Replace the self-signed Remote Desktop Certificate with an PKI Certificate from your internal CA
brief, General
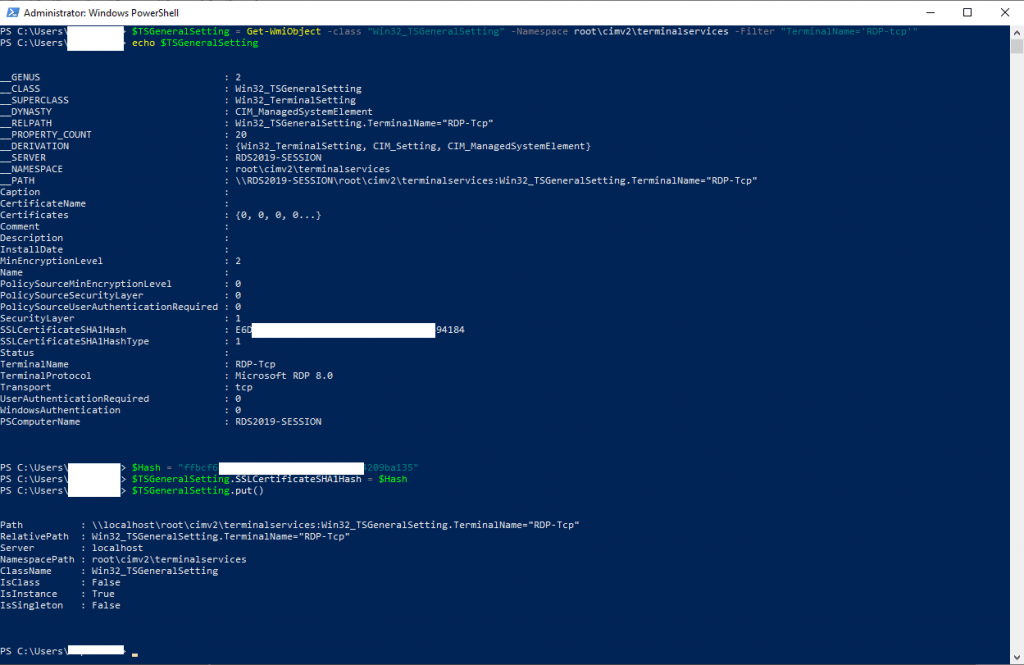
Copy the Thumbprint of the Certificate you want to use for the RDP Connection and copy it to the $Hash variable.
$TSGeneralSetting = Get-WmiObject "Win32_TSGeneralSetting" -ComputerName "<Server Name>" -Namespace rootcimv2terminalservices -Filter "TerminalName='RDP-tcp'" $Hash = "<hash of new certificate>" $TSGeneralSetting.SSLCertificateSHA1Hash = $Hash $TSGeneralSetting.put()
Or via command line
wmic /namespace:\rootcimv2TerminalServices PATH Win32_TSGeneralSetting Set SSLCertificateSHA1Hash="<THUMBPRINT>"
After fire off the put() command, the new Certificate will kick in! No need to restart the computer.
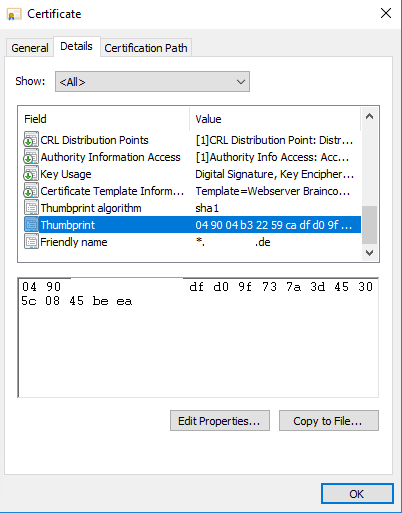
Copy the thumbprint from the new certficate over the details tab from the certificate and paste it into powershell to cut out the spaces.
Since Windows Server 2019 the thumbprint will be displayed without spaces within the certificate itself?.
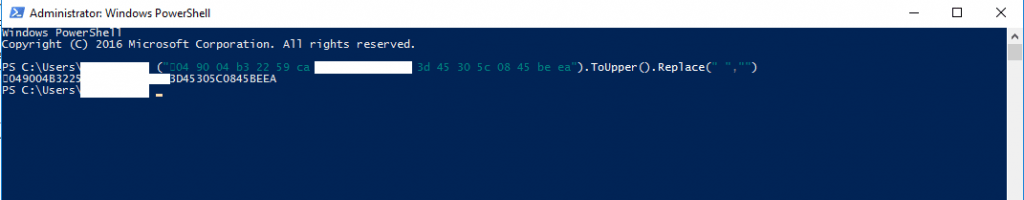
But before you can use the powershell replace command instead deleting it manual.
Follow me on LinkedIn


