Set up Ubuntu’s Built-In Firewall
Ubuntu’s built-in firewall is named ufw (uncomplicated firewall).
Actually Ufw is just an utility which makes it easier to configure the complex IP packet filter rules for the Linux kernel firewall which is since Linux kernel 2.4.x and later Netfilter.
Netfilter who was written by Rusty Russel was merged in March 2000 into the Linux kernel 2.4.x and later kernel series. The predecessor was ipchains in the kernel 2.2 series.
Source: https://en.wikipedia.org/wiki/Netfilter
Introduction
Normally to configure these rules you used in past iptables and now the successor nftables (since Linux kernel 3.13).
Ufw is a frontend for iptables and nftables which makes it much easier to configure these rules.
Also iptables and nftables itself are just used to connect to Netfilter which is a framework inside the Linux kernel.
Netfilter offers various functions and operations for packet filtering, network address translation, and port translation, which provide the functionality required for directing packets through a network and prohibiting packets from reaching sensitive locations within a network.
Source: https://en.wikipedia.org/wiki/Netfilter
iptables is the userspace command line program used to configure the Linux 2.4.x and later packet filtering ruleset. It is targeted towards system administrators.
nftables is the successor of iptables, it allows for much more flexible, scalable and performance packet classification. This is where all the fancy new features are developed.
Source: https://www.netfilter.org/
nftables is now the default in and since Debian 10, Ubuntu 20.04, RHEL 8, SUSE 15 and Fedora 32.
To check the version of nftables you can use
$ nft -V

You can still use iptables in Ubuntu’s new releases (i.e, using iptables syntax with the nf_tables kernel subsystem) but with nf_tables as the default backend.
Source: https://wiki.debian.org/nftables
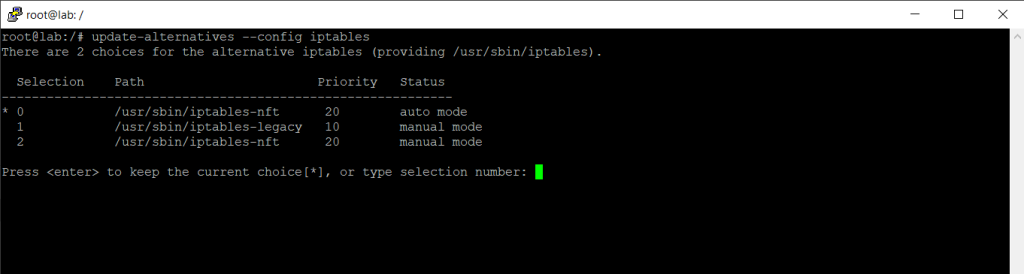
As you can see below wenn executing the update-alternative –config iptables command, you can also switch to the legacy iptables tool.
$ iptables -V
or
$ iptables-nft -V


By executing the update-alternative –config iptables command, you can see all installed versions.
Installation
Normally Ufw is by default installed on Ubuntu but not enabled, if not you can install it as follows.
$ apt update
$ apt upgrade
$ apt install ufw
Configuration
By default Ufw is disabled. So before enable Ufw, you should first configure and allow the ports you need to access Ubuntu, like SSH.
$ sudo ufw allow ssh
Or you can enter the port number directly for the service, this will allow TCP and UDP Port 22
$ sudo ufw allow 22
To just allow TCP traffic on the port
$ sudo ufw allow 22/tcp
To remove you can use
$ sudo ufw delete allow ssh
$ sudo ufw delete allow 22
Ufw by default will set the rule for incoming traffic, to block outbound traffic you can also specify a direction
$ sudo ufw reject out ssh
To remove the outbound rule use
$ sudo ufw delete reject out ssh
If you want to block traffic just from a specific IP
$ sudo ufw deny proto tcp from 8.8.8.8 to any port 22
If you want to allow traffic from just a specific IP
$ sudo ufw allow proto tcp from 192.168.0.2 to any port 22
To enable ufw
$ sudo ufw enable
To disable ufw
$ sudo ufw disable
To check the rules and if ufw is enabled
$ sudo ufw status
To reset the firewall to its default state
$ sudo ufw reset
To disable/enable IPv6
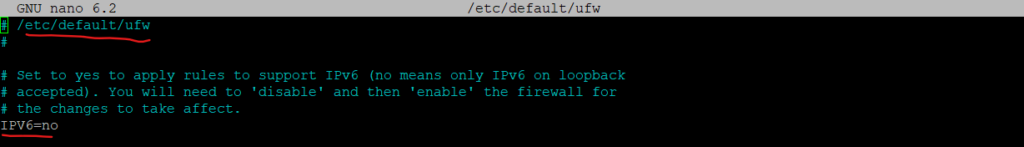
In order to disable/enable IPv6 you need to adjust the following file
/etc/default/ufw and its IPV6 parameter (yes or no).In order the changes here will immediately active you need to disable & enable
$ sudo ufw disable && sudo ufw enable
More here
https://ubuntu.com/server/docs/security-firewall
https://manpages.debian.org/bullseye/ufw/ufw.8.en.html#RULE_SYNTAX
Links
UncomplicatedFirewall
https://wiki.ubuntu.com/UncomplicatedFirewall
ufw – Uncomplicated Firewall
https://ubuntu.com/server/docs/security-firewall
netfilter
https://www.netfilter.org/
nftables
https://www.netfilter.org/projects/nftables/index.html
nftables
https://wiki.debian.org/nftables



