How to enable Microsoft Entra ID Authentication by manually publishing Users into the vCenter Identity Broker (vIDB) and not by SCIM
In my two previous posts we saw how we can enable Microsoft Entra ID Authentication for vCenter Server and performing User Provisioning by using System for Cross-domain Identity Management (SCIM).
Now this time we will also enable Microsoft Entra ID Authentication for vCenter Server but without using SCIM for User Provisioning and just by adding Entra ID users manually to vCenter’s Identity Broker (vIDB).
By provisioning the Entra ID users manually to vCenter’s Identity Broker (vIDB), we neither need to install the Microsoft Entra Provisioning Agent in our on-premise Network nor we need to expose the vCenter-SCIM-App’s API used for SCIM User Provisioning by VMware’s Identity Service app. About these both option I already wrote a post how to set up, you will find them at the end of this post.
- Set up the vCenter Entra ID Authentication App
- Set up Entra ID Identity Provider in VMware vSphere
- Adding Users manually to vCenter’s Identity Broker (vIDB)
- Removing Users manually from vCenter’s Identity Broker (vIDB)
- More about how to enable Microsoft Entra ID Authentication for vCenter Server
- Troubleshooting
- Links
Set up the vCenter Entra ID Authentication App
First we need to create a new app registration for the vCenter Server’s WebGUI to authenticate to vCenter by using Microsoft Entra ID.
I will spare here the individual steps for creating the Entra ID Authentication app, these steps you can see in my previous both posts here.
More in general about OAuth which stands for Open Authorization and is the de facto industry standard for online authorization and OpenID Connect (OIDC) which enables the authorization server to not only issue access tokens but also ID tokens to the 3rd party applications (client) you will find in my following post.
Set up Entra ID Identity Provider in VMware vSphere
Microsoft Entra ID can be used as an Identity Provider (IdP) for VMware vSphere authentication. This setup allows you to leverage modern authentication methods, such as SSO, MFA, and conditional access, to securely log in to vSphere.
I will also spare here the individual steps to set up the Entra ID Identity Provider in VMware vSphere, as these steps will been already shown in my previous posts here.
Just one exception this time, a secret token we doesn’t really need to generate here, but nevertheless we can if we wanted, finally we are not using SCIM and therefore no app in Entra ID needs to connect and authenticate to vCenter‘s Tenant URL for user provisioning.
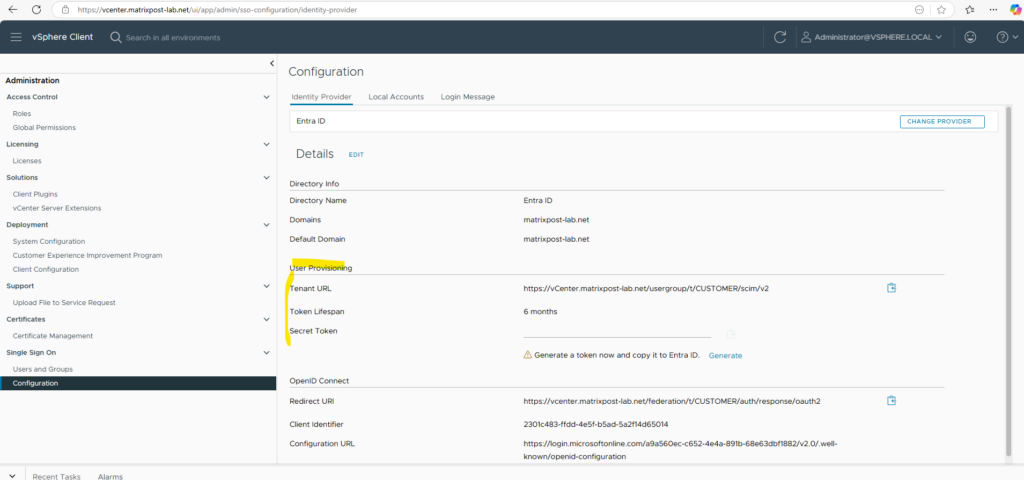
From now on we will see already the following sign-in screen where we can choose to sign-in by using either Entra ID or local accounts.
Adding Users manually to vCenter’s Identity Broker (vIDB)
So the next step is to publish the Entra ID users into vCenter’s Identity Broker (vIDB).
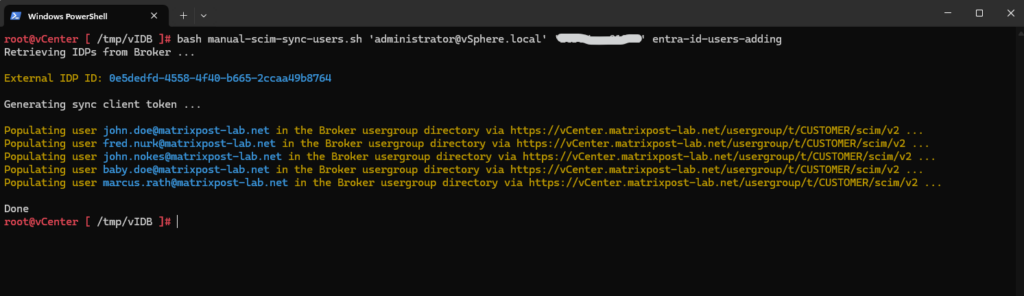
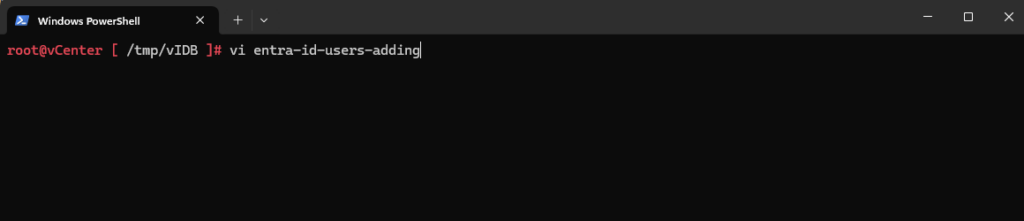
Therefore we need to connect to our vCenter Server’s (VCSA) console by using SSH. I will first create a separate folder within the /tmp folder to finally store the file with my Entra ID users I want to add to the Identity Broker (vIDB). I will name it entra-id-users-adding.
root@vCenter [ /tmp/vIDB ]# vi entra-id-users-adding
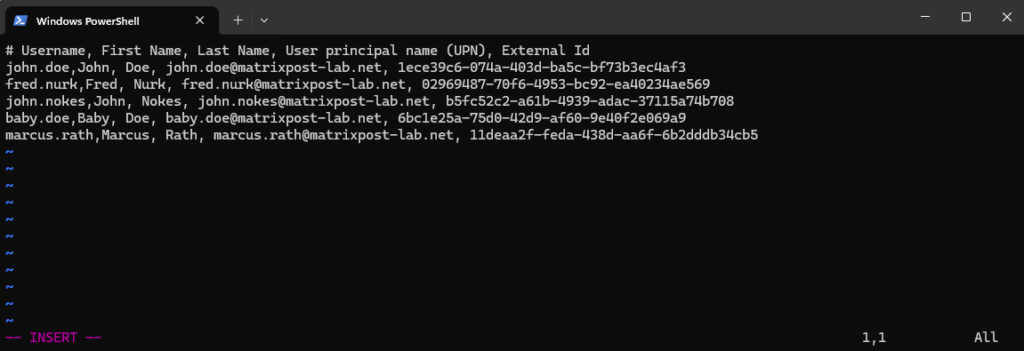
Create a file with all users you want to add manually to vCenter’s Identity Broker (vIDB).
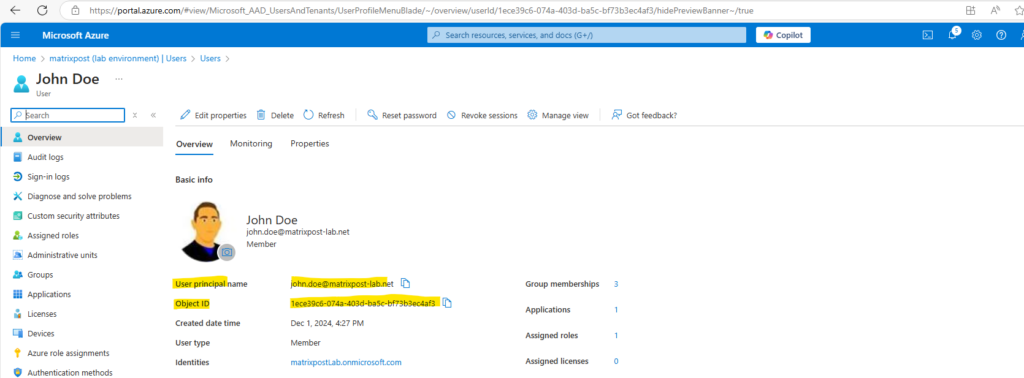
The External ID attribute below must match the Object ID attribute in Entra ID as shown below for the user John Doe.
# Username, First Name, Last Name, User principal name (UPN), External Id john.doe,John, Doe, john.doe@matrixpost-lab.net, 1ece39c6-074a-403d-ba5c-bf73b3ec4af3 fred.nurk,Fred, Nurk, fred.nurk@matrixpost-lab.net, 02969487-70f6-4953-bc92-ea40234ae569 john.nokes,John, Nokes, john.nokes@matrixpost-lab.net, b5fc52c2-a61b-4939-adac-37115a74b708 baby.doe,Baby, Doe, baby.doe@matrixpost-lab.net, 6bc1e25a-75d0-42d9-af60-9e40f2e069a9 marcus.rath,Marcus, Rath, marcus.rath@matrixpost-lab.net, 11deaa2f-feda-438d-aa6f-6b2dddb34cb5
Next I will create a new file to insert the manual-scim-sync-users.sh script which will finally publish our users in vCenter’s Identity Broker (vIDB).
root@vCenter [ /tmp/vIDB ]# vi manual-scim-sync-users.sh
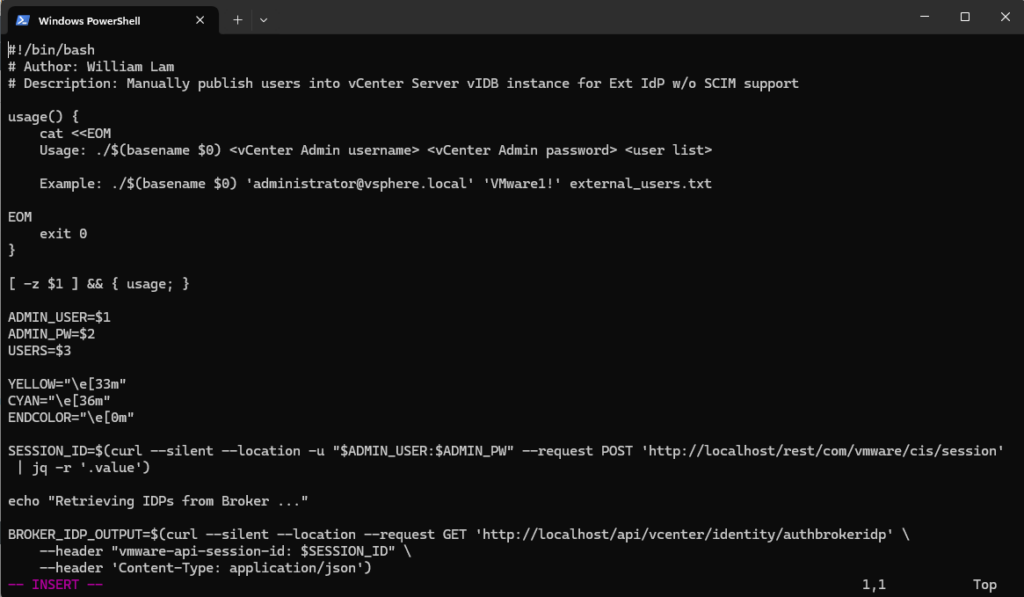
Manually publish users into vCenter Server vIDB instance for Ext IdP w/o SCIM support
https://github.com/lamw/vmware-scripts/blob/master/shell/manual-scim-sync-users.sh
We can now run the script to add our Entra ID users (added to the file) into vCenter’s Identity Broker (vIDB). The script is expecting the following three arguments: vSphere admin username, its password and the file name including our Entra ID users we want to add to.
As you can see on the screenshot below, I was already adding two more files, one is a file with all users we may want to remove again from the Identity Broker (vIDB) and one is the script to remove them. We will see this also further down.
root@vCenter [ /tmp/vIDB ]# bash manual-scim-sync-users.sh 'administrator@vSphere.local' 'password' entra-id-users-adding
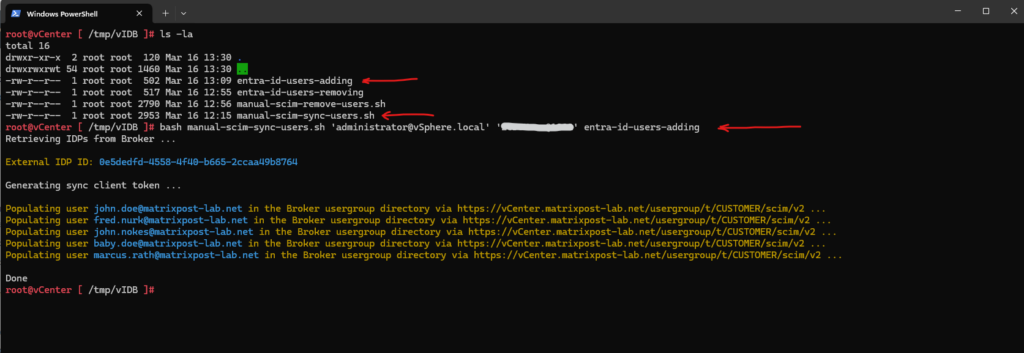
A quick check in the vSphere Client if my users are really imported successfully. Looks good!
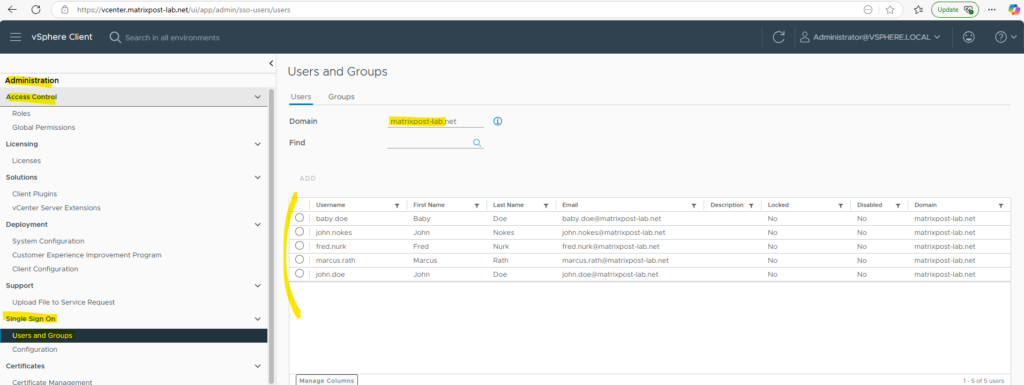
From now on we can authorize these users as usual by assigning the desired permission to.
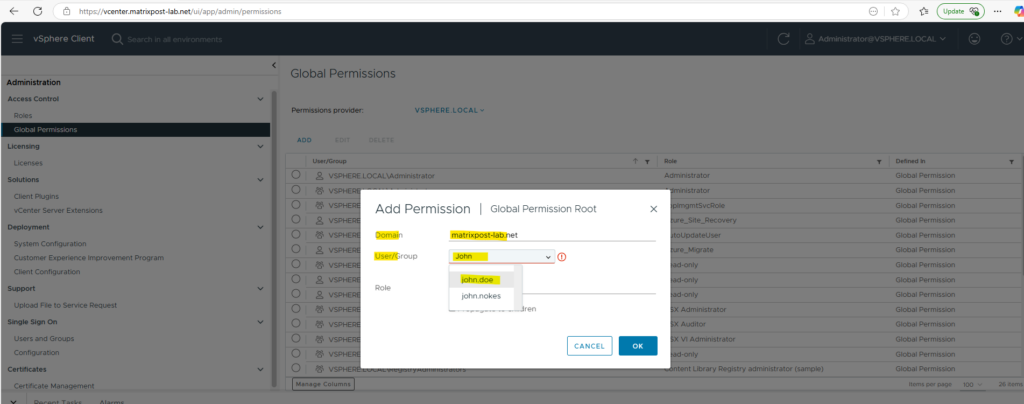
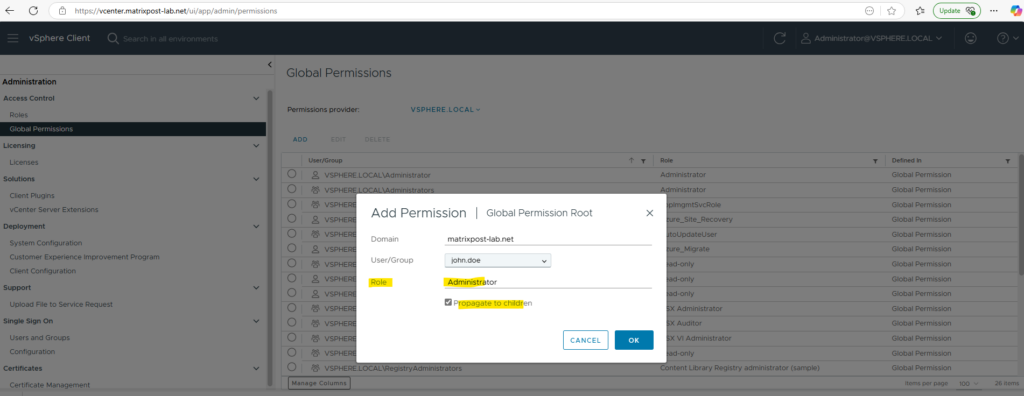
Here for example I will assign the user John Doe the Administrator role in vSphere.
If you set a permission at a vCenter Server level and propagate it to the children objects, the permission applies to data centers, folders, clusters, hosts, virtual machines, and similar objects in the vCenter Server instance.
I will now try if this user finally is able to sign-in to the vSphere Client by using its Entra ID account.
We get now correctly redirected to Microsoft’s primary authentication endpoint used for signing into Microsoft cloud services, including Microsoft Entra ID (Azure AD), Microsoft 365, and other Microsoft cloud applications.
Here especially the OpenID Connect endpoint for our Entra ID tenant we configured as new Identity provider (IdP) previously in the vSphere Client.
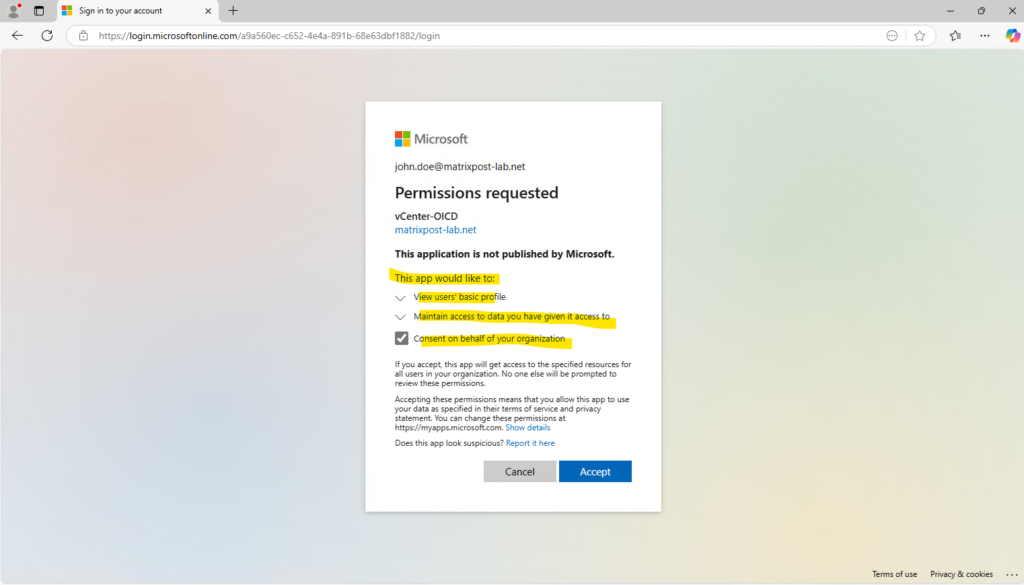
Accept to consent on behalf of your organization. Because John Doe has assigned the Global Administrator role in Entra ID, he can consent on behalf of my organization in Azure.
When integrating applications with Microsoft Entra ID, users and admins may encounter a “Consent on behalf of your organization” option during authentication. This setting determines whether an app can access data for multiple users without each user needing to grant consent individually.
Looks Good! The user is signed-in with its Entra ID account.
Removing Users manually from vCenter’s Identity Broker (vIDB)
As mentioned further above, we can also use a script to remove users manually from vCenter’s Identity Broker (vIDB).
Manually remove users from vCenter Server vIDB instance for Ext IdP w/o SCIM support
https://github.com/lamw/vmware-scripts/blob/master/shell/manual-scim-remove-users.sh
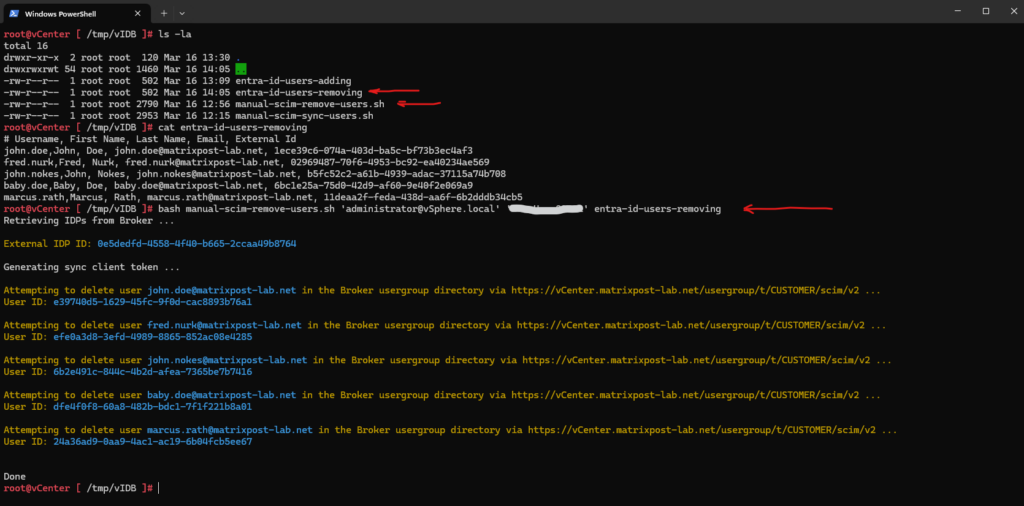
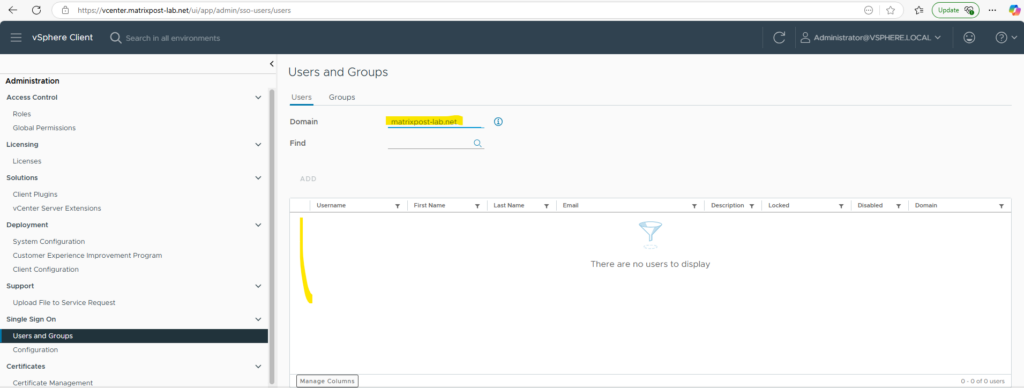
Looks good!
More about how to enable Microsoft Entra ID Authentication for vCenter Server
As mentioned to the beginning, I also wrote two previous posts about how to enable Microsoft Entra ID Authentication for vCenter Server, both will use SCIM for user provisioning, one is using the on-premise SCIM app by Microsoft and one the VMware Identity Service app.
Troubleshooting
ERROR: no healthy upstream while login to vCenter using domain accounts (or Login by using SIGN IN WITH ENTRA ID)
https://knowledge.broadcom.com/external/article/397359/error-no-healthy-upstream-while-login-to.html
Links
How to Enable Entra ID for vCenter Server
https://knowledge.broadcom.com/external/article/322179/how-to-enable-entra-id-for-vcenter-serve.htmlWhat is OpenID Connect (OIDC)?
https://www.microsoft.com/en-us/security/business/security-101/what-is-openid-connect-oidc


