Microsoft Azure Management Groups
In this post I want to summarize some information about Azure Management Groups to organize and manage multiple subscriptions in your Azure AD directory (tenant).
Each directory (tenant) is given a single top-level management group called the root management group.
Azure Management Groups are frequently compared and mentioned as counterpart in the web to Google Cloud’s organization resource or AWS organizations.
About the differences between them you can read my following post.
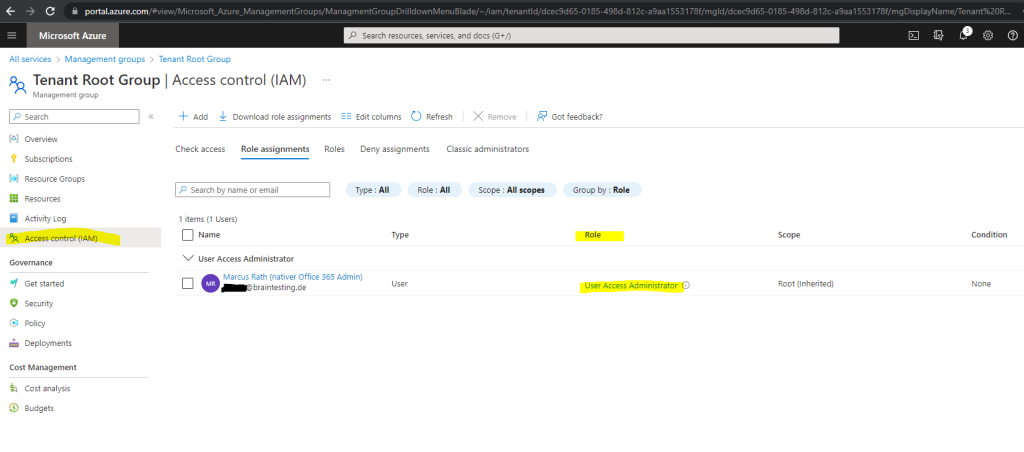
If you try as Global Administrator in Azure Active Directory (Azure AD) the first time to access the management groups, you may wonder why you haven’t access to as shown below for my lab environment.
You are registered as a directory admin but do not have the necessary permissions to access the root management group.
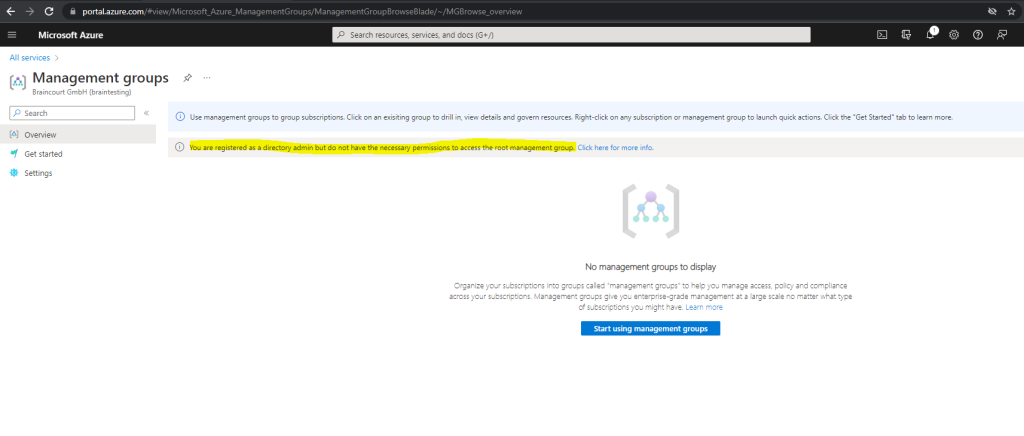
So why would you need to elevate your access?
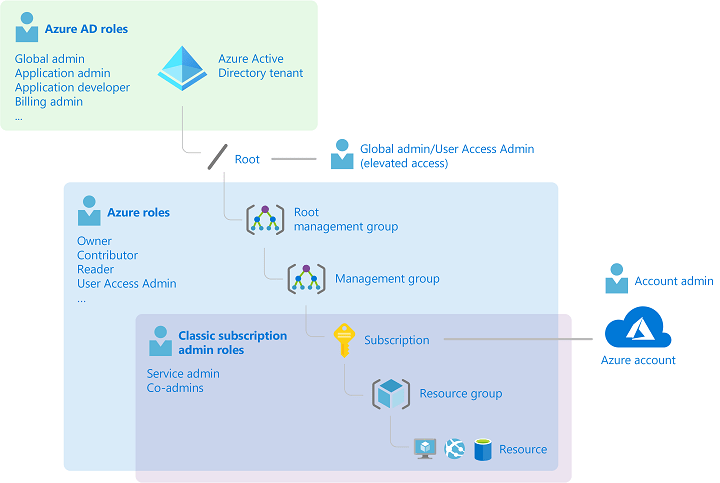
Azure AD and Azure resources are secured independently from one another. That is, Azure AD role assignments do not grant access to Azure resources, and Azure role assignments do not grant access to Azure AD.
Differences between Azure roles and Azure AD roles
At a high level, Azure roles control permissions to manage Azure resources, while Azure AD roles control permissions to manage Azure Active Directory resources.
However, if you are a Global Administrator in Azure AD, you can assign yourself access to all Azure subscriptions and management groups in your directory. Use this capability if you don’t have access to Azure subscription resources, such as virtual machines or storage accounts, and you want to use your Global Administrator privilege to gain access to those resources.
When you elevate your access, you will be assigned the User Access Administrator role in Azure at root scope (
/). This allows you to view all resources and assign access in any subscription or management group in the directory. User Access Administrator role assignments can be removed using Azure PowerShell, Azure CLI, or the REST API.Source: https://learn.microsoft.com/en-us/azure/role-based-access-control/elevate-access-global-admin
So if you are a Global Administrator in your Azure tenant (directory), you can elevate yourself to access all subscriptions and management groups in your tenant.
Therefore you just need to click on properties in Azure Active Directory and click on yes under Access management for Azure resources as shown below.
Finally don’t forget to save the settings.
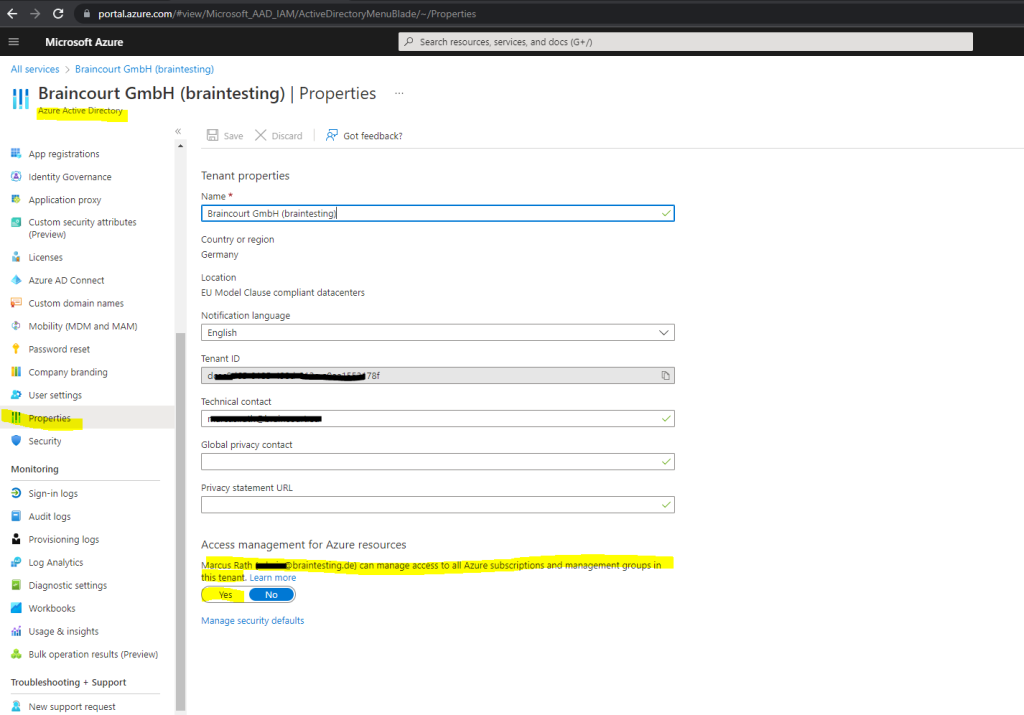
When you set the toggle to Yes, you are assigned the User Access Administrator role in Azure RBAC at root scope (/). This grants you permission to assign roles in all Azure subscriptions and management groups associated with this Azure AD directory. This toggle is only available to users who are assigned the Global Administrator role in Azure AD.
Source: https://learn.microsoft.com/en-us/azure/role-based-access-control/elevate-access-global-admin
From now on I will see the root management group and can also click on it to change settings and mange access.
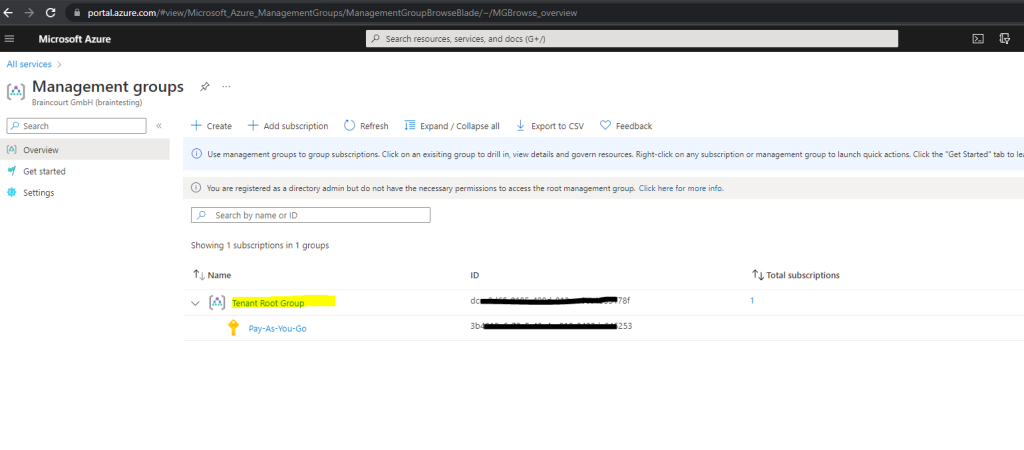
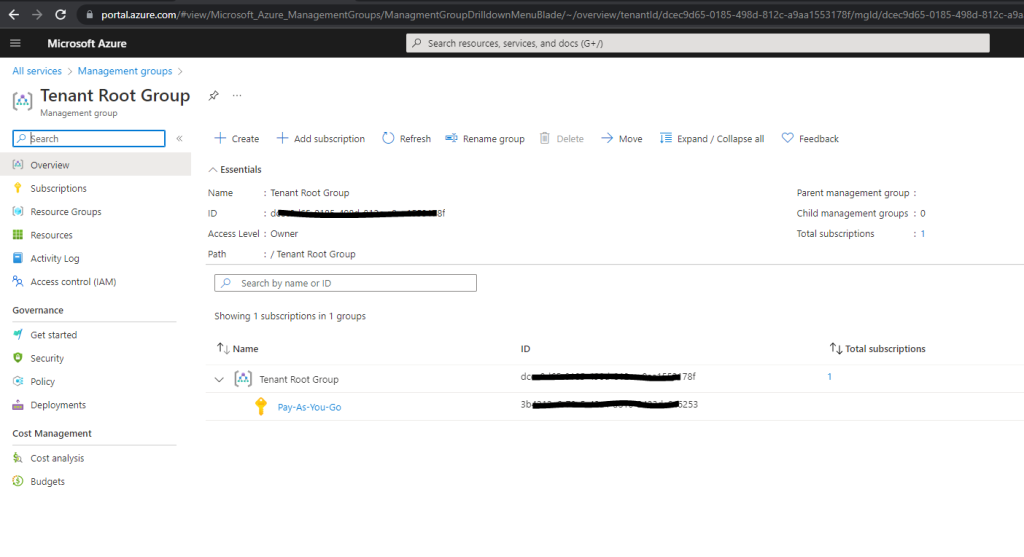
What are Azure management groups?
If your organization has many Azure subscriptions, you may need a way to efficiently manage access, policies, and compliance for those subscriptions.
Management groups provide a governance scope above subscriptions.
You organize subscriptions into management groups; the governance conditions you apply cascade by inheritance to all associated subscriptions.
Management groups give you enterprise-grade management at scale no matter what type of subscriptions you might have. However, all subscriptions within a single management group must trust the same Azure Active Directory (Azure AD) tenant.
For example, you can apply policies to a management group that limits the regions available for virtual machine (VM) creation. This policy would be applied to all nested management groups, subscriptions, and resources, and allow VM creation only in authorized regions.
Hierarchy of management groups and subscriptions
You can build a flexible structure of management groups and subscriptions to organize your resources into a hierarchy for unified policy and access management. The following diagram shows an example of creating a hierarchy for governance using management groups.
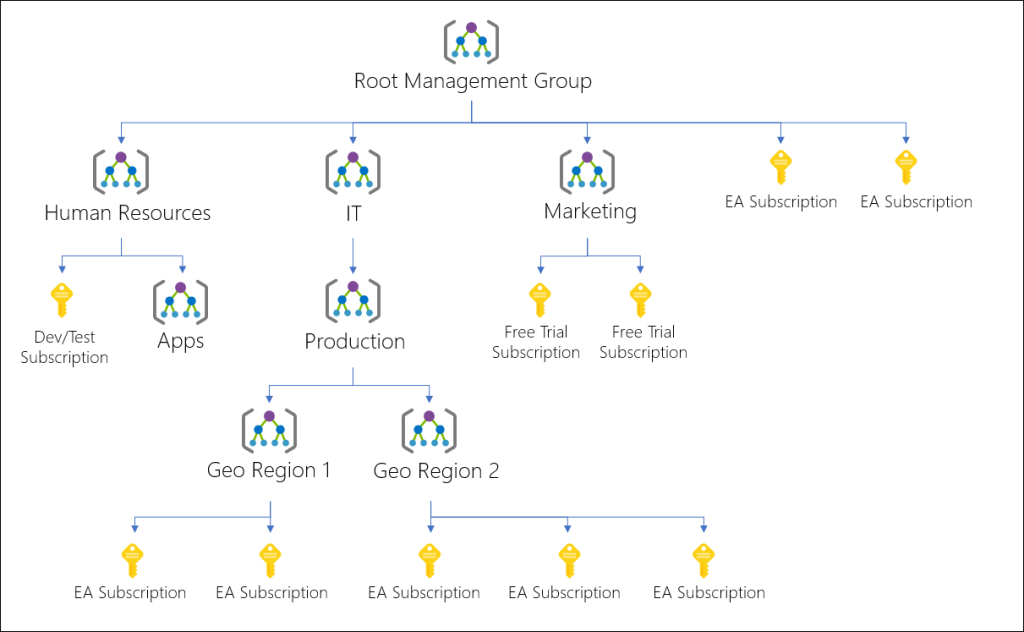
You can create a hierarchy that applies a policy, for example, which limits VM locations to the West US region in the management group called “Production”. This policy will inherit onto all the Enterprise Agreement (EA) subscriptions that are descendants of that management group and will apply to all VMs under those subscriptions. This security policy cannot be altered by the resource or subscription owner allowing for improved governance.
Another scenario where you would use management groups is to provide user access to multiple subscriptions. By moving multiple subscriptions under that management group, you can create one Azure role assignment on the management group, which will inherit that access to all the subscriptions. One assignment on the management group can enable users to have access to everything they need instead of scripting Azure RBAC over different subscriptions.
Source: https://learn.microsoft.com/en-us/azure/governance/management-groups/overview
What’s the difference between Azure roles and Azure AD roles?
As previously further above already mentioned, at a high level, Azure roles control permissions to manage Azure resources, while Azure AD roles control permissions to manage Azure Active Directory resources.
Below you will find an great article from @Sonia Cuff which takes a closer look about the differences between Azure roles and Azure AD roles.
What’s the difference between Azure roles and Azure AD roles?
https://techcommunity.microsoft.com/t5/itops-talk-blog/what-s-the-difference-between-azure-roles-and-azure-ad-roles/ba-p/2363647
In a nutshell from her article.
Azure roles
The four fundamental roles are:
- Owner – Full rights to change the resource and to change the access control to grant permissions to other users.
- Contributor – Full rights to change the resource, but not able to change the access control.
- Reader – Read-only access to the resource
- User Access Administrator – No access to the resource except the ability to change the access control.
For a full list of the built-in roles and their permissions, visit Azure built-in roles.
Learn more about custom roles.
Azure AD roles
The Azure AD roles include:
- Global administrator – the highest level of access, including the ability to grant administrator access to other users and to reset other administrator’s passwords.
- User administrator – can create and manage users and groups, and can reset passwords for users, Helpdesk administrators and User administrators.
- Helpdesk administrator – can change the password for users who don’t have an administrator role and they can invalidate refresh tokens, which forces users to sign back in again.
- Billing Administrator – can make purchases and manage subscriptions.
For a full list of Azure AD built-in roles visit Azure AD roles or learn how to create and assign a custom role in Azure Active Directory.
Links
Azure management groups documentation
https://learn.microsoft.com/en-us/azure/governance/management-groups/What are Azure management groups?
https://learn.microsoft.com/en-us/azure/governance/management-groups/overviewWhat’s the difference between Azure roles and Azure AD roles?
https://techcommunity.microsoft.com/t5/itops-talk-blog/what-s-the-difference-between-azure-roles-and-azure-ad-roles/ba-p/2363647Classic subscription administrator roles, Azure roles, and Azure AD roles
https://learn.microsoft.com/en-us/azure/role-based-access-control/rbac-and-directory-admin-roles


