Enable Hybrid Modern Authentication for on-premises Skype for Business and Exchange servers – Part 1 Exchange Server
In this post we will configure Hybrid Modern Authentication (HMA) on our on-premises Exchange Server.
This post is split into two parts, in part 1 we configure HMA for Exchange and in part 2 for Skype for Business.
About modern authentication and HMA you will find in my following post all necessary information.
Turn on Modern Authentication for Exchange Online
Before you enable modern authentification for your on-premises environment, please check that you enabled it first for Exchange Online.
Follow the instructions here: Exchange Online: How to enable your tenant for modern authentication.
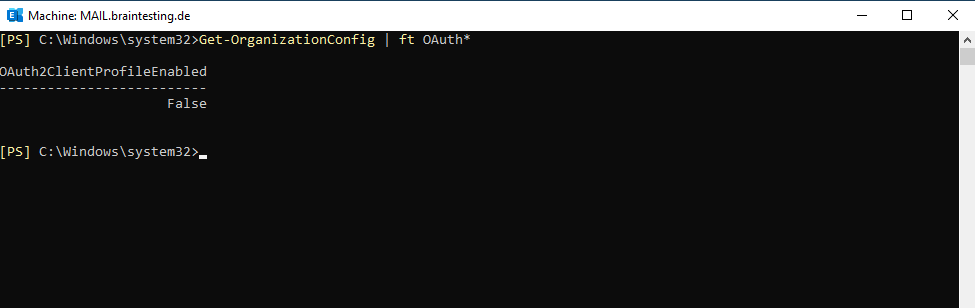
First we check the status on our on-premises Exchange Server by running the following PowerShell command:
Get-OrganizationConfig | ft OAuth*
If the value of the OAuth2ClientProfileEnabled property is False, then modern authentication is disabled.
For more information about the Get-OrganizationConfig cmdlet, see Get-OrganizationConfig.
So on the Exchange Servers in my lab environment, modern authentication is disabled.
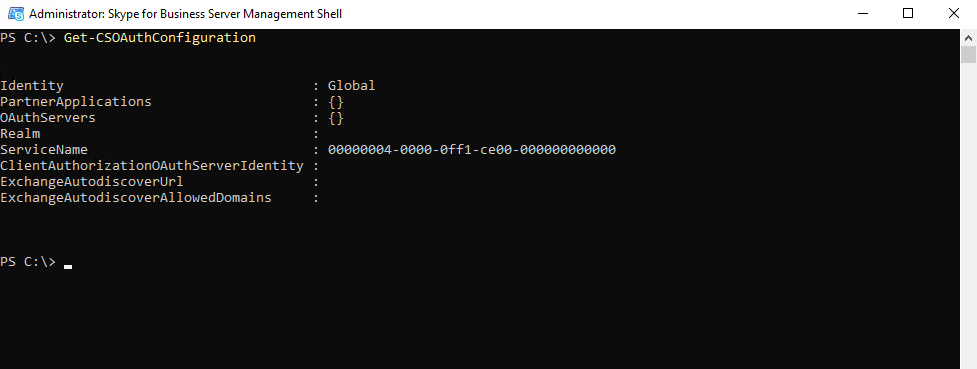
We also check the status on our on-premises Skype for Business Server by running the following PowerShell command:
Get-CSOAuthConfiguration
If the command returns an empty OAuthServers property, or if the value of the ClientADALAuthOverride property is not Allowed, then modern authentication is disabled.
For more information about the Get-CsOAuthConfiguration cmdlet, see Get-CsOAuthConfiguration.
Also on my on-premises Skype for Business server in my lab environment, modern authentication is disabled.
After that check if your on-premises environment meets the prerequisites for modern authentication.
Do you meet modern authentication prerequisites?
https://docs.microsoft.com/en-us/microsoft-365/enterprise/hybrid-modern-auth-overview?view=o365-worldwide#do-you-meet-modern-authentication-prerequisites
Now we can configure our on-premises Exchange Server to use Hybrid Modern Authentication.
Hybrid Modern Authentication (HMA) is a method of identity management that offers more secure user authentication and authorization, and is available for Exchange server on-premises hybrid deployments.
I will use the following post from Microsoft to configure it.
How to configure Exchange Server on-premises to use Hybrid Modern Authentication
https://docs.microsoft.com/en-us/microsoft-365/enterprise/configure-exchange-server-for-hybrid-modern-authentication
First we need to add our on-premises web service URLs as Service Principal Names (SPNs) in Azure AD.
Therefore we first gather all the URLs we need to add as SPN in Azure AD as follows.
Get-MapiVirtualDirectory | FL server,*url*
Get-WebServicesVirtualDirectory | FL server,*url*
Get-ClientAccessServer | fl Name, AutodiscoverServiceInternalUri
Get-OABVirtualDirectory | FL server,*url*
Get-AutodiscoverVirtualDirectory | FL server,*url*
Ensure the URLs clients may connect to are listed as HTTPS service principal names in AAD
Now we need to connect to the Azure AD using the Connect-MsolService command as follows.
Connect-MsolService
# For your Exchange-related URLs, type the following command:
Get-MsolServicePrincipal -AppPrincipalId 00000002-0000-0ff1-ce00-000000000000 | select -ExpandProperty ServicePrincipalNames
The Application ID 00000002-0000-0ff1-ce00-000000000000 belongs to Exchange Online which you can see in Azure Enterprise applications.

Take note of (and screenshot for later comparison) the output of this command, which should include an https:// autodiscover.yourdomain.com and https:// mail.yourdomain.com URL, but mostly consist of SPNs that begin with 00000002-0000-0ff1-ce00-000000000000/. If there are https:// URLs from your on-premises that are missing, we will need to add those specific records to this list.
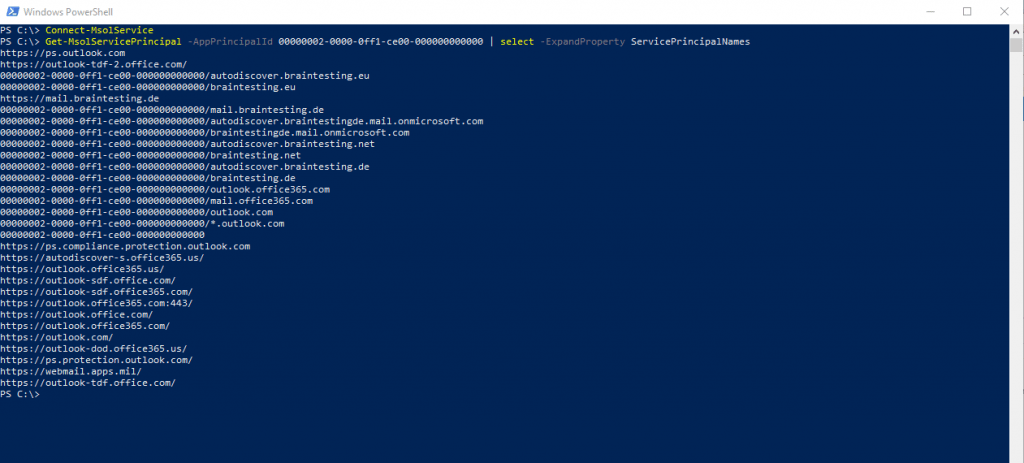
If you don’t see your internal and external MAPI/HTTP, EWS, ActiveSync, OAB, and Autodiscover records in this list, you must add them using the command below (the example URLs are ‘mail.corp.contoso.com’ and ‘owa.contoso.com’, but you’d replace the example URLs with your own):
$x= Get-MsolServicePrincipal -AppPrincipalId 00000002-0000-0ff1-ce00-000000000000
$x.ServicePrincipalnames.Add("https://mail.corp.contoso.com/")
$x.ServicePrincipalnames.Add("https://owa.contoso.com/")
Set-MSOLServicePrincipal -AppPrincipalId 00000002-0000-0ff1-ce00-000000000000 -ServicePrincipalNames $x.ServicePrincipalNamesIn my case https://mail.braintesting.de is still listed and also used for OWA.
Now verify OAuth is properly enabled in Exchange on all of the Virtual Directories Outlook might use by running the following commands:
Get-MapiVirtualDirectory | FL server,*url*,*auth*
Get-WebServicesVirtualDirectory | FL server,*url*,*oauth*
Get-OABVirtualDirectory | FL server,*url*,*oauth*
Get-AutoDiscoverVirtualDirectory | FL server,*oauth*
Check the output to make sure OAuth is enabled on each of these VDirs, it will look something like this (and the key thing to look at is ‘OAuth’):
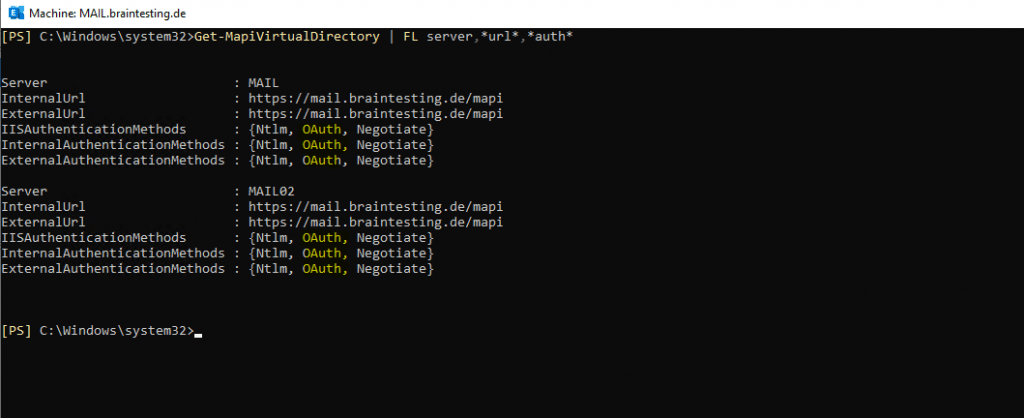
If OAuth is missing from any server and any of the four virtual directories, you need to add it using the relevant commands before proceeding (Set-MapiVirtualDirectory, Set-WebServicesVirtualDirectory, Set-OABVirtualDirectory, and Set-AutodiscoverVirtualDirectory).
Confirm the EvoSTS Auth Server Object is Present
Return to the on-premises Exchange Management Shell for this last command. Now you can validate that your on-premises has an entry for the evoSTS authentication provider:
Get-AuthServer | where {$_.Name -like “EvoSts*”}
Your output should show an AuthServer of the Name EvoSts and the ‘Enabled’ state should be True. If you don’t see this, you should download and run the most recent version of the Hybrid Configuration Wizard.
To enable HMA we need to run the following commands in the Exchange Management Shell, on-premises:
Set-AuthServer -Identity “EvoSTS – {GUID}” -IsDefaultAuthorizationEndpoint $true
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
Finally we can verify if the clients will use for the next login HMA.
Once you enable HMA, a client’s next login will use the new auth flow. Note that just turning on HMA won’t trigger a reauthentication for any client. The clients re-authenticate based on the lifetime of the auth tokens and/or certs they have.
You should also hold down the CTRL key at the same time you right-click the icon for the Outlook client (also in the Windows Notifications tray) and click ‘Connection Status’. Look for the client’s SMTP address against an ‘Authn’ type of ‘Bearer*’, which represents the bearer token used in OAuth.
You can also force the user to re-authenticate against the new AuthServer, by setting his actual using Token to expired with the following command in Exchange Online PowerShell Module.
Import-Module ExchangeOnlineManagement $credential = Get-Credential Connect-ExchangeOnline -Credential $credential -ShowProgress $true Set-User -identity jdoe -StsRefreshTokensValidFrom $([System.DateTime]::UtcNow)
Disable Modern Authentication
In case you will run into trouble with modern authentification, like the Azure AD and Office 365 service fails or your local companies internet connection fails, you can quickly disable modern authentification as follows.
Keep in mind, that with HMA, also the on-premise users depends on Azure AD to authenticate against Exchange.
# for Exchange on-premise Set-AuthServer -Identity evoSTS -IsDefaultAuthorizationEndpoint $false # for Skype for Business on-premise Set-CsOAuthConfiguration -ClientAuthorizationOAuthServerIdentity ""
Links
Hybrid modern authentication overview and prerequisites for using it with on-premises Skype for Business and Exchange servers
https://docs.microsoft.com/en-us/microsoft-365/enterprise/hybrid-modern-auth-overview?view=o365-worldwide
How to configure Exchange Server on-premises to use Hybrid Modern Authentication
https://docs.microsoft.com/en-us/microsoft-365/enterprise/configure-exchange-server-for-hybrid-modern-authentication
Related Posts
Latest posts
Deploying NetApp Cloud Volumes ONTAP (CVO) in Azure using NetApp Console (formerly BlueXP) – Part 5 – Backup and Recovery
Follow me on LinkedIn


