Set up a Central Log Server with syslog-ng daemon on SUSE Linux Enterprise Server
Centralized logging is essential for monitoring, troubleshooting, and securing enterprise systems. On SUSE Linux Enterprise Server (SLES), the syslog-ng daemon offers a flexible and powerful way to collect, filter, and forward log messages from various sources.
In this post, we will see step by step how to set up syslog-ng on SLES, configuring it for common use cases, and ensuring your logs are structured and accessible for analysis.
Introduction
The syslog-ng daemon is a log management service that acts as a central logging engine on Unix-like systems, including SUSE Linux Enterprise Server (SLES).
It captures, processes, filters, and forwards log messages generated by applications, system components, or remote machines.
When an application logs a message (e.g., login attempt, service failure), syslog-ng reads it from a source (like /dev/log), processes it based on configured rules, and writes it to a local file, console, or sends it to a central log server.
In essence, syslog-ng is a more advanced and configurable alternative to traditional syslog daemons, giving system administrators granular control over how logs are handled.
Install the syslog-ng Daemon
First we need to determine which repository contains the syslog-ng package we want to install by executing the following command.
# zypper search-packages syslog-ng
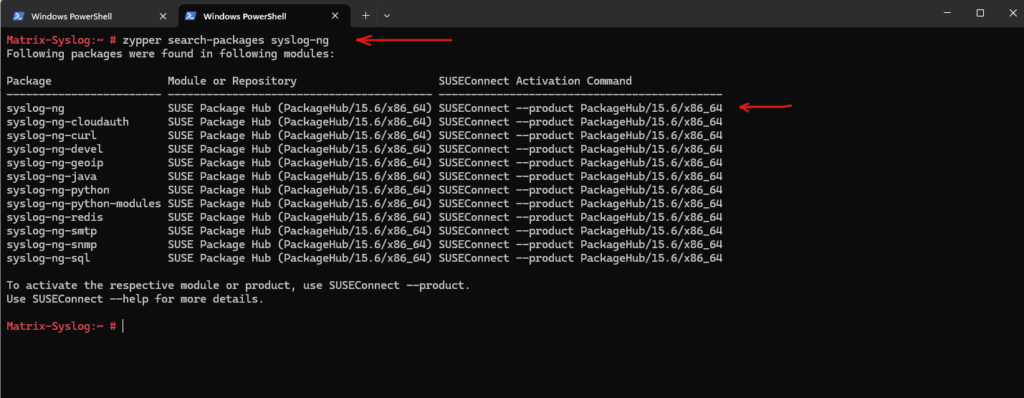
To connect this repository run the following command.
# SUSEConnect --product PackageHub/15.6/x86_64
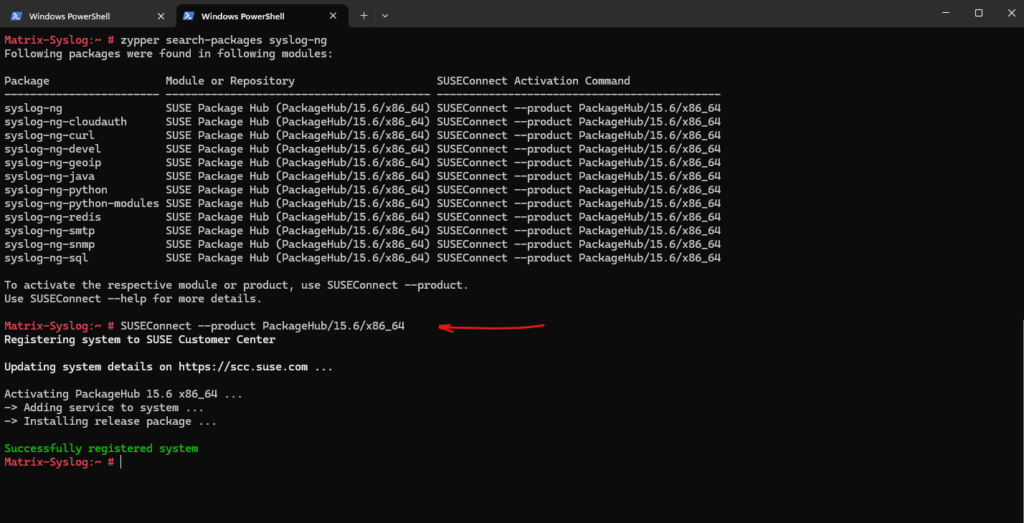
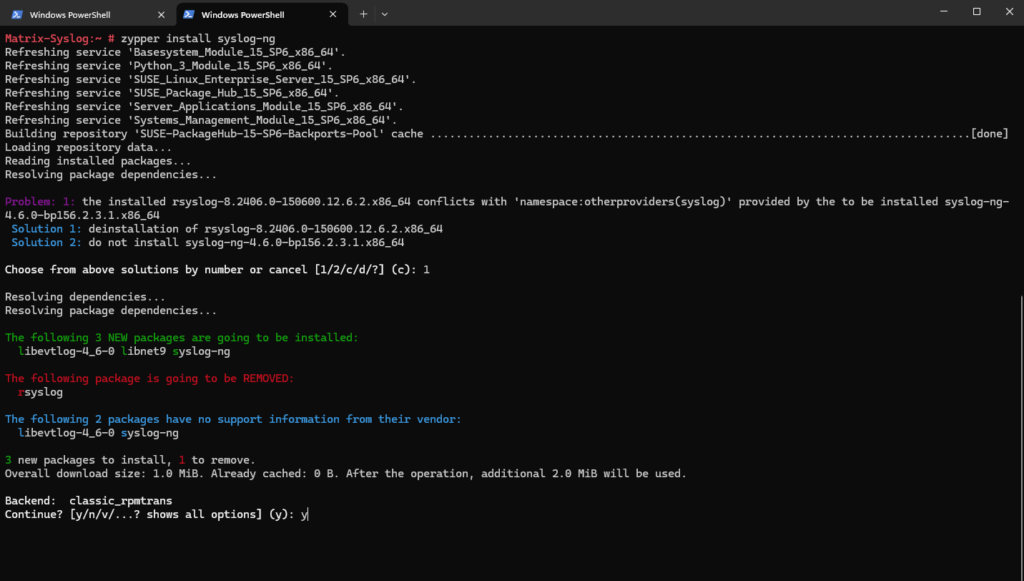
We can now install the syslog-ng package by running. We also first need to uninstall the by default installed rsyslog package which conflicts with syslog-ng, to uninstall just select solution 1 below.
# zypper install syslog-ng
Use rsyslog if you want speed, you’re in a high-load environment, or you’re using a distro that defaults to it.
Use syslog-ng if you need more flexibility, easier config management, or structured logging.
If you’re managing logs for security or compliance, syslog-ng may give you an edge with its more powerful filtering and formatting features. For sheer speed and wide support, rsyslog is hard to beat.
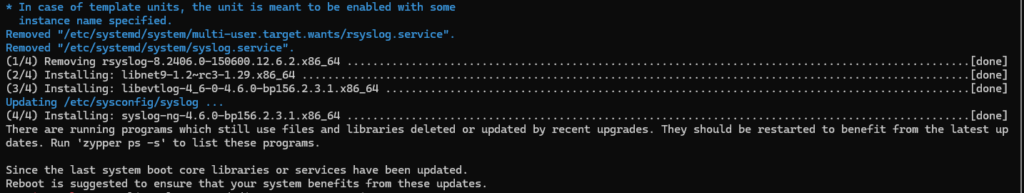
Configure syslog-ng
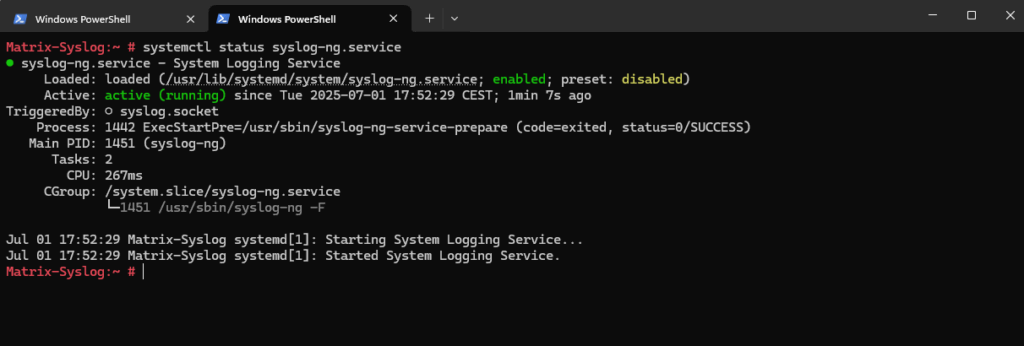
The syslog-ng daemon is already enabled and running after the installation.
# systemctl status syslog-ng.service
To configure syslog-ng we need to edit the main configuration file under /etc/syslog-ng/syslog-ng.conf.
# vi /etc/syslog-ng/syslog-ng.conf
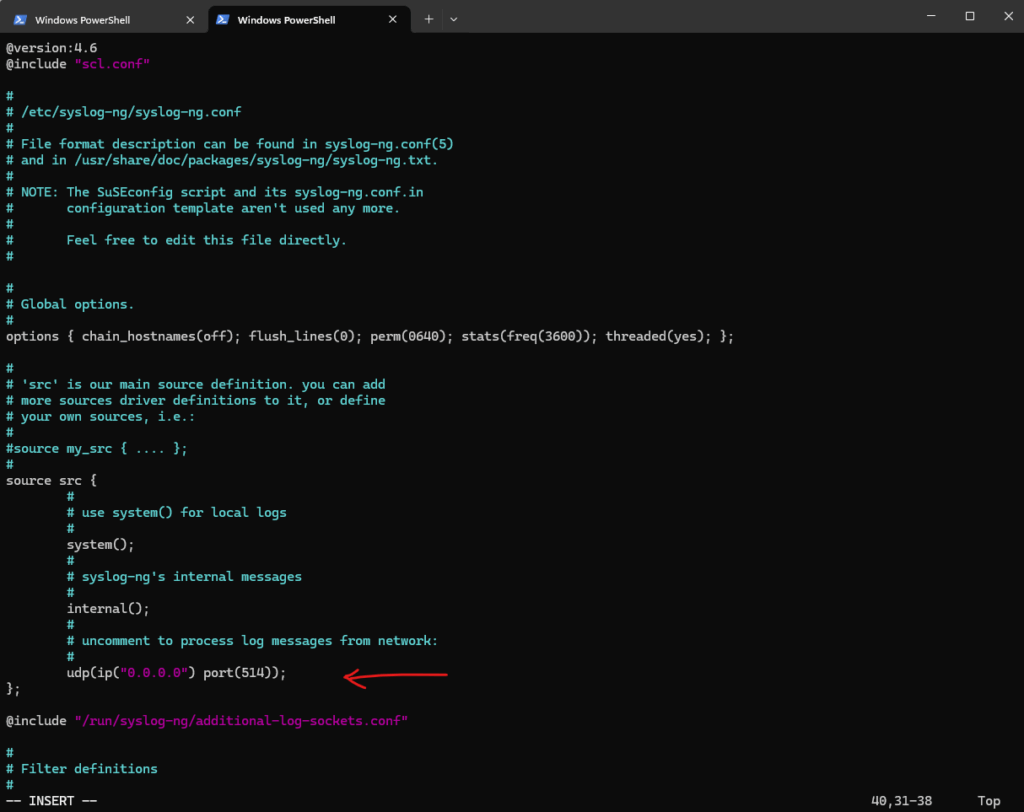
We now need to configure the host to collect and receive syslog messages from remote servers.
First uncomment the following line to process log messages from remote servers.
Here the host will listen on all its IP addresses and UDP port 514 for incoming log messages from remote servers.
source src {
#
# use system() for local logs
#
system();
#
# syslog-ng's internal messages
#
internal();
#
# uncomment to process log messages from network:
#
udp(ip("0.0.0.0") port(514));
};
Next I will create a folder to store the log messages from remote servers.
# mkdir -p /loghost/dailylogs/ # chmod 755 /loghost # chmod 755 /loghost/dailylogs
Also be sure the user which is running the syslog-ng daemon have permissions to write to the directory. To determine the user run the following command.
# ps aux | grep syslog-ng
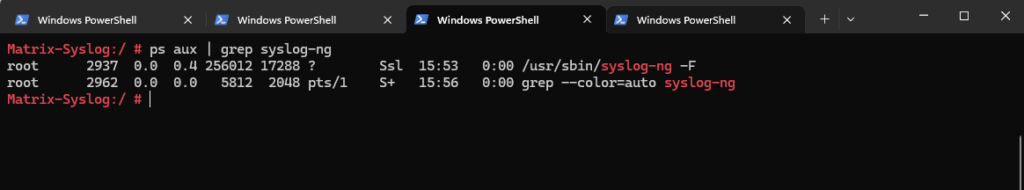
So in my case the root user by default have permissions to write to the directory. In case you will use some different user run the following command to set the ownership and permissions for.
# chown <user>:<group> /loghost/ /loghost/dailylogs/ # chmod 755 /loghost # chmod 755 /loghost/dailylogs
Also we must tell syslog-ng where to save the logs from the remote server.
The destination d_host_daily parameter will define the destination /loghost/dailylogs/$HOST.$WEEKDAY.log where $HOST is the remote host and $WEEKDAY is Mon, Tue, Wed, etc.
The files will be created automatically with the right owner and permissions. This configuration saves the logs for one week with a separate log file for each host and weekday.
Each log file is overwritten the next week automatically.
overwrite-if-older()
https://www.syslog-ng.com/technical-documents/doc/syslog-ng-open-source-edition/3.18/administration-guide/overwrite-if-older
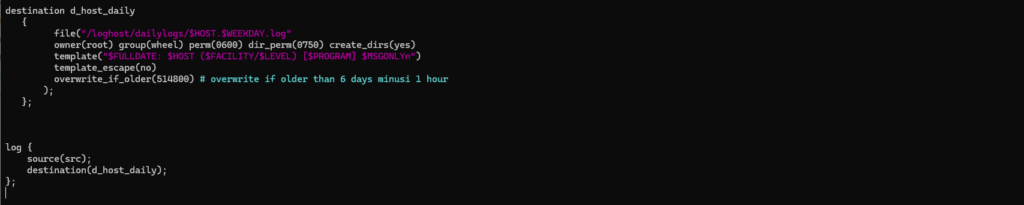
destination d_host_daily
{
file("/loghost/dailylogs/$HOST.$WEEKDAY.log"
owner(root) group(wheel) perm(0600) dir_perm(0750) create_dirs(yes)
template("$FULLDATE: $HOST ($FACILITY/$LEVEL) [$PROGRAM] $MSGONLYn")
template_escape(no)
overwrite_if_older(514800) # overwrite if older than 6 days minus 1 hour
);
};We also need to tell the syslog-ng daemon to finally start logging with the code below.
log {
source(src);
destination(d_host_daily);
};
Restart the syslog-ng daemon.
# systemctl restart syslog-ng.service
Putting AppArmor Profile for syslog-ng into Complain Mode
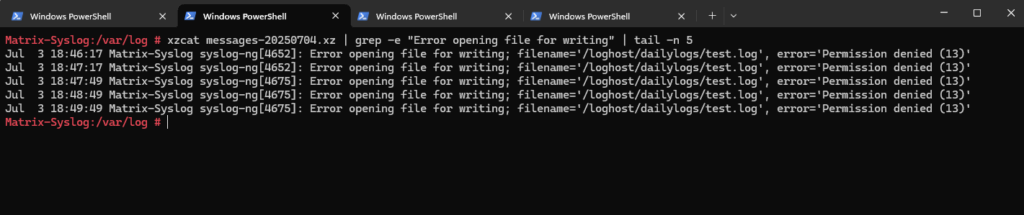
So far on SUSE Linux Enterprise 15 by default the syslog-ng daemon couldn’t write the logs into our previously defined and created path /loghost/dailylogs/ as shown in /var/log/messages.
Error opening file for writing; filename=’/loghost/dailylogs/test.log’, error=’Permission denied (13)’
Jul 3 18:47:17 Matrix-Syslog syslog-ng[4652]: Error opening file for writing; filename=’/loghost/dailylogs/test.log’, error=’Permission denied (13)’
The syslog-ng daemon is running here with the root user account and the ownership and permissions we set previously correct resp. for the root user they were already set by default.
The reason for why writing into this directory nevertheless isn’t working so far and we run into this permission denied error is related to AppAmor.
AppArmor is blocking syslog-ng from writing to /loghost/dailylogs/ due to profile restrictions, causing the “Permission denied” errors.
AppArmor is an effective and easy-to-use Linux application security system. AppArmor proactively protects the operating system and applications from external or internal threats, even zero-day attacks, by enforcing good behavior and preventing both known and unknown application flaws from being exploited.
AppArmor supplements the traditional Unix discretionary access control (DAC) model by providing mandatory access control (MAC). It has been included in the mainline Linux kernel since version 2.6.36 and its development has been supported by Canonical since 2009.
Source: https://apparmor.net/
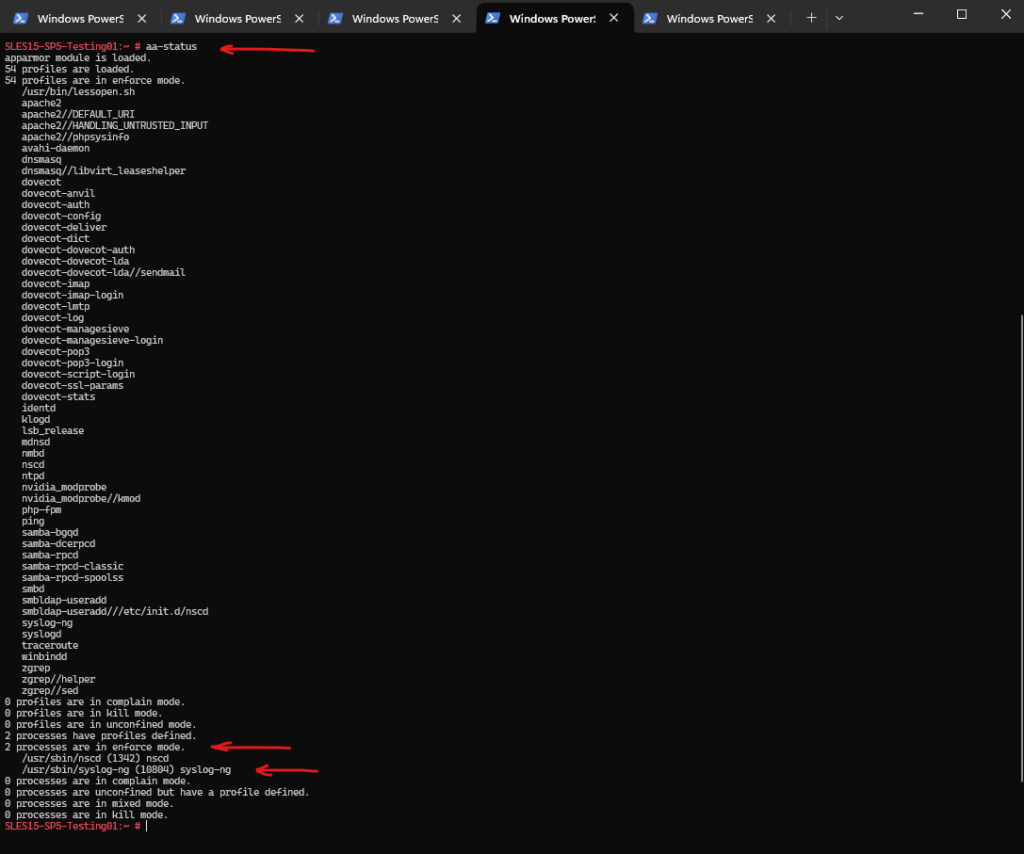
To check the current status of AppArmor on the syslog server run the following command.
- Enforce mode blocks and denies any actions that don’t comply with the profile rules — like writing files in certain directories.
- Complain mode allows those actions but logs warnings instead of blocking.
Below we will see the profile of a remote client where also syslog-ng is installed which is sending log messages to the syslog server, on the real syslog server I have already adjusted the AppAmor profile to allow writing log into our defined path.
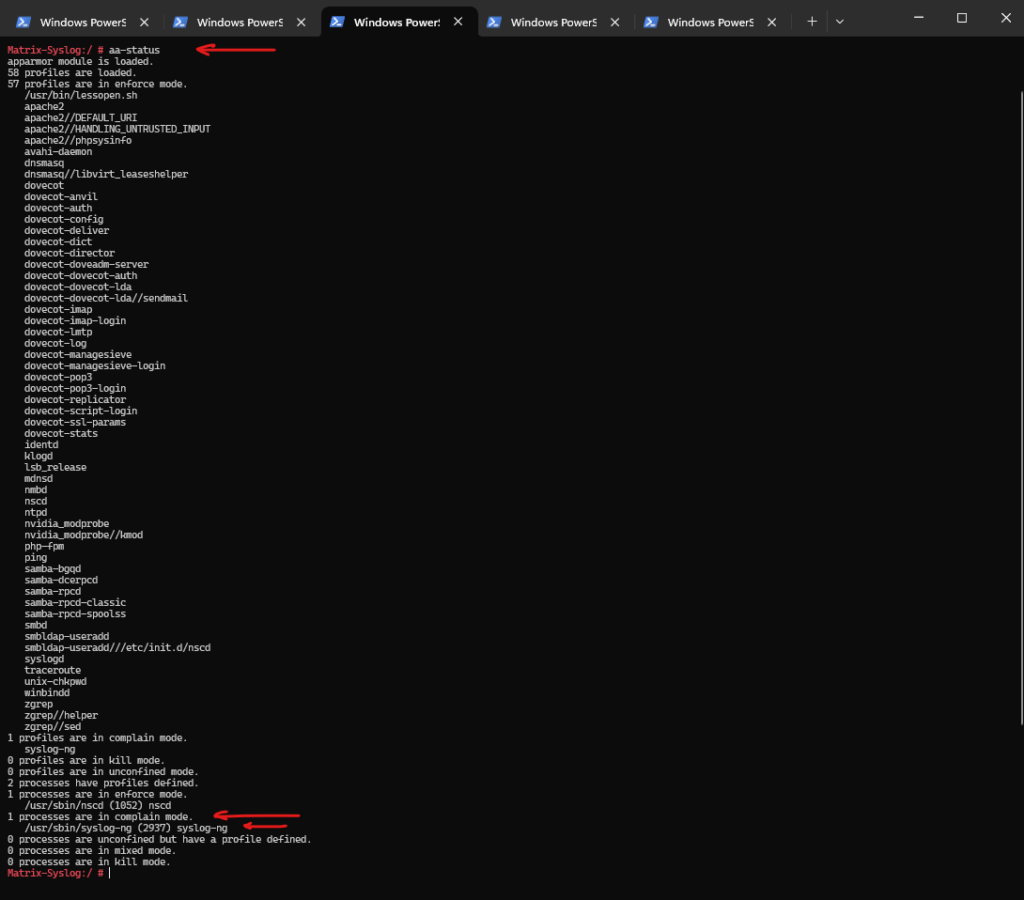
# aa-status
By default the /user/sbin/syslog-ng daemon (binary) is configured in enforced mode and therefore the daemon couldn’t write logs into this path.
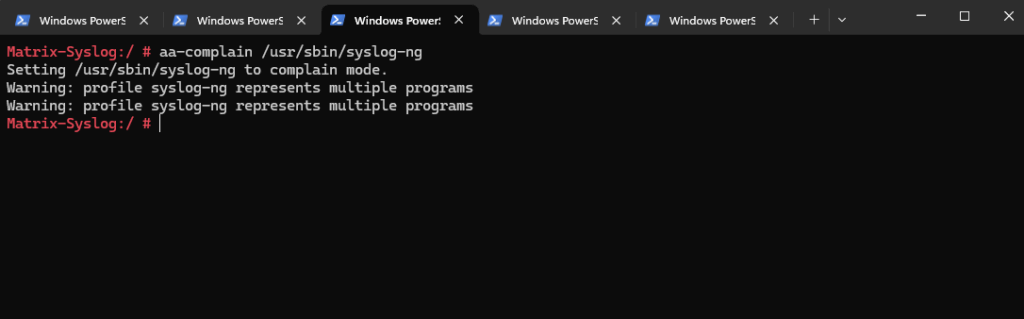
To resolve this and to allow the syslog-ng daemon to finally write logs into /loghost/dailylogs/, we need to put /user/sbin/syslog-ng daemon (binary) into complain mode by running.
# aa-complain /usr/sbin/syslog-ng
We can check it again by running the following command, looks good.
# aa-status
Finally restart syslog-ng. From now the syslog-ng daemon should write logs from remote hosts into this path.
# systemctl restart syslog-ng.service
If you want to fix this permanently, you can adjust the AppArmor profile to allow the needed file access, then put it back in enforce mode. Otherwise, complain mode is useful for troubleshooting or temporary relief.
Test Logging
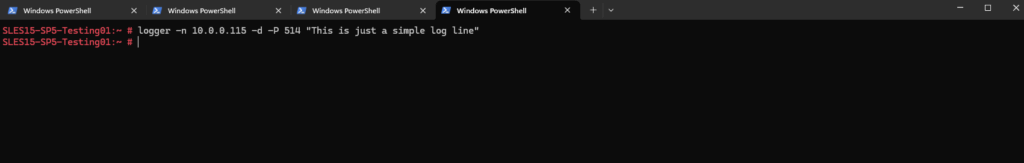
To test if logging works, we can sent some test syslog messages from a remote host by running the following command on it
logger –> A standard Linux command to send messages to the syslog system.
-n 10.0.0.115 –> Sends the log message to the remote host with IP 10.0.0.115.
-d –> Enables debug mode — shows what logger is doing (useful for troubleshooting).
-p 514 –> Specifies the destination port, 514 is the default port for syslog over UDP.
“This is just a simple log line” –> The log message being sent.
# logger -n 10.0.0.115 -d -P 514 "This is just a simple log line"
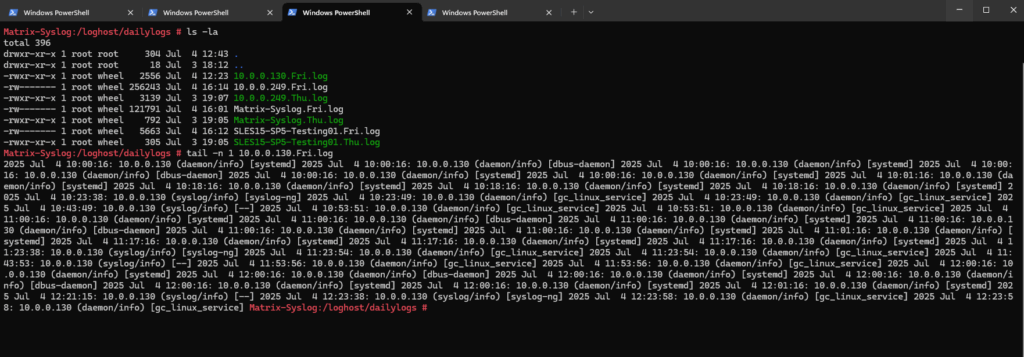
On the syslog-ng server we can check the logfiles which will be stored as configured in /loghost/dailylogs/.
You will also find in my following posts more about syslog-ng and rsyslog.
Links
Latest posts
Deploying NetApp Cloud Volumes ONTAP (CVO) in Azure using NetApp Console (formerly BlueXP) – Part 5 – Backup and Recovery
Follow me on LinkedIn


