External Identities in Azure Active Directory
In this post I want to accumulate all necessary informations I found about External Identities in Azure AD for B2B and B2C collaboration.
Microsoft has well documented this topic, so I only want to summarize and point out the key functions.
- External Identities documentation
- What are External Identities in Azure Active Directory?
- External Identities scenarios
- Collaborate with any partner using their identities
- What is guest user access in Azure Active Directory B2B?
- Understand the B2B user | Properties of an Azure Active Directory B2B collaboration user
- Source
- Can Azure AD B2B users be added as members instead of guests?
- Convert UserType
- Remove guest user limitations
- Can I update a guest user's email address?
- What is Azure Active Directory B2C?
- Custom-branded identity solution
External Identities documentation
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/
External Identities is a set of capabilities that enables organizations to secure and manage any external user, including customers and partners. Building on B2B collaboration, External Identities gives you more ways to interact and connect with users outside your organization.
What are External Identities in Azure Active Directory?
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/compare-with-b2c
With External Identities in Azure AD, you can allow people outside your organization to access your apps and resources, while letting them sign in using whatever identity they prefer. Your partners, distributors, suppliers, vendors, and other guest users can “bring their own identities.” Whether they’re part of Azure AD or another IT-managed system, or have an unmanaged social identity like Google or Facebook, they can use their own credentials to sign in. The identity provider manages the external user’s identity, and you manage access to your apps with Azure AD to keep your resources protected.
External Identities scenarios
Azure AD External Identities focuses less on a user’s relationship to your organization and more on the way an individual wants to sign in to your apps and resources. Within this framework, Azure AD supports a variety of scenarios from business-to-business (B2B) collaboration to app development for customers and consumers (business-to-consumer, or B2C).
- Share apps with external users (B2B collaboration). Invite external users into your own tenant as “guest” users that you can assign permissions to (for authorization) while allowing them to use their existing credentials (for authentication). Users sign in to the shared resources using a simple invitation and redemption process with their work account, school account, or any email account. And now with the availability of Self-service sign-up user flows (Preview), you can also provide a sign-in experience for your external users through the application you want to share. You can configure user flow settings to control how the user signs up for the application and that allows them to use their work account, school account, or any social identity (like Google or Facebook) they want to use. For more information, see the Azure AD B2B documentation.
- Develop apps intended for other Azure AD tenants (single-tenant or multi-tenant). When developing applications for Azure AD, you can target users from a single organization (single tenant), or users from any organization that already has an Azure AD tenant (called multi-tenant applications). These multi-tenant applications are registered once by yourself in your own Azure AD, but can then be used by any Azure AD user from any organization without any additional work on your part.
- Develop white-labeled apps for consumers and customers (Azure AD B2C). If you’re a business or developer creating customer-facing apps, you can scale to consumers, customers, or citizens by using an Azure AD B2C. Developers can use Azure AD as the full-featured identity system for their application, while letting customers sign in with an identity they already have established (like Facebook or Gmail). With Azure AD B2C, you can completely customize and control how customers sign up, sign in, and manage their profiles when using your applications. For more information, see the Azure AD B2C documentation.
Collaborate with any partner using their identities
With Azure AD B2B, the partner uses their own identity management solution, so there is no external administrative overhead for your organization. Guest users sign in to your apps and services with their own work, school, or social identities.
- The partner uses their own identities and credentials; Azure AD is not required.
- You don’t need to manage external accounts or passwords.
- You don’t need to sync accounts or manage account lifecycles.
What is guest user access in Azure Active Directory B2B?
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/what-is-b2b
Azure Active Directory (Azure AD) business-to-business (B2B) collaboration is a feature within External Identities that lets you invite guest users to collaborate with your organization. With B2B collaboration, you can securely share your company’s applications and services with guest users from any other organization, while maintaining control over your own corporate data. Work safely and securely with external partners, large or small, even if they don’t have Azure AD or an IT department. A simple invitation and redemption process lets partners use their own credentials to access your company’s resources. Developers can use Azure AD business-to-business APIs to customize the invitation process or write applications like self-service sign-up portals. For licensing and pricing information related to guest users, refer to Azure Active Directory pricing.
Starting March 31, 2021, Microsoft will no longer support the redemption of invitations by creating unmanaged Azure AD accounts and tenants for B2B collaboration scenarios. In preparation, we encourage customers to opt into email one-time passcode authentication. We welcome your feedback on this public preview feature and are excited to create even more ways to collaborate.
Understand the B2B user | Properties of an Azure Active Directory B2B collaboration user
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/user-properties
This article describes the properties and states of the B2B guest user object in Azure Active Directory (Azure AD) before and after invitation redemption. An Azure AD business-to-business (B2B) collaboration user is a user with UserType = Guest. This guest user typically is from a partner organization and has limited privileges in the inviting directory, by default.
Depending on the inviting organization’s needs, an Azure AD B2B collaboration user can be in one of the following account states:
- State 1: Homed in an external instance of Azure AD and represented as a guest user in the inviting organization. In this case, the B2B user signs in by using an Azure AD account that belongs to the invited tenant. If the partner organization doesn’t use Azure AD, the guest user in Azure AD is still created. The requirements are that they redeem their invitation and Azure AD verifies their email address. This arrangement is also called a just-in-time (JIT) tenancy or a “viral” tenancy.
- State 2: Homed in a Microsoft or other account and represented as a guest user in the host organization. In this case, the guest user signs in with a Microsoft account or a social account (google.com or similar). The invited user’s identity is created as a Microsoft account in the inviting organization’s directory during offer redemption.
- State 3: Homed in the host organization’s on-premises Active Directory and synced with the host organization’s Azure AD. You can use Azure AD Connect to sync the partner accounts to the cloud as Azure AD B2B users with UserType = Guest. See Grant locally-managed partner accounts access to cloud resources.
- State 4: Homed in the host organization’s Azure AD with UserType = Guest and credentials that the host organization manages.
Source
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/user-properties#source
This property indicates how the user signs in.
- Invited User: This user has been invited but has not yet redeemed an invitation.
- External Azure Active Directory: This user is homed in an external organization and authenticates by using an Azure AD account that belongs to the other organization. This type of sign-in corresponds to State 1.
- Microsoft account: This user is homed in a Microsoft account and authenticates by using a Microsoft account. This type of sign-in corresponds to State 2.
- Windows Server Active Directory: This user is signed in from on-premises Active Directory that belongs to this organization. This type of sign-in corresponds to State 3.
- Azure Active Directory: This user authenticates by using an Azure AD account that belongs to this organization. This type of sign-in corresponds to State 4.
Can Azure AD B2B users be added as members instead of guests?
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/user-properties#can-azure-ad-b2b-users-be-added-as-members-instead-of-guests
Typically, an Azure AD B2B user and guest user are synonymous. Therefore, an Azure AD B2B collaboration user is added as a user with UserType = Guest by default. However, in some cases, the partner organization is a member of a larger organization to which the host organization also belongs. If so, the host organization might want to treat users in the partner organization as members instead of guests. Use the Azure AD B2B Invitation Manager APIs to add or invite a user from the partner organization to the host organization as a member.
Convert UserType
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/user-properties#convert-usertype
It’s possible to convert UserType from Member to Guest and vice-versa by using PowerShell. However, the UserType property represents the user’s relationship to the organization. Therefore, you should change this property only if the relationship of the user to the organization changes. If the relationship of the user changes, should the user principal name (UPN) change? Should the user continue to have access to the same resources? Should a mailbox be assigned? We don’t recommend changing the UserType by using PowerShell as an atomic activity. Also, in case this property becomes immutable by using PowerShell, we don’t recommend taking a dependency on this value.
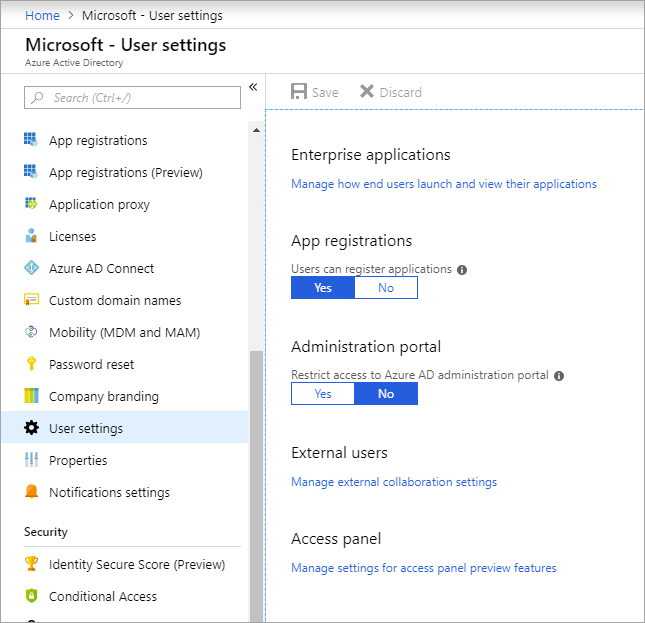
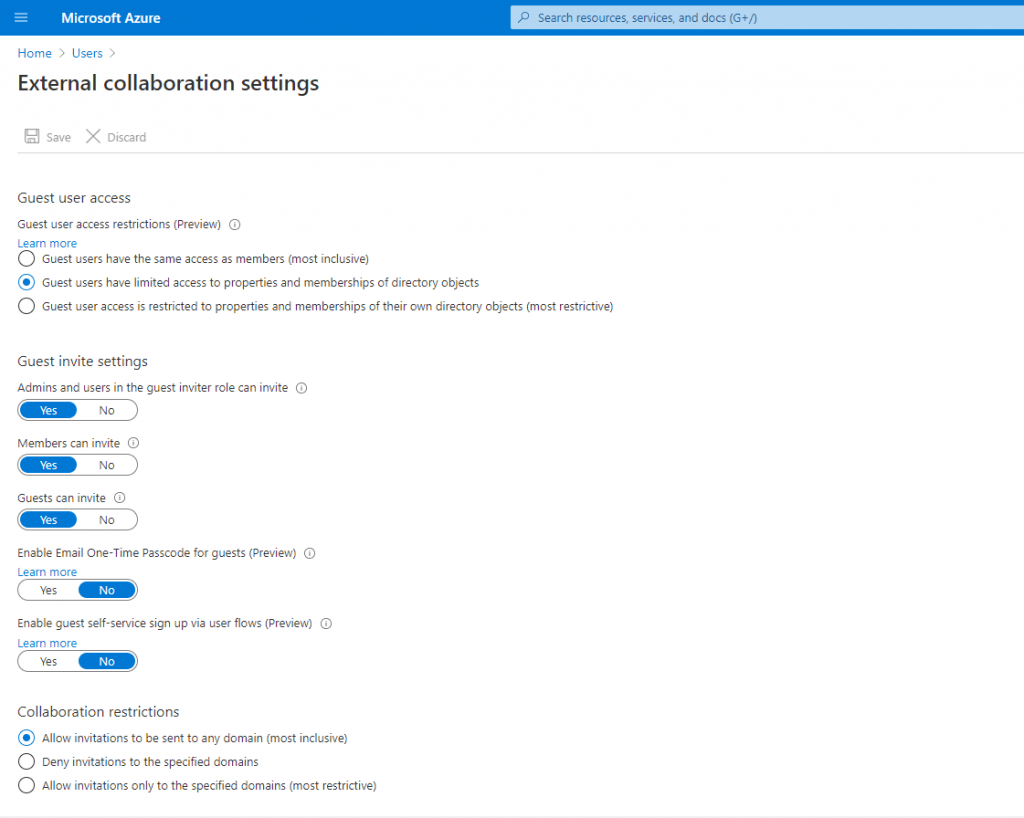
Remove guest user limitations
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/user-properties#remove-guest-user-limitations
There may be cases where you want to give your guest users higher privileges. You can add a guest user to any role and even remove the default guest user restrictions in the directory to give a user the same privileges as members.
It’s possible to turn off the default limitations so that a guest user in the company directory has the same permissions as a member user.
Can I update a guest user’s email address?
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/user-properties#can-i-update-a-guest-users-email-address
If a guest user accepts your invitation and they subsequently change their email address, the new email doesn’t automatically sync to the guest user object in your directory. The mail property is created via Microsoft Graph API. You can update the mail property via the Microsoft Graph API, the Exchange admin center, or Exchange Online PowerShell. The change will be reflected in the Azure AD guest user object.
What is Azure Active Directory B2C?
https://docs.microsoft.com/en-us/azure/active-directory-b2c/overview
Azure Active Directory B2C provides business-to-customer identity as a service. Your customers use their preferred social, enterprise, or local account identities to get single sign-on access to your applications and APIs.

Azure Active Directory B2C (Azure AD B2C) is a customer identity access management (CIAM) solution capable of supporting millions of users and billions of authentications per day. It takes care of the scaling and safety of the authentication platform, monitoring and automatically handling threats like denial-of-service, password spray, or brute force attacks.
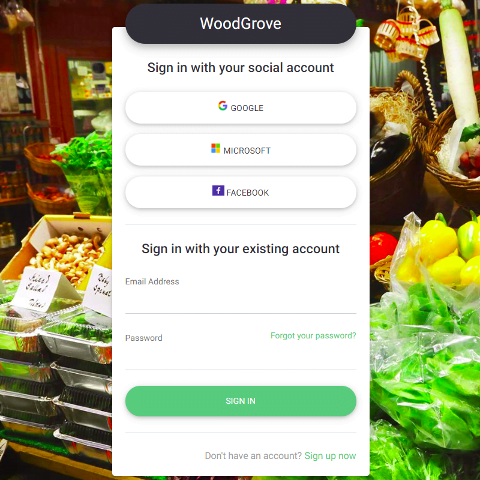
Custom-branded identity solution
https://docs.microsoft.com/en-us/azure/active-directory-b2c/overview#custom-branded-identity-solution
Azure AD B2C is a white-label authentication solution. You can customize the entire user experience with your brand so that it blends seamlessly with your web and mobile applications.
Customize every page displayed by Azure AD B2C when your users sign up, sign in, and modify their profile information. Customize the HTML, CSS, and JavaScript in your user journeys so that the Azure AD B2C experience looks and feels like it’s a native part of your application.
Tags In
Related Posts
Latest posts
Deploying NetApp Cloud Volumes ONTAP (CVO) in Azure using NetApp Console (formerly BlueXP) – Part 5 – Backup and Recovery
Follow me on LinkedIn


