How to use the Serial Console and Special Administration Console (SAC) for VMware vSphere Windows Virtual Machines
When managing Windows virtual machines in VMware vSphere, mostly we can rely on RDP or vSphere Console for access.
But what happens if the network stack isn’t available or the VM is stuck during boot?
In these cases, having a low-level management channel can make all the difference like when you think the virtual machine is stuck when updating the OS as shown in my post about mastering Windows updates here.
Windows provides this capability through the Serial Console and the Special Administration Console (SAC), enabled via Emergency Management Services (EMS).
Emergency Management Services (EMS) is a feature in Windows that allows remote management of a system via a serial port, especially useful for headless servers or troubleshooting boot issues.
By routing the VM’s virtual serial port to a network endpoint, VMware ESXi allows administrators to connect directly to SAC using a simple Telnet session.
This enables powerful out-of-band management features such as restarting services, initiating shutdowns, or troubleshooting issues even when the system is otherwise unresponsive.
This out-of-band channel (serial console access) is exposed directly by the hypervisor, so you retain console access even when the operating system cannot provide network connectivity.
SAC is built into the Windows kernel itself and runs independently of the regular user-mode components. This means it can provide out-of-band management features such as viewing system status, restarting services, or initiating shutdowns even when the operating system hasn’t fully booted or the network stack is unavailable.
In this post, we will see step by step how to enable EMS on a Windows VM, configure the virtual serial port in vSphere, and activate the necessary firewall rules on the ESXi host so that you can securely connect to SAC and gain reliable fallback access to your Windows virtual machines.
About how to access the SAC on Azure virtual machines you can read my following post.
About how to access the SAC on GCP virtual machines you can read my following post.
Enable SAC inside the Guest OS (Windows Server)
To be able to use SAC, we first need to enable the Emergency Management Services (EMS) on Windows by running the following commands.
When using the CMD we can run the following commands. About using PowerShell see further below.
# show configuration
> bcdedit /enum
# enabling SAC
# enables EMS for the Windows Boot Manager, which is the first stage of the boot process. Enable EMS before OS loads.
> bcdedit /set {current} bootems yes
# enables EMS for the Windows loader (the OS boot phase). Enable EMS during OS boot
> bcdedit /ems {current} on
# EMSPORT:1 refers to COM1. The baudrate is optional, and the default is 9,600 bps.
> bcdedit /emssettings EMSPORT:1 EMSBAUDRATE:115200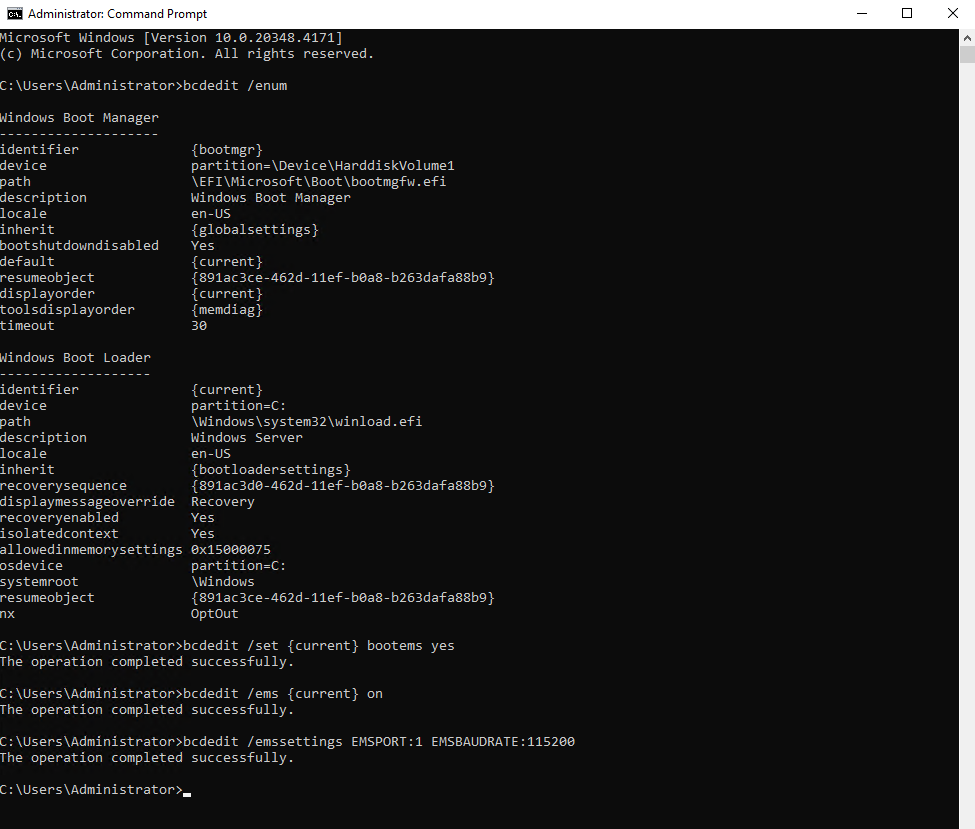
Validate if EMS is enabled successful.
> bcdedit /enum
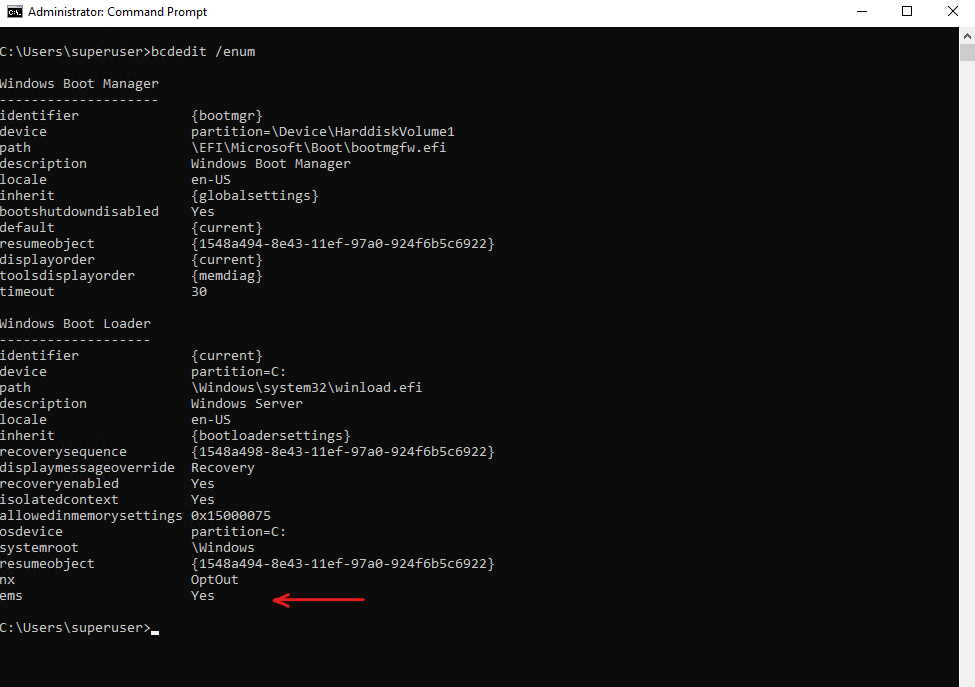
Reboot for it to take effect.
We can also use PowerShell but then we must quote the identifiers.
PS> bcdedit /enum
PS> bcdedit /set "{bootmgr}" bootems yes
PS> bcdedit /ems "{current}" on
PS> bcdedit /emssettings EMSPORT:1 EMSBAUDRATE:115200Add a Virtual Serial Port in vSphere
To add a virtual port in vSphere, we first need to shutdown and power off the virtual machine for which we want to enable the serial console and Special Administration Console (SAC) .
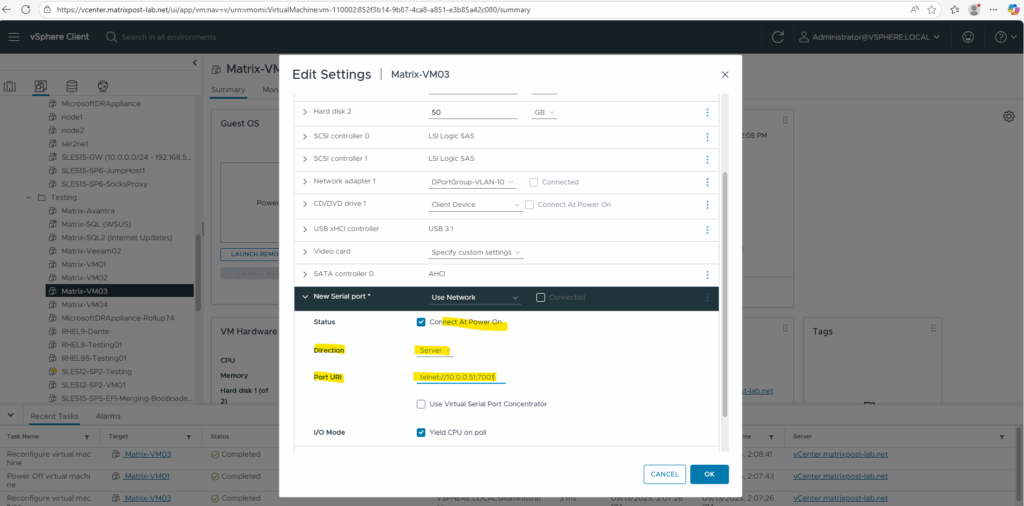
Edit VM settings → Add other device → Serial port.
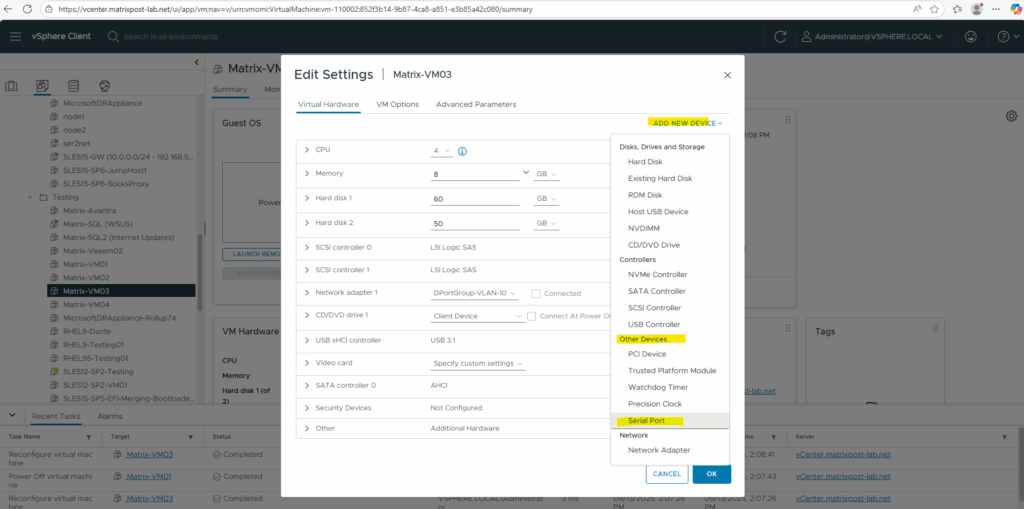
Choose where the serial port connects:
- Use Network ==> Connects the VM serial port over TCP/IP
- Use named pipe ==> Creates a bidirectional communication channel between the VM and another process (e.g., a terminal emulator or another VM).
- Use physical serial port ==> Connects the VM to a real serial port on the host.
- Use output file ==>Logs serial output to a file.
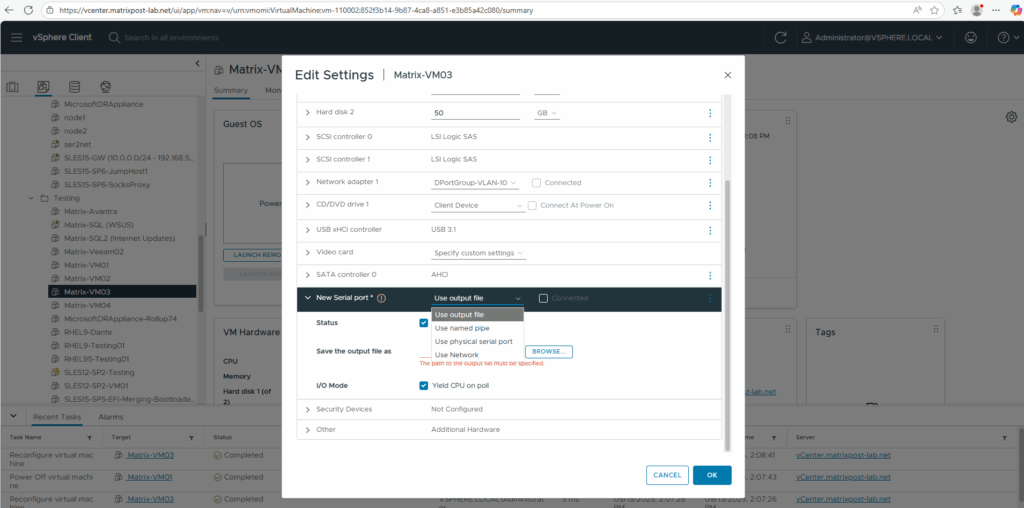
For the Direction we need to select Server, further make sure Connect At Power On is checked and we can also check Yield CPU on poll.
Direction Server ==> Select this if you want your VM to be a listening endpoint that waits for an external device or another VM to connect to it.
Yield CPU on poll ==> This option prevents the guest from consuming excessive CPUs.
For the Port URI I will use the following telnet command line.
telnet://<VMkernel interface IP address ESXi Host the VM is running on>:<free useable port number> telnet://10.0.0.51:7001
Enable VMware Remote Serial Port Service
We also need to allow connectivity to the remote serial port on the ESXi Host where the virtual machine is running we want to access the SAC.
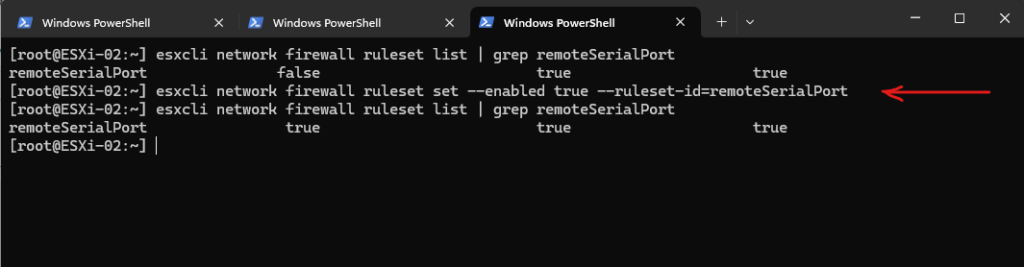
By default the Remote Serial Port service is disabled on the ESXi host.
Connect to the corresponding ESXi Host by using SSH and execute the following command.
# check if the Remote Serial Port service is still disabled (default) [root@ESXi-02:~] esxcli network firewall ruleset list | grep remoteSerialPort # Enable the remoteSerialPort ruleset [root@ESXi-02:~] esxcli network firewall ruleset set --enabled true --ruleset-id=remoteSerialPort # Validate that the remoteSerialPort service is now enabled. [root@ESXi-02:~] esxcli network firewall ruleset list | grep remoteSerialPort
The port number we will finally use for the serial port connection of course shouldn’t be currently in use by the ESXi host. Make sure to use a port that is not used for any other VMkernel service such as vMotion, etc.
Connect to the SAC
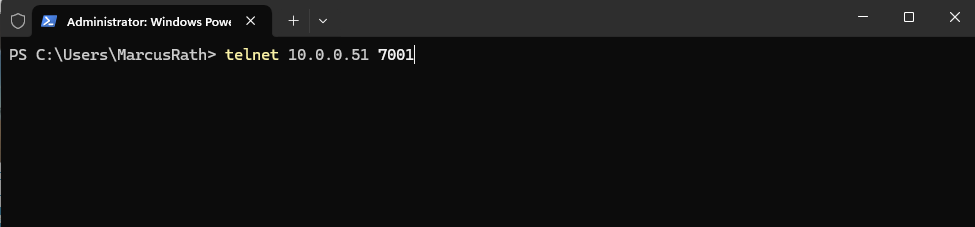
We now should be able to connect to our virtual machine’s SAC we exposed its virtual serial port in vSphere previously by using telnet from any remote computer which finally can access the ESXi host’s VMkernel adapter IP address.
10.0.0.51 is the IP address of the ESXi Host (its VMkernel adpater) where the virtual machine named Matrix-VM03 is running and the port number 7001 we set previously for the virtual serial port of this VM.
PS> telnet 10.0.0.51 7001
Press Enter to get into the SAC, finally the same as for Azure or GCP virtual machines.

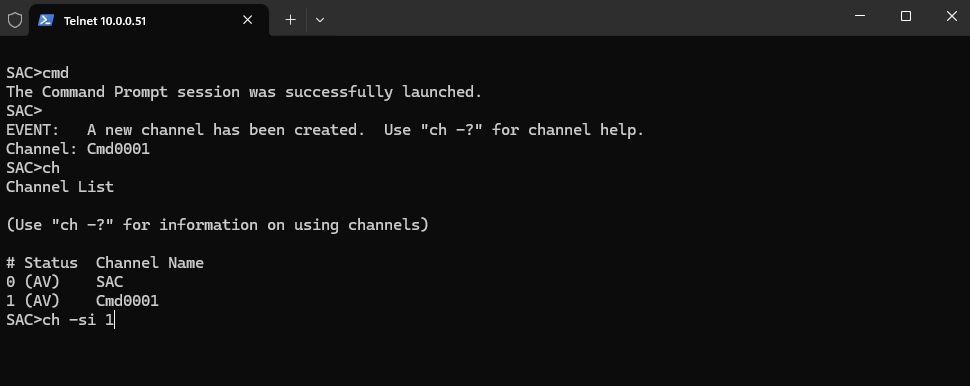
We are now connected to the virtual machine’s SAC.

Enter the following commands to finally open an administrator command prompt (CMD).
ch → Channel management commands.
ch -si 1 → switch to channel 1 and interact with it (the -si stands for “switch and interact”).
SAC>cmd SAC>ch CMD is on channel 1. Switch to a channel by its number SAC>ch -si 1
Enter admin login credentials for the VM (either local users then just leave the Domain part blank or domain users).


We are now connected with an administrator command prompt (CMD) for our virtual machine.
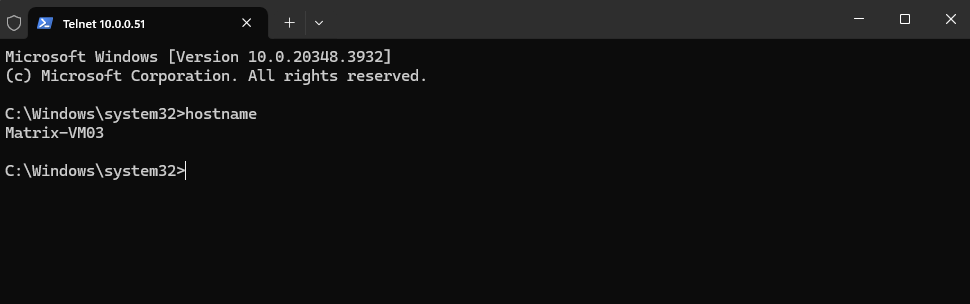
From here we can also start a PowerShell instance by just enter PowerShell in the CMD instance and press Enter.
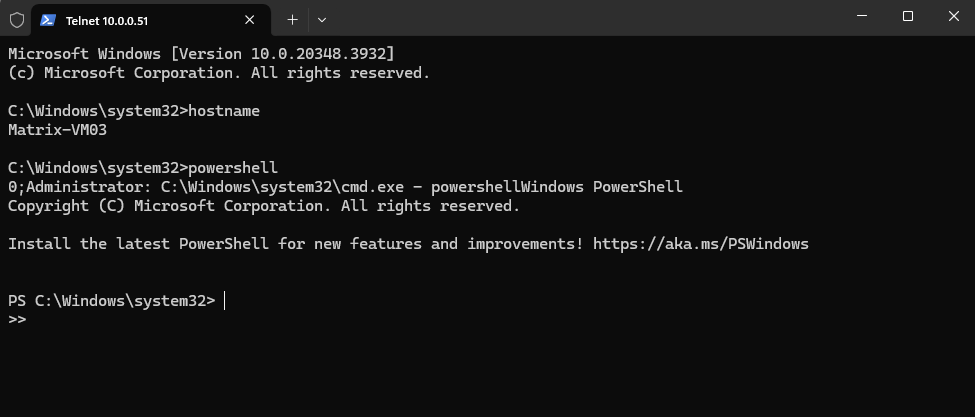
When rebooting the virtual machine, we are still connected through the hypervisor (ESXi Host) and the virtual machine’s serial console to the SAC.
Here we are still connected during the boot phase of the OS.
As soon as the kernel is booted we can also connect to the CMD (or PowerShell triggered from CMD) no matter if the network stack is already loaded or working.
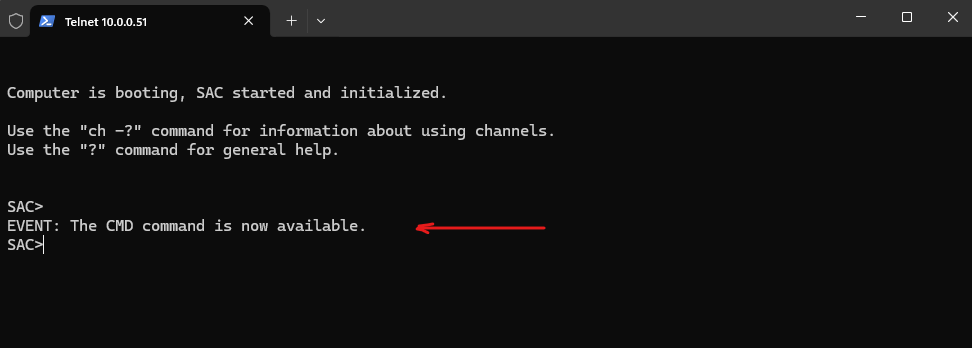
Special Administration Console (SAC)
SAC is a low-level console designed for emergency management, especially when the system is otherwise unresponsive. It doesn’t have a traditional “exit” because it’s not a shell, it’s a persistent interface tied to the system’s serial port.
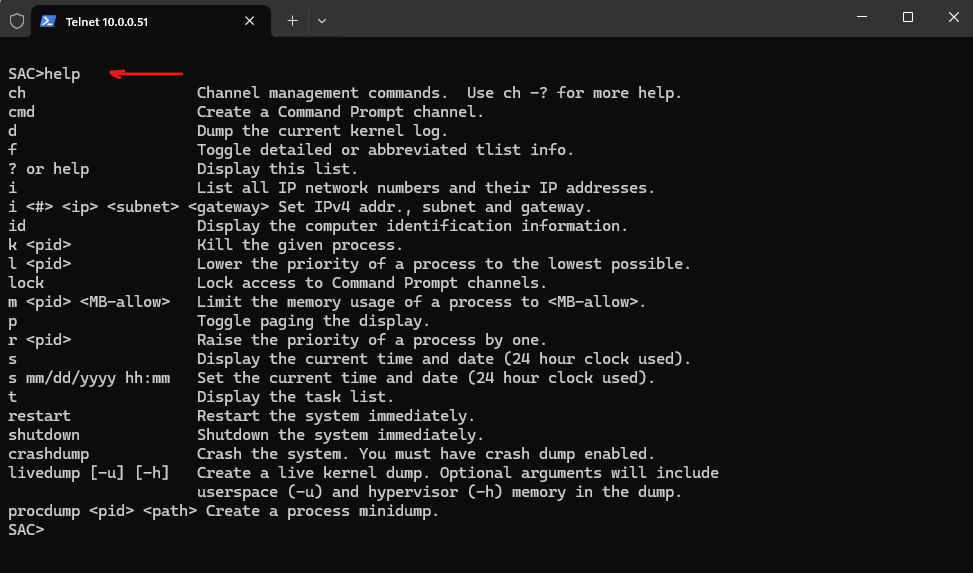
When you’re inside the SAC (Special Administration Console) and type help, you’ll get a list of available commands and channels.
SAC>help
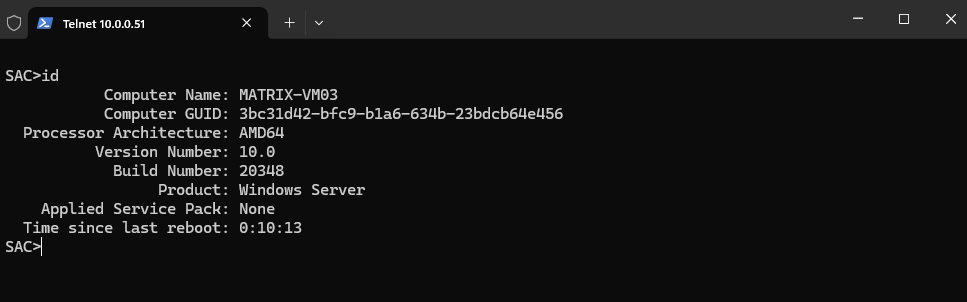
Display the computer identification information
SAC>id
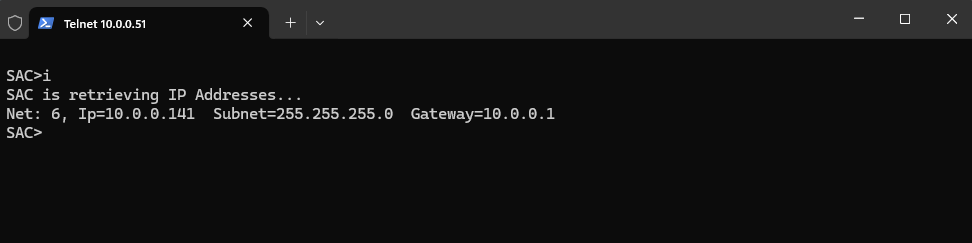
List all IP network numbers and their IP addresses
SAC>i
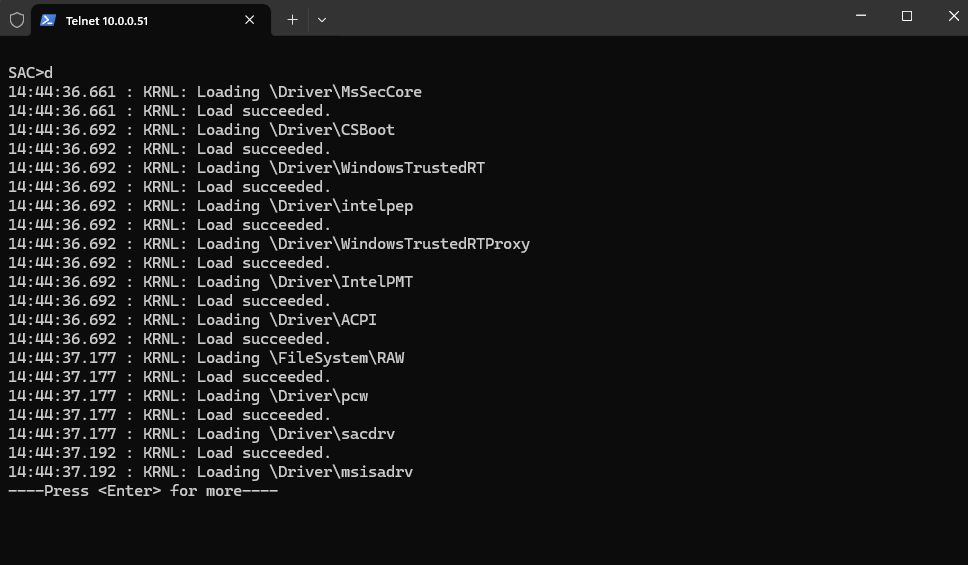
Dump the current kernel log
SAC>d
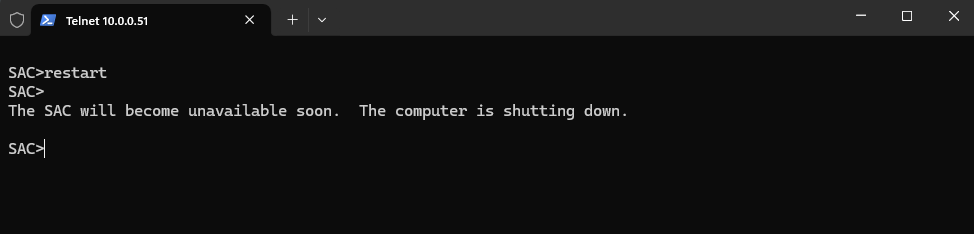
Restart the system immediatley
SAC>restart
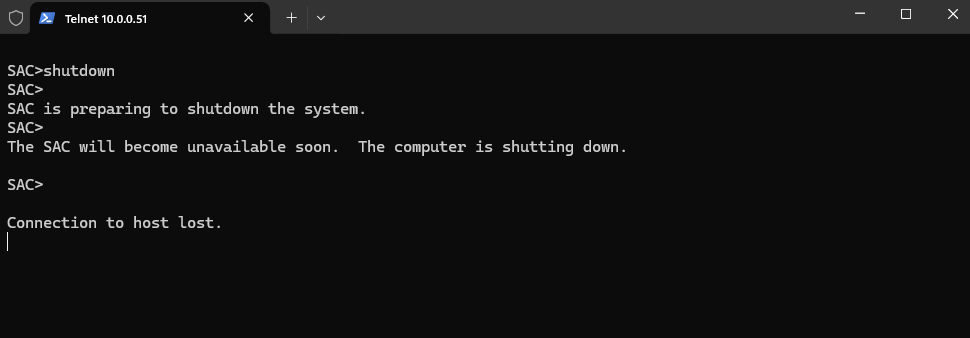
Shutdown the system immediately
SAC>shutdown
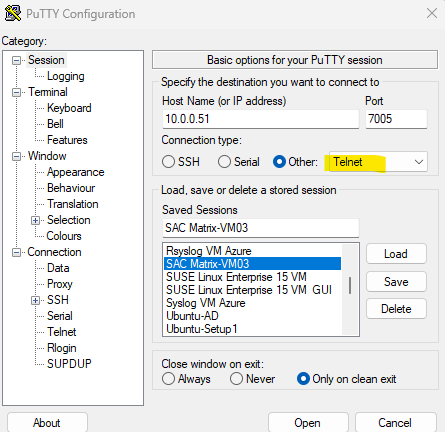
Using PuTTY as terminal utility for SAC
A common issue when using PowerShell’s telnet client to connect to SAC, console output corruption or crashes, while PuTTY works fine.
PowerShell’s telnet is not a full-featured terminal emulator and lacks proper handling of control characters, ANSI sequences, and buffering. Often fails with interactive or dynamic console output, like SAC’s real-time logs and command responses.
PuTTY in contrast is a true terminal emulator and handles serial and telnet sessions with full support for console features, much more stable for SAC and other low-level interfaces.
Links
BCDEdit /set
https://learn.microsoft.com/en-us/windows-hardware/drivers/devtest/bcdedit–setBCDEdit Options Reference
https://learn.microsoft.com/en-us/windows-hardware/drivers/devtest/bcd-boot-options-referenceBCDEdit Command-Line Options
https://learn.microsoft.com/en-us/windows-hardware/manufacture/desktop/bcdedit-command-line-options?view=windows-11Azure Serial Console
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/serial-console-overviewAzure Serial Console for Windows
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/serial-console-windowsAzure Serial Console for Linux
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/linux/serial-console-linuxSpecial Administration Console (SAC)
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/cc787940(v=ws.10)Common scenarios for accessing the serial console
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/serial-console-windows#common-scenarios-for-accessing-the-serial-consoleRunning Remote Commands
https://learn.microsoft.com/en-us/powershell/scripting/security/remoting/running-remote-commands?view=powershell-7.4Windows Commands – CMD and PowerShell
https://learn.microsoft.com/en-us/troubleshoot/azure/virtual-machines/windows/serial-console-cmd-ps-commands


