Set up Active Directory Federation Services (AD FS 5.0) – Certificate Requirements – Part 3
In an ADFS environment, certificates are one of the most critical and important parts, therefore I want to document this in a separate post, besides the vast amount of information about it.
This post is split into multiple parts
Part 1 … will cover the installation from the internal ADFS ServerPart 2 … will cover the installation from the ADFS Reverse Proxy Server in the perimeter network
Part 3 … will cover all about certificates for an ADFS environmentPart 4 … we will create an ASP.NET Web Application (.NET Framework -Web Forms) and configure it to be claim aware using WS-FED.
Part 5 … we will create an ASP.NET Core Web Application (MVCs) and configure it to be claim aware using WS-FED.
Part 6 … we will create an ASP.NET Web Application (.NET Framework – MVC) and configure it to be claim aware by using OAuth 2.0 and OpenID Connect.
Part 7 … we will create an ASP.NET Core Web Application (MVC) and configure it to be claim aware by using OAuth 2.0 and OpenID Connect.
Part 8 … will explain and list all identity protocols, AD FS supports.
Certificate requirements
AD FS Requirements
https://docs.microsoft.com/en-gb/windows-server/identity/ad-fs/overview/ad-fs-requirements#BKMK_1
Each AD FS and Web Application Proxy server has an SSL certificate to service HTTPS requests to the federation service. The Web Application Proxy can have additional SSL certificates to service requests to published applications.
Recommendation: Use the same SSL certificate for all AD FS federation servers and Web Application proxies
Requirements:
SSL certificates on federation servers must meet the following requirements
- Certificate is publicly trusted (for production deployments)
- Certificate contains the Server Authentication Enhanced Key Usage (EKU) value
- Certificate contains the federation service name, such as “fs.contoso.com” in the Subject or Subject Alternative Name (SAN)
- For user certificate authentication on port 443, certificate contains “certauth.<federation service name>”, such as “certauth.fs.contoso.com” in the SAN
- For device registration or for modern authentication to on premises resources using pre-Windows 10 clients, the SAN must contain “enterpriseregistration.<upn suffix>” for each UPN suffix in use in your organization.
SSL certificates on the Web Application Proxy must meet the following requirements
- If the proxy is used to proxy AD FS requests that use Windows Integrated Authentication, the proxy SSL certificate must be the same (use the same key) as the federation server SSL certificate
- If the AD FS property “ExtendedProtectionTokenCheck” is enabled (the default setting in AD FS), the proxy SSL certificate must be the same (use the same key) as the federation server SSL certificate
- Otherwise, the requirements for the proxy SSL certificate are the same as those for the federation server SSL certificate
Service Communication Certificate
This certificate is not required for most AD FS scenarios including Azure AD and Office 365. By default, AD FS configures the SSL certificate provided upon initial configuration as the service communication certificate.
Recommendation:
- Use the same certificate as you use for SSL.
Token Signing Certificate
This certificate is used to sign issued tokens to relying parties, so relying party applications must recognize the certificate and it’s associated key as known and trusted. When the token signing certificate changes, such as when it expires and you configure a new certificate, all relying parties must be updated.
Recommendation: Use the AD FS default, internally generated, self-signed token signing certificates.
Requirements:
- If your organization requires that certificates from the enterprise PKI be used for token signing, this can be done using the SigningCertificateThumbprint parameter of the Install-AdfsFarm cmdlet.
- Whether you use the default internally generated certificates or externally enrolled certificates, when the token signing certificate is changed you must ensure all relying parties are updated with the new certificate information. Otherwise, logons to any relying parties not updated will fail.
Obtain and Configure TS and TD Certificates for AD FS
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/operations/configure-ts-td-certs-ad-fs
This topic describes tasks and procedures that you can perform to ensure that your AD FS token signing and token decryption certificates are up to date.
Token signing certificates are standard X509 certificates that are used to securely sign all tokens that the federation server issues. Token decryption certificates are standard X509 certificates that are used to decrypt any incoming tokens. They are also published in federation metadata.
Token Encrypting/Decrypting Certificate
This certificate is used by claims providers who encrypt tokens issued to AD FS.
Recommendation: Use the AD FS default, internally generated, self-signed token decrypting certificates.
Requirements:
- If your organization requires that certificates from the enterprise PKI be used for token signing, this can be done using the DecryptingCertificateThumbprint parameter of the Install-AdfsFarm cmdlet.
- Whether you use the default internally generated certificates or externally enrolled certificates, when the token decrypting certificate is changed you must ensure all claims providers are updated with the new certificate information. Otherwise, logons using any claims providers not updated will fail.
Certificates that are used for token-signing and token-decrypting/encrypting are critical to the stability of the Federation Service. Customers managing their own token-signing & token-decrypting/encrypting certificates should ensure that these certificates are backed up and are available independently during a recovery event.
AD FS Troubleshooting – Certificates
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/troubleshooting/ad-fs-tshoot-certs
Add a Token-Signing Certificate
As Certification Template for the Token Signing Certificate you can use a Web Server Template.
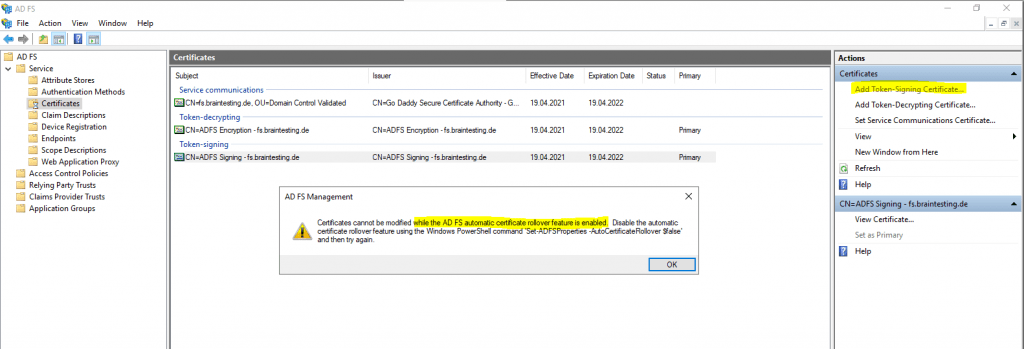
Determine whether AD FS renews the certificates automatically
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/operations/configure-ts-td-certs-ad-fs
Get-AdfsProperties | fl AutoCertificateRollover, CertificateGenerationThreshold
The AutoCertificateRollover property describes whether AD FS is configured to renew token signing and token decrypting certificates automatically.
So first I have to disable AutoCertificateRollover as follow.
Set-AdfsProperties -AutoCertificateRollover $false
Now I can change the Token-Signing Certificate
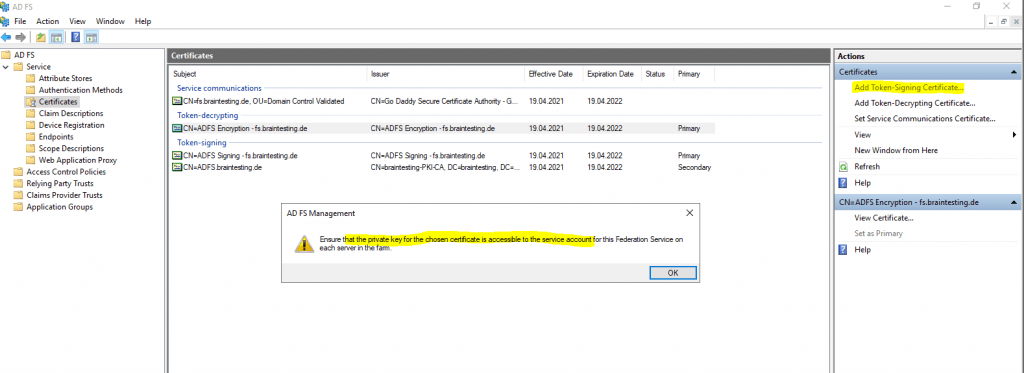
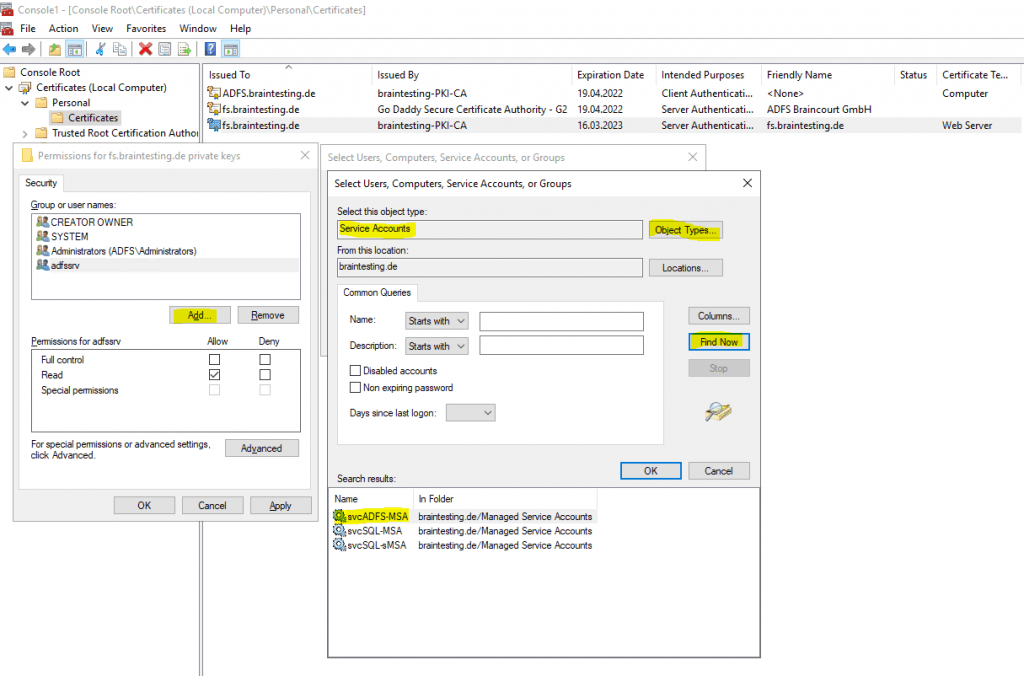
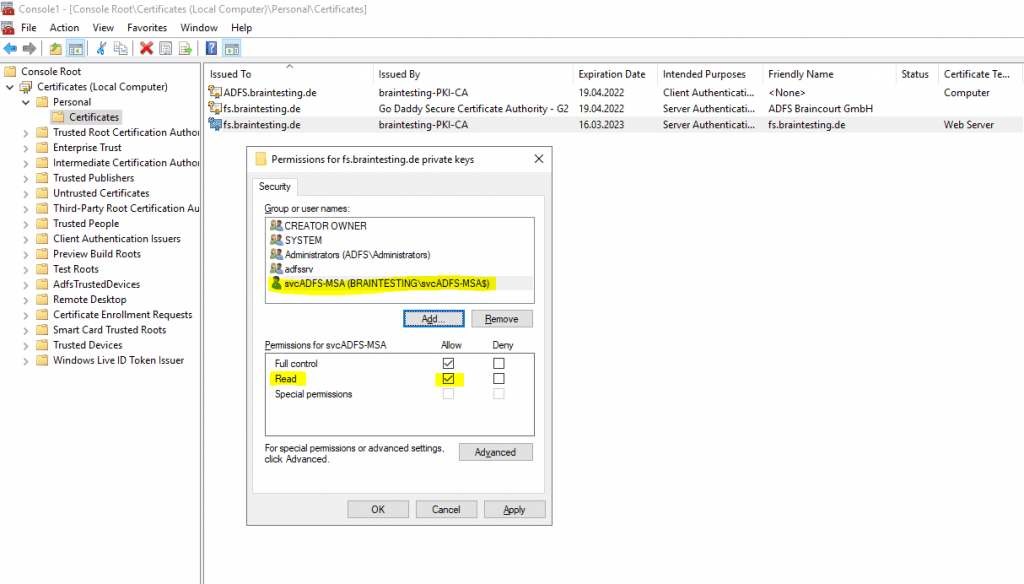
As shown in the message above, I also have to check if the ADFS service account at least have read permissions to the private key of the new Token-Signing Certificate.
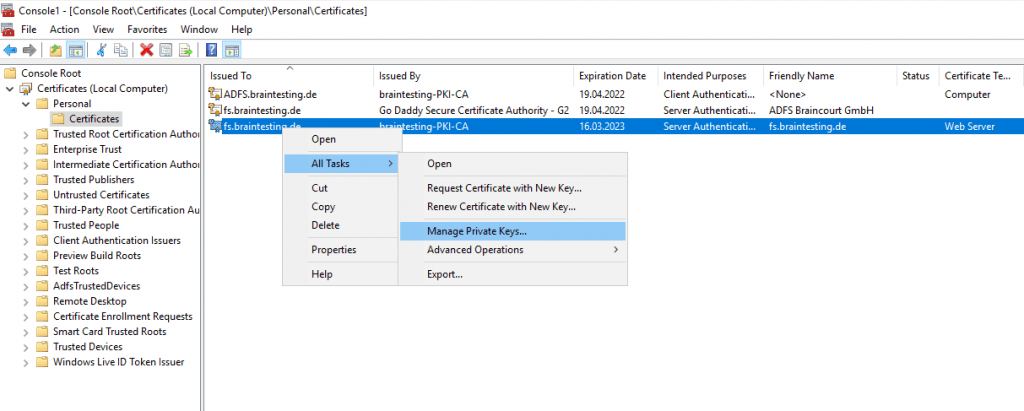
- With the local computer certificate store still open, select the certificate that was just imported.
- Right-click the certificate, click All Tasks, and then click Manage Private Keys.
- Add the account that is running the ADFS Service, and then give the account at least read permissions.
Note If you do not have the option to manage private keys, you may have to run the following command:
certutil -repairstore my *
So I need to ensure that the Group Managed Service Account braintestingsvcADFS-MSA at least have read permissions to the private key of the new Token-Signing Certificate.
First check what account is running the ADFS service.
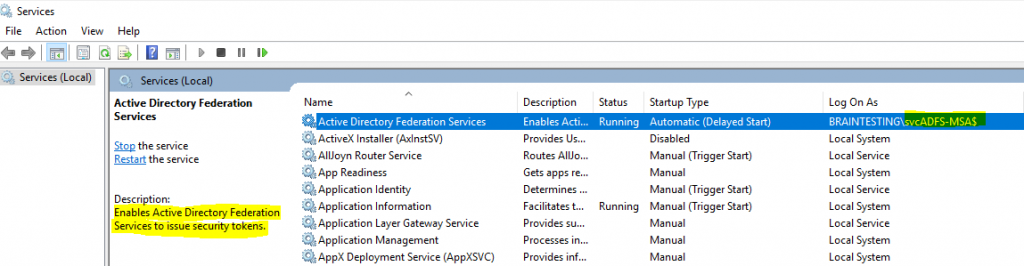
After that check if this account still have read permissions or add the permissions to it.
How to change the AD FS 2.0 service communications certificate after it expires
https://docs.microsoft.com/en-US/troubleshoot/windows-server/identity/change-ad-fs-2-dot-0-service-communications
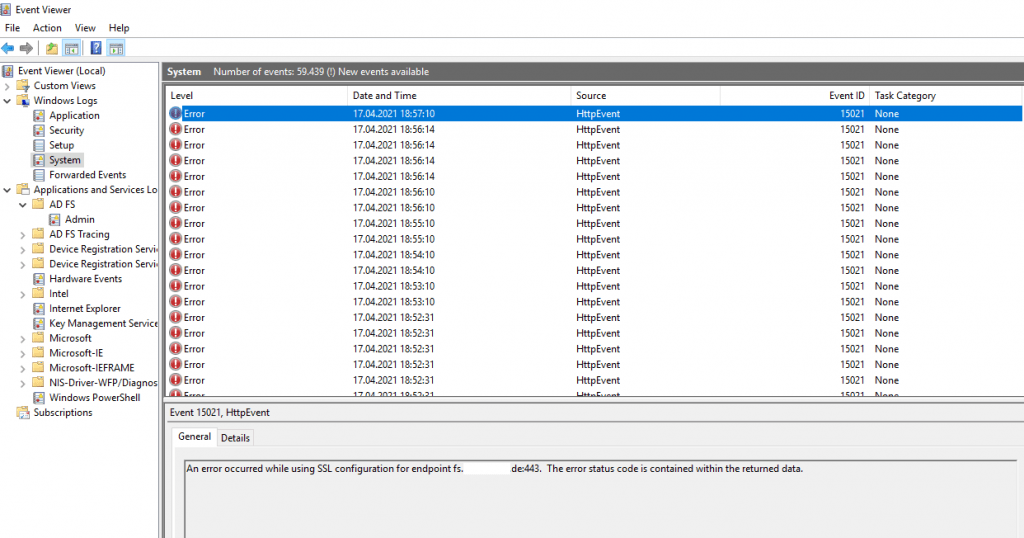
If you encounter the following errors after assigning the new Service Communications Certificate in the ADFS Console, you will also have to assign the new Certificate as SSL Certificate as follows.
An error occurred while using SSL configuration for endpoint fs.braintesting.de:443. The error status code is contained withing the returned data.
https://fs.braintesting.de/FederationMetadata/2007-06/FederationMetadata.xml
# internal ADFS Server
Set-AdfsCertificate -CertificateType Service-Communications -Thumbprint <Thumbprint of the certificate>
Set-AdfsSslCertificate -Thumbprint <Thumbprint>
# Reverse ADFS Proxy
Set-WebApplicationProxySslCertificate -Thumbprint <Thumbprint of the certificate>
ADFS Proxy
Assign Certificate on the Web Application Proxy
https://docs.microsoft.com/en-gb/windows-server/identity/ad-fs/overview/ad-fs-requirements#BKMK_1
SSL certificates on the Web Application Proxy must meet the following requirements
- If the proxy is used to proxy AD FS requests that use Windows Integrated Authentication, the proxy SSL certificate must be the same (use the same key) as the federation server SSL certificate
- If the AD FS property “ExtendedProtectionTokenCheck” is enabled (the default setting in AD FS), the proxy SSL certificate must be the same (use the same key) as the federation server SSL certificate
- Otherwise, the requirements for the proxy SSL certificate are the same as those for the federation server SSL certificate
Get-WebApplicationProxySslCertificate
https://docs.microsoft.com/en-us/powershell/module/webapplicationproxy/get-webapplicationproxysslcertificate
Set-WebApplicationProxySslCertificate
https://docs.microsoft.com/en-us/powershell/module/webapplicationproxy/set-webapplicationproxysslcertificate
# List certificates from the local storage
Dir Cert:LocalMachineMy
Set-WebApplicationProxySslCertificate -Thumbprint <Thumbprint of the certificate>
In case there is some misconfiguration with the certificates on the Web Application Proxy, you will see the following errors. In this case check if you have assigned on the Web Application Proxy the same certificate as the federation server SSL certificate and then run the Install-WebApplicationProxy PowerShell cmdlet to re-establish the trust with the internal ADFS server.
Reset the WAP trust using the Install-WebApplicationProxy PowerShell cmdlet
Install-WebApplicationProxy -FederationServiceName fs.braintesting.de -CertificateThumbprint <Thumbprint of the certificate>
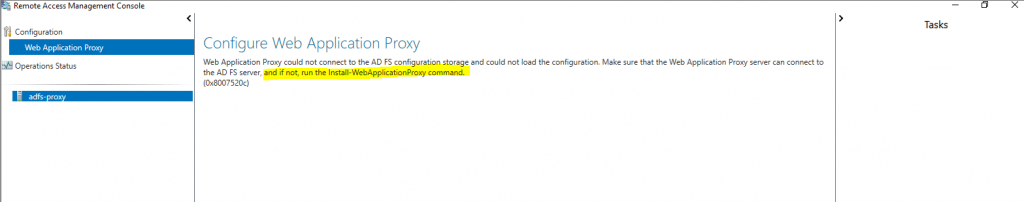
Web Application Proxy could not connect to AD FS configuration storage and could not load the configuration. Make sure that the Web Application Proxy server can connect to the AD FS server, and if not, run the Install-WebApplicationProxy command. (0x8007520c)
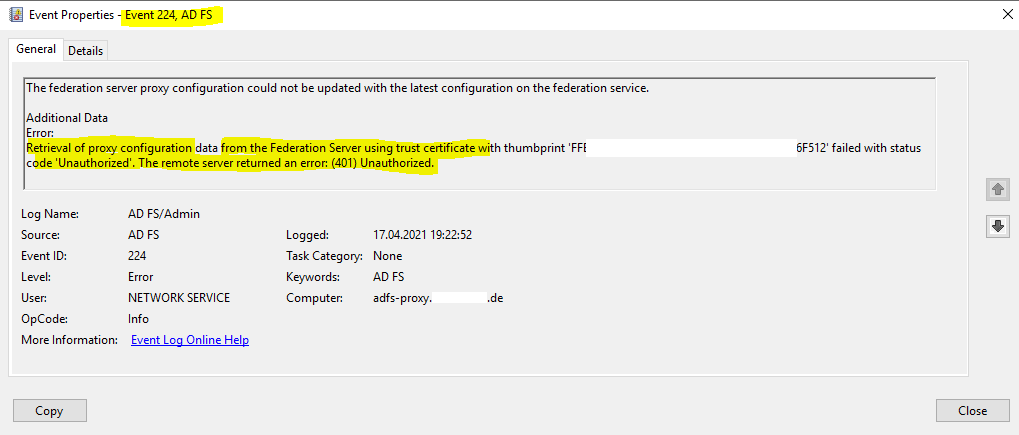
The federation server proxy configuration could not be updated with the latest configuration on the federation service.
Additional Data
Error:
Retrieval of proxy configuration data from the Federation Server using trust certificate with thumbprint ‘FFE67CCB127854A1936A5FD6F849AD1241F6F512’ failed with status code ‘Unauthorized’. The remote server returned an error: (401) Unauthorized.
AD FS self-signed Certificates
A great article about AD FS self-signed Token-Signing certificates, which is also true for the encryption/decryption certificates, you fill find here.
AD FS and self-signed Token-Signing certificates
https://blog.kloud.com.au/2013/07/17/ad-fs-and-self-signed-token-signing-certificates-3/
AD FS Certificate Chain Validation and Revocation Status Checking
If you will using the by default installed self-signed certificates for encrytion/decrytion and token-signing, there will be no certificate chain validation and revocation status checking in AD FS, as there or course for self-singed certificates in no chain and available revocation list (CRL).
In contrast for every certificate using from an CA, certificate chain validation is done!
Links
AD FS Requirements
https://docs.microsoft.com/en-gb/windows-server/identity/ad-fs/overview/ad-fs-requirements#BKMK_1
Obtain and Configure TS and TD Certificates for AD FS
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/operations/configure-ts-td-certs-ad-fs
AD FS Troubleshooting – Certificates
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/troubleshooting/ad-fs-tshoot-certs
Determine whether AD FS renews the certificates automatically
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/operations/configure-ts-td-certs-ad-fs
In Part 4 we will create two ASP.NET Web Applications (Web Forms & MVC) and configure them to be claim aware and authenticate users against an AD FS server.
Tags In
Follow me on LinkedIn


