How to reject Emails in Office 365 they fail DMARC
EASYDMARC had an interesting blog post about DMARC handling with Microsoft 365.
DMARC and Microsoft : What is Happening?
https://easydmarc.com/blog/dmarc-and-microsoft/
You will also find an article from Microsoft itself how they handle inbound email that fails DMARC.
How Microsoft 365 handles inbound email that fails DMARC
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/use-dmarc-to-validate-email?view=o365-worldwide#how-microsoft-365-handles-inbound-email-that-fails-dmarc
The main point is, that if the DMARC policy for the domain from the sending server is p=reject, and DMARC verification will fail from Exchange Online Protection (EOP), then EOP it will mark the message as spoof instead of rejecting it. So for inbound email, Microsoft 365 treats p=reject and p=quarantine the same way.
In short, email messages they fail DMARC, still landed in Microsoft 365 in the users Junk Email folder, instead get rejected by EOP and registered in the sending domains DMARC policy.
The reason for that Microsoft 365 is configured like this:
Microsoft 365 is configured like this because some legitimate email may fail DMARC. For example, a message might fail DMARC if it’s sent to a mailing list that then relays the message to all list participants. If Microsoft 365 rejected these messages, people could lose legitimate email and have no way to retrieve it. Instead, these messages will still fail DMARC but they’ll be marked as spam and not rejected.
Source: https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/use-dmarc-to-validate-email?view=o365-worldwide#how-microsoft-365-handles-inbound-email-that-fails-dmarc
So what I have to do to reject Email messages they fail DMARC
If you just want to quarantine the message you can edit the default Office 365 Anti phishing policy in the Microsoft 365 Defender portal under https://security.microsoft.com/antiphishing as follows.
Select the policy and click on Edit actions. As you can see Spoof intelligence is enabled by default. If not you can click on Edit protection settings to enable it. (second screenshot below)
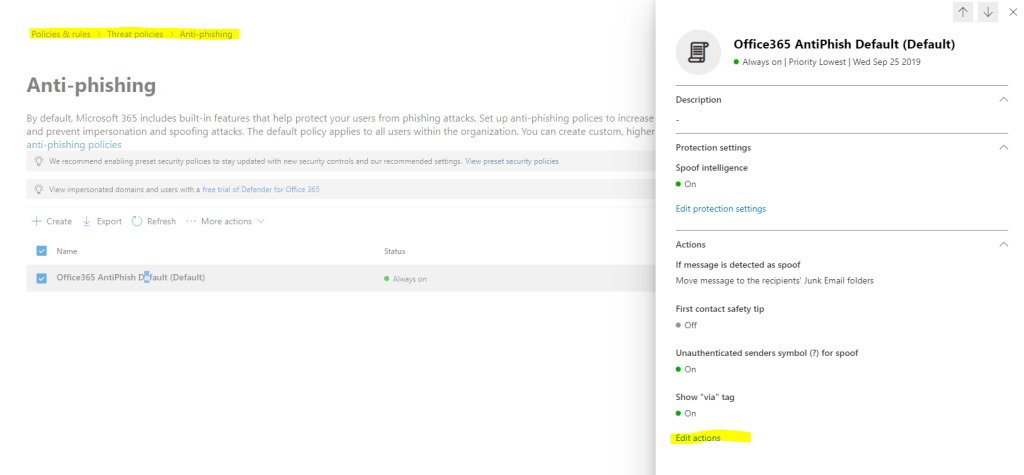
If not still enabled, you can enable it here.
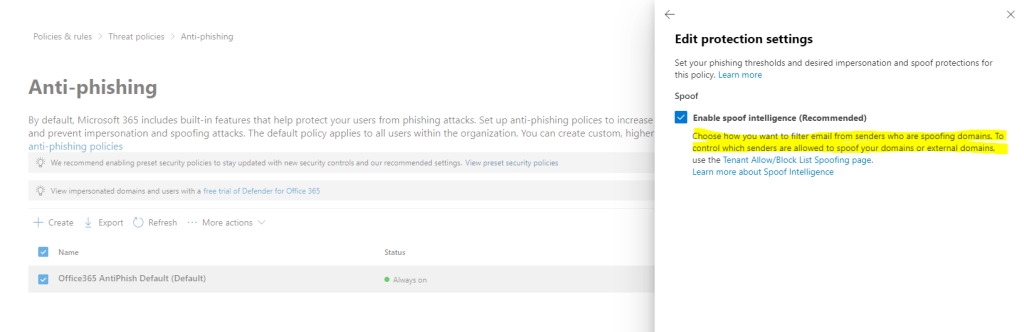
Here you can see the mentioned behavior how Microsoft 365 handle email messages they fail DMARC. By default the message is moved to the recipients Junk Email folders instead rejecting it.
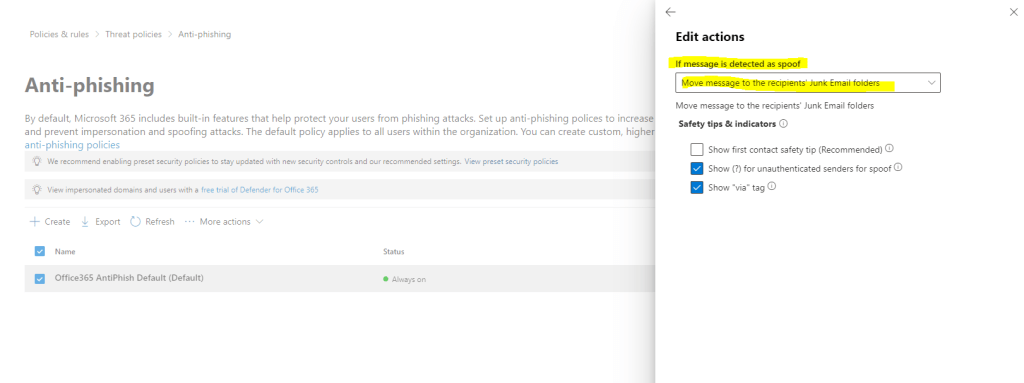
As you can see, by using the default policy we just can quarantine the message but not rejecting it. So to just quarantine the message we can select here Quarantine the message.
To reject the messages that fail DMARC we can create a new rule in the Exchange admin center under the Mail flow item as follows.
Your DMARC DNS TXT record still have to be p=reject
For example the _dmarc record for my lab environment and email domain braintesting.net is:
v=DMARC1; p=reject; rua=mailto:noreply-emailsecurity@braintesting.net; ruf=mailto:noreply-emailsecurity@braintesting.net;aspf=r
https://admin.exchange.microsoft.com/#/transportrules
Choose Create a new rule …
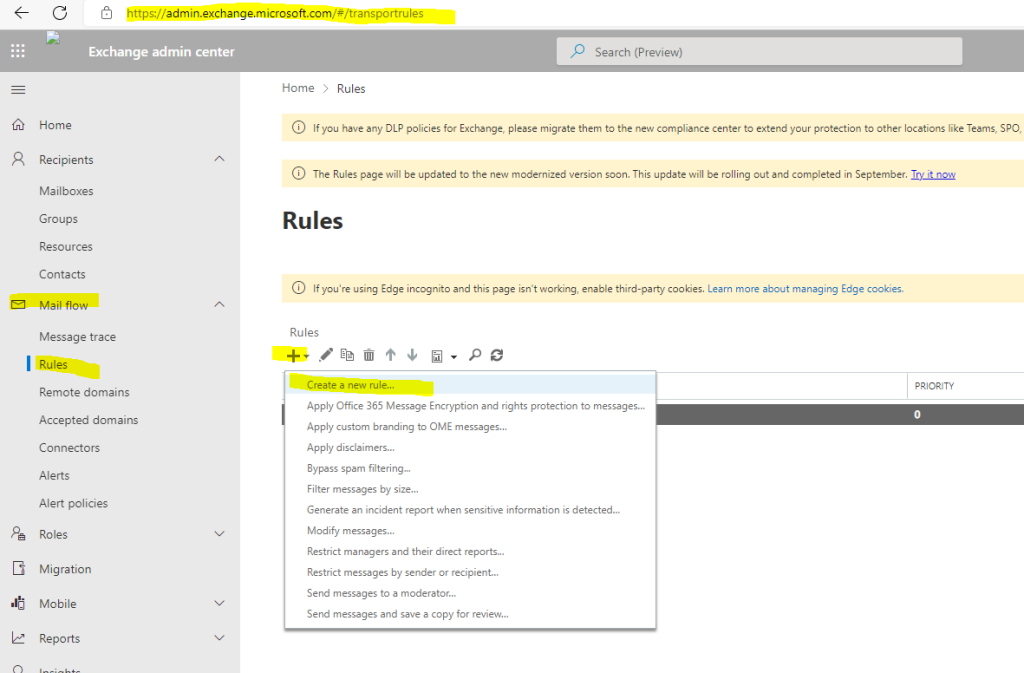
Click on More options …
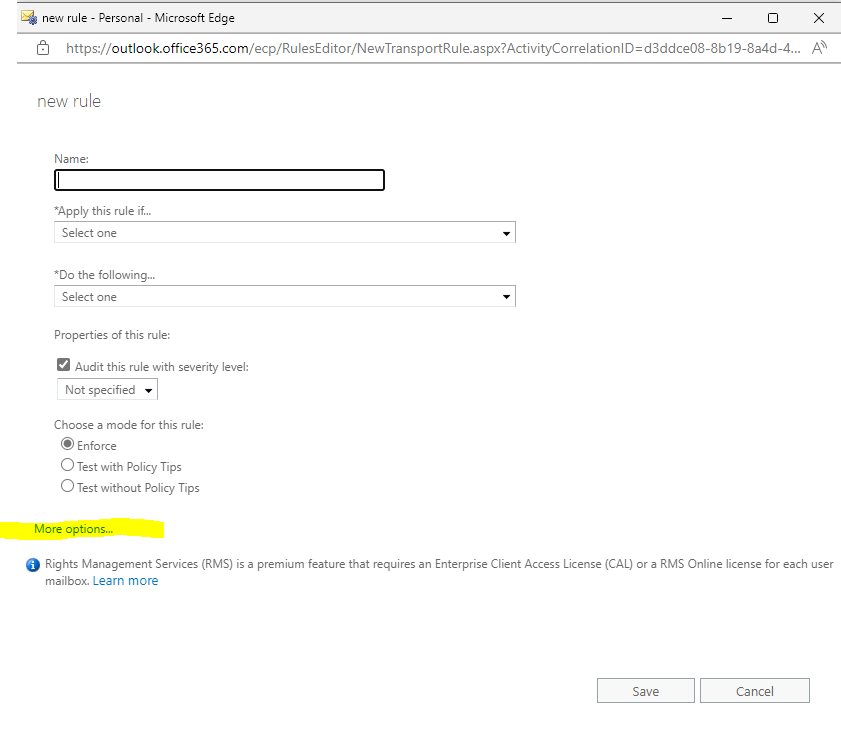
Give the rule a name like Reject Messages they fail DMARC.
Under Apply this rule if … select A message header … and includes any of these words
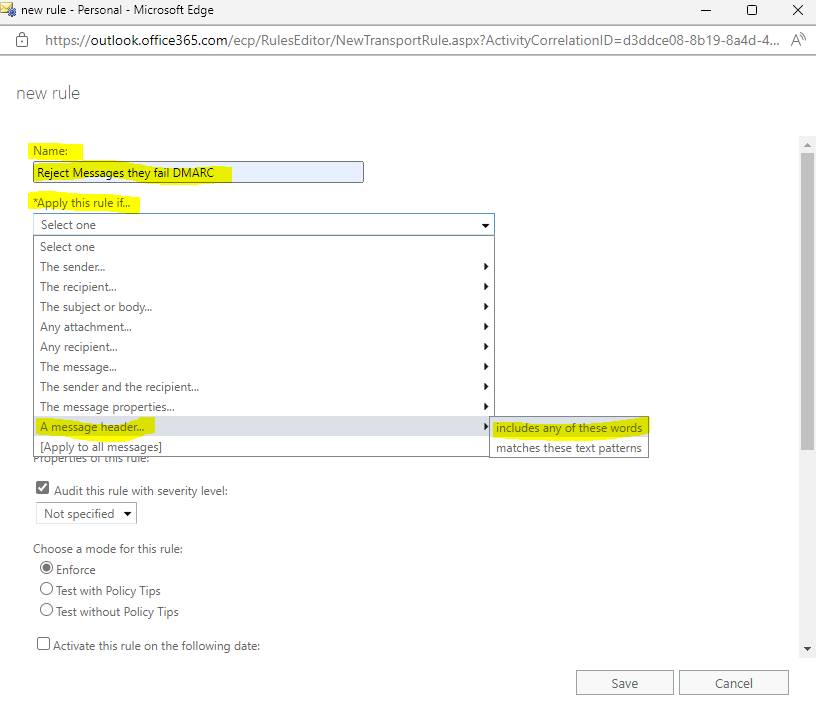
Click on Enter text … for specify header name and add Authentication-Results.
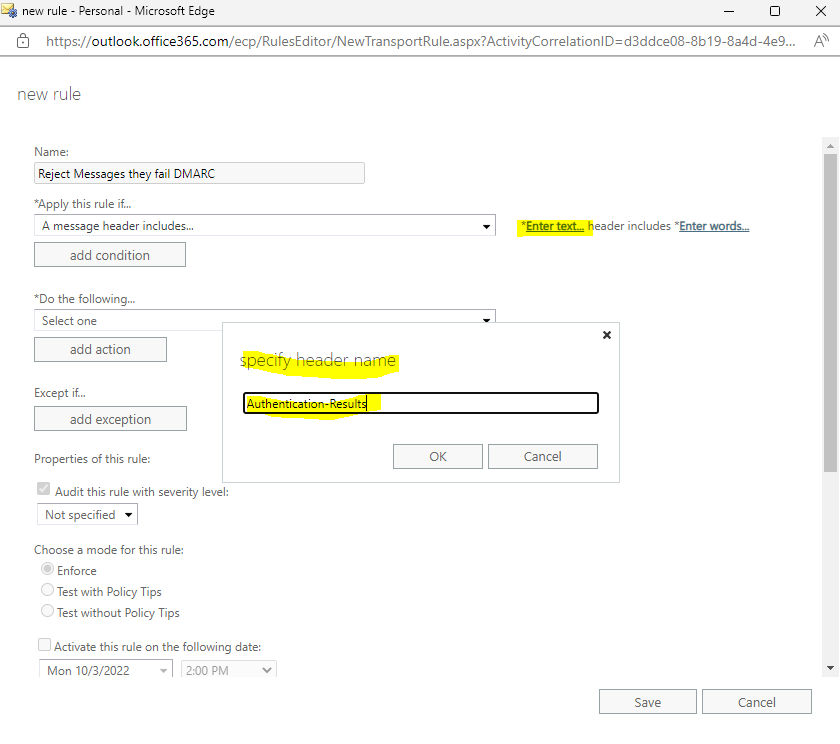
Click on Enter words … for specify words or phrases and add dmarc=fail action=oreject
The interesting point here is the message header field action=oreject
Indicates the action taken by the spam filter based on the results of the DMARC check.
oreject or o.reject: Stands for override reject. In this case Microsoft 365 uses this action when it receives a message that fails the DMARC check from a domain whose DMARC TXT record has a policy of p=reject. Instead of deleting or rejecting the message, Microsoft 365 marks the message as spam.
Source: https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/anti-spam-message-headers?view=o365-worldwide#authentication-results-message-header-fields
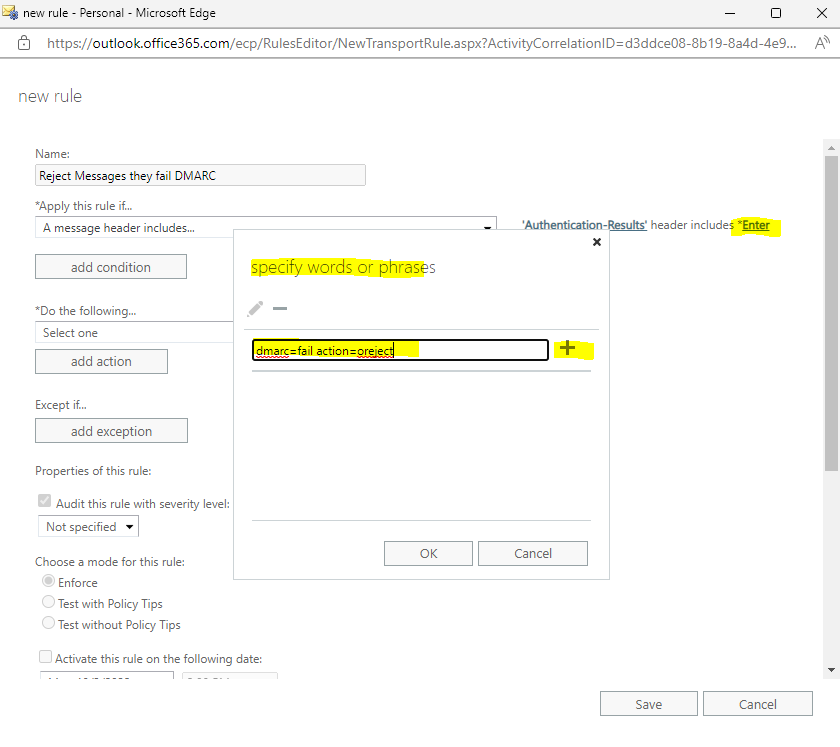
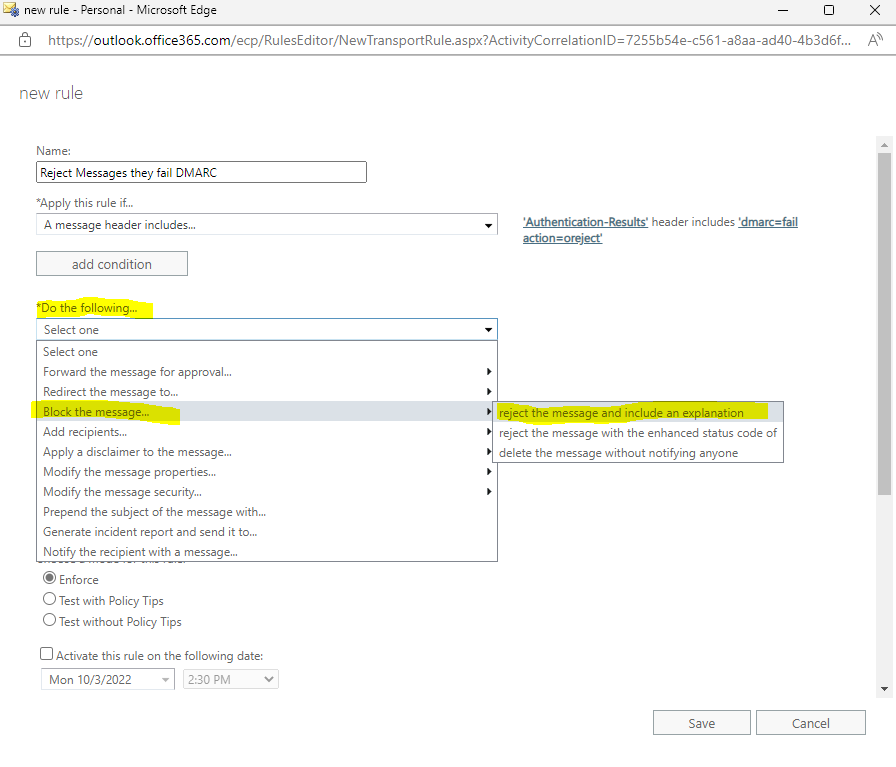
Next under Do the following … select Block the message … and reject the message and include an explanation
Keep in mind!
By rejecting the message and include an explanation, the real legitimate sender mailbox of course will get the NDR (Non Delivery Report). As the sender email is spoofed, unfortunately we cannot send the NDR to the actually spoofing sender.On one side this will inform the user which address was abused for email spoofing, otherwise I think most users will get confused by this NDR.
So you maybe better select here delete the message without notifying anyone
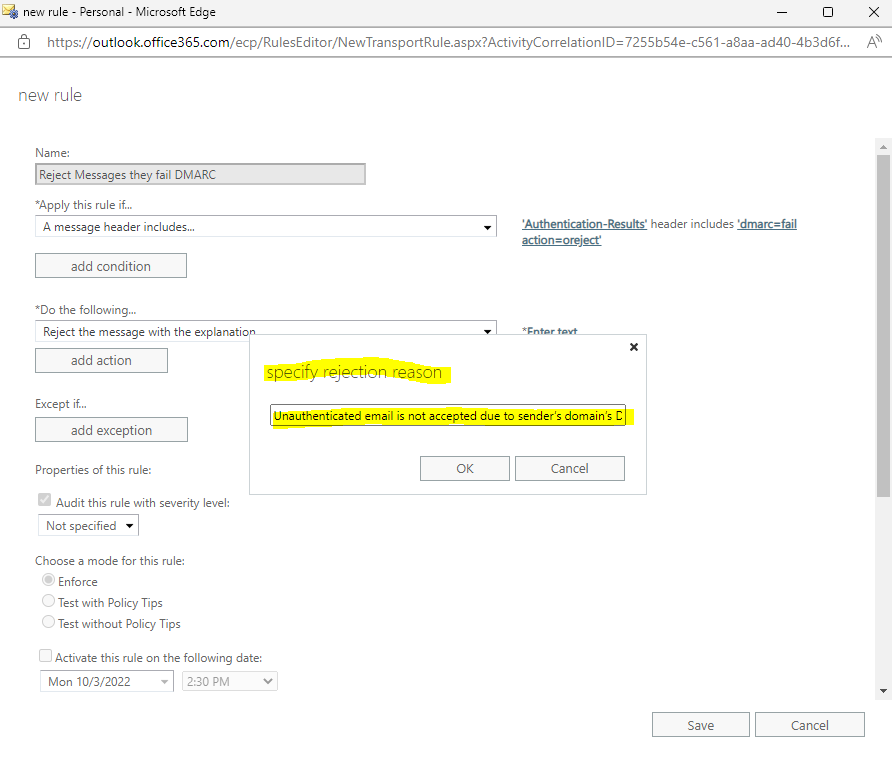
For specify rejection reason you can use for example Unauthenticated email is not accepted due to sender’s domain’s DMARC policy
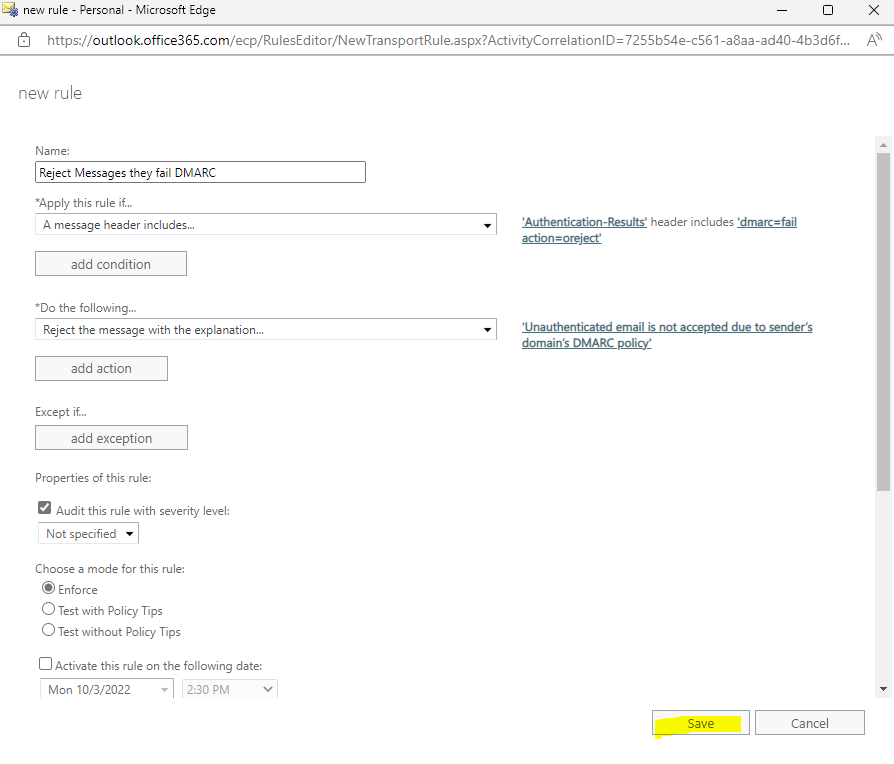
Now you can save the new rule.
From now on spoofed email messages should be rejected with a NDR (Non Delivery Report).
To test if it works, either you can use several online pages like for example https://emailspooftest.com or if available your own SMTP Server like postfix and shown below.
How to set up postfix on Ubuntu you can see in my following post.
My postfix server is just authoritative for the matrixpost.net SMTP domain.
To test email spoofing against my lab environment braintesting.net, I was adding a virtual mailbox John.Doe@braintesting.net on it.
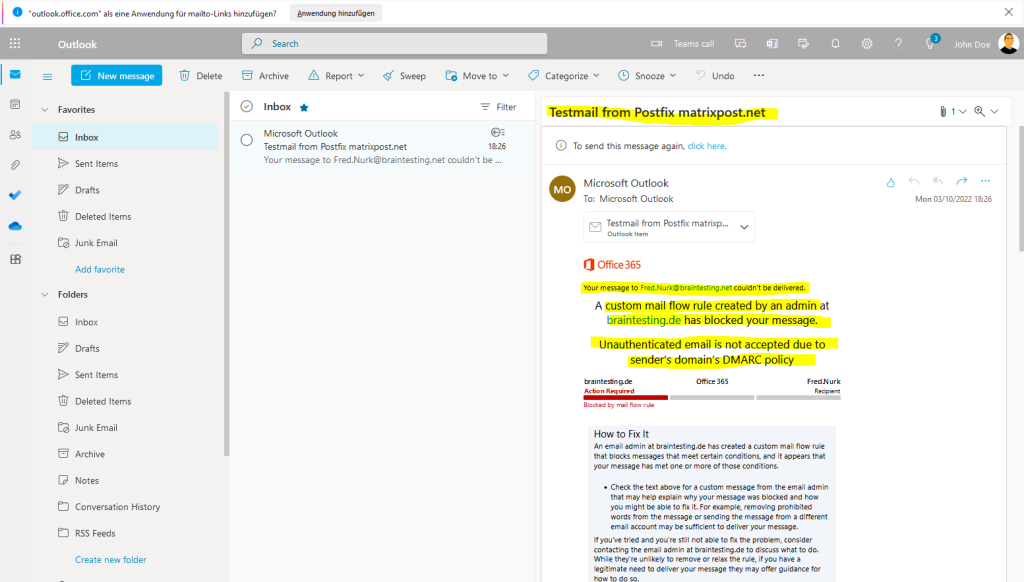
When I now send an email from this mailbox, which is hosted on my postfix server, to the recipient Fred.Nurk@braintesting.net in my lab environment and hosted in Microsoft 365 (Exchange Online), the real legitimate mailbox from John.Doe@braintesting.net will get the NDR (Non Delivery Report) as shown below.
So it works as expected!
But as mentioned earlier, this NDR report can confuse your users, so maybe you better use above at configuring this rule just delete the message without notifying anyone
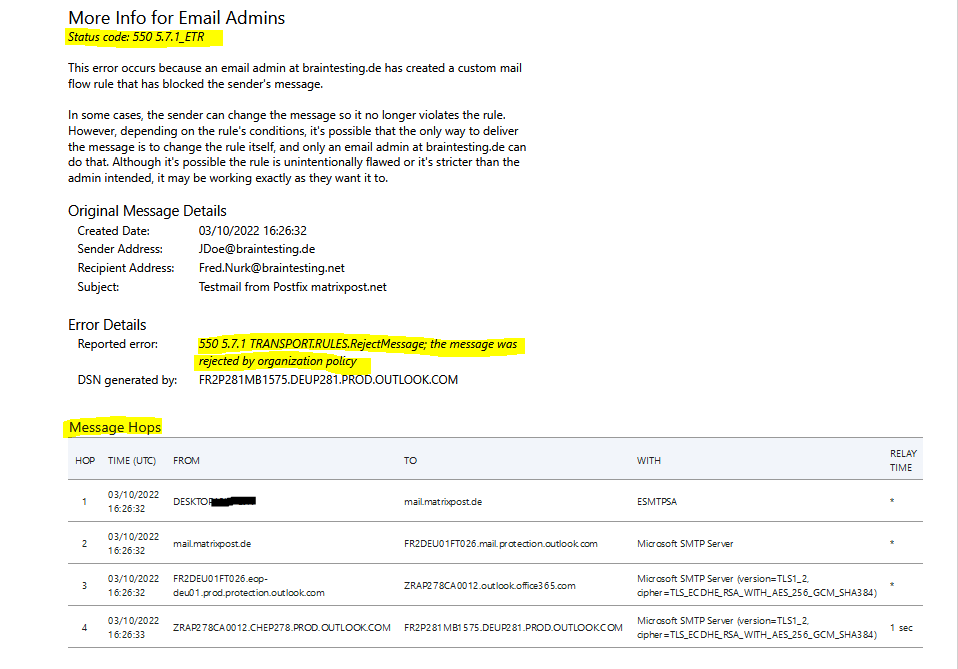
You will also get a detailed log. Here you can see the sender address which actually was John.Doe@braintesting.net, but MS will show here the username if different from the email address.
Links
How Microsoft 365 handles inbound email that fails DMARC
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/use-dmarc-to-validate-email?view=o365-worldwide#how-microsoft-365-handles-inbound-email-that-fails-dmarc
Authentication-results message header fields
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/anti-spam-message-headers?view=o365-worldwide#authentication-results-message-header-fields
DMARC and Microsoft : What is Happening?
https://easydmarc.com/blog/dmarc-and-microsoft/



