Set up Microsoft Defender for Cloud
In this post I want to give you a brief summary about:
- what Microsoft Defender for Cloud is exactly?
- what it will actually protect?
- and and how you can enable the available plans for your subscriptions resp. resources running within these subscription?
This is well documented by Microsoft and I will refer to their articles in this post.
For some of the workloads (eg. APIs, Servers, Containers, Storage Accounts, …) which are protected by Microsoft Defender for Cloud, I will also demonstrate in detail how to protect them in dedicated posts coming soon and linked here.
Introduction
Microsoft Defender for Cloud is a cloud-native application protection platform (CNAPP) with a set of security measures and practices designed to protect your cloud-based applications end-to-end by combining the following capabilities:
- A development security operations (DevSecOps) solution that unifies security management at the code level across multicloud and multiple-pipeline environments
- A cloud security posture management (CSPM) solution that surfaces actions that you can take to prevent breaches
- A cloud workload protection platform (CWPP) with specific protections for servers, containers, storage, databases, and other workloads
Defender for Cloud includes Foundational CSPM capabilities and access to Microsoft 365 Defender for free. You can add additional paid plans to secure all aspects of your cloud resources. To learn more about these plans and their costs, see the Defender for Cloud pricing page.
Defender for Cloud helps you find and fix security vulnerabilities. Defender for Cloud also applies access and application controls to block malicious activity, detect threats using analytics and intelligence, and respond quickly when under attack.
To view information related to a resource in Defender for Cloud, you must be assigned the Owner, Contributor, or Reader role for the subscription or for the resource group that the resource is located in.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-cloud-introduction
Enable Defender for Cloud on your Subscriptions
You can use several ways to enable Defender for Cloud on your subscriptions.
Either you can use the Azure Portal or you can use PowerShell therefore by assigning an Azure Policy to your subscriptions.
Further you can enable Defender for Cloud in one step to all of your subscriptions or as shown below just to one subscription.
On the subscription blade select Policies within the Settings section. Then select Definitions and search for Enable Microsoft Defender for Cloud on your subscription and click on it.
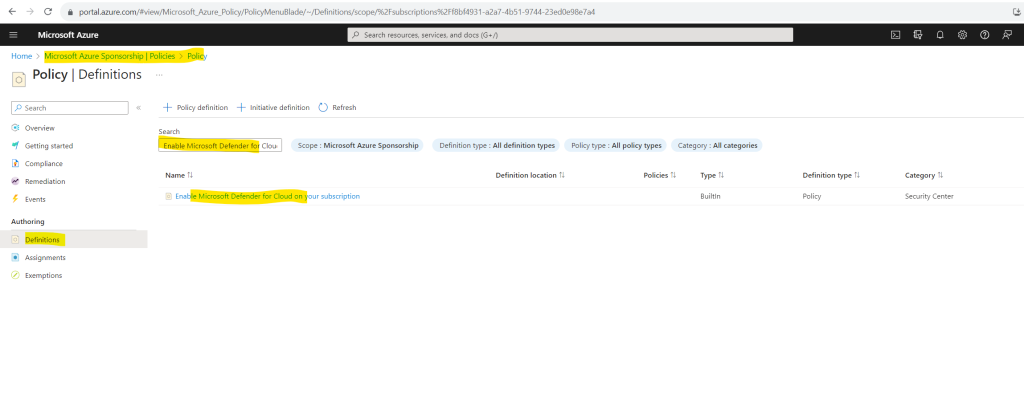
Select Assign.
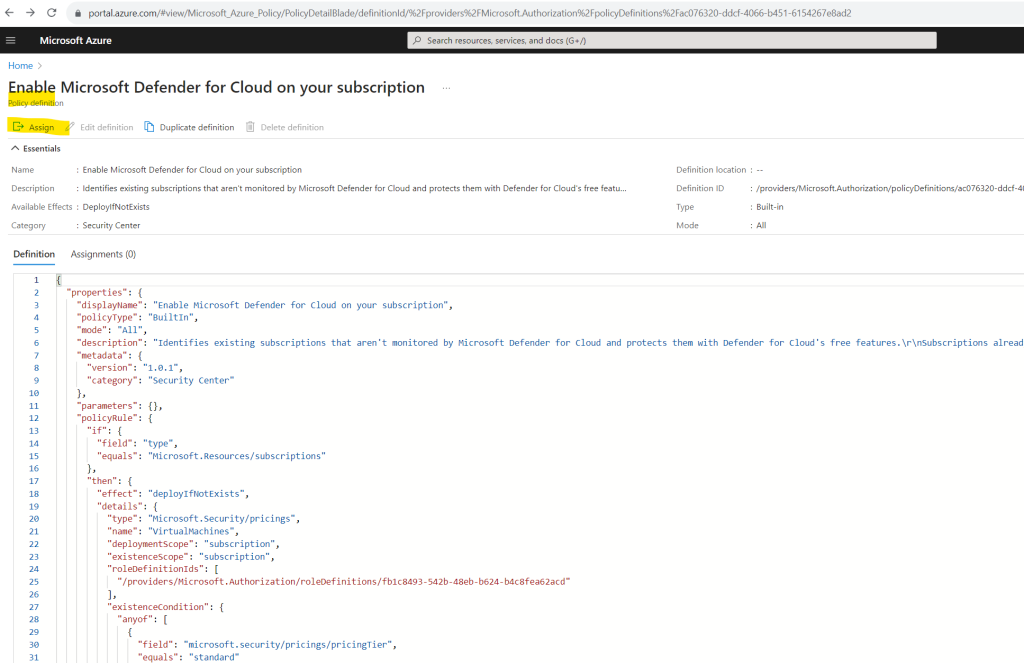
The assigning process first needs the scope we want to assign Microsoft Defender for Cloud to. We can assign Microsoft Defender for Cloud as mentioned in one step to all subscriptions or we can just select one subscription.
To enable Defender for Cloud on all subscriptions we can select below the root management group which manages all subscriptions in my tenant or we can just select here a dedicated separate subscription.
In order to demonstrate Defender for Cloud I will just select one subscription here.
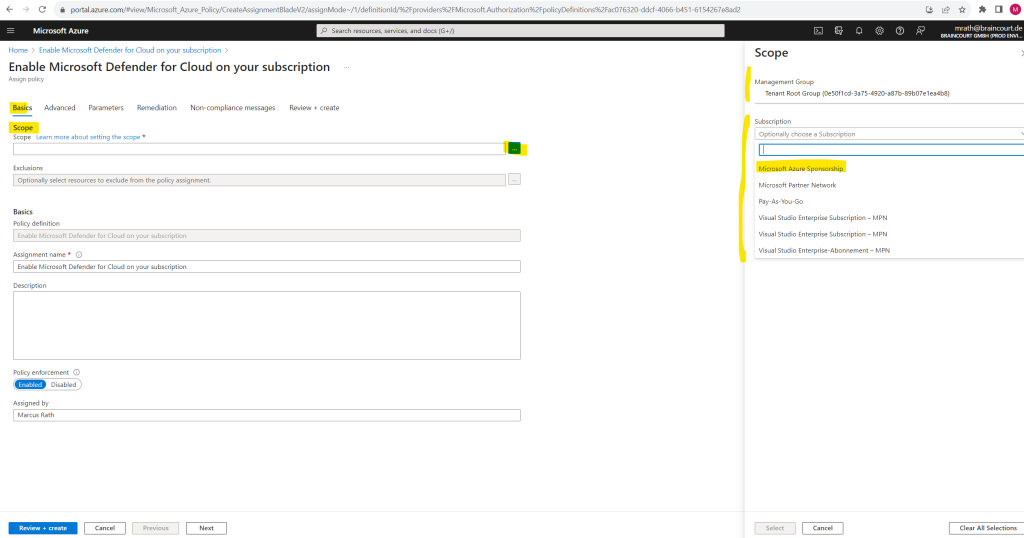
When selecting just a dedicated subscription we can further limit the scope optionally to just one resource group within this subscription.
I will not limit the scope to a resource group and leave it blank.
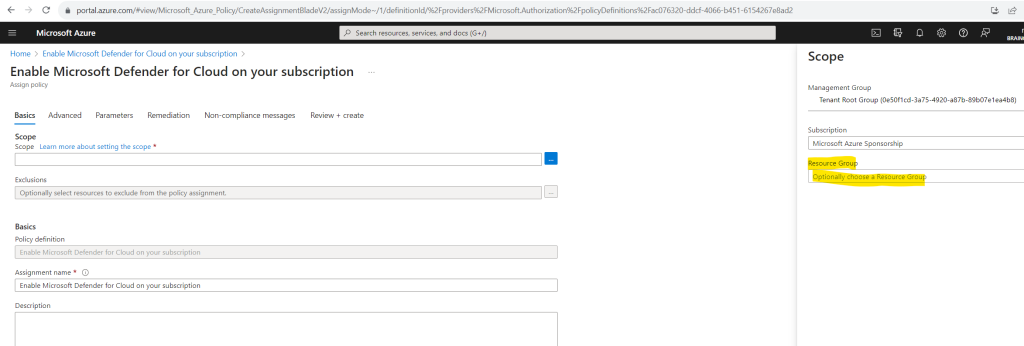
In the next tab Advanced you can additionally limit the assignment by using resource selectors. I will skip this step because I want to enable Defender for Cloud for all resources within my subscription. Because this policy has no parameters we can also skip the Parameters tab.
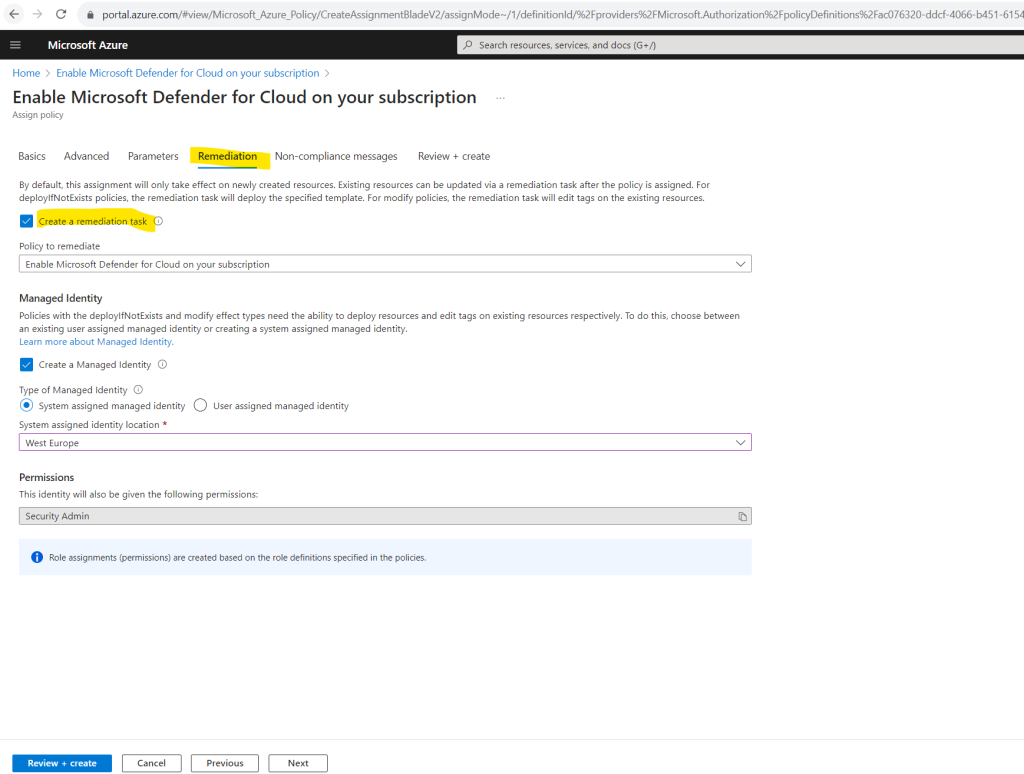
Within the Remediation tab we need to create a remediation task, therefore we need to check this as shown below.
By default, this assignment will only take effect on newly created resources. Existing resources can be updated via a remediation task after the policy is assigned. For deployIfNotExists policies, the remediation task will deploy the specified template. For modify policies, the remediation task will edit tags on the existing resources.
By default under Managed Identity is a system assigned managed identity selected which I will also user here.
Policies with the deployIfNotExists and modify effect types need the ability to deploy resources and edit tags on existing resources respectively. To do this, choose between an existing user assigned managed identity or creating a system assigned managed identity.
Finally I will click on Review + create.
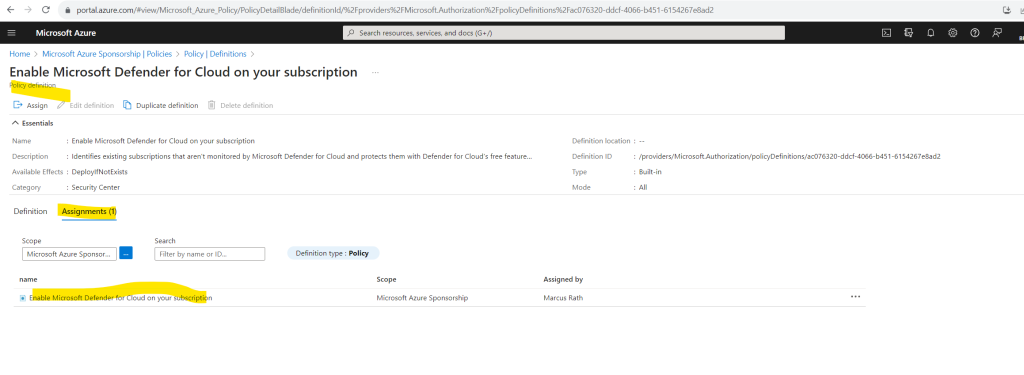
Finally the policy is assigned to my subscription.
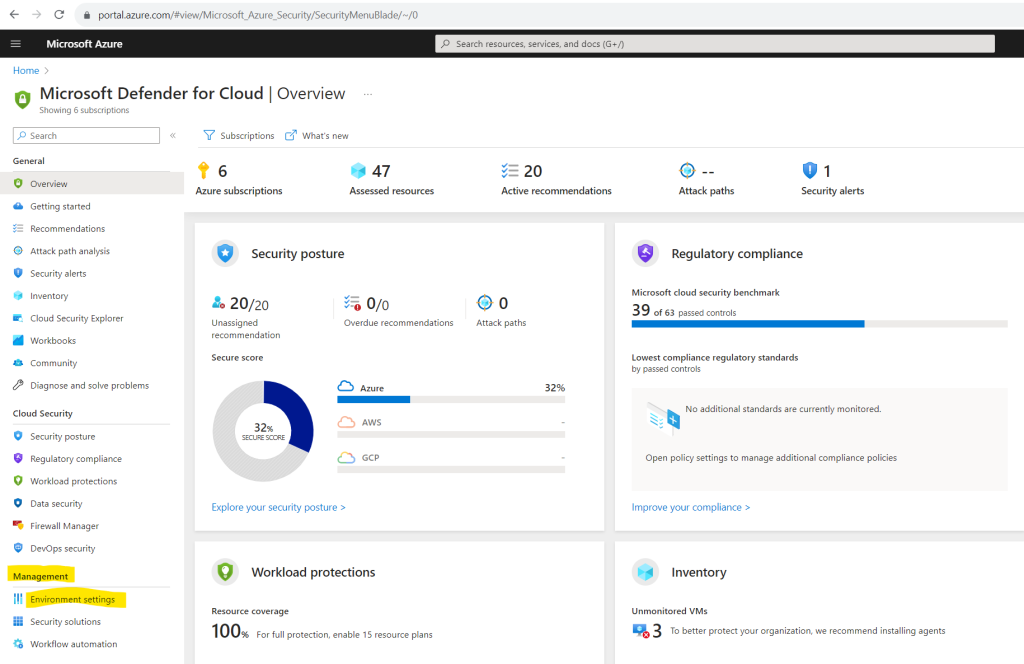
Defender for Cloud is now enabled on your subscription and you have access to the basic features provided by Defender for Cloud. These features include:
- The Foundational Cloud Security Posture Management (CSPM) plan.
- Recommendations.
- Access to the Asset inventory.
- Workbooks.
- Secure score.
- Regulatory compliance with the Microsoft cloud security benchmark.
The Defender for Cloud overview page provides a unified view into the security posture of your hybrid cloud workloads, helping you discover and assess the security of your workloads and to identify and mitigate risks. Learn more in Microsoft Defender for Cloud’s overview page.
You can view and filter your list of subscriptions from the subscriptions menu to have Defender for Cloud adjust the overview page display to reflect the security posture to the selected subscriptions.
Within minutes of launching Defender for Cloud for the first time, you might see:
- Recommendations for ways to improve the security of your connected resources.
- An inventory of your resources that Defender for Cloud assesses along with the security posture of each.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/connect-azure-subscription
Enable all paid plans on your subscription
When you enable Defender plans on an entire Azure subscription, the protections are applied to all other resources in the subscription.
To enable additional paid plans on a subscription:
Sign in to the Azure portal
Search for and select Microsoft Defender for Cloud.
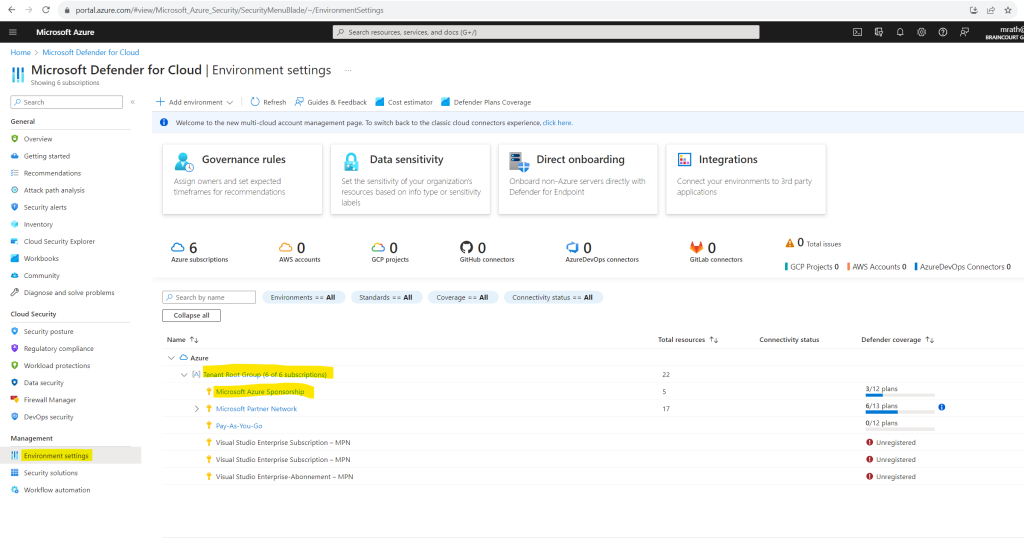
In the Defender for Cloud menu, select Environment settings.
Select the subscription or workspace that you want to protect. I will select here my Microsoft Azure Sponsorship subscription.
Select Enable all to enable all of the plans for Defender for Cloud and click on Save.
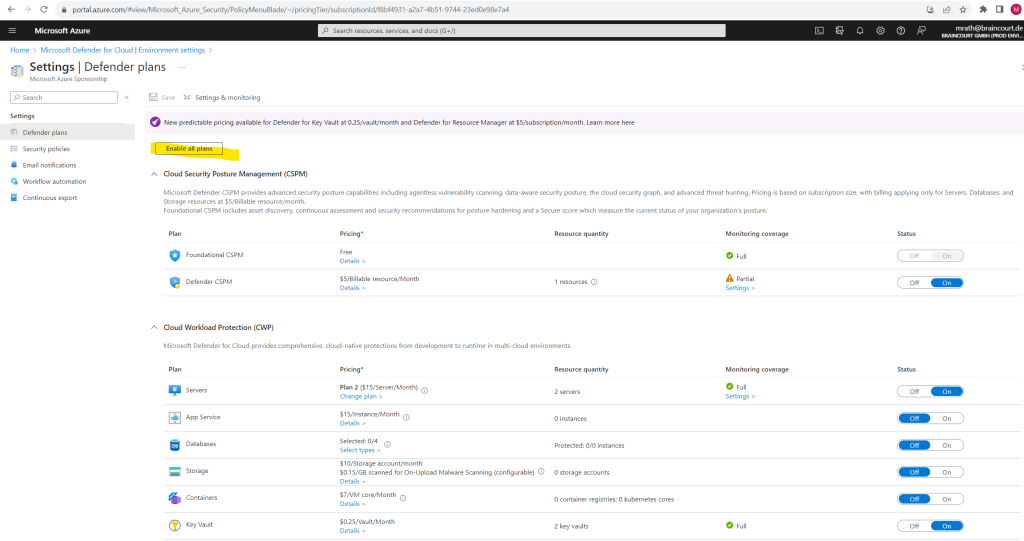
All of the plans are turned on and the monitoring components required by each plan are deployed to the protected resources.
If you want to disable any of the plans, toggle the individual plan to off. The extensions used by the plan aren’t uninstalled but, after a short time, the extensions stop collecting data.
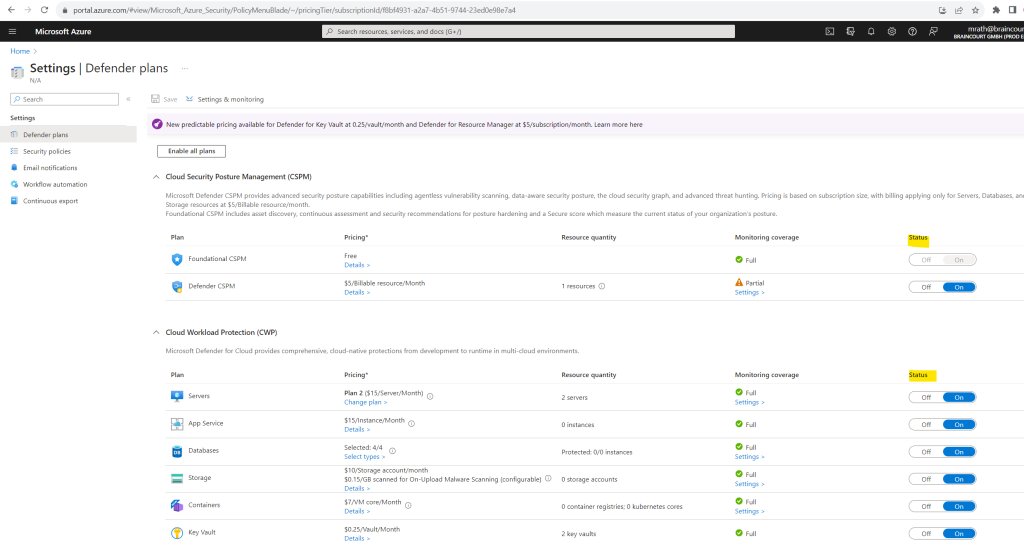
When you enable Defender for Cloud, Defender for Cloud’s alerts are automatically integrated into the Microsoft 365 Defender portal. No further steps are needed.
The integration between Microsoft Defender for Cloud and Microsoft 365 Defender brings your cloud environments into Microsoft 365 Defender. With Defender for Cloud’s alerts and cloud correlations integrated into Microsoft 365 Defender, SOC teams can now access all security information from a single interface.
Microsoft Defender for Cloud portal
The Microsoft Defender for Cloud portal is just a blade within the Azure portal. Therefore you can open Microsoft Defender for Cloud either by using the following link directly https://portal.azure.com/#blade/Microsoft_Azure_Security/SecurityMenuBlade/0 or by searching within the Azure portal for Microsoft Defender for Cloud as shown below.
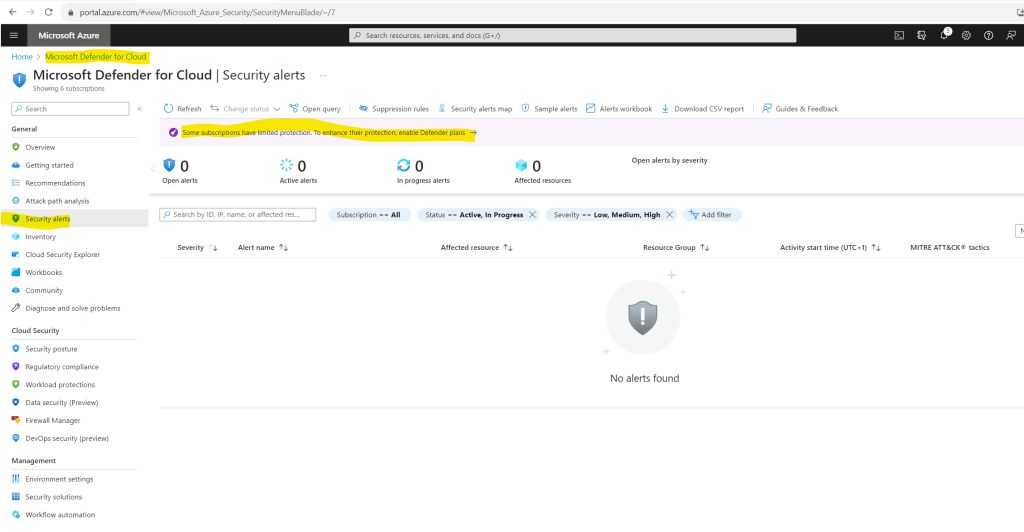
The Security alerts in the Microsoft Defender for Cloud portal gives you a great summary page of all alerts so that you doesn’t necessarily need to leverage the Microsoft Sentinel portal for that reason.
Further as already mentioned when you enable Defender for Cloud, Defender for Cloud’s alerts are automatically integrated into the Microsoft 365 Defender portal. No further steps are needed.
The integration between Microsoft Defender for Cloud and Microsoft 365 Defender brings your cloud environments into Microsoft 365 Defender. With Defender for Cloud’s alerts and cloud correlations integrated into Microsoft 365 Defender, SOC teams can now access all security information from a single interface.
Workloads protected by Microsoft Defender for Cloud
Defender for Cloud collects data from your Azure virtual machines (VMs), Virtual Machine Scale Sets, IaaS containers, and non-Azure (including on-premises) machines to monitor for security vulnerabilities and threats. Some Defender plans require monitoring components to collect data from your workloads.
Data collection is required to provide visibility into missing updates, misconfigured OS security settings, endpoint protection status, and health and threat protection. Data collection is only needed for compute resources such as VMs, Virtual Machine Scale Sets, IaaS containers, and non-Azure computers.
You can benefit from Microsoft Defender for Cloud even if you don’t provision agents. However, you’ll have limited security and the capabilities listed above aren’t supported.
Data is collected using:
- Azure Monitor Agent (AMA)
- Microsoft Defender for Endpoint (MDE)
- Log Analytics agent
- Security components, such as the Azure Policy for Kubernetes
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/monitoring-components
As mentioned Microsoft Defender for Cloud is among other capabilities a cloud workload protection platform (CWPP) which will protect the following workloads shown below.
Defender for APIs
Microsoft Defender for APIs is a plan provided by Microsoft Defender for Cloud that offers full lifecycle protection, detection, and response coverage for APIs.
Defender for APIs helps you to gain visibility into business-critical APIs. You can investigate and improve your API security posture, prioritize vulnerability fixes, and quickly detect active real-time threats.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-apis-introduction
Defender for Servers
Microsoft Defender for Servers extends protection to your Windows and Linux machines that run in Azure, Amazon Web Services (AWS), Google Cloud Platform (GCP), and on-premises. Defender for Servers integrates with Microsoft Defender for Endpoint to provide endpoint detection and response (EDR) and other threat protection features.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/plan-defender-for-servers
Defender for Containers
Microsoft Defender for Containers is a cloud-native solution to improve, monitor, and maintain the security of your containerized assets (Kubernetes clusters, Kubernetes nodes, Kubernetes workloads, container registries, container images and more), and their applications, across multicloud and on-premises environments.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-containers-introduction
Database protection
Defender for Databases in Microsoft Defender for Cloud allows you to protect your entire database estate with attack detection and threat response for the most popular database types in Azure. Defender for Cloud provides protection for the database engines and for data types, according to their attack surface and security risks.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/tutorial-enable-databases-plan
Defender for App Service
Microsoft Defender for App Service uses the scale of the cloud to identify attacks targeting applications running over App Service. Attackers probe web applications to find and exploit weaknesses. Before being routed to specific environments, requests to applications running in Azure go through several gateways, where they’re inspected and logged. The data is then used to identify exploits and attackers, and to learn new patterns that are used later.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/tutorial-enable-app-service-plan
Defender for Storage
Microsoft Defender for Storage is an Azure-native layer of security intelligence that detects potential threats to your storage accounts. It helps prevent the three major impacts on your data and workload: malicious file uploads, sensitive data exfiltration, and data corruption.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-storage-introduction
Defender for Key Vault
Azure Key Vault is a cloud service that safeguards encryption keys and secrets like certificates, connection strings, and passwords.
Microsoft Defender for Key Vault detects unusual and potentially harmful attempts to access or exploit Key Vault accounts. This layer of protection helps you address threats even if you’re not a security expert, and without the need to manage third-party security monitoring systems.
When anomalous activities occur, Defender for Key Vault shows alerts and optionally sends them via email to relevant members of your organization. These alerts include the details of the suspicious activity and recommendations on how to investigate and remediate threats.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-key-vault-introduction
Defender for Resource Manager
Azure Resource Manager is the deployment and management service for Azure. It provides a management layer that enables you to create, update, and delete resources in your Azure account. You use management features, like access control, locks, and tags, to secure and organize your resources after deployment.
The cloud management layer is a crucial service connected to all your cloud resources. Because of this, it is also a potential target for attackers. Consequently, we recommend security operations teams monitor the resource management layer closely.
Microsoft Defender for Resource Manager automatically monitors the resource management operations in your organization, whether they’re performed through the Azure portal, Azure REST APIs, Azure CLI, or other Azure programmatic clients. Defender for Cloud runs advanced security analytics to detect threats and alerts you about suspicious activity.
Defender for DNS
Microsoft Defender for DNS provides an additional layer of protection for resources that use Azure DNS’s Azure-provided name resolution capability.
From within Azure DNS, Defender for DNS monitors the queries from these resources and detects suspicious activities without the need for any additional agents on your resources.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-dns-introduction
DevOps security
Microsoft Defender for Cloud enables comprehensive visibility, posture management, and threat protection across multicloud environments including Azure, AWS, GCP, and on-premises resources.
DevOps security within Defender for Cloud uses a central console to empower security teams with the ability to protect applications and resources from code to cloud across multi-pipeline environments, including Azure DevOps, GitHub, and GitLab. DevOps security recommendations can then be correlated with other contextual cloud security insights to prioritize remediation in code.
Source: https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-devops-introduction
Links
What is Microsoft Defender for Cloud?
https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-cloud-introductionConnect your Azure subscriptions
https://learn.microsoft.com/en-us/azure/defender-for-cloud/connect-azure-subscriptionAutomate onboarding of Microsoft Defender for Cloud using PowerShell
https://learn.microsoft.com/en-us/azure/defender-for-cloud/powershell-onboarding
Tags In
Related Posts
Follow me on LinkedIn


