SSO Single-Sign-On to your onPremise RDS Remote Desktop Services 2016/2019 Environment
Normally, if you want to access a remote desktop services environement, first you have to logon to the RD Web Access Page, therefore you will be prompted with a logon dialog where you have to enter your username and password.
After that logon, you will see depending on the deployment, more or less remoteapp programms. These are the programms, published on the RD Session Host.
If you want to access and open these programms, you will be prompted a second time with an annoying logon dialog to enter your username and password.
Today I wanna go step by step through the points, to enable SSO Single-Sign-ON and passing your local windows credentials through the Remote Desktop Services RDS.
Set up SSO to RDS
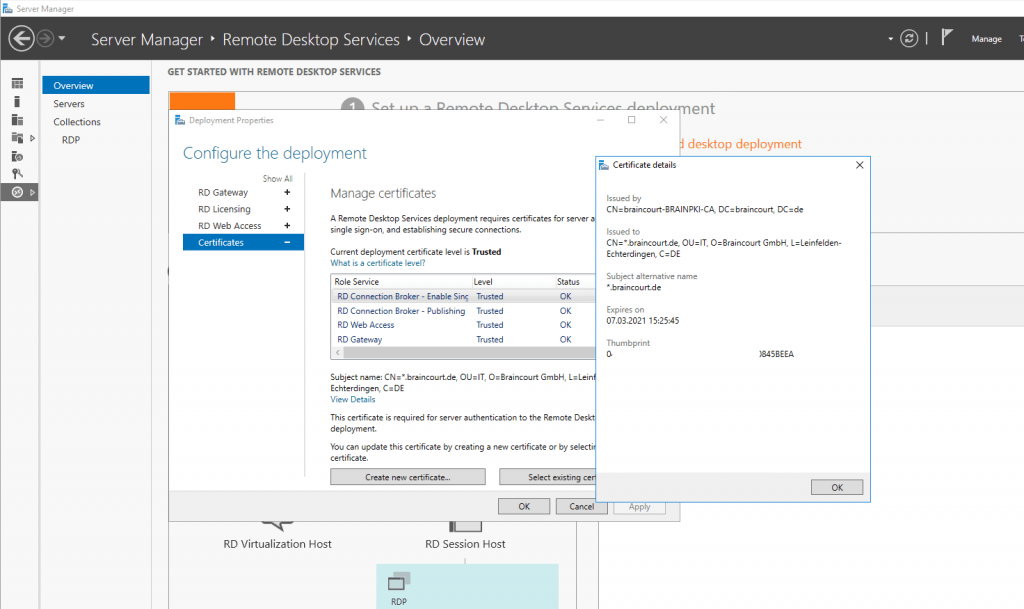
First check that you use a trusted certificate for the Role Services:
- RD Connection Broker
- RD Web Access
- RD Gateway
In my case I use a wildcard certificate from the internal company CA (PKI/ADCS), therefore the certificates are trusted on all clients from the company as they will enrolled automatically to all domain members.
If you are not using a wildcard certificate, make sure to include the DNS names from your RD Web Access FQDN and your RD Connection Broker FQDN.
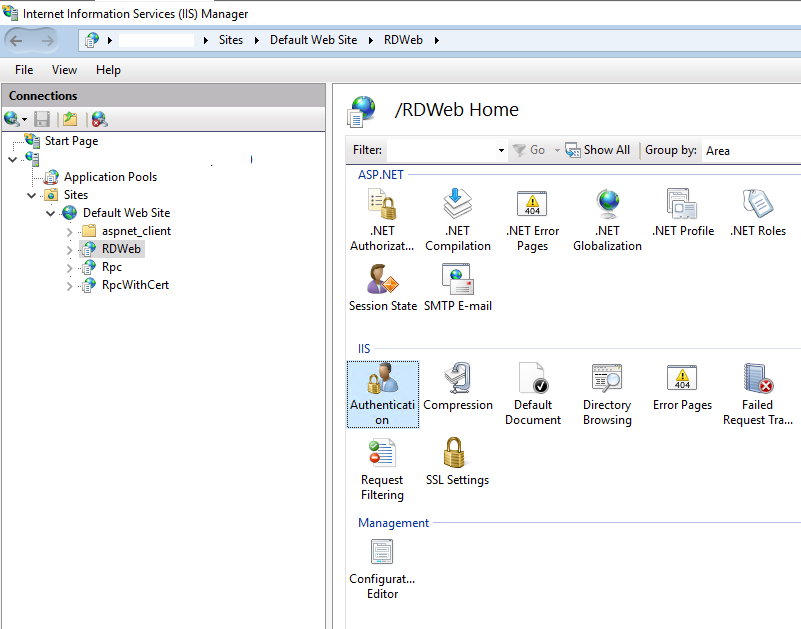
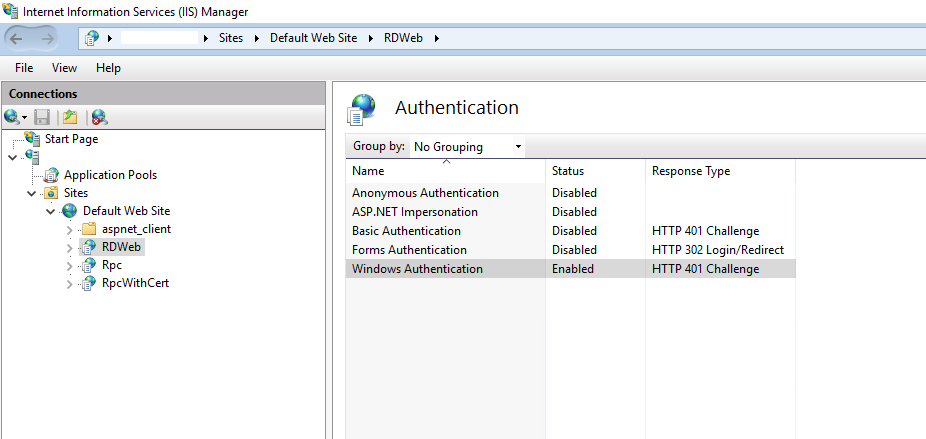
Then you must change the default authentication from Anonymous Authentication to Windows Authentication. So disable Anonymous Authentication and enable Windows Authentication.
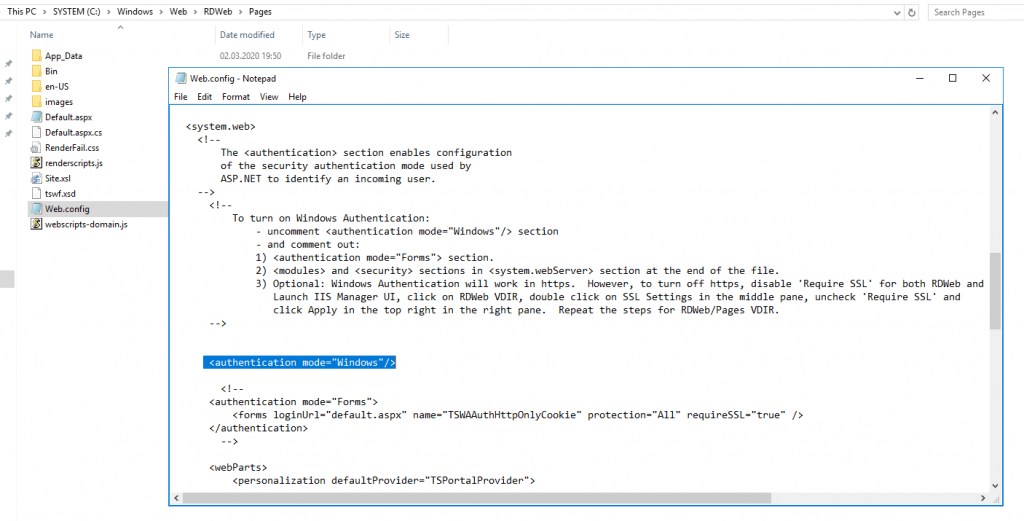
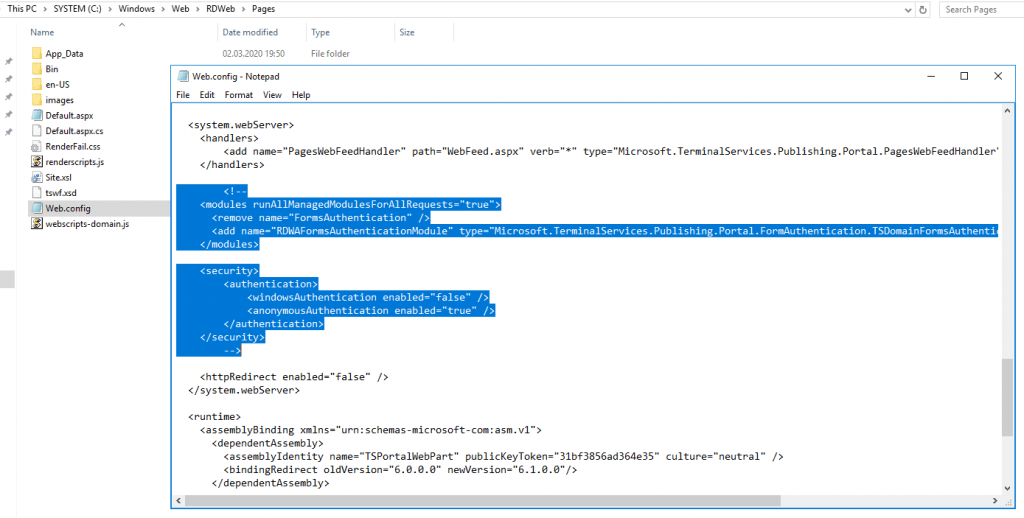
Also you must enable Windows Authentication in the web.config file under C:WindowsWebRDWebPages
You have to comment out Form Authentication + the <modules> and <security> sections in <system.webServer> and uncomment Windows Authentication as described itself in the web.config file.
For SSO we also do not want to be asked whether we use a public or private computer as per default in C:WindowsWebRDWebPagesen-USDefault.aspx is set.
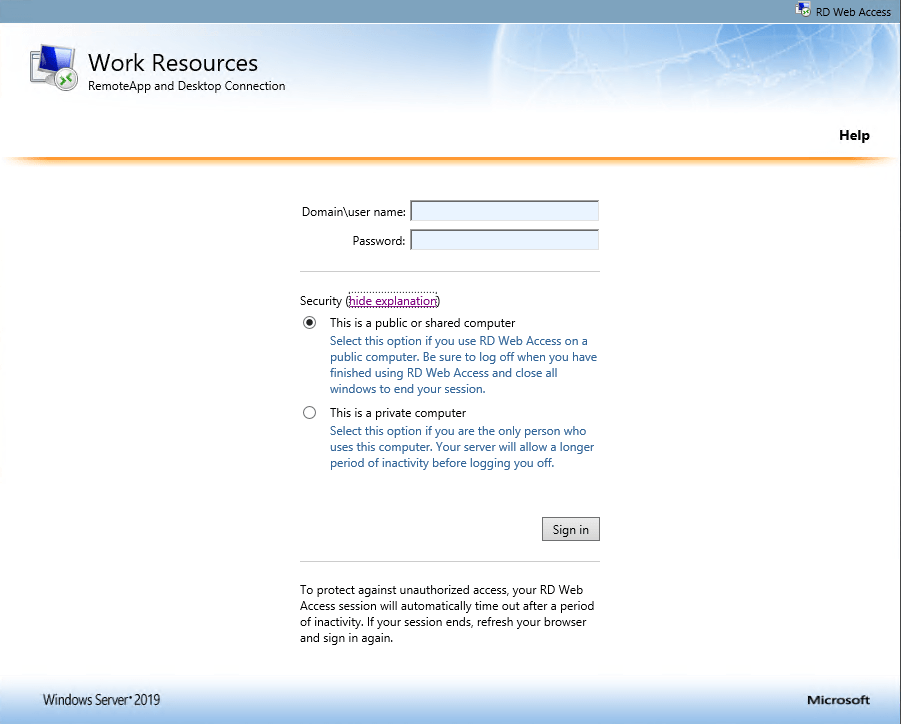
So we have to change this fix into This is a private computer.
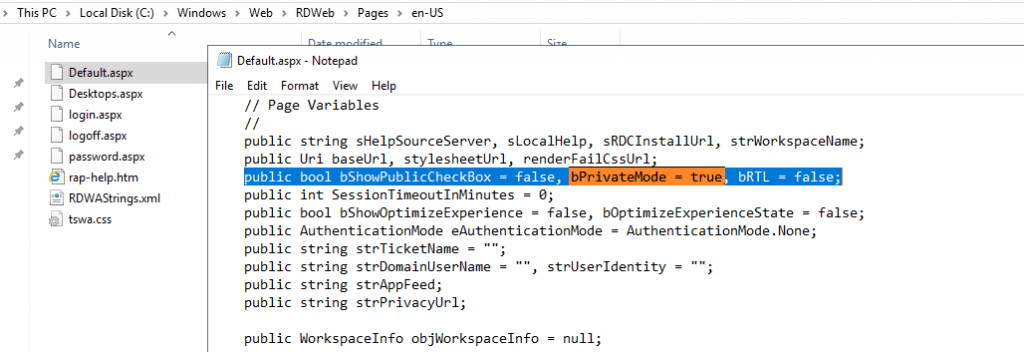
Set the bPrivateMode variable into true inside the C:WindowsWebRDWebPagesen-USDefault.aspx file.
In order to get Single-Sign-On kick in, we also needs to configure a bunch of Group Policy (GPO) settings.
We need to configure both, Computer- and User Configuration settings at the GPO. So I use one GPO and linked it to my users OU who wants to single-sign-on into RDS and also linked this GPO to an OU which includes my RDS servers.
So first we editing the Computer Configuration settings of this GPO!
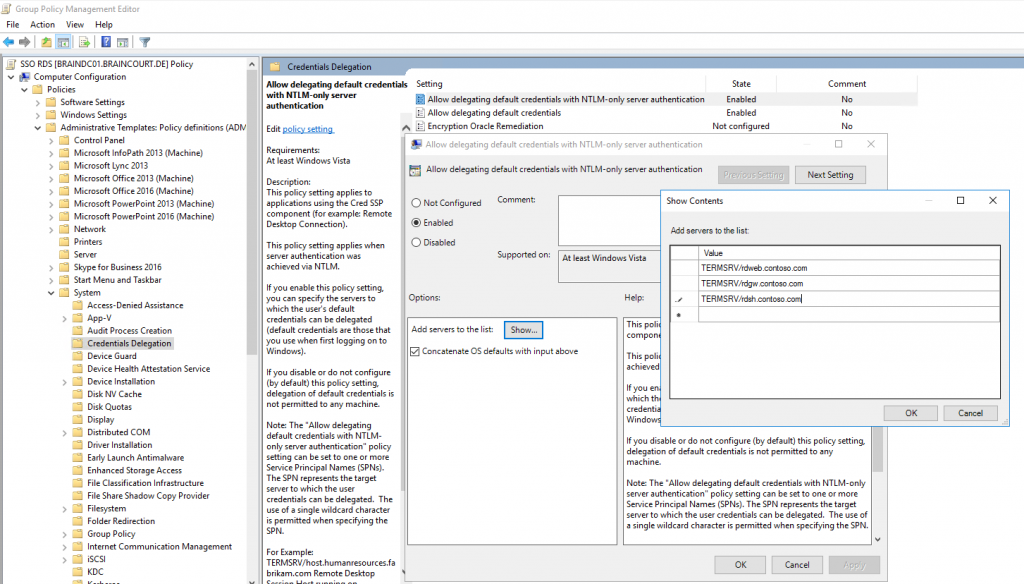
Open Computer Configuration – Policies – Administrative Templates – System – Credentials Delegation
Enable Allow delegation default credentials with NTLM-only server authentication and add the names (FQDNs) of your RDS servers (RD Web Access, RD Gateway, RD Connection Broker and RD Session Host).
Add the servers with the format of a Service Principal Name (SPN)
- TERMSRV/rdweb.contoso.com
TERMSRV must be in uppercase!
Instead listing all your RDS servers separate, you can also use a wildcard FQDN like
TERMSRV/*.contoso.com
or
TERMSRV/*
Be aware that these wilcards can be a security risk!
This setting applies when the server authentication was achieved via NTLM, which is the case when you access your RDS environment from external outside of your companies network and without client certificates.
Do the same for Allow delegating default credentials. This policy setting applies when server authentication was achieved by using a trusted X509 client certificate or Kerberos.
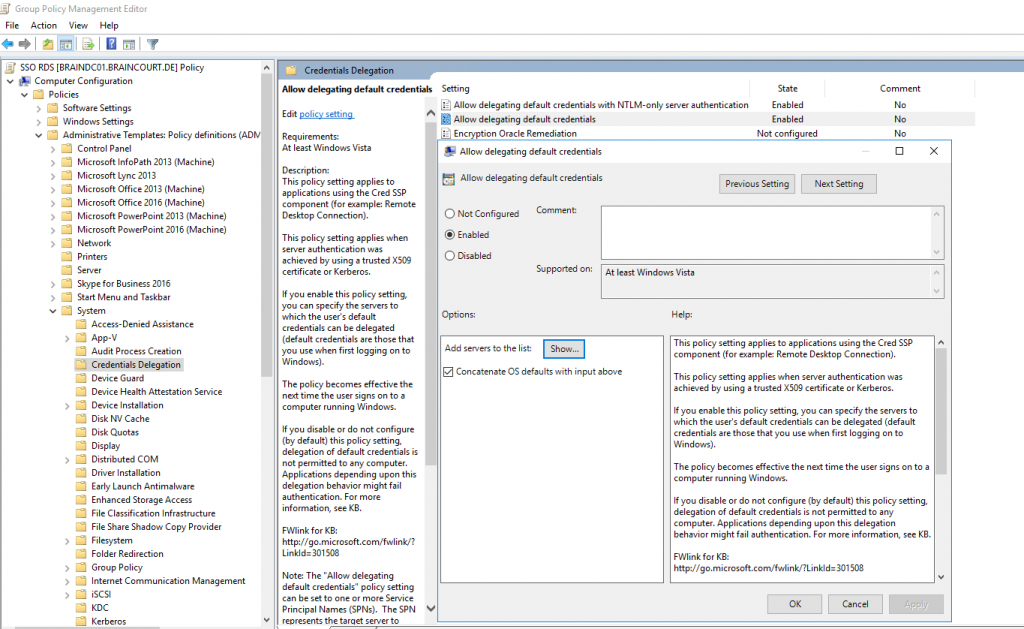
Those Credentials Delegation GPOs will set the following registry settings under the hood.
CredSSP is enabled by default since Vista and Windows 7.
You will find this under HKLMSYSTEMCurrentControlSetControlSecurityProviders
REG_SZ value credssp.dll
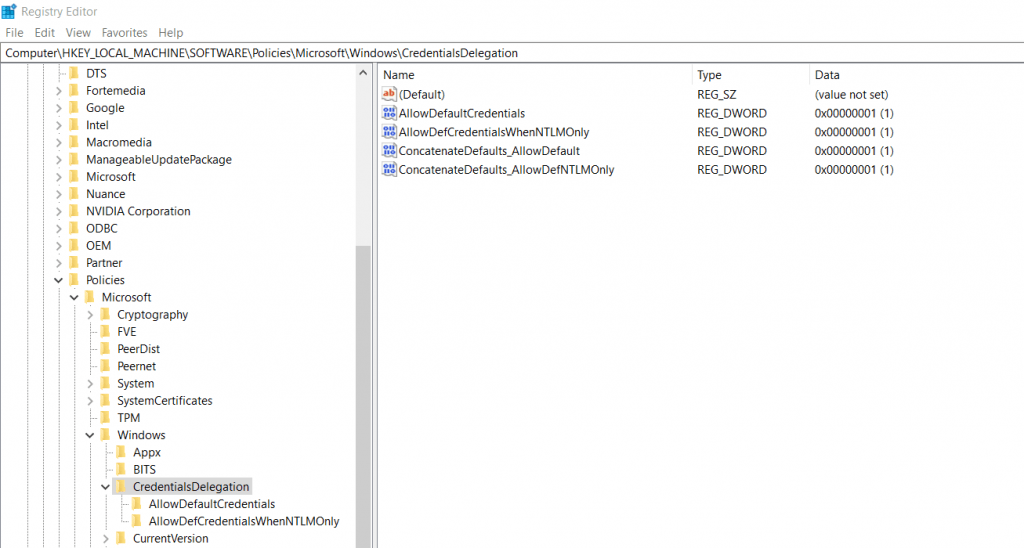
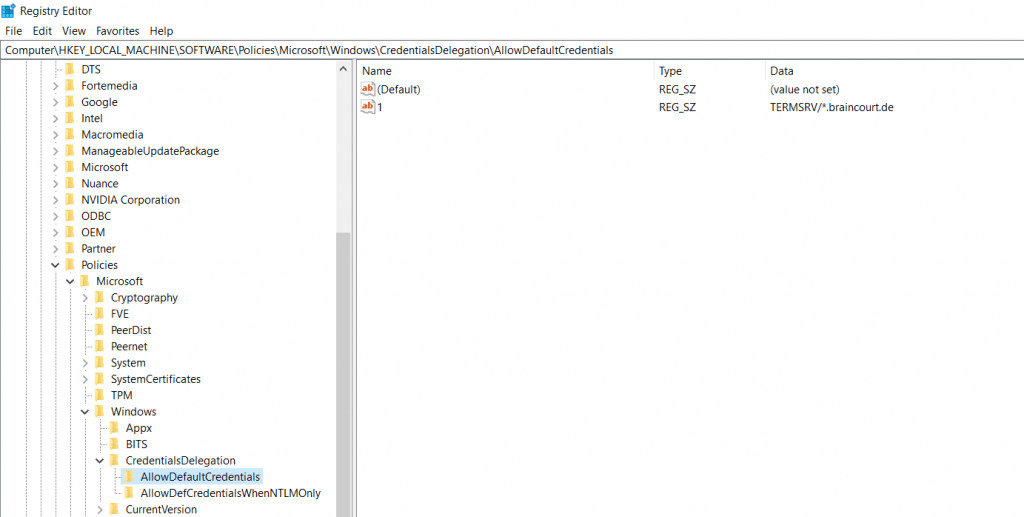
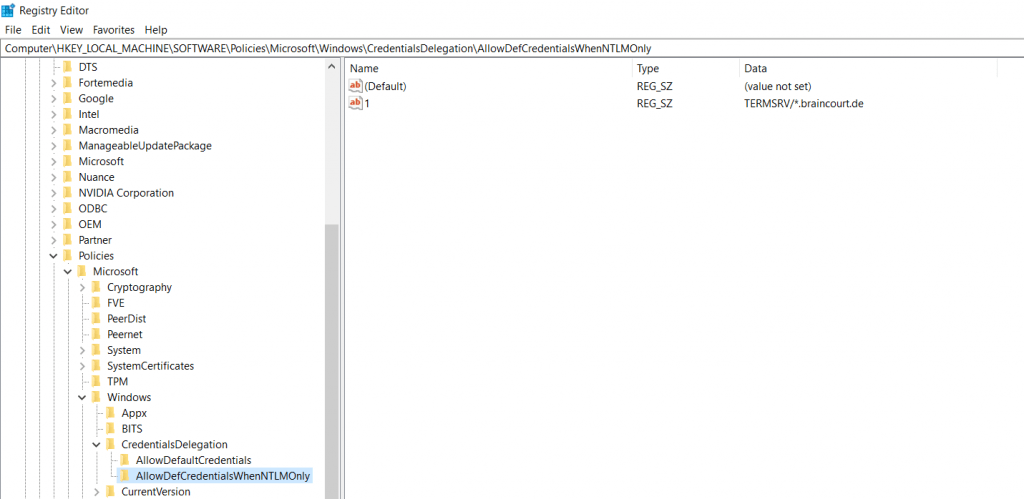
To allow Internet Explorer, to pass our credentials through the rdp connection in order to open the remote apps, we must add the addresses (FQDNs) of the RD Connection Broker, RD Web Access and RD Gatway servers under
Computer Configuration – Policies – Administrative Templates – Windows Components – Internet Explorer – Internet Control Panel – Security Page
Enable here Site to Zone Assignment List and add your addresses with an value of 2 for Trusted Sites zone.
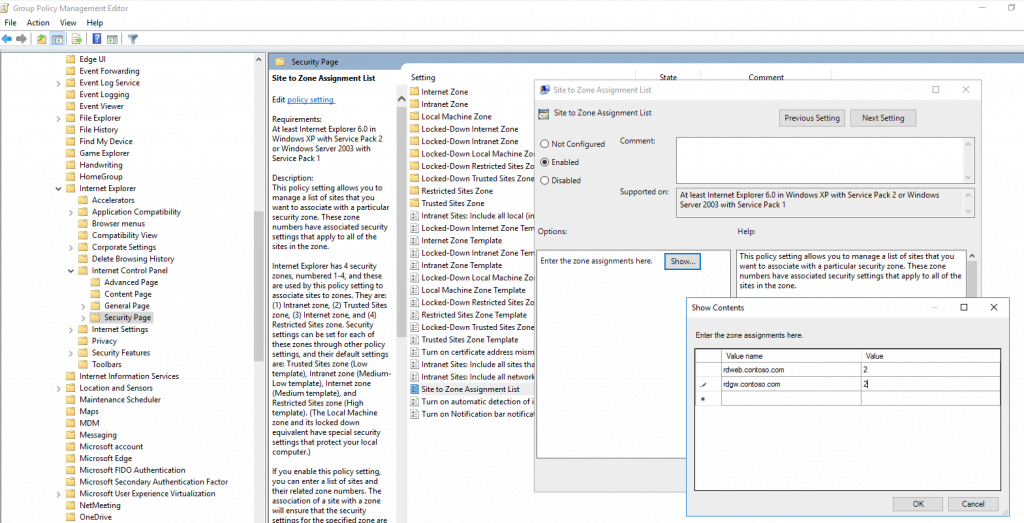
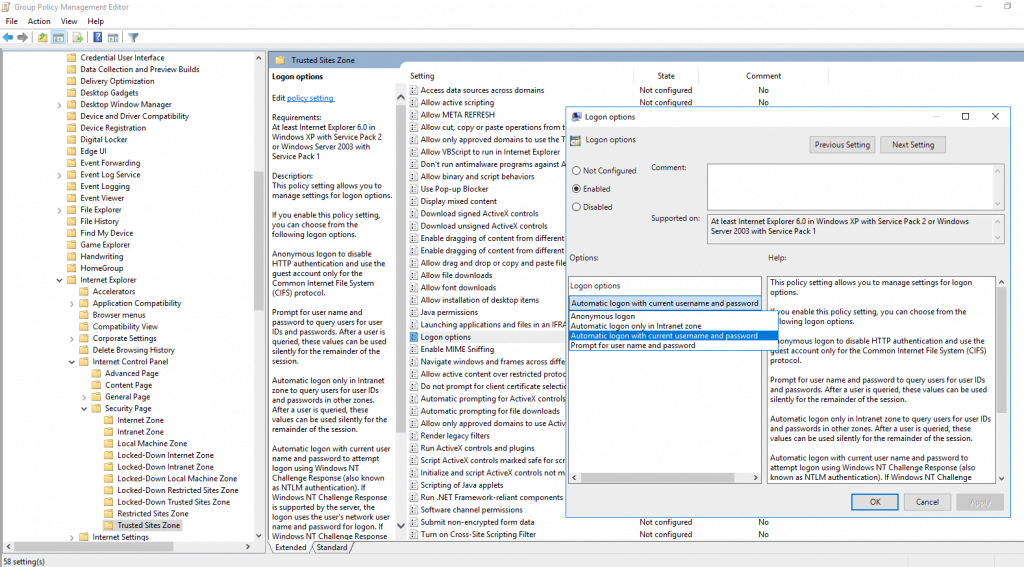
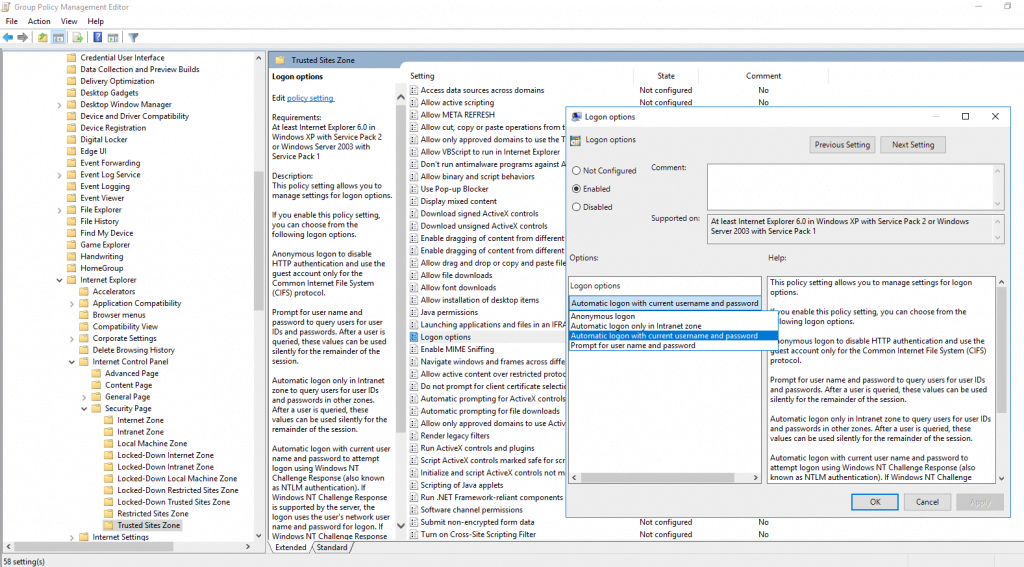
Further you will find here the folder Trusted Sites Zones in which we enable Logon options and set them to Automatic logon with current username and password
The last setting under Computer Configuration we must set you will find under:
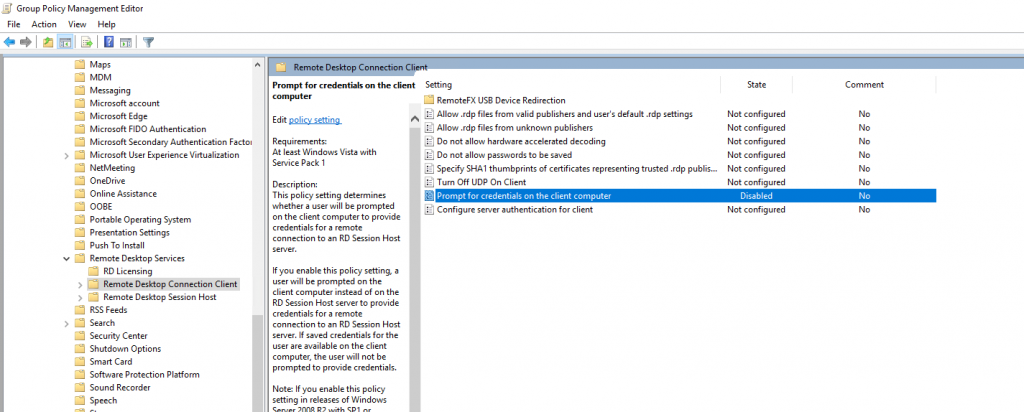
Computer Configuration – Policies – Administrative Templates – Windows Components – Remote Desktop Services – Remote Desktop Connection Client
Disable Prompt for credentials on the client computer
So far we finished the Computer Configuration GPO settings and now have to configure some User Configuration settings!
As I link this GPO to both, computers and users and their OUs, I can make these settings in the same GPO.
We also have to add the addresses (FQDNs) of the RD Connection Broker, RD Web Access and RD Gatway servers as done before for the Computer Configuration, under
User Configuration – Policies – Administrative Templates – Windows Components – Internet Explorer – Internet Control Panel – Security Page
Enable here Site to Zone Assignment List and add your addresses with an value of 2 for Trusted Sites zone.
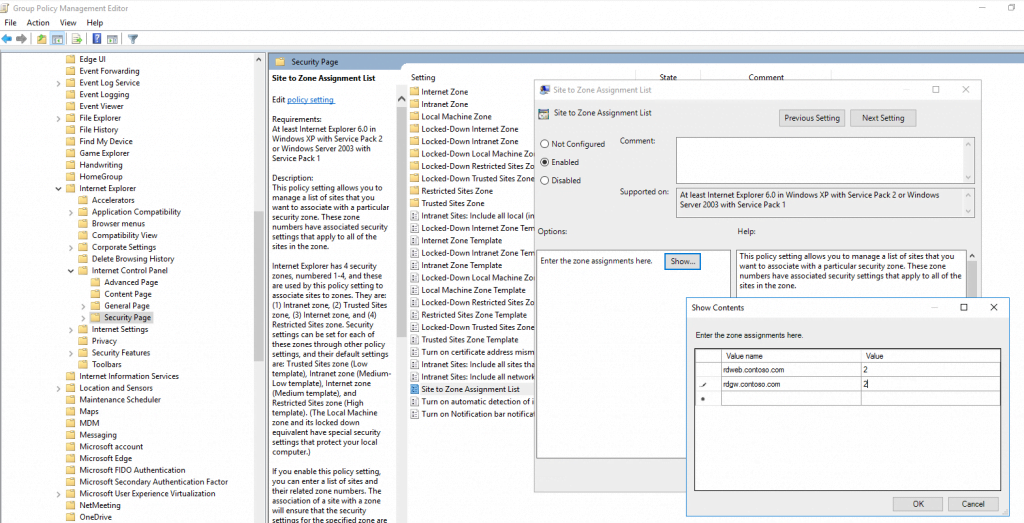
Further as also configured before in Computer Configuration, you will find here also the folder Trusted Sites Zones in which we enable Logon options and set them to Automatic logon with current username and password
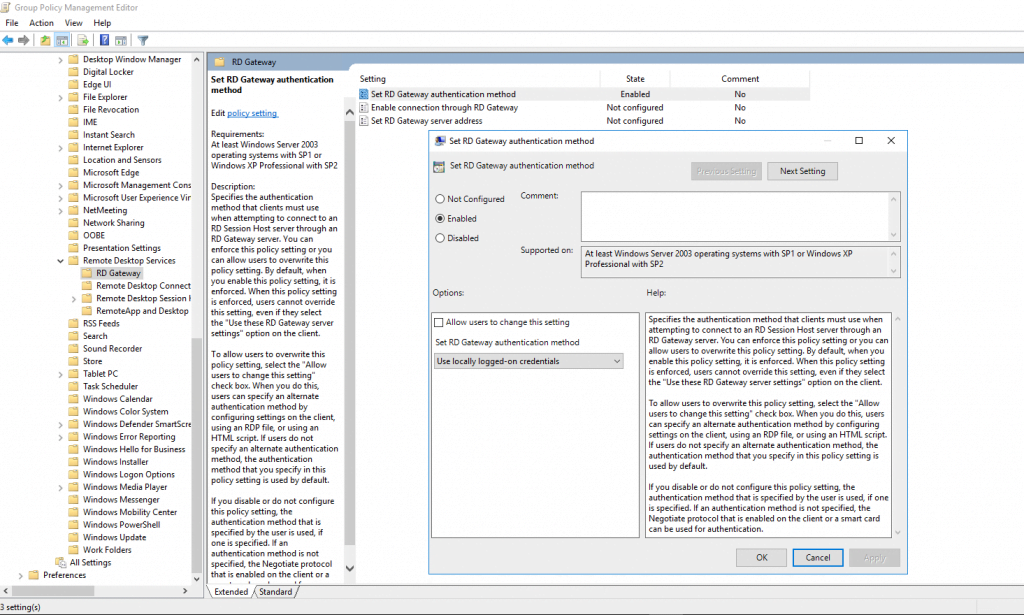
Next point is to configure the RD Gateway authentication method. So go to:
User Configuration – Policies – Administrative Templates – Windows Components – Remote Desktop Services – RD Gateway
Enable Set RD Gateway authentication method and select Use locally logged-on credentials
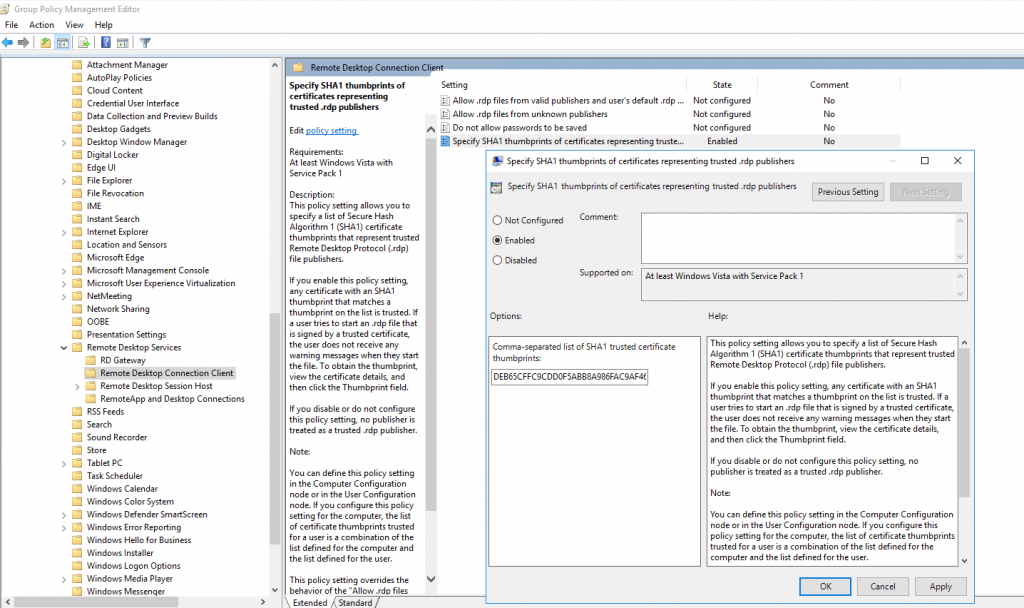
And now the last and final GPO setting still in User Configuration, is to specify the SHA1 thumbprints from the certificates of our RDS Servers in order to avoid warning prompts regarding untrusted publishers.
User Configuration – Policies – Administrative Templates – Windows Components – Remote Desktop Services – Remote Desktop Connection Client
Enable Specify SHA1 thumbprints of certificates representing trusted .rdp publishers
To get the GPO settings kicks in, restart your RDS Servers or execute gpupdate /force in the command line.
Also for your user to update the user policy, enforce an gpupdate /force on a computer inside your local network (internal or over vpn connected).
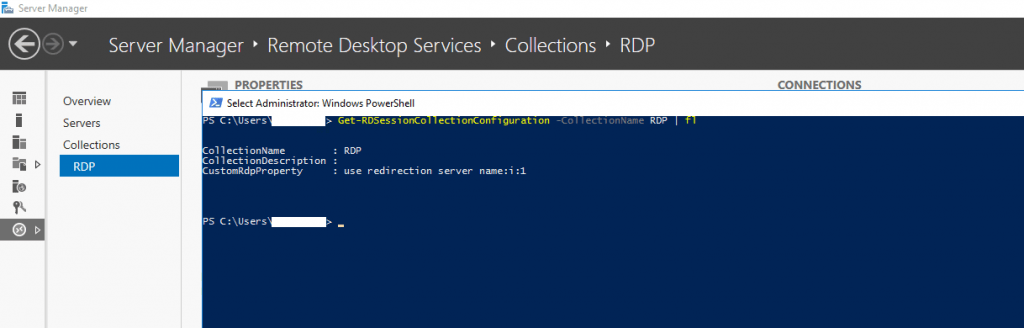
Also check finally your CustomRdpProperty settings
Get-RDSessionCollectionConfiguration -CollectionName <Collection> | fl
Should look like the following, if not
Set-RDSessionCollectionConfiguration -CollectionName <Collection Name> -CustomRdpProperty “use redirection server name:i:1”
From now on, if everything was configured correct, you won’t be prompted for your credentials, neither to access the RDWeb page nor at opening the remote apps inside RDWeb.
Troubleshooting
An authentication error has occured (Code: 0x607).
Remote computer:
This error message will come up if an incorrect terminalservices certificate is assigned.
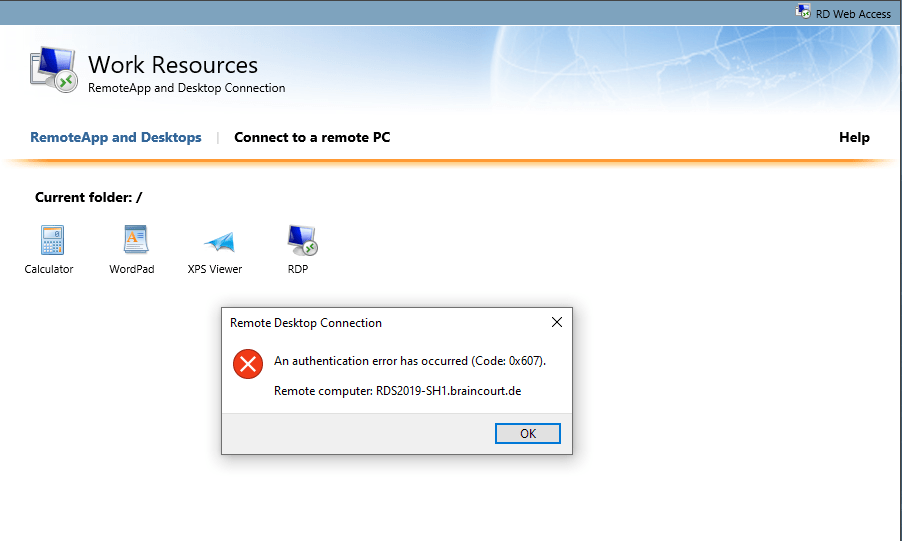
So check out what certficate is assigned and replace it with a correct one. For the session host it is quite ok to use a self-signed certificate, you only need trusted certificates for the RD Connection Broker, RD Gateway an RD Web Access Server. In my case the problem was, that I renamed the session host and the terminalservices still use the old certificate with the old name.
How to replace this certificate you can see here
Some interesting stuff about RDS and SSO
Network Level Authentication (NLA)
https://en.wikipedia.org/wiki/Network_Level_Authentication
Credential Security Support Provider
https://docs.microsoft.com/en-us/windows/win32/secauthn/credential-security-support-providerhttps://en.wikipedia.org/wiki/Security_Support_Provider_Interface
https://docs.ansible.com/ansible/latest/user_guide/windows_winrm.htmlCredSSP authentication is a newer authentication protocol that allows credential delegation. This is achieved by encrypting the username and password after authentication has succeeded and sending that to the server using the CredSSP protocol. Because the username and password are sent to the server to be used for double hop authentication, ensure that the hosts that the Windows host communicates with are not compromised and are trusted. CredSSP can be used for both local and domain accounts and also supports message encryption over HTTP.
SSPI
https://docs.microsoft.com/en-us/windows/win32/secauthn/sspi
Bypassing RDP Authentication
https://ryanmangansitblog.com/2013/03/10/configuring-rds-2012-certificates-and-sso/
Older versions of windows connected to the computer before checking credentials, RDS now checks credentials before connecting. The following custom RDP Property is not to be used without security considerations, but if you want to turn off warning or alerts for use in a POC/LAB/UAT Environment then its perfectly fine to get round warnings and connection issues. I do not recommend that you use this in a production environment.
Set-RDSessionCollectionConfiguration –CollectionName QuickSessionCollection -CustomRdpProperty “authentication level:i:0”
RD Web Access role service can be used to present applications on a website that is accessed by the user with a browser.
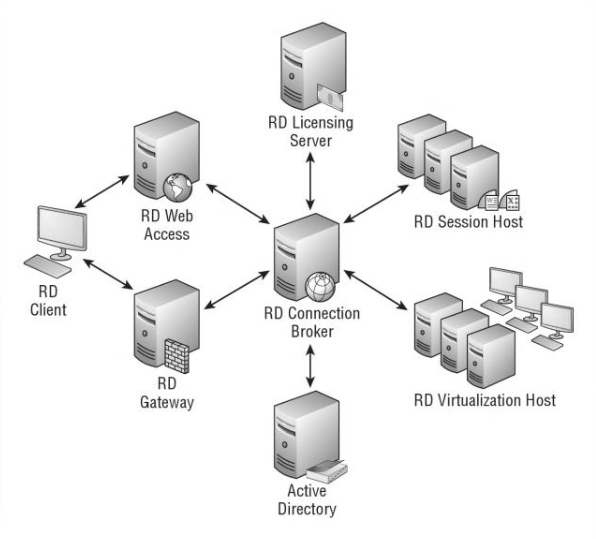
Relation between RD Session Host, RD Web Access, RD Gateway and RD Connection Broker
Virtualizing Microsoft Tier 1 Applications with VMware vSphere 4
A remote desktop (RD) client gets connection information from the RD Web Access server in an RDS solution. If an RD Client is outside a corporate network, the client connects through an RD Gateway. If an RD client is internal, the client can then directly connect to an intended RD Session Host or RD Viritualization Host once RD Connection Broker provides the connection information. In both cases, RD Connection Broker plays a central role to make sure a client gets connected to correct resource.
RD Gateway functions as an RDP proxy. It proxies incoming RDP traffic (on port 443) to the Remote Desktop Session Host (RD Session Host) servers on port 3389.
Authentication of the user/computer if he is authorized to connect to the RD Gateway
Checks if the client is allowed to connect to the requested ressource
Secure connections via HTTPS (Port 443 Default) without the use of a VPN
Enables connections through firewalls without opening additional ports IE:3389https://statemigration.com/windows-server-remote-desktop-services/
When an external client connects to the Remote Desktop Services environment through RD Gateway, RD Gateway acts as a security broker, performing client authentication by calling back-end services. It accepts the connection and authenticates the client through Remote Desktop connection authorization policies (RD CAPs) and Remote Desktop resource authorization policies (RD RAPs) that are called from AD DS. It may also call NAP to test the client’s health. Figure 3 illustrates these connections.
Once authorization is complete, the RD Gateway role service connects the client to the requested server or the RD Session Host server farm through the firewall. The RD Session Host server then performs a Windows authentication challenge with the user. If the user passes authentication, the Remote Desktop Services session can begin.
RD Connection Broker perform a variety of tasks, including:
Checking user credentials.
Assigning users to remote desktops.
Turning remote desktops on and off as needed.
Load balancing the servers that host the desktops.
Managing desktop images.
Redirecting multimedia processing to the client.Design and Place the RD Connection Broker Role Service
https://statemigration.com/windows-server-remote-desktop-services/
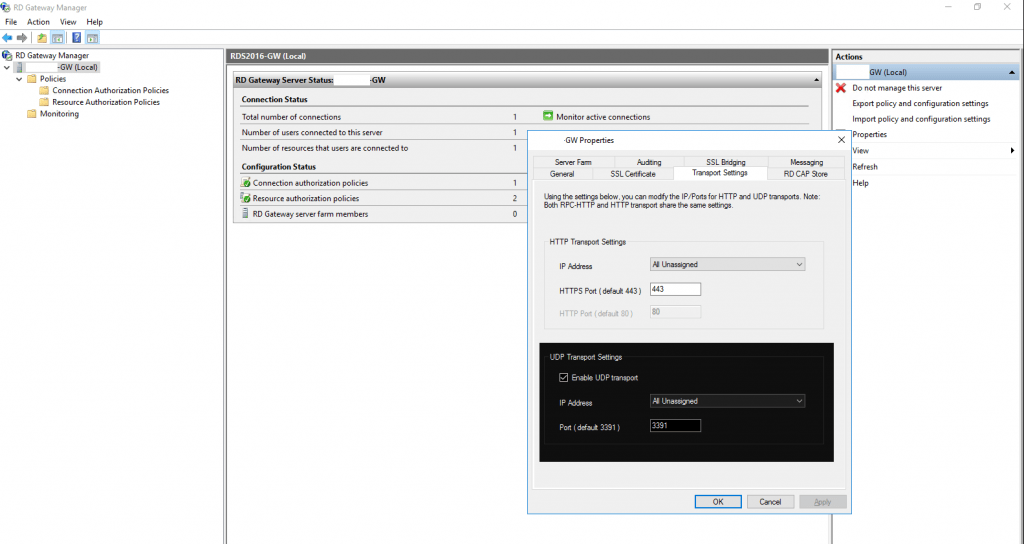
UDP Support
https://redmondmag.com/Articles/2013/12/24/RD-Gateway-in-Windows-Server.aspx?Page=1
RD Gateway supports UDP since Windows Server 2012 to optimize transport of data over the internet.
The UDP tunnel uses DTLS to secure its communications so will also utilize the SSL certificate in place on the RD Gateway server.
https://en.wikipedia.org/wiki/Datagram_Transport_Layer_SecurityBy default RD Gateway uses port 443 for HTTP and port 3391 for UDP.
Links
Remote Desktop Services roles
https://docs.microsoft.com/en-us/windows-server/remote/remote-desktop-services/rds-rolesHow To Work with RD Gateway in Windows Server 2012
https://redmondmag.com/Articles/2013/12/24/RD-Gateway-in-Windows-Server.aspx?Page=1RD Connection Broker
https://www.petri.com/remote-desktop-services-deployment-options-windows-server-2012-r2Windows Server 2012 R2: Get a list of active Remote Desktop Users
https://www.petri.com/windows-server-2012-r2-get-list-active-remote-desktop-usersRemote Desktop Services 2016, Standard Deployment – Part 4 – RD Web Access (Part4) – SSO & High Availability
https://nedimmehic.org/2017/11/20/remote-desktop-services-2016-standard-deployment-part-4-rd-web-access-part4-sso-high-availability/Windows 2012 R2 – How to Create a (Mostly) Seamless Logon Experience For Your Remote Desktop Services Environment
https://www.rdsgurus.com/windows-2012-r2-how-to-create-a-mostly-seamless-logon-experience-for-your-remote-desktop-services-environment/
Tags In
Related Posts
Latest posts
Deploying NetApp Cloud Volumes ONTAP (CVO) in Azure using NetApp Console (formerly BlueXP) – Part 5 – Backup and Recovery
Follow me on LinkedIn


