Active Directory Certificate Mapping – Implicit vs. Explicit
In Active Directory you can use certificate mapping to bind an identity to a X.509 certificate, which then can be used to authenticate against services from Microsoft.
Implicit vs. Explicit
For certificate mapping we need to distinguish between the implicit and explicit mapping.
Implicit is what in most cases if using certificates from the internal CA will be used by default in your environment. In that case the certificate by default contains the User Principal Name (UPN) for user certificates in the Subject Alternative Name (SAN) extension, further the CA’s certificate is listed in the Enterprise NTAuth store from Active Directory.
Therefore Active Directory trusted the certificate presented by the user and will check the account by using the Subject Alternative Name (SAN) from that user certificate.
Explicit mapping you must define if the issued certificates to clients are from a third-party CA and therefore not trusted by default from Active Directory. For explicit mapping you must add the third-party CA certificate to the NTAuth store and ensure that the certificate’s Subject or Subject Alternative Name contains the user’s User Principal Name (UPN) from the user certificate.
Check if Implicit Certificate Mapping is still enabled
This will be the case if the issuing CA is still listed in the NTAuth store, if not you have to add the CA’s certificate to.
Go to your CA server and open the PKIVIEW tool which will help you also to check the health from your CA.
pkiview.msc
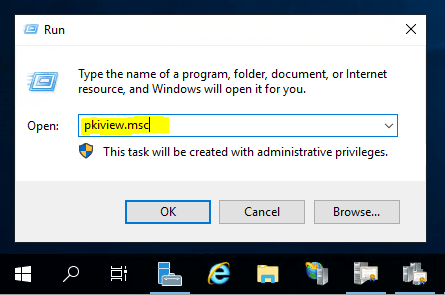
Right click on Enterprise PKI and select Manage AD Containers…
Understanding Active Directory Certificate Services containers in Active Directory
https://www.pkisolutions.com/understanding-active-directory-certificate-services-containers-in-active-directory/
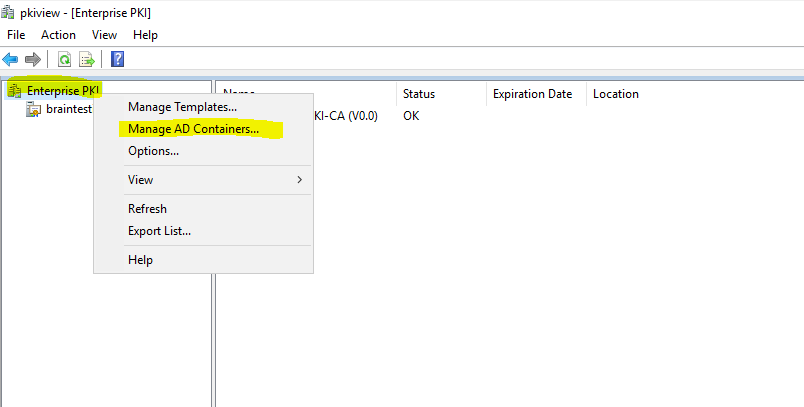
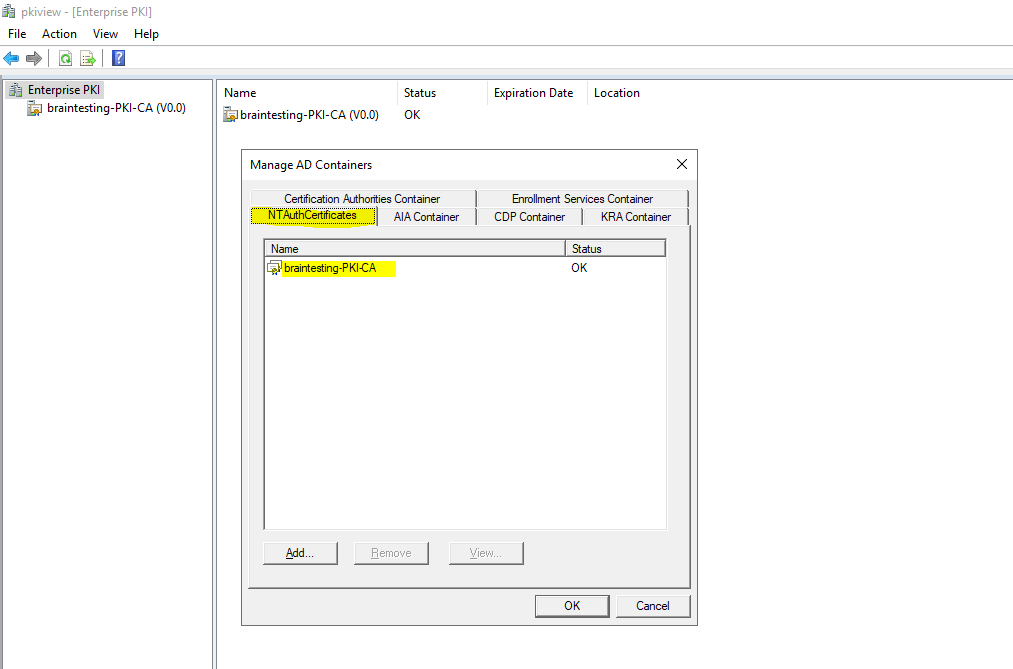
Check if your CA’s certificate is still listed in the tab NTAuthCertificates
Here my internal CA in my lab environment is still listed.
Enable Explicit Mappings
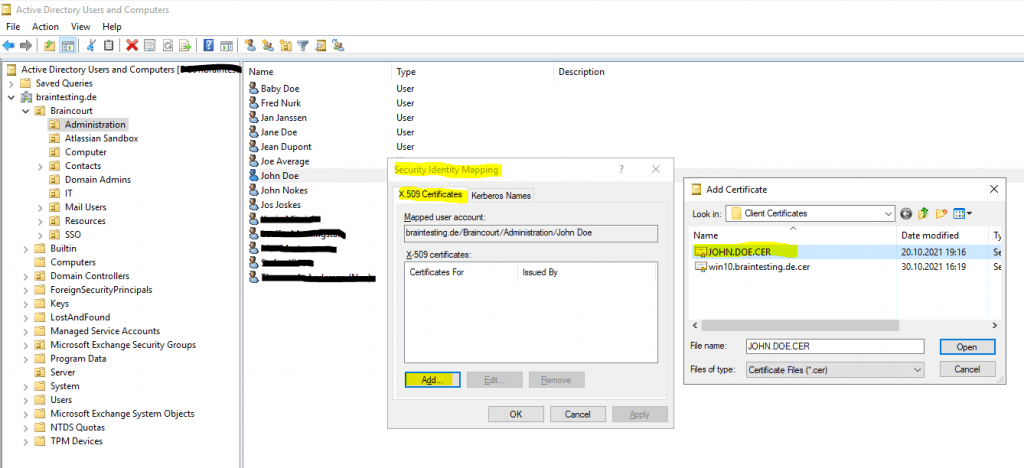
In order to enable explicit mapping for a user in Active Directory, you first need the concerned user certificate.
Implicit mapping takes precedence by SChannel for validating a client certificate.
SChannel will attempt to perform an implicit mapping based on the certificate’s subject before determining whether an explicit mapping exists.
Source: https://www.serverbrain.org/certificate-security-2003/defining-the-mapping-in-active-directory.html
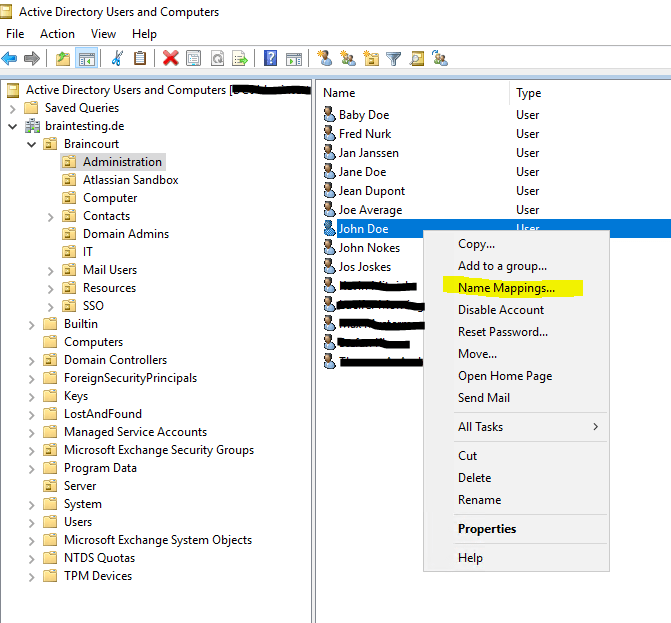
To add an explicit mapping to a user, open the Active Directory Users and Computers console and go to the user object you want to add to.
But first enable the Advanced Features.
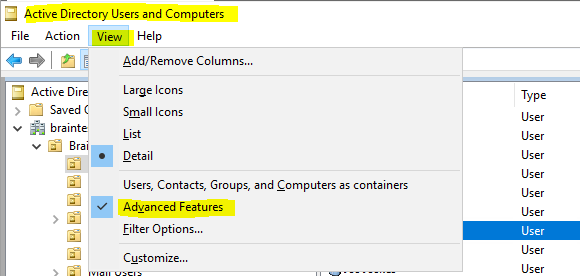
Right click on the user and select Name Mappings…
On the X.509 Certificates tab click on Add to add the user certificate.
The check boxes below depends on the mapping you want to enable, below you will see the different mapping scenarios available.
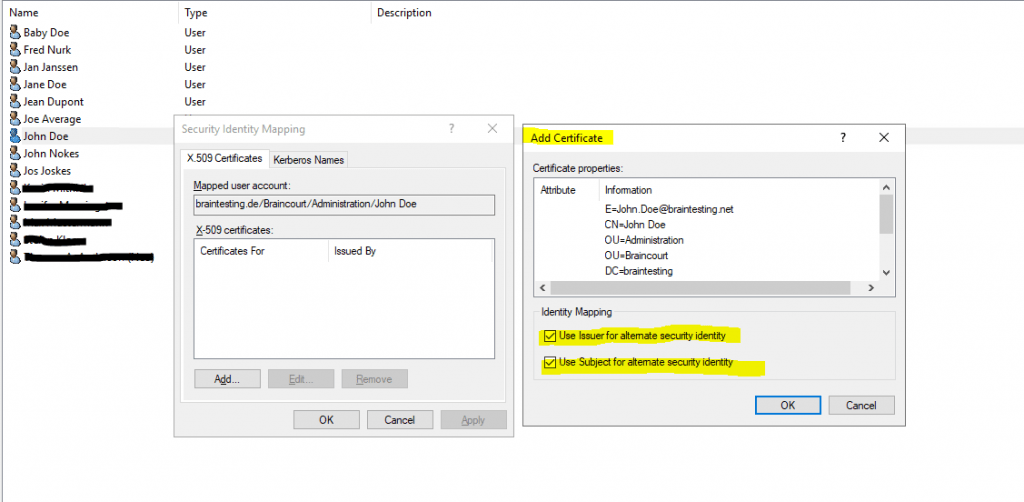
Use Issuer for alternate security identity plus Use Subject of alternate security identity is checked-> Map the certificate to one account (one-to-one mapping)
Use Subject of alternate security identity only is checked -> Map any certificate that has the same subject to the user account, regardless of the issuer of the certificate (many-to-one mapping)
Use Issuer for alternate security identity -only is checked > Map any certificate to that has the same issuer to the user account, regardless of the subject of the certificate (many-to-one mapping)
Explicit mappings cannot be used for smart card logon. Smart card logon only uses an implicit mapping by mapping the UPN in the Subject Alternative Name of the certificate to the UPN of a user account in Active Directory. Explicit mappings can be used for Web authentication, wireless authentication, and VPN authentication.
Source: https://www.serverbrain.org/certificate-security-2003/defining-the-mapping-in-active-directory.html
Enterprise NTAuth store
By publishing the CA certificate to the Enterprise NTAuth store, the Administrator indicates that the CA is trusted to issue certificates of these types. Windows CA’s automatically publish their CA certificates to this store.
The NTAuth store is an Active Directory directory service object that is located in the Configuration container of the forest.
The Lightweight Directory Access Protocol (LDAP) distinguished name is similar to the following example:
CN=NTAuthCertificates,CN=PublicKeyServices,CN=Services,CN=Configuration,DC=MyDomain,DC=com
Certificates that are published to the NTAuth store are written to the cACertificate multiple-valued attribute.

Links
Map a certificate to a user account
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/cc736781(v=ws.10)?redirectedfrom=MSDN
What is certificate mapping?
https://www.securew2.com/blog/certificate-mapping
Defining the Mapping in Active Directory
https://www.serverbrain.org/certificate-security-2003/defining-the-mapping-in-active-directory.html
User Certificate
https://www.sciencedirect.com/topics/computer-science/user-certificate
Managing user certificates
https://support.oneidentity.com/technical-documents/active-roles/7.2/user-guide/17
Understanding Active Directory Certificate Services containers in Active Directory
https://www.pkisolutions.com/understanding-active-directory-certificate-services-containers-in-active-directory/
How to import third-party certification authority (CA) certificates into the Enterprise NTAuth store
https://docs.microsoft.com/en-us/troubleshoot/windows-server/windows-security/import-third-party-ca-to-enterprise-ntauth-store
Tags In
Follow me on LinkedIn


