Mastering the Firewall on SUSE Linux Enterprise Server
Whenever Linux is used in a network environment, you can use the kernel functions that allow the manipulation of network packets to maintain a separation between internal and external network areas.
The Linux netfilter framework provides the means to establish an effective firewall that keeps different networks apart. Using iptables—a generic table structure for the definition of rule sets—precisely controls the packets allowed to pass a network interface.
By default, netfilter (and tools like firewalld on top of it) restricts incoming traffic while allowing all outgoing traffic.
This means services on the host are protected unless explicitly opened, but applications running on the host can reach out freely. Outbound restrictions only apply if you add custom egress rules.
Such a packet filter can be set up using firewalld and its graphical interface firewall-config.
firewalld is finally just like Ufw under Ubuntu a frontend for iptables and nftables which makes it much easier to configure these rules.
As of SLES 15 SP3, the default backend for firewalld has changed from iptables to nftables.More about iptables and nftables you can read in my following post:
https://blog.matrixpost.net/set-up-ubuntus-built-in-firewall/SUSE Linux Enterprise Server 15 GA introduces firewalld as the new default software firewall, replacing SuSEfirewall2.
Source: https://documentation.suse.com/sles/15-SP4/html/SLES-all/cha-security-firewall.html
Firewall Zones
Zones represent a concept to manage incoming traffic more transparently. The zones are connected to networking interfaces or assigned a range of source addresses. You manage firewall rules for each zone independently, which enables you to define complex firewall settings and apply them to the traffic.
The firewalld packet filtering model allows any outgoing connections to pass. Outgoing connections are connections that are actively established by the local host. Incoming connections that are established by remote hosts are blocked if the respective service is not allowed in the zone in question. Therefore, each of the interfaces with incoming traffic must be placed in a suitable zone to allow for the desired services to be accessible. For each of the zones, define the services or protocols you need.
firewalld implements different security zones. Several predefined zones like internal and public exist. The administrator can define additional custom zones if desired. Each zone contains its own set of iptables rules. Each network interface is a member of exactly one zone. Individual connections can also be assigned to a zone based on the source addresses.
Source: https://documentation.suse.com/sles/15-SP4/html/SLES-all/cha-security-firewall.html
To list all available zones you can run the following command:
# firewall-cmd --get-zones
You can list all network interfaces currently assigned to a zone like this:
eth0 here is assigned to the public zone.
firewall-cmd is the command line client of the firewalld daemon. It provides an interface to manage the runtime and permanent configurations.
# firewall-cmd --get-active-zones
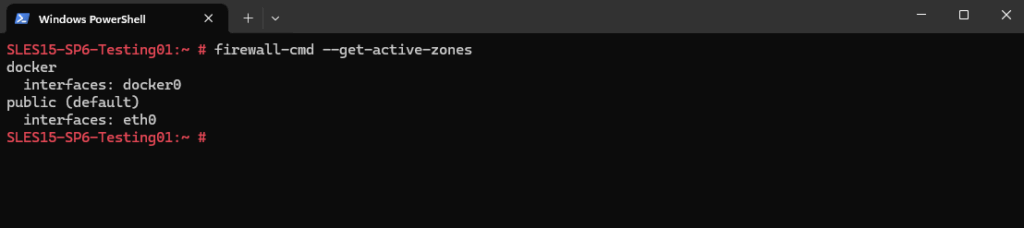
To determine which interfaces are assigned to a specific zone we can also run the following command.
List all network interfaces on the system > ip link show Determine which interfaces are assigned to the public zone > sudo firewall-cmd --zone=public --list-interface
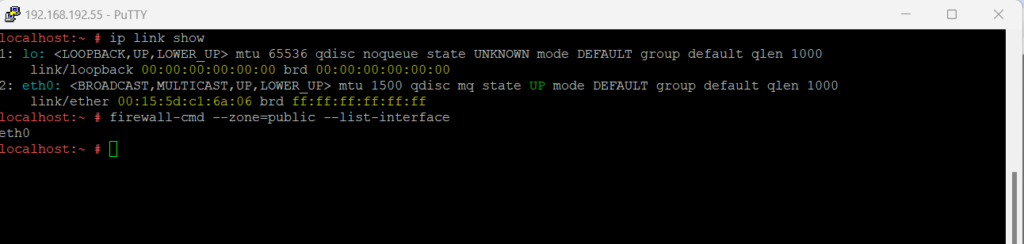
To assign an interface to a zone, you can use the following commands.
The variant using --add-interface will only work if eth0 is not already assigned to another zone. > sudo firewall-cmd --zone=internal --add-interface=eth0 The variant using --change-interface will always work, removing eth0 from its current zone if necessary: > sudo firewall-cmd --zone=internal --change-interface=eth0 Any operations without an explicit --zone argument will implicitly operate on the default zone. This pair of commands can be used for getting and setting the default zone assignment: > sudo firewall-cmd --get-default-zone dmz firewall-cmd --set-default-zone=public
Any network interfaces not explicitly assigned to a zone will be automatically part of the default zone. Changing the default zone will reassign all those network interfaces immediately for the permanent and runtime configurations. You should never use a trusted zone like internal as the default zone, to avoid unexpected exposure to threats. For example hotplugged network interfaces like USB Ethernet interfaces would automatically become part of the trusted zone in such cases.
Source: https://documentation.suse.com/sles/15-SP4/html/SLES-all/cha-security-firewall.html
We can determine the default zone by running.
# firewall-cmd --get-default-zone
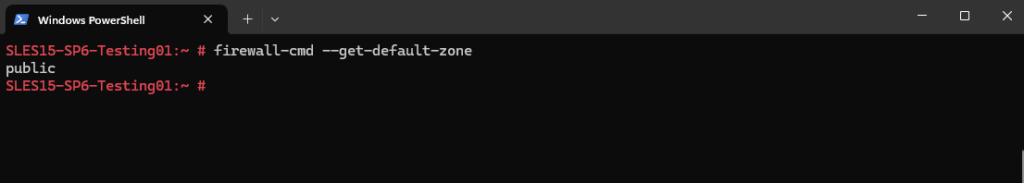
To remove an interface from a zone, you can use the following command.
# sudo firewall-cmd --zone=public --remove-interface=eth0
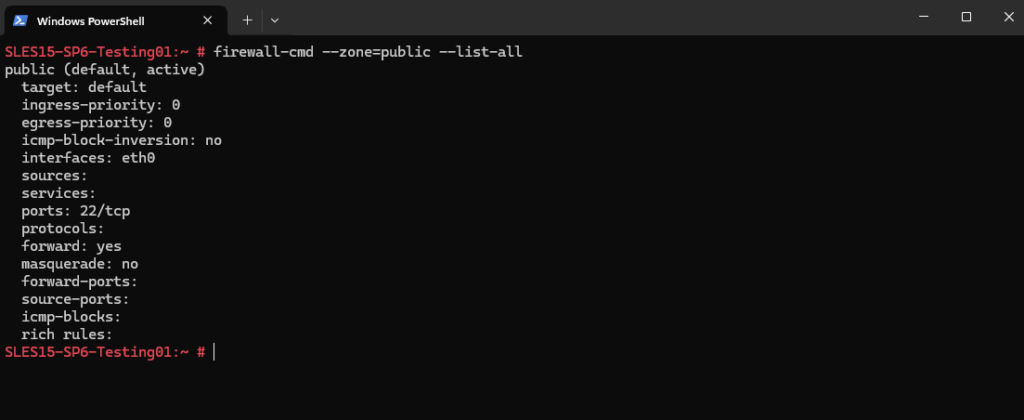
To get detailed info for the currently active zone on an interface we can run.
The output shows that the public zone is active on eth0 and explicitly allows only TCP port 22 (SSH). No predefined services or other ports are open, so all other incoming connections are blocked by default. Forwarding is enabled, but masquerading (enabling source NAT when forwarding) and custom rules are not configured.
target: default ==> means use the zone’s built-in behavior. For the public zone (and most others) this usually means “drop unsolicited traffic unless explicitly allowed”. So below just TCP 22 is allowed.
target: ACCEPT ==> means if no rule matches, just accept all traffic. This makes the zone effectively wide open, similar to the trusted zone.
# firewall-cmd --zone=public --list-all
Runtime Configuration vs. Permanent Configuration
By default all firewall-cmd commands operate on the runtime configuration. You can apply most operations to the permanent configuration only by adding the --permanent parameter.
When doing so the change will only affect the permanent configuration and will not be effective immediately in the runtime configuration.
There is currently no way to add a rule to both runtime and permanent configurations in a single invocation. To achieve this you can apply all necessary changes to the runtime configuration and when all is working as expected issue the following command:
> sudo firewall-cmd --runtime-to-permanent
This will write all current runtime rules into the permanent configuration. Any temporary modifications you or other programs may have made to the firewall in other contexts are made permanent this way. If you are unsure about this, you can also take the opposite approach to be on the safe side: Add new rules to the permanent configuration and reload firewalld to make them active.
> sudo firewall-cmd --reload or > sudo systemctl reload firewalld
Adding and manage Firewall Rules
To add new rules you can either use the service name or the port number. To see all the available pre-defined services (names) you can enter:
> sudo firewall-cmd --get-services
Allowing or Denying a Port/Protocol
> sudo firewall-cmd --zone=public --add-port=22/tcp --permanent > sudo firewall-cmd --zone=public --remove-port=22/tcp --permanent
Allowing or Denying a service (name)
> sudo firewall-cmd --zone=public --add-service=http --permanent > sudo firewall-cmd --zone=public --remove-service=http --permanent
Reload firewalld to make the new permanent rules kick in immediately.
> sudo firewall-cmd --reload
To get enabled configurations/rules:
> sudo firewall-cmd --list-all
To get all configurations for all zones:
> sudo firewall-cmd --list-all-zones
To get all configurations for a specific zone:
> sudo firewall-cmd --zone=public --list-all
Source: https://firewalld.org/documentation/man-pages/firewall-cmd.html
Enable or Disable the Firewall
On SUSE Linux Enterprise Server the firewall is enabled by default.
As mentioned SUSE Linux Enterprise Server 15 GA introduces firewalld as the new default software firewall and replacing the SuSEfirewall2.
To disable firewalld you first need to stop the firewalld daemon and then disable it by executing the following commands:
# systemctl stop firewalld.service # systemctl disable firewalld.service
To enable the firewalld enter the following commands:
# systemctl enable firewalld.service # systemctl start firewalld.service
Links
Firewalld
https://firewalld.org/Masquerading and firewalls
https://documentation.suse.com/sles/15-SP5/html/SLES-all/cha-security-firewall.htmlGetting Started with firewalld
https://docs.redhat.com/en/documentation/red_hat_enterprise_linux/7/html/security_guide/sec-using_firewalls


