How to Check if the Firewall Is Active on Linux (Across Different Distributions)
On Linux systems the active firewall service depends on the distribution. On Ubuntu or Debian you often check with ufw status or systemctl status nftables/iptables, while SUSE Linux Enterprise and openSUSE typically use SuSEfirewall2 (older) or firewalld like Red Hat–based systems (systemctl status firewalld).
CentOS the standard check is also systemctl status firewalld.
By default, netfilter (and tools like firewalld/UFW on top of it) restricts incoming traffic while allowing all outgoing traffic.
This means services on the host are protected unless explicitly opened, but applications running on the host can reach out freely. Outbound restrictions only apply if you add custom egress rules.
This way you can quickly verify if the local firewall is running and enforcing rules.
Finally no matter whether it’s RHEL, CentOS, Rocky, Alma, Oracle, or even SUSE/Debian/Ubuntu, under the hood, Linux firewalls are always based on the Netfilter framework in the kernel.
The older user-space tool is iptables, newer systems are moving to nftables.
iptables and nftables are user-space tools used to configure netfilter, the packet filtering and firewall framework inside the Linux kernel. Frontends such as firewalld, ufw, or the legacy SuSEfirewall2 simply provide a higher-level interface but still rely on iptables or nftables underneath.
Tools like firewalld (RHEL, CentOS, Rocky, Alma, newer SLES/openSUSE) or ufw (Ubuntu/Debian) are just frontends that make managing rules easier.
Netfilter who was written by Rusty Russel was merged in March 2000 into the Linux kernel 2.4.x and later kernel series. The predecessor was ipchains in the kernel 2.2 series.
Source: https://en.wikipedia.org/wiki/Netfilter
Ubuntu/Debian
Ubuntu/Debian distributions can use different firewall frontends such as UFW (Uncomplicated Firewall), or directly rely on iptables or the newer nftables framework.
Below the commands we can use to check if the firewall is enabled and active on Ubuntu/Debian distributions.
Below INPUT, FORWARD, OUTPUT chains all have policy ACCEPT. That means there is no active firewall on this Debian VM.
ACCEPT ==> means if no rule matches, just accept all traffic. This makes the zone effectively wide open, similar to the trusted zone. More here.
# iptables -L -n -v
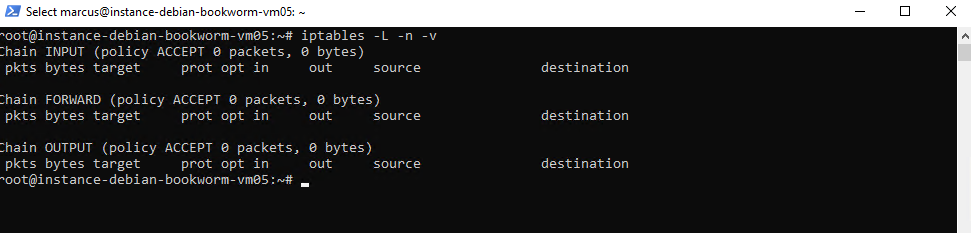
On modern Debian/Ubuntu, both nftables and iptables can exist, but only one is normally the active backend. So above iptables is active but allow all traffic.
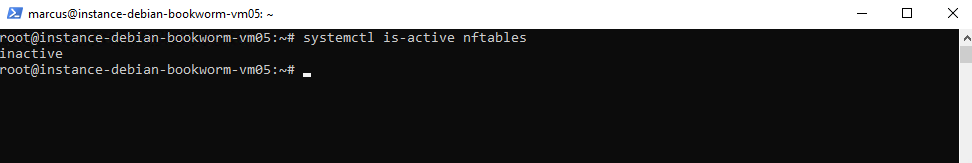
Check if nftables service is active.
# systemctl is-active nftables if active check the rules loaded # nft list ruleset
About using the UFW utility to configure the firewall (iptables and nftables) you can read my following post.
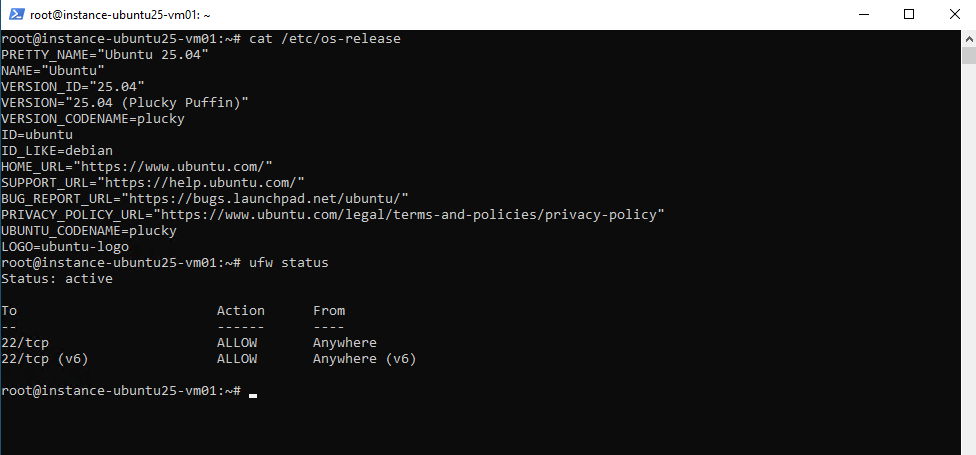
Here the UFW utility is installed and enabled and only inbound TCP 22 traffic is allowed.
Outbound traffic: allowed by default unless you explicitly configure rules to block it.
# ufw status
SUSE Linux Enterprise Server / openSUSE
SUSE Linux Enterprise Server 15 GA introduces firewalld as the new default software firewall, replacing SuSEfirewall2.
So therefore you can either read my following post or just look below at Red Hat–based systems or CentOS which also uses firewalld to control the firewall service (Netfilter framework).
Red Hat–based systems
Red Hat–based systems are Linux distributions that are derived from or closely follow Red Hat Enterprise Linux (RHEL). Examples include:
- CentOS (community rebuild of RHEL, now replaced by CentOS Stream)
- Rocky Linux (RHEL-compatible successor created by CentOS founder)
- AlmaLinux (another RHEL-compatible successor, backed by CloudLinux)
- Oracle Linux (RHEL-compatible distribution maintained by Oracle)
RHEL 7+ → uses firewalld (which can run on top of either iptables or nftables, depending on version).
# systemctl status firewalld
RHEL 8 and 9 → firewalld uses nftables by default, but can still fall back to iptables if configured.
firewall-cmd --state firewall-cmd --info-zone=public
CentOS
CentOS as mentioned uses also firewalld to control the firewall service (Netfilter framework). To check if the firewall is enabled and running we can run.
# systemctl status firewalld
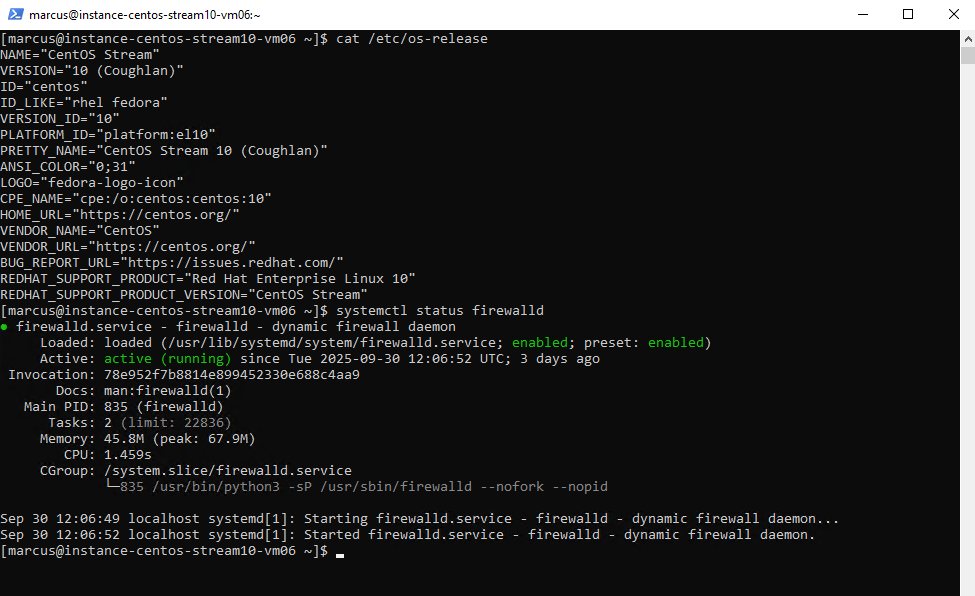
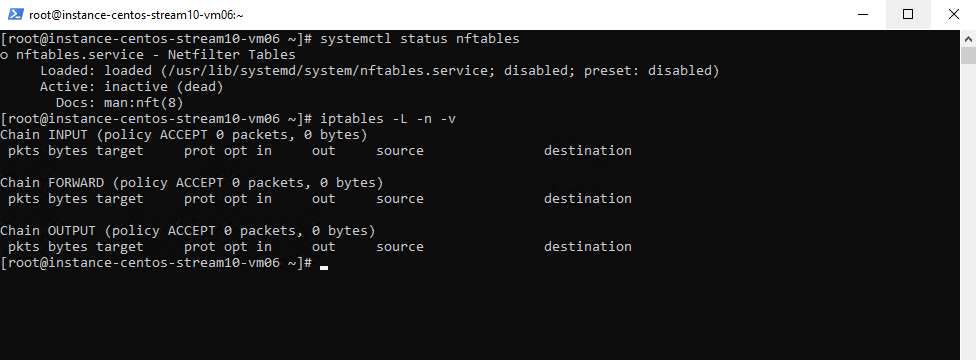
Below we can see that CentOS 10 (Stream) still using iptables as user-space tool to configure the Netfilter framework.
Therefore we can also use the following command to check if any traffic is denied.
Below INPUT, FORWARD, OUTPUT chains all have policy ACCEPT. That means there is no active firewall on this CentOS VM.
ACCEPT ==> means if no rule matches, just accept all traffic. This makes the zone effectively wide open, similar to the trusted zone. More here.
# iptables -L -n -v
About how to control the firewall by using the firewalld frontend/utility you can read my following post. SUSE Linux Enterprise Server 15 GA introduces firewalld as the new default software firewall, replacing SuSEfirewall2.
By running the two commands below, we can quickly determine the state of the firewall and which traffic finally is blocked.
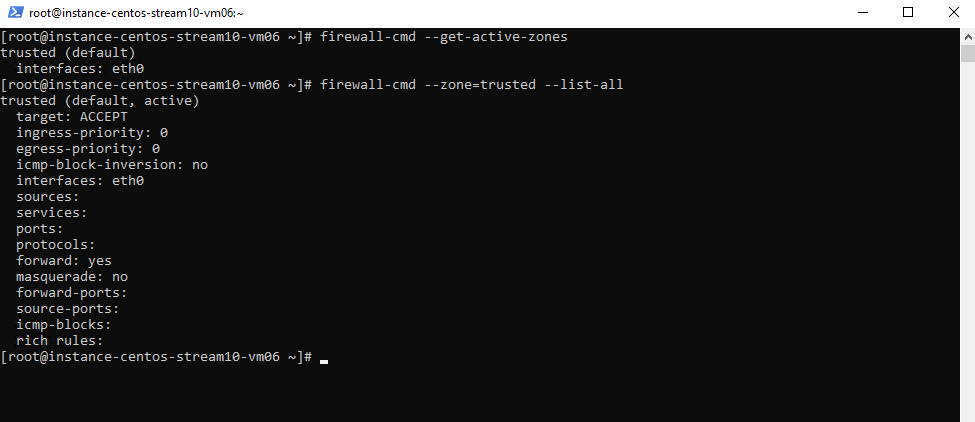
As mentioned by default, netfilter (and tools like firewalld/UFW on top of it) just restricts incoming traffic while allowing all outgoing traffic Outbound restrictions unless we didn’t add custom egress rules to restrict.
The output shows that the trusted zone is active on eth0 and also set as the default zone. Its target is ACCEPT, which means all incoming traffic is allowed without restrictions. No specific services, ports, or custom rules are defined, so the firewall here effectively behaves like it is disabled.
# firewall-cmd --get-active-zones # firewall-cmd --zone=trusted --list-all
Links
Firewall Ubuntu Server
https://documentation.ubuntu.com/server/how-to/security/firewalls/Getting Started with firewalld
https://docs.redhat.com/en/documentation/red_hat_enterprise_linux/7/html/security_guide/sec-using_firewallsfirewalld
https://firewalld.org/netfilter
https://www.netfilter.org/
Related Posts
Follow me on LinkedIn


