Linux Sudoers (sudo command) File
Below I will summarize some information about the Linux sudoers file. The file will grant priviliges to users and groups what commands they allowed to execute by using the sudo command on the system.
sudo is a program for Unix-like computer operating systems that enables users to run programs with the security privileges of another user, by default the superuser. It originally stood for superuser do, as that was all it did, and it is its most common usage; however, the official Sudo project page lists it as su do. The current Linux manual pages for su define it as substitute user, making the correct meaning of sudo substitute user, do, because sudo can run a command as other users as well.
The /etc/sudoers file contains a list of users or user groups with permission to execute a subset of commands while having the privileges of the root user or another specified user. The program may be configured to require a password.
To determine which users or groups are member of the sudo group, you can use the following commands.
$ getent group sudo

To list all groups the user is member of.
$ groups <username>
For the logged on user just
$ groups
Further you can also directly check the sudoers file to which users or groups are root priviliges been granted.
/etc/sudoers
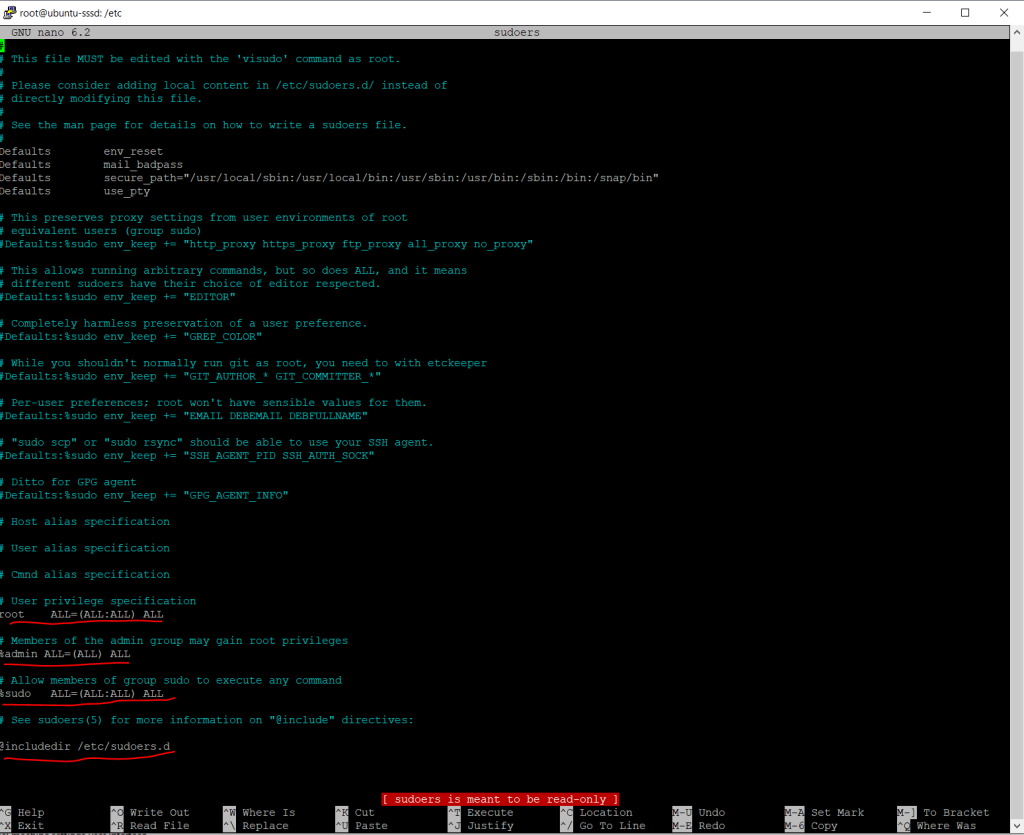
The above privileges in short
- root ALL=(ALL:ALL) ALL
The root user can execute all commands by using sudo even not necessary for most commands besides for example user impersonation. - %admin ALL=(ALL) ALL
The admin group is granted root permission. A group is defined here by using the % symbol as prefix. The admin group has been deprecated and no longer exists since Ubuntu 12.04 and is just for backwards compatibility included here. - %sudo ALL=(ALL:ALL) ALL
The sudo group is granted root permission so that members can execute all commands by using the sudo command.
(ALL:ALL) means that members of the group can execute all commands for each user and each group on the system. - %google-sudoers ALL=(ALL:ALL) NOPASSWD:ALL
Further down I will show an example of a sudoers file from a Google Cloud Linux VM instance, they will include that privilege.
The google-sudoers group is granted root permission so that members can execute all commands by using the sudo command.
NOPASSWD:ALL means that members can execute commands without prompted for password.
When checking the sudoers file for privileges you also have to check the @include directives at the end of the file and screenshot as shown above. Here also all files present in the directory /etc/sudoers.d will be included.
In my case no further file with privileges will be included and in the directory just the README file is present.

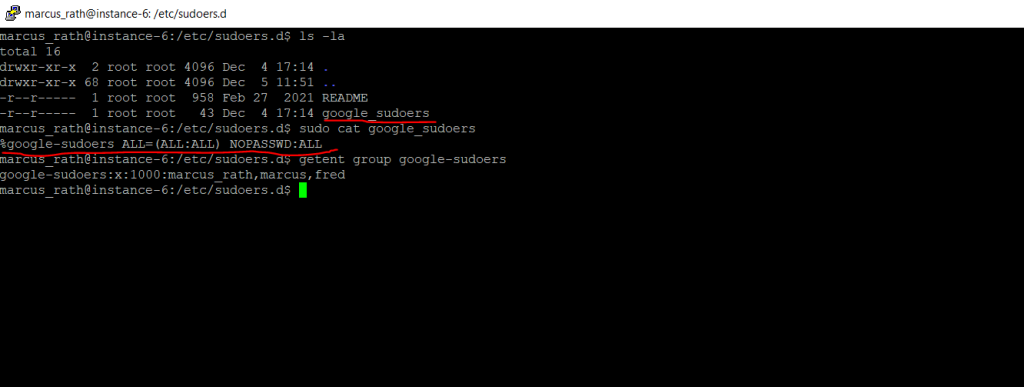
Below is a nice example for a Google Cloud Linux VM instance, where the users or groups will not be added directly to the sudo group in the /etc/sudoers file but instead a group named google_sudoers will be granted root privileges by using a separate file also named google_sudoers in the /etc/sudoers.d directory.
So in this case all users which are members in the google_sudoers group, will be granted root priviliges and because of the NOPASSWD:ALL entry they didn’t even need to enter their password for executing the sudo command.
Besides after all that privileges and permissions stuff, in case you wonder where exactly is the difference between privileges and permissions, in a nutshell below.
Permissions are associated with resources/objects like files or folders for example. They define who is allowed to perform what actions on the object like read, modify, write or delete.
So permissions are bound directly to the resource/object.
In contrast privileges are assigned permissions to an user or group. So when you assign for example the read permissions for an object like a file to an user, the user have the privilege to read the file.
Links
sudo
https://en.wikipedia.org/wiki/Sudosudoers(5) – Linux man page
https://linux.die.net/man/5/sudoers



