Set up Checkmk on SUSE Linux Enterprise Server (SLES)
In this post we will see how to set up Checkmk on SLES 15 SP5 and how to secure the web interface (GUI) with HTTPS.
Checkmk is a robust and versatile IT monitoring platform that helps organizations keep track of their entire IT infrastructure in real time. Originally developed as an open-source project, Checkmk has evolved into a powerful enterprise-grade solution used by businesses worldwide to monitor servers, networks, applications, cloud environments, and more.
It offers a highly scalable and modular architecture, allowing users to monitor thousands of devices and services efficiently. With its extensive range of pre-built plugins, customizable dashboards, and automated alerting system, Checkmk empowers IT teams to quickly identify and resolve issues, optimize performance, and ensure the availability of critical services. Whether deployed in small environments or across complex, distributed networks, Checkmk provides the tools needed to maintain a stable and secure IT landscape.
Introduction and History
Checkmk is a software system developed in Python and C++.
Checkmk is available in four editions: an open source edition (Checkmk Raw Edition), a commercial enterprise-grade edition (Checkmk Enterprise Edition), a commercial edition with advanced cloud monitoring features (Checkmk Cloud Edition), and an edition for managed services providers (Checkmk Managed Services Edition).
These Checkmk Editions are available for a range of platforms, in particular for various versions of Debian, Ubuntu, SLES and Red Hat, and also as a Docker Image. In addition, physical appliances of various sizes as well as a virtual appliance are offered to simplify the administration of the underlying operating system through a graphical user interface and to enable high-availability solutions.
The agents used by Checkmk to collect data are available for 11 platforms, including Windows.
Checkmk originated in 2008 as an Agent-substituting shell script for Inetd, and was published in April 2009 under GPL. It was initially based on Nagios, and extended this with a number of new components.
The open source edition (Checkmk Raw Edition) also continues to be based on the Nagios-core, and bundles this with additional open source components into a complete system.
Over many years, Checkmk’s commercial editions have evolved into a self-contained monitoring system – one that has replaced all of the essential Nagios components with its own – including its very own monitoring core. The majority of the developments for the commercial editions, in particular all plug-ins, are also available into the Checkmk Raw Edition.
Checkmk is being developed by Checkmk GmbH in Munich, Germany. Until 16.04.2019 it operated under the name of Mathias Kettner GmbH, at which point the company was rebranded to tribe29 GmbH, while the product name “Check_MK” was also changed to “Checkmk”. A subsequent rebranding took place on 14.04.2023, when the company has been renamed to Checkmk GmbH.
Checkmk GmbH follows an open core business model. The open source edition is available under different open source licenses – mostly GPLv2, while large parts of the commercial editions run under the proprietary “Checkmk Enterprise License”.
Source: https://en.wikipedia.org/wiki/Checkmk
Download and Install checkmk
To download Checkmk we can browse to the following URL https://checkmk.com/download.
Here you first need to select on which platform you want to install. I want to install Checkmk on SUSE Linux Enterprise Server 15 SP5.
Then you also need to choose between the 5 different versions, I will install the Enterprise version.
Actually for my lab environment I wanted to install the free open source version Checkmk Raw. I also first installed this version but then was running into an error that all hosts I was setting up finally not shown up in the main dashboard.
Regarding a quick web search this is a known error and bug in versions before check-mk-raw-2.3.0p13. I was experience this issue still in the current version mentioned.
After using the enterprise version, the hosts shown up immediately in the main dashboard by default.
In case the free trial period of one of the commercial editions expires, you still be able to monitor up to 750 services (amount of monitored services on hosts) which is enough for my lab environment.
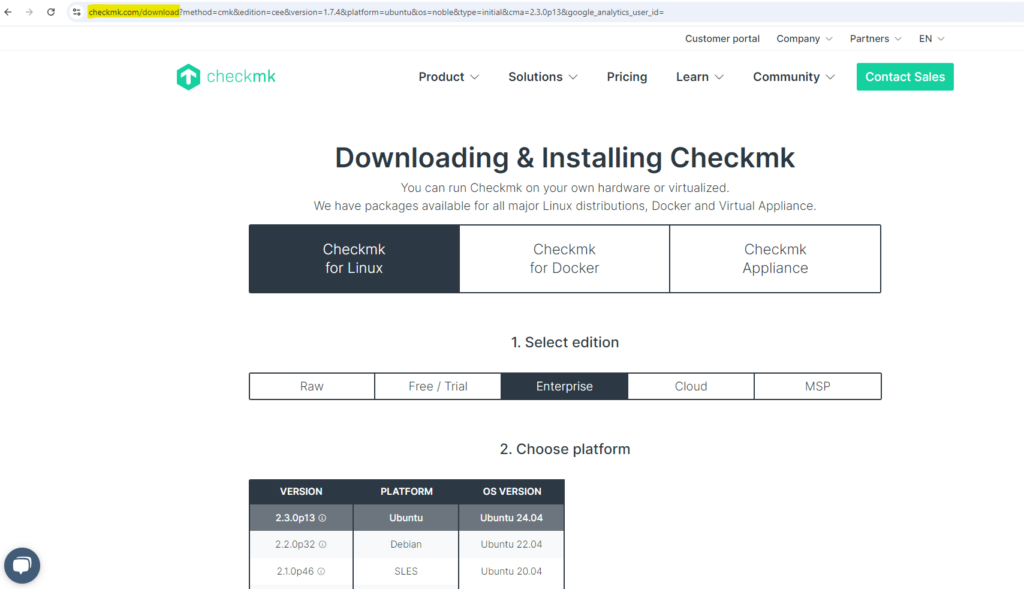
When selecting above the desired version and platform on which to install, you will get the final command to run with the wget command and full URI of the version to download.
In my case for the current enterprise version:
# wget https://download.checkmk.com/checkmk/2.3.0p12/check-mk-raw-2.3.0p12-sles15sp5-38.x86_64.rpm
Install the Checkmk package on SLES.
# zypper install ./check-mk-raw-2.3.0p12-sles15sp5-38.x86_64.rpm
Afterwards we can test if the installation was successful by running the omd version command:
$ omd version
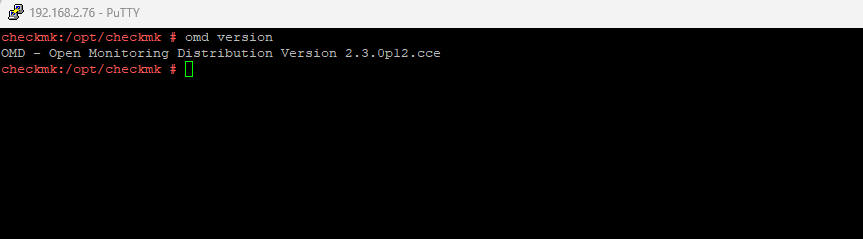
Source: https://checkmk.com/download
The next step is to create a Checkmk monitoring site.
You can create multiple sites on Checkmk, each site is a self-contained monitoring system which runs independently of the others. The site is responsible for monitoring a specific set of hosts, services, and devices within an IT infrastructure. Each site runs independently and has its own configuration, data, and user interface.
Create a checkmk Monitoring Site
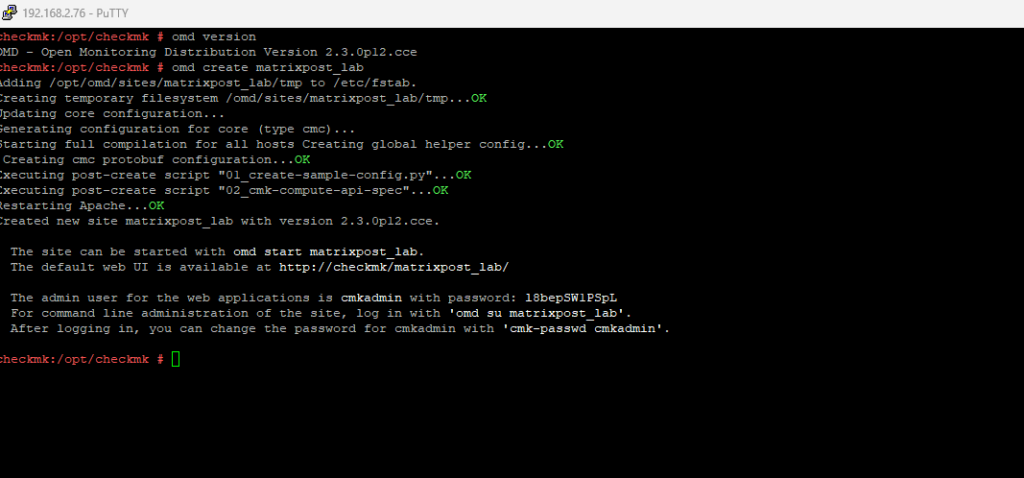
Use the omd command to create a new checkmk site. You can choose your own name, in my case I will use the name matrixpost_lab.
The site name must begin with a character, may contain characters, digits and _ and have length 1 up to 16
$ sudo omd create matrixpost_lab
Note the web UI URL, the admin user and password.
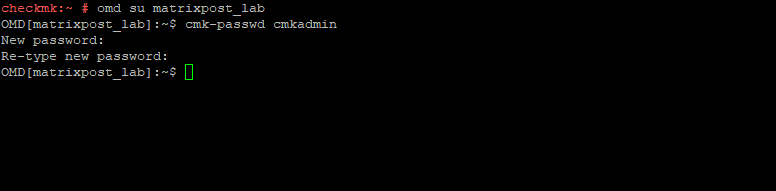
For command line administration of the site, log in with omd su matrixpost_lab.
After logging in, you can change the password for cmkadmin with cmk-passwd cmkadmin.
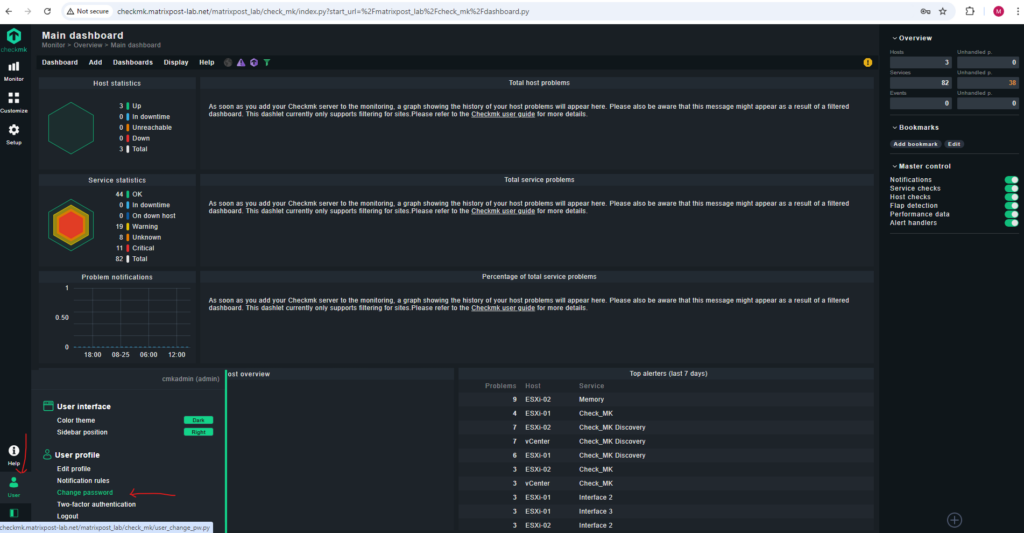
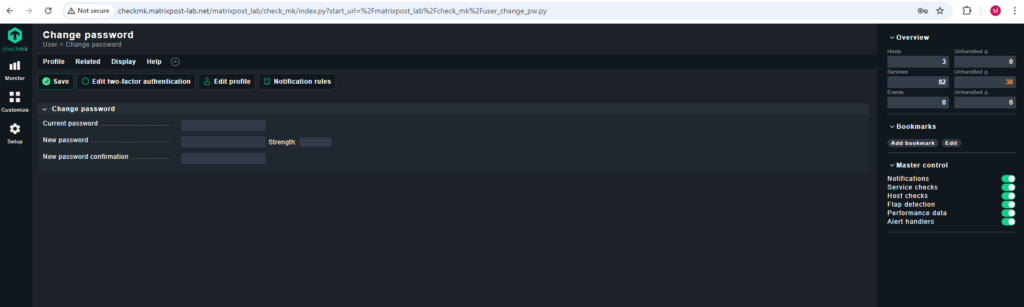
The password you can later also change in the GUI by either clicking on the left menu at the bottom on User and Change password for the current signed-in user or by browsing to Setup -> Users for all users.
Or as mentioned under Setup -> Users for all users.
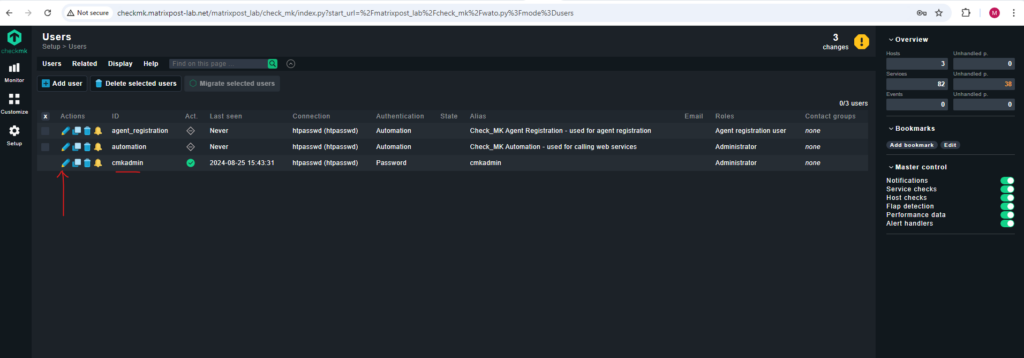
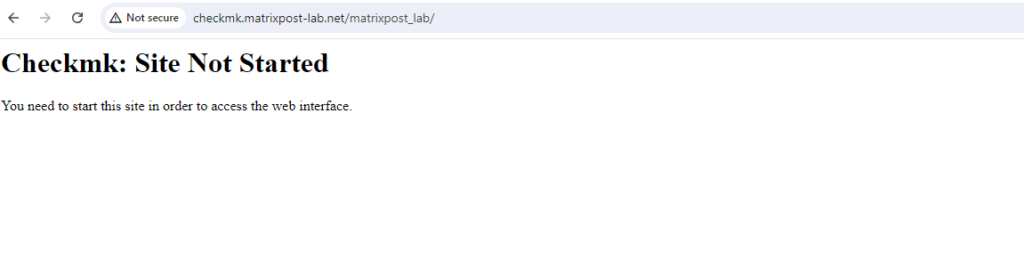
The site is now created, but it still first needs to be started.
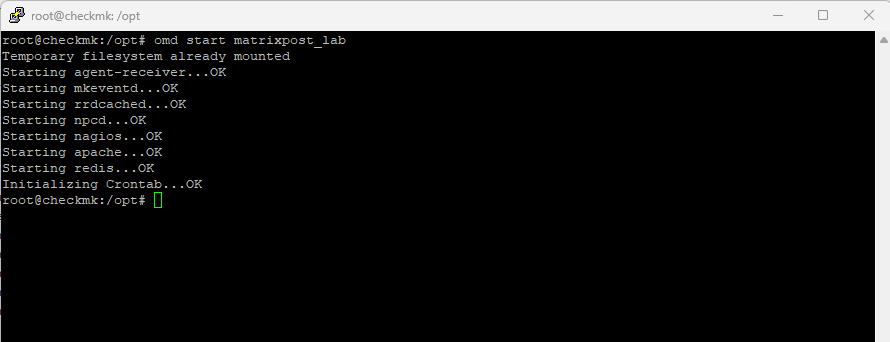
The site can be started with omd start <mysite name>.
$ omd start matrixpost_lab
Use the previously shown credentials to sign-in to checkmk.
Source: https://checkmk.com/download
Securing the web interface with HTTPS
In order to enable HTTPS we first need to make sure that the following Apache modules are installed in activated:
- mod_ssl
- mod_rewrite
- mod_headers
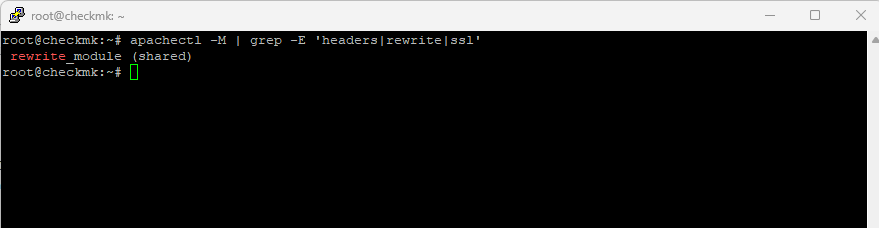
We can check this by entering the following command:
apachectl -M | grep -E 'headers|rewrite|ssl'
In my case so far just the mod_rewrite is installed and activated.
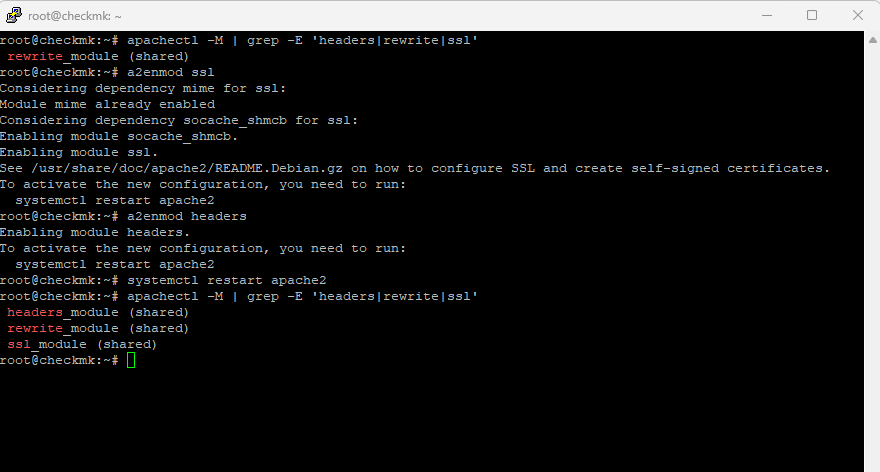
We can install and activate the missing modules as follows:
# a2enmod ssl # a2enmod headers # systemctl restart apache2
Whether the Apache web server can be restarted now or later depends on whether simple, self-signed certificates were automatically generated when Apache was installed.
You can find this out by first searching for the configuration file that contains the file paths to the certificate and keys, and then checking whether these files exist (for RHEL, specify /etc/httpd as the starting directory for the search):
find /etc/apache2/ -type f -exec grep -Hn '^\s*SSLCertificate.*File' {} \;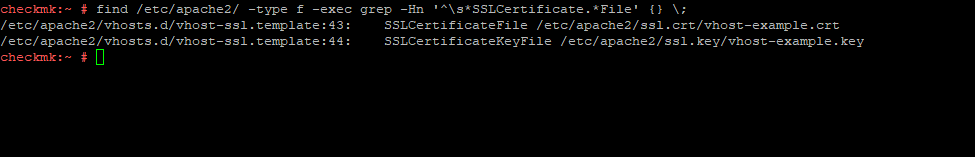
To secure Checkmk with HTTPS I will use a SSL certificate from my internal PKI, therefore I first need to create a private key for the new certificate on SLES.
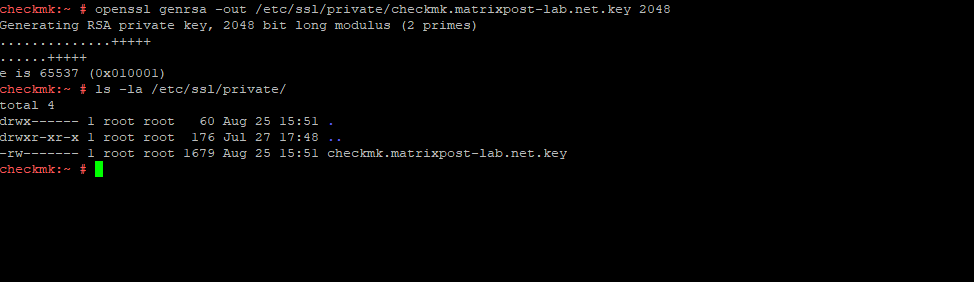
To generate a new private key we can use the following openssl command.
# openssl genrsa -out /etc/ssl/private/checkmk.matrixpost-lab.net.key 2048
In the next step, we create the Certificate Signing Request (CSR) — a digital request for the creation of an identity certificate (here: a public key certificate).
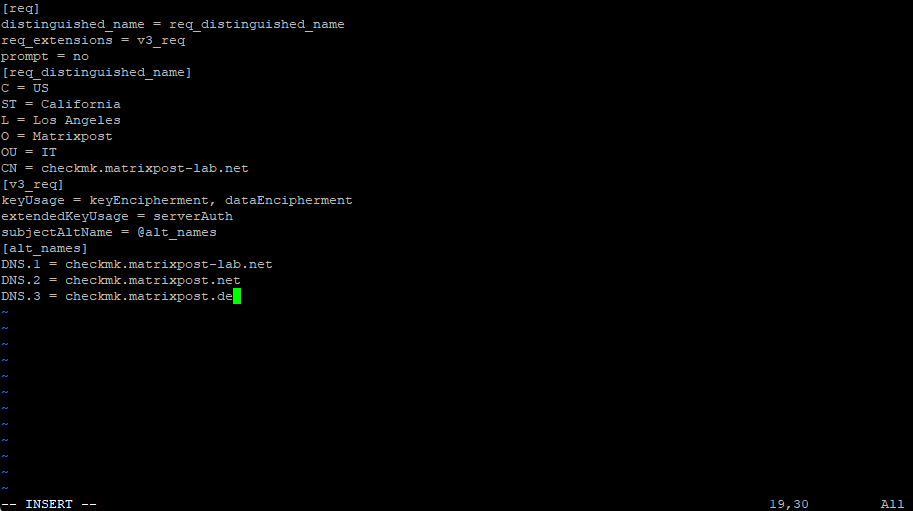
I will first create an extension file named req.conf to also include a subject alternative name which is these days mandatory for most browsers.
[req] distinguished_name = req_distinguished_name req_extensions = v3_req prompt = no [req_distinguished_name] C = US ST = California L = Los Angeles O = Matrixpost OU = IT CN = checkmk.matrixpost-lab.net [v3_req] keyUsage = keyEncipherment, dataEncipherment extendedKeyUsage = serverAuth subjectAltName = @alt_names [alt_names] DNS.1 = checkmk.matrixpost-lab.net DNS.2 = checkmk.matrixpost.net DNS.3 = checkmk.matrixpost.de
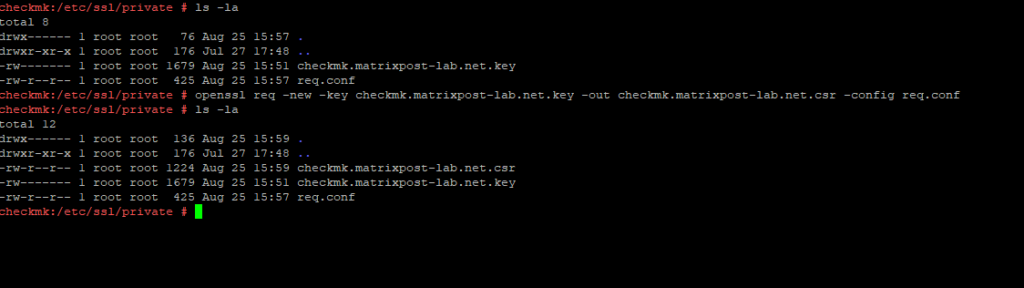
Now we can create the Certificate Signing Request (CSR) by using our extension file named req.conf.
# openssl req -new -key checkmk.matrixpost-lab.net.key -out checkmk.matrixpost-lab.net.csr -config req.conf
I will request for Checkmk a certificate from my internal Active Directory PKI (AD CS).
More about how to set up an internal PKI by using the Active Directory Certificate Services (AD CS) you will find in my following post.
To request a new certificate from my internal PKI, I will browse to CAs Web Enrollment site shown up under the PKIs FQDN and /certsrv folder.
Certification Authority Web Enrollment Role Service
https://learn.microsoft.com/en-us/windows-server/identity/ad-cs/certificate-authority-web-enrollment

We will submit an advanced request by using the previously created Certificate Signing Request (CSR).
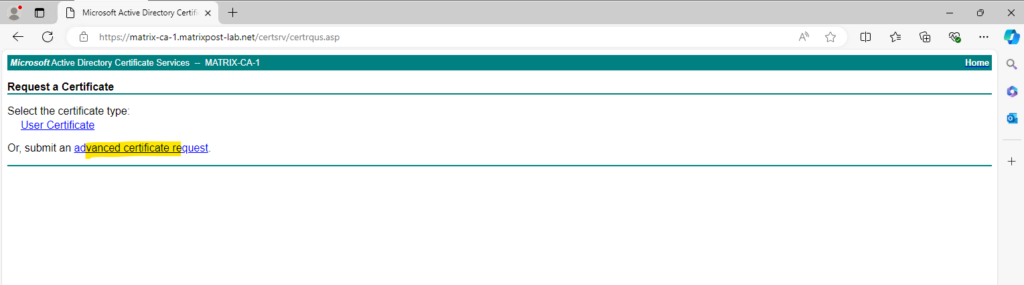
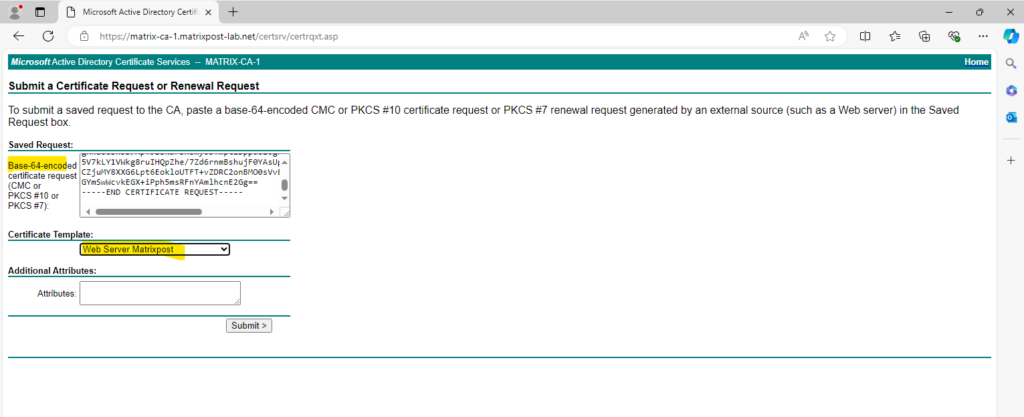
Here we need to enter the content of our CSR and select a certificate template for web server.
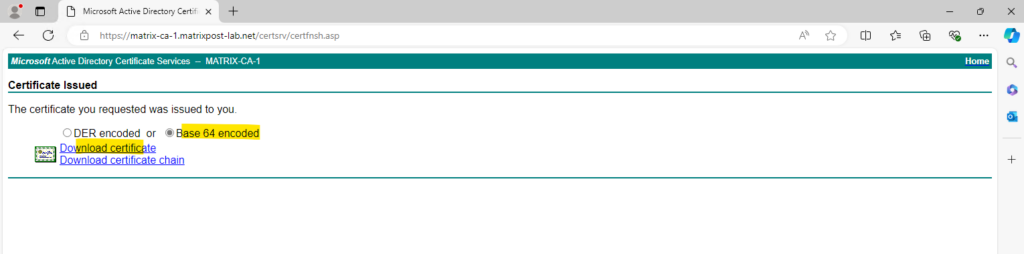
Finally we can download our new certificate for the Checkmk server. For Linux and the apache web server we use here Base 64 encoded.
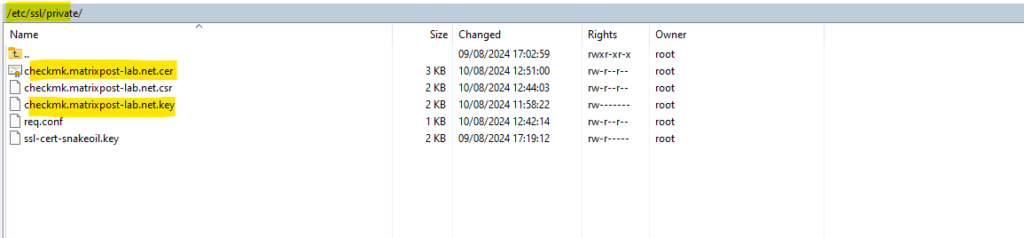
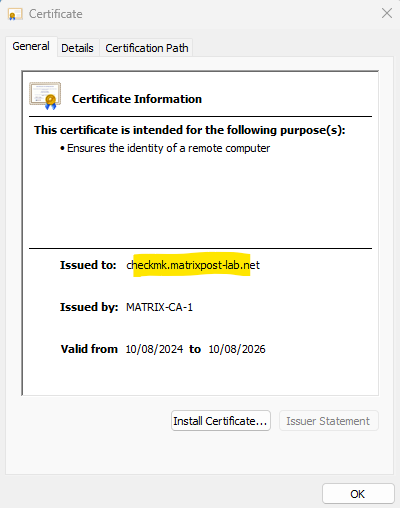
Because we previously used our extension file named req.conf for the CSR, which includes the subject alternative names, we now have these names listed in our certificate as shown below.
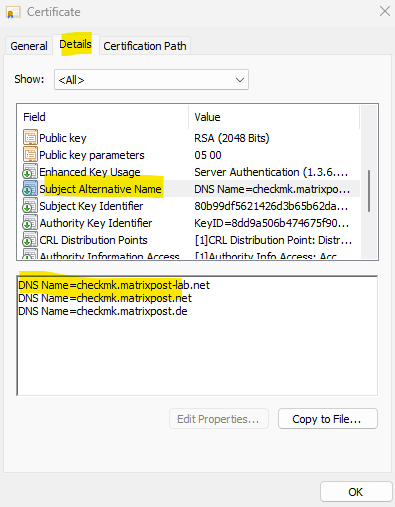
The certificate chain of the new certificate including my root and subordinate CA (Intermediate CA).
In order to include the complete certificate chain including the root and intermediate CA from my PKI, we now first need to export the new certificate as p7b file, this will include the whole certificate chain.
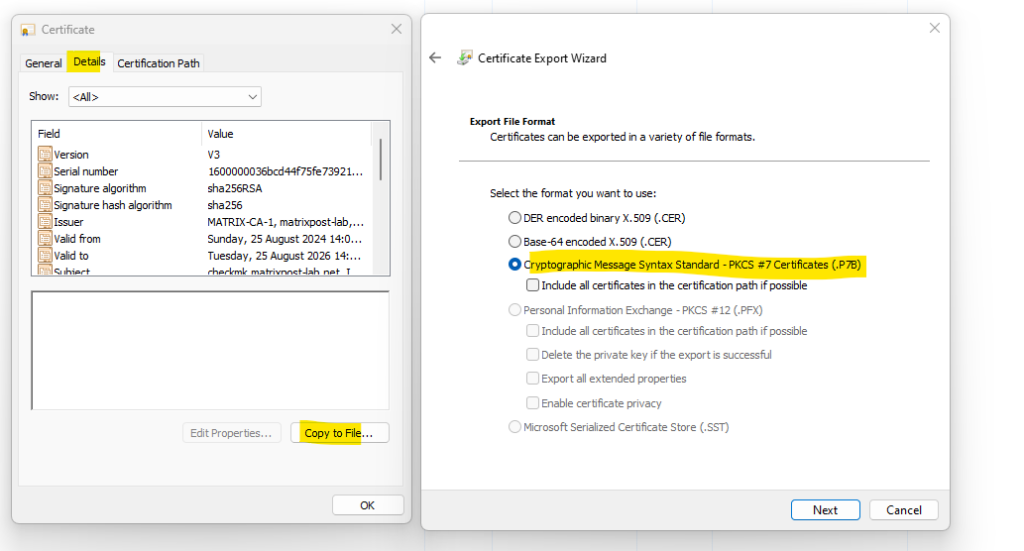
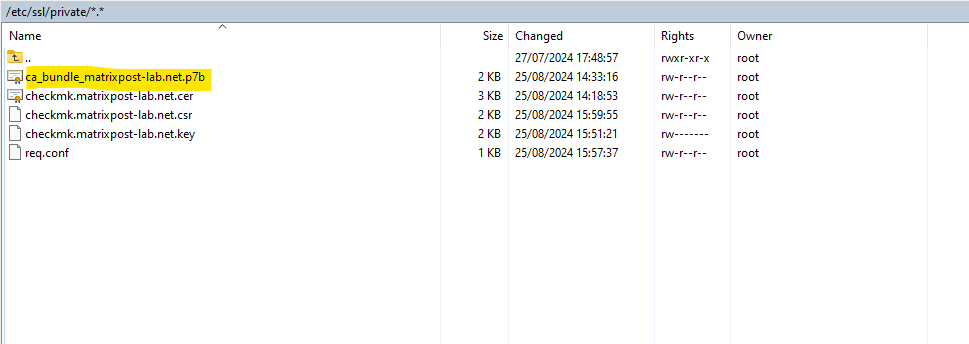
To use this bundle file including our certificate chain on apache, we need to convert it to the *.cer format as shown below.
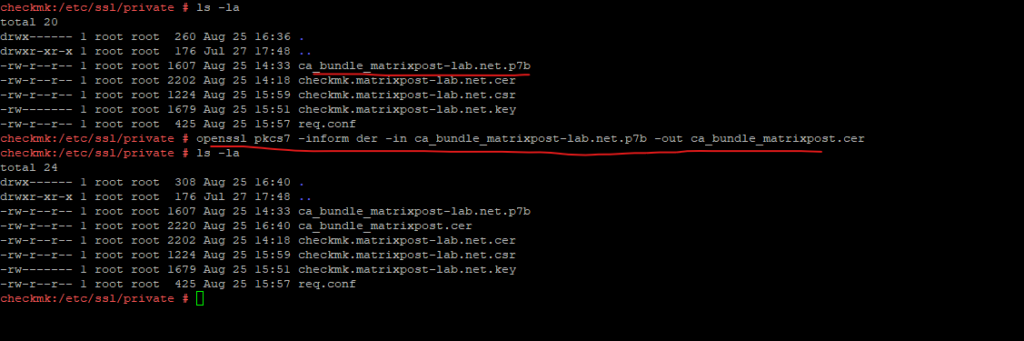
Convert p7b into cer.
# openssl pkcs7 -inform der -in ca_bundle_matrixpost-lab.net.p7b -out ca_bundle_matrixpost.cer
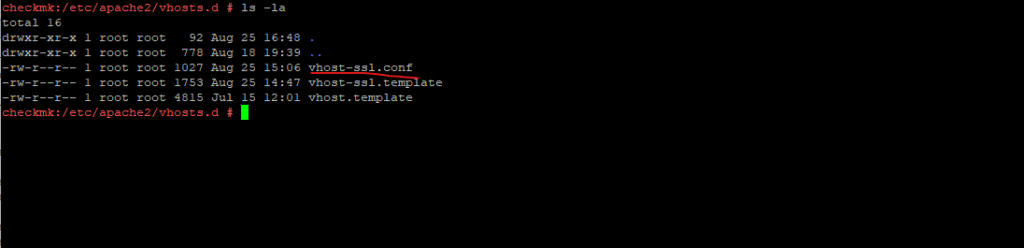
On SLES we can set up a virtual host in apache by copying and adjusting the template files in /etc/apache2/vhosts.d/, either for HTTP named vhost.template or for HTTPS named vhost-ssl.template.
The file for the new virtual host we then need to save as *.conf.
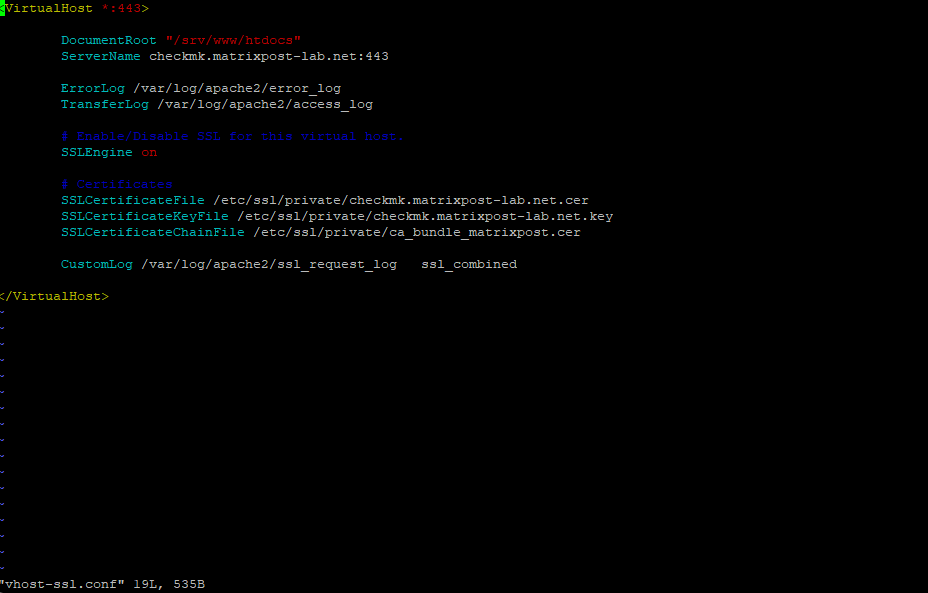
<VirtualHost *:443> DocumentRoot "/srv/www/htdocs" ServerName checkmk.matrixpost-lab.net:443 ErrorLog /var/log/apache2/error_log TransferLog /var/log/apache2/access_log # Enable/Disable SSL for this virtual host. SSLEngine on # Certificates SSLCertificateFile /etc/ssl/private/checkmk.matrixpost-lab.net.cer SSLCertificateKeyFile /etc/ssl/private/checkmk.matrixpost-lab.net.key SSLCertificateChainFile /etc/ssl/private/ca_bundle_matrixpost.cer CustomLog /var/log/apache2/ssl_request_log ssl_combined </VirtualHost>
On SLES the SSL module is enabled by default in the global server configuration. In case it has been disabled on your host, you can activate it by using the a2enmod ssl command as usual.
To finally enable SSL for apache on SLES, the server needs to be started with the flag “SSL”. To do so, call a2enflag SSL (case-sensitive!) and restart apache by using the systemctl restart apache2 command.

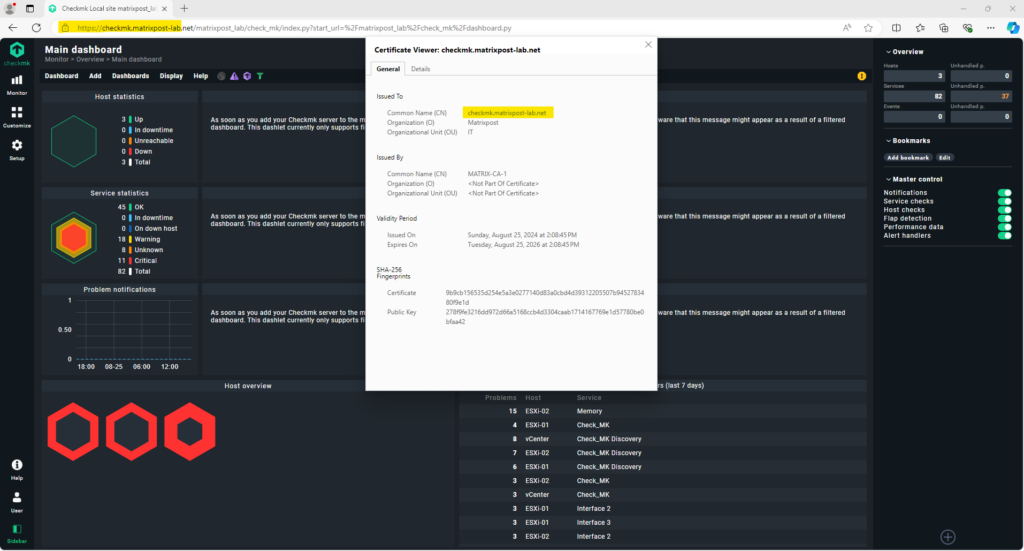
Source: https://docs.checkmk.com/latest/en/omd_https.html
In my following post we will see how to monitor VMware vSphere environments and Windows clients in Checkmk.
Display Checkmk Version
To display the installed version of Checkmk we can run the following command on the shell.
# omd version
When you display the version of a Checkmk site with the omd version command, you will see a further suffix, which the OMD views as a part of the version number. So below we can see that I will run the Checkmk Cloud version.
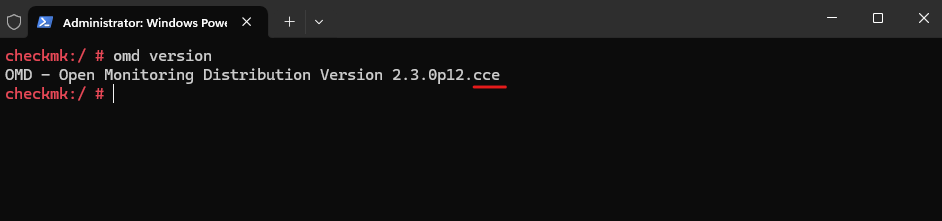
This suffix enables the same versions of various Checkmk editions to be distinguished.
- .cre
 Checkmk Raw
Checkmk Raw
.cee Checkmk Enterprise
Checkmk Enterprise
.cce Checkmk Cloud
Checkmk Cloud
.cme Checkmk MSP
Checkmk MSP
Source: https://docs.checkmk.com/latest/en/cmk_versions.html
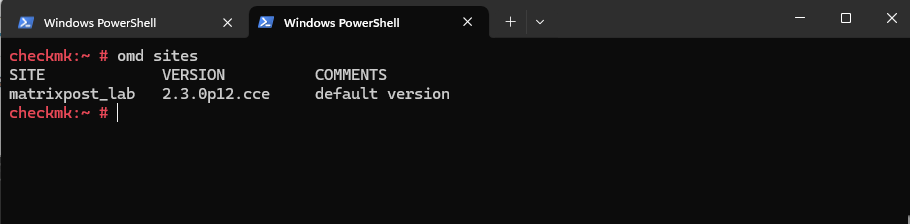
List all available Sites on the Checkmk Server
If you want to list all sites running on a specific server, use:
checkmk:~ # omd sites
Links
Downloading & Installing Checkmk
https://checkmk.com/downloadWelcome to the Checkmk User Guide
https://docs.checkmk.com/latest/en/welcome.htmlSite administration with omd
https://docs.checkmk.com/latest/en/omd_basics.htmlSecuring the web interface with HTTPS
https://docs.checkmk.com/latest/en/omd_https.htmlThe Apache HTTP server
https://documentation.suse.com/sles/15-SP5/html/SLES-all/cha-apache2.htmlWhy you should replace Nagios with a modern monitoring tool | Checkmk
https://checkmk.com/guides/nagios-alternativeCheckmk
https://de.wikipedia.org/wiki/CheckmkWhat is the Open Monitoring Distribution?
https://checkmk.com/guides/open-monitoring-distribution
Follow me on LinkedIn


