What’s the Difference in Linux between the Commands SU – vs. SU without the Dash
The difference between su – and su in Linux is primarily related to how they handle the user environment after switching users.
su – <other user> (with a dash)
This command switches to the specified user and loads the target user’s full login environment, similar to how it would be if the user logged in directly.When just entering su – without a given user you will switch to the root user.
A new login shell is started, and environment variables such as HOME, SHELL, USER, PATH, etc., are set according to the target user’s login configuration (as defined in their shell startup files like .bash_profile or .profile).
After running this, you would be switched to root and land in /root, with all the environment variables set as if you logged in as root directly.

su <other user> (without the dash)
This command switches to the specified user but does not load the target user’s full login environment.When just entering su without a given user you will switch to the root user.
The environment variables (like PATH, HOME, etc.) remain mostly the same as the original user’s, with a few exceptions (such as the USER and SHELL environment variables being updated).
After running this, you stay in the same directory, and some environment variables are inherited from the current user session.

In case we just want to run individual commands as another user (typically root) without switching to that user entirely. It is more fine-grained to use the sudo command over su because it grants temporary, limited elevated privileges for the execution of a specific command.
By using sudo you remain as your normal user but can run commands as another user (commonly root) with the necessary privileges.
- su requires you to know the password of the target user (typically root). Once you switch users, you have unrestricted access to everything that user can do for the entire session. This can be a security risk because anyone who gains access to the root account can have full control over the system.
- sudo uses a least-privilege model. You do not need to know the root password, just your own password (and the sudoers file must grant you permission to run the command). The access is temporary and command-specific, reducing the security risk compared to su.
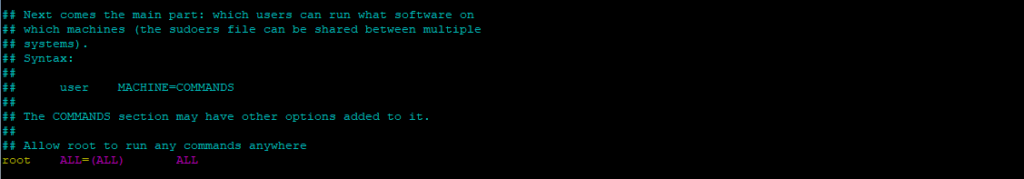
The /etc/sudoers file defines who can run commands via sudo and which commands they can run. The root user is of course allowed by default to run any commands anywhere.
This means the user marcus can run any command using sudo.
marcus ALL=(ALL) ALL
In Unix operating systems, the term wheel refers to a user account with a wheel bit, a system setting that provides additional special system privileges that empower a user to execute restricted commands that ordinary user accounts cannot access.
Modern Unix systems generally use user groups as a security protocol to control access privileges. The wheel group is a special user group used on some Unix systems, mostly BSD systems, to control access to the su or sudo command, which allows a user to masquerade as another user (usually the super user).
On RHEL 9 by default the wheel group is enabled.
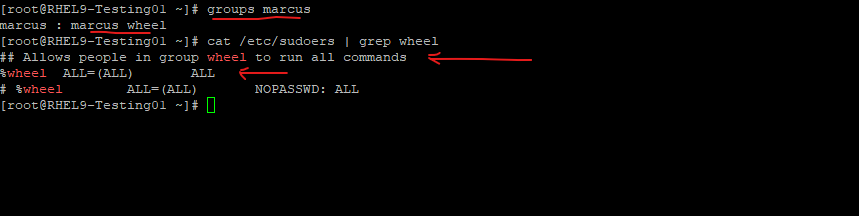
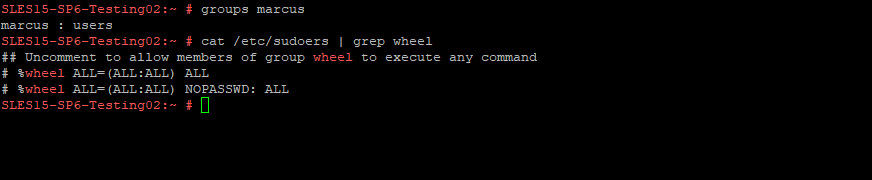
On SLES 15 the wheel group is commented and not enabled.
Adding a user account to the group wheel.
:~> sudo usermod -a -G wheel USERNAME -a --append -> append the user to the supplemental Groups mentioned in the -G option without removing the user from other groups.
To remove a user from the group wheel run.
:~> sudo gpasswd -d USERNAME wheel
Links
Using sudo without root password
https://documentation.suse.com/sles/15-SP5/html/SLES-all/cha-adm-sudo.html#sec-sudo-usecases-userpwUser authorizations in sudoers
https://docs.redhat.com/en/documentation/red_hat_enterprise_linux/9/html/configuring_basic_system_settings/managing-sudo-access_configuring-basic-system-settings#con_user-authorizations-in-sudoers_managing-sudo-access


