pfSense enable Logging for Firewall Rules to log internal Client IPs
By default for outbound internet traffic with NAT you won’t see the internal client ip addresses in the firewall logs of pfSense.
pfSense by default only will log the NAT address and destination address.
So if you want to check and see which internal client was connected to a specific internet destination, you have to enable Log packets that are handled by this rule at the specific rule which allows the client to access this destination.
For example you can see here a rule which generally allows all outbound IPv4 traffic. Also you can see the symbol besides the green hook which shows that the traffic for this rule will be logged from pfsense.
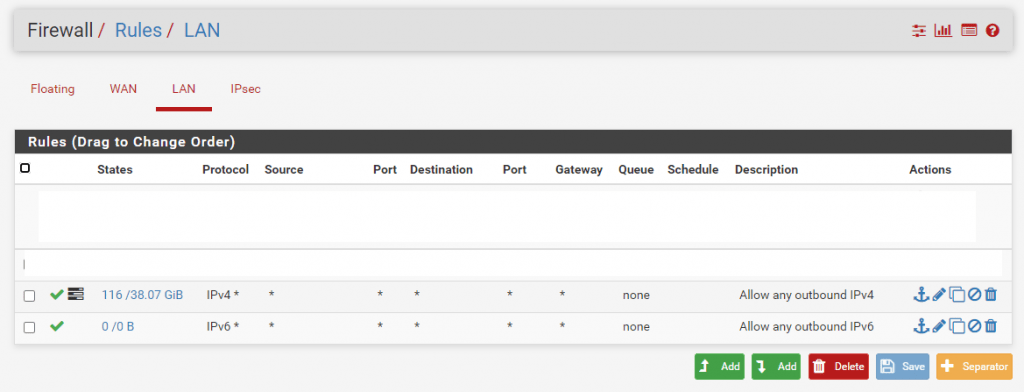
If you edit the rule you can enable or disable this option, by default it is not enabled.
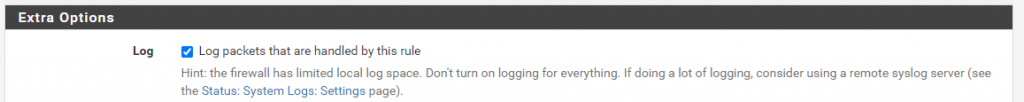
Keep in mind if you enable this option, to have enough space for the logs or using a remote syslog server.
How to set up a syslog server with the syslog-ng package read the following post.



