pfSense | Site-to-Site IPSec VPN | Subnets on each Site are identical
If you want to connect subnets from two sites over an IPSec Site-to-Site VPN and both subnets on each site are identical, you have to use 1:1 NAT aka BINAT (Bidirectional NAT) to overcome this pitfall.
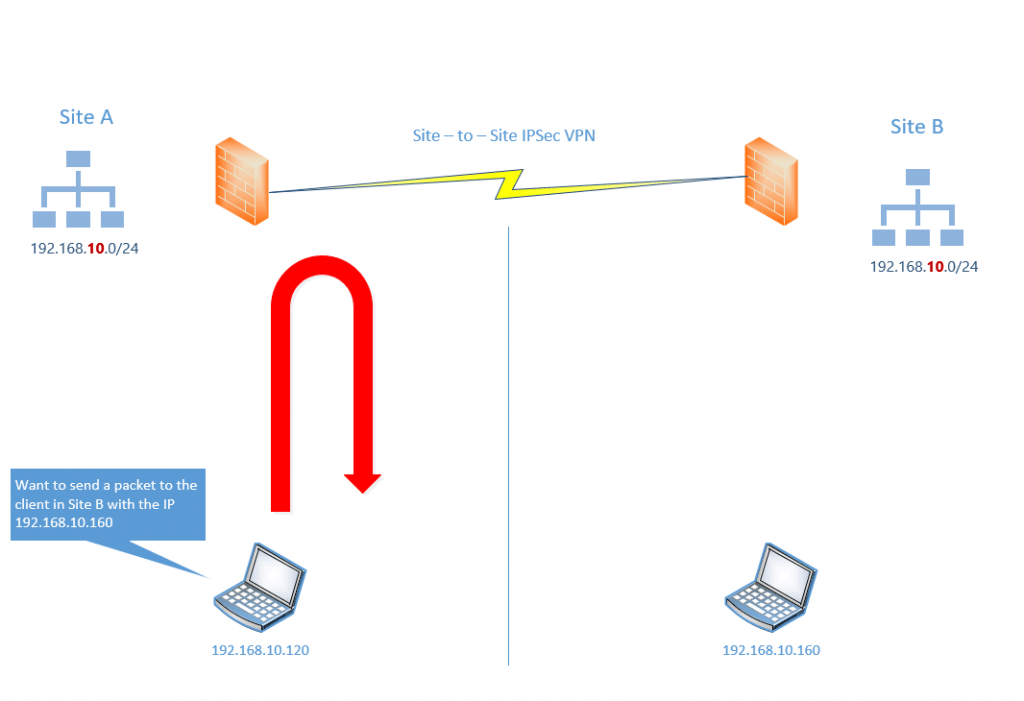
Imagine the following situation. You want to connect Site A over an IPSec Site-to-Site VPN Tunnel with Site B. The pitfall is that both sites using the same subnet 192.168.10.0/24.
If in the figure below the client from Site A with its own IP 192.168.10.120 wants to send a packet to the client in Site B with the IP 192.168.10.160.
The packet from the client in Site A will be never send to and hit the gateway in Site A because the destination IP resides in the same subnet and therefore the client tries to submit the packet directly to the destination in the same subnet. So the packet will never reaches the destination and remote network.
Therefore you can use NAT/BINAT translation on both sites to mask the real networks 192.168.10.0/24 behind a different network which doesn’t exists on the other site.
In case both sites wants access each destination on the other site, we have to translate the complete network/subnet on each site.
For example Site A will mask/translate his local network 192.168.10.0/24 behind the network 192.168.100.0/24 and Site B will also mask/translate his local network 192.168.10.0/24 behind the network 192.168.200.0/24.
In pfSense this would look like this from Site A in phase 2 for the IPSec tunnel configuration:
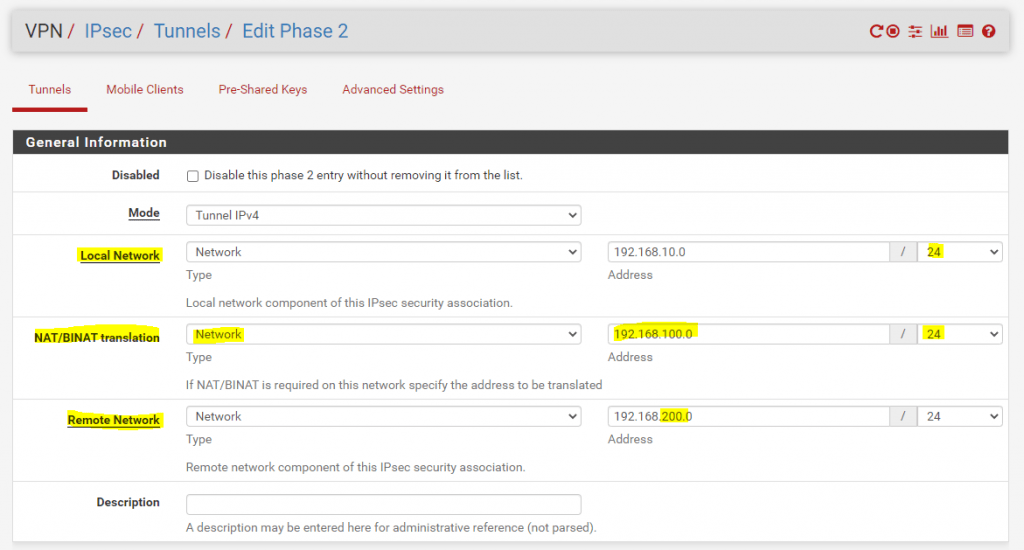
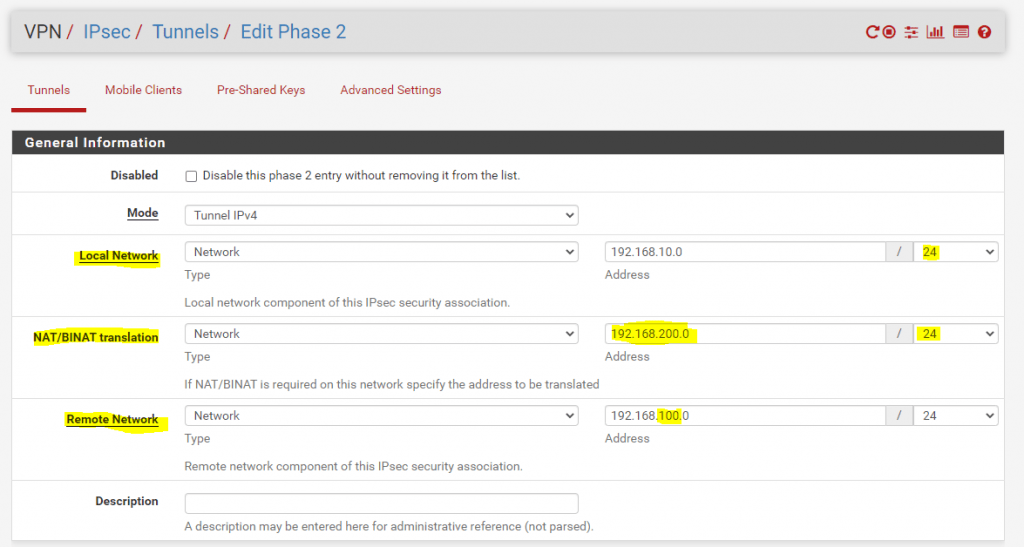
Above you can see that Site A mask/translate his local network 192.168.10.0/24 with 192.168.100.0/24 toward Site B. For the remote network in Site B we have to enter the new masked/translated network 192.168.200.0/24 from Site B. In order that this work, Site B on his part also have to mask/translate its own local network behind the network 192.168.200.0/24 toward Site A.
On Site B this would look like this in pfSense:
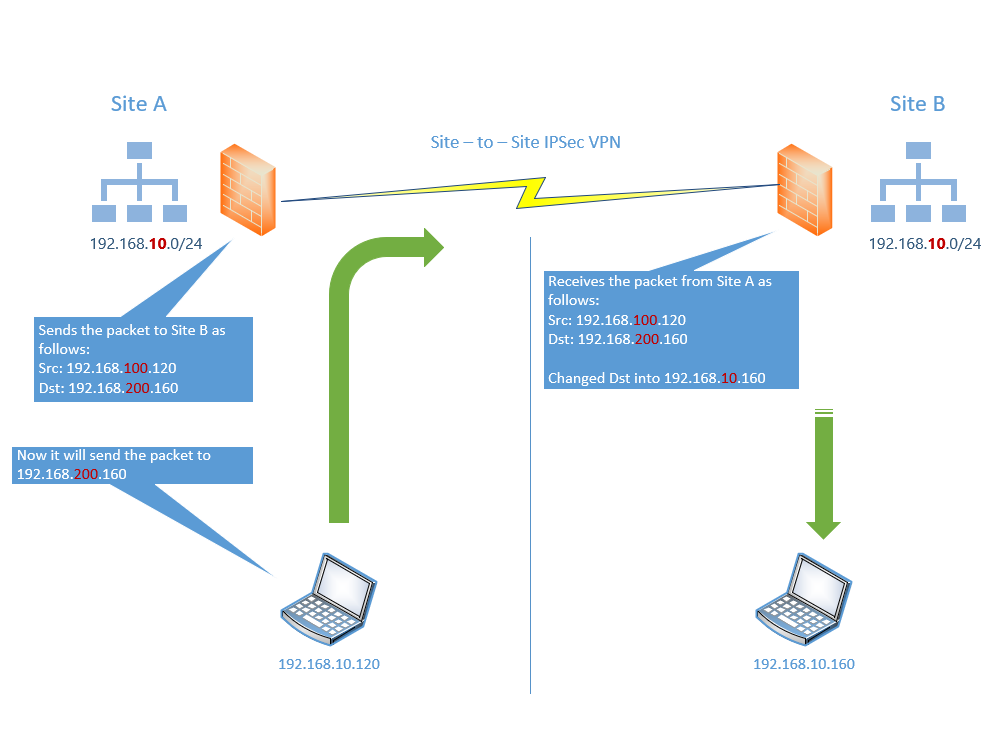
If now the client from Site A sends a packet to the client in Site B, pfSense in Site A will translate the source IP 192.168.10.120 from the client in Site A into 192.168.100.120 toward Site B.
Incoming packets from Site B to the client in Site A will then also have the masked/translated destination IP 192.168.100.120, therefore pfSense in Site A have to change the destination IP into the real IP in Site A with 192.168.10.120 in order to be able to submit the packets to the Client in Site A.
The same happens in Site B for the other way.
Because of that clients in each site have to know the masked/translated IP from the destination in the other site as it is not possible to address them with their real IP as mentioned.
So if my client in Site A wants to send a packet to the client in Site B, it cannot send the packet to its real IP 192.168.10.160, instead it have to use the masked/translated new IP 192.168.200.160.
You can accomplish this with a new DNS Forward Lookup Zone or Conditional Forwarders in each site which contains the masked IPs or quick an dirty in smaller deployments with local hosts files.
In the example above we assumed that both sites want to access each other.
In cases only one site want’s to access the other site, you can mask/translate the site who wants to access the remote site just behind one IP address instead a complete network/subnet.
Also known as Port Address Translation
Port Address Translation (PAT), is an extension to network address translation (NAT) that permits multiple devices on a local area network (LAN) to be mapped to a single public IP address. The goal of PAT is to conserve IP addresses.
In this case it is mapped to a single local network address.
For example only clients from Site A wants to access clients in Site B. In this case the configuration in pfSense from Site A looks like this:
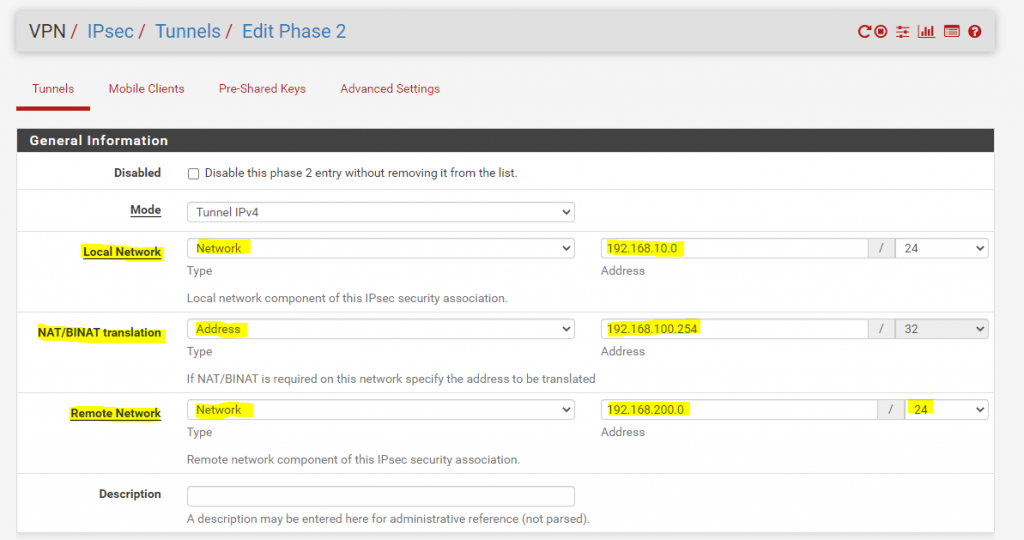
The network 192.168.10.0/24 from Site A will be masked/translated with one IP address 192.168.100.254/32 toward Site B.
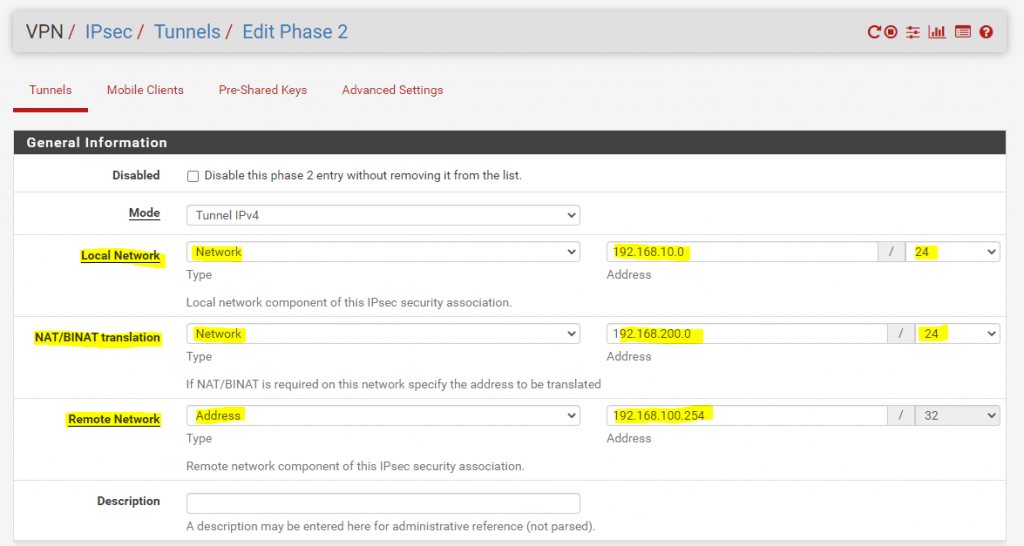
In Site B the configuration should look like this. The local network is masked/translated with 192.168.200.0/24 as used but for the remote network in Site A we only have to use one IP address 192.168.100.254/32.
Therefore we do not have to waste a complete /24 subnet in Site B as we only have to spend one IP address for the remote network.
Links
Network address translation (NAT)
https://en.wikipedia.org/wiki/Network_address_translation
Port and Address Translation (PAT)
https://de.wikipedia.org/wiki/Port_Address_Translation
NAT with IPsec Phase 2 Networks
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/phase-2-nat.html



