How to enable Remote Desktop by using Group Policies
In enterprise environments, enabling Remote Desktop manually on multiple machines can be time-consuming. Instead, Group Policies (GPOs) provides a centralized way to enable and configure Remote Desktop across multiple computers efficiently.
In this post, we will see step by step how to enable Remote Desktop by using Group Policies, configure firewall rules, and ensure secure access for authorized users.
Enable Remote Desktop Access
To allow in general Remote Desktop Connections on a computer, we need to configure and apply the Allow users to connect remotely by using Remote Desktop Services policy.
Finally we control the following highlighted setting by this policy.
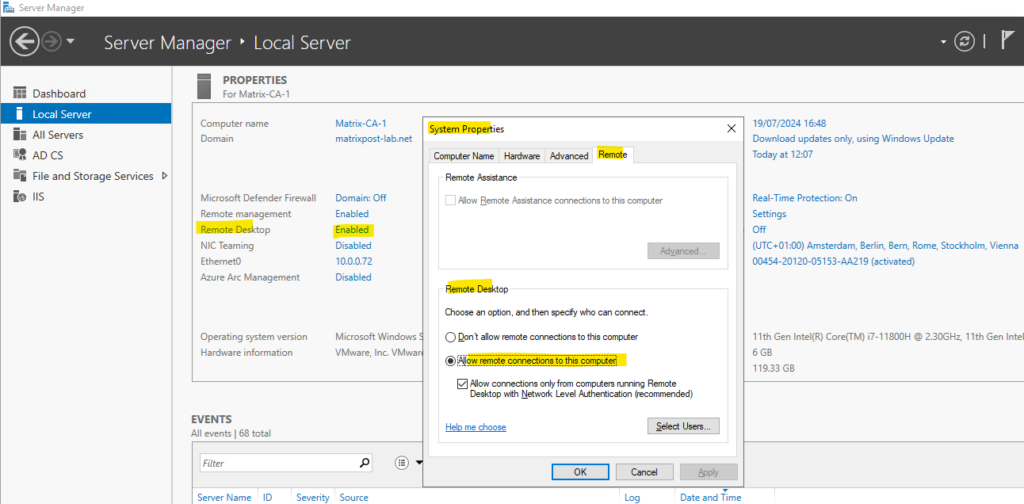
To control this by a group policy, navigate to the following settings and enable Allow users to connect remotely by using Remote Desktop Services.
Computer Configuration → Policies → Administrative Templates → Windows Components → Remote Desktop Services → Remote Desktop Session Host → Connections → Allow users to connect remotely by using Remote Desktop Services
From now on all computers to which this policy is applied to, will in general allow Remote Desktop Connections to users they are either members in their local Administrators or local Remote Desktop Users group.
We can now adding by hand other users and groups which are also allowed to logon remote to this computer or we can use a further policy to control the membership of the local Administrators or Remote Desktop Users group as shown further down.
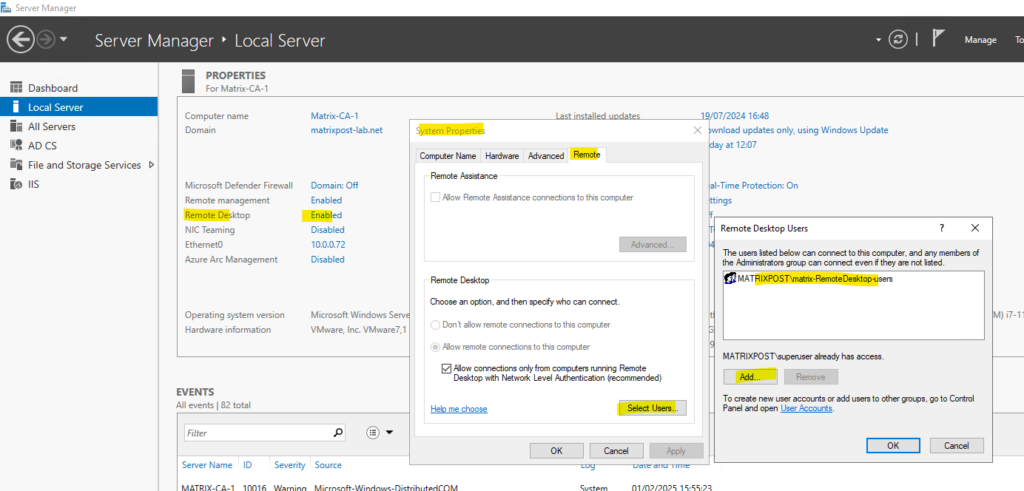
But first we also enable Network Level Authentication (NLA) for remote session as shown next.
Enable Network Level Authentication (NLA) by using a Group Policy
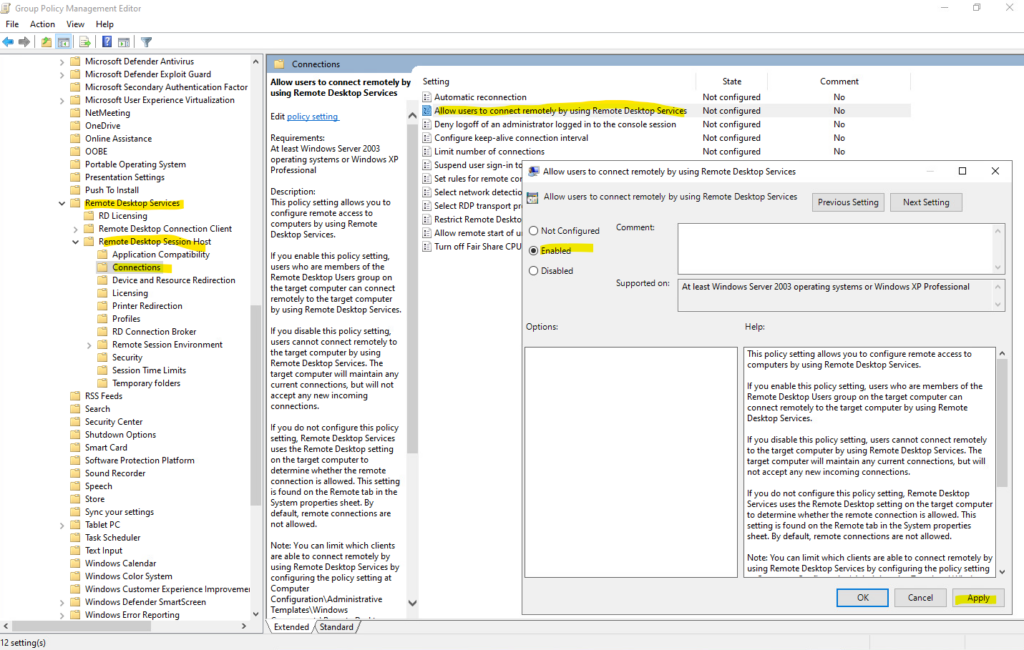
To control this by a group policy, navigate to the following settings and enable Require user authentication for remote connections by using Network Level Authentication.
Network Level Authentication (NLA) is a security feature used in Remote Desktop Services (RDS) and Remote Desktop Protocol (RDP) that requires users to authenticate before a remote session is established.
It helps protect against unauthorized access and reduces the risk of denial-of-service (DoS) attacks by requiring authentication before a session is created.
When a user attempts to connect via Remote Desktop (RDP), the client must authenticate with valid credentials before the session starts. The authentication process happens at the network level, before loading the full remote desktop interface.
If authentication fails, the session is rejected without consuming server resources.
Enable Require user authentication for remote connections by using Network Level Authentication
Computer Configuration → Policies → Administrative Templates → Windows Components → Remote Desktop Services → Remote Desktop Session Host → Security → Require user authentication for remote connections by using Network Level Authentication
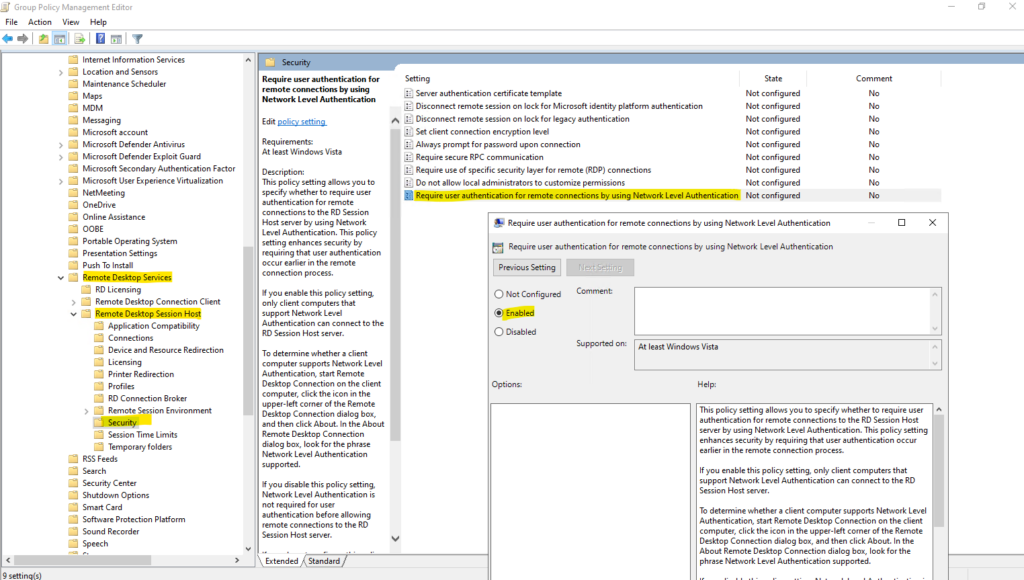
Finally when both policies we configured so far and are applied to our computers, the settings for Allow remote connections to this computer and Allow connections only from computers running Remote Desktop with Network Level Authentication (recommended) are enabled and greyed out.
The users which are allowed to connect remotely we can still adding by hand and clicking on the Select Users … button.
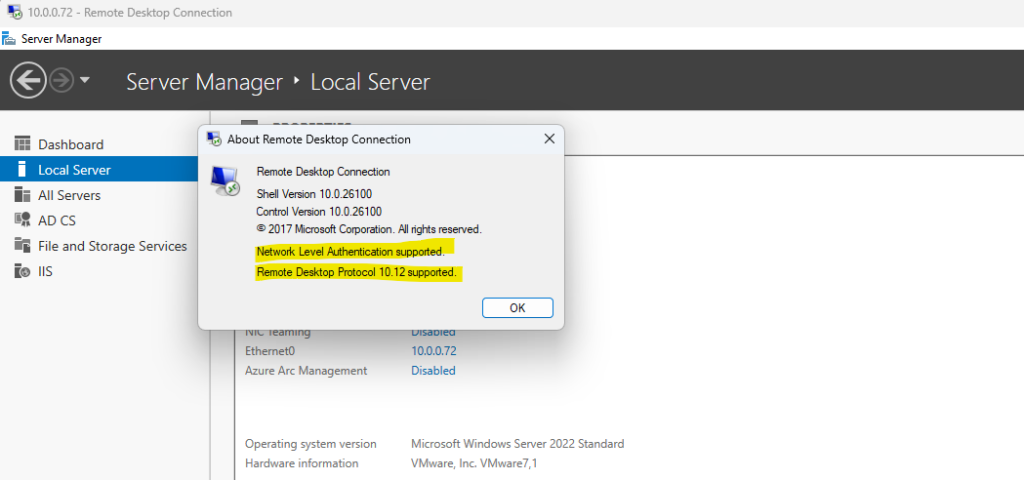
To determine whether a computer is running a version of Remote Desktop Connection that supports Network Level Authentication, start Remote Desktop Connection, click the icon in the upper-left corner of the Remote Desktop Connection dialog box, and then click About.
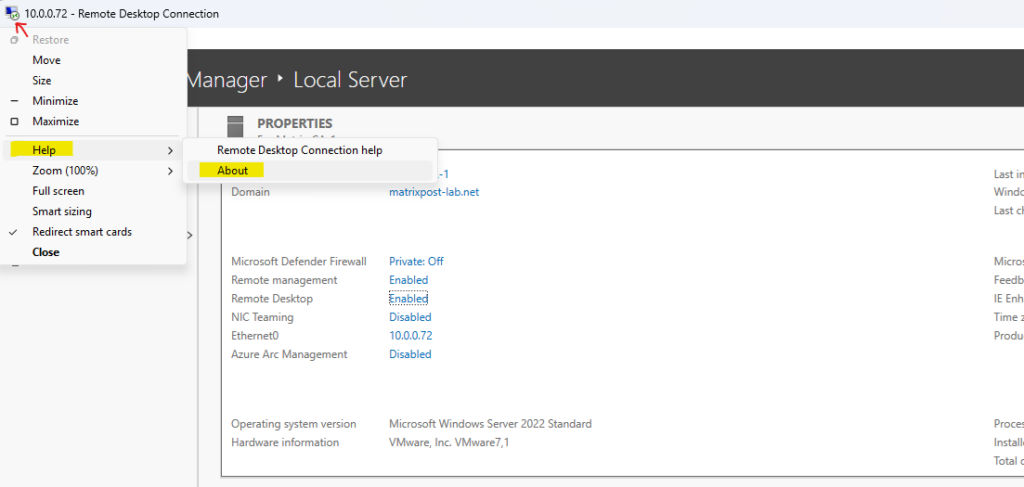
Look for the phrase Network Level Authentication supported in the About Remote Desktop Connection dialog box as shown below.
Using Restricted Groups to control the Members of local Security Groups on Computers
As mentioned above the local Administrators and local Remote Desktop Users group will have by default the permissions to establish a Remote Desktop Services session to the computer and finally to sign-in.
The final sign-in permission we can also control by a further dedicated policy, here more about further down.
To control which users are members in these groups we can use a group policy to define restricted groups or by adding local users and groups configured within the control panel settings for the GPO, we will see both methods below.
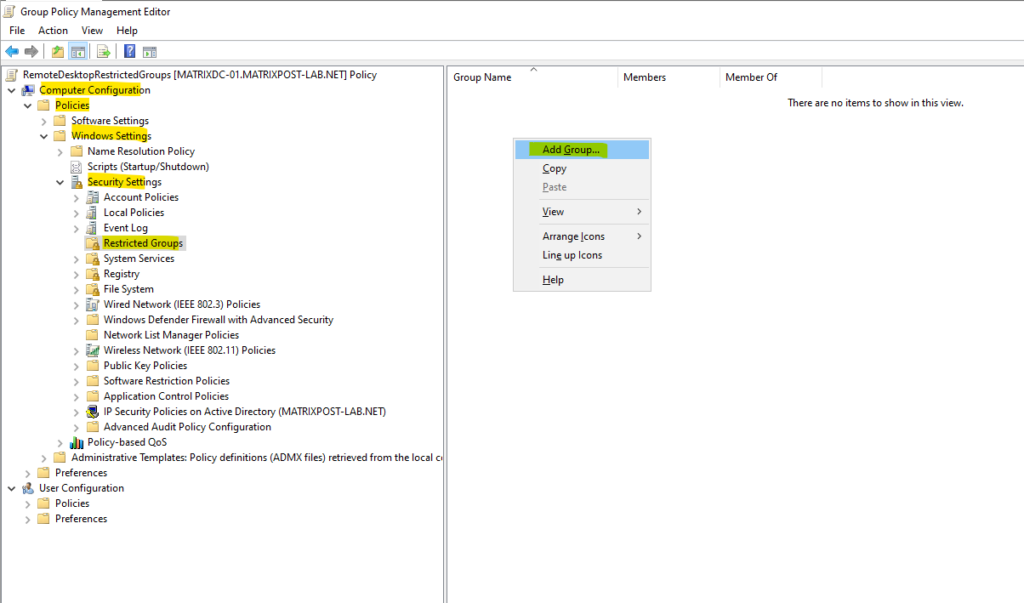
Restricted Groups in Windows Group Policy Objects (GPOs) are a feature used to enforce membership in specific security groups on a computer. This is particularly useful for ensuring that only authorized users or groups are members of critical security groups, such as Administrators, Remote Desktop Users, or other custom groups.
Navigate to the Restricted Groups settings shown below and right click on the right section to add a new restricted group where we finally can define the membership in the local Administrators or local Remote Desktop Users group on the computers we apply this policy.
Computer Configuration → Administrative Templates → Windows Components → Remote Desktop Services → Remote Desktop Session Host → Connections → Allow users to connect remotely by using Remote Desktop Services
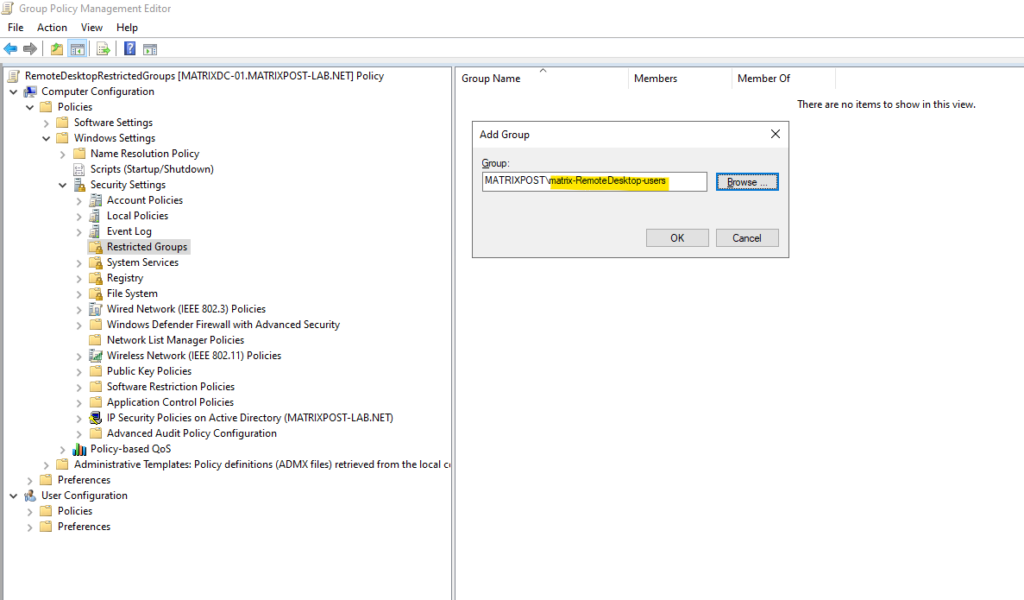
I was creating a new security group named matrix-RemoteDesktop-users in which all members will have local Administrator permissions later when applied to the domain computers.
Adding the local Remote Desktop Users or local Administrators group in which our new restricted group is member of on the computers this policy is applied to.
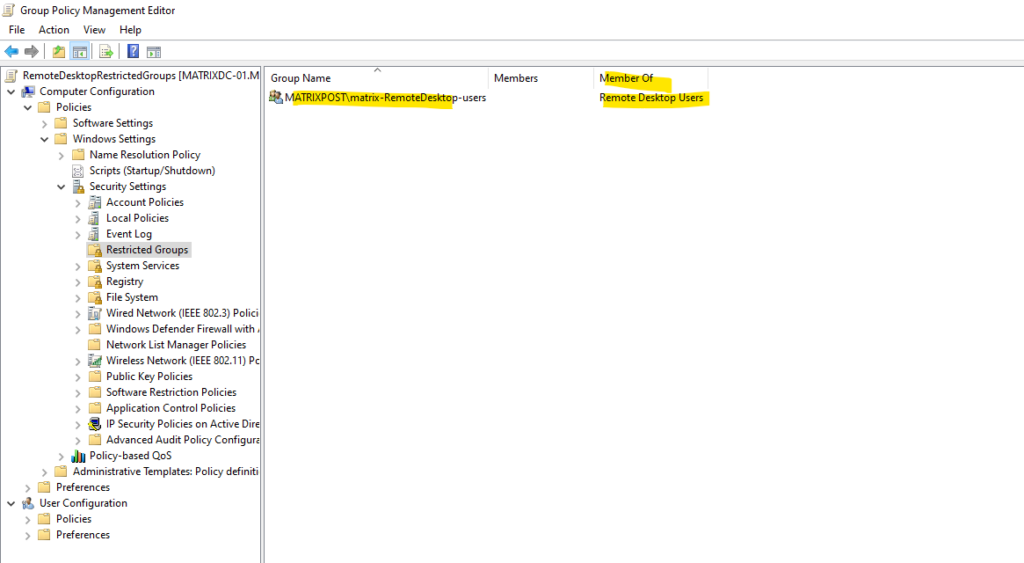
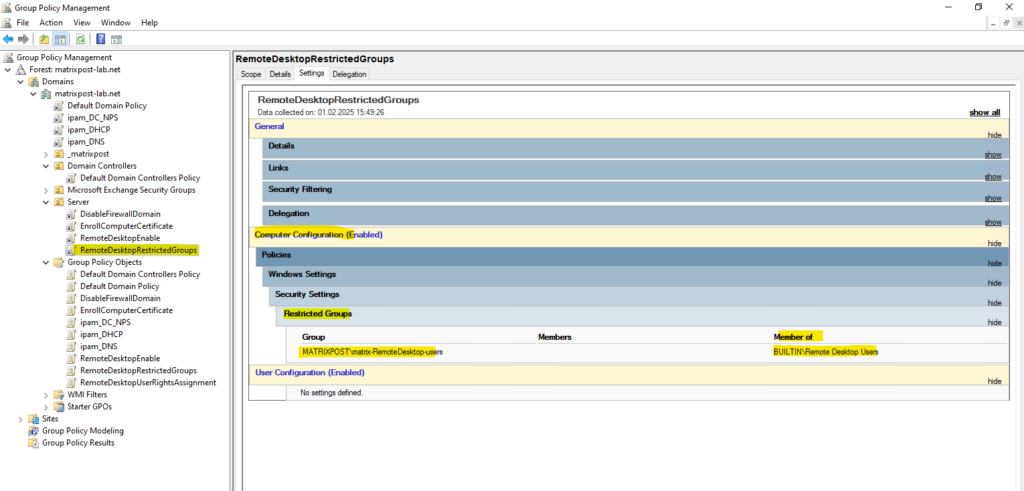
Therefore all users which are member in the MATRIXPOST\matrix-RemoteDesktop-users security group, will be added to the local Remote Desktop Users or local Administrators group on the computers to which this policy is applied to.
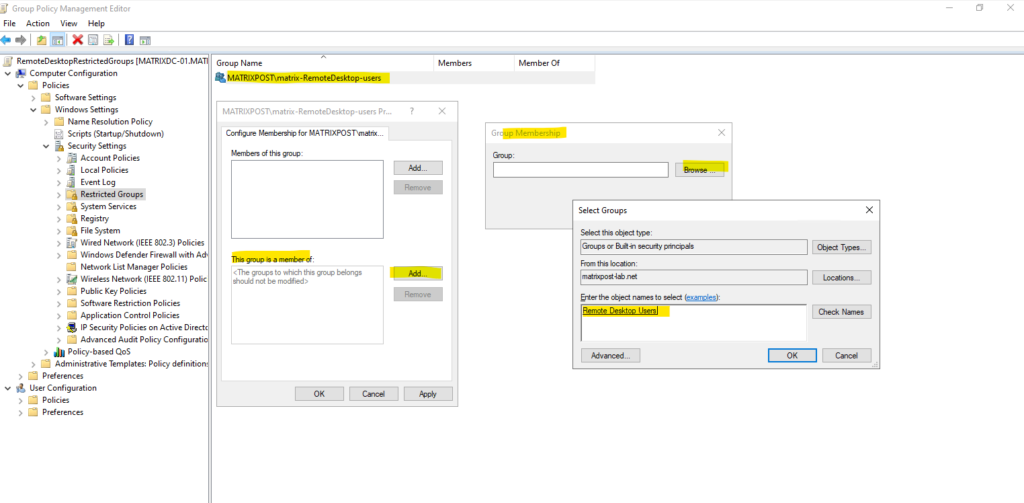
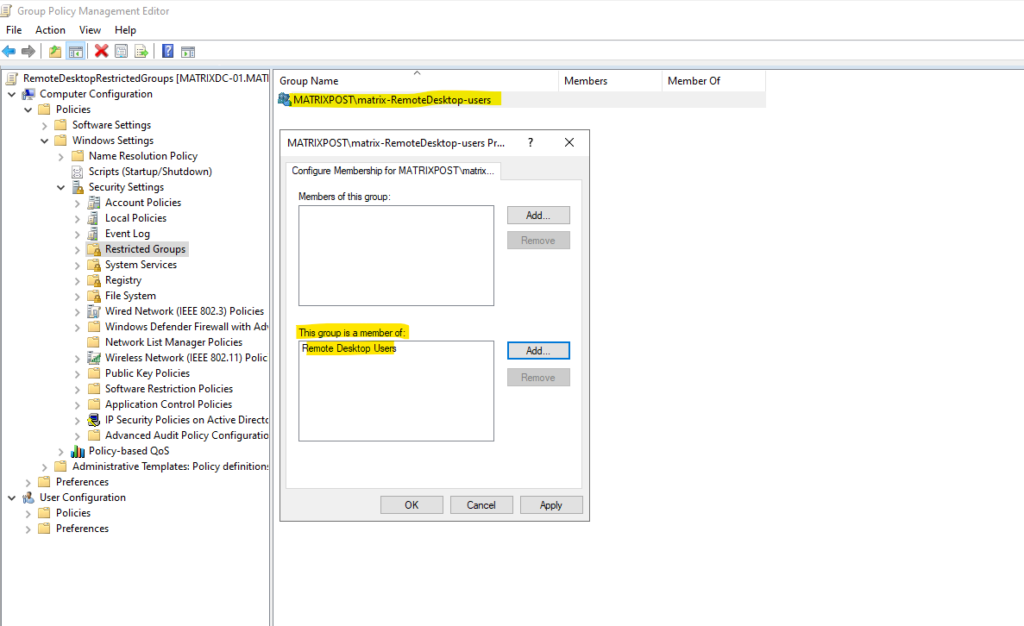
Finally we need to add all users we want to allow to login remote to our previously created custom security group we added as new restricted group.
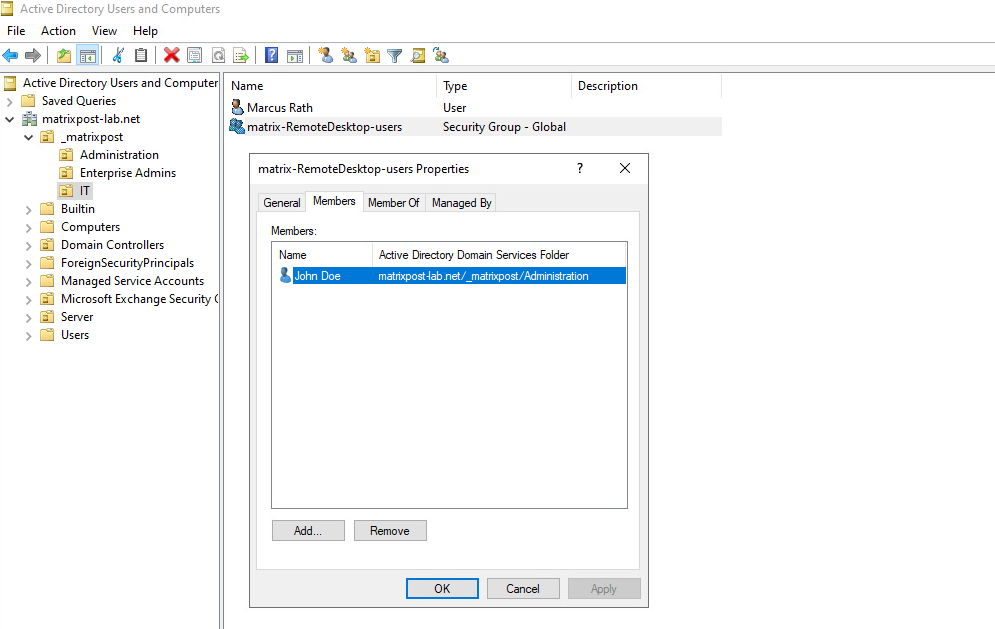
After the policy applied to our destination computers, the newly created restricted group will appear as member within the Remote Desktop Users group.
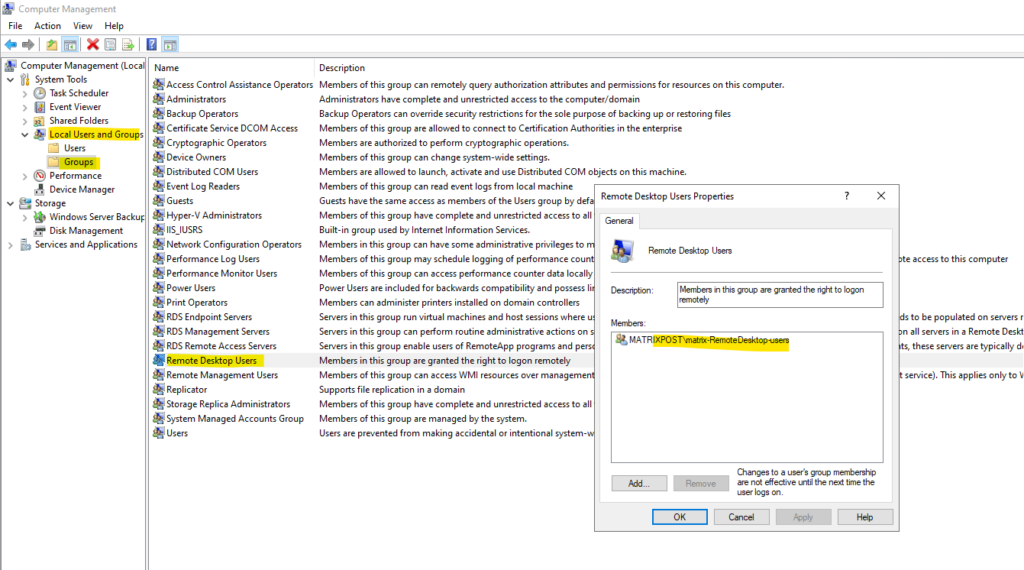
We can also still add by hand further users and groups to allow remote login to the computer.
Using the Control Panel Settings to control the Members of local Security Groups on Computers
As mentioned further above to control which users are members in the local Administrators and local Remote Desktop Users group, we can also adding local users and groups by configuring the following settings in the GPO.
Therefore navigate to the following section and right click → New → Local Group
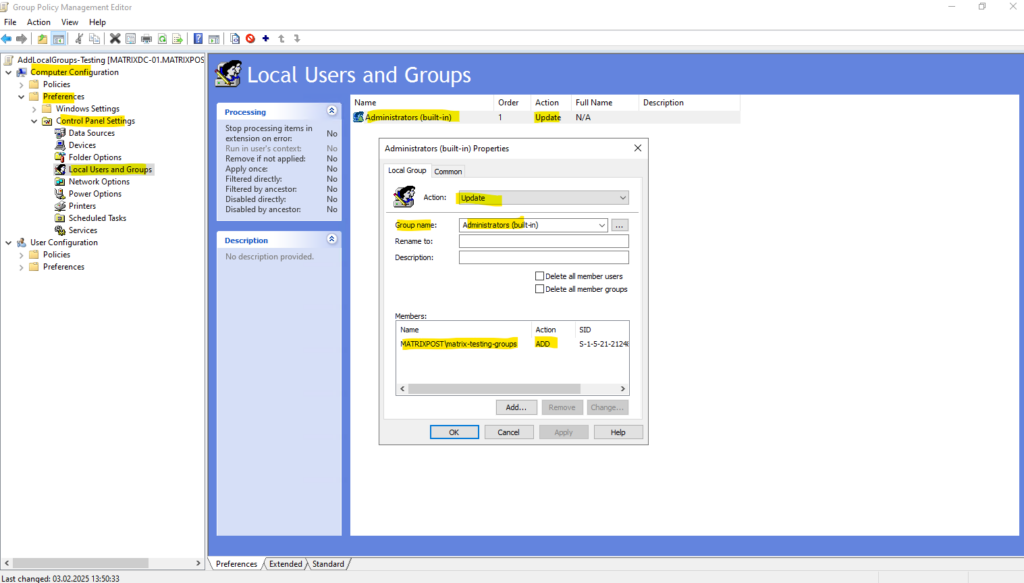
Computer Configuration → Preferences → Control Panel Settings → Local Users and Groups
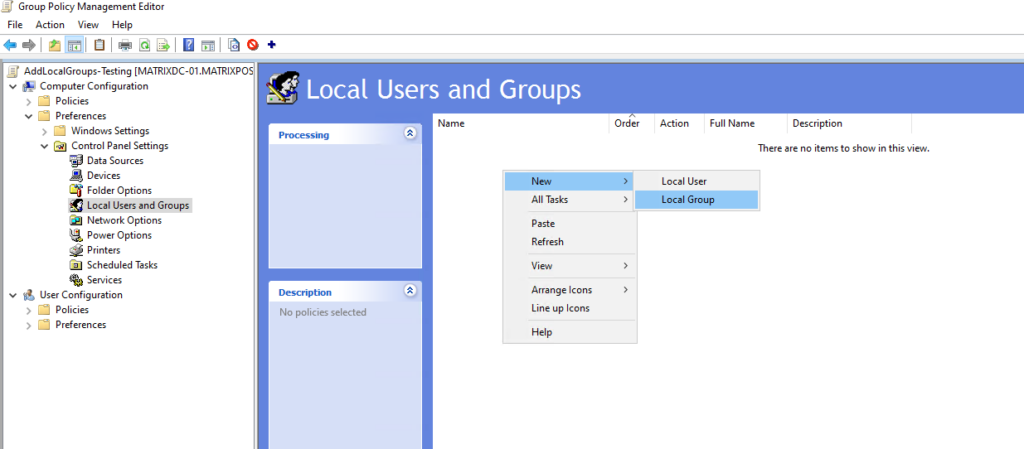
Select Update for the Action and for the group Administrators (built-in), click on Add … and select your security group you finally want to add to the local Administrators group on the machines the GPO will be applied to.
For the Action here we need to select Add to this group.
There is one more group policy as mentioned further above to control the final sign-in permission for a user.
More below in the next section.
Allow logon through Remote Desktop Services GPO
We can use this policy to control which users and groups can access the sign-in screen of a remote device through a Remote Desktop Services connection.
This policy setting determines which users or groups can access the sign-in screen of a remote device through a Remote Desktop Services connection. It’s possible for a user to establish a Remote Desktop Services connection to a particular server but not be able to sign in to the console of that same server.
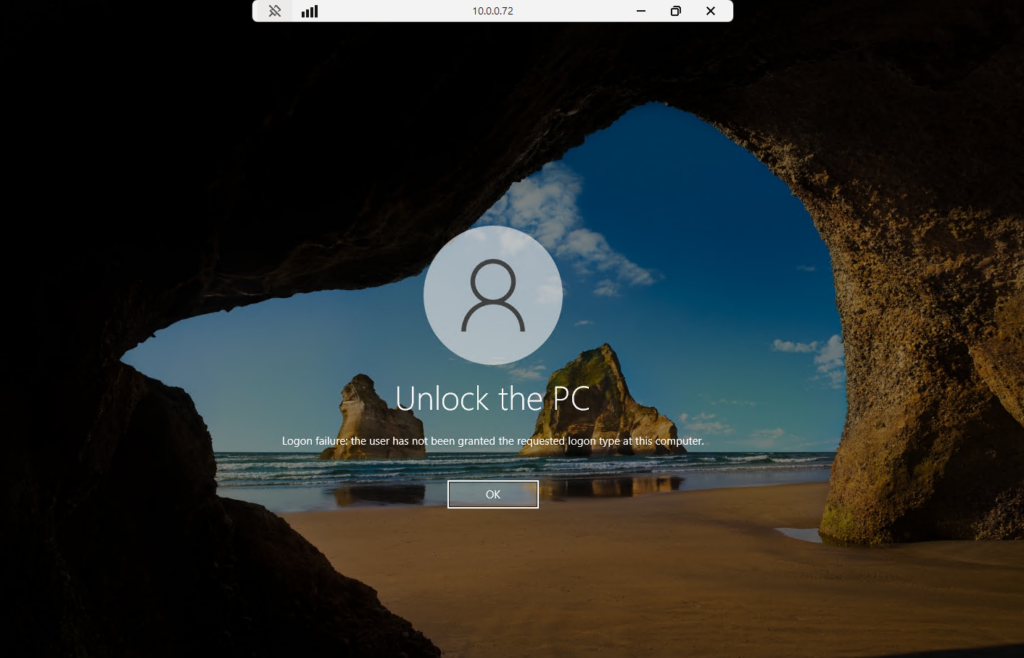
When this policy is applied to a remote computer, all users which are not configured in this policy but still be a member in the local Remote Desktop Users or local Administrators group, can establish a Remote Desktop Services connection but finally cannot sign-in to the computer and will see the following logon failure message.
So it’s possible for a user to establish a Remote Desktop Services session to a particular server, but not be able to sign in to the console of that same server.
Logon failure: the user has not been granted the requested logon type at this computer
Best practices is to control who can open a Remote Desktop Services connection and sign in to the destination computer, like shown further above to add users to or remove users from the Remote Desktop Users group.
Adding the users and groups either by hand or by using the policy with the restricted groups.
!! Note !!
First of all, just defining this policy alone will not allow to establish a Remote Desktop Services session to a remote computer, just the permission to sign-in is granted, to establish a Remote Desktop Services session the users still have to be a member in either the local Remote Desktop Users or local Administrators group on the destination computer.
Second when defining and applying this policy to our destination computers, all users and groups which should be able to logon remote, must be added here, if not also the users they are still members of the local Remote Desktop Users or local Administrators group will not have the permission to sign-in to the remote computer and the above shown Logon failure will appear.
By default the local Remote Desktop Users and local Administrators group have the permission to sign-in to the remote computer, this policy will change these permissions and just granting to the users we assign here.
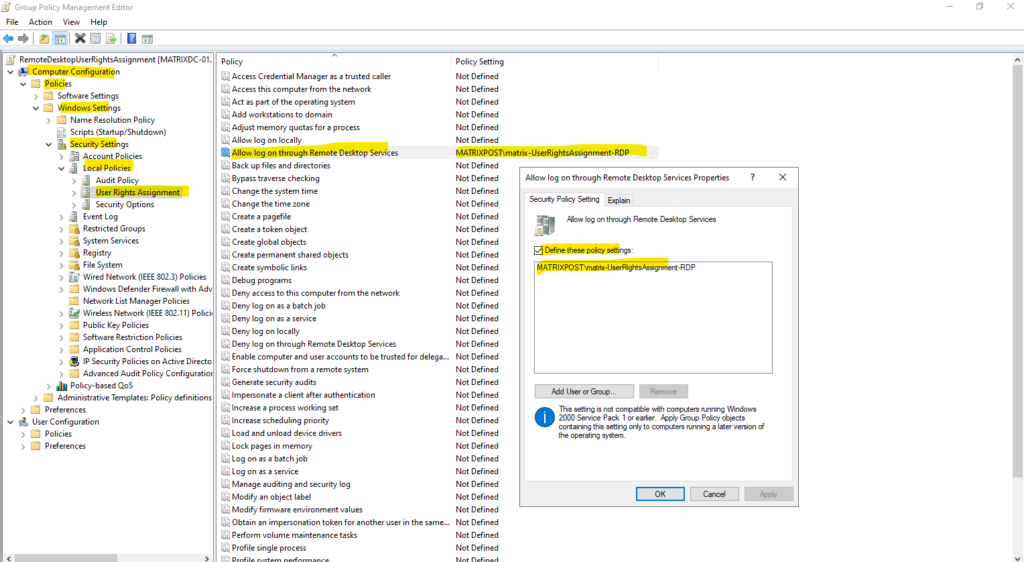
To configure this policy navigate to the following settings, here I will for example add the matrix-UserRightsAssignment-RDP security group, so all members of this group will have remote sign-in rights to the destination computers this policy will be applied to.
And as mentioned they also still needs to be a member in the local Remote Desktop Users or local Administrators group to be able to establish a Remote Desktop Services session in the first place to the destination computer.
Computer Configuration → Windows Settings → Security Settings → Local Policies → User Rights Assignment → Allow log on through Remote Desktop Services
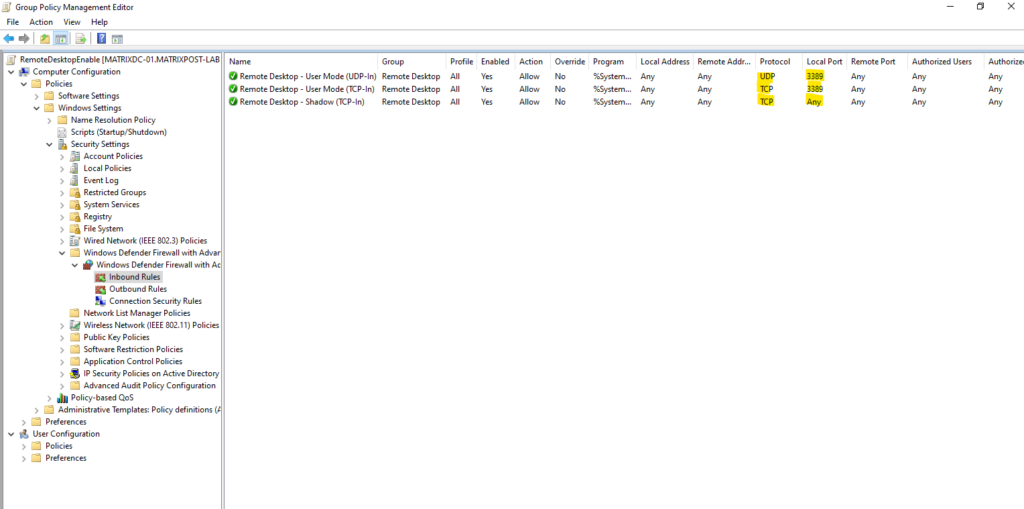
Control the Windows Defender Firewall by using a Group Policy
We also need to allow inbound TCP 3389 and since RDP version 8.0 best practice also UDP 3389 traffic on the remote computers we want to enable Remote Desktop.
I will user therefore also use my first group policy named Allow users to connect remotely by using Remote Desktop Services where we enabled in general Remote Desktop connections.
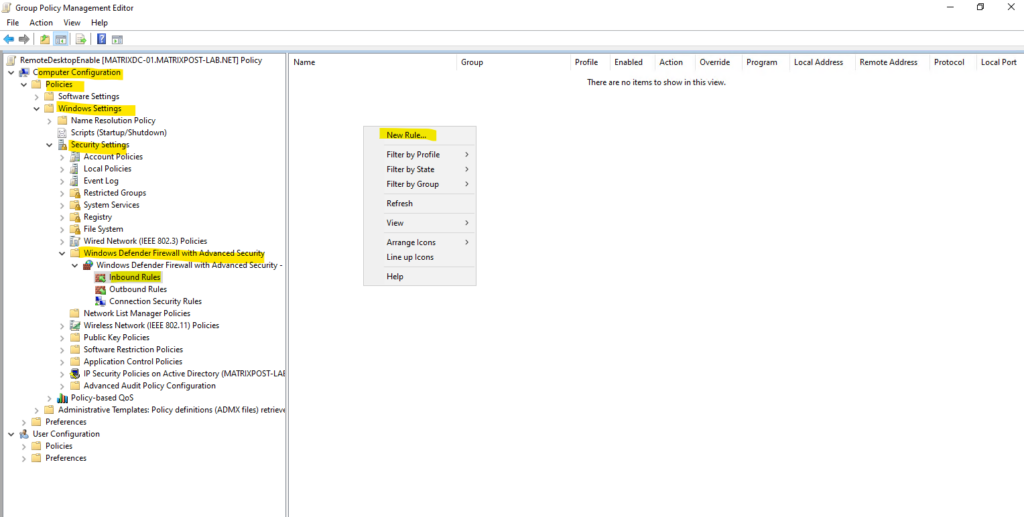
Here we need to navigate to the following settings and right click on the right section and New Rule … as shown below.
Computer Configuration → Windows Settings → Security Settings → Security Settings → Windows Defender Firewall with Advanced Security → Inbound Rules
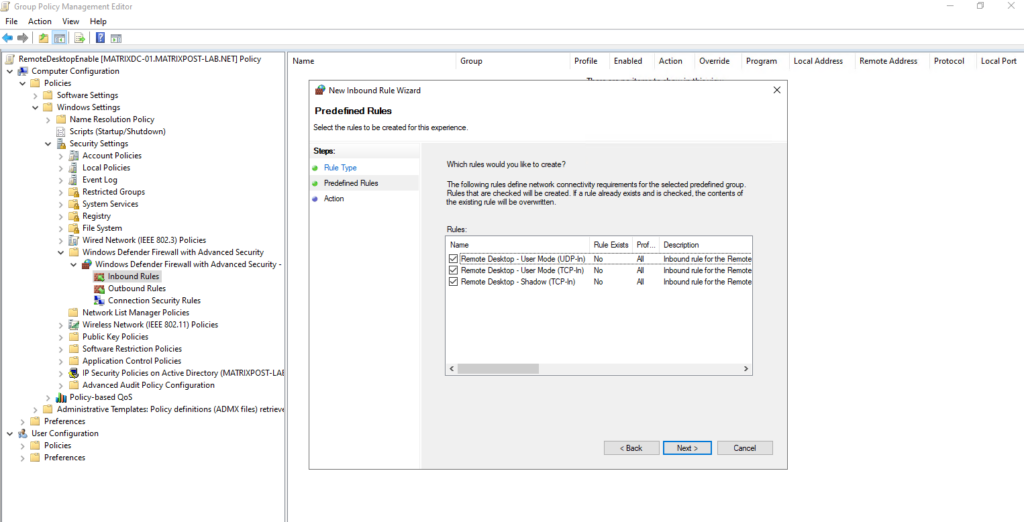
Here we can either select Port or Predefined → Remote Desktop. When using predefined not just TCP 3389 as usual but also UDP 3389 will be opened. Further here by default the settings will be applied to all profiles (Domain, Private and Public).
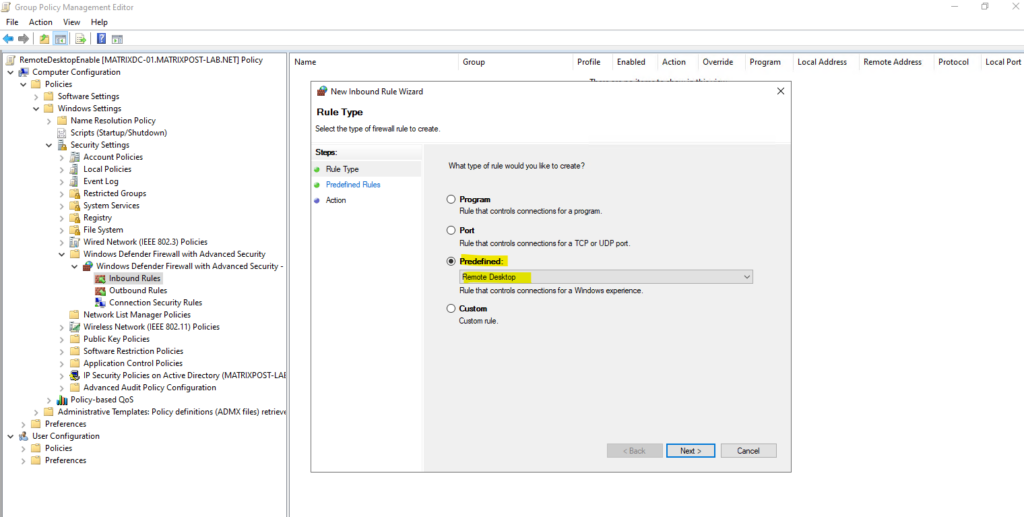
By default, the server listens on TCP port 3389 and UDP port 3389.
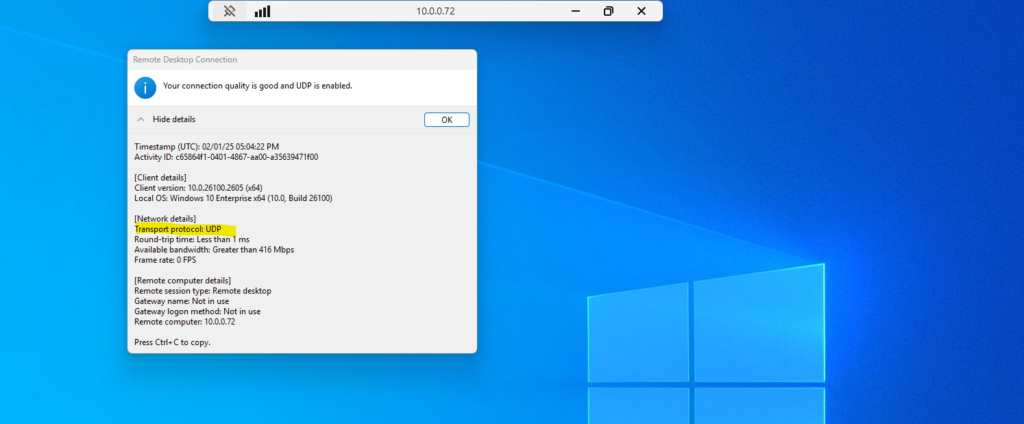
UDP support was introduced in RDP version 8.0 (Windows 8 and Windows Server 2012). A connection quality dialog is displayed in the RDP client connection bar for RDP 8.0 or later connections; clicking on it provides further information about connection, including whether UDP is in use or not like shown below.
As mentioned you can click on the RDP client connection bar (network icon) to see further information about the connection and if for the transport protocol TCP or UPD is used.
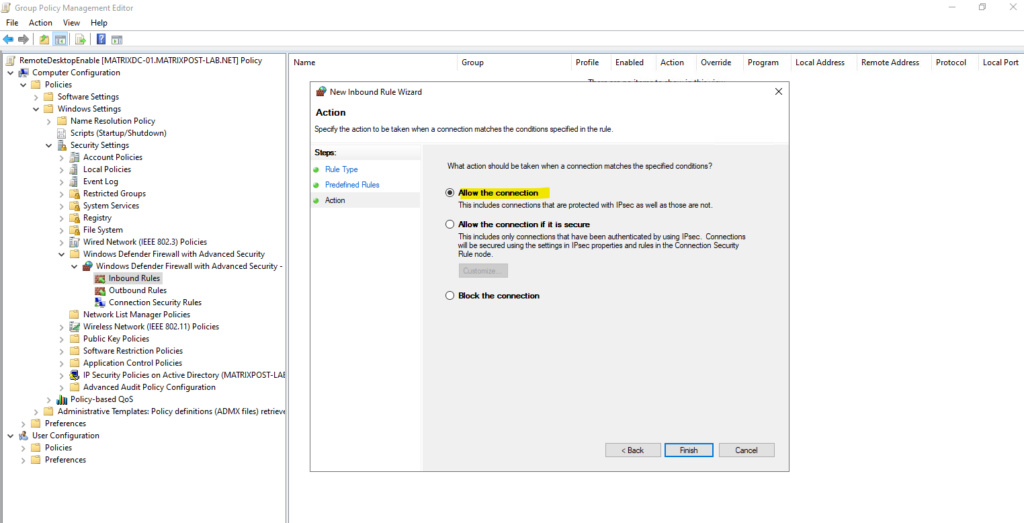
Select Allow the connection.
Links
Allow log on through Remote Desktop Services
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-10/security/threat-protection/security-policy-settings/allow-log-on-through-remote-desktop-servicesRemote Desktop Protocol: UDP Transport Extension Protocol
https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-rdpeudp/fe211d97-92dd-47e6-8fa3-b23f2c1a5af9Why allow connections only with Network Level Authentication?
https://learn.microsoft.com/en-us/windows-server/remote/remote-desktop-services/clients/remote-desktop-allow-access#why-allow-connections-only-with-network-level-authenticationConfigure Network Level Authentication for Remote Desktop Services Connections
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc732713(v=ws.11)


