Configure Hybrid Azure AD join for managed domains
Like a user in your organization, a device is a core identity you want to protect. You can use a device’s identity to protect your resources at any time and from any location. You can accomplish this goal by managing device identities in Azure AD. Use one of the following methods:
- Azure AD join
- Hybrid Azure AD join
- Azure AD registration
The differences between them will be described in the following article from Microsoft under the Concepts menu point.
Azure AD device identity documentation
https://learn.microsoft.com/en-us/azure/active-directory/devices/
Bringing your devices to Azure AD maximizes user productivity through single sign-on (SSO) across your cloud and on-premises resources. You can secure access to your cloud and on-premises resources with Conditional Access at the same time.
You can deploy a managed environment by using password hash sync (PHS) or pass-through authentication (PTA) with seamless single sign-on. These scenarios don’t require you to configure a federation server for authentication.
Source: https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-managed-domains
In this post I want to configure Hybrid Azure AD join.
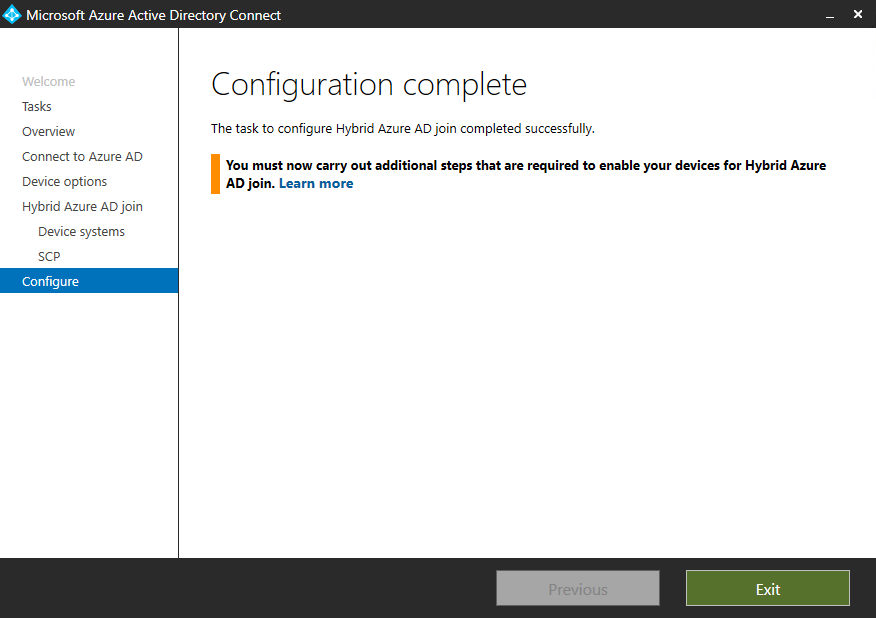
Configure Hybrid Azure AD join
To configure Hybrid Azure AD join we can also use the Azure AD Connect tool.
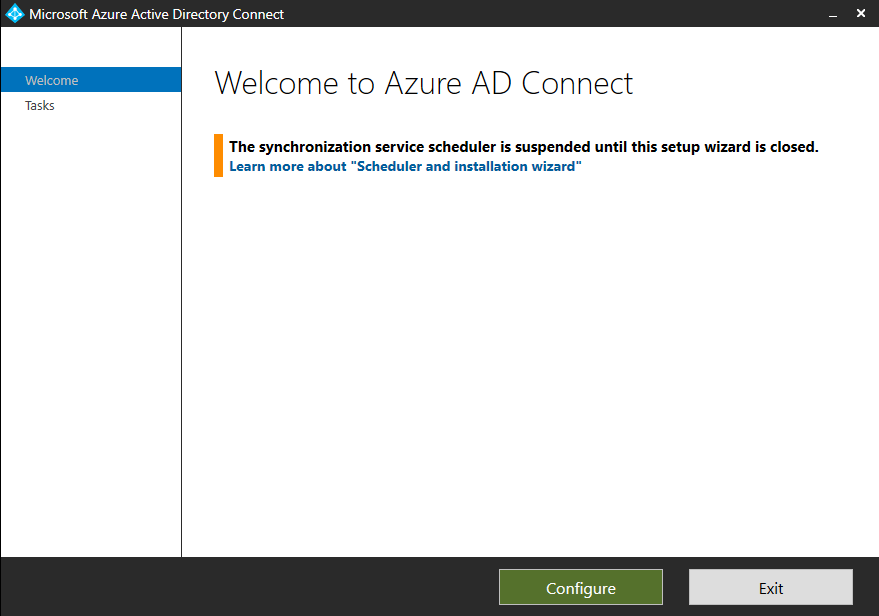
First we need to be sure, that besides our synced users also the computer objects will be synced to Azure AD.
So click on Customize synchronization options
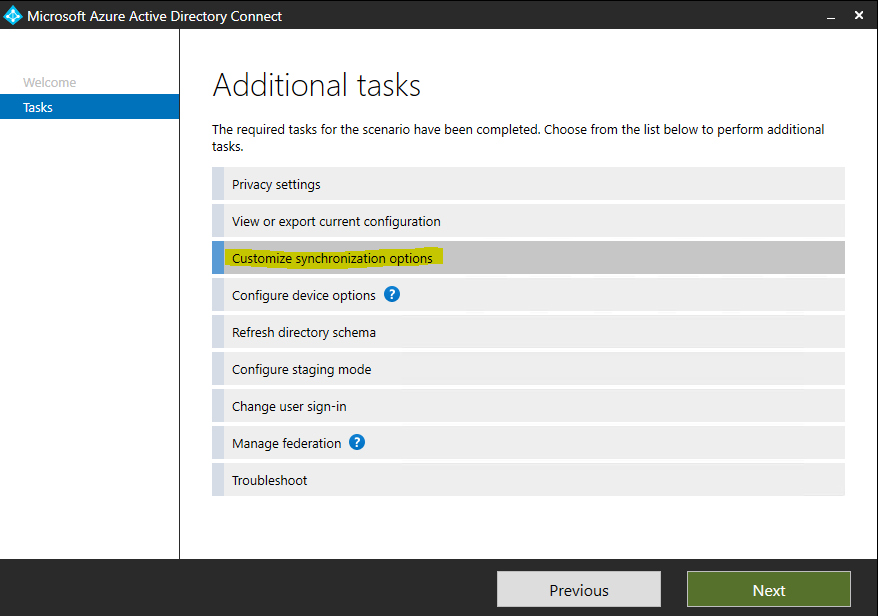
Be sure to check all OUs where you store your computer objects which should be used for Hybrid Azure AD join and therefore must be synced to Azure AD.
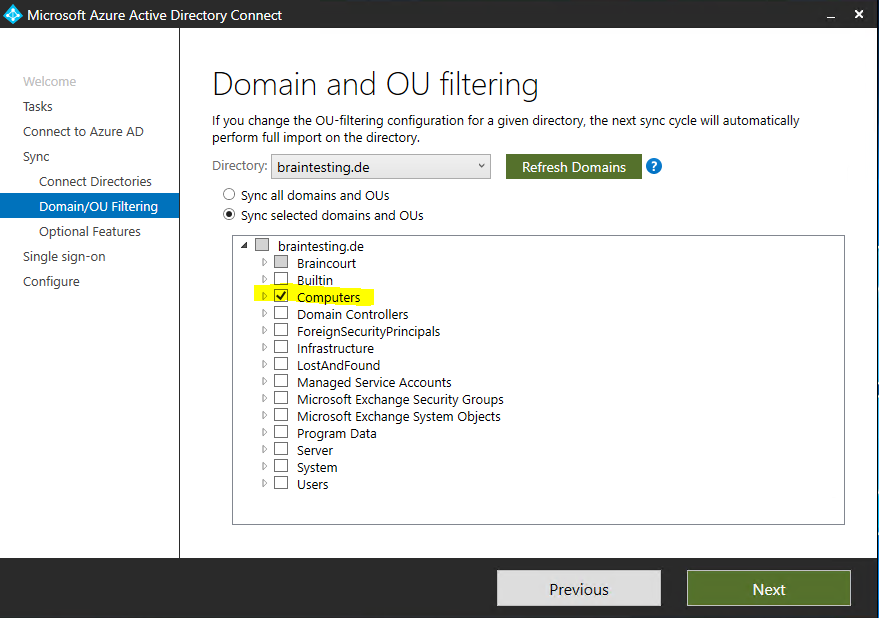
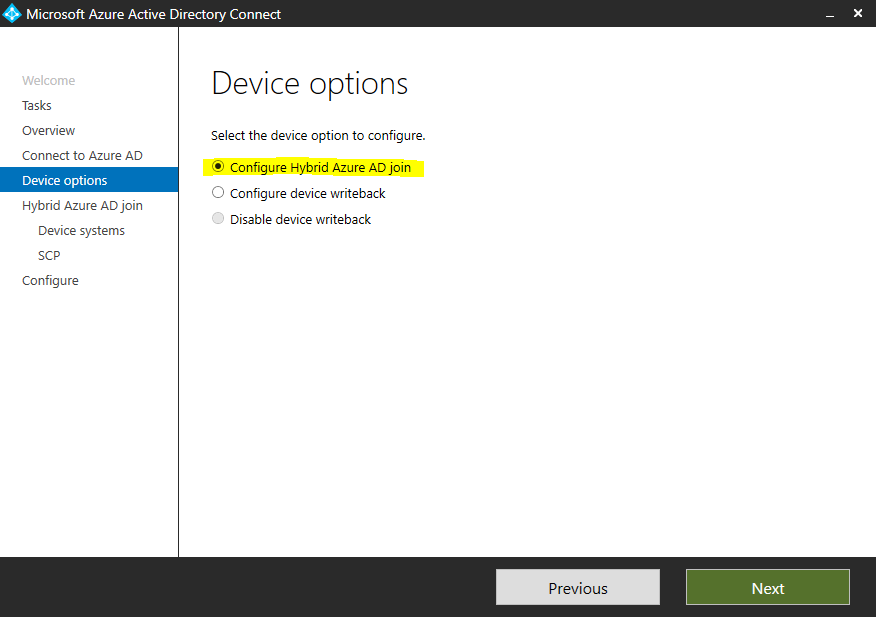
For the actual configuration of Hybrid Azure AD join we need to select Configure device options
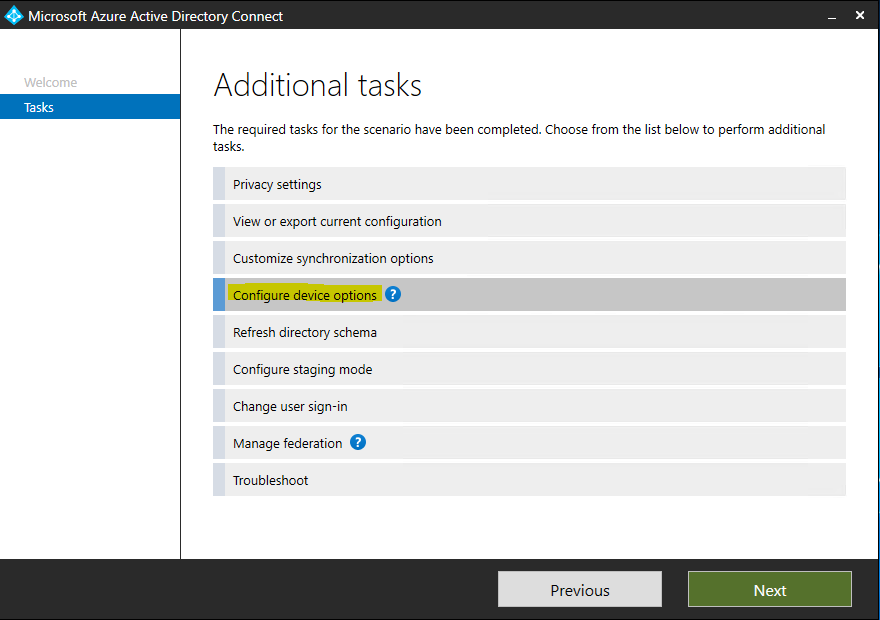
Select Configure Hybrid Azure AD join
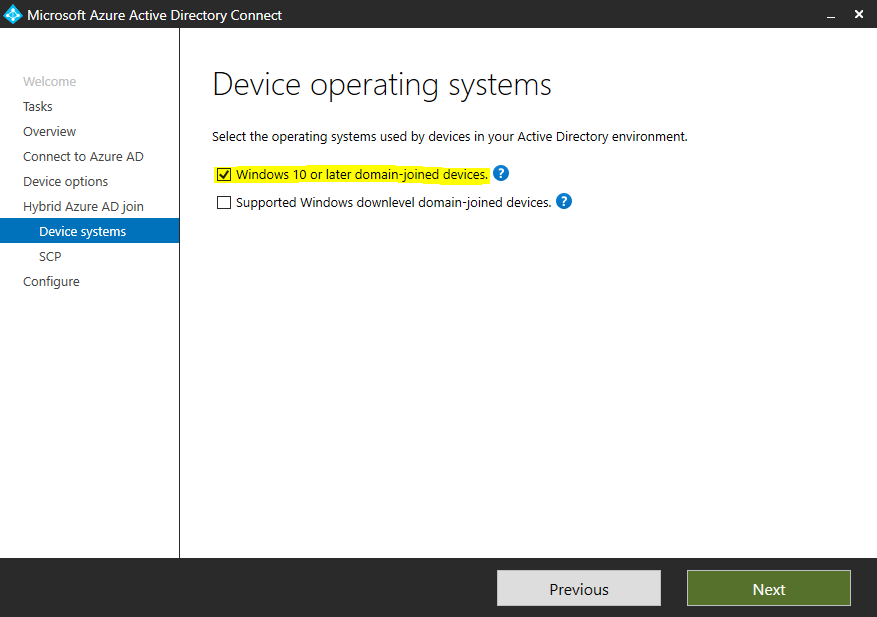
I will only have Windows 10 clients in my environment.
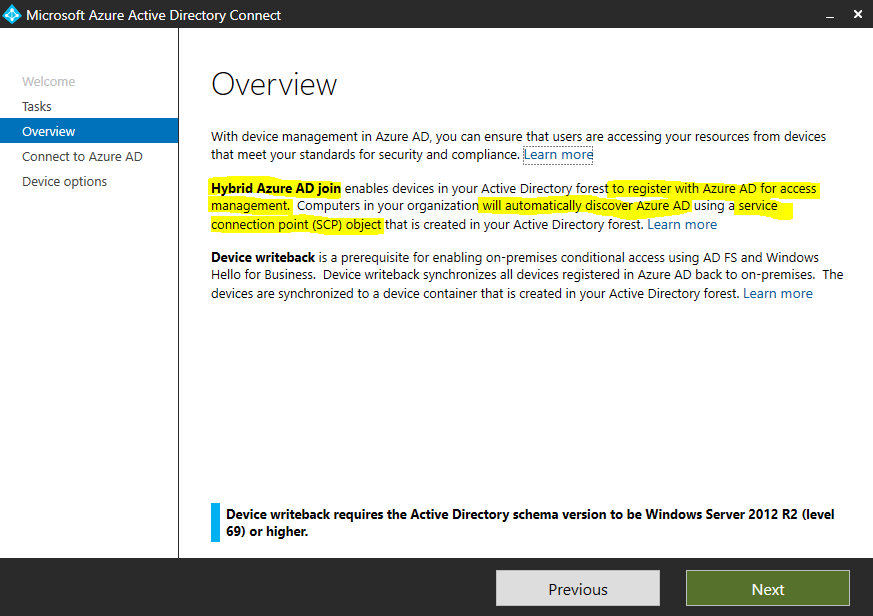
Beginning with version 1.1.819.0, Azure AD Connect includes a wizard to configure hybrid Azure AD join. The wizard significantly simplifies the configuration process. The wizard configures the service connection points (SCPs) for device registration to discover your Azure AD tenant information.
- Select the forest.
- Select the authentication service. You must select AD FS server unless your organization has exclusively Windows 10 clients and you have configured computer/device sync, or your organization uses seamless SSO.
- Select Add to enter the enterprise administrator credentials.
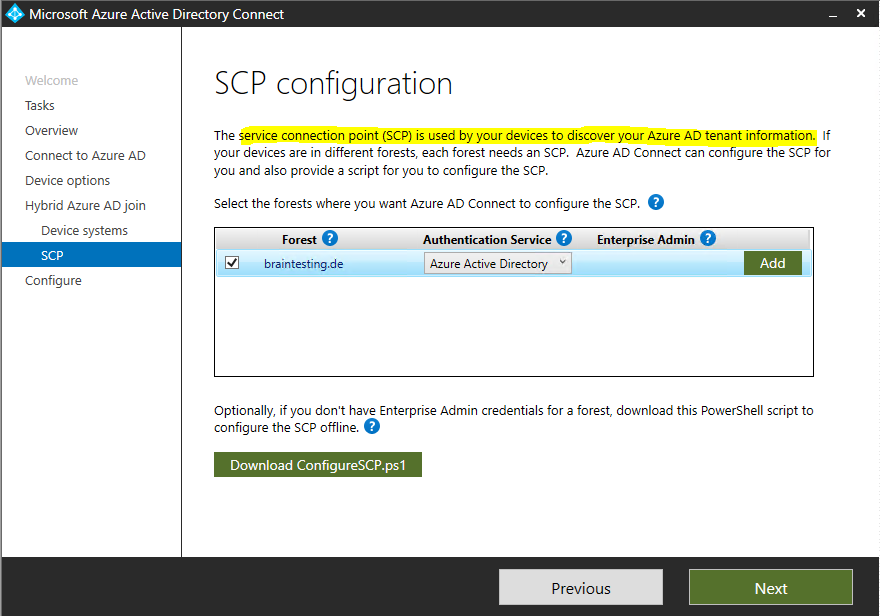
After the configuration you can check the SCP as follows.
Open ADSIEDIT.MSC and open the Configuration Naming Context.
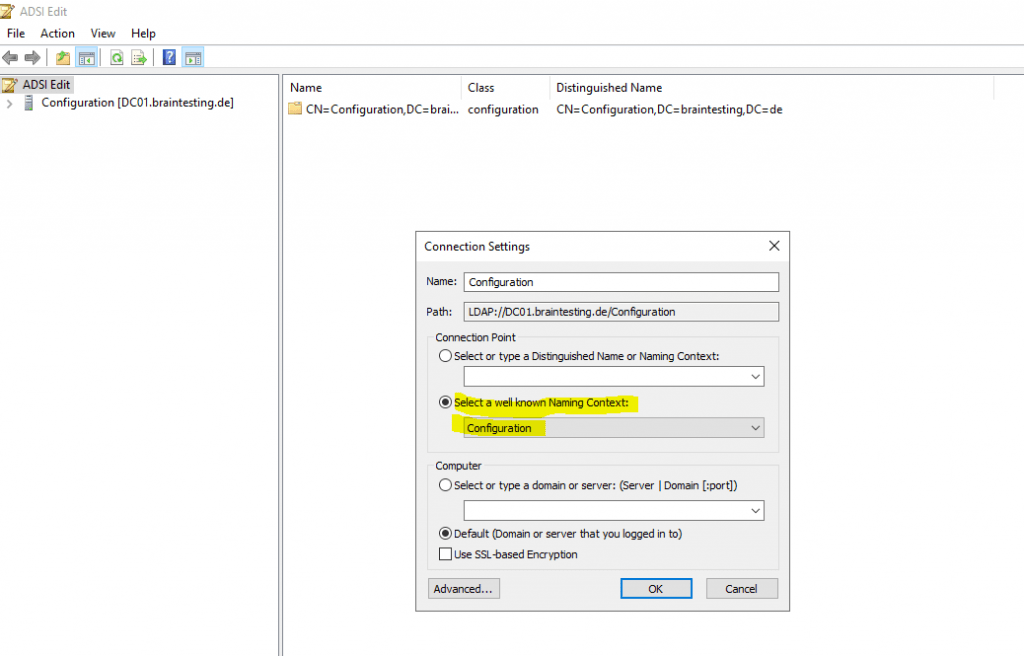
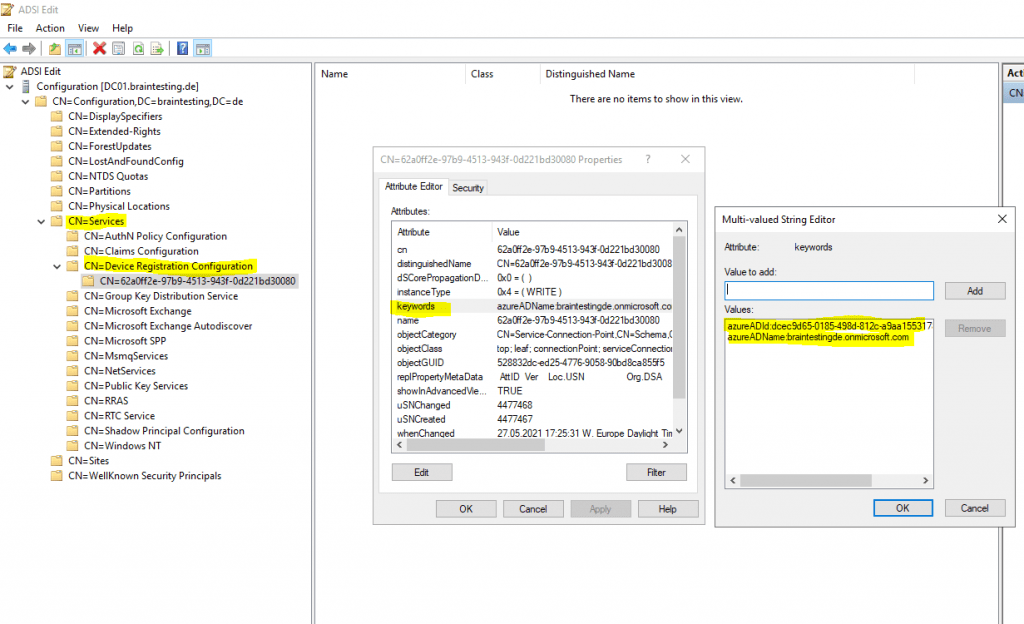
Configuration -> Services -> Device Registration Configuration
Under keywords the Azure AD domain is listed to what windows 10 will connect for device registration.
To successfully complete hybrid Azure AD join of your Windows downlevel devices and to avoid certificate prompts when devices authenticate to Azure AD, you can push a policy to your domain-joined devices to add the following URLs to the local intranet zone in Internet Explorer:
https://device.login.microsoftonline.com- Your organization’s STS (For federated domains)
https://autologon.microsoftazuread-sso.com(For seamless SSO)
You also must enable Allow updates to status bar via script in the user’s local intranet zone.
Group policy option – Detailed steps
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sso-quick-start#group-policy-option—detailed-steps
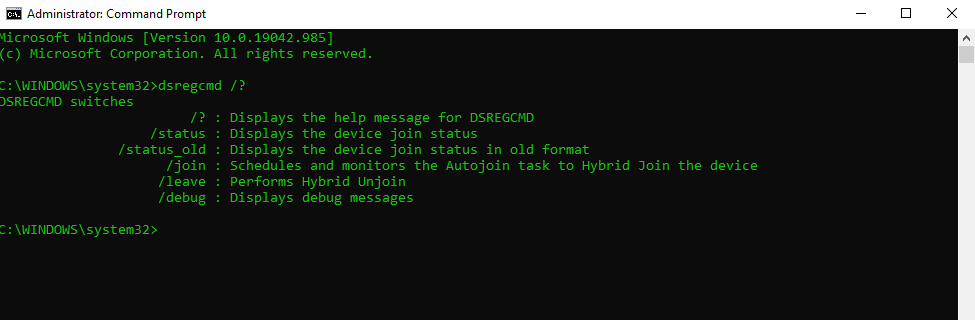
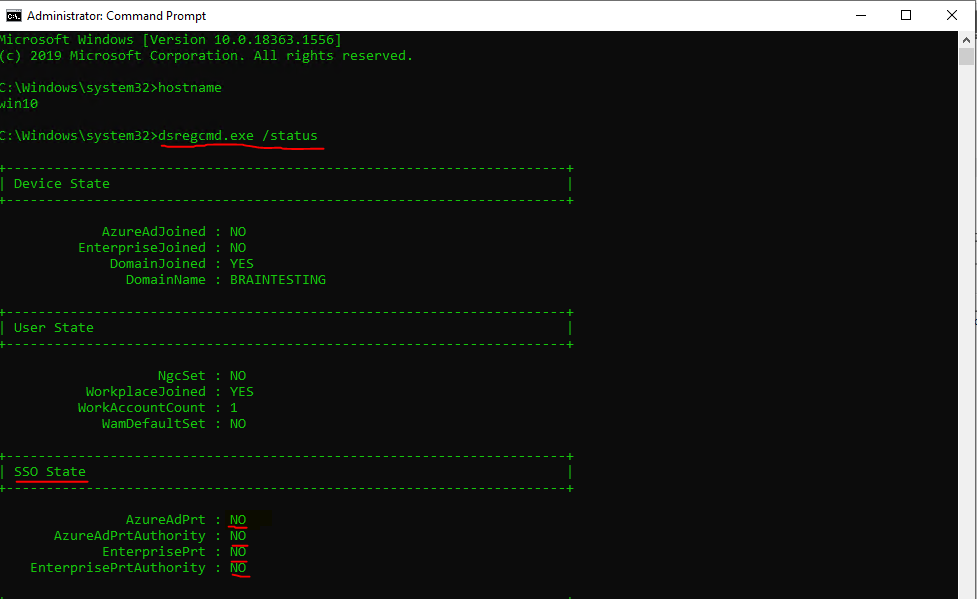
Verify the registration by using dsregcmd
dsregcmd /status
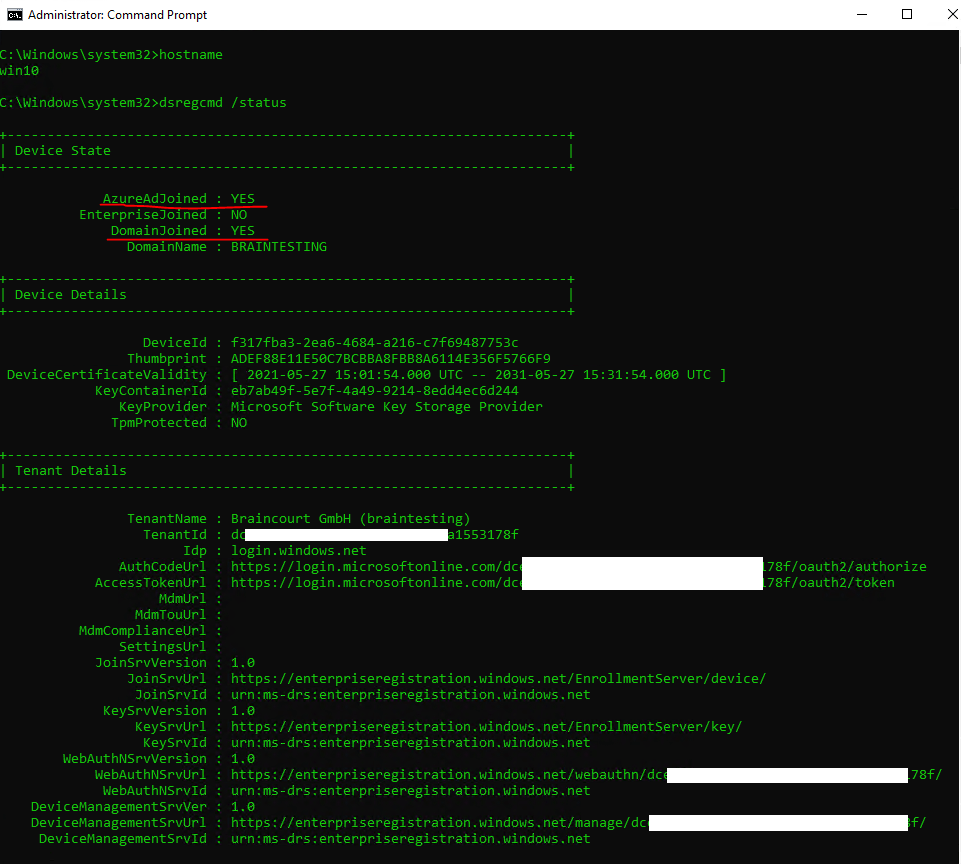
AzureAdJoined : YES
This field indicates whether the device is joined. The value will be YES if the device is either an Azure AD joined device or a hybrid Azure AD joined device. If the value is NO, the join to Azure AD has not completed yet.
WorkplaceJoined : NO
This field indicates whether the device is registered with Azure AD as a personal device (marked as Workplace Joined). This value should be NO for a domain-joined computer that is also hybrid Azure AD joined. If the value is YES, a work or school account was added prior to the completion of the hybrid Azure AD join. In this case, the account is ignored when using Windows 10 version 1607 or later.
EnterpriseJoined : NO
If the device is Joined to an on-premises Device Registration Service (DRS). A device cannot be both EnterpriseJoined and AzureAdJoined. The Device Registration Service (DRS) is a new Windows service that is included with the Active Directory Federation Service (AD FS) Role on Windows Server 2012 R2. The DRS must be installed and configured on all of the federation servers in your AD FS farm. For information on deploying DRS, see Configure a federation server with Device Registration Service.
DomainJoined : YES
This field indicates whether the device is joined to an on-premises Active Directory or not. If the value is NO, the device cannot perform a hybrid Azure AD join.EnterpriseJoined
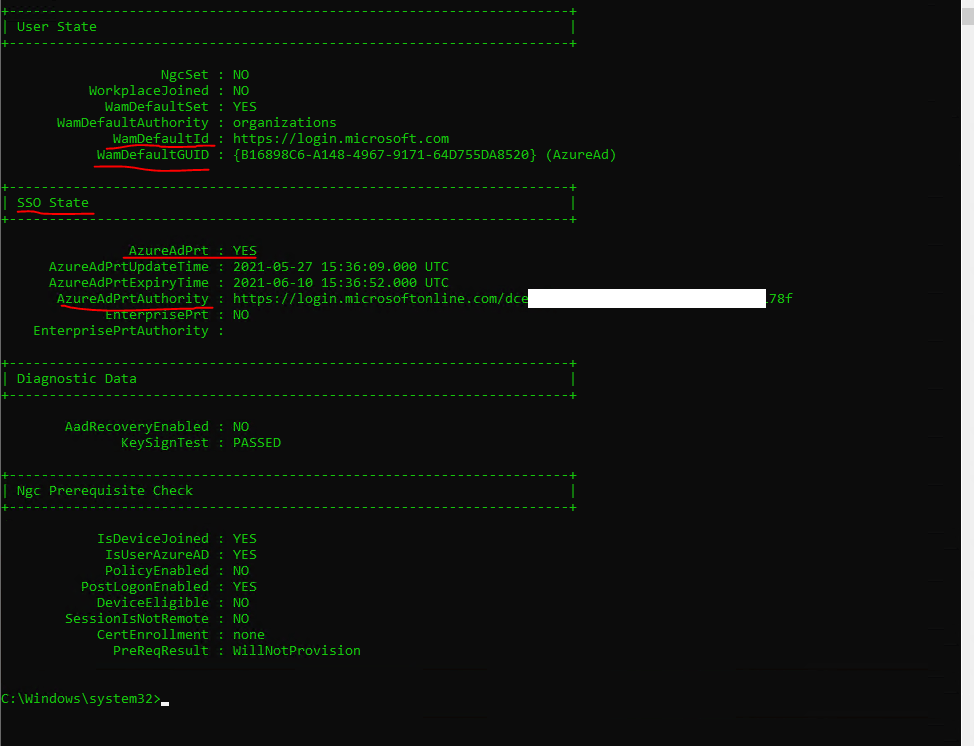
Web Account Manager (WAM): WAM is the default token broker on Windows 10 devices. WAM also provides a plugin framework that identity providers can build on and enable SSO to their applications relying on that identity provider.
Source: https://docs.microsoft.com/en-us/azure/active-directory/devices/concept-primary-refresh-token#key-terminology-and-components
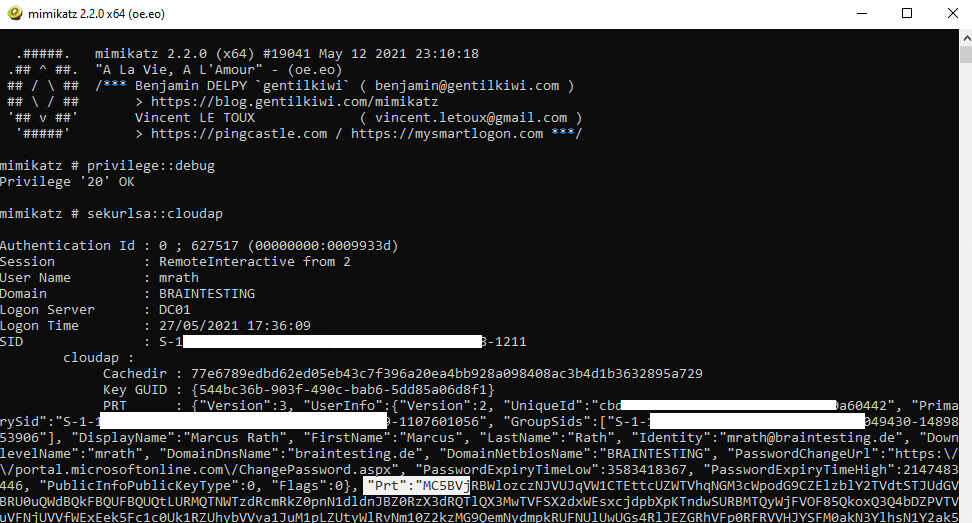
The revealed prt token from mimikatz.
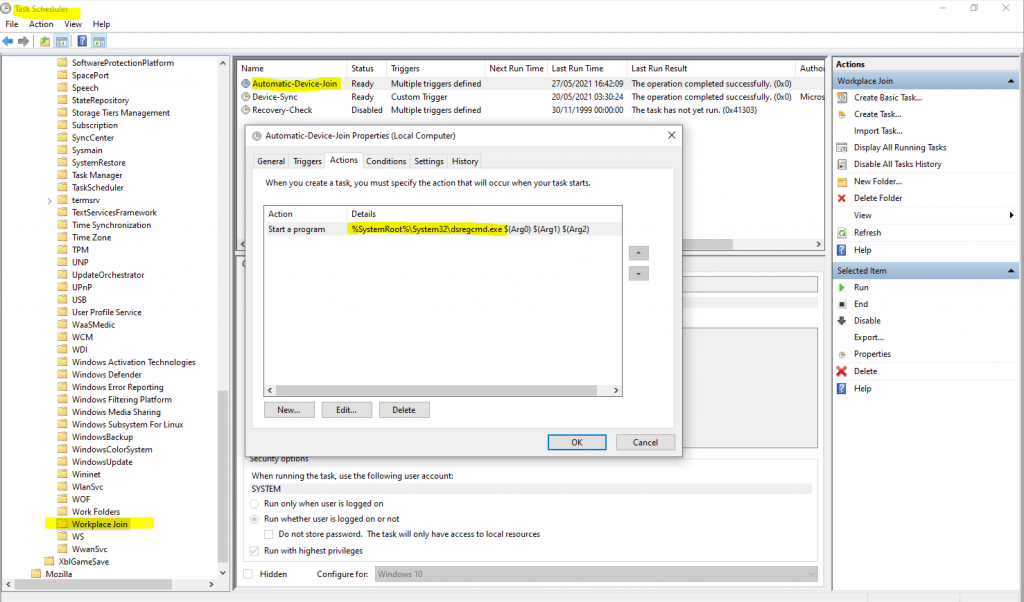
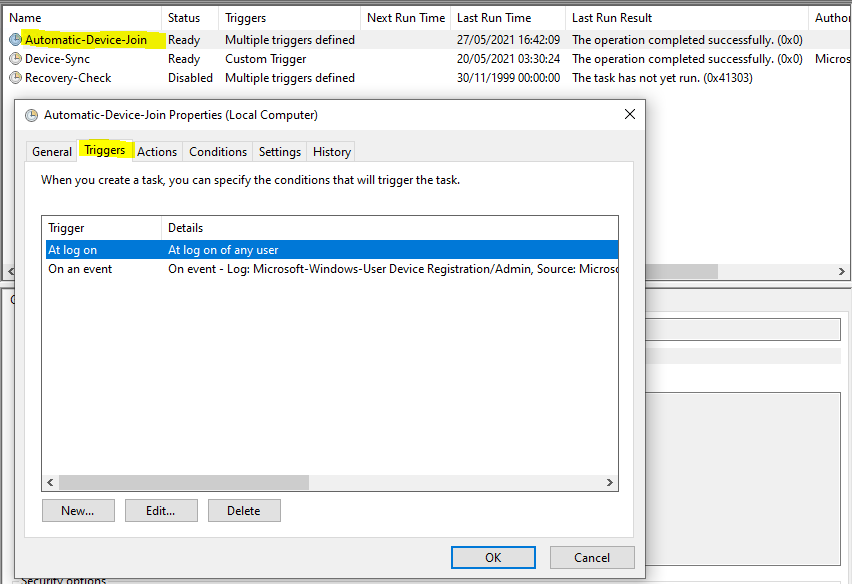
Windows Task – Automatic-Device-Join
The task Automatic-Device-Join below is by default disabled for standalone windows 10 computers and will be enabled after domain join. Also after leaving domain it will be disabled again.
After the first successful run of this task, the computer will be Hybrid Azure AD joined and the second Task Device-Sync will be enabled. Device-Sync will synchronize device attributes with Azure AD.
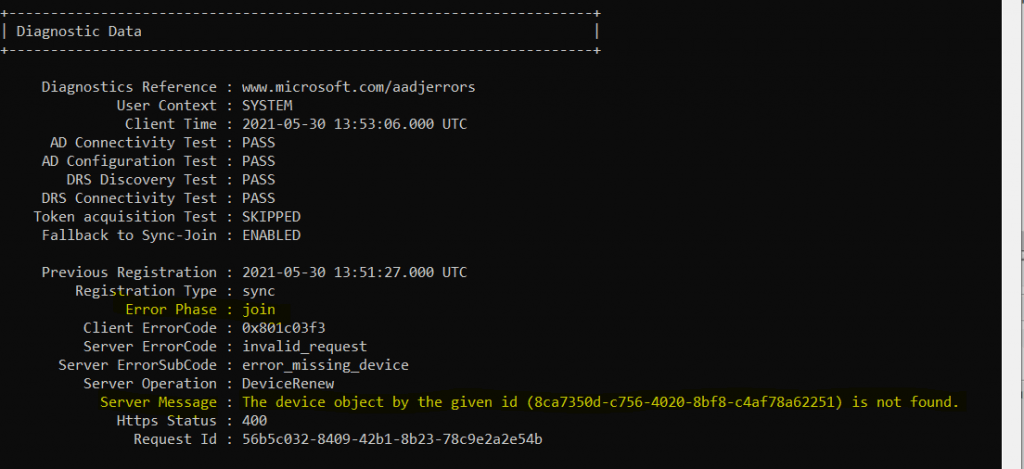
In order the Automatic-Device-Join task can run successfully, the computer object from on-premises first have to be synced to Azure AD, otherwise the following error will appear after running dsregcmd /status
The device object by the given id is not found.
Task Scheduler -> Microsoft -> Windows -> Workplace Join
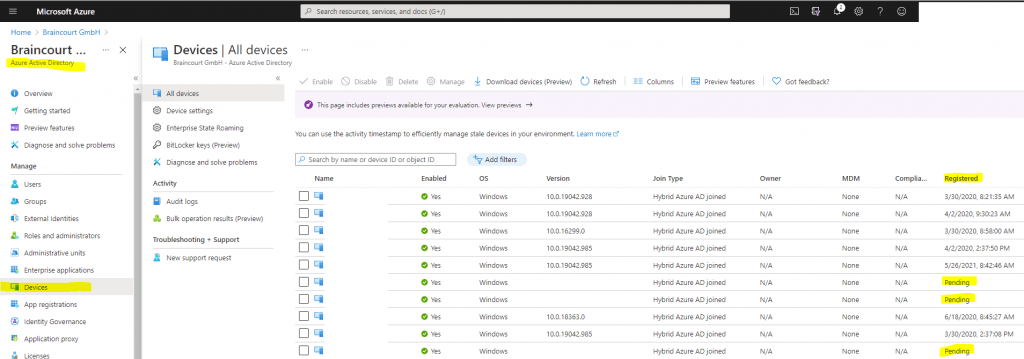
In Azure Active Directory under Devices, you will see the synced computers from on-premises with the Join type Hybrid Azure AD join, also every computer with Azure AD registered and Azure AD joined.
Hybrid Azure AD joined computers in state Pending as below, means that the device has been synchronized from on-premises to Azure AD, and is waiting to complete the registration from the client. Therefore the Automatic-Device-Join task on the client first needs to run to complete the registration as mentioned above.
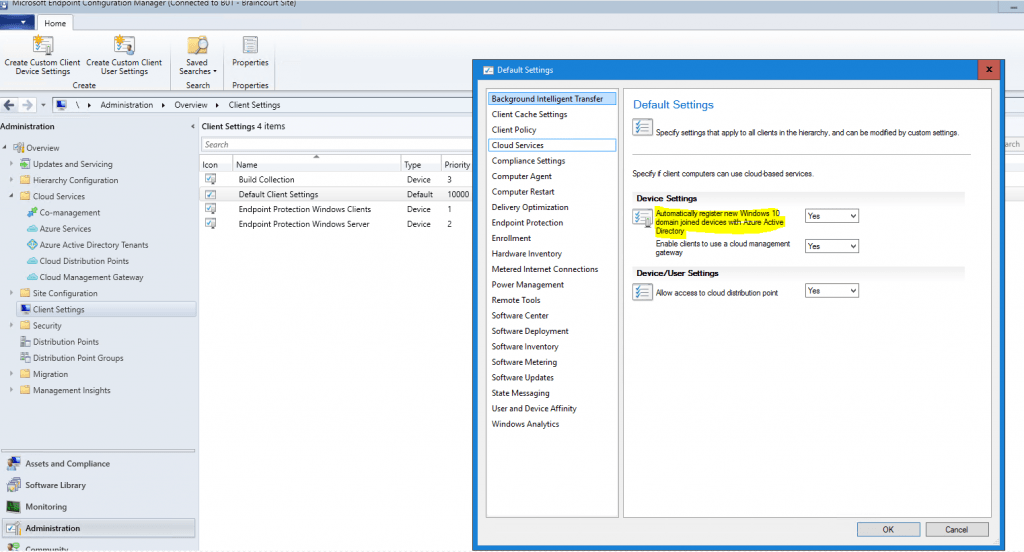
If you are using System Center Configuration Manager (SCCM) in your network, you may also know the Client Settings Automatically register new Windows 10 domain joined devices with Azure Active.
This behavior is also the default in Windows 10, version 1709.
https://docs.microsoft.com/en-us/mem/configmgr/core/clients/deploy/deploy-clients-cmg-azure#configure-client-settings
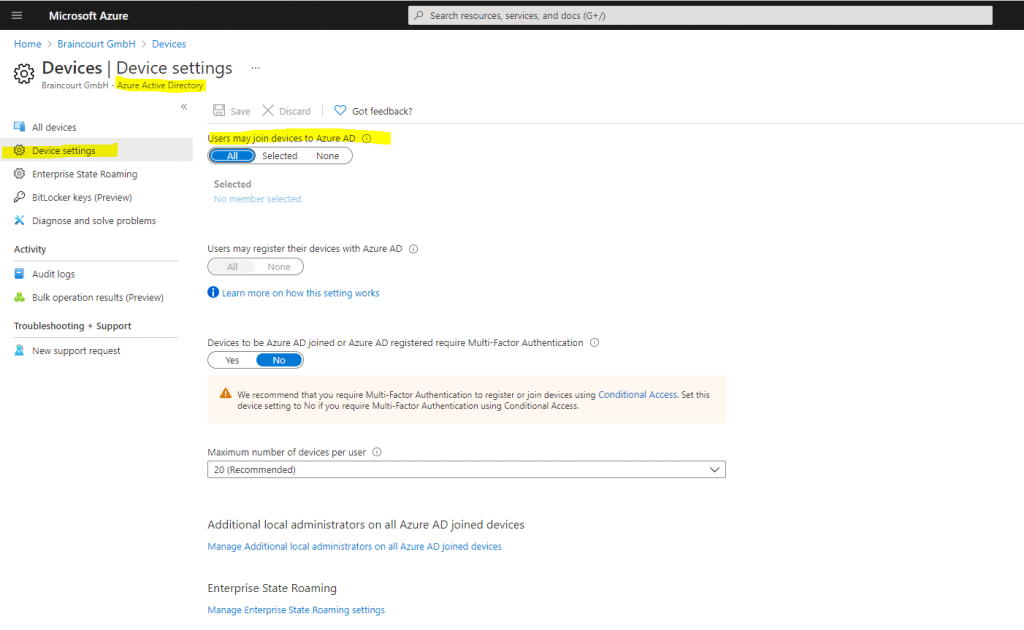
Users must be able to join devices to Azure AD, so switch to All or Selected and add the users who should be able to join.
Regarding System Center Configuration Manger (SCCM) and co-management with Microsoft Intune, please read my following post.
Re-register a Windows 10 device for Hybrid Azure AD join
First we need to remove the existing registration to Azure AD from the device as follow.
dsregcmd /leave
dsregcmd /debug /leave
Will display debug messages in addition
Also remove the following two certificates from the computer accounts personal store.
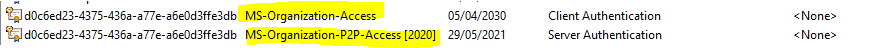
Sign out and sign in to trigger the scheduled task that registers the device again with Azure AD or execute the task by hand as follows:
Go to Task Scheduler > Microsoft > Windows > Workplace Join
Run the Automatic-Device-Join task
For Windows 10 Version 1607 and later Hybrid Azure AD join is invoked by a scheduled task which is by default created.
The task Automatic-Device-Join is by default disabled for standalone windows 10 computers and will be enabled after domain join.

By default will be triggered at every logon and every hour for on-premises domain joined devices.
Check that the two certificates was re-created.
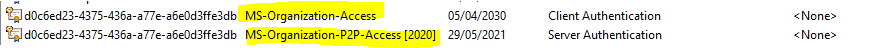
Check again with dsregcmd /status if the device re-registered successfully.
Handling devices with Azure AD registered state
If your Windows 10 domain joined devices are Azure AD registered to your tenant, it could lead to a dual state of Hybrid Azure AD joined and Azure AD registered device. We recommend upgrading to Windows 10 1803 (with KB4489894 applied) or above to automatically address this scenario. In pre-1803 releases, you will need to remove the Azure AD registered state manually before enabling Hybrid Azure AD join. In 1803 and above releases, the following changes have been made to avoid this dual state:
- Any existing Azure AD registered state for a user would be automatically removed after the device is Hybrid Azure AD joined and the same user logs in. For example, if User A had an Azure AD registered state on the device, the dual state for User A is cleaned up only when User A logs in to the device. If there are multiple users on the same device, the dual state is cleaned up individually when those users log in. In addition to removing the Azure AD registered state, Windows 10 will also unenroll the device from Intune or other MDM, if the enrollment happened as part of the Azure AD registration via auto-enrollment.
- Azure AD registered state on any local accounts on the device is not impacted by this change. It is only applicable to domain accounts. So Azure AD registered state on local accounts is not removed automatically even after user logon, since the user is not a domain user.
- You can prevent your domain joined device from being Azure AD registered by adding the following registry value to HKLMSOFTWAREPoliciesMicrosoftWindowsWorkplaceJoin: “BlockAADWorkplaceJoin”=dword:00000001.
- In Windows 10 1803, if you have Windows Hello for Business configured, the user needs to re-setup Windows Hello for Business after the dual state clean up.This issue has been addressed with KB4512509
Source: https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-plan
MS-Organization-Access and MS-Organization-P2P-Access Certificate
Both certificates will be populated by the User Device Registration Scheduled Task on the workstation.
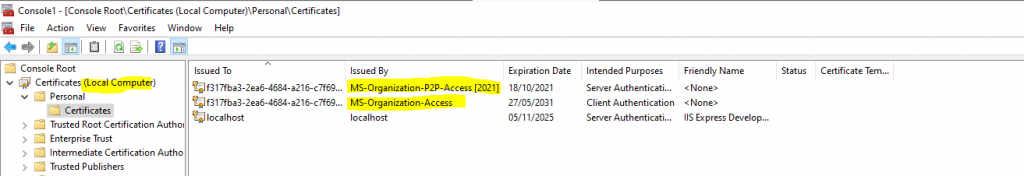
The MS-Organization-P2P-Access certificates are issued by Azure AD to both, Azure AD joined and hybrid Azure AD joined devices. These certificates are used to enable trust between devices in the same tenant for remote desktop scenarios. One certificate is issued to the device and another is issued to the user. The device certificate is present in Local ComputerPersonalCertificates and is valid for one day. This certificate is renewed (by issuing a new certificate) if the device is still active in Azure AD. The user certificate is present in Current UserPersonalCertificates and this certificate is also valid for one day, but it is issued on-demand when a user attempts a remote desktop session to another Azure AD joined device. It is not renewed on expiry. Both these certificates are issued using the MS-Organization-P2P-Access certificate present in the Local ComputerAAD Token IssuerCertificates. This certificate is issued by Azure AD during device registration.
Source: https://docs.microsoft.com/en-us/azure/active-directory/devices/faq#what-are-the-ms-organization-p2p-access-certificates-present-on-our-windows-10-devices
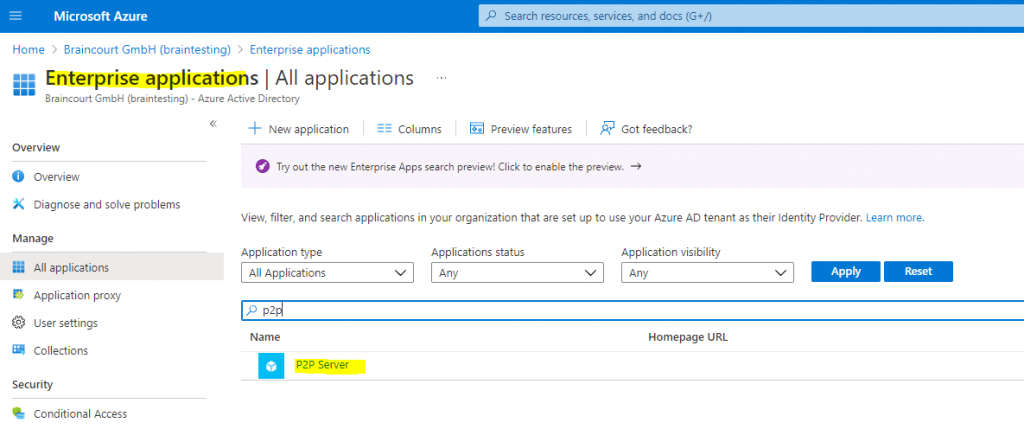
The following service principal below will be automatically registered after a windows device has been successfully joined to Azure AD. (Azure AD joined and hybrid Azure AD joined devices)
Using this principal, Windows devices that are Azure AD joined will provision device certificates in their computer store with a name matching “MS-Organization-P2P-Access” that enables RDP using Azure AD credentials. Via PKI, these certificates trust the tenant root certificate that is registered on the “P2P Server” service principal in Azure AD.
Source: https://www.jasonfritts.me/tag/ms-organization-p2p-access/
Troubleshooting
The first tool to check if you encounter some issues regarding Hybrid Azure AD join is the command line tool dsregcmd.
Troubleshooting devices using the dsregcmd command
https://docs.microsoft.com/en-us/azure/active-directory/devices/troubleshoot-device-dsregcmd
Azure Active Directory device management FAQ
https://docs.microsoft.com/en-us/azure/active-directory/devices/faq
Yo can check the status with
dsregcmd /status
Here I can saw that something went wrong and the computer wasn’t joined to Azure AD.
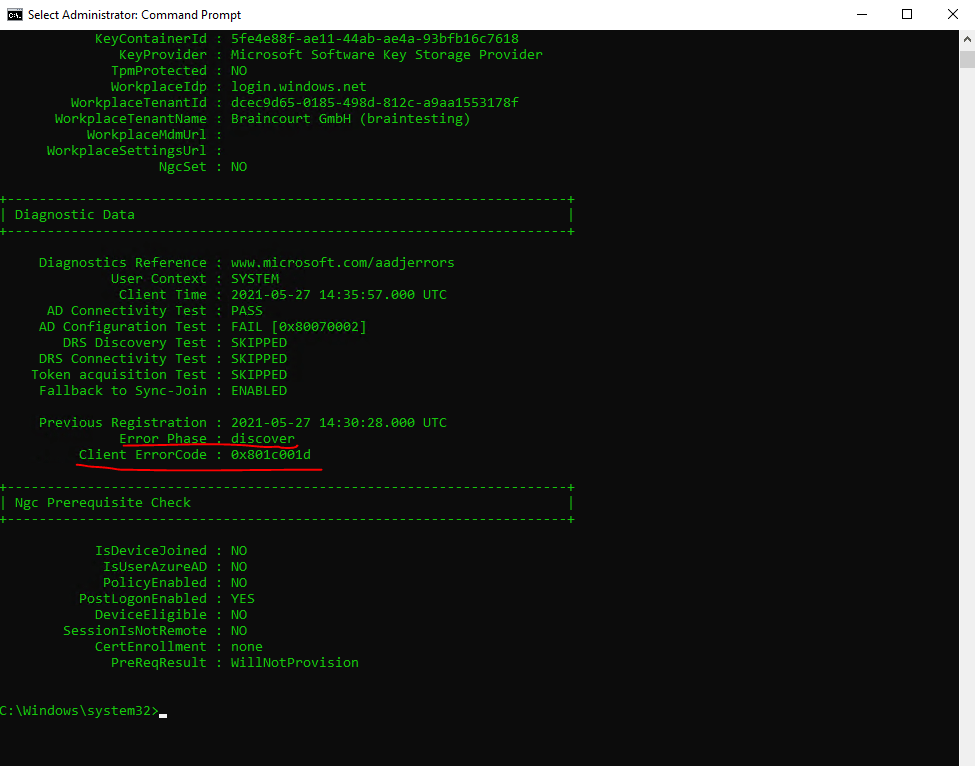
Therefore I checked the windows logs for the User Device Registration.
Event Viewer -> Microsoft -> Windows -> User Device Registration
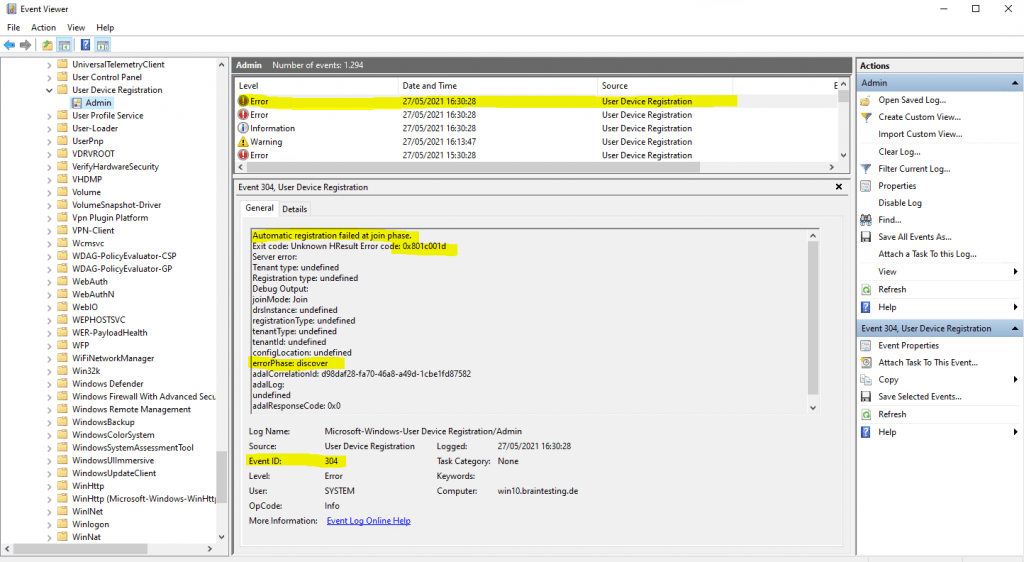
Automatic registration failed at join phase.
Exit code: Unknown HResult Error code: 0x801c001d
errorPhase: discover
Source: User Device Registration
Event ID: 304
User: SYSTEM
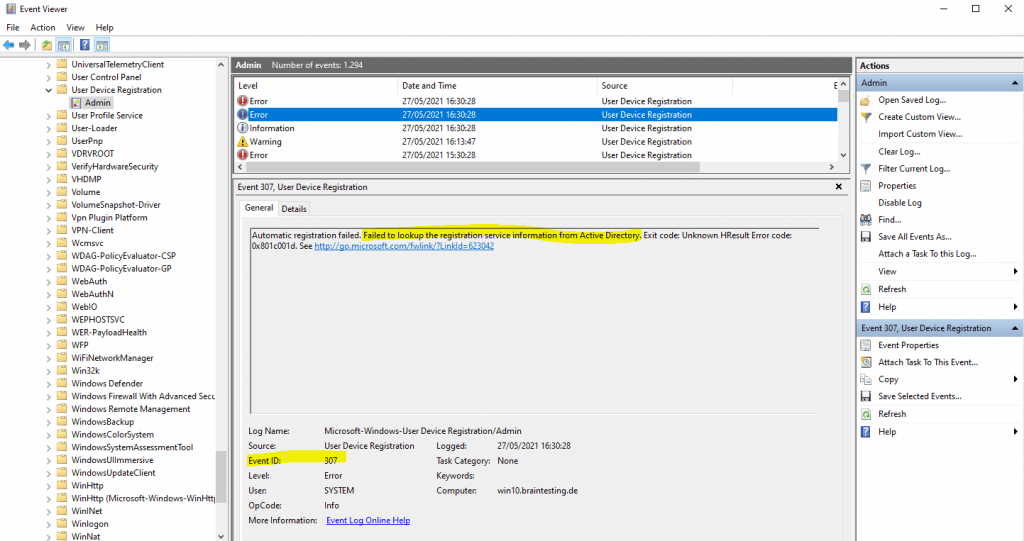
Automatic registration failed. Failed to lookup the registration service information from Active Directory. Exit code: Unknown HResult Error code: 0x801c001d.
The reason for is, that in my lab environment, I will first need to configure Hybrid Azure AD join, which will create a Service Connection Point (SCP), which the devices needs to discover the Azure AD tenant information.
Beginning with version 1.1.819.0, Azure AD Connect includes a wizard that you can use to configure hybrid Azure AD join. The wizard significantly simplifies the configuration process. The related wizard:
- Configures the service connection points (SCPs) for device registration
- Backs up your existing Azure AD relying party trust
Links
Configure hybrid Azure AD join
https://docs.microsoft.com/en-us/azure/active-directory/devices/hybrid-azuread-join-federated-domains#configure-hybrid-azure-ad-join
Troubleshooting hybrid Azure Active Directory joined devices
https://docs.microsoft.com/en-us/azure/active-directory/devices/troubleshoot-hybrid-join-windows-currentTroubleshooting devices using the dsregcmd command
https://docs.microsoft.com/en-us/azure/active-directory/devices/troubleshoot-device-dsregcmd



