AWS – IAM vs. IAM Identity Center vs. Directory Service
In this post I want to summarize some information about the different account types you can use in AWS. This topic is well documented from AWS.
You can use different account types in AWS to manage resources from AWS. When you create an AWS account, you begin with one sign-in identity that has complete access to all AWS services and resources in the account.
This identity is called the AWS account root user and is accessed by signing in with the email address and password that you used to create the account.
To login to the AWS Console by using the root user, you can click on Sign in using root user email.
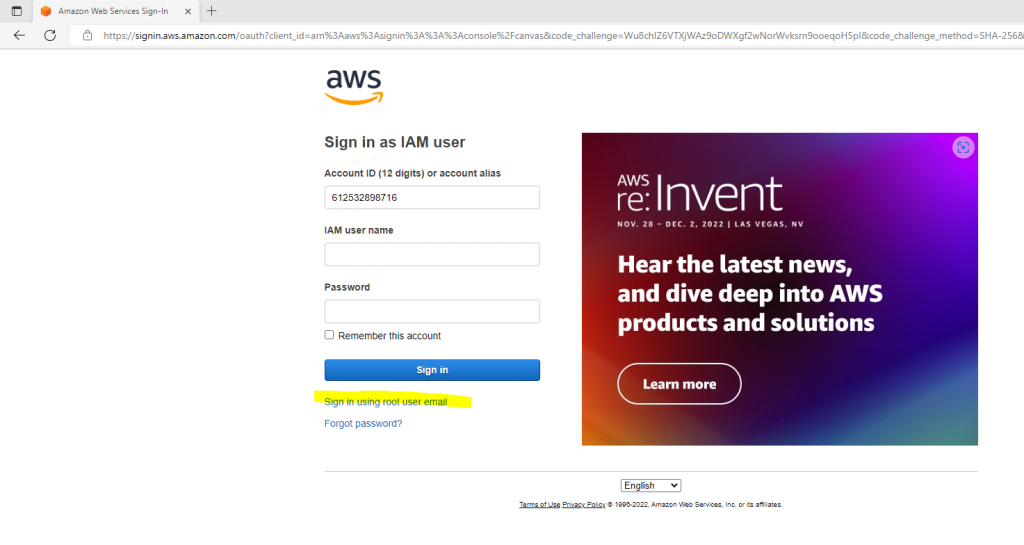
Btw. you will see in the screenshot above and used URL, that AWS will use here for the sign in also OpenID Connect and the OAuth framework which is the de facto industry standard for online authorization. If you are interested to read more about OAuth and OpenID connect, you will find a few posts about in my blog at the link below.
Enter the root user’s email address you used when creating the account.
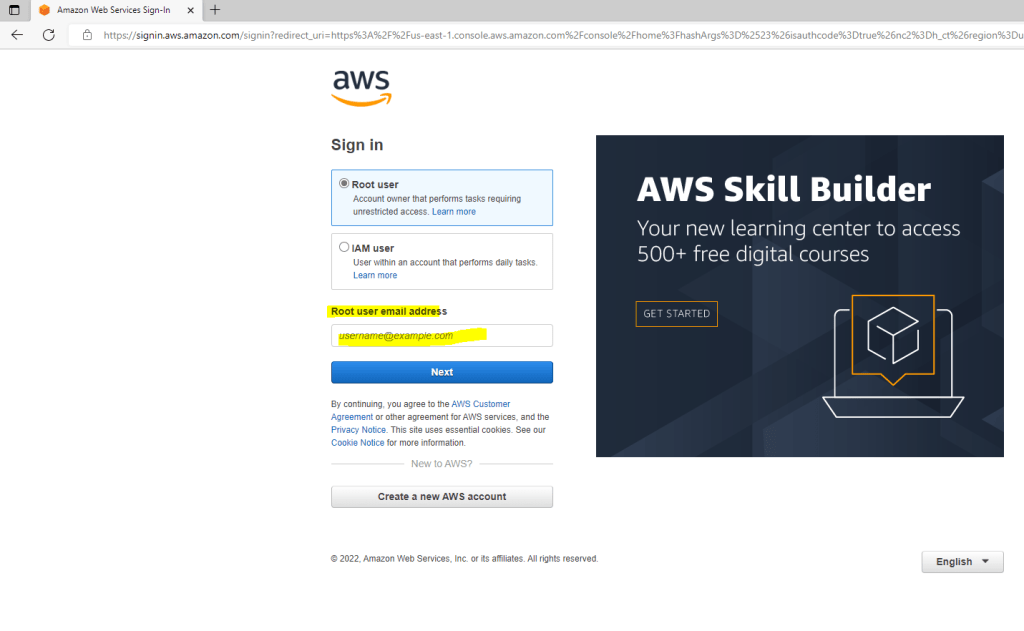
IAM
To create further cloud only AWS users you can use AWS Identity and Access Management (IAM).
With AWS Identity and Access Management (IAM), you can specify who or what can access services and resources in AWS, centrally manage fine-grained permissions, and analyze access to refine permissions across AWS.
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. You use IAM to control who is authenticated (signed in) and authorized (has permissions) to use resources.
When you create an AWS account, you begin with one sign-in identity that has complete access to all AWS services and resources in the account. This identity is called the AWS account root user and is accessed by signing in with the email address and password that you used to create the account.
We strongly recommend that you do not use the root user for your everyday tasks. Safeguard your root user credentials and use them to perform the tasks that only the root user can perform. For the complete list of tasks that require you to sign in as the root user, see Tasks that require root user credentials in the AWS General Reference.
Source: https://docs.aws.amazon.com/IAM/latest/UserGuide/introduction.html
Understanding how IAM works
In the link below you will find detailed information about how IAM works.
https://docs.aws.amazon.com/IAM/latest/UserGuide/intro-structure.html
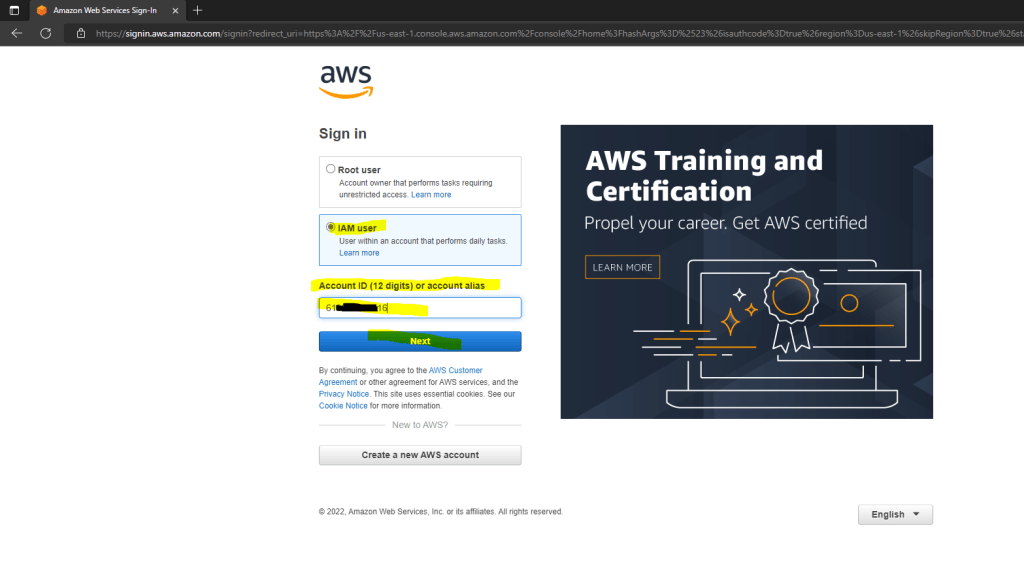
To login to the AWS Console by using an IAM user account, you have to choose below IAM user and enter your Account ID created in the Identity and Access Management (IAM) console.
The AWS Account ID is like the Tenant ID in Microsoft Azure.
Viewing account identifiers (AWS account ID, Canonical user ID)
https://docs.aws.amazon.com/accounts/latest/reference/manage-acct-identifiers.html
Azure and AWS accounts and subscriptions
https://learn.microsoft.com/en-us/azure/architecture/aws-professional/accounts
Next you have to enter your IAM username and password.
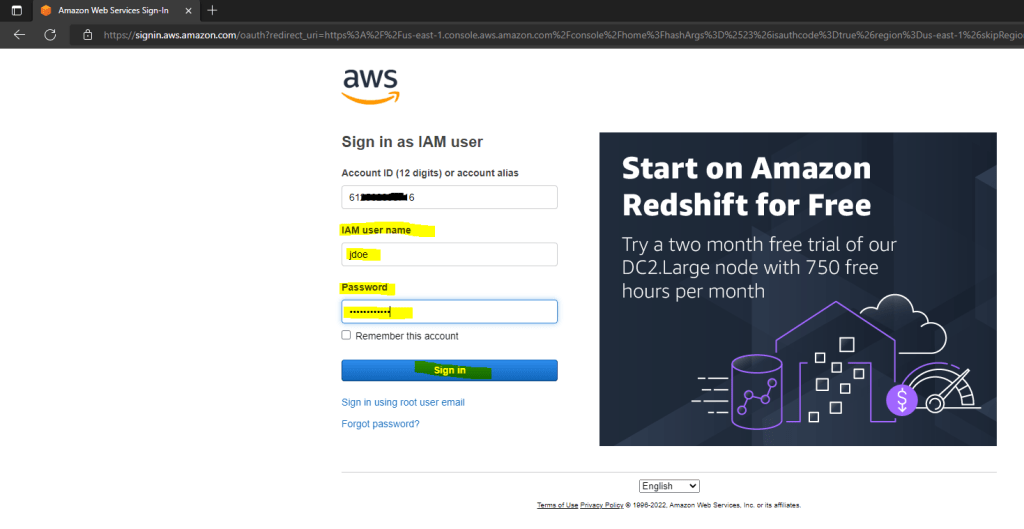
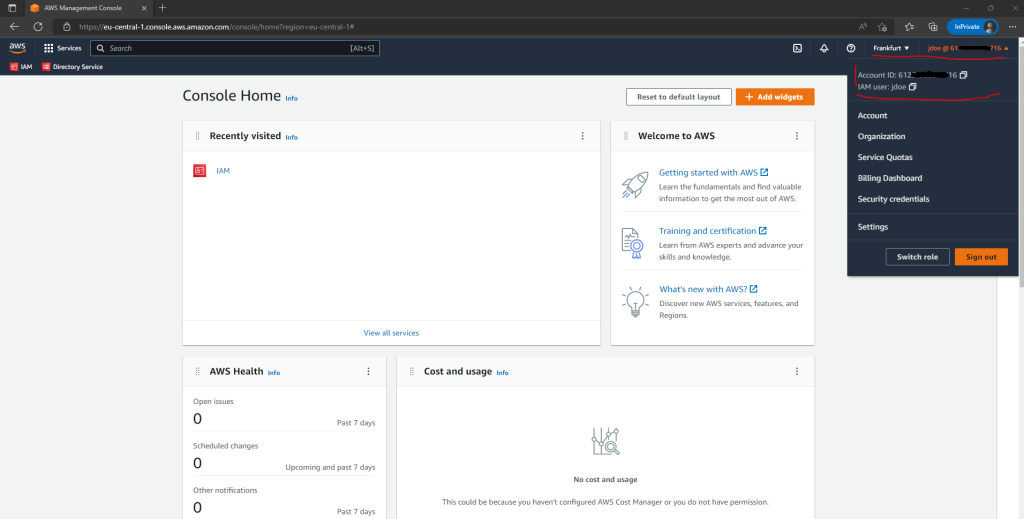
To determine the Account ID and username of an IAM user you can use the IAM console as shown below or just click as shown above on your username.
AWS Console –> Identity and Access Management (IAM) –> Access management –> Users –> User name –> USR ARN
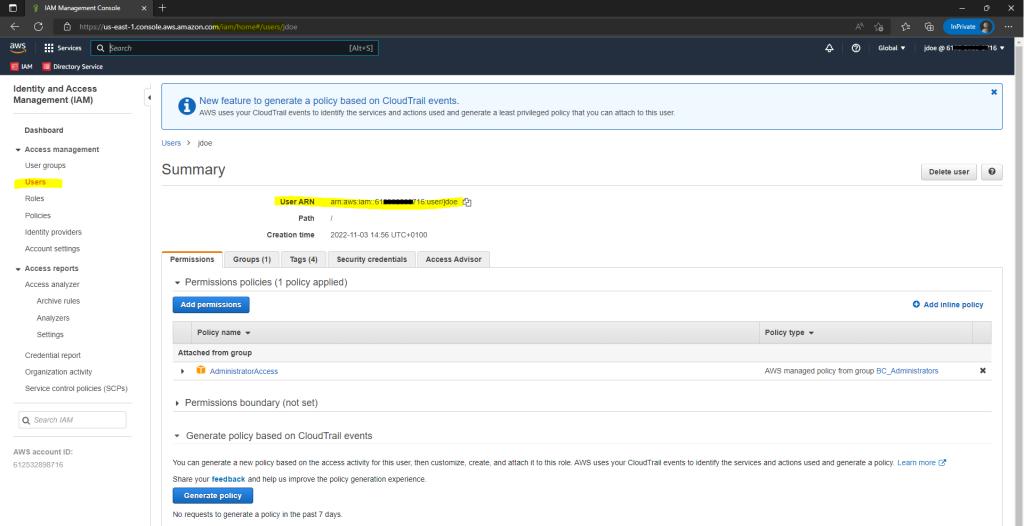
Amazon-Ressourcennamen (ARNs)
Amazon Resource Names (ARNs) uniquely identify AWS resources. We require an ARN when you need to specify a resource unambiguously across all of AWS, such as in IAM policies, Amazon Relational Database Service (Amazon RDS) tags, and API calls.
https://docs.aws.amazon.com/general/latest/gr/aws-arns-and-namespaces.html
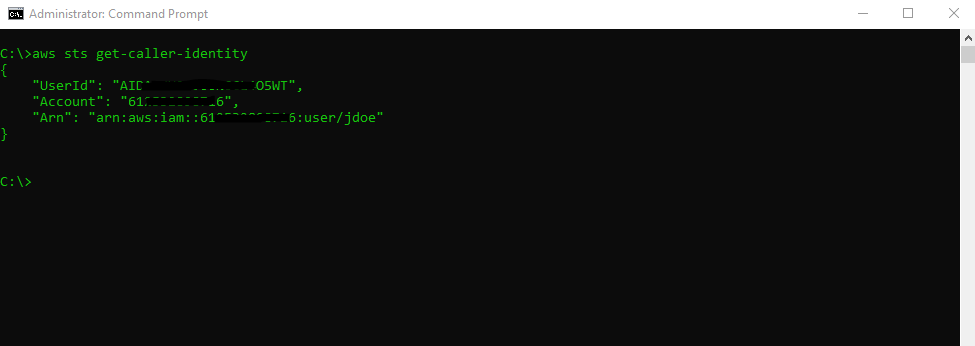
Alternatively you can also use the AWS CLI to get the Account ID.
$ aws sts get-caller-identity
Welcome to the AWS Security Token Service API Reference
https://docs.aws.amazon.com/STS/latest/APIReference/welcome.html
sts
Security Token Service (STS) enables you to request temporary, limited-privilege credentials for Identity and Access Management (IAM) users or for users that you authenticate (federated users)
https://docs.aws.amazon.com/cli/latest/reference/sts/
About how to install, configure and use the AWS CLI you can read my following posts.
IAM Identity Center (successor to AWS Single Sign-ON)
AWS IAM Identity Center (successor to AWS Single Sign-On) expands the capabilities of AWS Identity and Access Management (IAM) to provide a central place that brings together administration of users and their access to AWS accounts and cloud applications. Although the service name AWS Single Sign-On has been retired, the term single sign-on is still used throughout this guide to describe the authentication scheme that allows users to sign in one time to access multiple applications and websites.
With IAM Identity Center you can manage sign-in security for your workforce by creating or connecting your users and groups to AWS in one place. With multi-account permissions you can assign your workforce identities access to AWS accounts. You can use application assignments to assign your users access to software as a service (SaaS) applications. With a single click, IAM Identity Center enabled application admins can assign access to your workforce users, and can also use application assignments to assign your users access to software as a service (SaaS) applications.
Source: https://docs.aws.amazon.com/singlesignon/latest/userguide/what-is.html
So both, IAM and IAM Identity Center manages access to AWS services and resources. The difference is that with IAM Identity Center you can manage all AWS accounts within an AWS Organization and also other cloud applications.
AWS IAM Identity Center is ideal for managing multiple AWS accounts.
When you open the IAM Identity Center the first time, you just need to enable it.
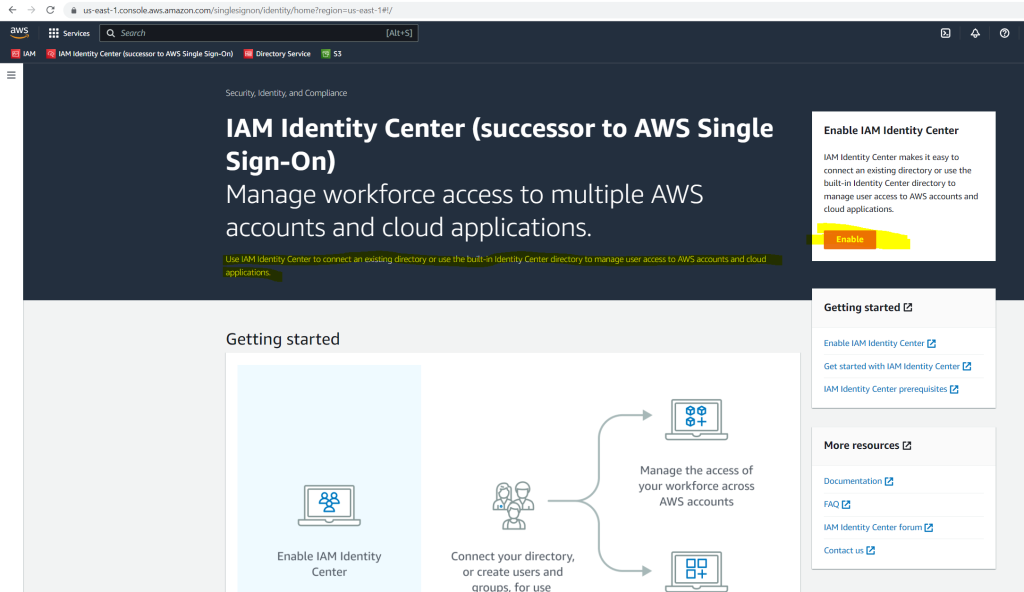
AWS will on the IAM page and the identity provider tab also show a banner to suggest to use intead of IAM the IAM Identity Center.
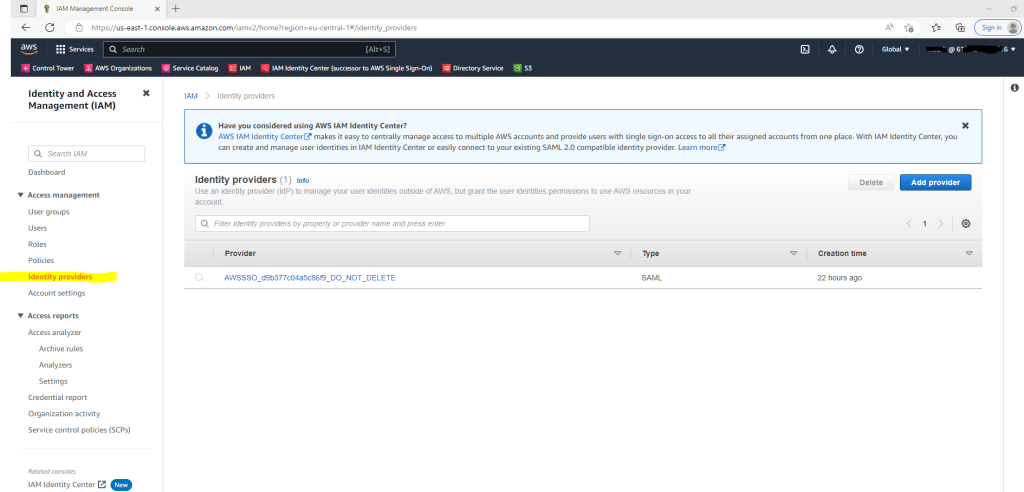
When you enable IAM Identity Center for the first time, it is automatically configured with an Identity Center directory as your default identity source.
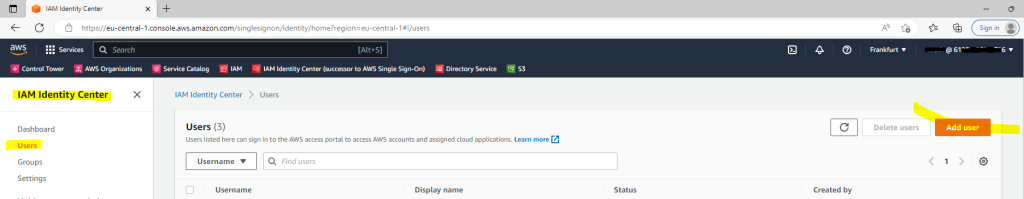
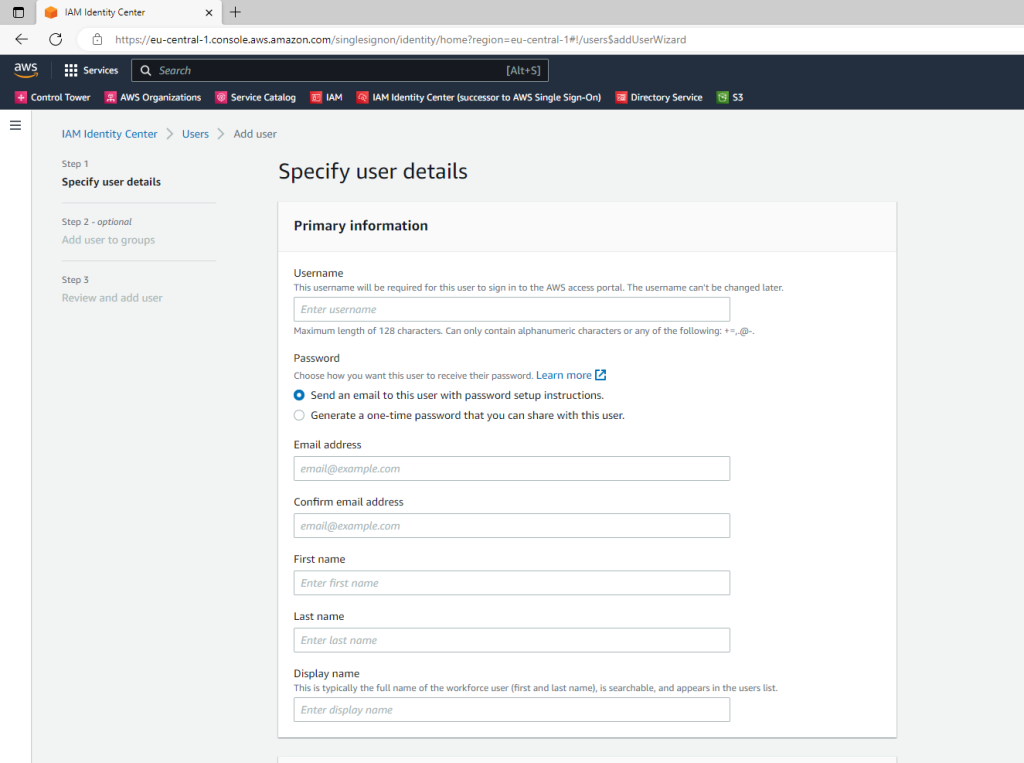
Users and groups that you create in your Identity Center directory are available in IAM Identity Center only. Use the following procedure to add users to your Identity Center directory. Alternatively, you can call the AWS API operation CreateUser to add users.
The invited user will get the below invitation email.
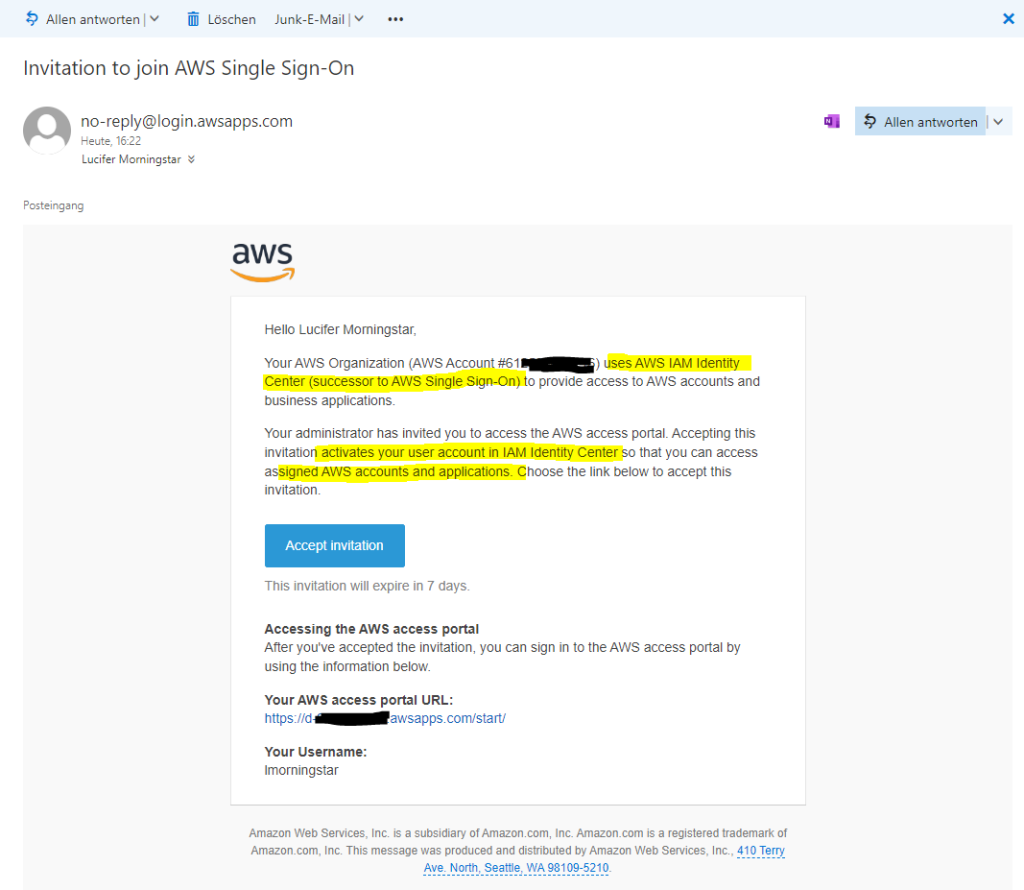
By clicking on the provided AWS access portal URL in the email the user can log in to the portal and choose an account to manage.
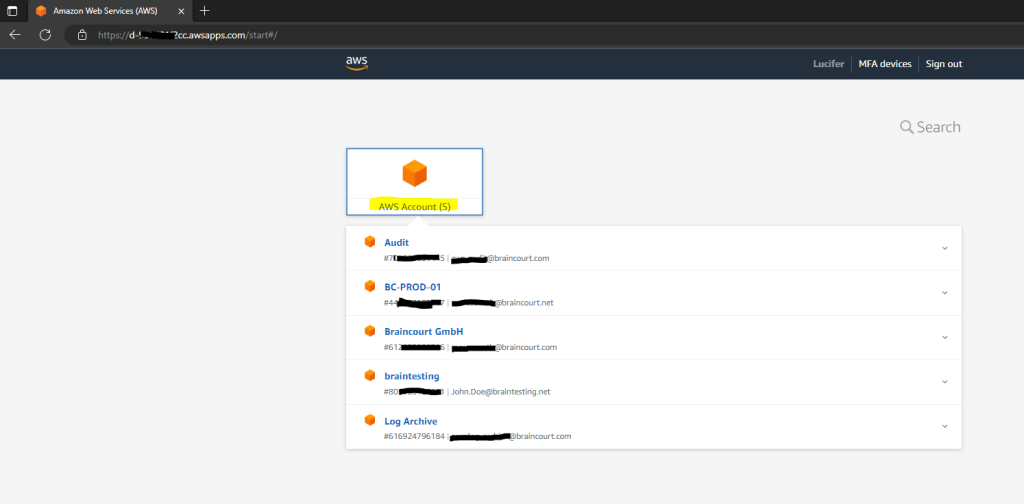
To assign to a user from the IAM Identity Center specific permissions for a specific AWS account, you can do this as follows.
IAM Identity Center –> Multi-account permissions –> AWS accounts
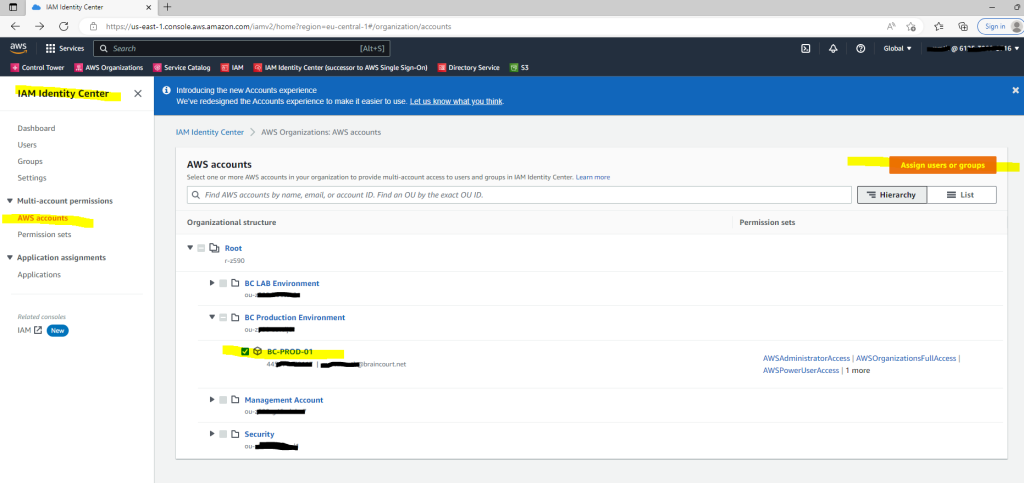
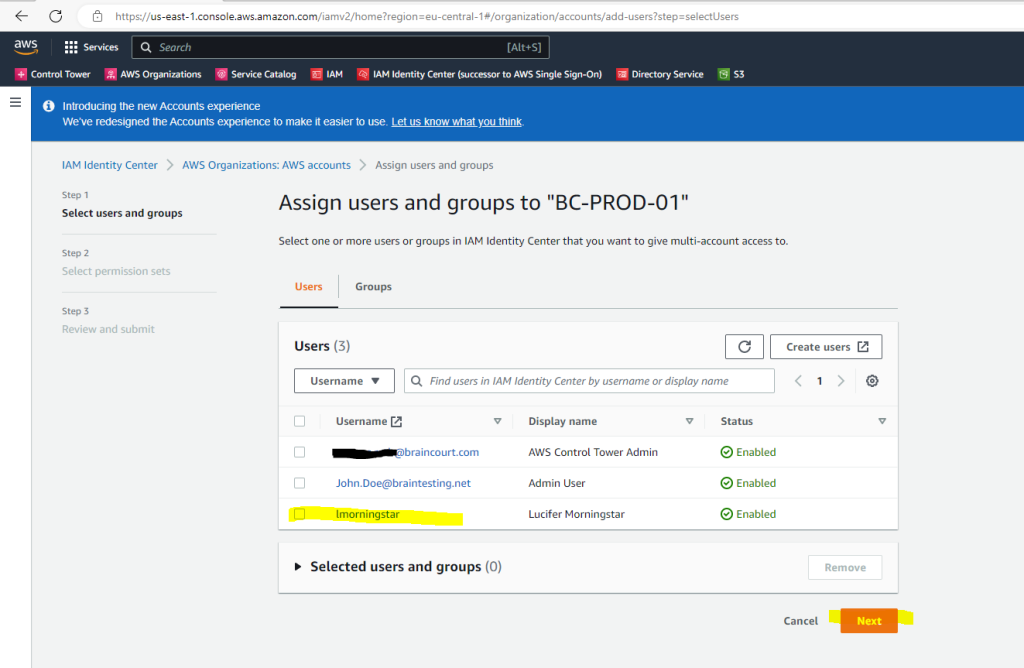
Here I will assign the user lmorningstar to the AWS account BC-PROD-01
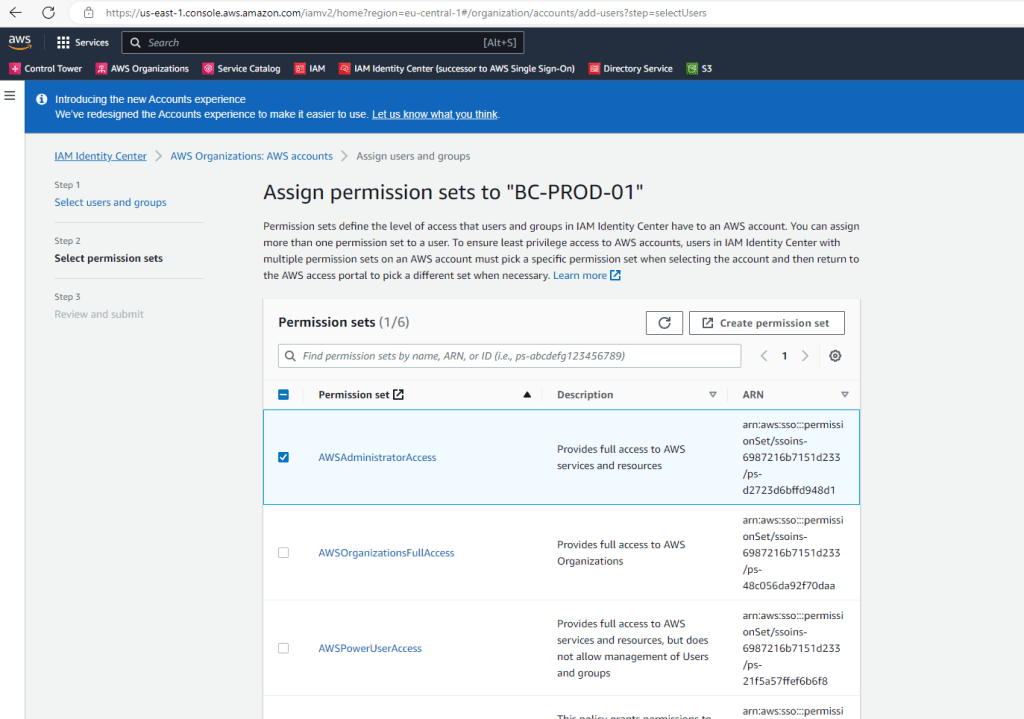
For this account I will gave the user the permission set AWSAdministratorAccess
Directory Service
AWS Directory Service provides multiple ways to use Microsoft Active Directory (AD) with other AWS services. Directories store information about users, groups, and devices, and administrators use them to manage access to information and resources. AWS Directory Service provides multiple directory choices for customers who want to use existing Microsoft AD or Lightweight Directory Access Protocol (LDAP)–aware applications in the cloud. It also offers those same choices to developers who need a directory to manage users, groups, devices, and access.
Source: https://docs.aws.amazon.com/directoryservice/latest/admin-guide/what_is.html
AWS Directory Service includes several directory types to choose from. These are:
- AWS Directory Service for Microsoft Active Directory (AWS Managed Microsoft AD)
is powered by an actual Microsoft Windows Server Active Directory (AD), managed by AWS in the AWS Cloud. AWS Managed Microsoft AD is your best choice if you need actual Active Directory features to support AWS applications or Windows workloads, including Amazon Relational Database Service for Microsoft SQL Server. It’s also best if you want a standalone AD in the AWS Cloud that supports Office 365 or you need an LDAP directory to support your Linux applications. - AD Connector
is a proxy service that provides an easy way to connect compatible AWS applications, such as Amazon WorkSpaces, Amazon QuickSight, and Amazon EC2 for Windows Server instances, to your existing on-premises Microsoft Active Directory. AD Connector also eliminates the need of directory synchronization or the cost and complexity of hosting a federation infrastructure. AD Connector is your best choice when you want to use your existing on-premises directory with compatible AWS services. - Simple AD
is a Microsoft Active Directory–compatible directory from AWS Directory Service that is powered by Samba 4. Simple AD supports basic Active Directory features such as user accounts, group memberships, joining a Linux domain or Windows based EC2 instances, Kerberos-based SSO, and group policies. AWS provides monitoring, daily snap-shots, and recovery as part of the service. - Amazon Cognito
is a user directory that adds sign-up and sign-in to your mobile app or web application using Amazon Cognito User Pools.
Source: https://docs.aws.amazon.com/directoryservice/latest/admin-guide/what_is.html#directoryoptions
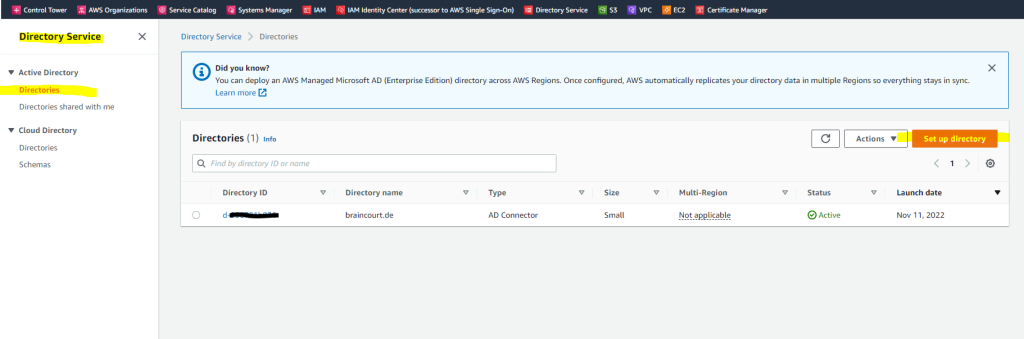
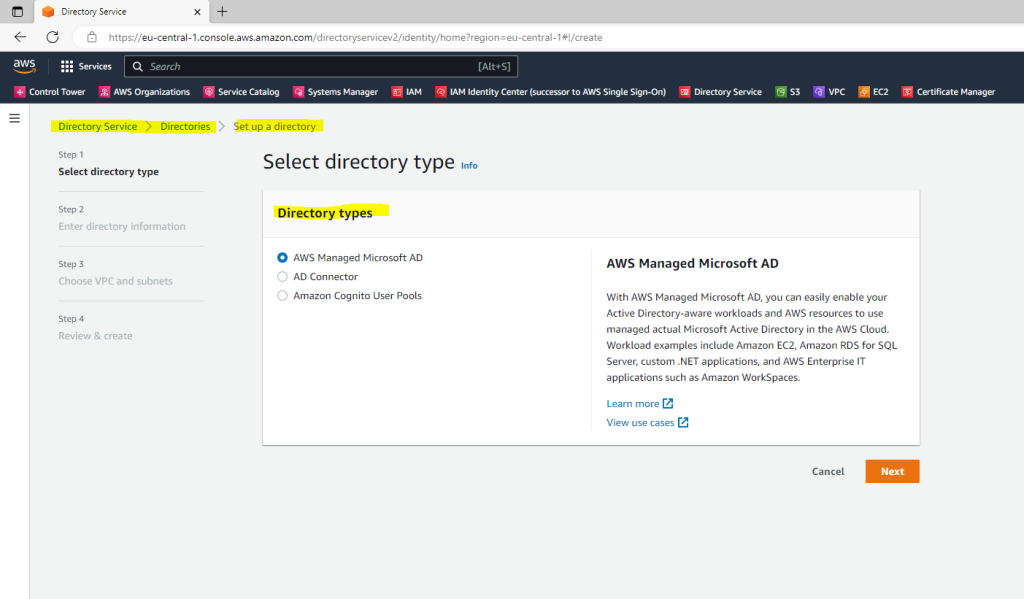
You can create these directories under AWS –> Directory Service –> Directories –> Click on Set up directory
As you can see I still created an AD Connector which redirects directory requests from AWS to my on-premise Active Directory and domain controllers.
About how to set up AD Connector you can read my following post.
About how to join EC2 instances (VMs) to your on-premise Active Directory by using the AD Connector, you can read my following post.
Links
Identity and access management for AWS Directory Service
https://docs.aws.amazon.com/directoryservice/latest/admin-guide/iam_auth_access.htmlWhat is IAM?
https://docs.aws.amazon.com/IAM/latest/UserGuide/introduction.htmlAWS Identity and Access Management (IAM)
https://aws.amazon.com/iam/What is IAM Identity Center?
https://docs.aws.amazon.com/singlesignon/latest/userguide/what-is.html
Tags In
Latest posts
Deploying NetApp Cloud Volumes ONTAP (CVO) in Azure using NetApp Console (formerly BlueXP) – Part 5 – Backup and Recovery
Follow me on LinkedIn


