Set up a Key Recovery Server for the Microsoft certification authority (CA)
In this post I want tho show how to setup a key recovery server for your internal Windows CA (AD CS server role).
A Microsoft certification authority (CA) can be configured to archive and recover the private key associated with the public key submitted in the certificate request. Recovery is useful if a key is lost. By default, only encryption keys can be archived. It is not necessary to archive keys intended only for signing because only the public key is needed to verify a signature if the private signing key is lost.
Source: https://docs.microsoft.com/en-us/windows/win32/seccertenroll/about-key-recovery-server
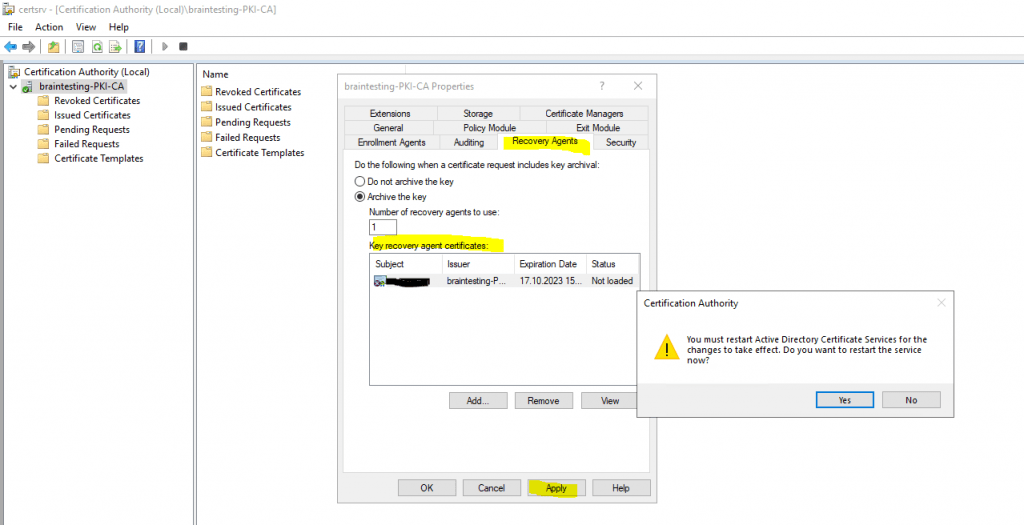
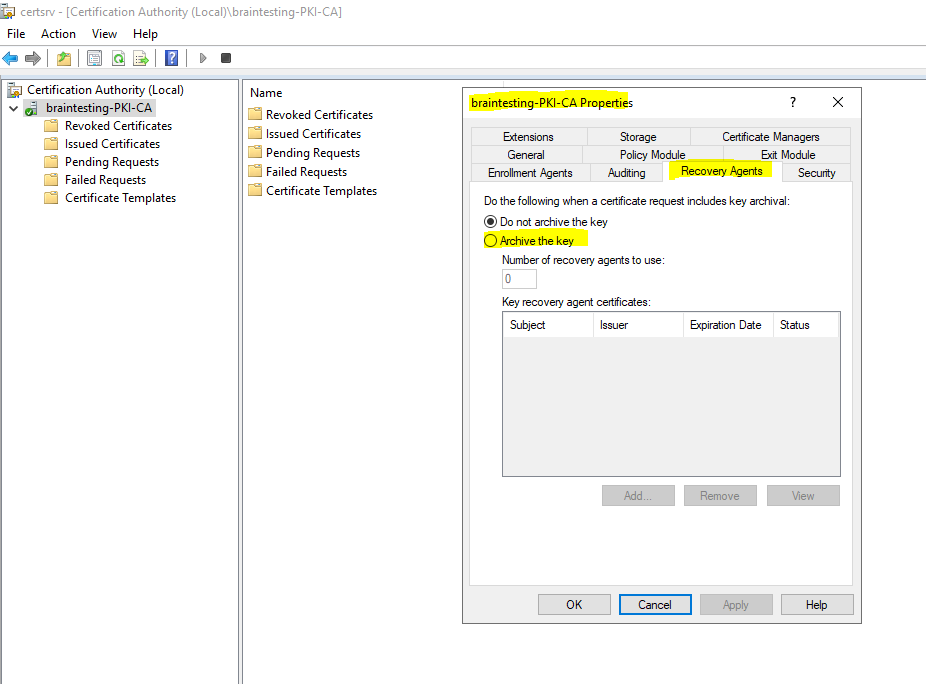
First you need to enable the CA for key archival by right clicking on the CA and select Properties. In the Recovery Agents tab select Archive the key.
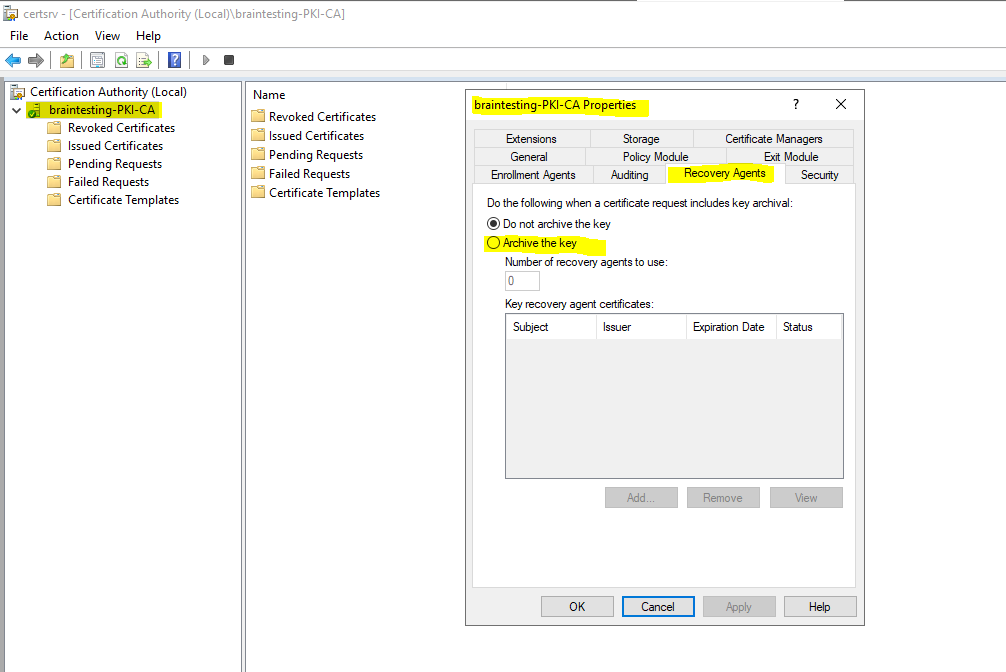
You will get a message that you also need to issue at least one recovery agent.
To archive a key, the CA must be configured to issue key recovery agent (KRA) certificates and to have already issued at least one. A key recovery agent is an administrator authorized by an organization to decrypt private keys. To enhance security, we recommend that the key recovery agent and the certificate manager roles be assigned to different individuals, that the certificate manager be permitted to retrieve but not decrypt archived keys, and that the key recovery agent be permitted to decrypt keys but not retrieve them.
Source: https://docs.microsoft.com/en-us/windows/win32/seccertenroll/about-key-recovery-server
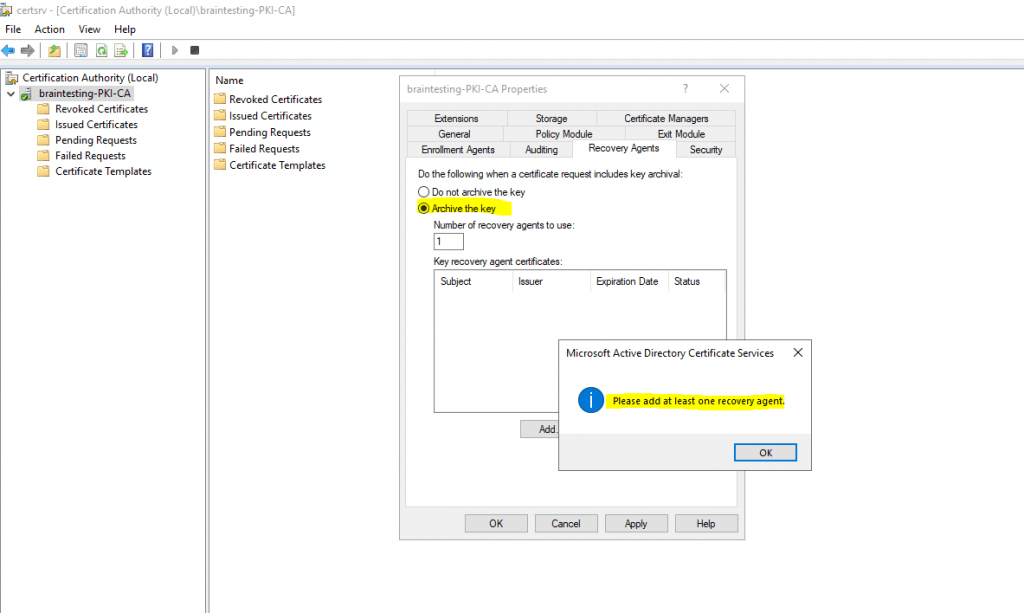
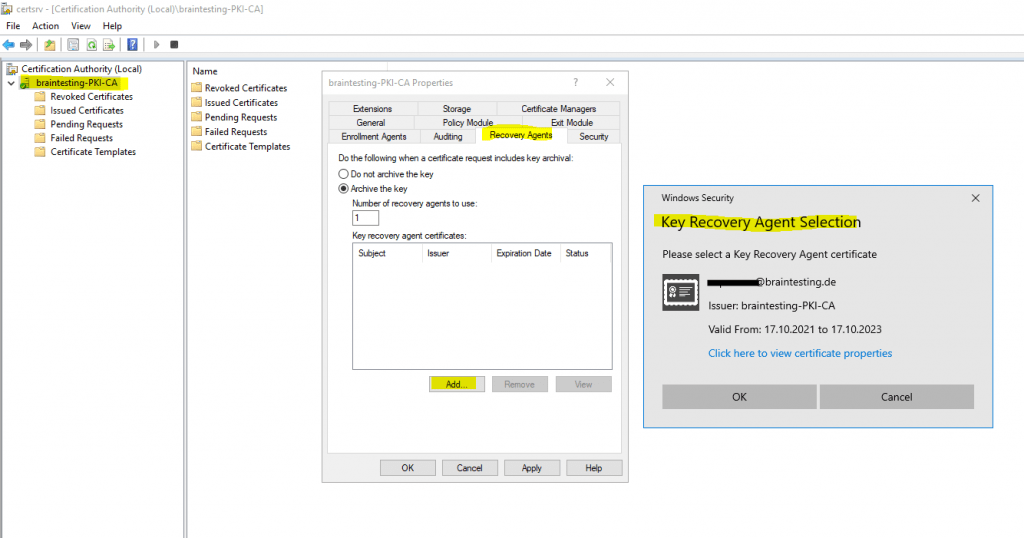
You can click on the Add button for adding a recovery agent certificate to your CA.
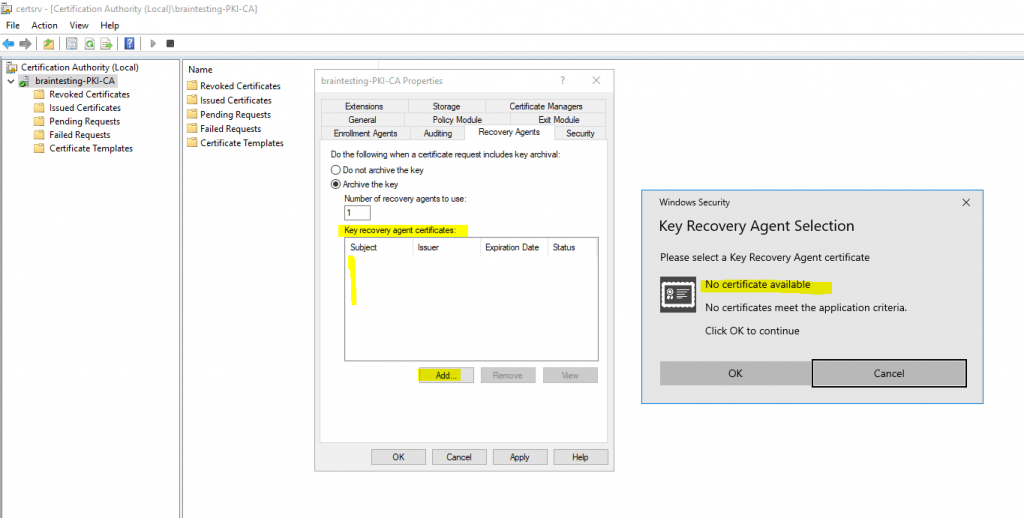
But first I have to request one on the CA server with the logged in user account which is my organization admin (Enterprise Admin).
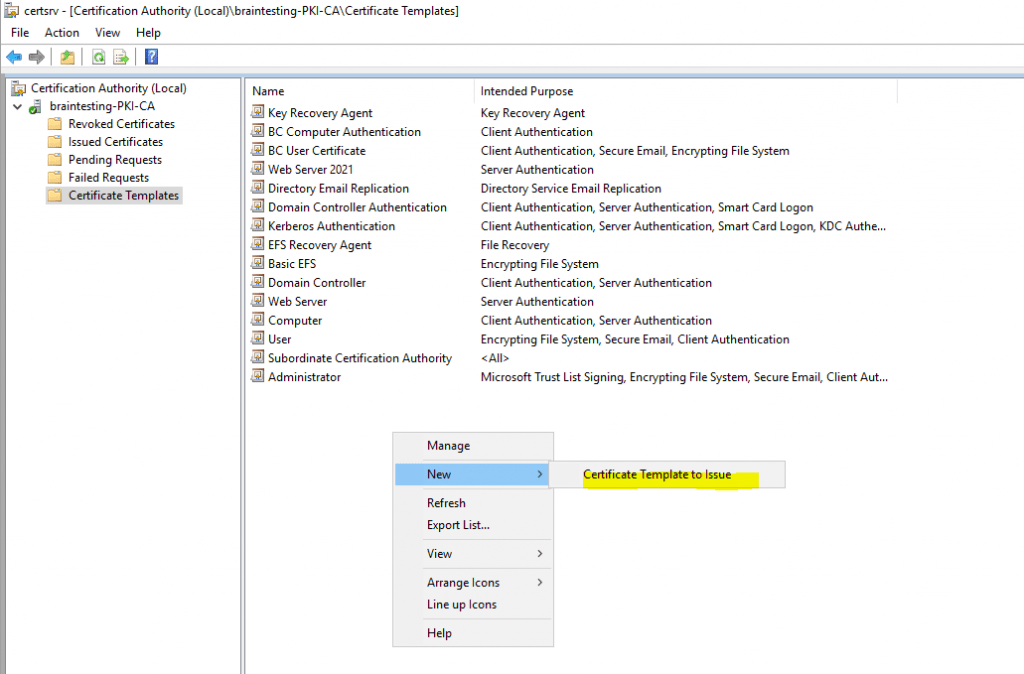
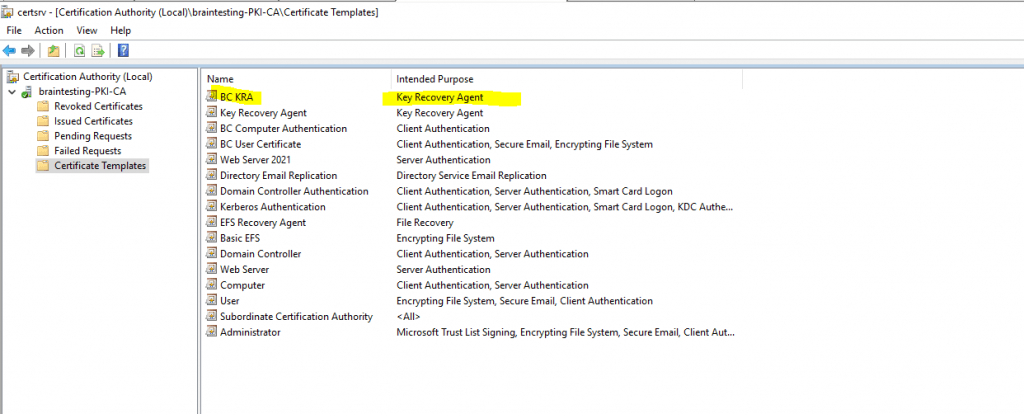
In order to I also first need to issue the certificate template Key Recovery Agent to the CA as follows.
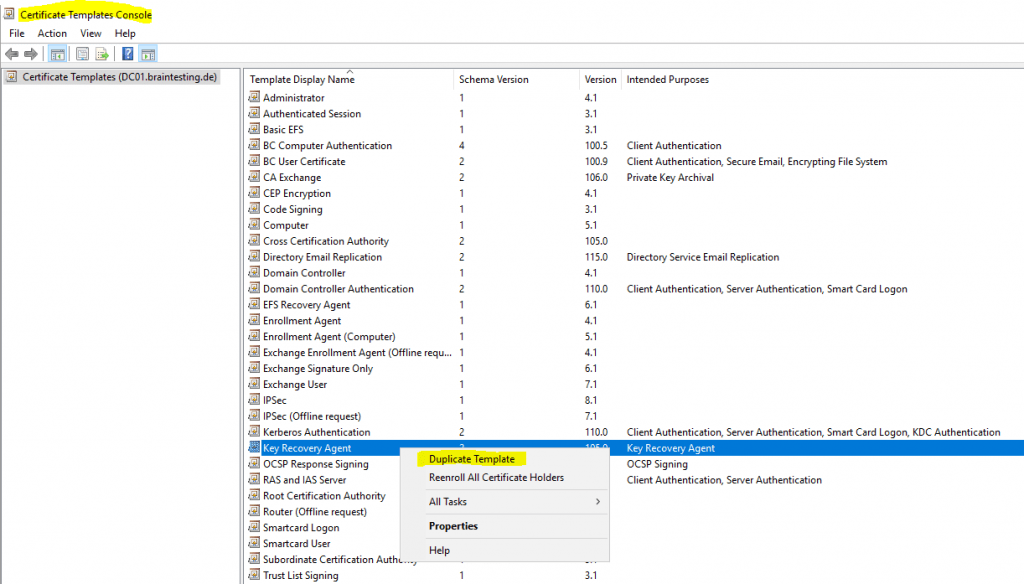
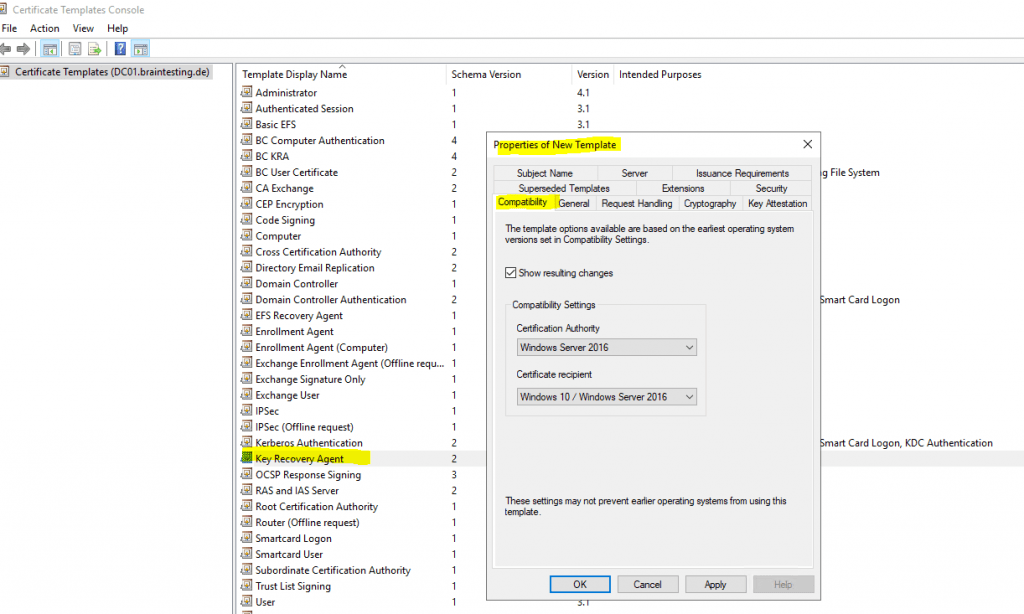
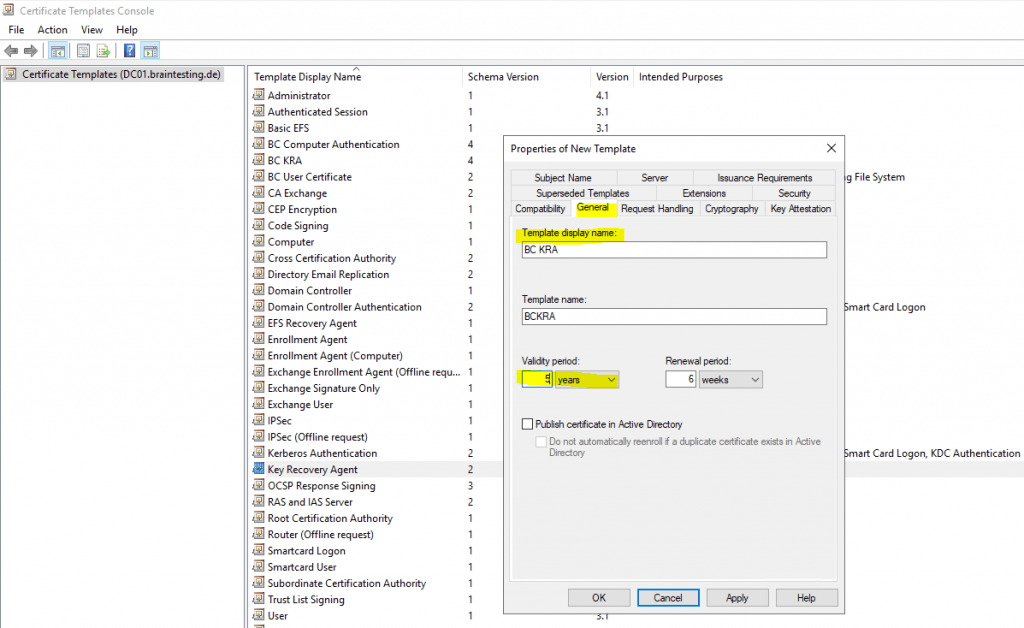
Therefore I will duplicate the default Key Recovery Agent certificate template to change some settings.
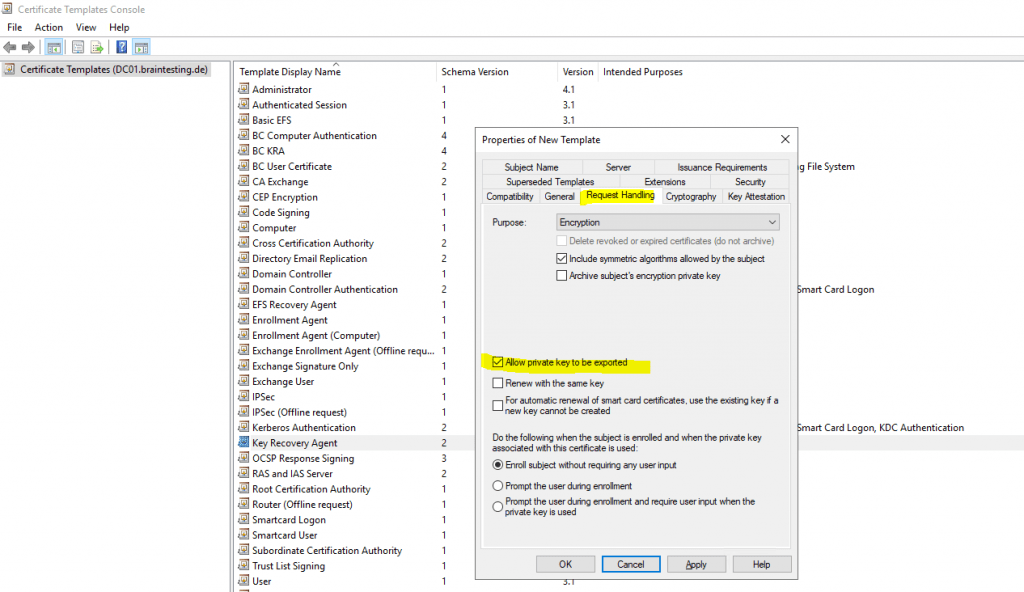
Allow private key to be exported is selected by default.
Disable in the Issuance Requirements tab the checkbox CA certificate manager approval.
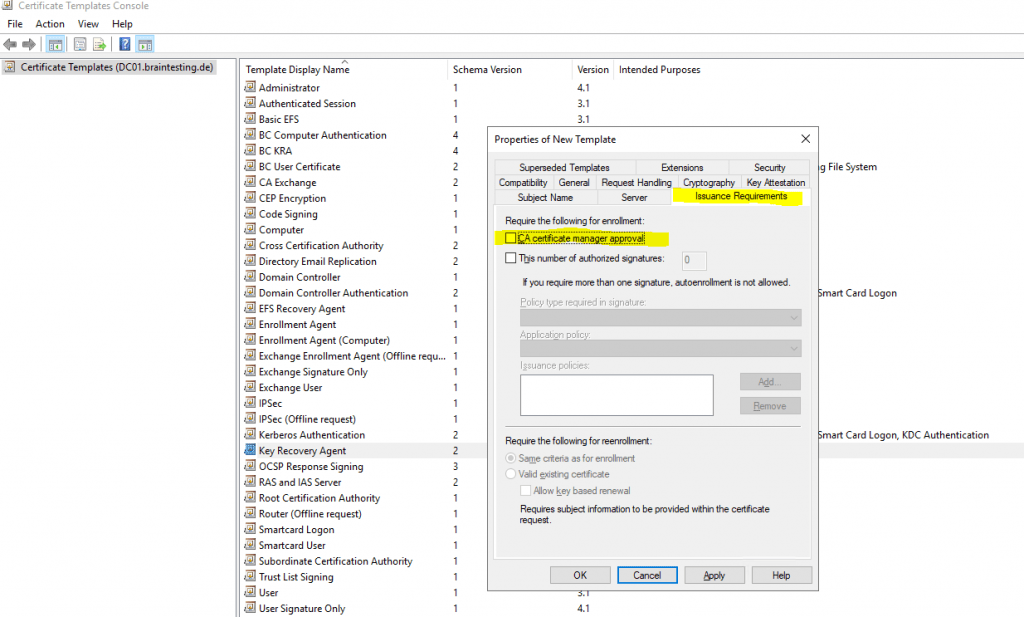
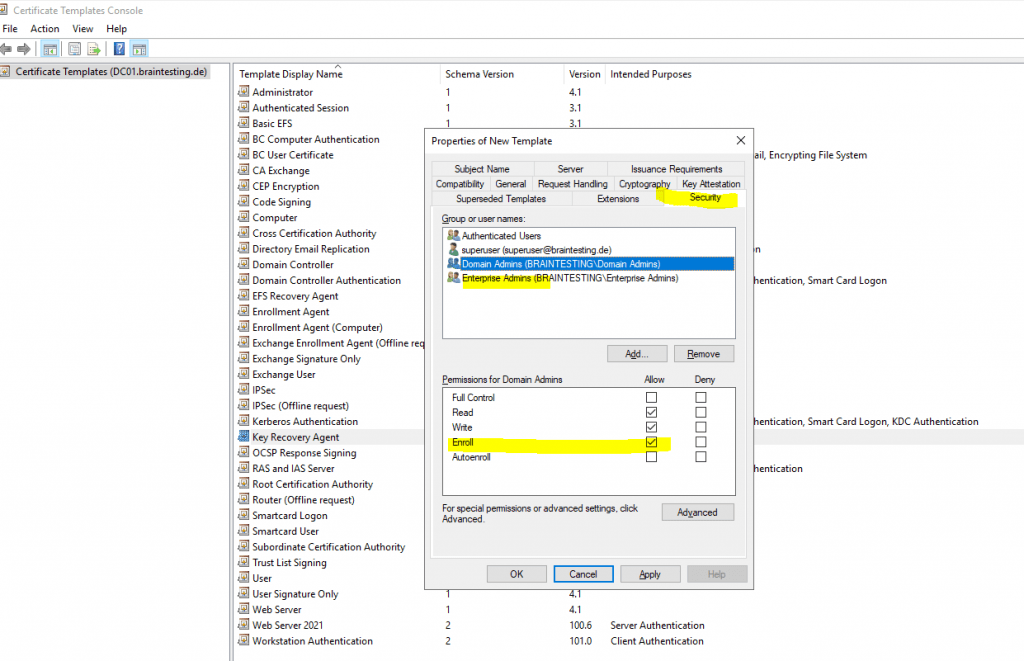
By default the Key Recovery Agent certificate can be enrolled to domain admins and enterprise admins.
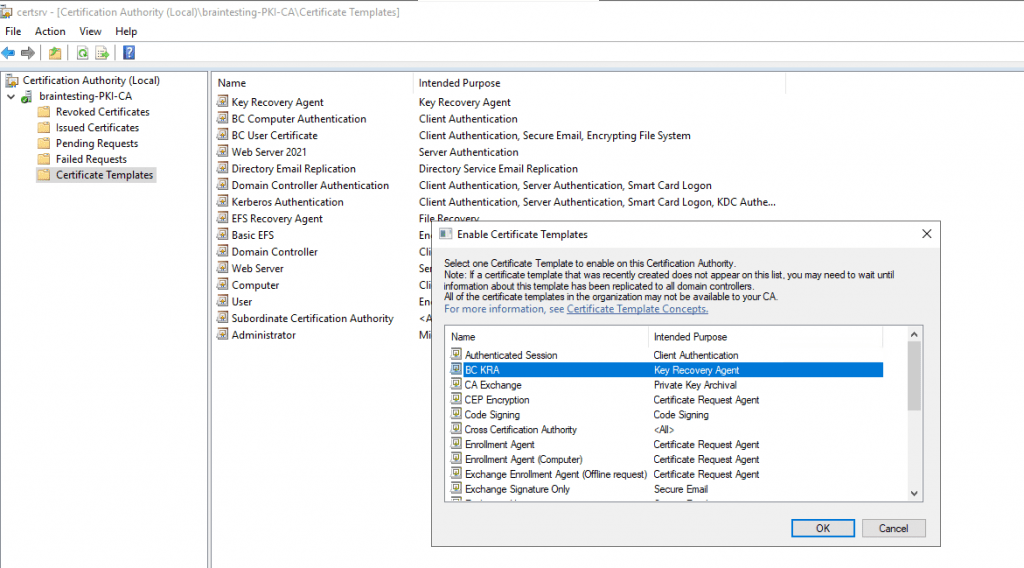
Add the template to your CA.
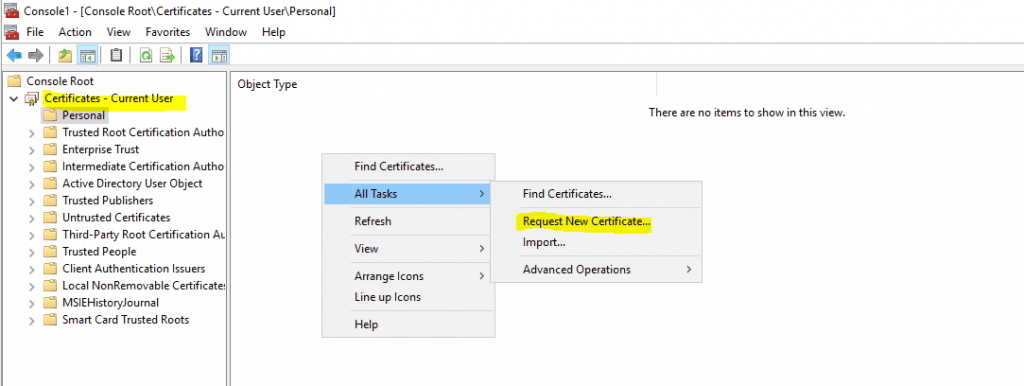
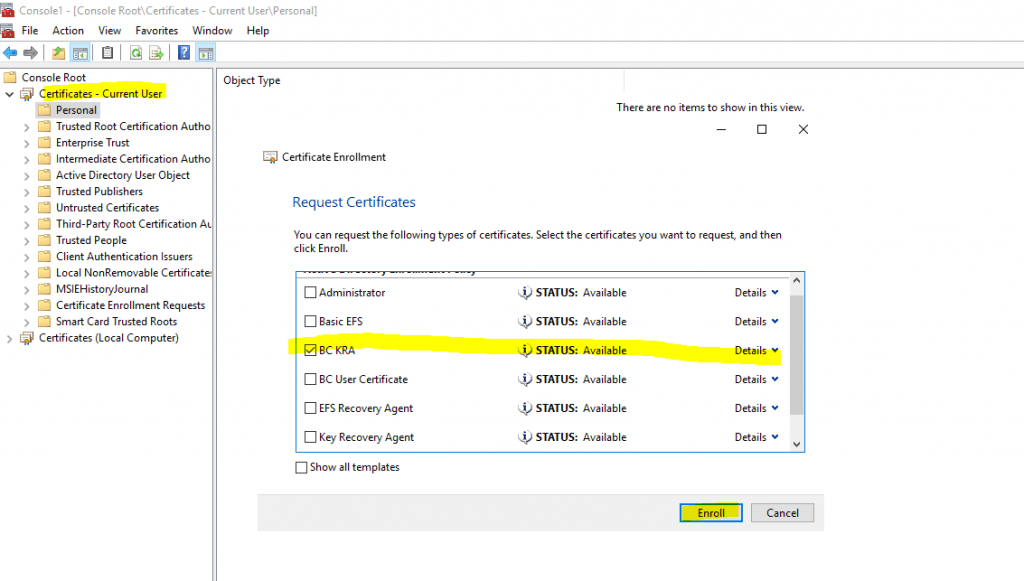
Now I can request a Key Recovery Agent certificate on the CA server and the logged in organization admin (Enterprise Admin) as follow.
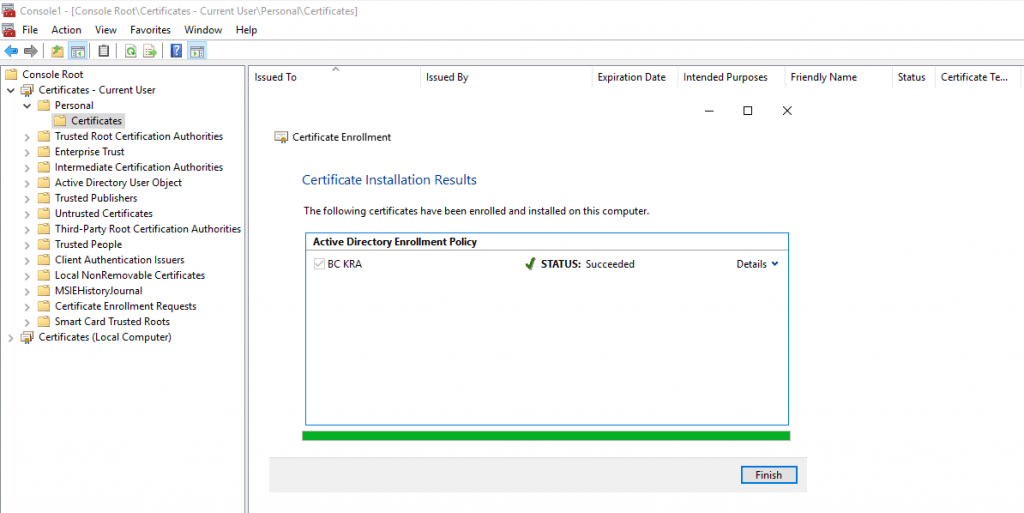
The certificate with the private key is stored in the personal user store.
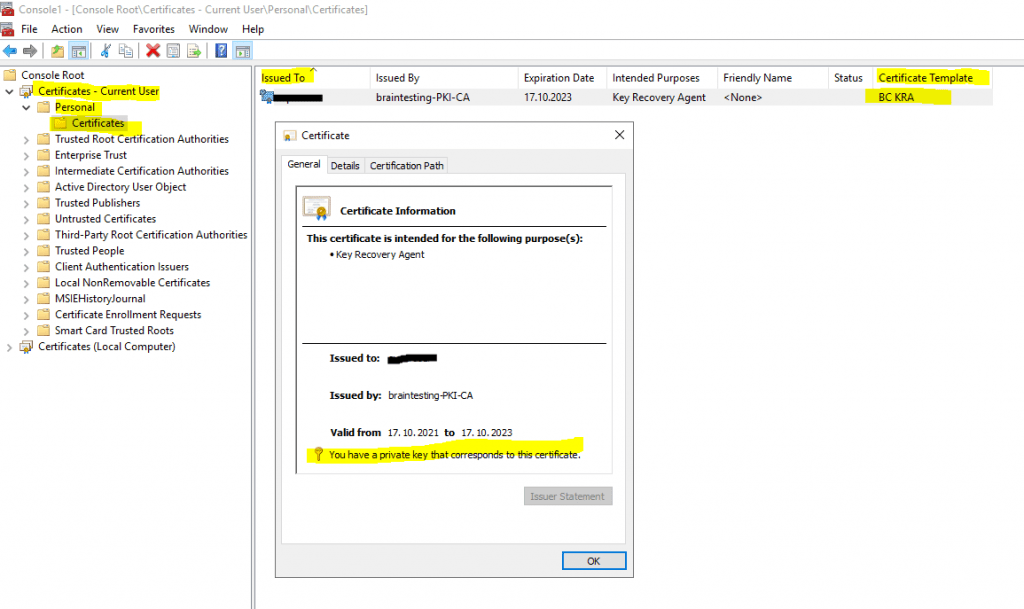
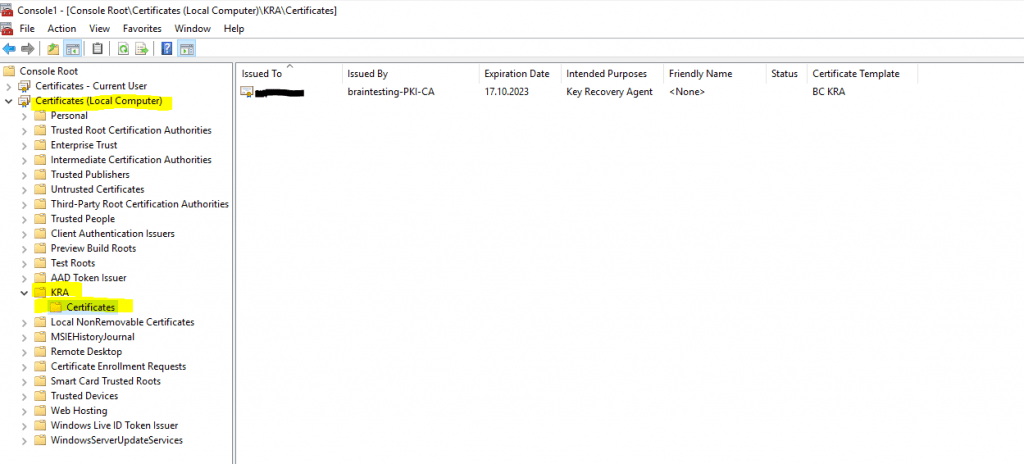
The certificate is also stored in the local computer store under KRA -> Certificates.
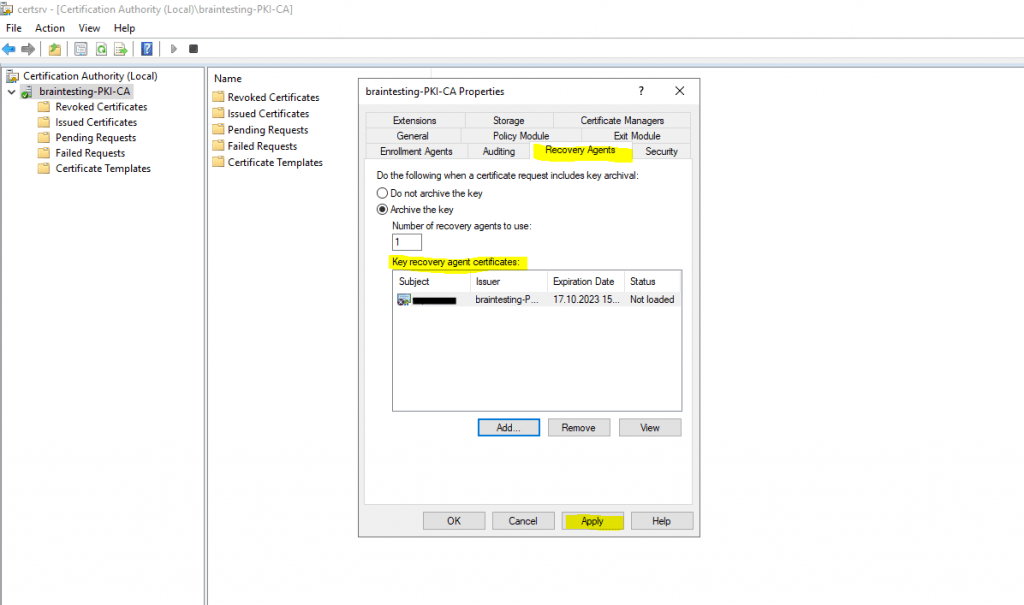
Now I can add the key recovery agent certificate to enable key archival on the CA.
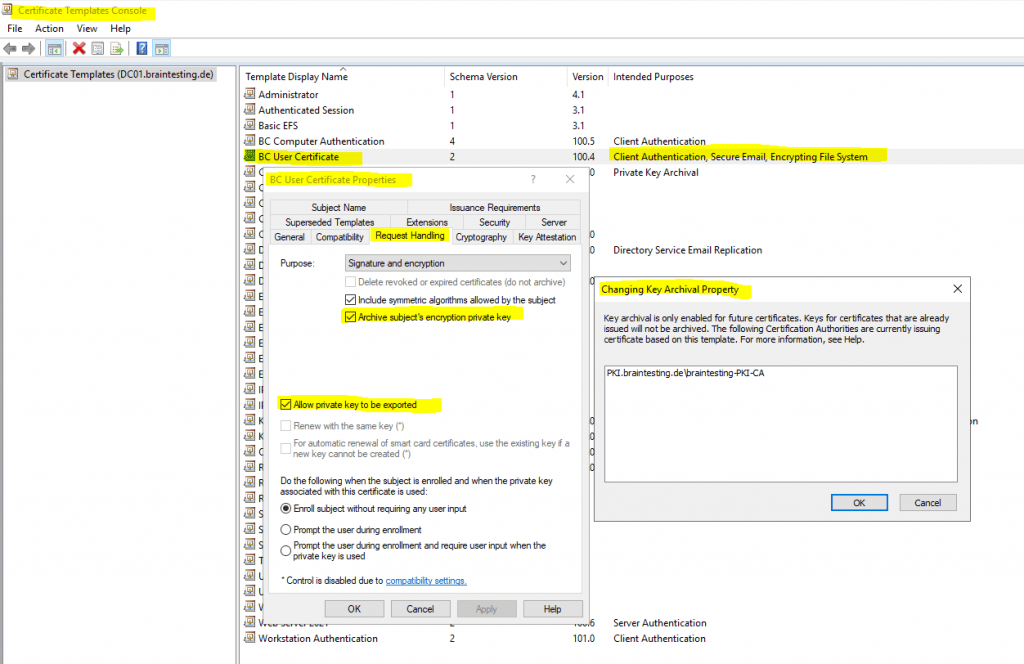
To enable key archival for a certificate you have to check the option Archive subject’s encryption private key in the Request Handling tab of the certificate template.
The checkbox Allow private key to be exported is enabled by default for the user certificate.
In case your CA already issued certificates based on that template, you will get the following information displayed to inform you that key archival is only enabled for future certificates.
Only a CMC request can be used for key archival. CMC requests are represented by the IX509CertificateRequestCmc interface.
Only the Certificate Management Messages over CMS (CMC) request format allows for securely transferring the requester’s private key to the CA for key archival.
Source: https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/certreq_1
Key Recovery
Key recovery is not directly supported by Active Directory Certificate Services or the Certificate Enrollment API. Microsoft does, however, provide the following applications to help with the process:
- Certutil.exe is a command line program that can be used to retrieve CA configuration information, verify certificates, key pairs, and certificate chains, and back up and restore keys. It is included in server operating systems beginning with Windows Server 2003.
- Krecover.exe is a dialog box–based program that enables key recovery. It is included with the Resource Kit beginning with Windows Server 2003.
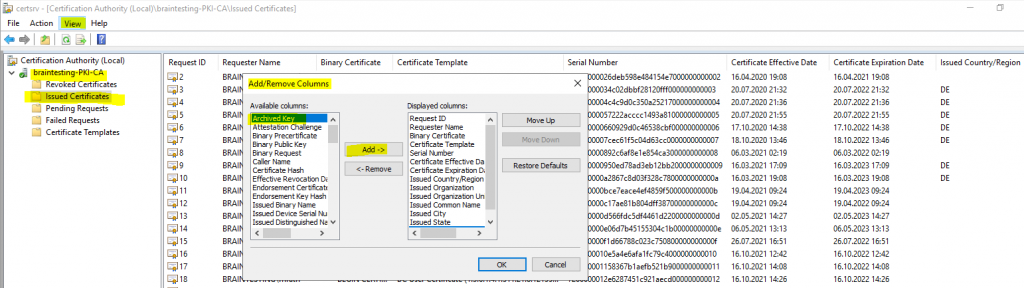
To determine if the private key is archived you can go to the Issued Certificates in your CA and add the Archived Key column to the list.
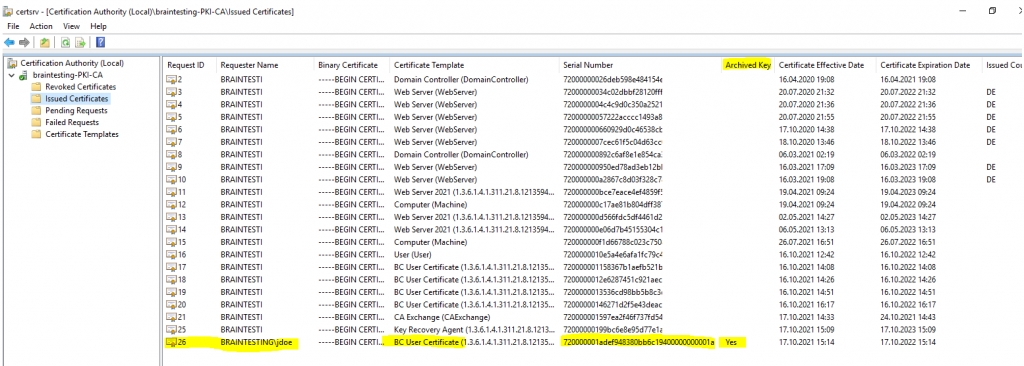
When the private key has been archived it can be recovered by the user who has the key recovery agent certificate. In order to recover the private key you first need to determine the serial number of the certificate you want to recover the private key for.
If you published the certificate in Active Directory you can easily determine the serial number from the user account as follows.
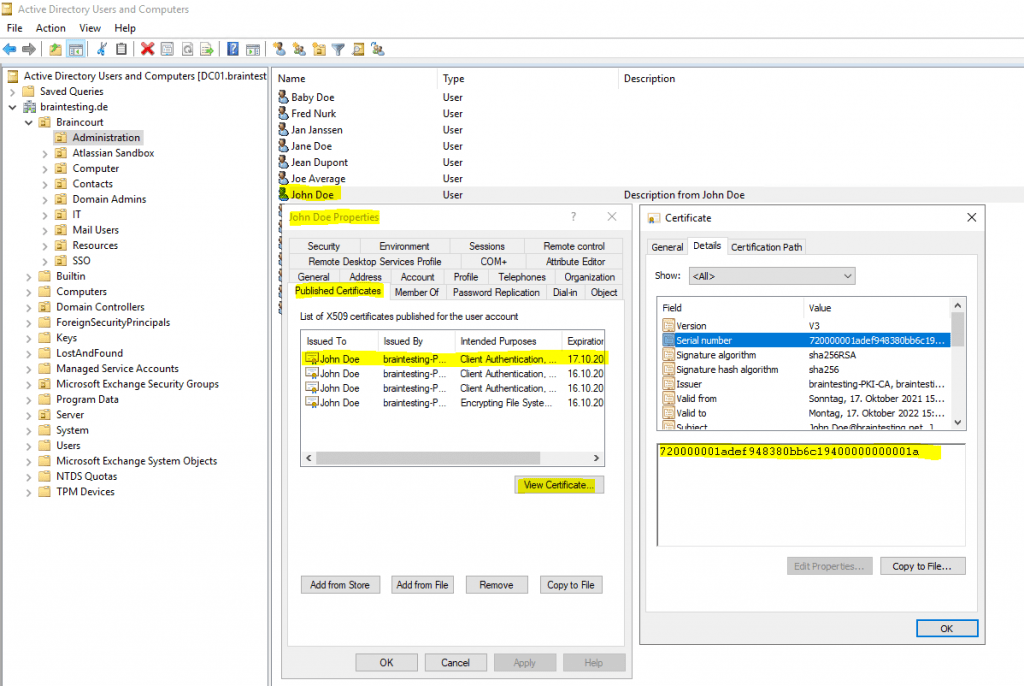
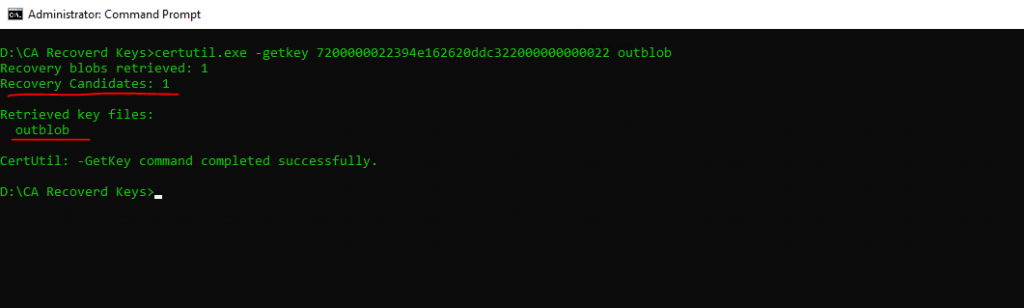
Now the user with the recovery agent certificate needs to execute the following command on the CA server.
certutil.exe -getkey <SearchToken> outblob
# SearchToken -> Can be the common name, serial number, thumbprint, UPN (user@domain), Requester Name (domainuser)
This command will creates a BLOB of the certificate from which we can extract in step 2 the private key to a password protected pfx file.
To extract the private key from the BLOB file execute the following command.
certutil.exe -recoverkey recoveryBlob jdoe.pfx
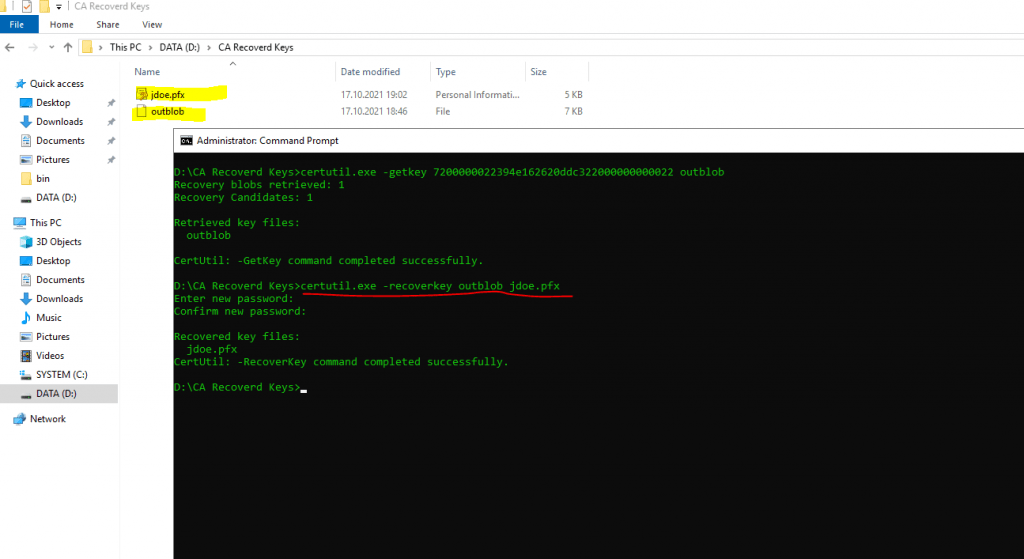
The output will be a pfx file which contains the public and private key of the certificate. Therefore you need to provide a password during the extraction from the BLOB into the pfx file.
Troubleshooting
In case you request a certificate for which key archival is enabled and you get the following error message, in most cases the Archive the key option for the CA is not enabled.
Cannot archive private key. The certification authority is not configured for key archival. 0x8009400a (-2146877430 CERTSRV_E_KEY_ARCHIVAL_NOT_CONFIGURED)
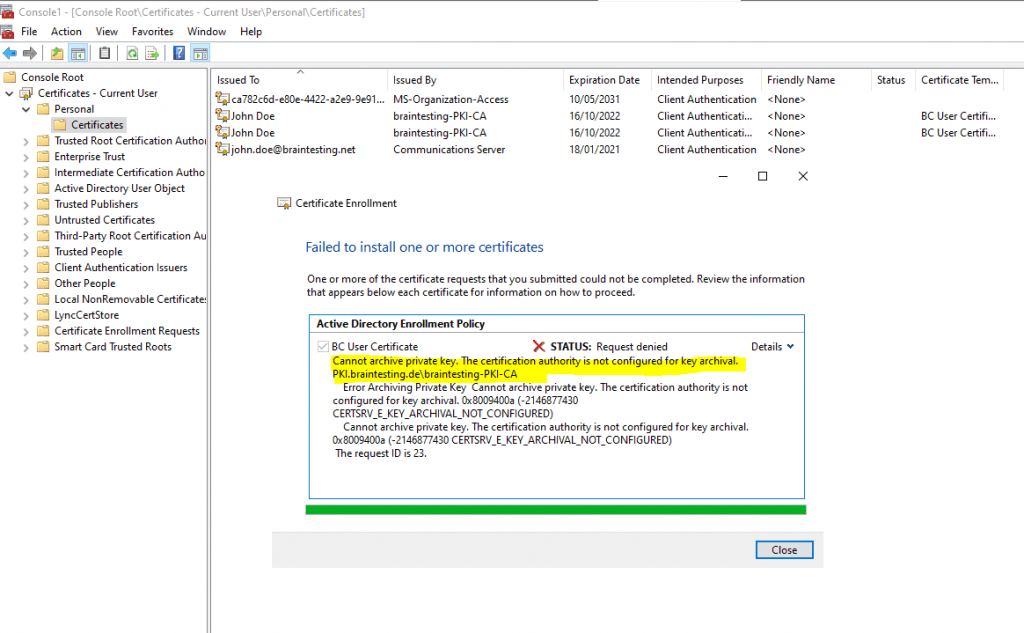
You have to enable the Archive the key option for the CA.
Links
Key Recovery Server
https://docs.microsoft.com/en-us/windows/win32/seccertenroll/about-key-recovery-serverEnabling Key Archival in a Certificate Template
https://www.serverbrain.org/certificate-security-2003/enabling-key-archival-in-a-certificate-template.html
Enabling a CA for Key Archival
https://www.serverbrain.org/certificate-security-2003/enabling-a-ca-for-key-archival.html
Understanding Cryptographic Providers
https://docs.microsoft.com/en-us/windows/win32/seccertenroll/understanding-cryptographic-providers
Archiving and recovering (export) private key in Active Directory Certification Services (ADCS)
https://b-blog.info/en/archiving-and-recovering-private-key-in-microsoft-certificate-authority.html



