How to reveal hidden WLANs (Hidden SSID)
By default all WLAN access points send out their SSIDs in beacon frames as shown below in the screenshot.
These beacon frames belonging to the 802.11 Management Frames and will announce the presence of a wireless LAN and to synchronize the members with the access point.
The access point here is operating in infrastructure mode or so called infrastructure basic service set (BSS) regarding the IEEE 802.11 standards.
In contrast the ad-hoc mode is called independent Basic Service Set (IBSS).
Beacon frame is one of the management frames in IEEE 802.11 based WLANs. It contains all the information about the network. Beacon frames are transmitted periodically, they serve to announce the presence of a wireless LAN and to synchronize the members of the service set. Beacon frames are transmitted by the access point (AP) in an infrastructure basic service set (BSS). In IBSS network beacon generation is distributed among the stations. For the 2.4 GHz spectrum, when having more than 15 SSIDs on non-overlapping channels (or more than 45 in total), beacon frames start to consume significant amount of air time and degrade performance even when most of the networks are idle.
You can use WireShark to see these beacon frames when setting your WLAN interface in monitor mode as explained further down.
To filter out beacon frames we can apply the following filter.
wlan.fc.type_subtype == 8
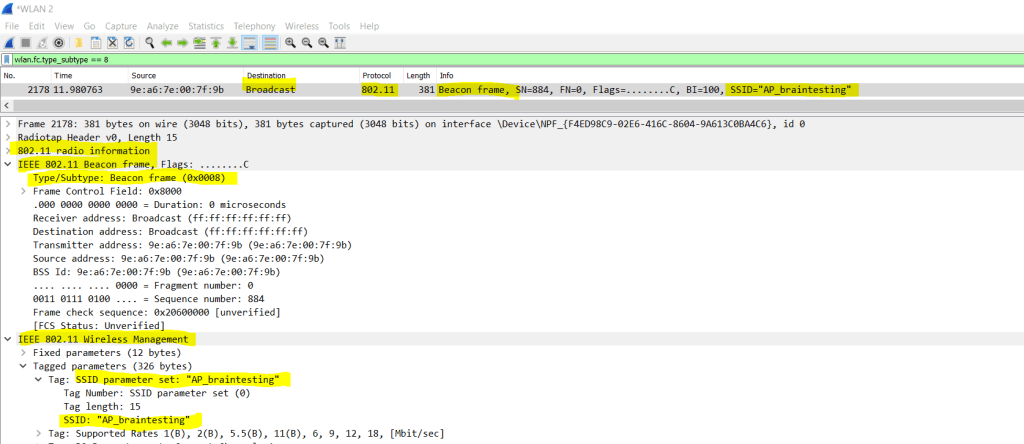
Below you can see regarding the filter that beacons have the subtype 0x8.
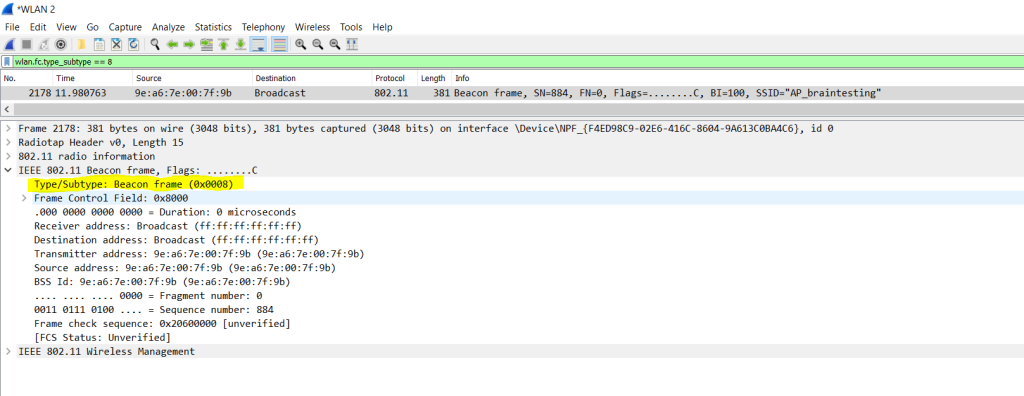
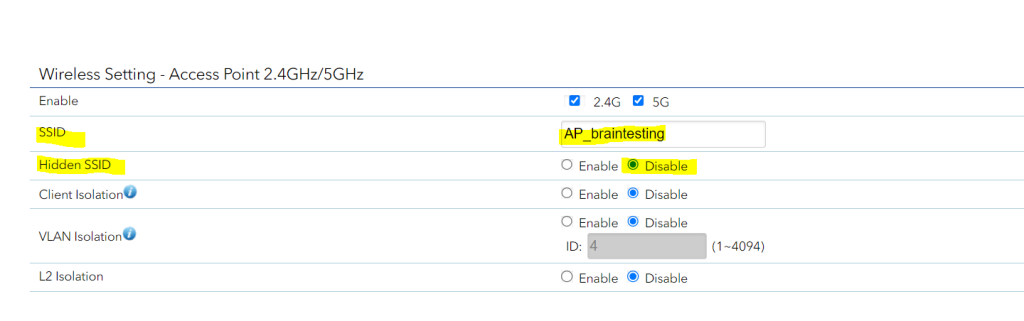
When you now set your access point to not send out its SSID, the beacon frames will disappear and the SSID is hidden from the access point.
From an security aspect it will just reduce the risk that attackers can see available access points in their directly neighborhood at first view without any effort.
To find hidden access points you can also use WireShark as shown above but this time we need to use another filter to focus on the probe request (subtype 0x4) management frames.
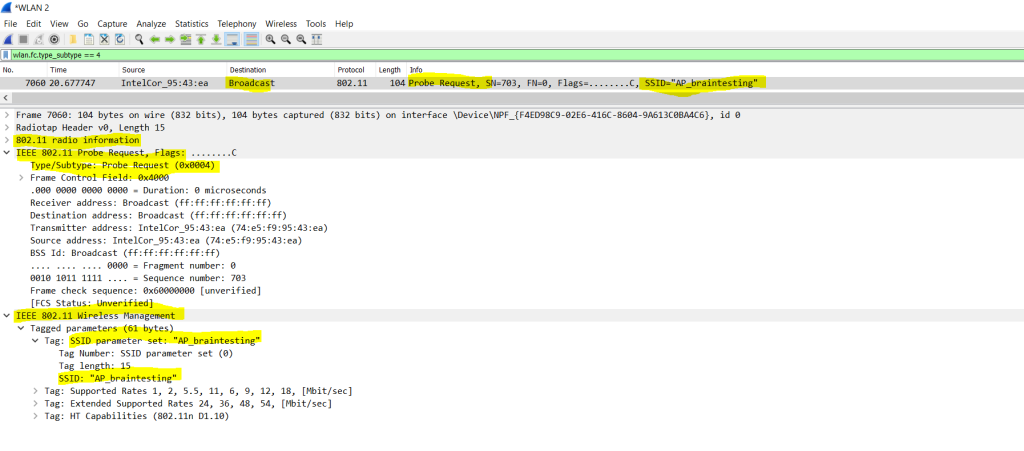
The probe request frames will be send out by clients they want to connect to the access point. The access point in return will also send out probe response packets that will contain the SSID of the network and therefore expose its presence.
So the feature to hide the SSID doesn’t really help to protect or hide your wireless network. We just need to wait for a legitimate client to connect to the access point.
The client therefore will generate a probe request packet to broadcast and the hidden access point will reply with a probe response packet.
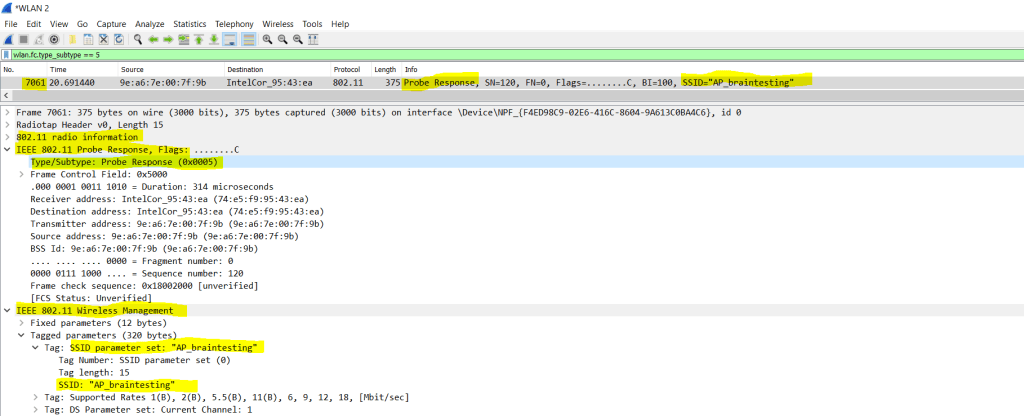
The probe response packet will include the SSID from the access point which we can tap using WireShark and enabled monitor mode from our WLAN adapter.
Below you will see a probe request packet send out from my computer as broadcast for the SSID AP_braintesting.
WireShark Filter: wlan.fc.type_subtype == 4
Below you will see the corresponding probe response packet to my previous request from my access point which also includes the SSID AP_braintesting.
WireShark Filter: wlan.fc.type_subtype == 5
802.11 Management Frames
802.11 Management Frames are used by clients to join and leave an access point in infrastructure mode –> infrastructure basic service set (BSS).
There are 12 802.11 Management Frames available as shown below, the three we used are highlited in bold.
- Association request (subtype 0x0)
- Association response (subtype 0x1)
- Reassociation request (subtype 0x2)
- Reassociation response (subtype 0x3)
- Probe request (subtype 0x4)
- Probe response (subtype 0x5)
- Beacon (subtype 0x8)
- ATIM (subtype 0x9)
- Disassociation (subtype 0xa)
- Authentication (subtype 0xb)
- Deauthentication (subtype 0xc)
- Action (subtype 0xd)
The filters in WireShark for these Management Frames are.
- Filter for all management frames: wlan.fc.type == 0
- Filter for Association Requests: wlan.fc.type_subtype == 0
- Filter for Association Responses: wlan.fc.type_subtype == 1
- Filter for Reassociation Requests: wlan.fc.type_subtype == 2
- Filter for Resssociation Responses: wlan.fc.type_subtype == 3
- Filter for Probe Requests: wlan.fc.type_subtype == 4
- Filter for Probe Responses: wlan.fc.type_subtype == 5
- Filter for Beacons: wlan.fc.type_subtype == 8
- Filter for ATIMs: wlan.fc.type_subtype == 9
- Filter for Disassociations: wlan.fc.type_subtype == 10
- Filter for Authentications: wlan.fc.type_subtype == 11
- Filter for Deauthentications: wlan.fc.type_subtype == 12
- Filter for Actions: wlan.fc.type_subtype == 13
Source: https://semfionetworks.com/wp-content/uploads/2021/04/wireshark_802.11_filters_-_reference_sheet.pdf
You can configure your access point to not broadcast its SSID in beacon frames as shown below for the Netgear WAX218 WiFi 6 wireless access point.
By default it will broadcast its SSID.
Enable Monitor Mode in WireShark
In order to capture raw 802.11 frames in WireShark you also need to install Npcap which can be installed side by side with WireShark.
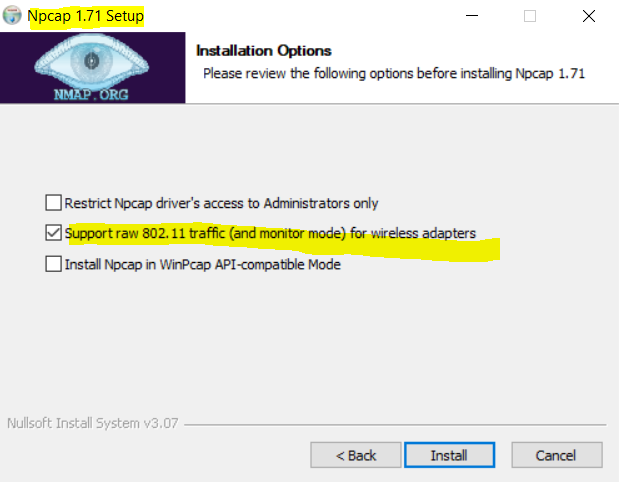
By default Support raw 802.11 traffic (and monitor mode) is checked to install.
Unfortunately, not all adapters support this mode, and several which do support it have limitations in their drivers.
The following page will attempt to document adapters that have been tested, and the degree of support they provide.
Npcap/WiFi adapters
https://secwiki.org/w/Npcap/WiFi_adaptersA common reason for an adapter to not show Monitor Mode in Wireshark is if you have WinPcap installed. Wireshark will not use Npcap if WinPcap is present.
My Intel Wireless-AC 9260 adapter will unfortunately not support monitor mode, therefore I was purchasing the following USB WLAN Adapter which will support monitor mode.
CSL – 300Mbit USB WLAN Adapter
https://www.amazon.de/gp/product/B00LLIOT34/ref=ppx_yo_dt_b_asin_title_o01_s00?ie=UTF8&psc=1
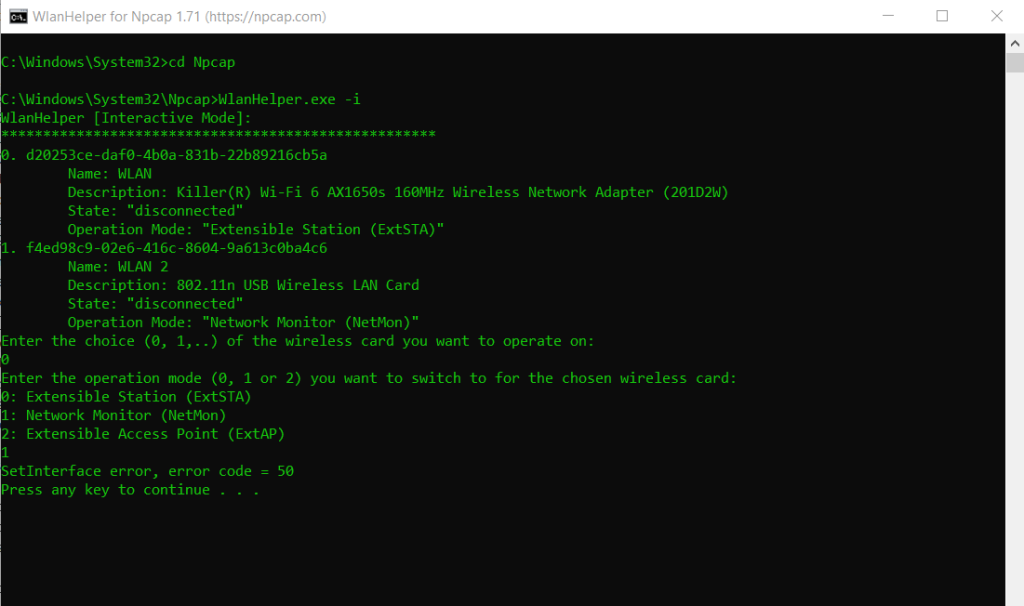
When you try to enable monitor mode on your adapter and it is not supported, you will get the following error.
The second one is my USB Adapter which will support monitor mode. I will try to enable monitor mode for the first one, my Intel Killer AX1650s adapter and will get the SetInterface error, error code = 1168.
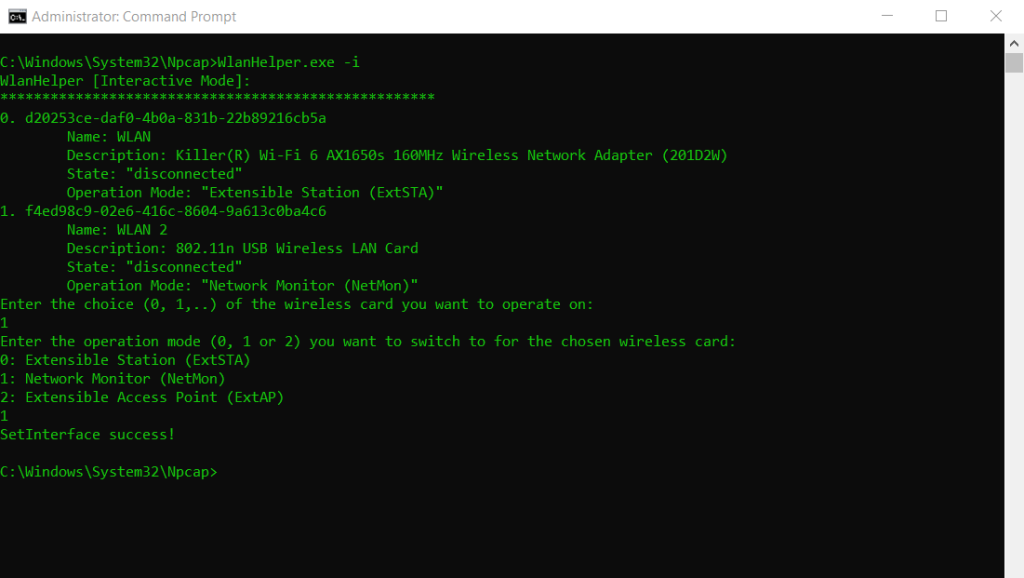
So now I will enable monitor mode on my supported WLAN USB adapter.
To enable monitor mode you can use the Wlanhelper tool which will be installed with Npcap. In Windows you will find the tool under C:Windowssystem32NpcapWlanHelper.exe.
Run WlanHelper.exe with Administrator privilege. If you use -i, follow the interactive prompts to choose your wireless adapter and select Network Monitor mode.
WlanHelper.exe also supports parameters to be used in an API manner, run WlanHelper.exe -h for details.
Source: https://npcap.com/guide/npcap-devguide.html#npcap-feature-dot11
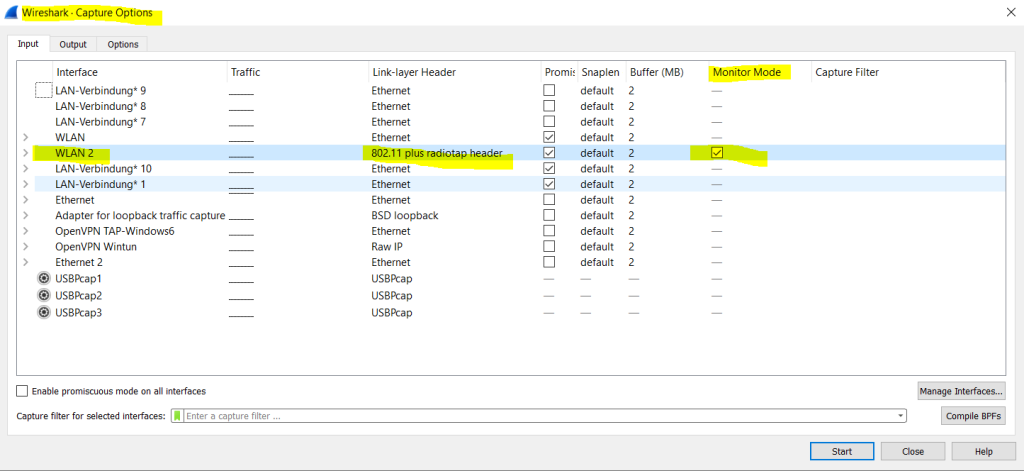
In WireShark you can now enable Monitor Mode under Capture –> Options by checking the Monitor Mode checkbox for your WLAN adapter.
Link
Npcap raw 802.11 feature
https://npcap.com/guide/npcap-devguide.html#npcap-feature-dot11Beacon frame
https://en.wikipedia.org/wiki/Beacon_frameNpcap/WiFi adapters
https://secwiki.org/w/Npcap/WiFi_adaptersWireshark Most Common 802.11 Filters
https://semfionetworks.com/wp-content/uploads/2021/04/wireshark_802.11_filters_-_reference_sheet.pdf


