How to reset a forgotten or not knowing Root Password for Linux by using the GRUB Boot Loader
In this post I want show how easily you can reset the root user password by using the GRUB 2 Boot Loader. There are several ways how you can reset a forgotten or not knowing root password in case you have directly access to the computer or in case of a virtual machine like below, access to the hypervisor and its virtual console.
Another way and not topic of this post is to boot from a Live/Installation CD/DVD/ISO and change root (chroot) into the Linux OS containing the user and password we want reset as shown in my following post.
About how to get privileged access to a domain controller or any other Windows computer running a recent Windows OS, you can also read my following post https://blog.matrixpost.net/domain-controller-protection-via-bitlocker-drive-encryption/#anchorlink_privileged_access.
Law #3: If a bad guy has unrestricted physical access to your computer, it’s not your computer anymore. (Ten immutable Laws of Security)
The immutable laws of security
https://learn.microsoft.com/en-us/security/zero-trust/ten-laws-of-security#immutable-laws-of-security-v2
In order to prevent unauthorized access to the GRUB command line and modifying kernel boot parameters, you can secure access by set up a GRUB password like shown further down.
In the GRUB 2 boot screen, highlight the entry you want to modify by using the arrow keys ↑ and ↓.
Press the E key.
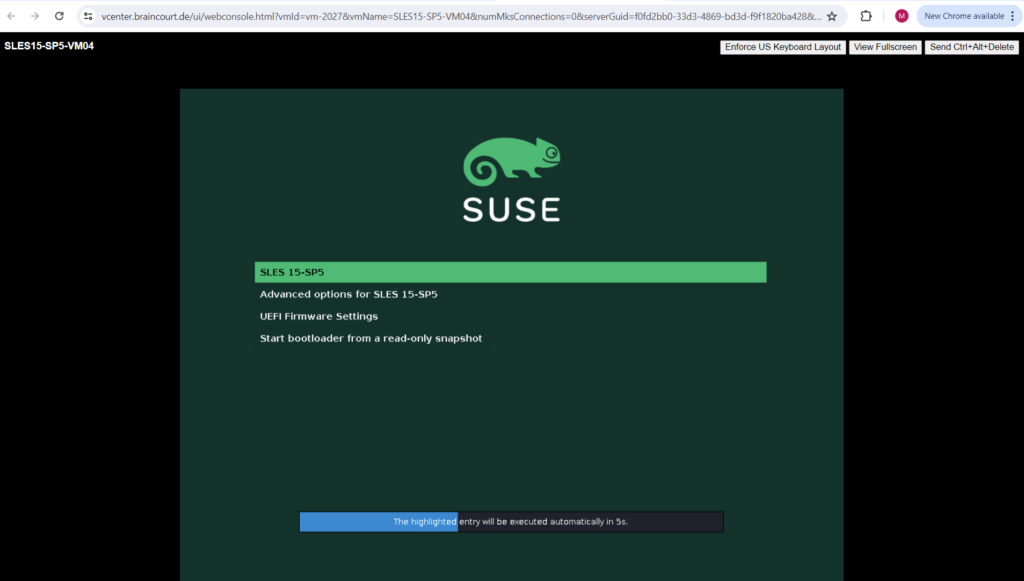
You will be presented with an editor and the content of the selected boot entry. It will look similar to the following screenshot. Find the line that starts with linux as shown below.
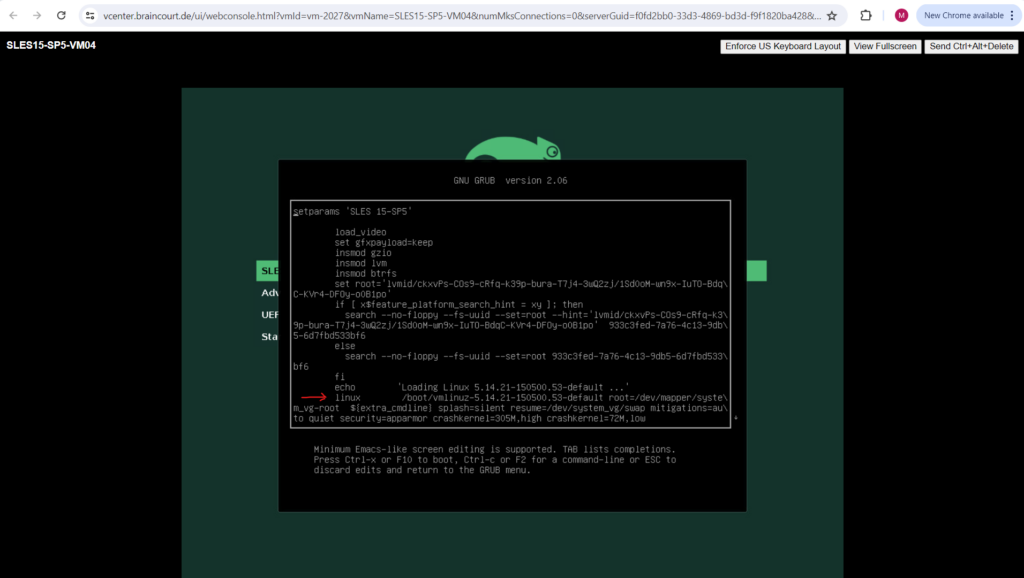
Add the following kernel boot parameter at the end of the line or somewhere between like shown below. The system will then boot directly into a Bash Shell with root permissions.
Press CTRL+ X or F10 to boot after adding the entry into the shell
init=/bin/bash
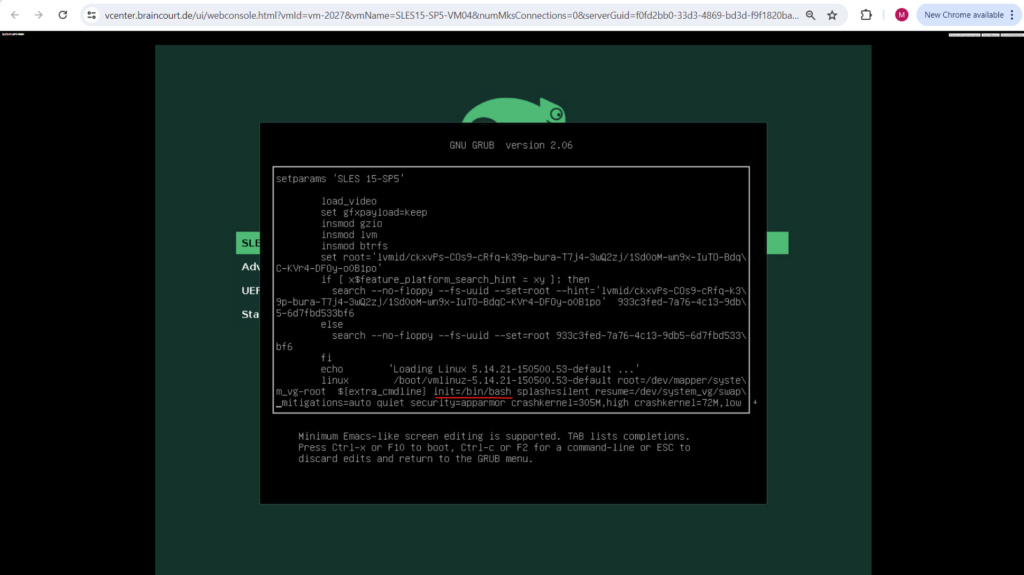
The system will boot.
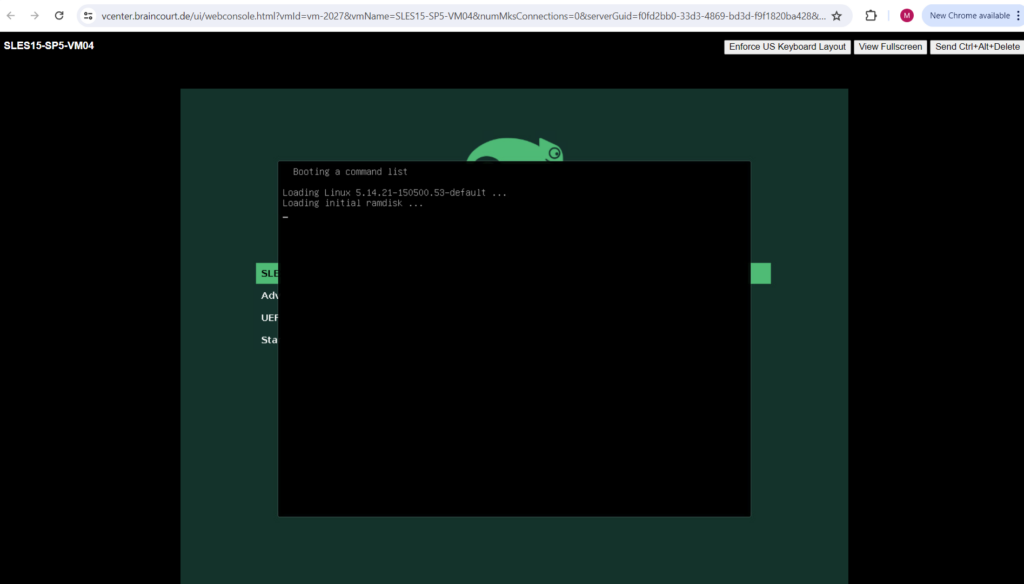
The Bash shell is shown up without having to provide a user and password like shown below.
!!! Note !!!
In past I was running unfortunately sometimes into an issue so that the system doesn’t boot into a Bash Shell with root permissions on the first try. Sometimes the system stuck at a black screen or it was booting as usual and supposedly skipping the by hand added kernel parameter.All these times it finally works by just repeating the procedure two or three times in a row.
!!! Note !!!
Sometimes depending on the distribution you also need to use the Bourne Shell sh by using the following kernel boot parameter -> init=/bin/sh and putting it at the end of the line that starts with linux.
On SUSE Linux Enterprise Server we can already see just because of the Bash prompt, that the system was booted directly into a Bash Shell with root permissions. (On Debian/Ubuntu it is also the # character but in white and not red color btw.)
About how to customize the Bash prompt you can read btw. my following post https://blog.matrixpost.net/set-up-suse-linux-enterprise-server/#anchorlink_bash_prompt.
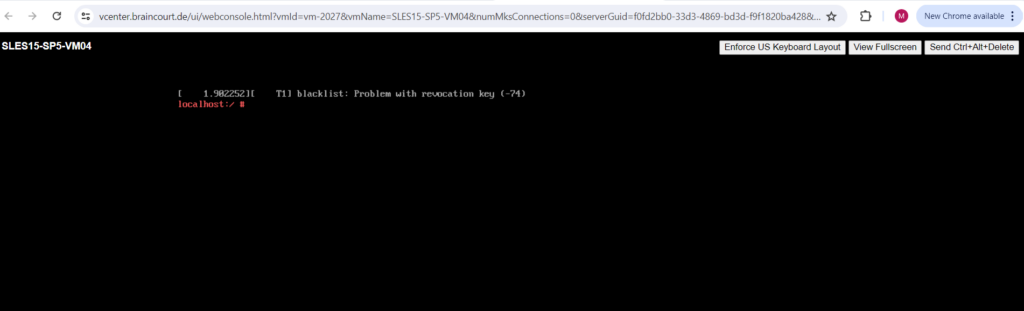
So far the filesystem is just mounted for read access.
To finally be able to change the root account password, we first need to mount the / root filesystem with read/write access as follows.
# mount -o remount,rw /
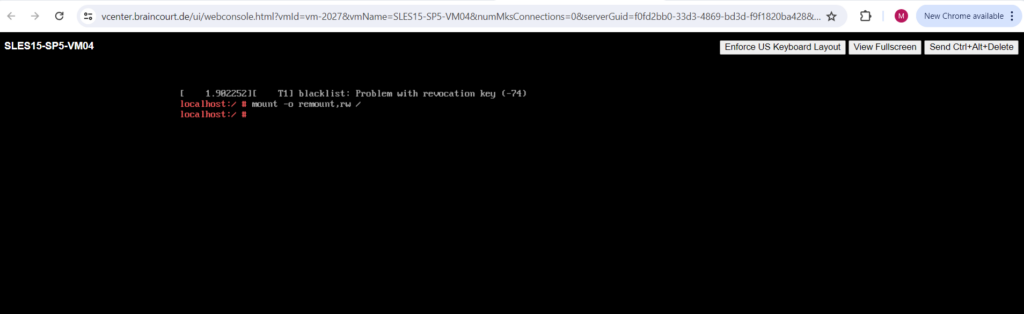
Now we can change the password for the root user as usual.
# passwd root
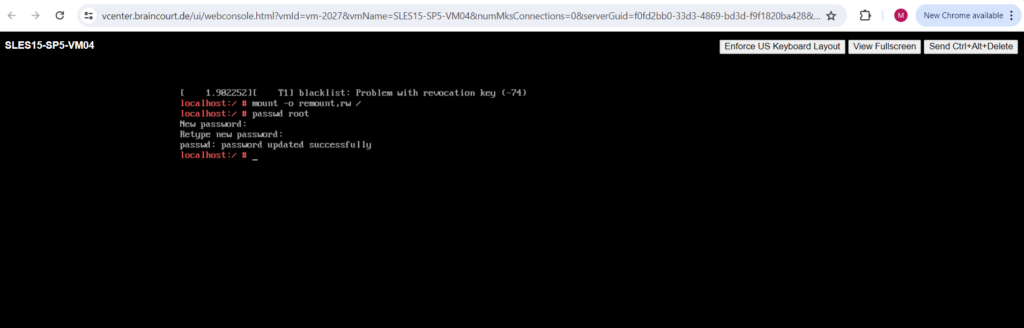
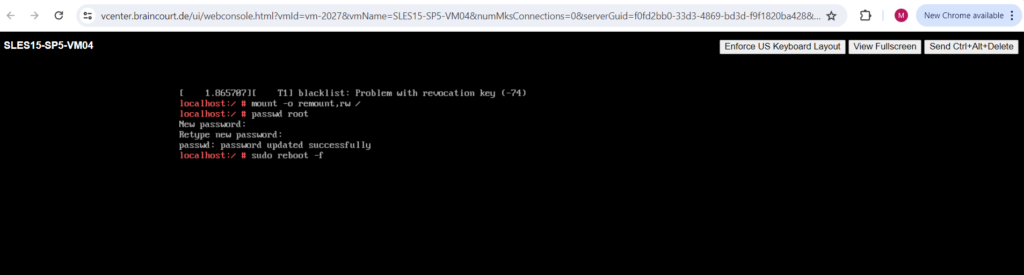
Finally reboot the system. From now on you should be able to logon to the system by using the root user and the new password.
# sudo reboot -f
Set up a GRUB password
As mentioned to the beginning, in order to prevent unauthorized access to the GRUB command line and modifying kernel boot parameters, you can secure access by set up a GRUB password.
Be aware that this is just a basic protection to prevent an unauthorized user from gaining access to the operating system via the GRUB 2 menu. Persons with physical access to the computer can gain access to the files via other methods which GRUB 2 cannot prevent like booting from a Live CD.
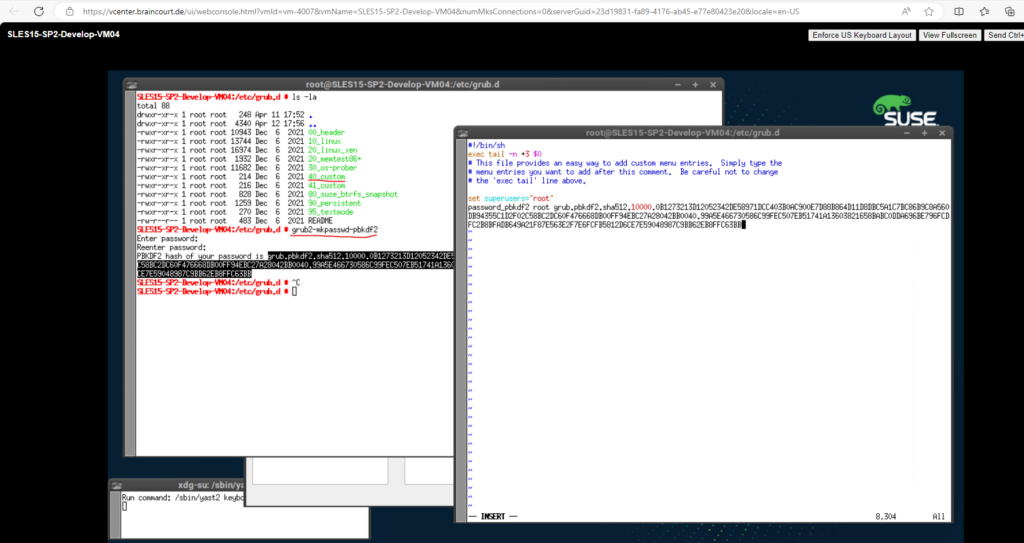
First we need to create a new password hash by executing the grub2-mkpasswd-pbkdf2 tool.
# grub2-mkpasswd-pbkdf2
The returned encrypted password hash we then need to place along with a so called superuser into the /etc/grub.d/40_custom file.
The superuser/user information and password do not have to be contained in the /etc/grub.d/00_header file. The information can be placed in any /etc/grub.d file as long as that file is incorporated into grub.cfg. The user may prefer to enter this data into a custom file, such as /etc/grub.d/40_custom so it is not overwritten should the Grub package be updated. If placing the information in a custom file, do not include the “cat << EOF” and “EOF” lines as the content is automatically added from these files.
set superusers="root" password _pbkdf2 root <password hash>
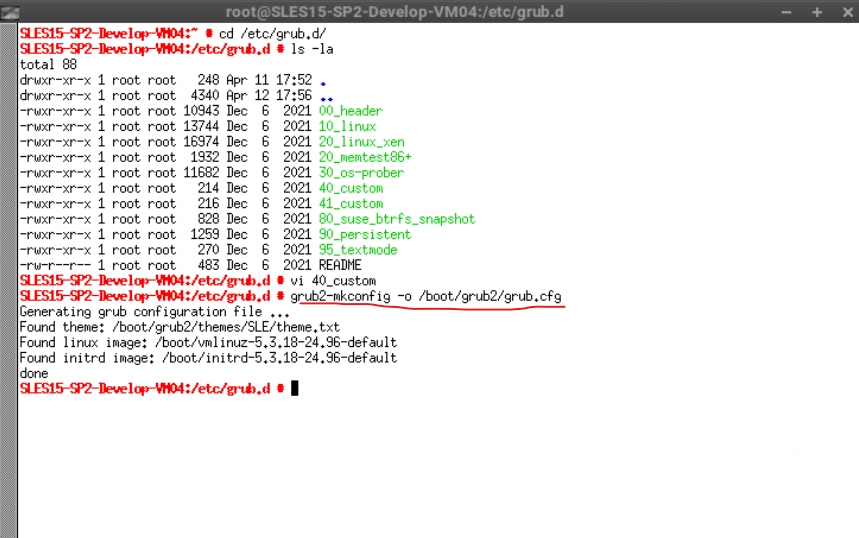
Finally we need to execute the following command to write the new configuration to GRUB.
# grub2-mkconfig -o /boot/grub2/grub.cfg
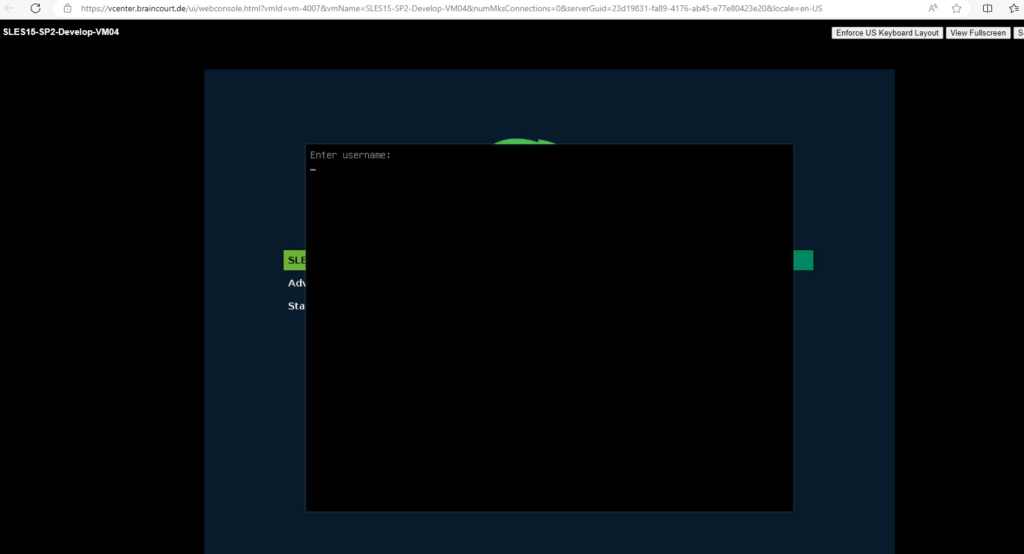
From now on when you highlight in the GRUB 2 boot screen a entry you want to modify by using the arrow keys ↑ and ↓ and then pressing the E key, you need to provide the username and password we set previously to access the GRUB command line and editor as shown below.
Links
GNU GRUB
https://www.gnu.org/software/grub/Temporarily modifying kernel boot parameters
https://documentation.suse.com/smart/systems-management/html/task-modify-kernel-boot-parameter/index.htmlGrub2/Passwords
https://help.ubuntu.com/community/Grub2/Passwords


