Windows Local Administrators Group Membership on Azure AD joined Devices
What actually happens to the local administrators group membership when you join a windows device to Azure AD?
Below to check the modifications to the local administrator group membership will occur during an Azure AD join, I will using a new installation from Windows 10 on a virtual machine.
Here I will sign in with a normal user account which had not assigned any roles especially not the Global administrator role, which by default will be added to the local administrators group similar to the on-premises AD group – Domain Admins, which will also be added during an on-premise AD join.
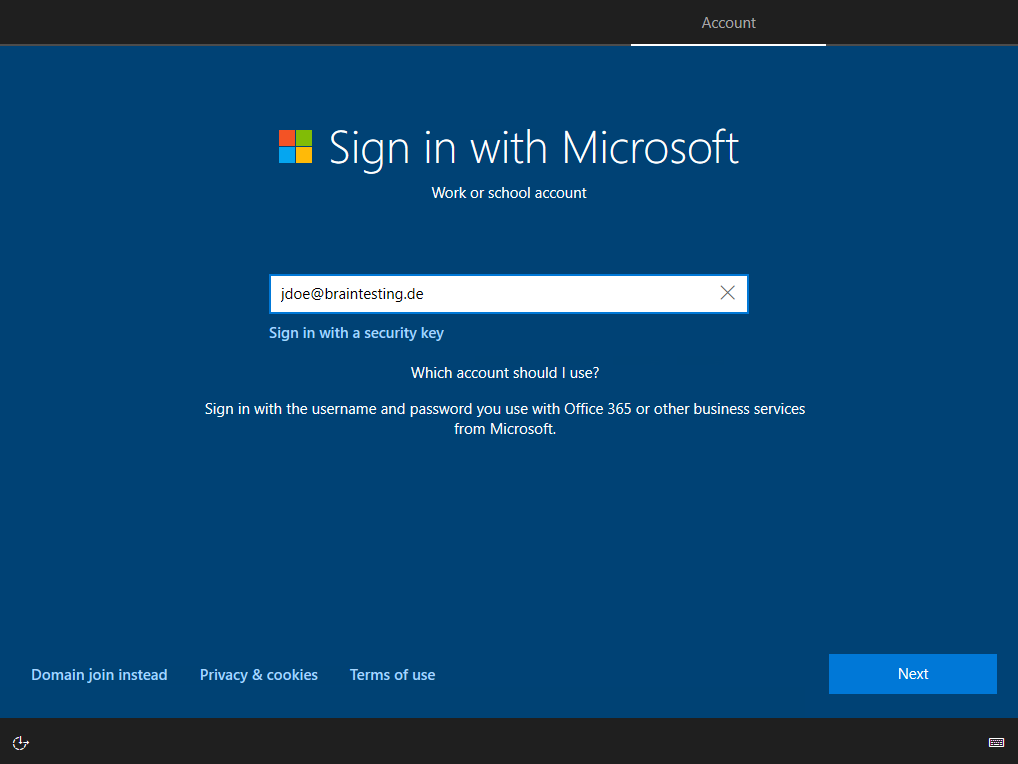
Afterwards the classic Out-of -Box Experience OOEB will appear to set up the account and profile.
Now we check by using the Computer Management Snap-In what happened to the local administrators group membership.
As already mentioned the Azure AD Global administrator role was added to the local administrators group.
Below the Global administrator role is the last entry with the following SID
S-1-12-1-9004393-1283818314-846049430-1489853906
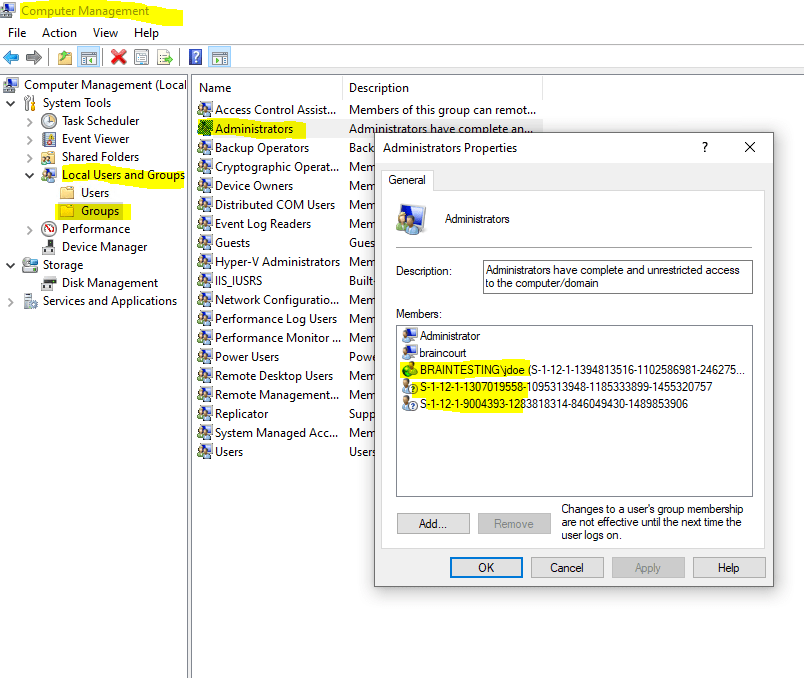
The forelast SID S-1-12-1-1307019558-1095313948-1185333899-1455320757 is the Azure AD Joined Device Local Administrator role which is also added to the local administrator group during the Azure AD join.
Finally also the user performing the Azure AD join is added to the local administrator group, here the user John Doe (BRAINTESTINGjdoe).
Unfortunately the Azure AD roles wouldn’t appear with its name like AD security groups in on-premises networks. To determine the corresponding name of the Azure AD role SIDs, you can use the following PowerShell script from Oliver Kieselbach.
Convert-AzureAdObjectIdToSid.ps1
https://github.com/okieselbach/Intune/blob/master/Convert-AzureAdObjectIdToSid.ps1
function Convert-AzureAdObjectIdToSid {
<#
.SYNOPSIS
Convert an Azure AD Object ID to SID
.DESCRIPTION
Converts an Azure AD Object ID to a SID.
Author: Oliver Kieselbach (oliverkieselbach.com)
The script is provided "AS IS" with no warranties.
.PARAMETER ObjectID
The Object ID to convert
#>
param([String] $ObjectId)
$bytes = [Guid]::Parse($ObjectId).ToByteArray()
$array = New-Object 'UInt32[]' 4
[Buffer]::BlockCopy($bytes, 0, $array, 0, 16)
$sid = "S-1-12-1-$array".Replace(' ', '-')
return $sid
}
$objectId = "73d664e4-0886-4a73-b745-c694da45ddb4"
$sid = Convert-AzureAdObjectIdToSid -ObjectId $objectId
Write-Output $sid
# Output:
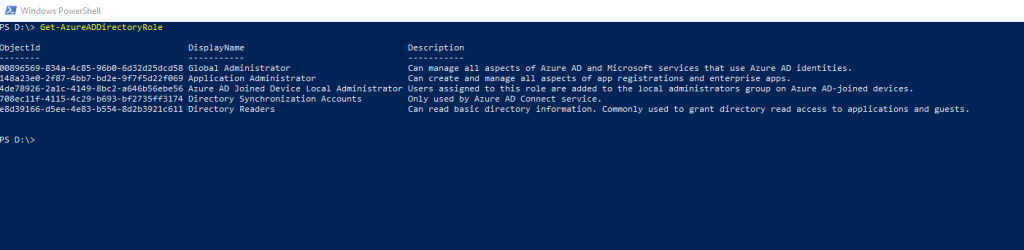
# S-1-12-1-1943430372-1249052806-2496021943-3034400218In order to run the script you first need the object ID from the Azure AD role you want to get the corresponding SID.
PS c:> Connect-AzureAD
PS c:> Get-AzureADDirectoryRole
So when you connect a Windows device with Azure AD using an Azure AD join, Azure AD adds the following security principals to the local administrators group on the device:
- The Azure AD Global Administrator role
- The Azure AD joined device local administrator role
- The user performing the Azure AD join
Source: https://learn.microsoft.com/en-us/azure/active-directory/devices/assign-local-admin
You can manage the device administrator role in Azure AD under the device settings.
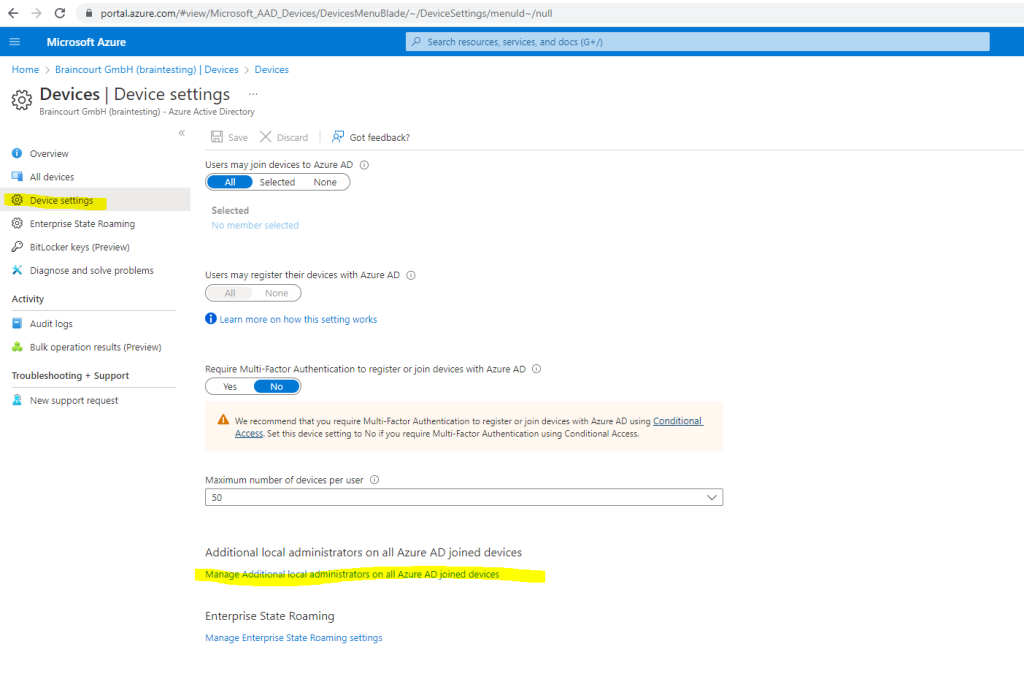
Device administrators are assigned to all Azure AD joined devices. You can’t scope device administrators to a specific set of devices. Updating the device administrator role doesn’t necessarily have an immediate impact on the affected users. On devices where a user is already signed into, the privilege elevation takes place when both the below actions happen:
- Upto 4 hours have passed for Azure AD to issue a new Primary Refresh Token with the appropriate privileges.
- User signs out and signs back in, not lock/unlock, to refresh their profile.
- Users won’t be listed in the local administrator group, the permissions are received through the Primary Refresh Token.
By default, Azure AD adds the user performing the Azure AD join to the administrator group on the device. If you want to prevent regular users from becoming local administrators, you have the following options:
- Windows Autopilot – Windows Autopilot provides you with an option to prevent primary user performing the join from becoming a local administrator by creating an Autopilot profile.
- Bulk enrollment – An Azure AD join that is performed in the context of a bulk enrollment happens in the context of an auto-created user. Users signing in after a device has been joined aren’t added to the administrators group.
More about Windows Autopilot and creating Autopilot profiles you can read in my following post in the section
Create the Windows Autopilot deployment profile
Links
How to manage the local administrators group on Azure AD joined devices
https://learn.microsoft.com/en-us/azure/active-directory/devices/assign-local-admin
Convert-AzureAdObjectIdToSid
https://github.com/okieselbach/Intune/blob/master/Convert-AzureAdObjectIdToSid.ps1


