Configure certificate auto-enrollment
In this post I want to show how to configure certificate auto-enrollment. This topic is well documented from Microsoft.
I will use certificate auto-enrollment among other things to deploy computer certificates to all computers in the network, they should be able to process computer authentication against a RADIUS server (NPS server role), in order to establish a wireless network connection through a wireless access point.
You can also use certificate auto-enrollment for your internal servers like web servers, RD Web Access, RD Gateway, WSUS and more. This will prevent services from being offline due to expired certificates.
About how to set up a RADIUS server on Windows for 802.11 Wireless networks you can read my following post.
In this post above I will apply a wireless network (IEEE 802.11) group policy to a organizational unit (OU) which includes all computer accounts they should be able to authenticate to the RADIUS server (NPS server role).
For the Authentication Mode I selected User or Computer authentication.
Computers need a computer certificate in order to be able to authenticate itself against a NPS server.
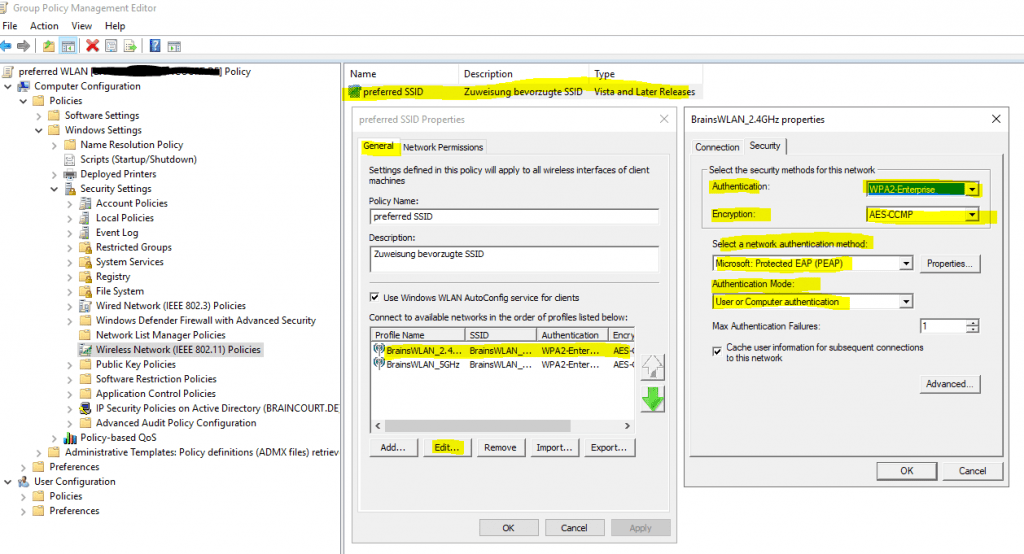
In order to deploy those computer certificates automatically to all computers homed in that mentioned OU, I need to create a certificate template for Client Authentication and enroll the certificate to all computers in this OU.
Further I need to apply an additional group policy or modify the above in the figure to automatically enroll this certificate to the computers.
Configure server certificate auto-enrollment
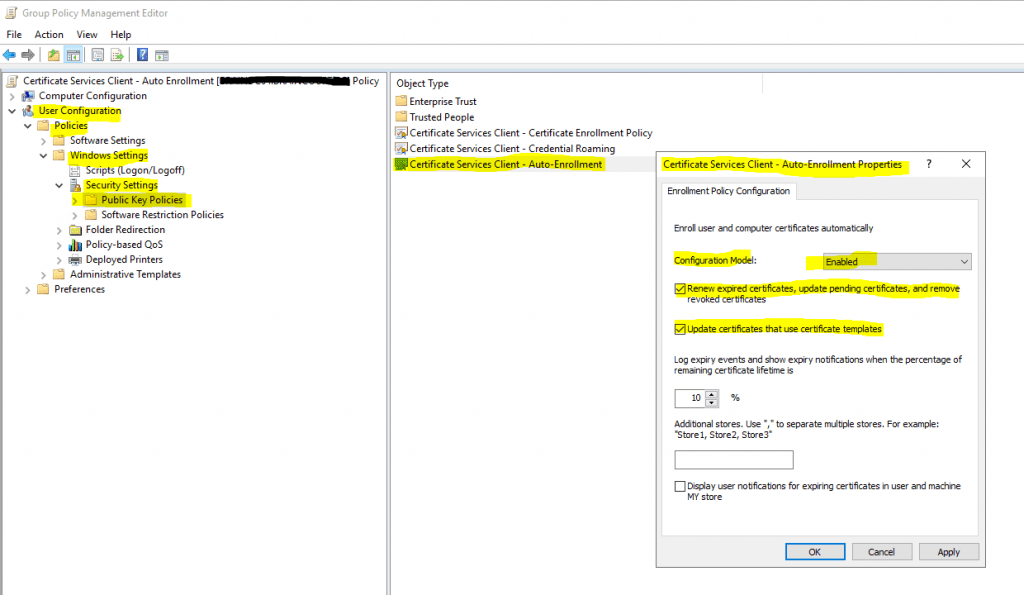
To automatically enroll computer certificates you need to enable the Certificate Services Client – Auto Enrollment policy as follows.
Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Public Key Policies – > Certificate Services Client – Auto Enrollment policy
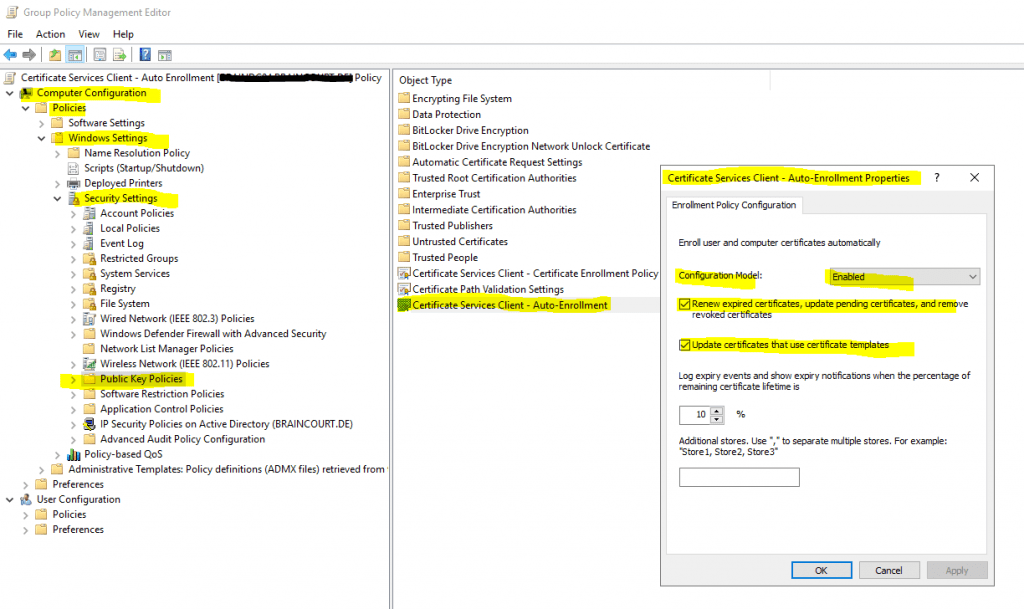
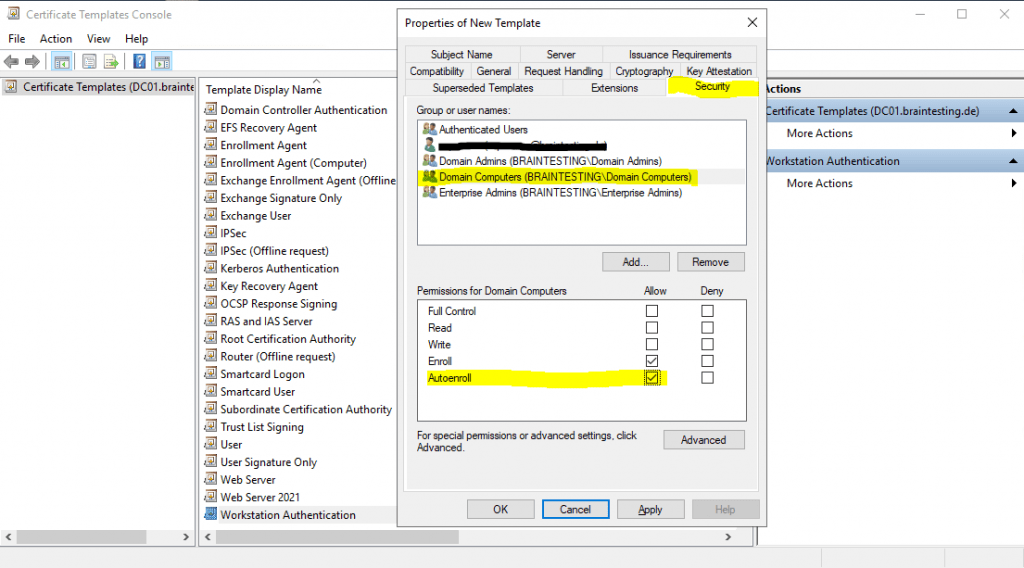
This policy will force computers to autoenroll all published certificates in the forest they had the following ACL permissions set with Autoenroll.
Domain Computers -> Autoenroll
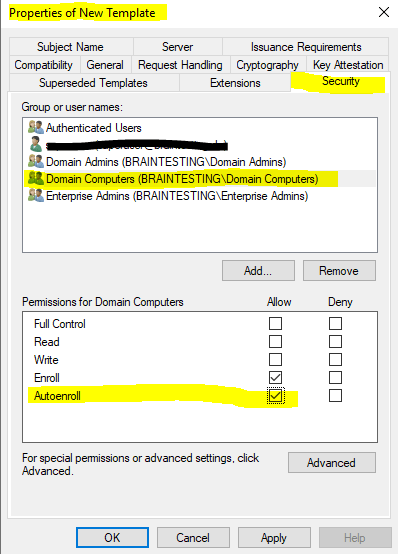
Therefore we also need to create a new certificate template based on an existing template and then adjust some settings we need for.
To create a new certificate template right click on Certificate Templates and then click on Manage inside your Certification Authority console as follows.
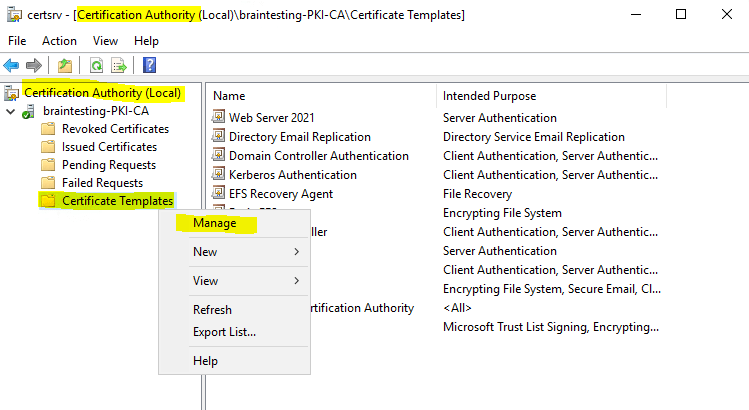
After that the Certificate Templates Console will be opened. Here will be listed all certificate templates from your forest.
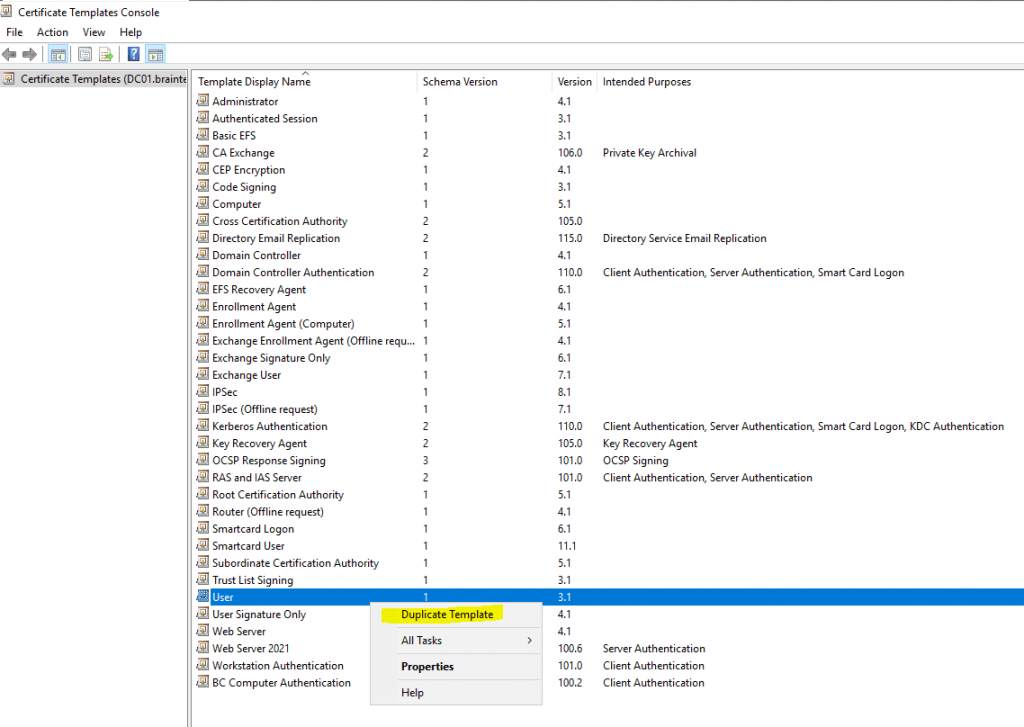
To create a new certificate template right click on an existing default template and select Duplicate Template as follows.
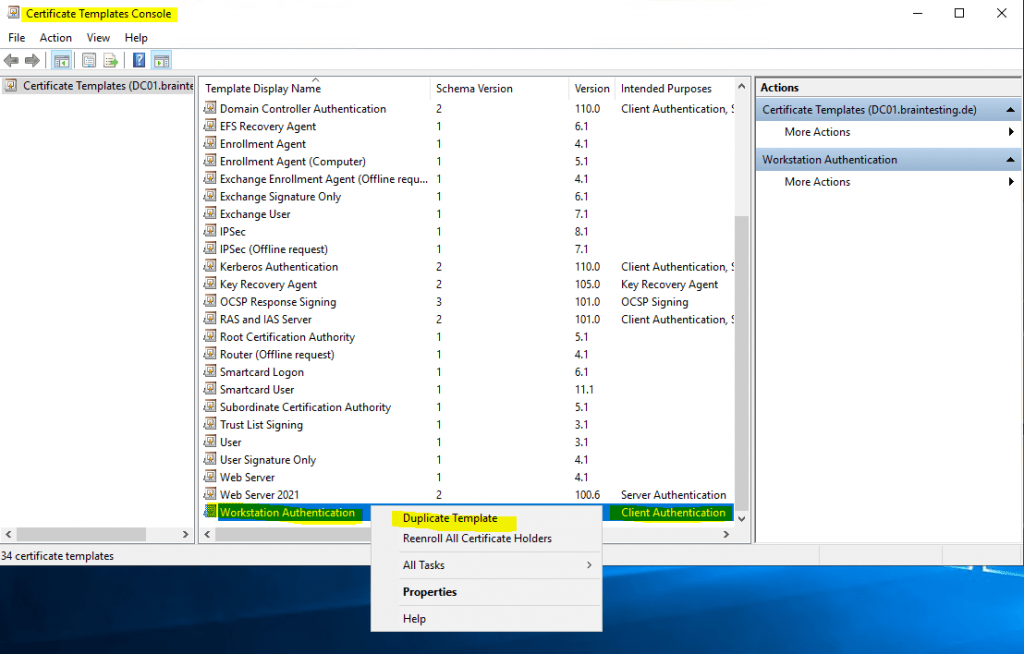
For computer authentication I will use the default Workstation Authentication template which provides client authentication, you can also use the Computer template for this purpose which will further provide server authentication.
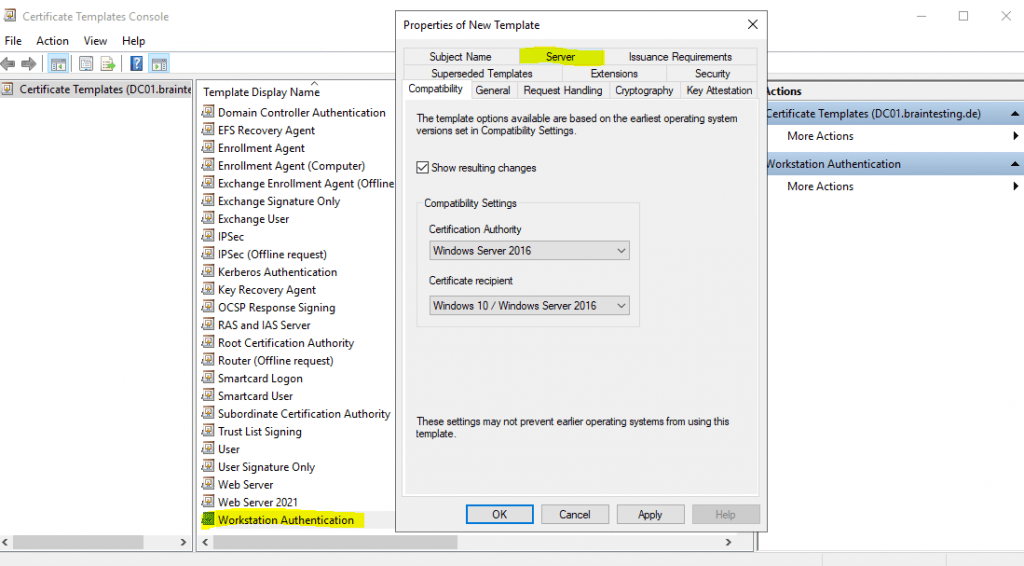
For the NPS server itself I will need to use a computer certificate in contrast so that clients can verify the identity of the NPS server.
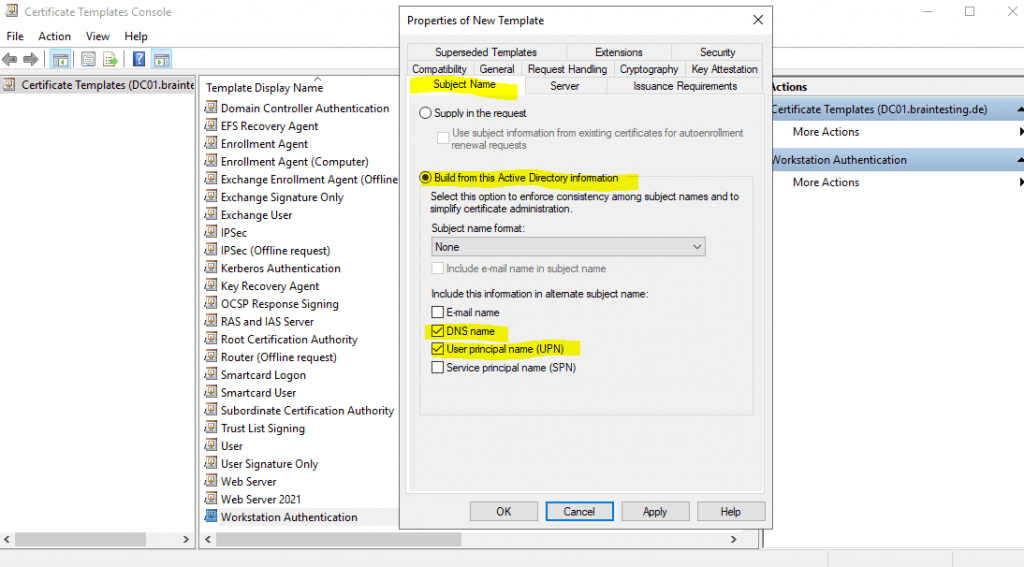
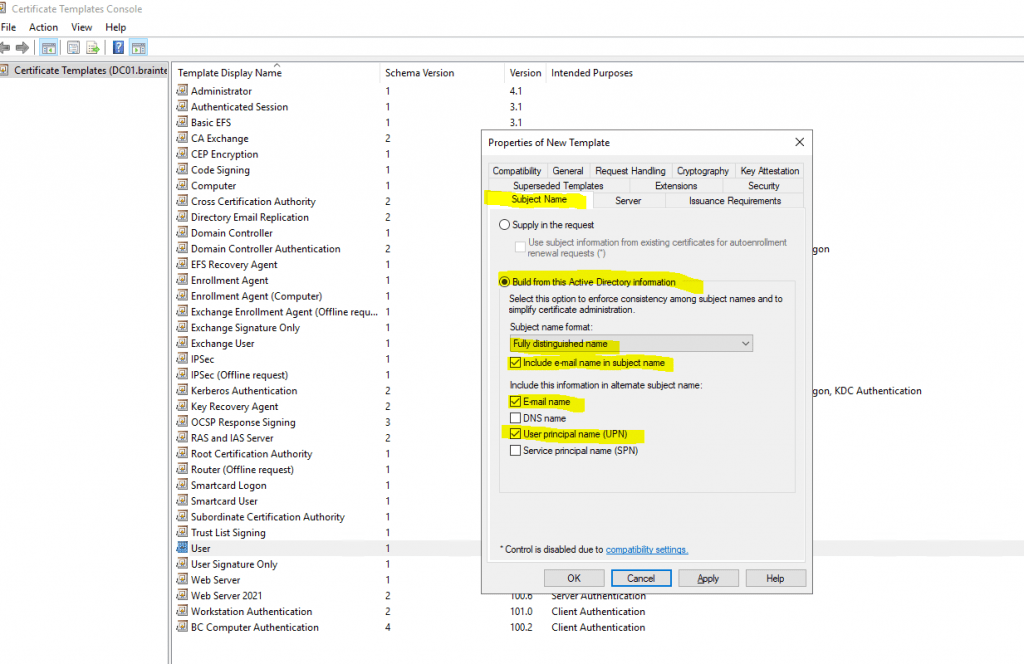
In the Subject Name tab I will check DNS name and User principal name (UPN) to be included in the certificate and build form Active Directory selected.
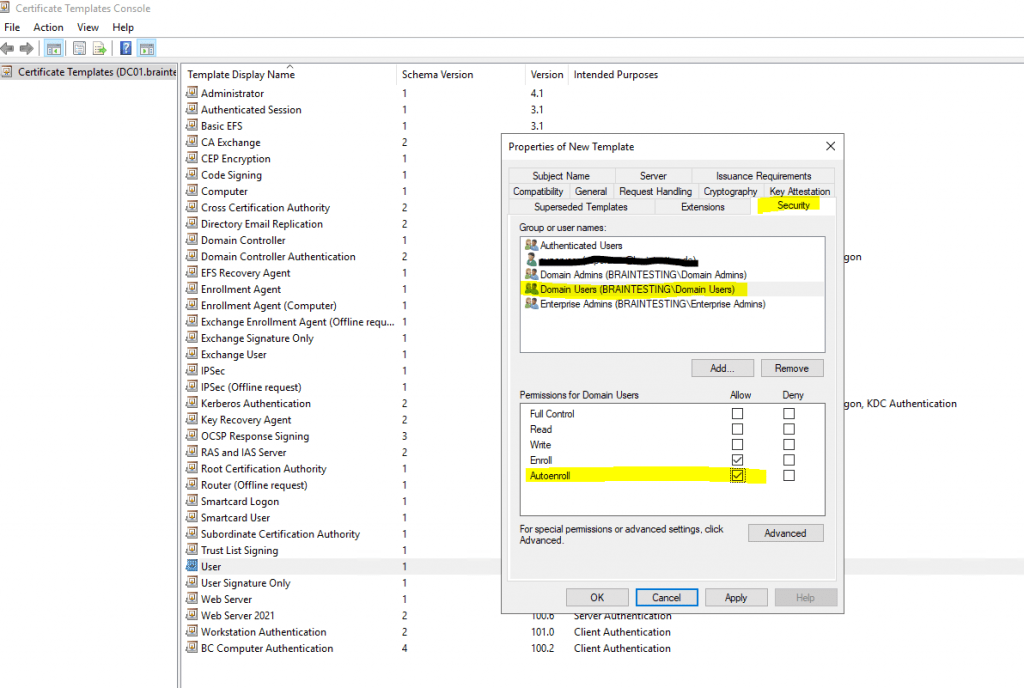
And as mentioned further above to be able to enroll this certificate automatically by using a group policy as shown below, we need to check Autoenroll in the Security tab for the Domain Computers security group as follow.
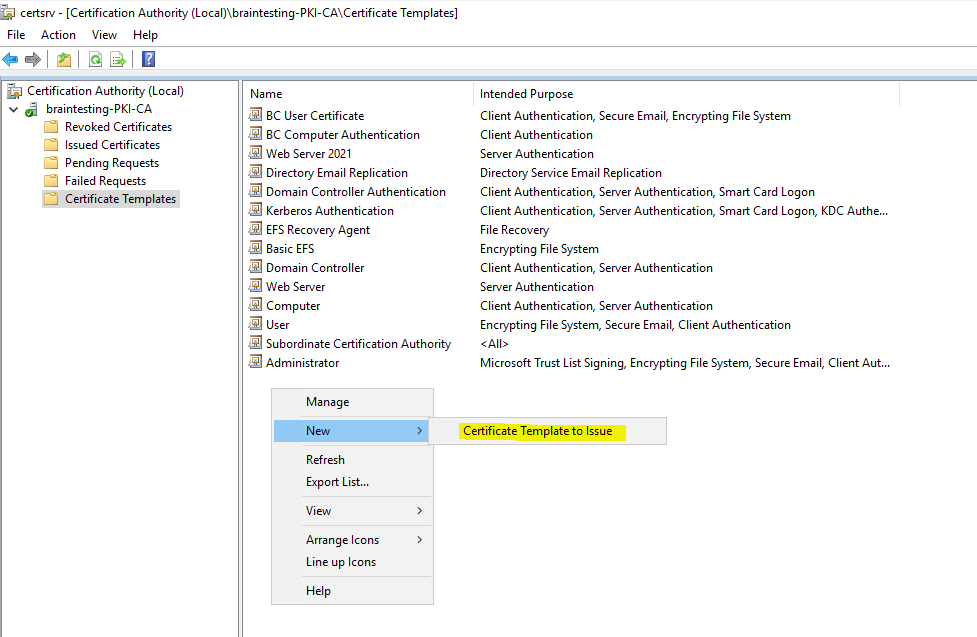
Finally you need to activate and issue this template in your PKI by right click inside your Certification Authority console, select new and click on Certificate Template to Issue as follow.
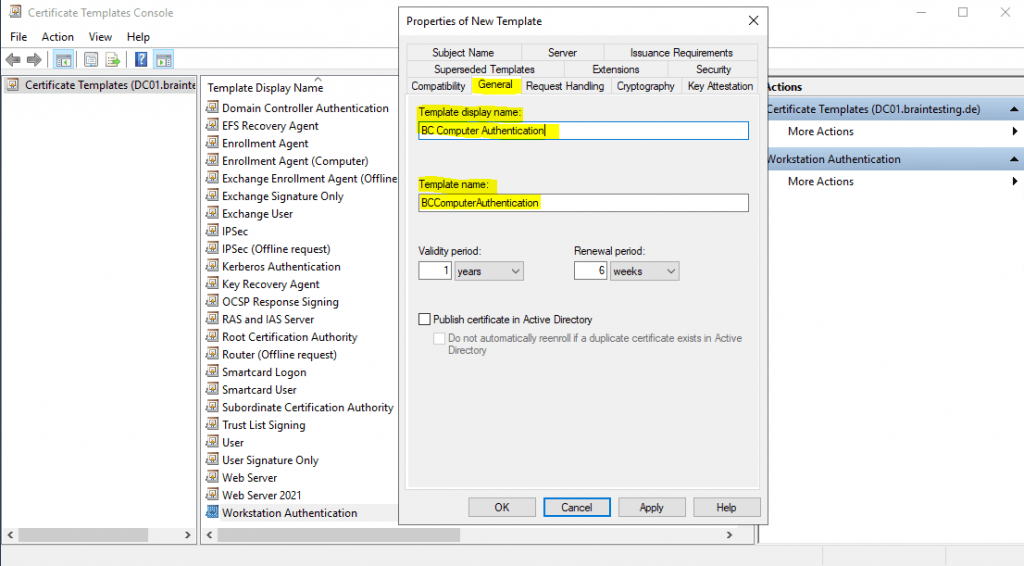
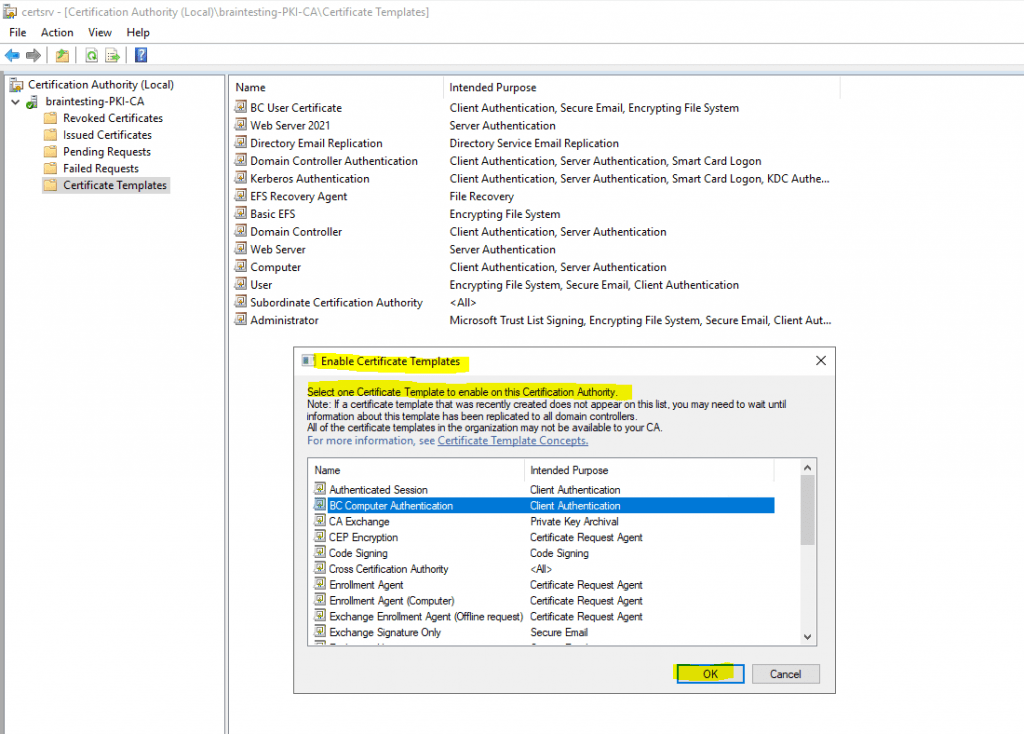
Select the created template, in my case the Workstation Authentication template named BC Computer Authentication and click on OK to enable it on your Certification Authority (PKI).
Configure user certificate auto-enrollment
To automatically enroll user certificates you also need to enable the Certificate Services Client – Auto Enrollment policy but this time of course in the User Configuration section as follow.
This time you need to apply that group policy to an OU where the user accounts reside, you want to deploy the user certificates.
User Configuration -> Policies -> Windows Settings -> Security Settings -> Public Key Policies – > Certificate Services Client – Auto Enrollment policy
This policy will force to autoenroll all published certificates in the forest they had the following ACL permissions set as mentioned.
Domain Users -> Autoenroll
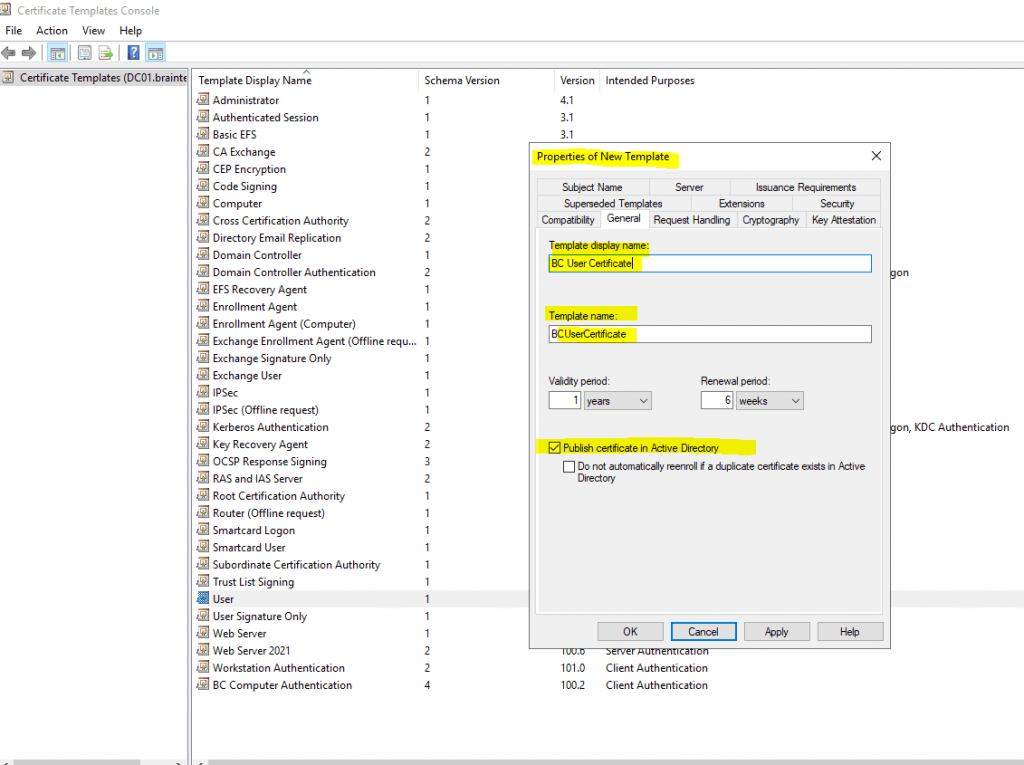
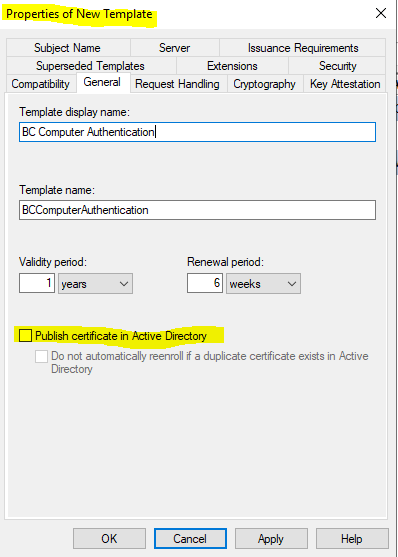
By default the user certificate template has enabled the Publish certificate in Active Directory option, I will disable it.
Keep in mind what this option means exactly, I will refer to below in the next section!
In the Subject Name tab we do not have to change anything and this settings are by default for the user certificate template.
Here we need to check Autoenroll for the Domain Users group in order to automatically issue user certificates to the user’s in the OU we applied our policy.
Finally I will have an User and a Workstation Authentication certificate which I can use for auto-enrollment through group policies.
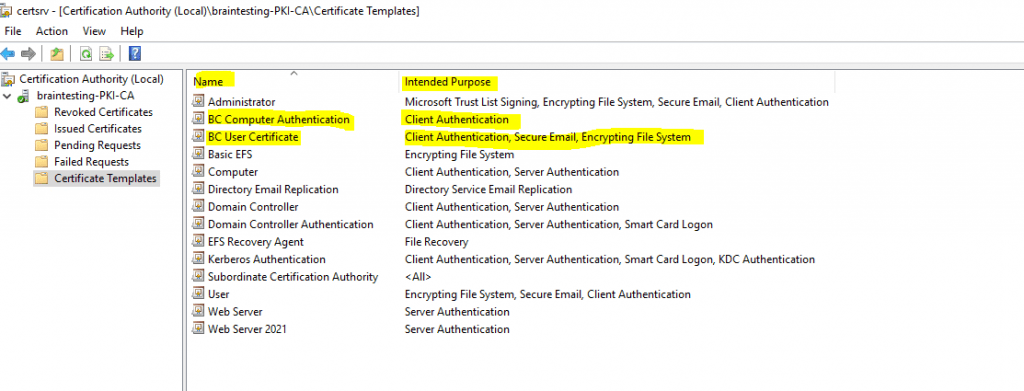
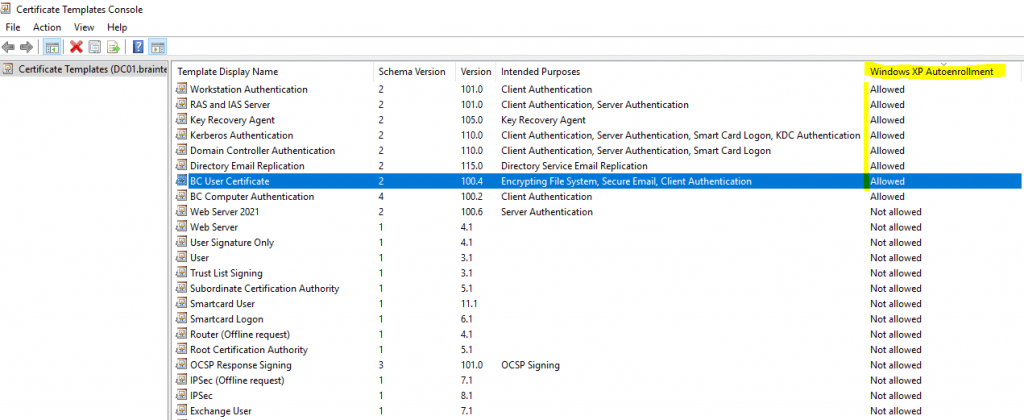
You can use the Certficate Templates Console to get an overview which certificates are enabled for Autoenrollment.
Publish certificate in Active Directory
The checkbox Publish certificate in Active Directory in the certificate templates in the General tab as show in the figure below, publishes the resulting certificate to the userCertificate attribute of the user or computer object in Active Directory depending on whether the template is a user or computer template.
Certificates published in Active Directory makes them available to other Active Directory users and to Active Directory-aware applications and services like:
- Outlook to find an internal recipients S/MIME certificate to encrypt messages for it
- Certificate-based authentication against Active Directory Domain Controller
- Published encryption certificates to manage encrypted content
Be careful by checking this option for certificates and enabled auto-enrollment!
If you have user’s they logon to several computers, each of these computers will request a user certificate for this user. Finally the user had a bunch of user certificates stored in its active directory user account which can all be used for S/MIME (Secure/Multipurpose Internet Mail Extensions) encryption.As each certificate have an associated private key which will only exists on the requested computer for the certificate, user’s can run into issues when the sender used one of these multiple certificates stored in the recipients active directory user account and the recipient itself tries to open the encrypted message on a computer with a different certificate an its associated private key stored on that computer.
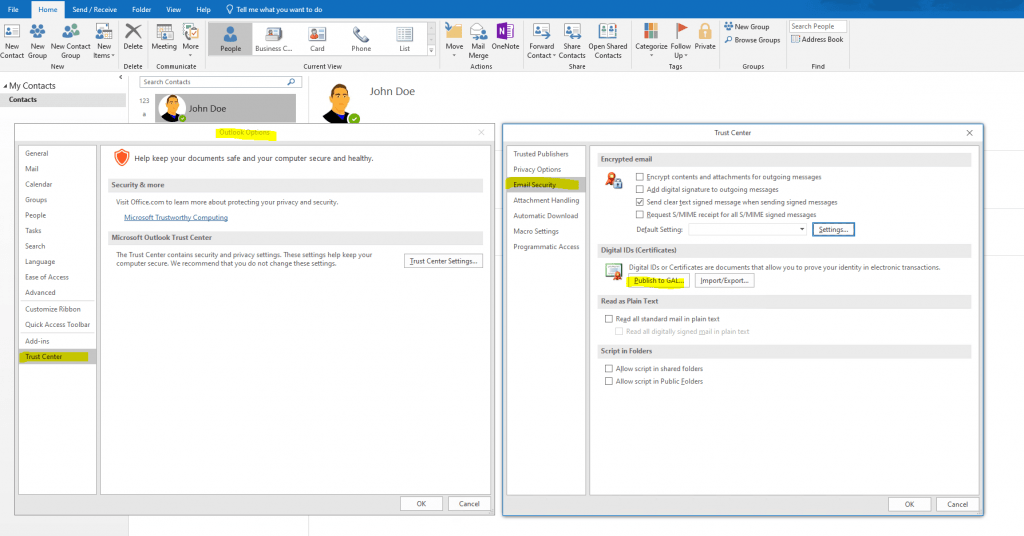
If a user searches the global address list (GAL) for the recipient it want to send an encrypted mail, it first needs to add the contact from the GAL to its local contacts.
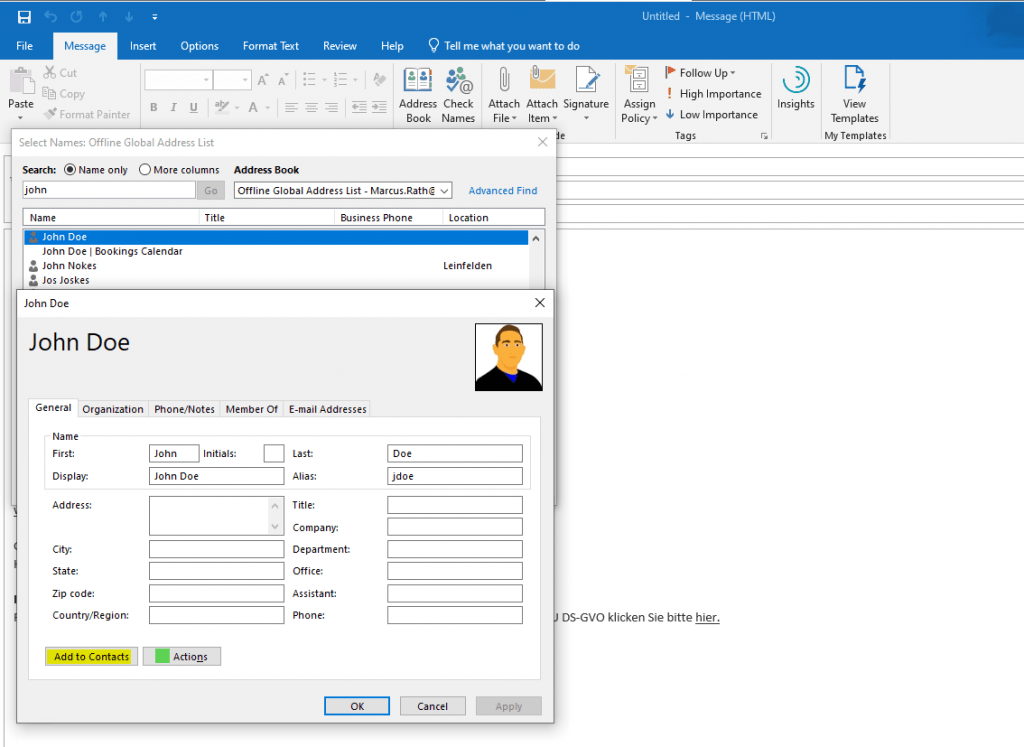
By adding the contact from the GAL, Outlook will receive the public key from the recipients user certificate which is needed to encrypt mails to the recipient.
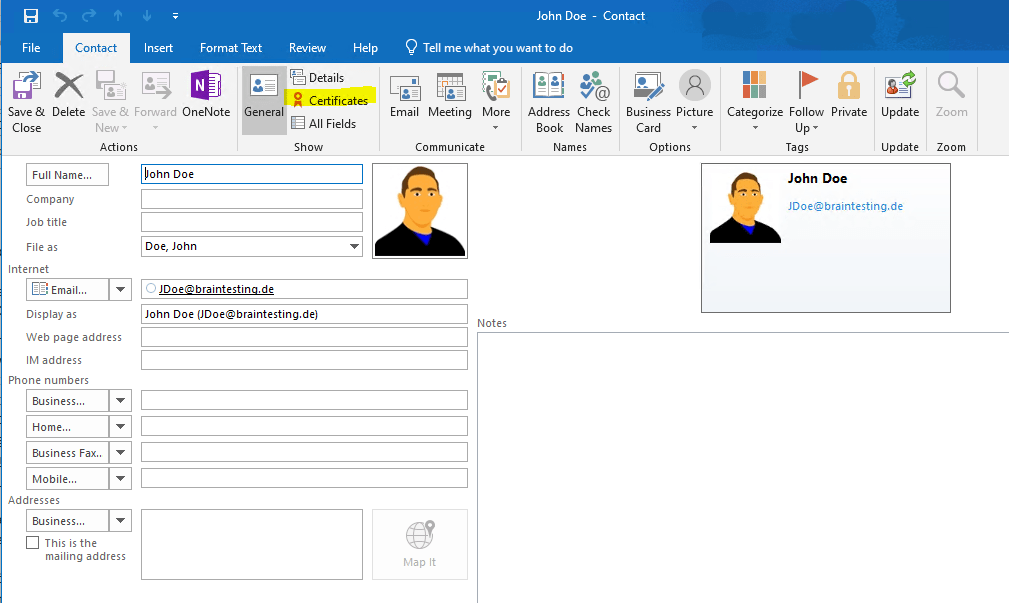
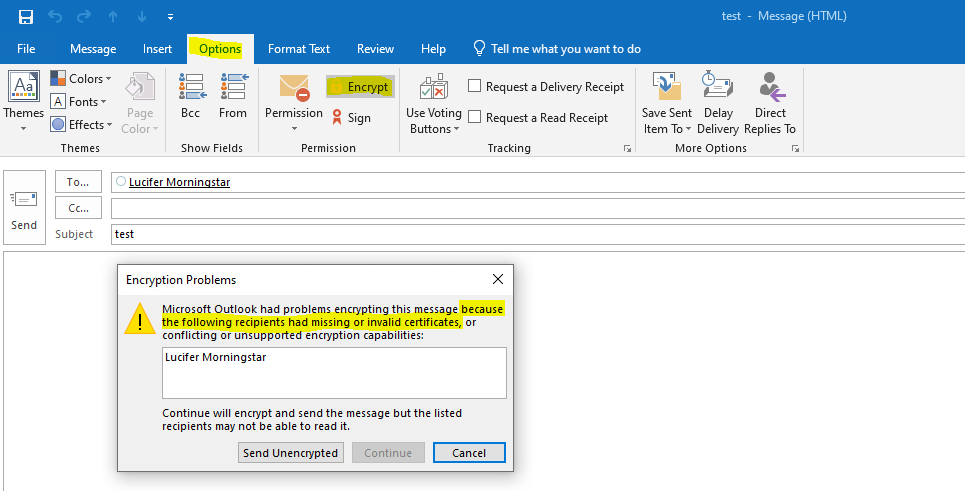
If you just select the recipient from the GAL without adding first to your local contacts, Outlook won’t have access to the public key from the recipient and will response with the following message.
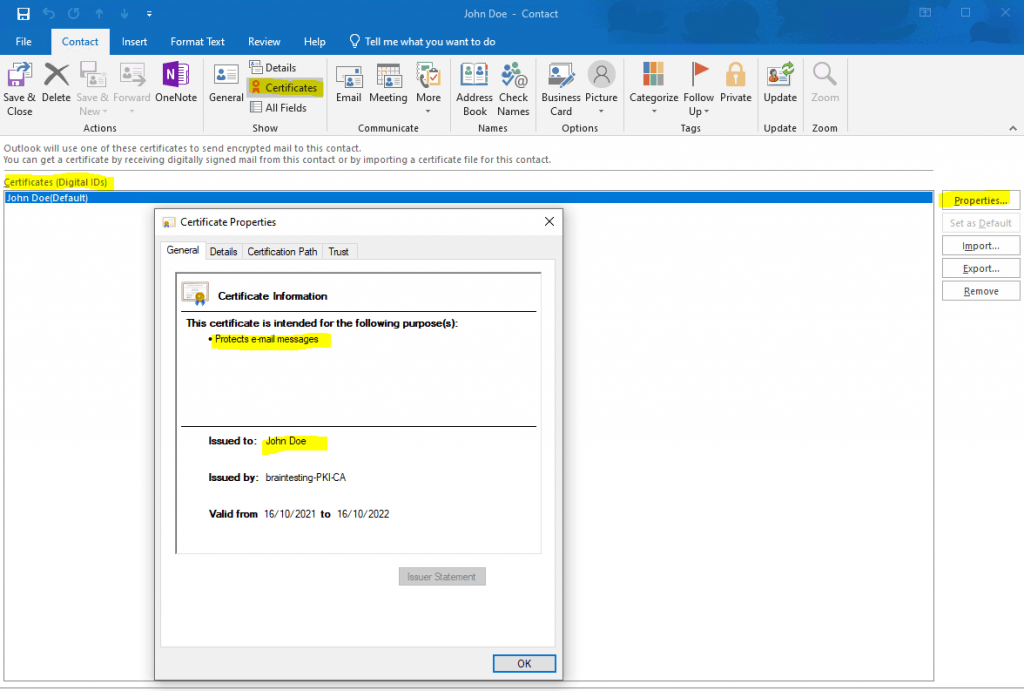
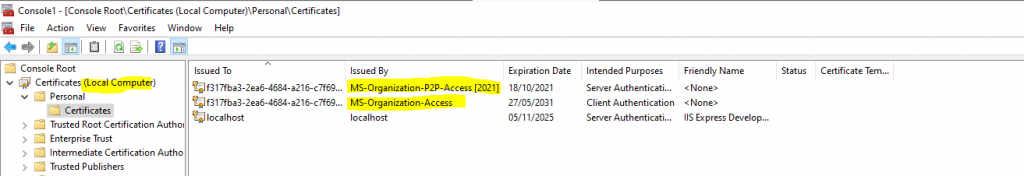
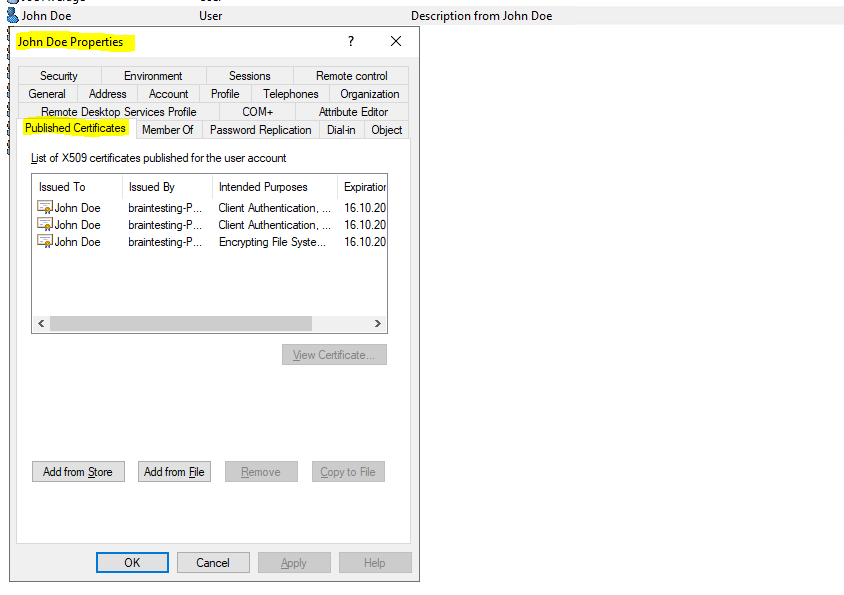
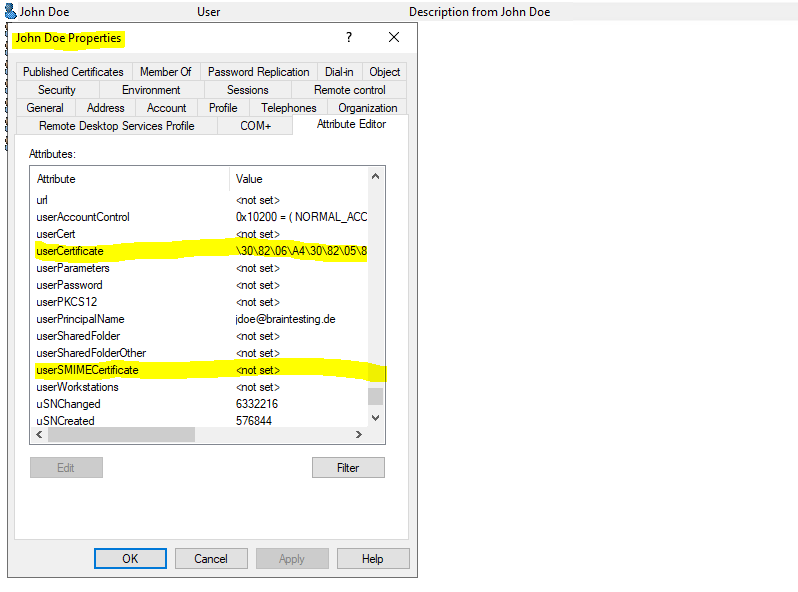
Here you will see the published certificates in Active Directory for a computer and an user object.
Only the public key will be stored in Active Directory
userCertificate attribute from computer object which is actually a computer certificate.
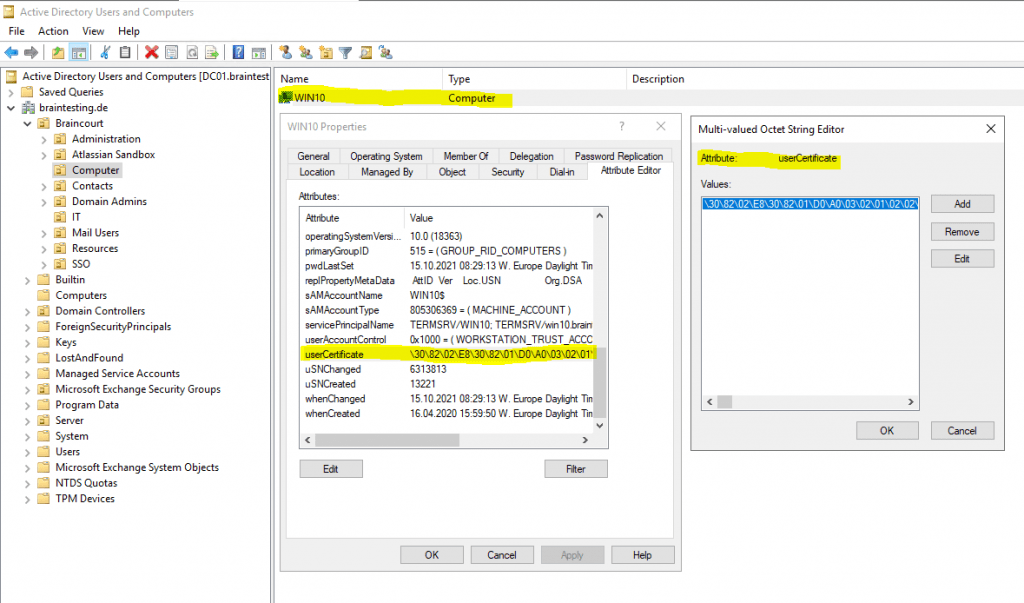
The computer certificate in the figure above wasn’t issued in my case from the internal PKI during the certificate auto-enrollment process.
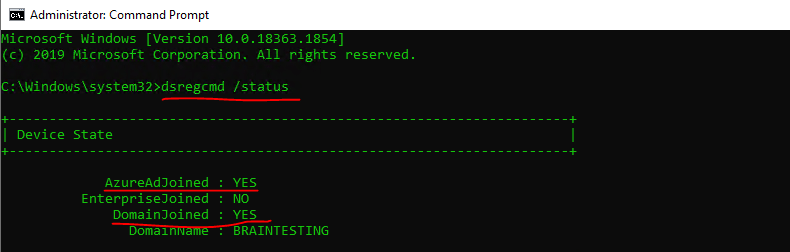
The userCertificate attribute on the computer account in my on-premises AD was populated by the User Device Registration Scheduled Task on the workstation. It generates a self-signed certificate and populates the computer account with the public key of this cert.
Source: https://github.com/MicrosoftDocs/azure-docs/issues/5872The on-premise lab environment is configured for Hybrid Azure AD join.
More about how to configure Hybrid Azure AD join for managed domains you will find in my following post.
userCertificate attribute from user object.
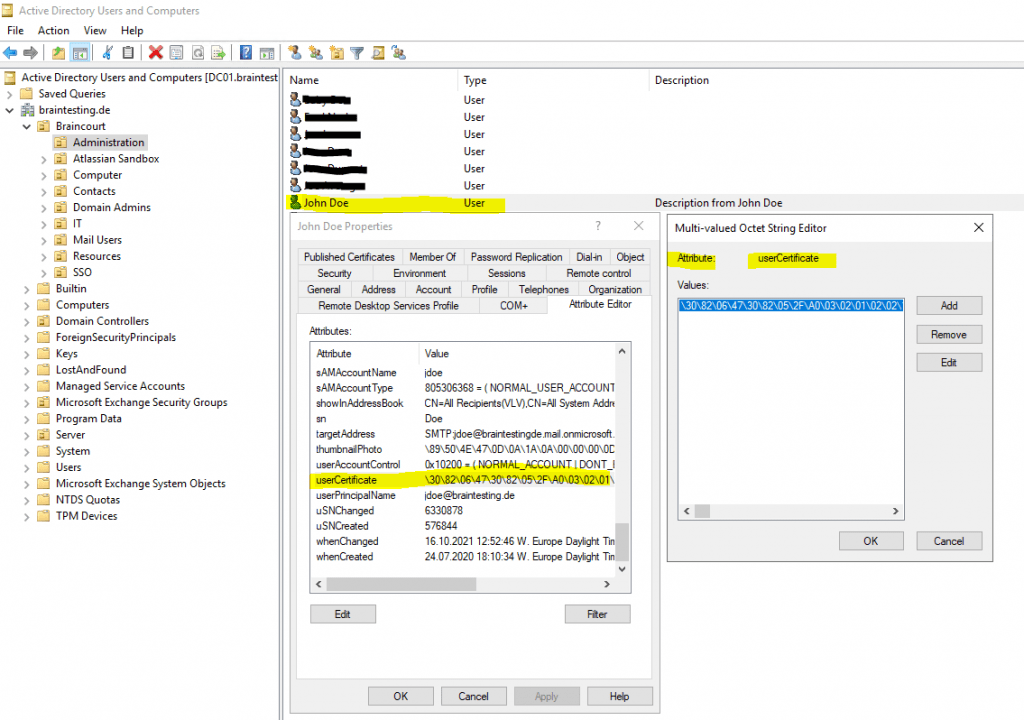
You can also export the binary field with the user or computer certificate from Active Directory by using the Ldifde command-line tool.
Ldifde
https://en.wikipedia.org/wiki/LDAP_Data_Interchange_Format
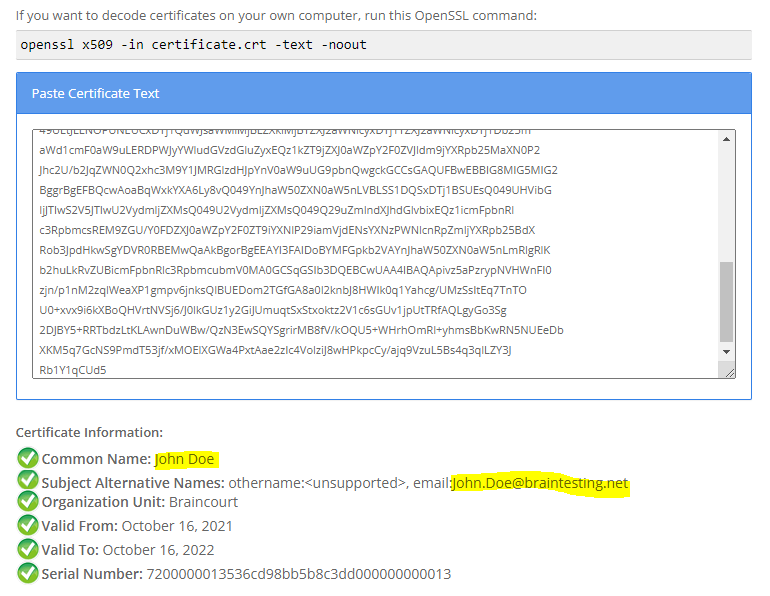
ldifde -f cert_john.doe.ldf -d “CN=John Doe,OU=Administration,OU=Braincourt,DC=braintesting,DC=de” -l Usercertificate
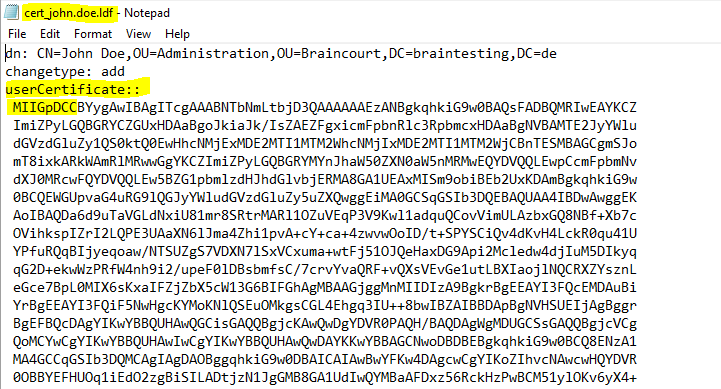
As the certificates are all base64-encoded you can paste them into an online decoder like
to decode the information or by using openssl and the following command.
openssl x509 -in certificate.crt -text -noout
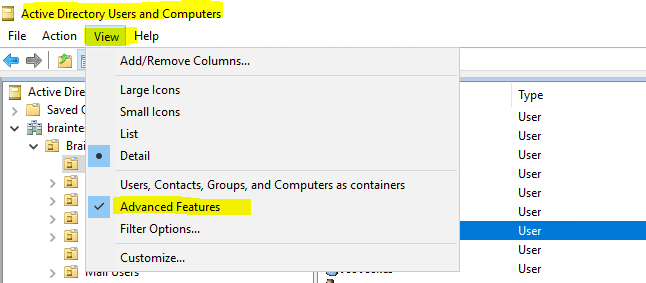
For the user certificates you can also enable the Advanced Features to get the Published Certificates tab for the user’s.
userCertificate attribute vs. userSMIMECertificate attribute
User’s can also publish their certificates themselves in the global address list (GAL) from Exchange, in this case the certificate actually will be published in Active Directory and here in the userSMIMECertificate attribute in contrast to the userCertificate attribute which is used by the certificate enrollment process.Exchange will then build its GAL from Active Directory.
Outlook will will prefer to use the certificate stored in the userSMIMECertificate attribute from the recipient to encrypt mails to it.
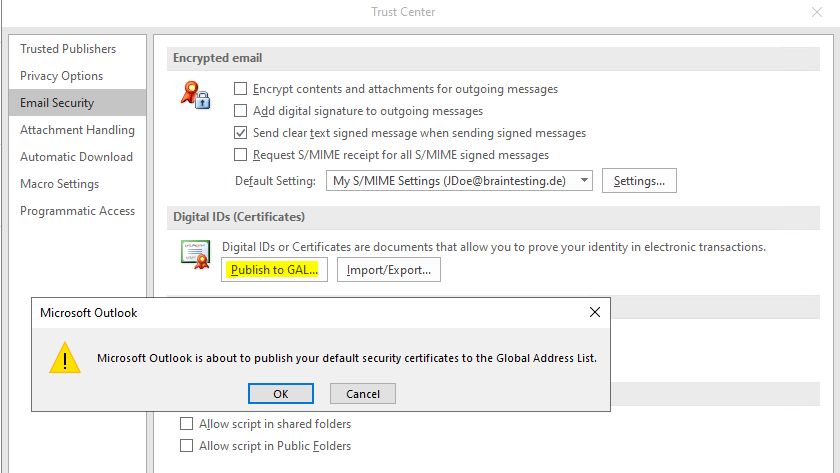
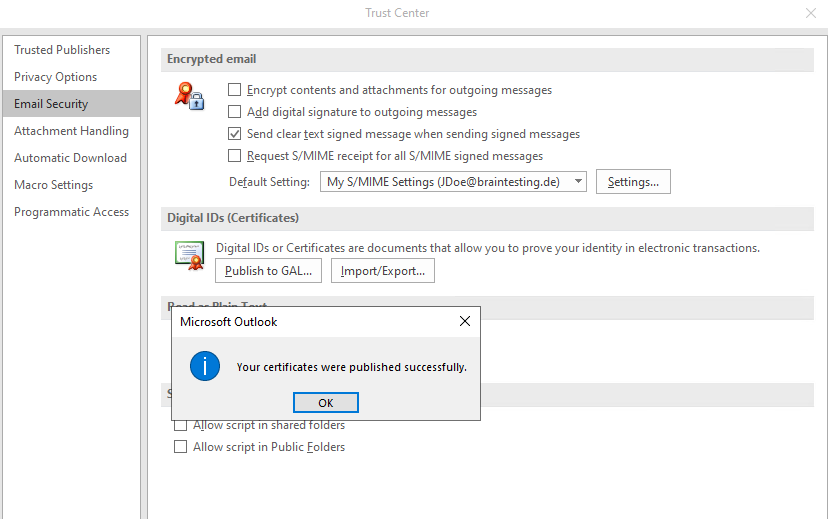
From now on the certificate is stored in the user’s userSMIMECertificate attribute in Active Directory. As the user’s mailbox from John Doe here is homed in Exchange Online, the certificate is stored in Azure AD.
$credential = Get-Credential
Connect-ExchangeOnline -Credential $credential -ShowProgress $true
Get-Mailbox -Identity jdoe@braintesting.de | fl UserSMimeCertificate
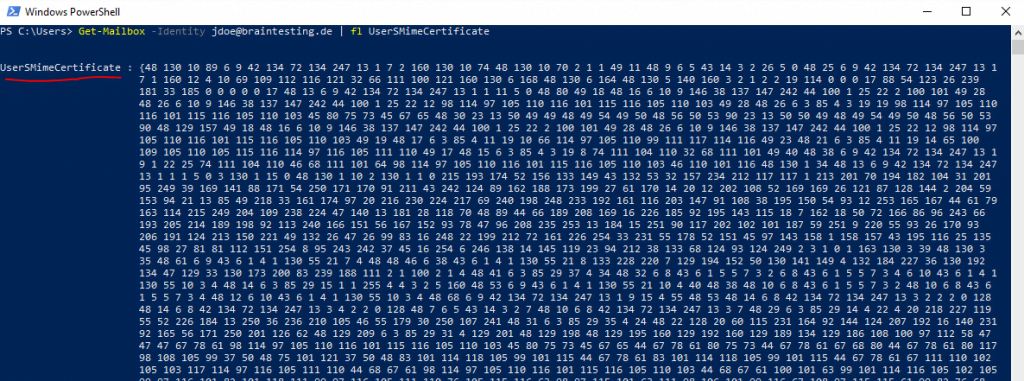
My lab environment is configured for Exchange Classic Full Hybrid and by default both the userCertificate attribute and the userSMIMECertificate attribute will by synced between the on-premise Active Directory and Azure AD.
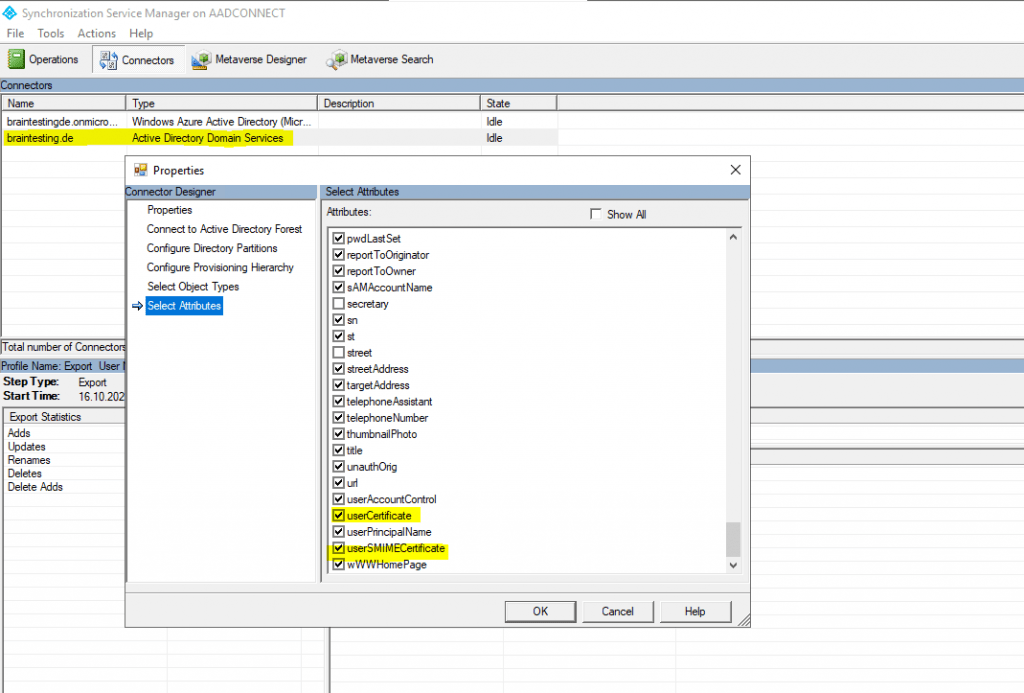
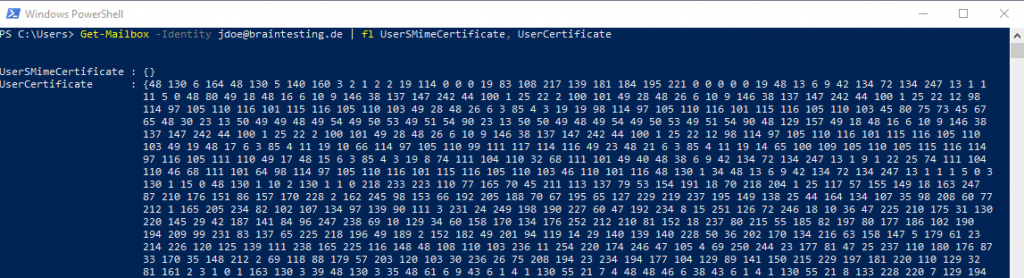
The request below was done before the user John Doe clicked on Publish to GAL in Outlook as showed above, so the userSMIMECertificate attribute is empty and only the userCertificate attribute from the certificate enrollment process in on-premise was synced from on-premise to Azure AD.
$credential = Get-Credential
Connect-ExchangeOnline -Credential $credential -ShowProgress $true
Get-Mailbox -Identity jdoe@braintesting.de | fl UserSMimeCertificate, UserCertificate
Links
Configure certificate auto-enrollment
https://docs.microsoft.com/en-us/windows-server/networking/core-network-guide/cncg/server-certs/configure-server-certificate-autoenrollment
Use Resultant Set of Policy logging to gather computer policy information
https://docs.microsoft.com/en-us/troubleshoot/windows-server/group-policy/use-resultant-set-of-policy-logging
This article describes how to use the Resultant Set of Policy utility (Rsop.msc) to gather only computer-specific policy information.
Auto-Enrollment – Avoid the challenges of making end users manage their certificates
https://azurecloudai.blog/2010/12/01/auto-enrollment-avoid-the-challenges-of-making-end-users-manage-their-certificates/



