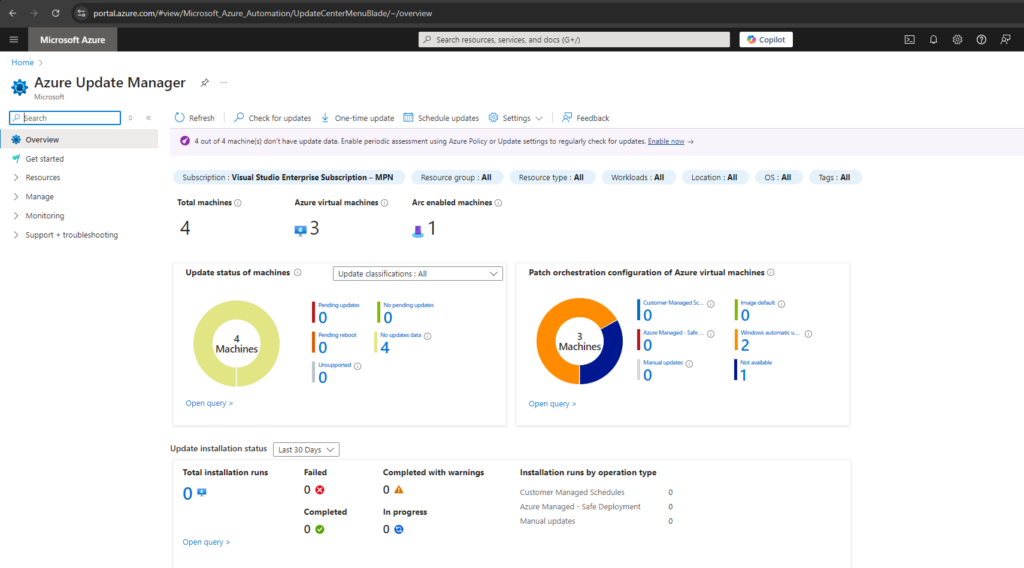
Below on the dashboard we can see on the first look that so far in the last 30 days, neither updates were installed nor were any pending shown which needs to be installed.
The reason for why so far no pending updates are available and installed, is because neither any update settings on a per machine level nor are any policies associated on a scale to these machines.
No updates data below within the Update status of machines section means, that these machines not checked for updates in last 7 days.
We first need to enable periodic assessment to see the latest updates available for our machines and removes the hassle of performing assessment manually every time we need to check the update status. After we enable this setting, Update Manager fetches updates on our machines once every 24 hours.
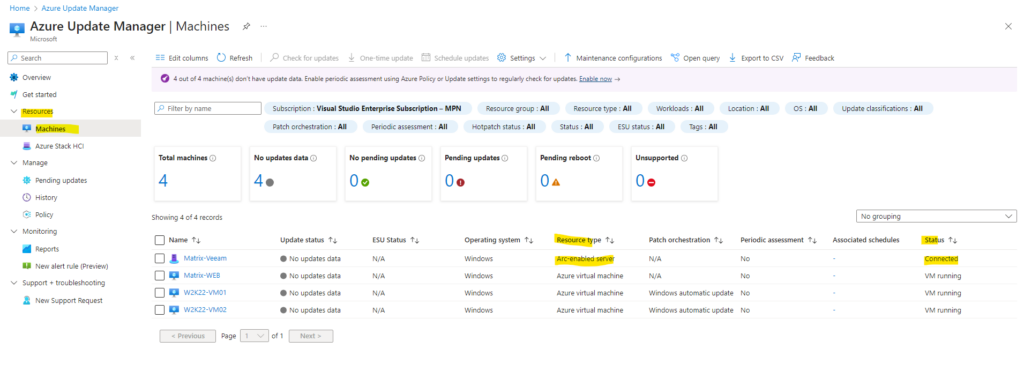
Within the Resources -> Machines blade we will see all of our Azure virtual machines and also Azure Arc-enabled server.
As you can see below, the first server is a Arc-enabled virtual machine running in my on-premise vSphere lab environment. Here we can also see on the first look that so far for all of my machines under the update status column no updates data is shown.
The reason for is as mentioned, that so far neither periodic assessment nor Customer Managed Schedules (using Azure Update Manager) are configured to update our Azure virtual machines.
By the way an assessment in Azure Update Manager will also be performed each time before updates will be installed and configured by using Customer Managed Schedules (using Azure Update Manager) for Patch orchestration.
More about periodic assessment and Customer Managed Schedules (using Azure Update Manager) we will see in the next section.
Update Settings
To finally manage updates on our virtual machines and that we can patch them by using the Azure Update Manager, we first need to configure either Update Settings on a per machine level and shown below or we can use and associate Azure Policies to automatically scale these settings as shown in Part 2.
As already mentioned, the reason for that no pending updates are shown, is because so far periodic assessment is disabled for these virtual machines and neither configured by using the update settings nor the policies.
Further in order to automatically patch our machines on a specific custom schedule, we also need to set for patch orchestration the option Custom Managed Schedules.
This new patch orchestration option enables the following VM properties on your behalf after receiving your consent:
– Patch mode = Azure-orchestrated
– BypassPlatformSafetyChecksOnUserSchedule = TRUE -> This setting ensures that machines are patched by using your configured schedules and not autopatched.BypassPlatformSafetyChecksOnUserSchedule is a setting in Azure Update Manager that allows users to override built-in platform safety checks during scheduled update deployments. Azure Update Manager includes safety checks to prevent disruptions during patching, such as:
– Avoiding updates during high-traffic periods.
– Ensuring that critical services are running before applying patches.
– Maintaining compliance with Azure resource health checks.Enabling BypassPlatformSafetyChecksOnUserSchedule disables these automatic checks, giving users complete control over when and how updates are applied.
Patch orchestration options allow you to control how patches will be applied to your virtual machine.
So far neither periodic assessment nor patch orchestration mode is configured for these machines.
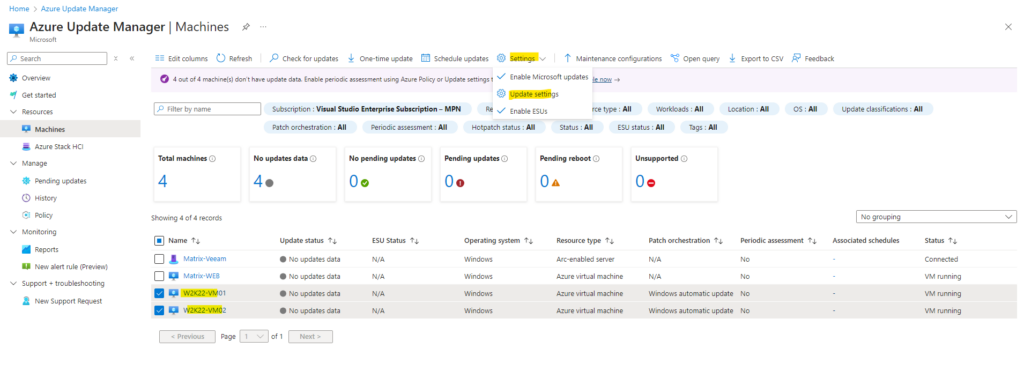
To configure these settings on a per machine level, we first need to select our desired machines we want to associate these settings to and then in the top bar menu we need to select Settings -> Update settings as shown below.
Instead of applying these settings on a per machine level, we can also assign an Azure policy as mentioned which we will see in Part 2. Further we can of course also check for updates on demand which we will see further down.
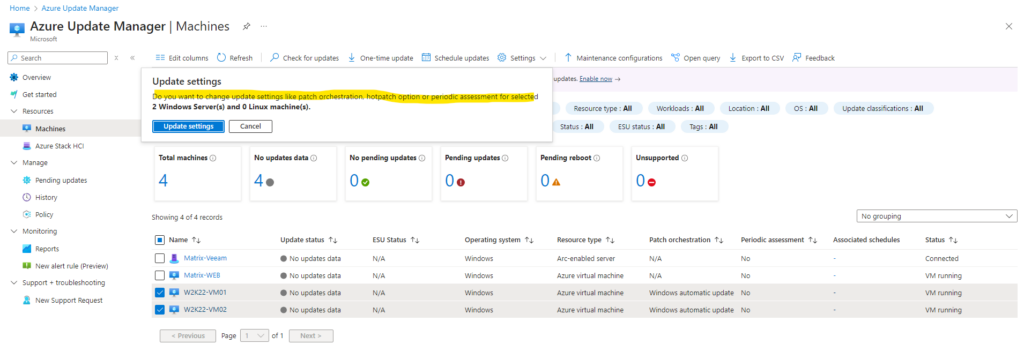
In Azure Update Manager, we have two main options to control how Windows updates will be applied/orchestrated on our virtual machines, aka Patch Orchestration mode.
First by using native Windows Automatic Updates (selected by default as shown below) or by implementing customer-managed schedules through Azure Update Manager.
- Windows Automatic Updates -> This is the native update management service provided by Windows itself. Windows Automatic Updates automatically checks for, downloads, and installs updates on a predefined schedule.
- Customer Managed Schedules -> With Azure Update Manager, you can manage updates on a per-schedule basis, giving you full control over when and how updates are applied to your resources.
There are also some more options which we can choose for Patch Orchestration:
- Azure Managed – Safe Deployment -> This mode enables automatic VM guest patching for the Azure virtual machine. Subsequent patch installation is orchestrated by Azure in a safe, controlled, and reliable manner. E.g. when patching VMs in an availability set, Azure coordinates reboots so that not all VMs in the availability set reboot at the same time.
- Manuel Updates -> This mode is supported only for Windows VMs. This mode disables Automatic Updates on the Windows virtual machine.
- Image Default -> for Linux machines, it uses the default patching configuration in Linux.
Periodic assessment
The periodic assessment is set to run every 24 hours. You can either enable or disable this setting.Hotpatch
You can enable hotpatching for Windows Server Azure Edition VMs. Hotpatching is a new way to install updates on supported Windows Server Azure Edition VMs that doesn’t require a reboot after installation. You can use Update Manager to install other patches by scheduling patch installation or triggering immediate patch deployment. You can enable, disable, or reset this setting.Patch orchestration
This setting allows you to control how patches will be applied to your virtual machine.
– Windows Automatic Updates (AutomaticByOS) – When the workload running on the VM doesn’t have to meet availability targets, the operating system updates are automatically downloaded and installed. Machines are rebooted as needed.
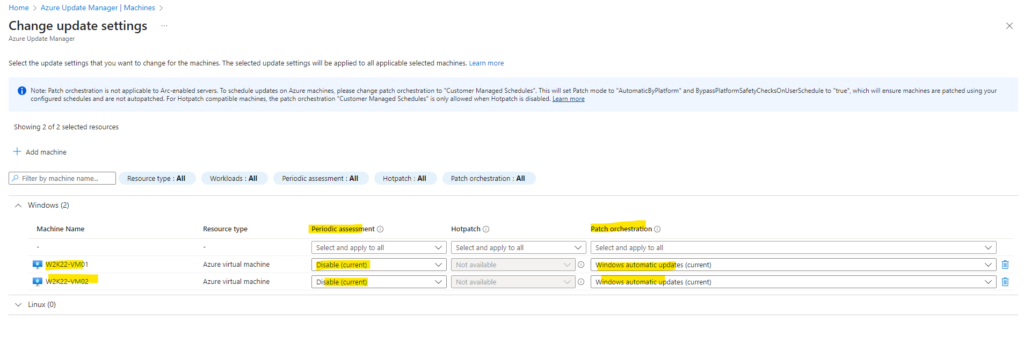
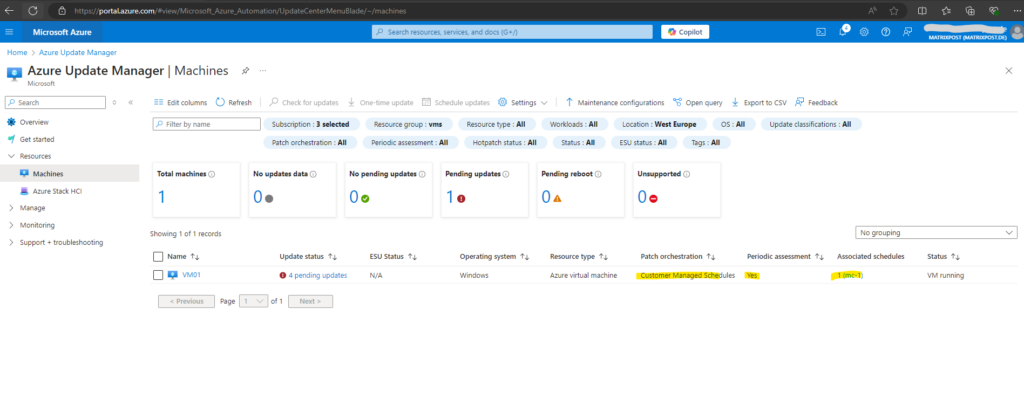
So now I will configure the Patch Orchestration below.
As mentioned, for Azure virtual machines we need to select Custom Managed Schedules which will finally enable updating our machines by using the Azure Update Manager.
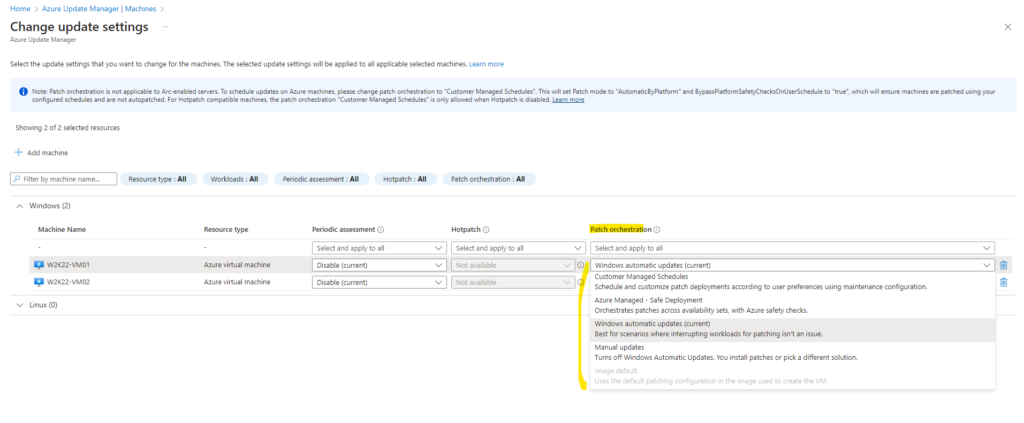
!! Note !!
Patch orchestration is not applicable to Arc-enabled servers. But we also can enable periodic assessment for them to check for updates every 24 hours and schedule when patches and updates are applied to Arc-enabled servers. For the update source they will use their already configured source on the machine itself (usually Windows Updates directly or WSUS).
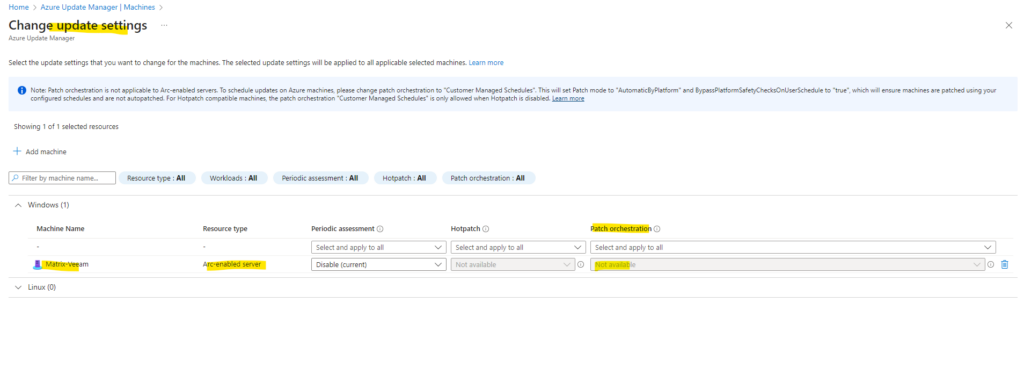
Further we need to enable periodic assessment so that these machines will be forced to check for updates every 24 hours.
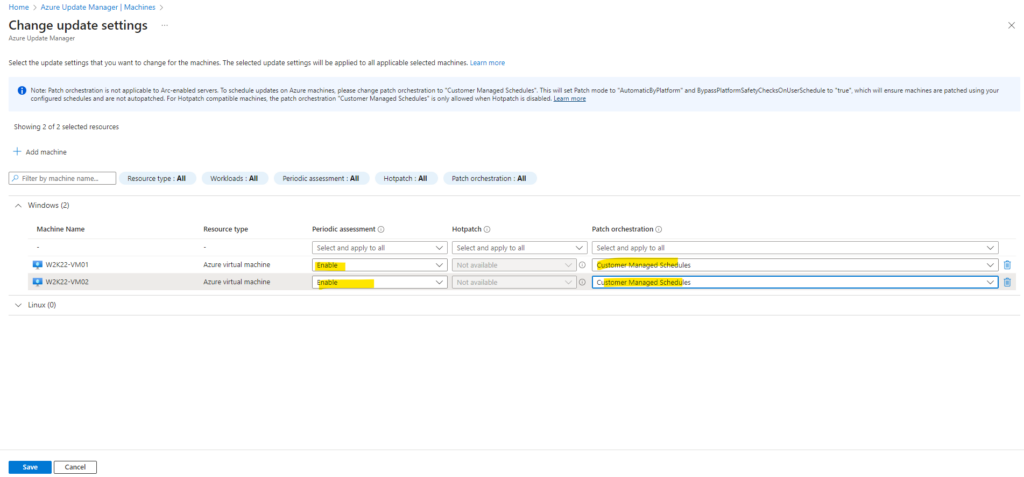
So from now on these two virtual machines will check for updates every 24 hours.
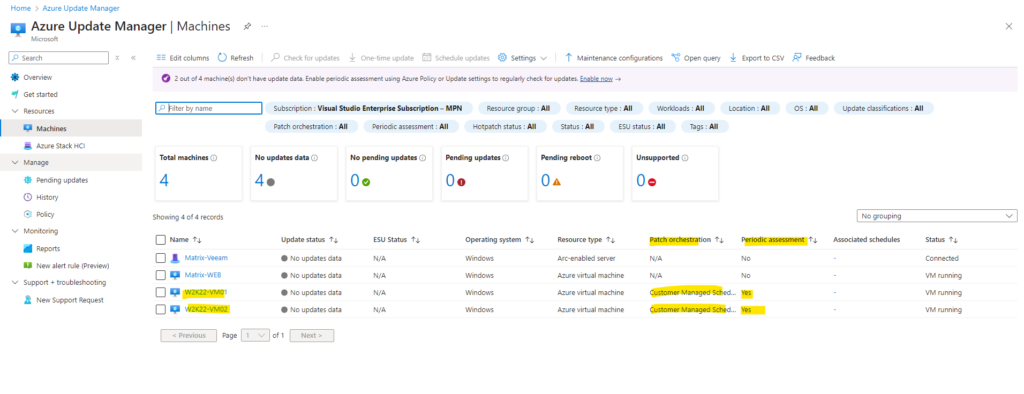
We can now also schedule when the updates will be installed on these virtual machines. Therefore we first need to select our desired virtual machines and then we can click on Schedule updates as shown below.
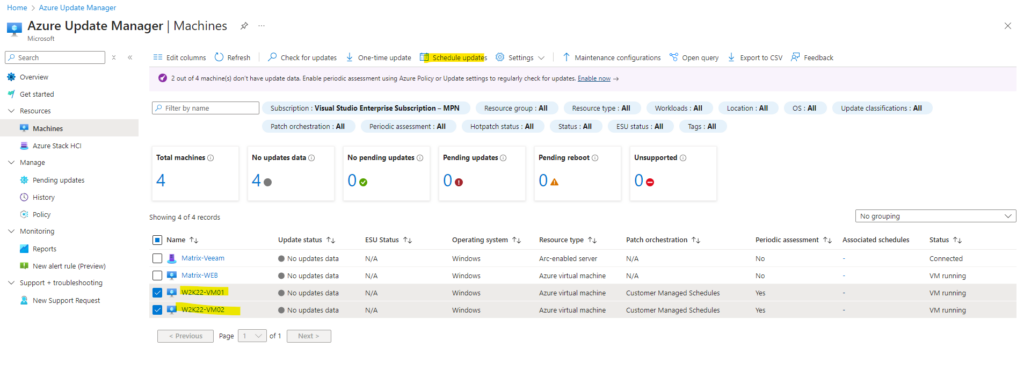
Here we will create a new maintenance configuration.
Therefore we need select the subscription and resource group in which we want to create this new maintenance configuration. Further we need to enter a name for, select the region, choose if reboot will be executed if required and we also need to specify a scope depending on the type of resources you intend to update.
You cannot change this after creation.
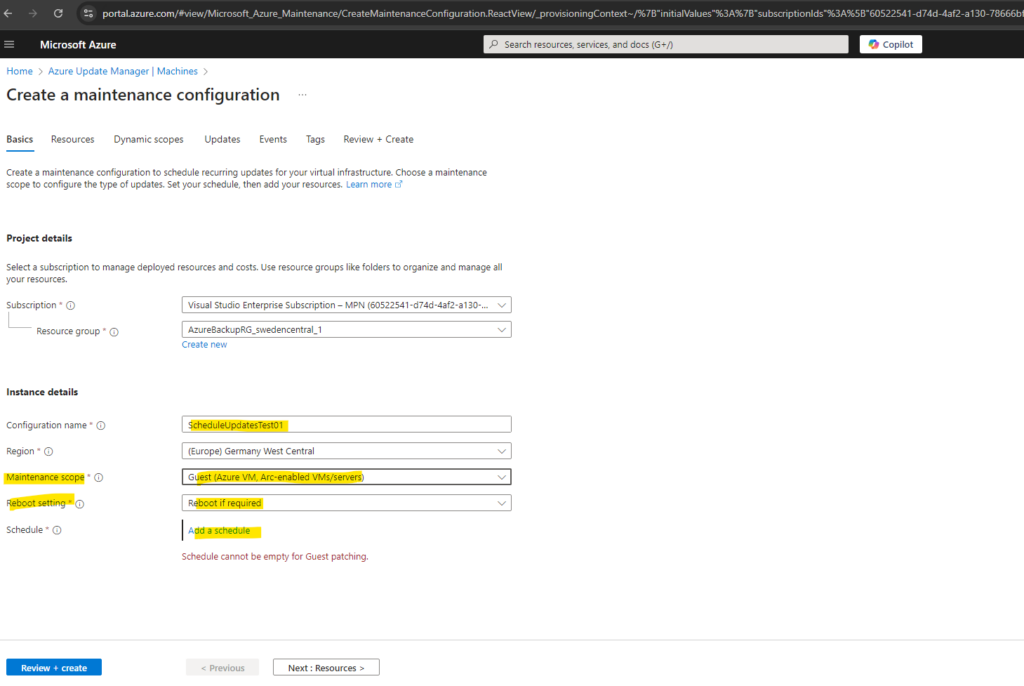
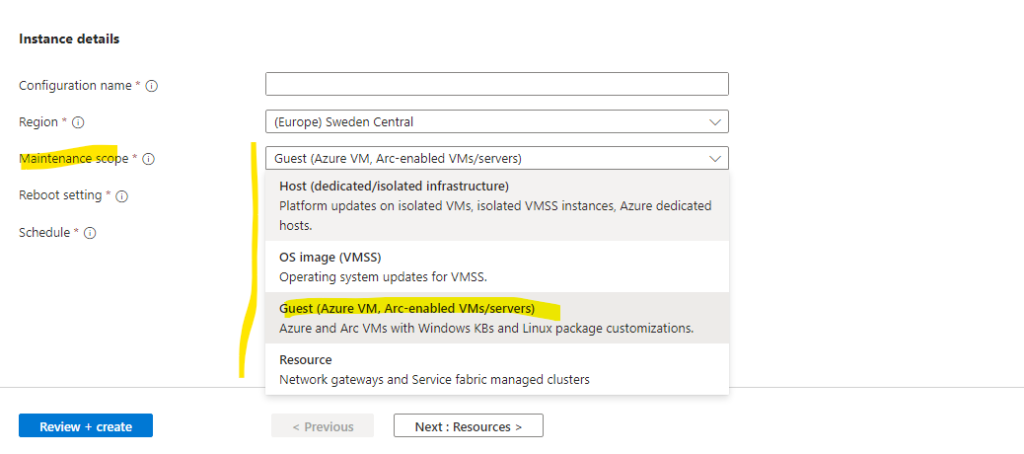
Here you can see the different scopes we can choose for.
To be able to assign this maintenance configuration to our Azure and Azure Arc enabled server, below we need to select Guest (Azure VM, Arc-enabled VMs/servers).
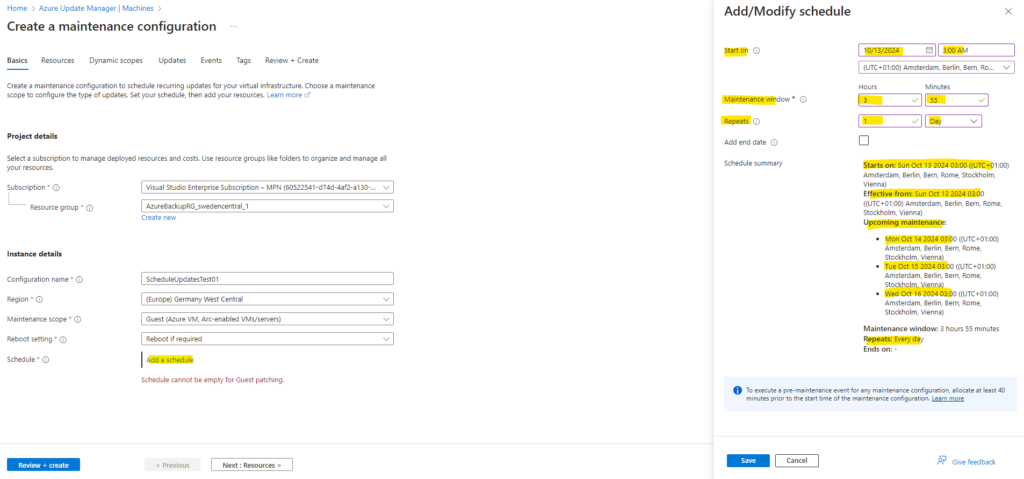
Then the essential point here is to create a new schedule where we can specify a start time and frequency of the maintenance configuration and the duration for each maintenance run.
So click on Add a schedule and within the right blade we set a start for the updates and a maintenance window how long it can take to update the machines.
Further we can set a repeat for this schedule.
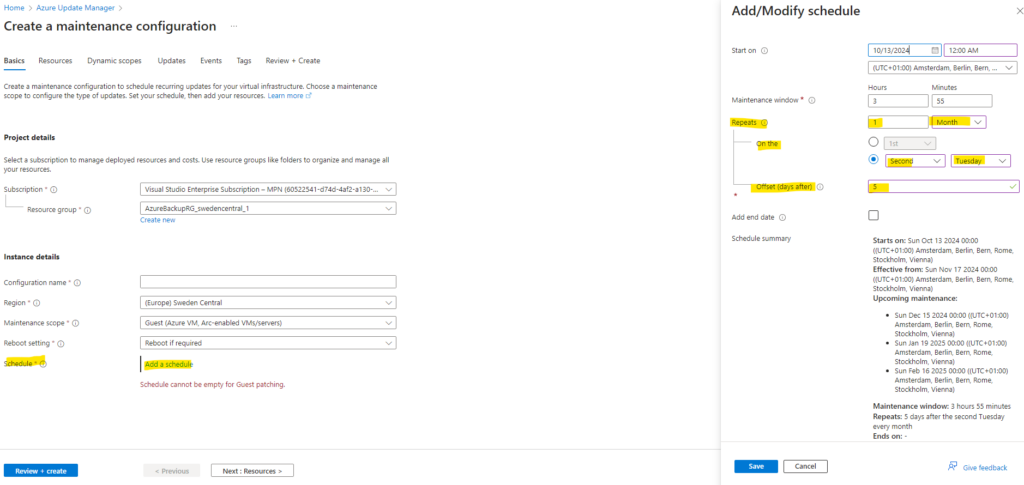
Another interesting option when creating a new schedule is the offset. We can specify an offset from the day set. It could be from 0 to +6/-6.
For example we can set to update the machine monthly on the second Tuesday (Microsoft-Patchday) and set an offset of 5 days later. So we can assure in case of any malfunctioning updates will be released on this date, they usually will get withdrawn within these 5 days offset.
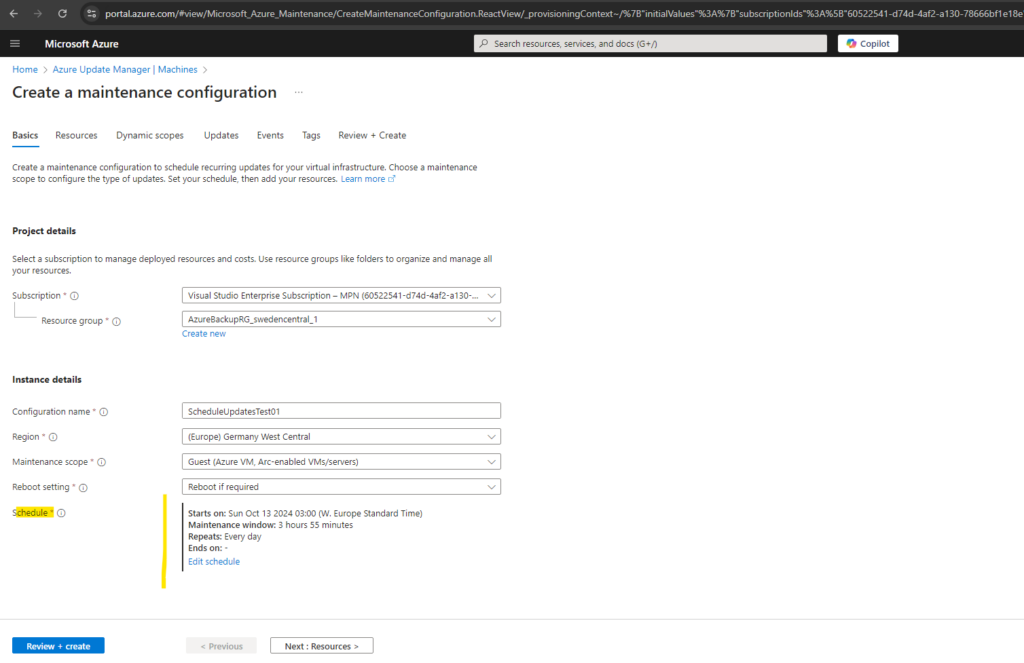
On the next tab we can select our machines we want to assign to this new maintenance configuration.
Previously assigned resources won’t be shown below.
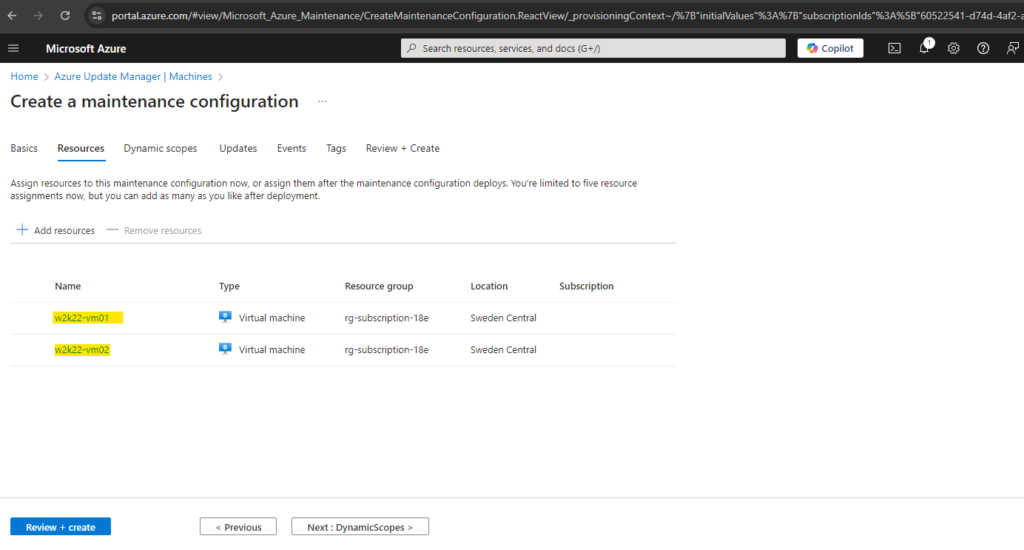
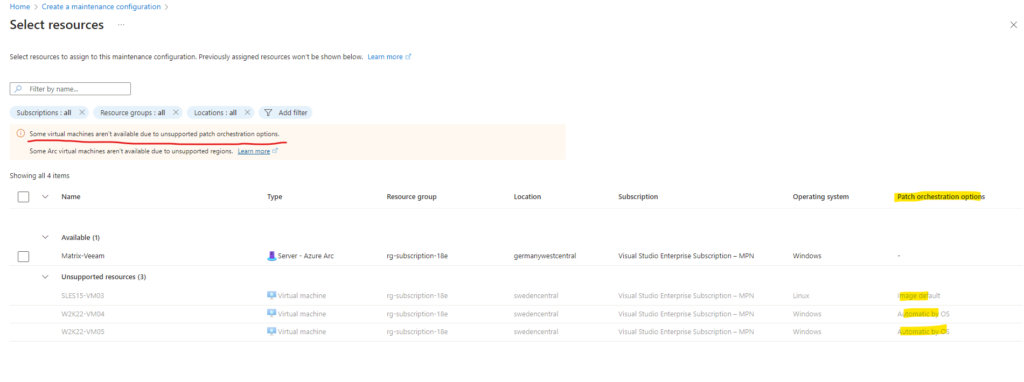
We can assign this maintenance configuration just for supported patch orchestration options.
In case Image default for Linux machines or Automatic by OS (Windows Automatic Update) is configured as shown below, we can’t assign these machines because they will user their own native local update service and out of the box schedule (Active hours configuration).
The next tab Dynamic scopes will give us the option to assign machines to this maintenance configuration dynamically and not fix.
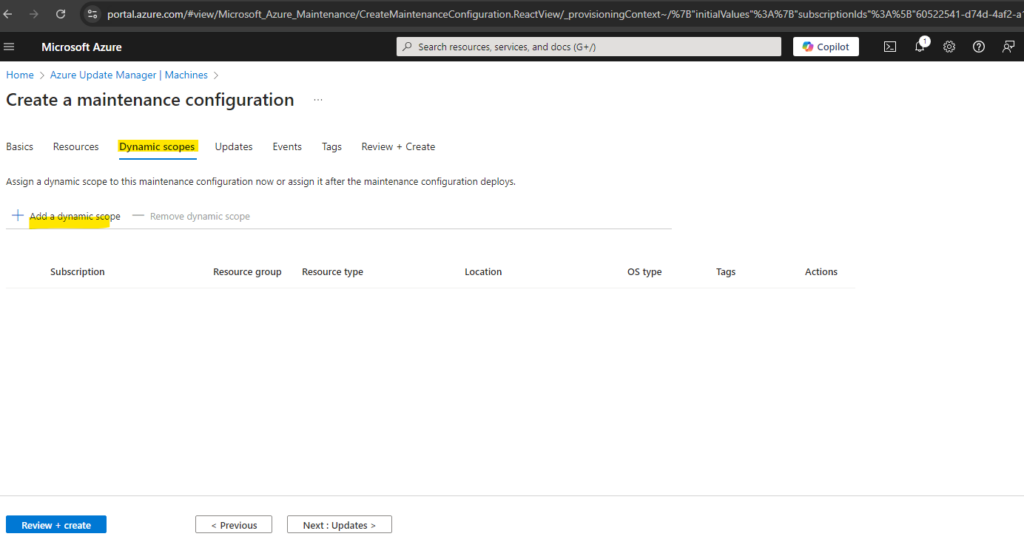
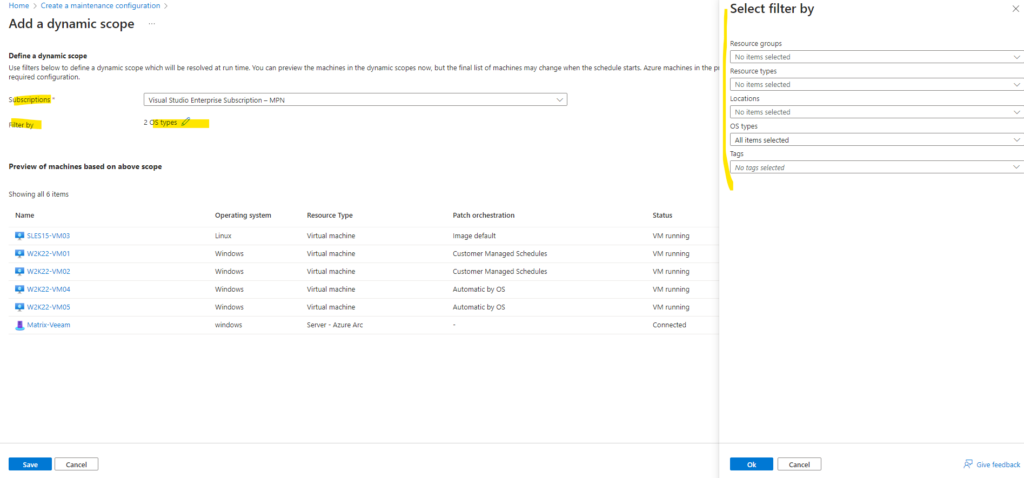
We can group machines based on criteria such as subscription, resource group, location, resource type, OS Type, and Tags. This becomes the definition of the scope.
Associate the scope to a schedule/maintenance configuration to apply updates at scale as per a pre-defined scope. To a scope a maximum of 1000 resources can be assigned to and the total number of resources associated to a schedule can be 3000.
The criteria will be evaluated at the scheduled run time, which will be the final list of machines that will be patched by the schedule. The machines evaluated during create or edit phase may differ from the group at schedule run time.
On the Updates tab we can also filter updates by selecting just specific update classifications or by excluding KB ID/package name or specifying maximum patch publish date.
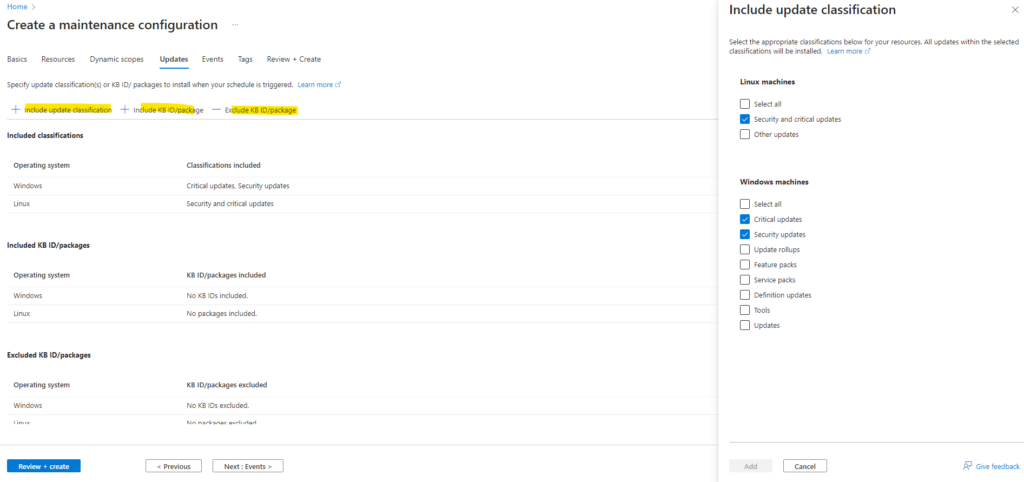
On the next tab Events we can configure pre and post events that allows us to execute user-defined actions before and after the scheduled maintenance configuration.
I will show this in detail in Part 2.
More about pre and post events you will find in the following article.
Create pre and post events
https://learn.microsoft.com/en-us/azure/update-manager/pre-post-events-schedule-maintenance-configuration
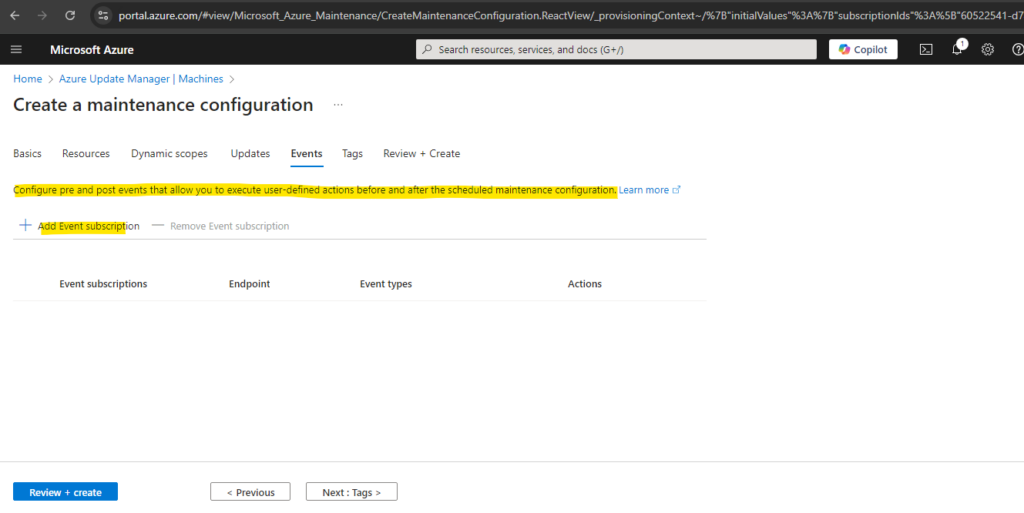
Finally we can click on Create.
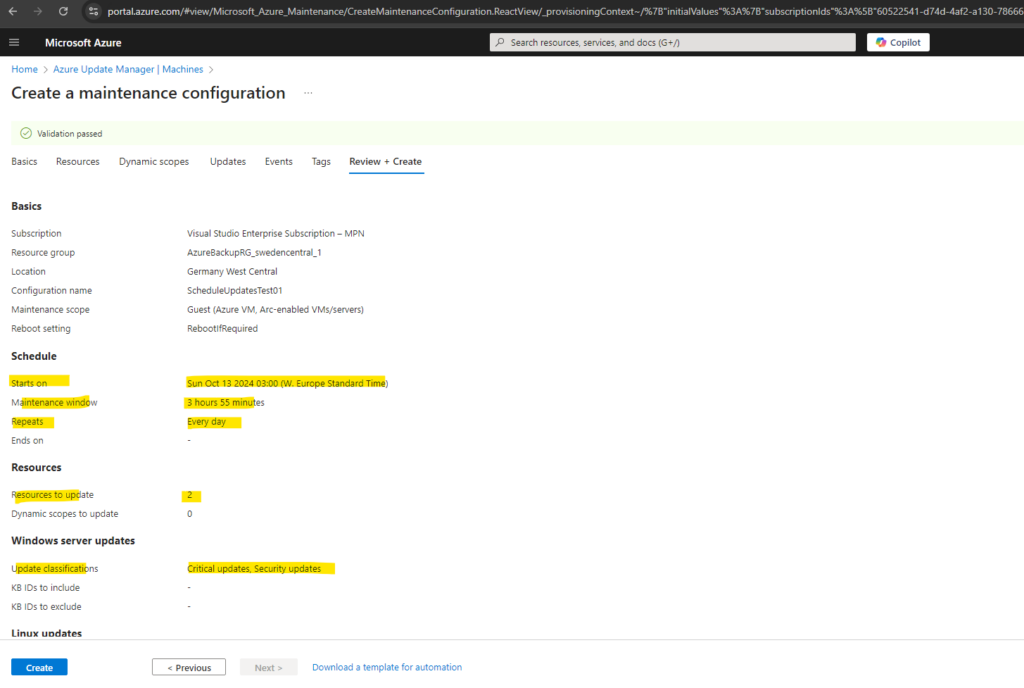
Our new maintenance configuration was deployed successful.
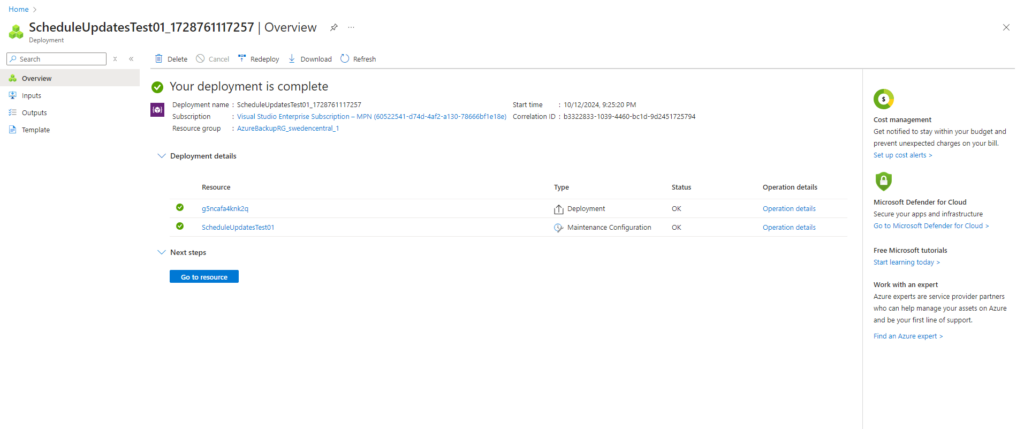
When we click above on Go to resource we will get forwarded to our newly created maintenance configuration.
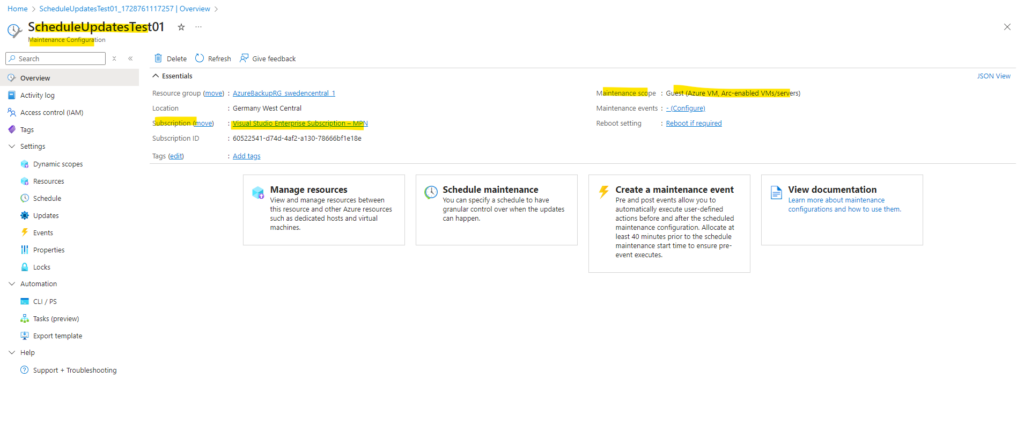
To see all of our maintenance configurations or later navigate to, we can also click on Maintenance configurations within Azure Update Manager -> Resources -> Machines.
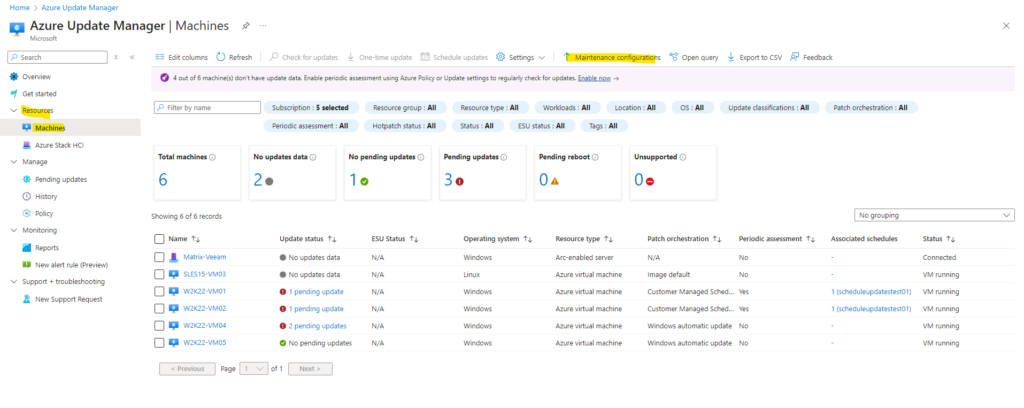
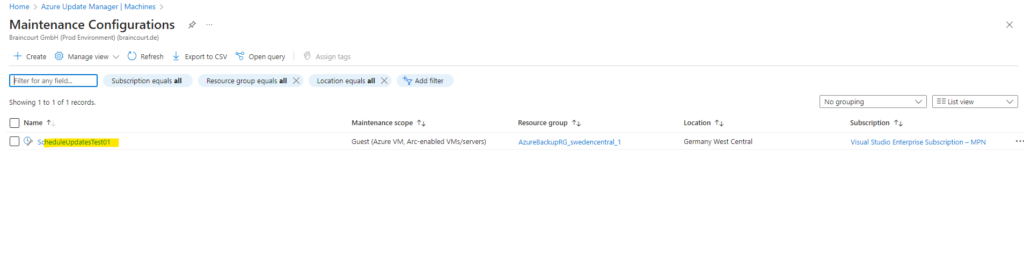
By clicking on the maintenance configurations above, a new blade will be opened where we can edit our settings. We can also add some configuration here.
Actually this below is not the same maintenance configurations as above, I was adding this one to show how we can use Azure Policy to associate periodic assessment and Patch Orchestration.
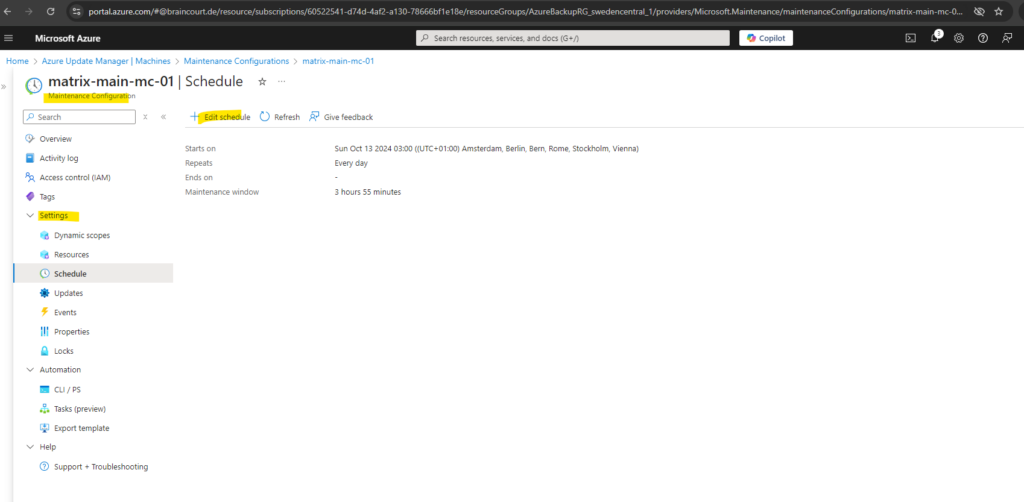
Check for Updates on demand
As already mentioned, we can also check for updates and install them on demand.
Therefore as usual we first need to select our desired machines we want to update and then we need to click on Check for updates as shown below.
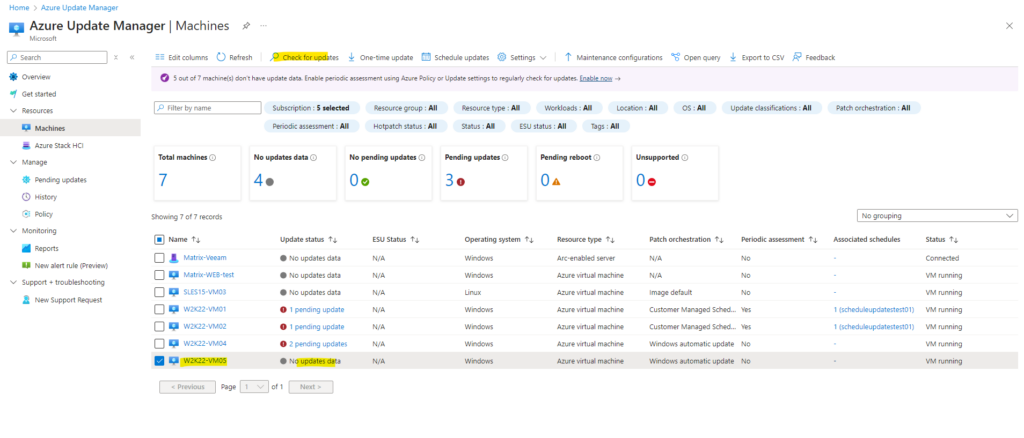
Click on Assess now.
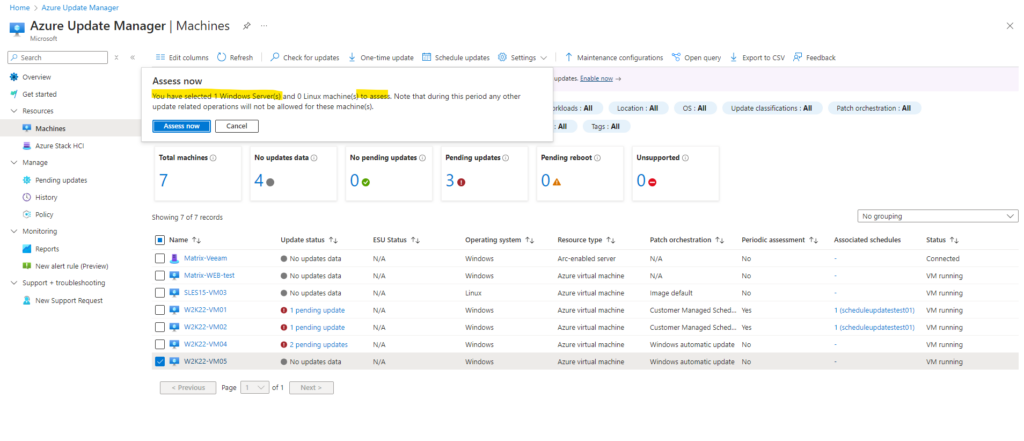
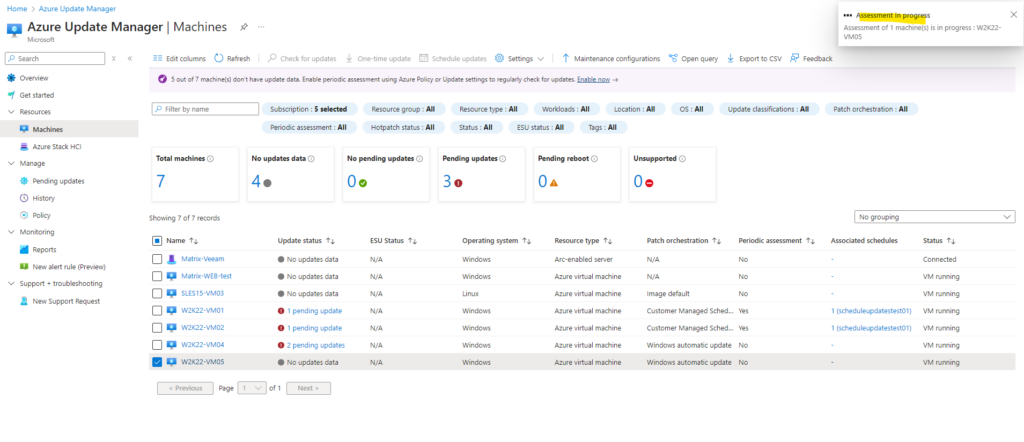
The assessment is running on this virtual machine.
Update Manager provides you with the flexibility to assess the status of available updates and manage the process of installing required updates for your machines.
It provides an analysis of the current patching status of the systems, helping you identify any security, critical, or optional updates that need to be applied.
After the assessment finished successful, we can immediately see that there are 2 pending updates available to install.
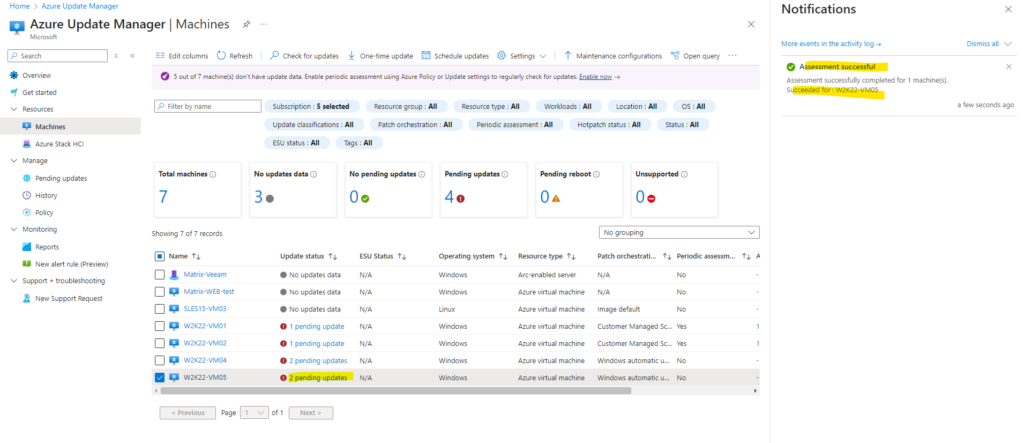
We can now also install these 2 pending updates on demand by clicking on One-time update on the top bar menu as shown below.
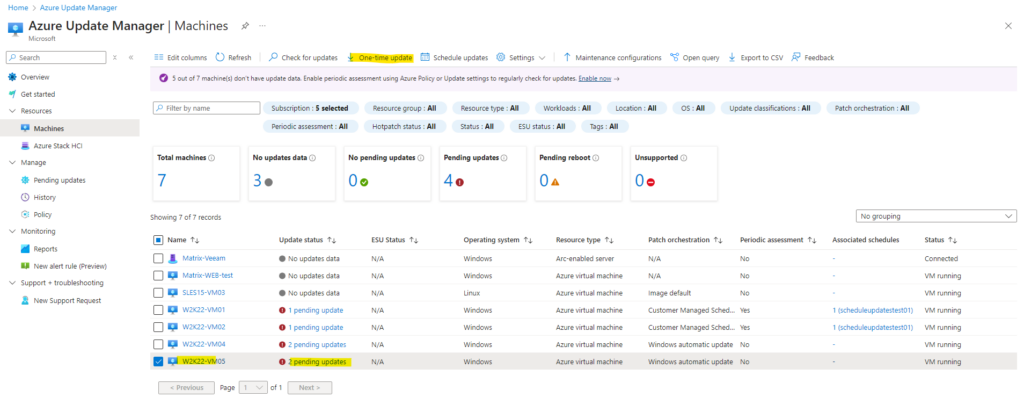
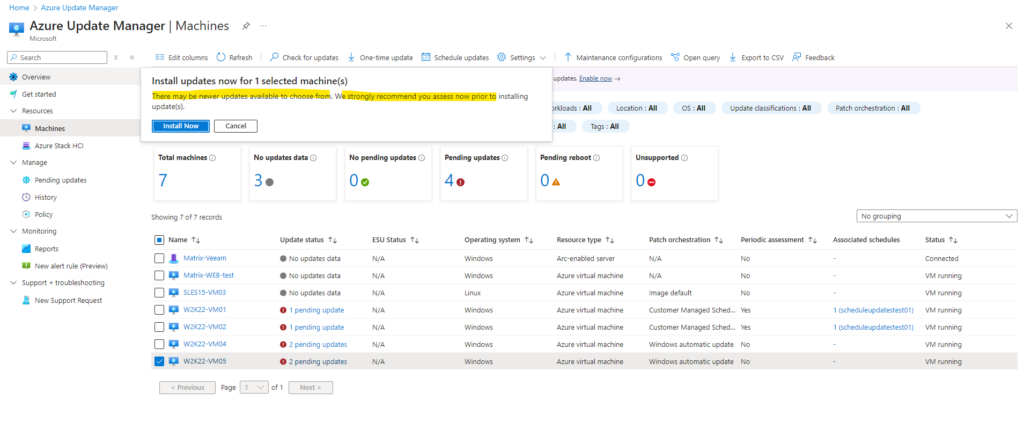
Because we already assess previously, we can click on Install now.
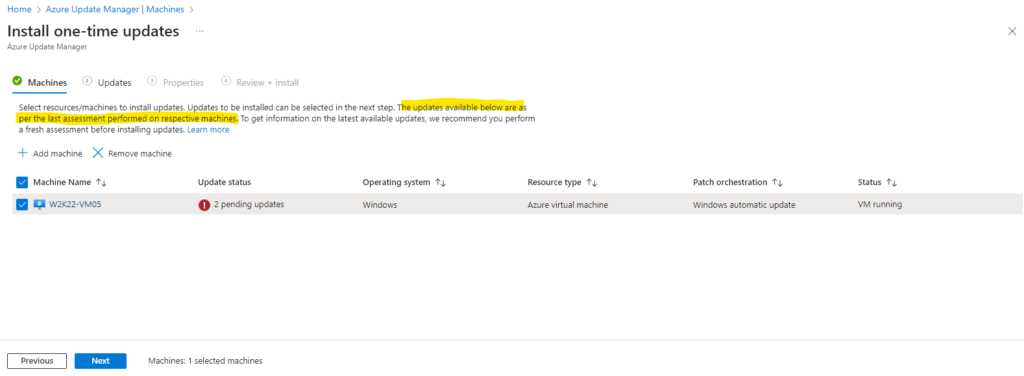
In my case I want to install all updates which are available for the virtual machine.
All classifications by default selected below.
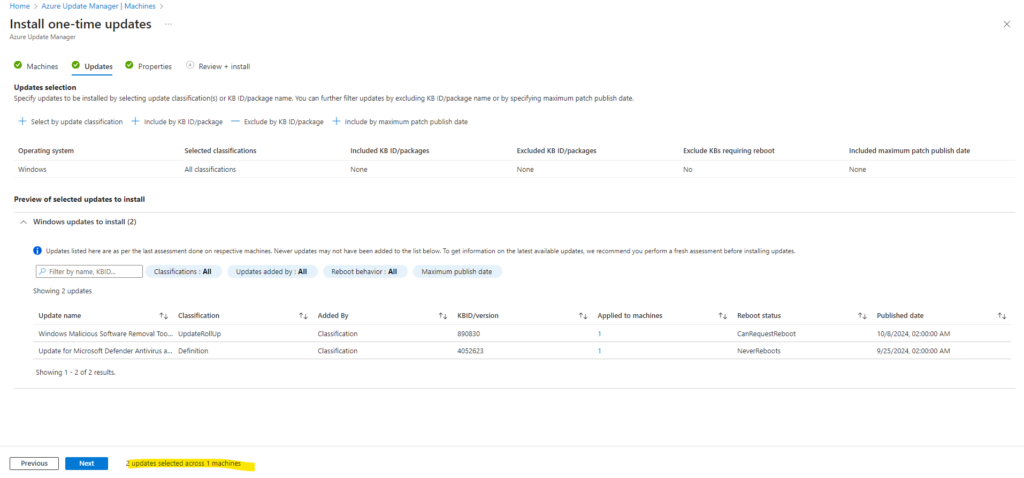
We can also filter updates by selecting just specific update classifications or by excluding KB ID/package name or specifying maximum patch publish date.
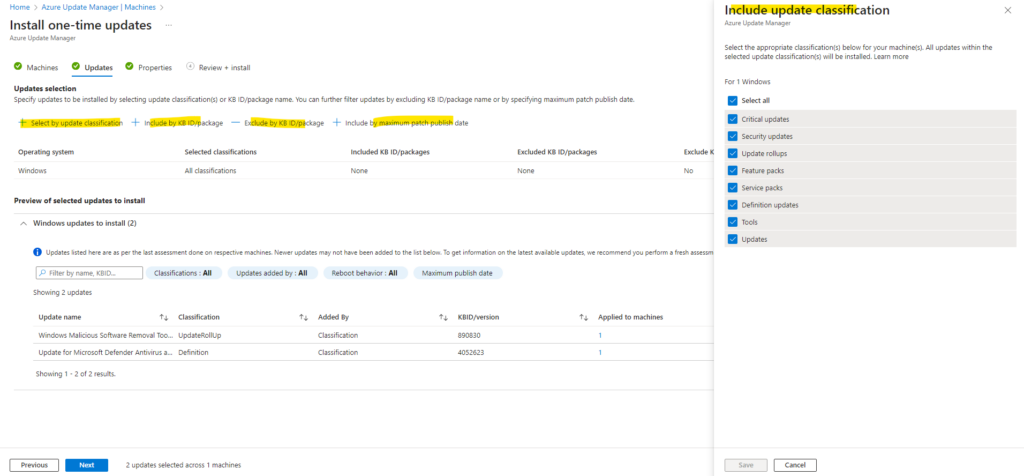
Next we need to choose if we want to reboot the machine if required or not.
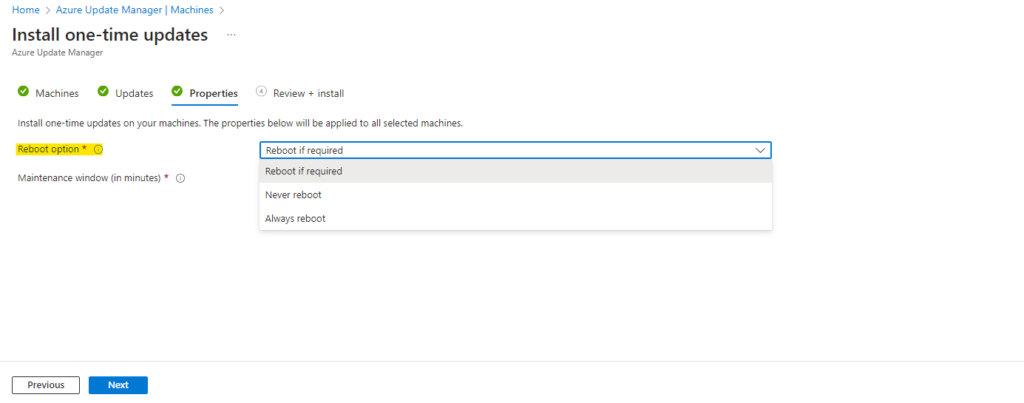
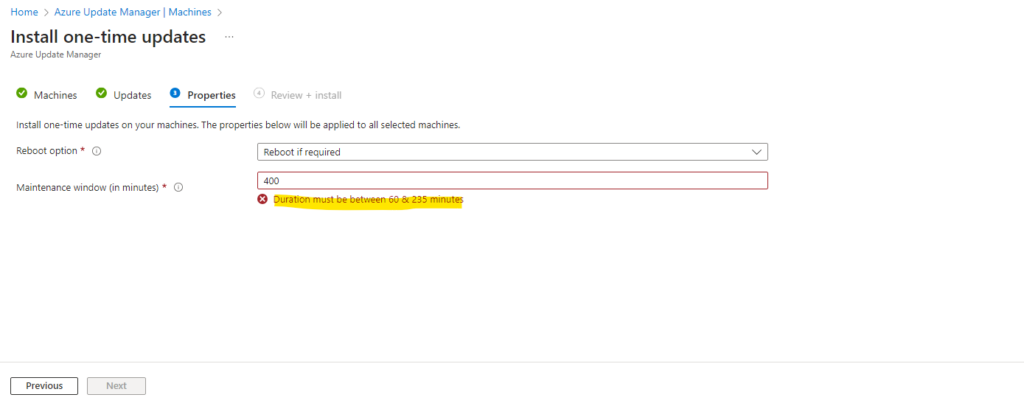
We also need to specify how much time, in minutes, Azure can take to deploy updates
Duration must be between 60 & 235 minutes.
More about you will find in the following article https://learn.microsoft.com/en-us/azure/update-manager/deploy-updates
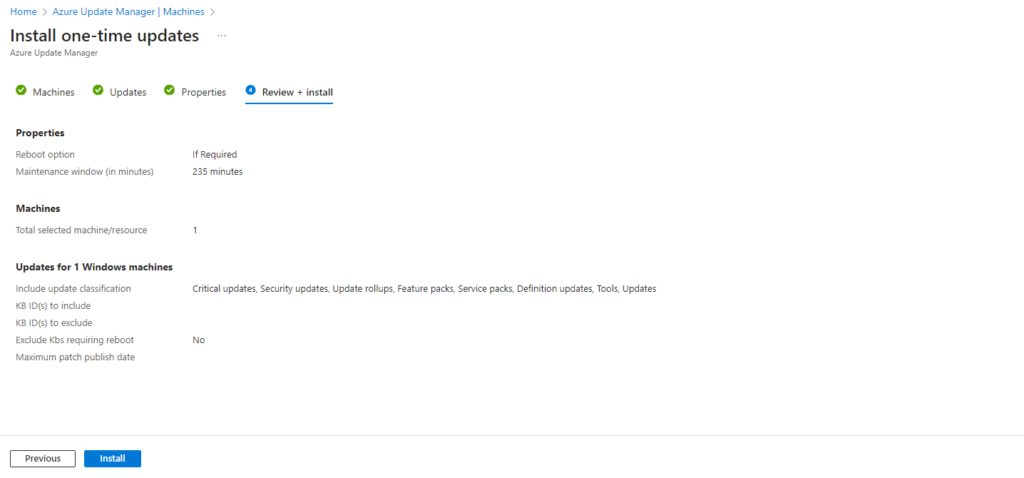
Finally we can click on Install.
We can track the status of the updates under Manage -> History.
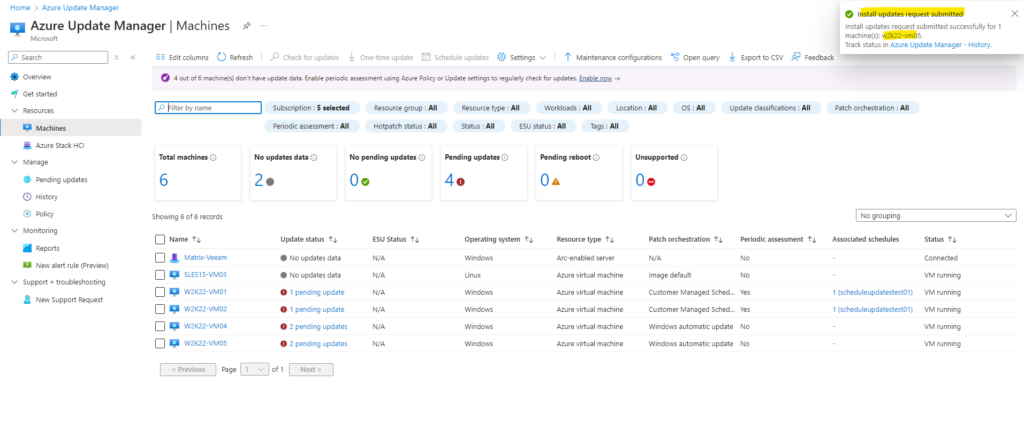
We can click below on InProgress to see more details.
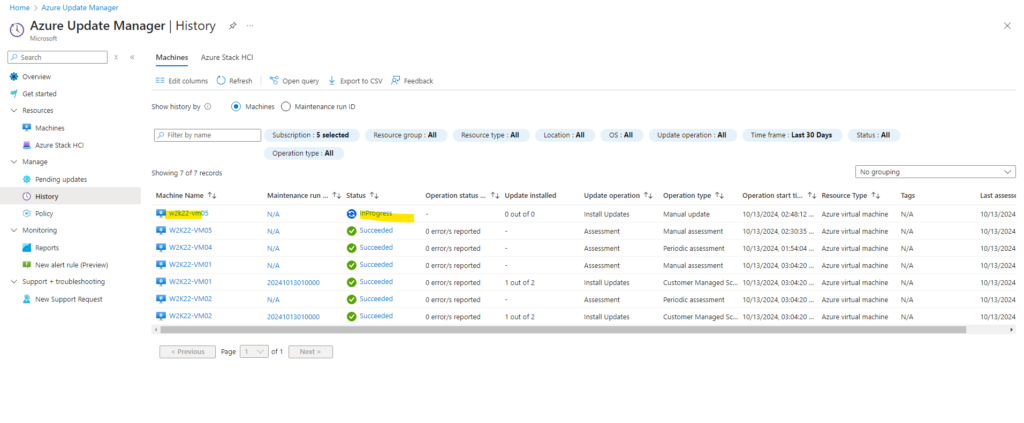
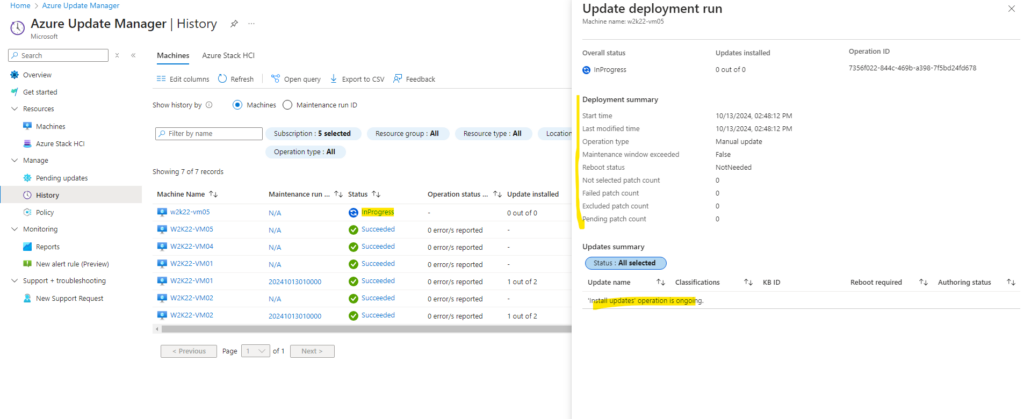
Finally the installation succeeded.
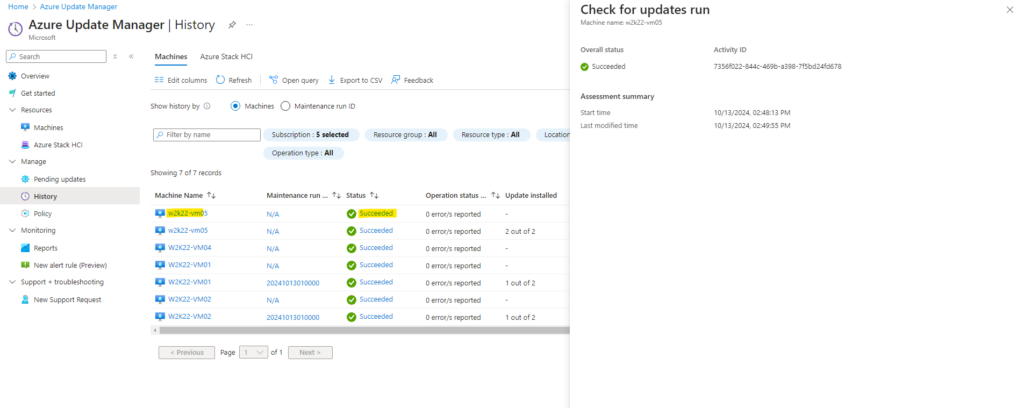
Back under Resources -> Machines we also see that for this virtual machine now no more pending updates are available and the update status is fine.
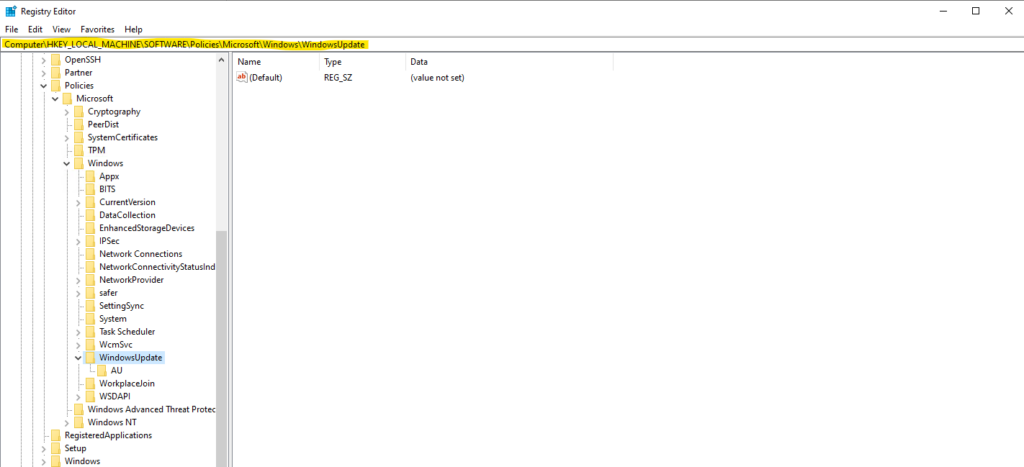
Azure Update Manger – Registry Settings on the Virtual Machines
When in the Azure Update Manger the patch orchestration mode Customer Managed Schedules is assigned to an Azure VM, the registry settings on the VM will looks like below.
For the following key just the Default string value is set.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate
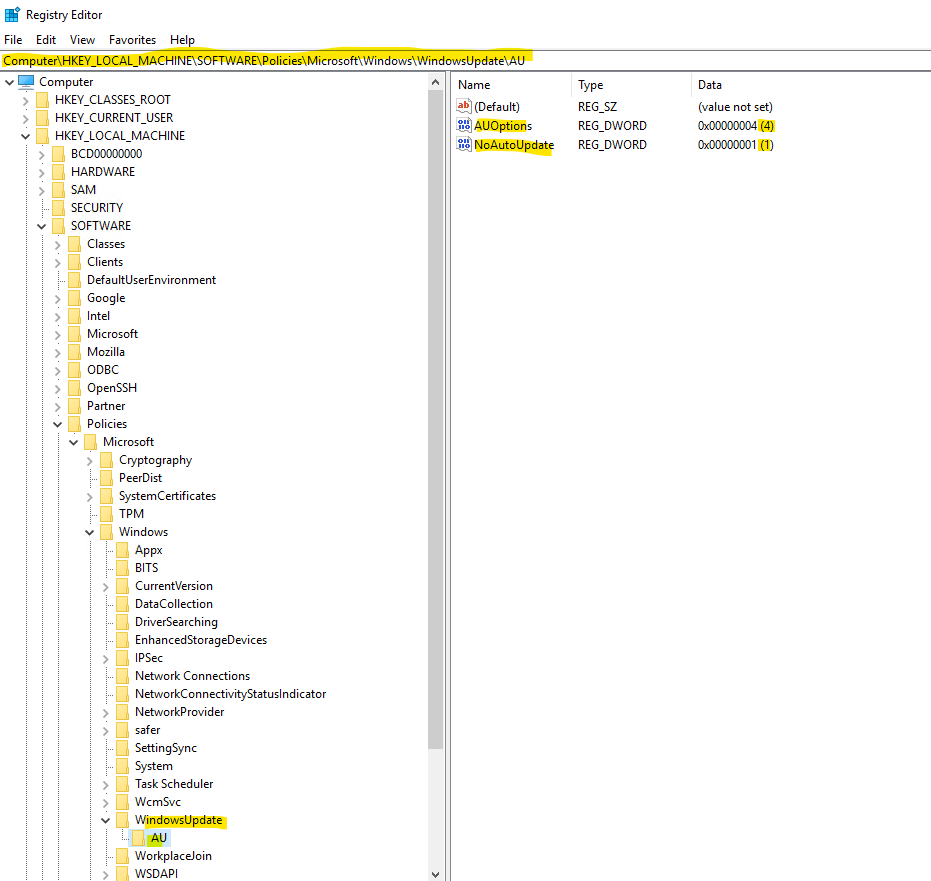
For the AU key the following.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU
AUOptions -> 4: Automatically download and scheduled installation.
NoAutoUpdate -> 1: Automatic Updates is disabled.
- NoAutoUpdate (REG_DWORD):
- 0: Automatic Updates is enabled (default).
- 1: Automatic Updates is disabled.
- AUOptions (REG_DWORD):
- 1: Keep my computer up to date is disabled in Automatic Updates.
- 2: Notify of download and installation.
- 3: Automatically download and notify of installation.
- 4: Automatically download and scheduled installation.
- 5: Allow local admin to select the configuration mode. This option isn’t available for Windows 10 or later versions.
- 7: Notify for install and notify for restart. (Windows Server 2016 and later only)
- SetProxyBehaviorForUpdateDetection
- 0 Default ==> Use user’s proxy settings (interactive session)
- 1 ==> Use system-level proxy settings (non-user context)
- 2 ==> Bypass proxy detection entirely
More Automatic Updates Settings you will find in the following Microsoft article https://learn.microsoft.com/en-us/windows/deployment/update/waas-wu-settings#configuring-automatic-updates-by-editing-the-registry.
- NoAutoUpdate (REG_DWORD):
- 0: Automatic Updates is enabled (default).
- 1: Automatic Updates is disabled.
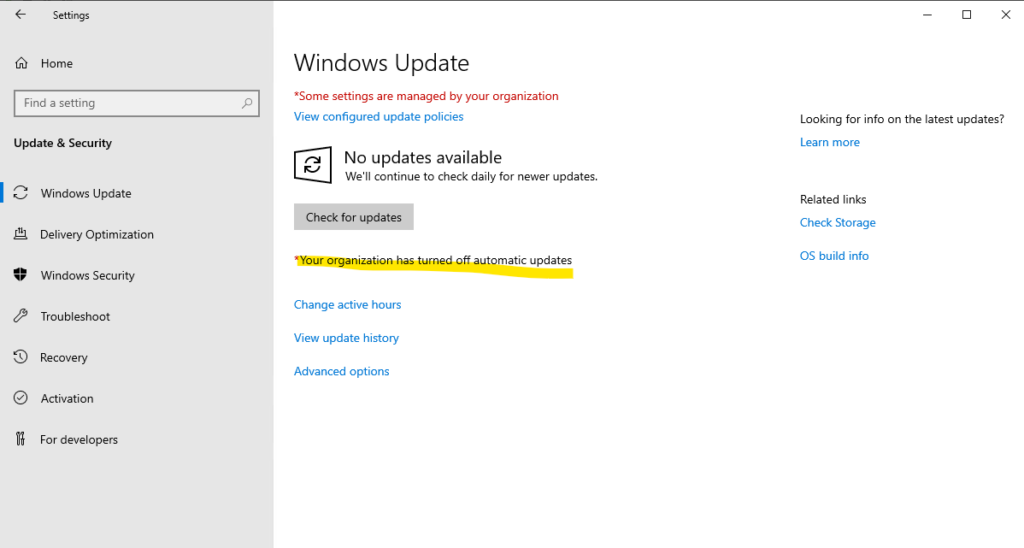
Azure Update Manager operation (AUM)
When an Azure Update Manager operation(AUM) is enabled or triggered on your Azure or Arc-enabled server, AUM installs an Azure extension or Arc-enabled servers extensions respectively on your machine to manage the updates.
Azure Update Manager does not install a visible Azure VM extension, but it uses the Azure VM Guest Agent to orchestrate updates and may inject a platform-managed component during assessment or patch runs, this is not shown in the Extensions UI.
The extension is automatically installed on your machine when you initiate any Update Manager operation on your machine for the first time, such as Check for updates, Install one-time update, Periodic Assessment or when scheduled update deployment runs on your machine for the first time.
Customer doesn’t have to explicitly install the extension and its lifecycle as it is managed by Azure Update Manager including installation and configuration. The Update Manager extension is installed and managed by using the below agents, which are required for Update Manager to work on your machines:
- Azure Arc-enabled servers agent
- Azure VM Windows agent or the Azure VM Linux agent for Azure VMs.
Troubleshooting
Windows Virtual Machines
In case you will face some update error messages for Windows virtual machines in the Azure Update Manager, first check if these virtual machines are able to connect to the endpoints required by the Windows Update agent as mentioned in the prerequisites section to the beginning.
Often these error messages are not really helpful to see on the first sight the real issue behind.
To get more detailed information about what happened during the update process, we can also leverage the Windows Updates Logs.
Run the following Windows PowerShell cmdlet to generate the logs.
This cmdlet will merge and convert Windows Update trace files (.etl files) into a single readable WindowsUpdate.log
Windows Update no longer directly produces a WindowsUpdate.log file. Instead, it produces .etl files that aren’t immediately readable as written.
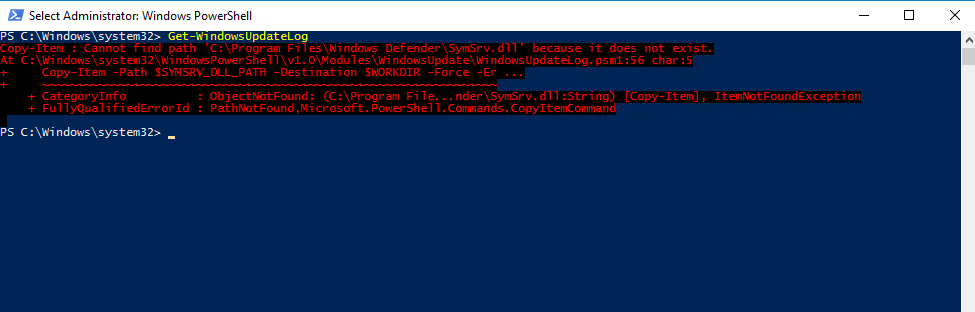
PS> Get-WindowsUpdateLog
In case you will run into the following error, we first need to copy the missing SymSrv.dll to the mentioned path.
Copy-Item : Cannot find path ‘C:\Program Files\Windows Defender\SymSrv.dll‘ because it does not exist
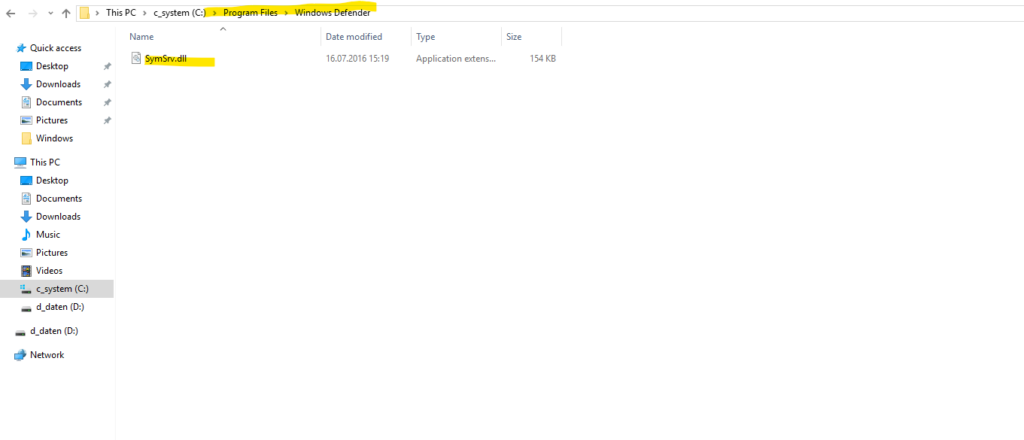
Copy SymSrv.dll either from the same machine and the following path C:\Windows\WinSxS\ or from another Windows Server 2016 where Defender wasn’t removed.
If these endpoints are reachable by the virtual machines we can also perform a reset of the Windows Updates Components.
Resetting Windows Updates Components can help resolve issues like failed updates, stuck updates, or corrupted update components.
To reset the Windows Updates Components perform the following steps. Open Windows PowerShell or the CMD as administrator and run the following commands.
> net stop wuauserv > net stop cryptSvc > net stop bits > net stop msiserver > Ren C:\Windows\SoftwareDistribution SoftwareDistribution.old > Ren C:\Windows\System32\catroot2 Catroot2.old > net start wuauserv > net start cryptSvc > net start bits > net start msiserver
Also check out to the following article by Microsoft for more information about troubleshooting Windows Update issues https://support.microsoft.com/en-us/windows/troubleshoot-problems-updating-windows-188c2b0f-10a7-d72f-65b8-32d177eb136c.
Finally to see if the virtual machine is able to check if new updates are available, besides triggering an assessment in Azure Update Manager, we can therefore also use the SConfig (Server Configuration Tool) as shown in my following post.
Using the Windows settings -> Windows Update page on the machine can trigger the immediate installation of updates when we actually just want to see if new updates are available.
Troubleshoot Windows Update Issues by using the msdt Utility
The msdt utility (Microsoft Support Diagnostic Tool) in Windows includes a set of built-in troubleshooters including one for Windows Update.
Note: Microsoft has deprecated msdt.exe as of 2023 and is gradually replacing it with modern troubleshooters in Settings and the Get Help app. However, it’s still available on many Windows 10/11 systems.
Deprecation of Microsoft Support Diagnostic Tool (MSDT) and MSDT Troubleshooters
https://support.microsoft.com/en-us/windows/deprecation-of-microsoft-support-diagnostic-tool-msdt-and-msdt-troubleshooters-0c5ac9a2-1600-4539-b9d0-069e71f9040a
PS> msdt /id WindowsUpdateDiagnostic
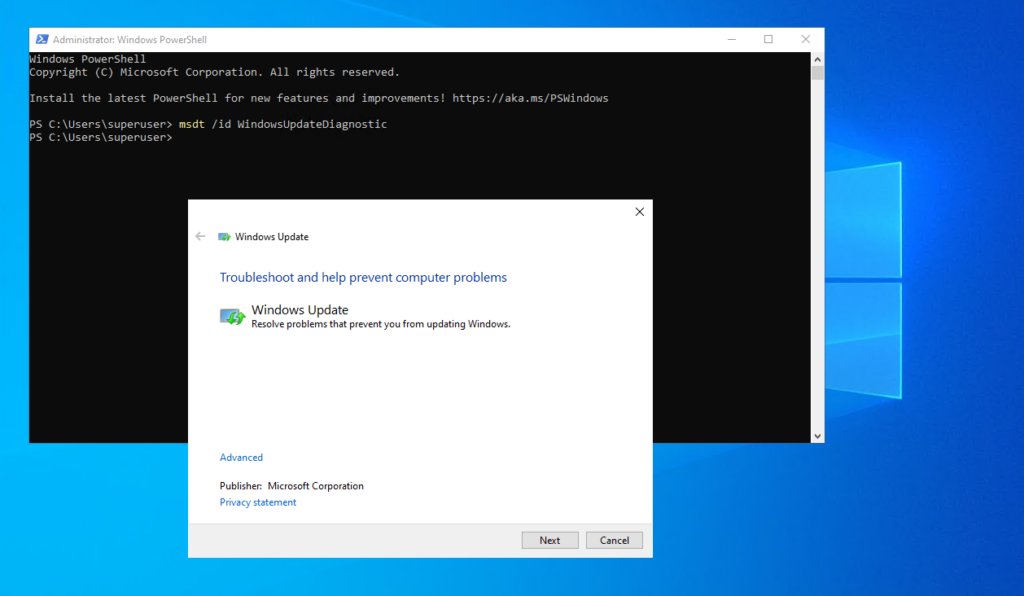
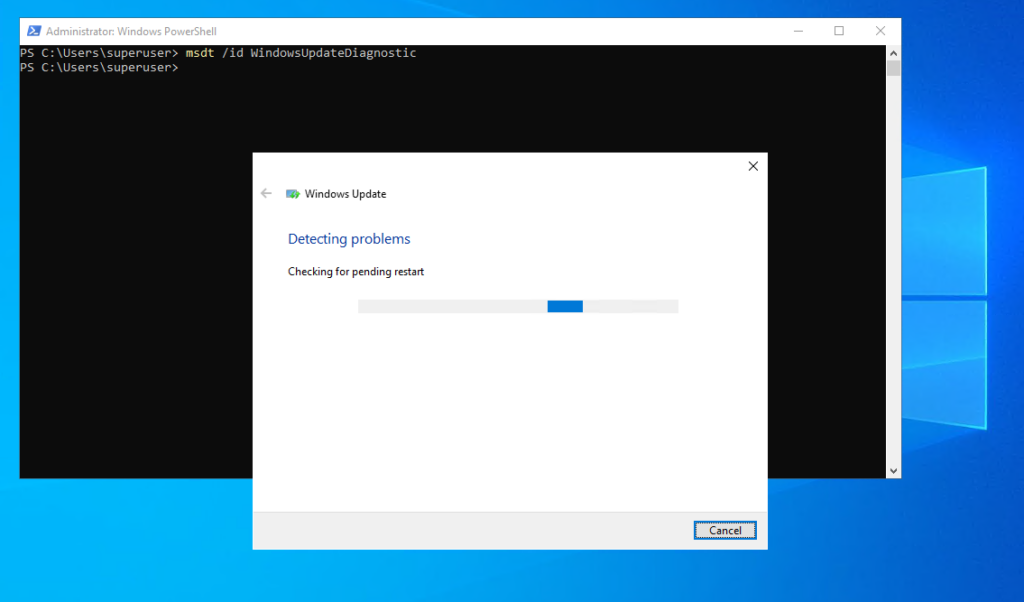
Determine Pending Reboot
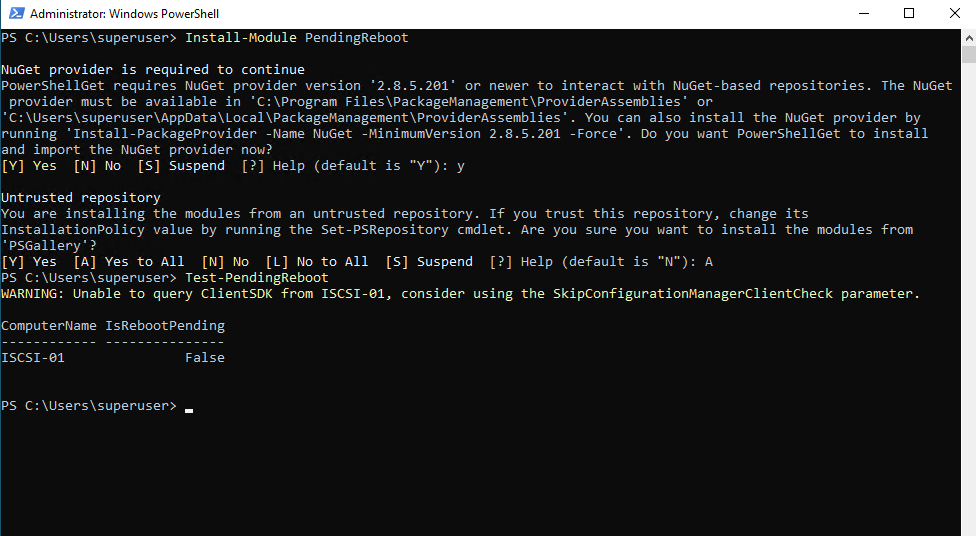
We can also use the Test-PendingReboot PowerShell cmdlet to determine if there are any pending reboot on our system.
PS> Install-Module PendingReboot PS> Test-PendingReboot
PS> Test-PendingReboot -Detailed
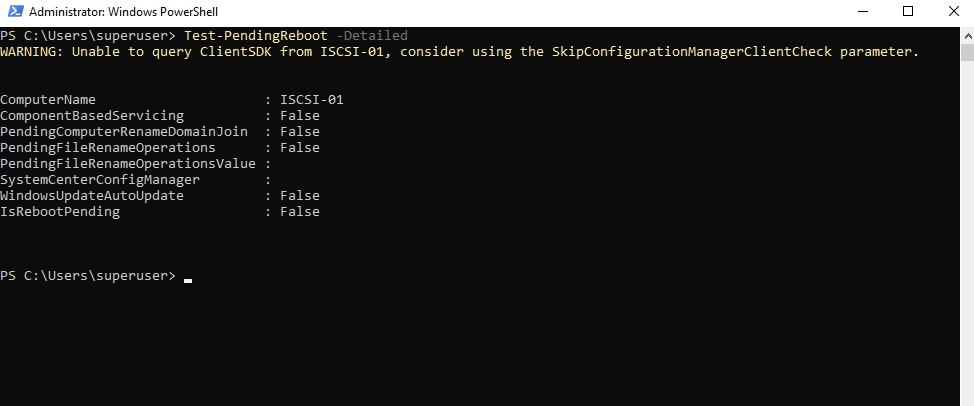
Source: https://www.powershellgallery.com/packages/Test-PendingReboot/1.7/Content/Test-PendingReboot.ps1
Install the PowerShell Module offline
In case the system has restricted internet access, we can also install the module offline by first downloading it on another machine.
PS> Find-Module -Name "PendingReboot" PS> Save-Module -Name "PendingReboot" -Path "C:\Users\superuser\Downloads"
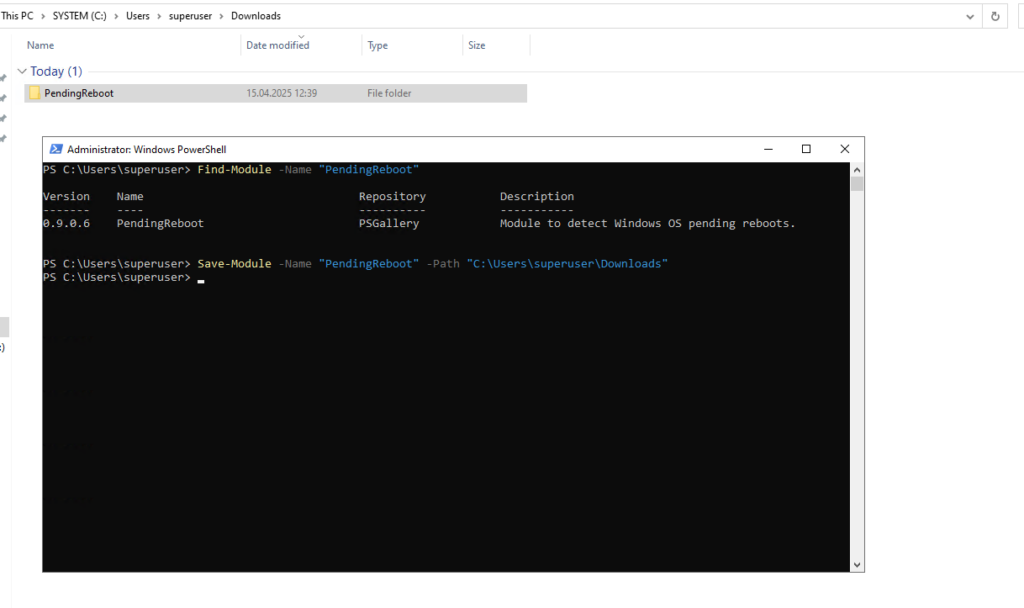
Copy the downloaded module to C:\Program Files\WindowsPowerShell\Modules on the machine with restricted internet access.
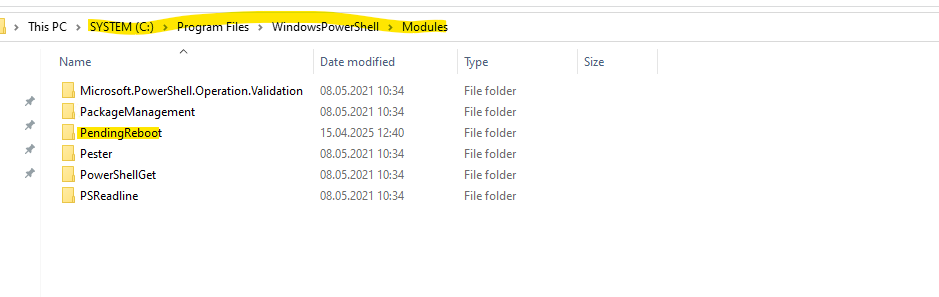
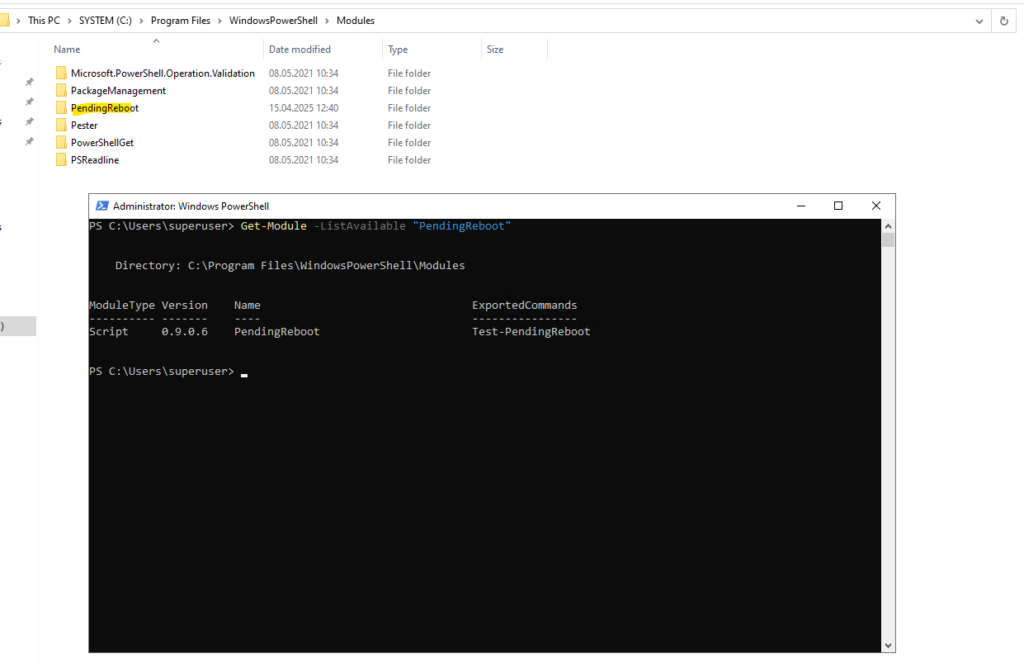
Testing if the module is now available on the machine we copied the module to.
PS> Get-Module -ListAvailable "PendingReboot"
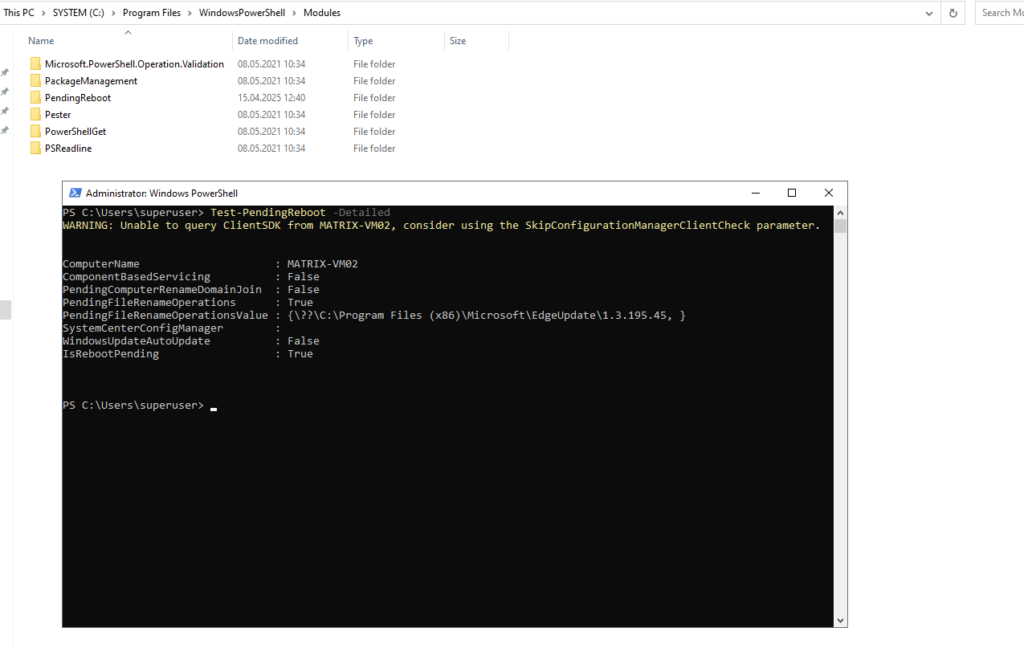
We can now run the PowerShell cmdlet.
PS> Test-PendingReboot -Detailed
As mentioned, in Part 2 we will see how we can onboard machines at scale to Azure Update Manager by using Azure Policy. Further we will see how we can create pre and post events for the update process.
Links
Azure Updates
https://azure.microsoft.com/en-us/updatesAbout Azure Update Manager
https://learn.microsoft.com/en-us/azure/update-manager/overviewAssessment options in Update Manager
https://learn.microsoft.com/en-us/azure/update-manager/assessment-optionsAzure Update Manager 2023 Edition (John Savill)
https://www.youtube.com/watch?v=LVmNh5YgBOQAzure Update Manager frequently asked questions
https://learn.microsoft.com/en-us/azure/update-manager/update-manager-faq#what-is-the-pricing-for-azure-update-managerHow Update Manager works
https://learn.microsoft.com/en-us/azure/update-manager/workflow-update-managerDeploy updates now and track results with Azure Update Manager
https://learn.microsoft.com/en-us/azure/update-manager/deploy-updates?tabs=install-single-overviewWhat is OVAL and how can I use it to learn about security issues?
https://access.redhat.com/solutions/4161What is Azure Resource Graph?
https://learn.microsoft.com/en-us/azure/governance/resource-graph/overviewAzure Monitor overview
https://learn.microsoft.com/en-us/azure/azure-monitor/overviewOverview of Log Analytics in Azure Monitor
https://learn.microsoft.com/en-us/azure/azure-monitor/logs/log-analytics-overviewLog Analytics tutorial
https://learn.microsoft.com/en-us/azure/azure-monitor/logs/log-analytics-tutoriManage additional Windows Update settings
https://learn.microsoft.com/en-us/windows/deployment/update/waas-wu-settingsPrerequisites for Azure Update Manager
https://learn.microsoft.com/en-us/azure/update-manager/prerequisitesConfiguring Automatic Updates by editing the registry
https://learn.microsoft.com/en-us/windows/deployment/update/waas-wu-settings#configuring-automatic-updates-by-editing-the-registrySupport matrix for Azure Update Manager
https://learn.microsoft.com/en-us/azure/update-manager/support-matrixTroubleshoot issues with Azure Update Manager
https://learn.microsoft.com/en-us/azure/update-manager/troubleshoot?tabs=azure-machinesWindows Update common errors and mitigation
https://learn.microsoft.com/en-us/troubleshoot/windows-client/installing-updates-features-roles/common-windows-update-errorsWindows Update issues troubleshooting
https://learn.microsoft.com/en-us/troubleshoot/windows-client/installing-updates-features-roles/windows-update-issues-troubleshootingPlan deployment for updating Windows VMs in Azure
https://learn.microsoft.com/en-us/azure/architecture/example-scenario/wsus/Manage additional Windows Update settings
https://learn.microsoft.com/en-us/windows/deployment/update/waas-wu-settingsAutomatic Guest Patching for Azure Virtual Machines and Scale Sets
https://learn.microsoft.com/en-us/azure/virtual-machines/automatic-vm-guest-patchingWhat Permission is required for configuring Azure policy
https://learn.microsoft.com/en-us/answers/questions/1634444/what-permission-is-required-for-configuring-azure
Tags In
Related Posts
Follow me on LinkedIn


